Industrial RFID safety communication method
A secure communication and RFID tag technology, applied in the field of industrial RFID secure communication, can solve problems such as immature autonomous controllability, poor security mechanism performance, impersonation attacks, etc., to reduce the waiting time of the production process, improve the efficiency of encryption and decryption, The effect of resisting differential attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0062] The present invention will be further explained below according to the accompanying drawings:
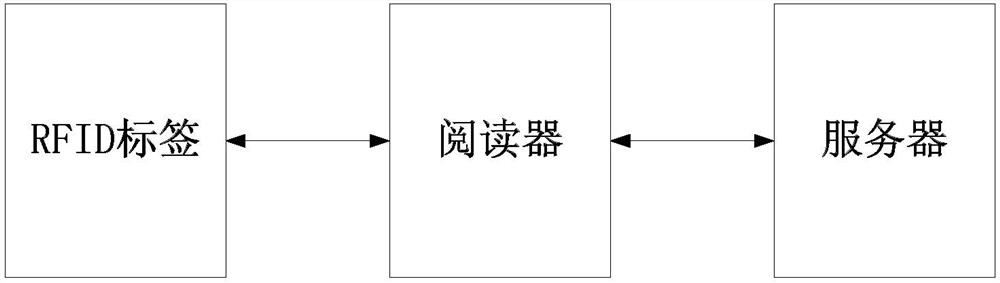
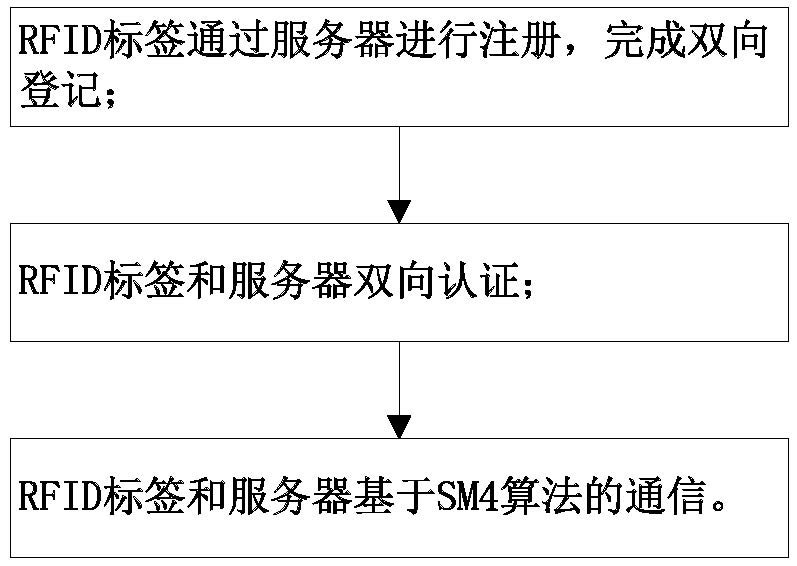
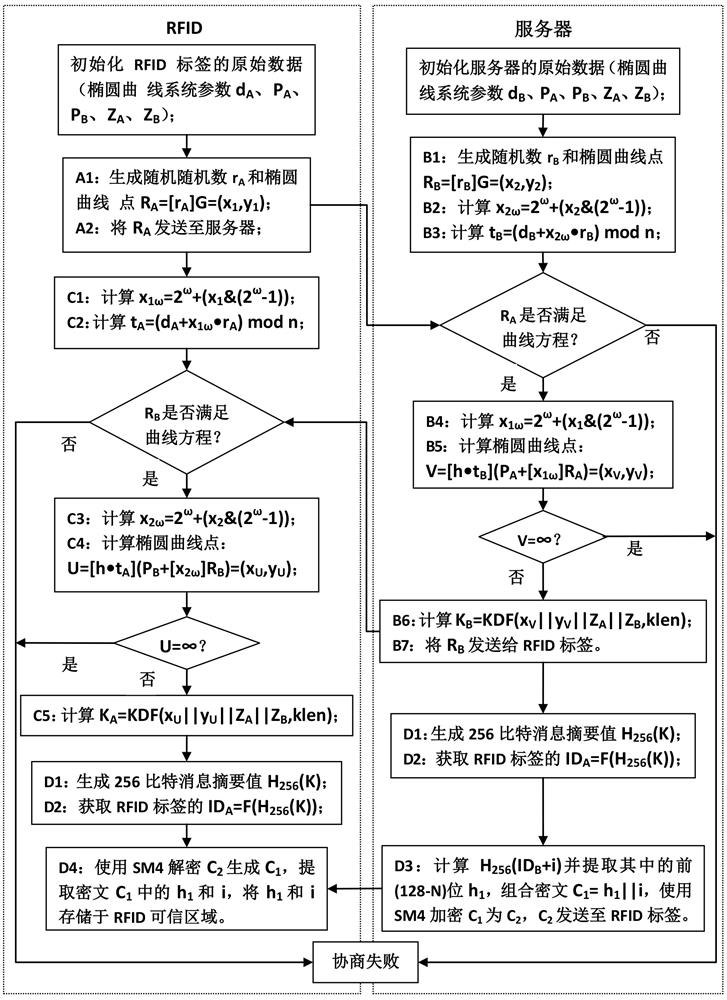
[0063] The embodiment of the present invention provides an industrial RFID security communication method, the hardware composition is as follows figure 1 As shown, it is mainly composed of RFID tags, readers and servers, and the workflow is as follows figure 2 As shown, it mainly consists of three processes: label registration, identity authentication, and communication interaction. In the tag registration stage, the RFID tag and the server use the elliptic curve-based key exchange protocol and the SM3 cryptographic hash algorithm to generate the same RFID tag unique identification code ID respectively. A , the server realizes its own unique identification code ID through the registered label serial number i B Calculate, intercept and send the hash value of the SM3 password of the RFID tag to realize the unique identification code ID of the RFID tag to the server B Storag...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com