A radio frequency identification security authentication method and system
A security authentication and radio frequency identification technology, applied in the field of security authentication, can solve the problems of denial of service, spending a lot of resources, destroying the synchronization of key updates, etc., to prevent counterfeiting attacks, help scale, and reduce difficulty.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
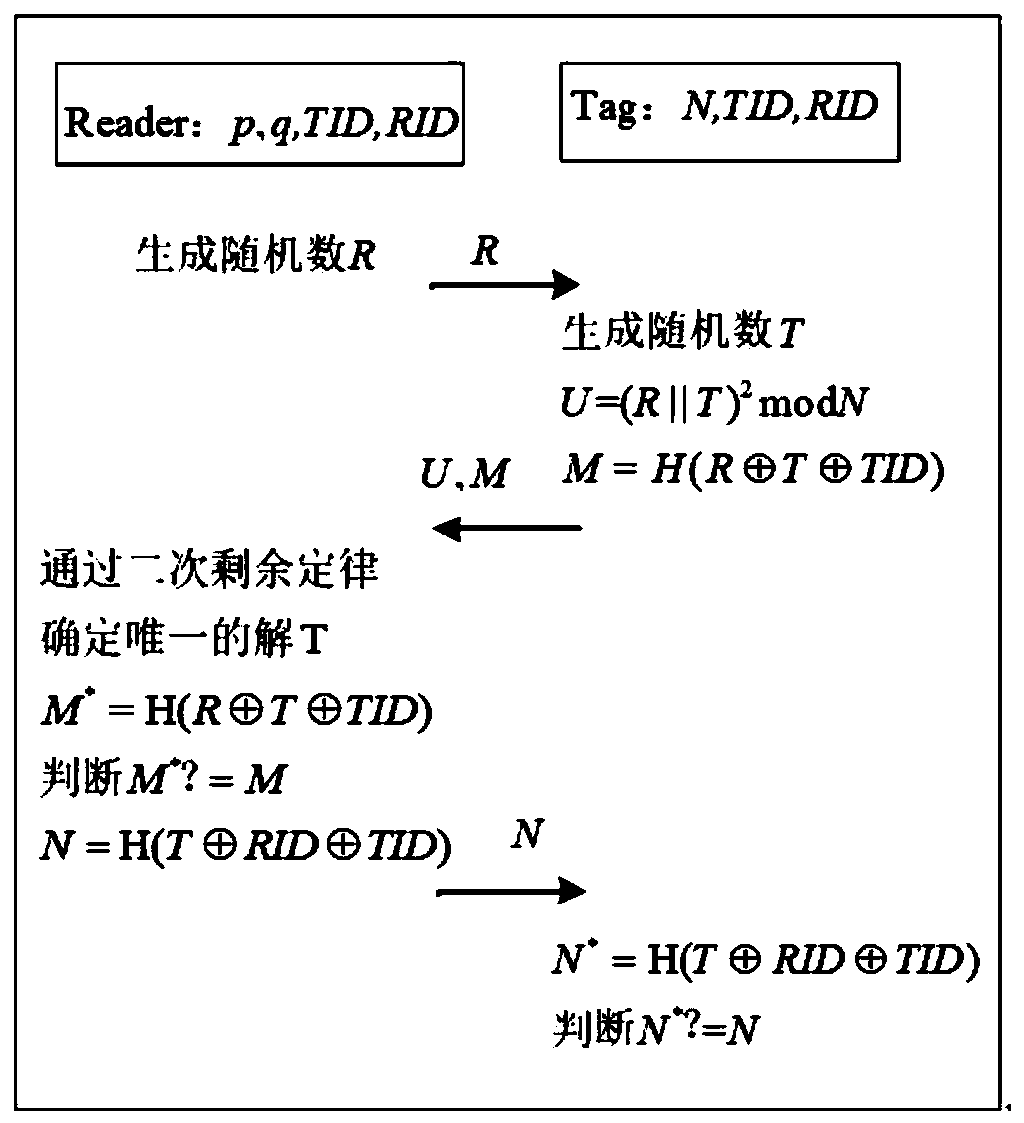
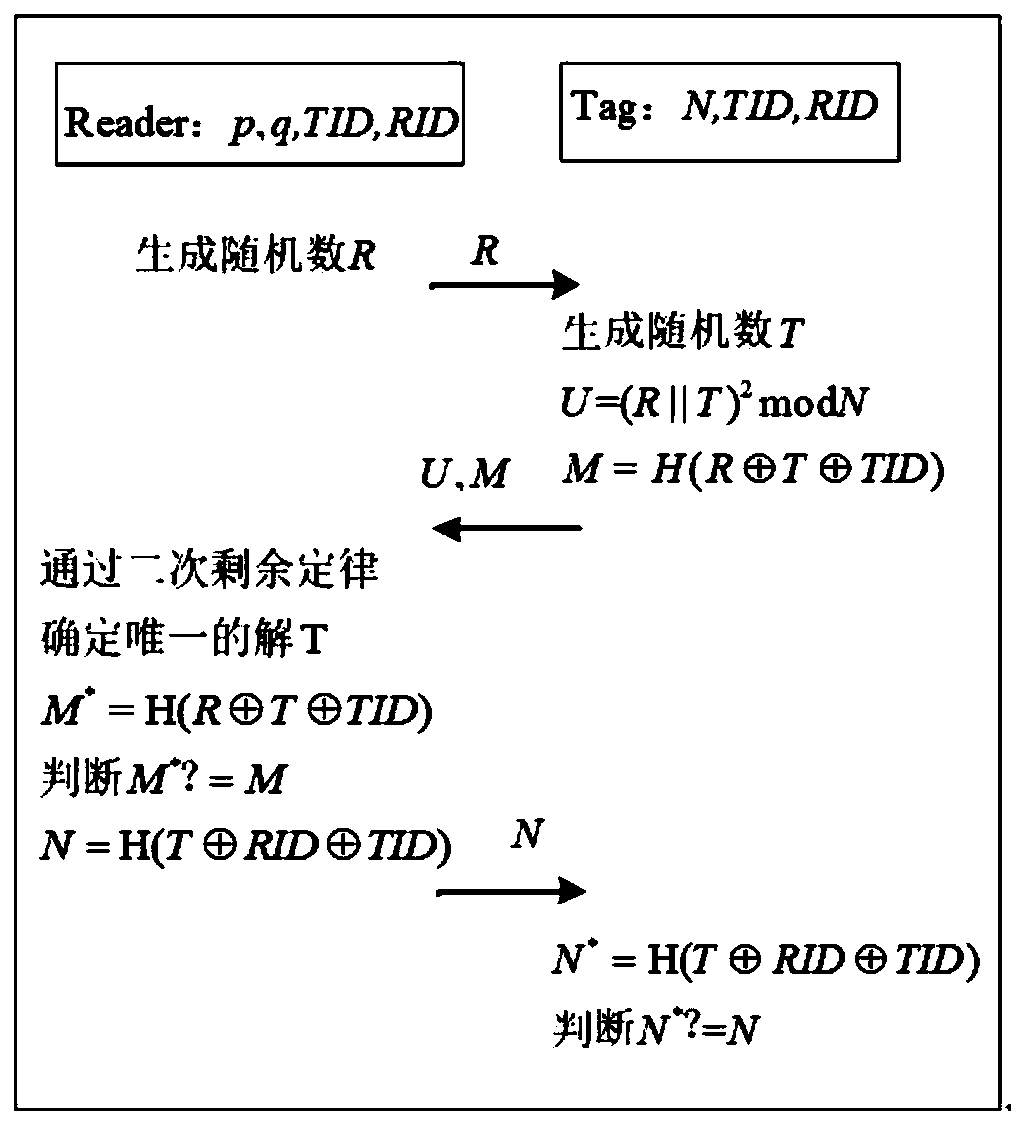
[0029]This embodiment proposes a radio frequency identification security authentication method based on quadratic remainder law mixed public key encryption and symmetric encryption mechanism, which can be applied to an electronic ticket authentication system. In the electronic ticketing system implemented by radio frequency identification, it is necessary to use the anti-counterfeiting characteristics of radio frequency identification technology itself to design electronic bills with globally unique identifiers, and the basic personnel information stored in the back-end database must be associated with the identifiers to ensure real-name registration. Attackers can easily take advantage of the uniqueness of the identifier to track the user's location information by tracking electronic bills. In addition, attackers may infer the private information in the note through eavesdropping, and use this information to further carry out malicious acts. Therefore, in order to promote the...
Embodiment 2
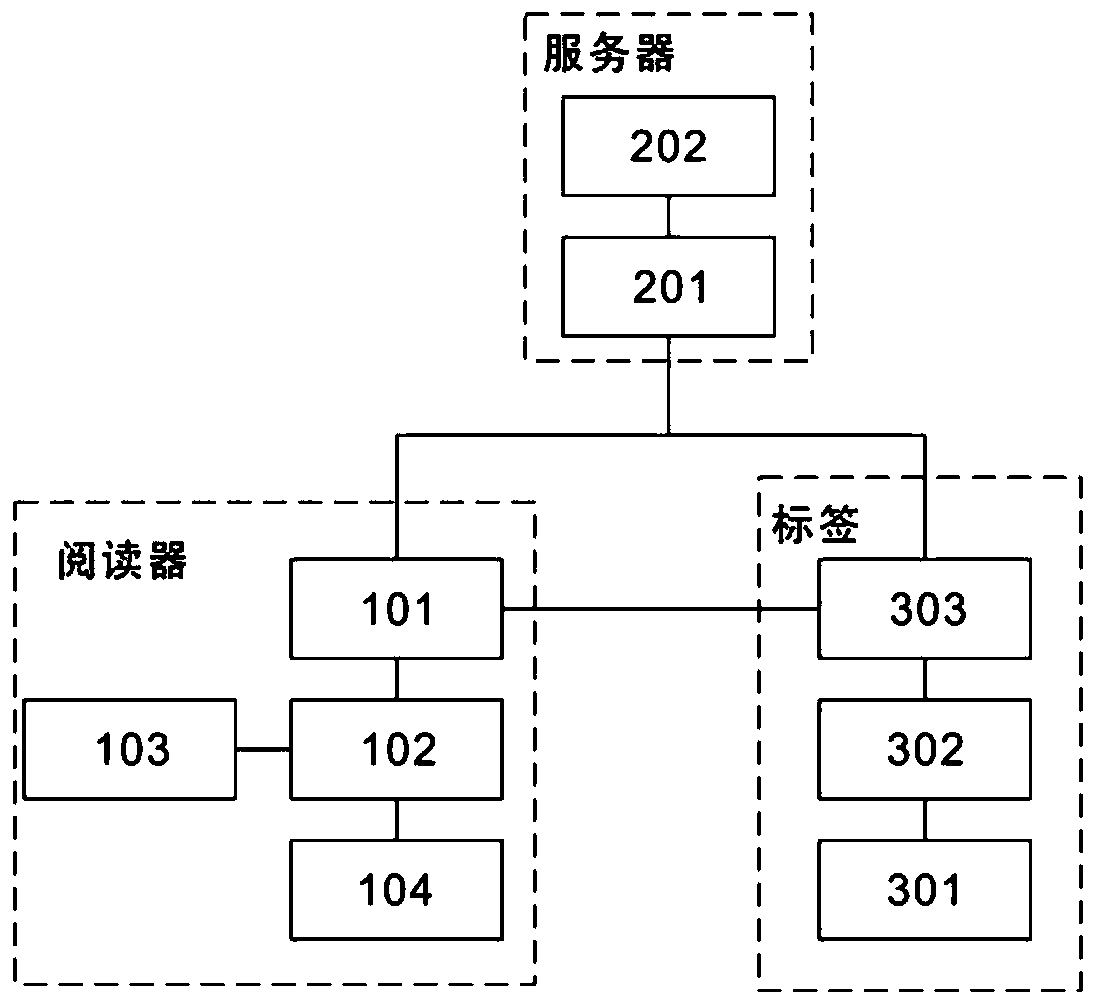
[0050] refer to figure 2 To illustrate, this example proposes a security authentication system that uses the radio frequency identification security authentication method proposed in the first embodiment. Specifically, the security authentication system includes a tag, a reader and a server, and the reader includes a reader communication module 101, a control module 102, a display module 103 and a reader storage module 104; the server includes a server communication module 201 and a database 202, and the database 202 Internally store information related to the identification; and the tag includes a tag storage module 301, an execution module 302 and a radio frequency module 303, and the radio frequency module 303 is connected to an external server for data forwarding. Specifically, the reader includes a control module 102 that mainly performs calculation operations in the protocol and system settings, etc.; realizes human-computer interaction through the display module 103 to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com