Entity authenticating system and method of cognitive radio network based on hierarchical structure
A technology of cognitive radio and authentication system, which is applied in the field of entity authentication system, can solve problems such as not considering spectrum switching and the impact of scheme efficiency, and achieve the effect of preventing denial of service attacks and congestion, and reducing authentication delay
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] Below in conjunction with example the present invention will be further described.
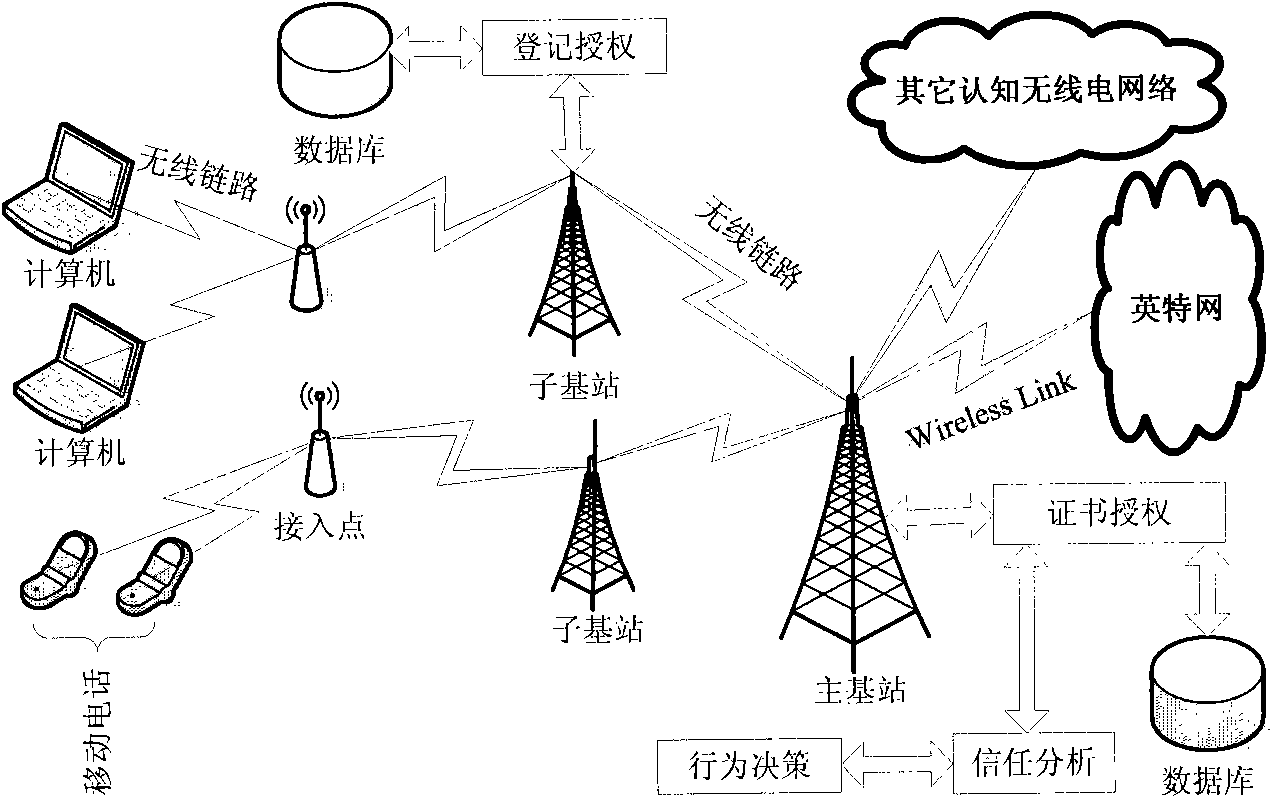
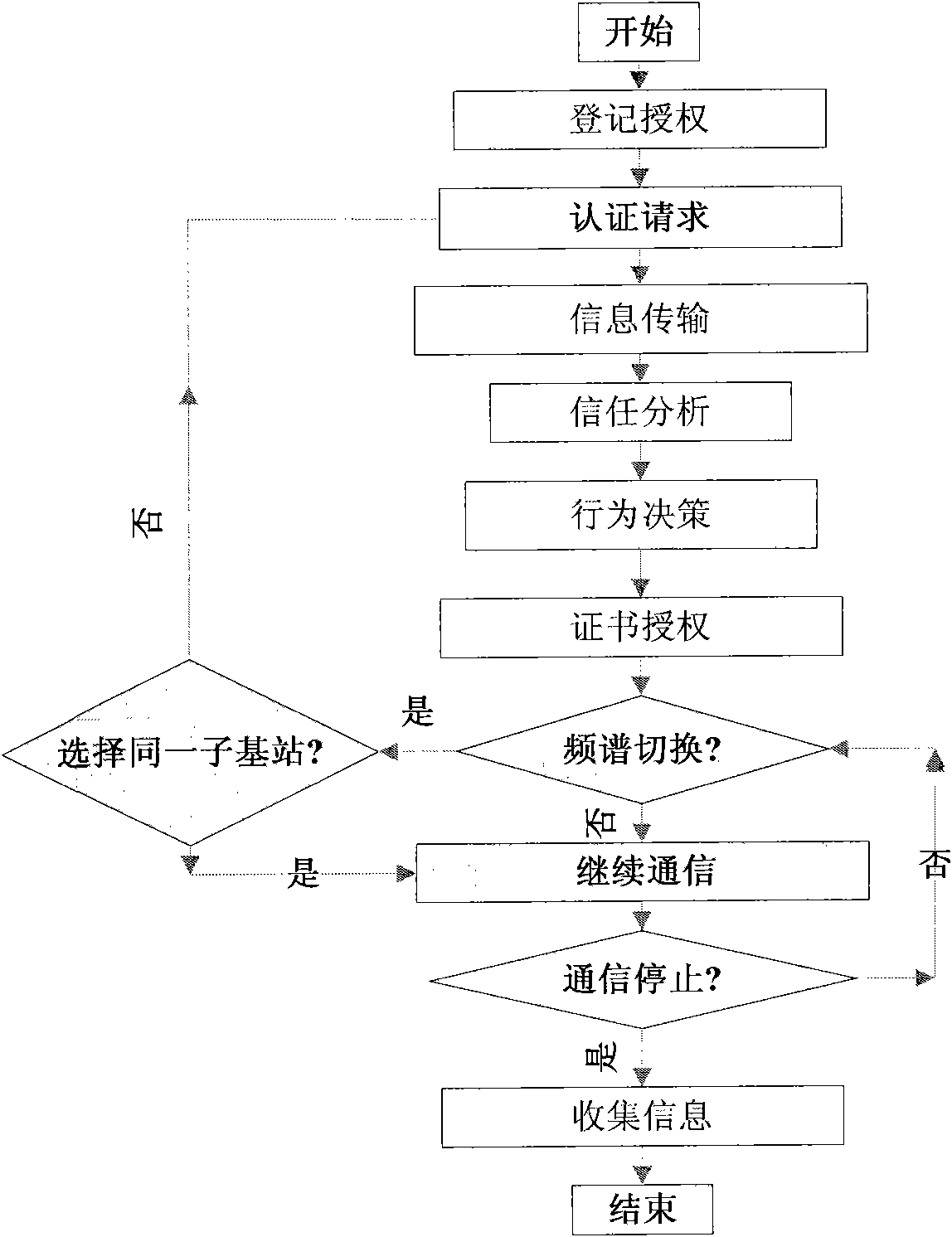
[0029] Such as figure 1 The entity authentication system and method authentication system based on the hierarchical structure cognitive radio network of the present invention is an authentication system diagram based on the layered architecture. Computers and mobile phones represent secondary users, and each sub-base station is directly connected to a database except the main base station Used to store digital certificates. The digital certificate includes a public key, user identification code and encrypted information. The main task of the main base station is to connect all sub-base stations and access the main network, such as the Internet or other cognitive radio networks. There is a unique wireless link between each sub-base station and the main base station to exchange data, and the main base station is connected to other cognitive radio networks. Therefore, the authentication ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com