RFID multi-tag joint authentication system and method based on Internet-of-Things application
An authentication method and technology of the Internet of Things, which is applied to the joint authentication of tags in the radio frequency identification technology. In the field of radio frequency identification of the Internet of Things, it can solve the problem that it is impossible to determine which group of items the counterfeit tags or missing tags are from, and it is impossible to determine the integrity of the tags. , product inspection difficulty, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
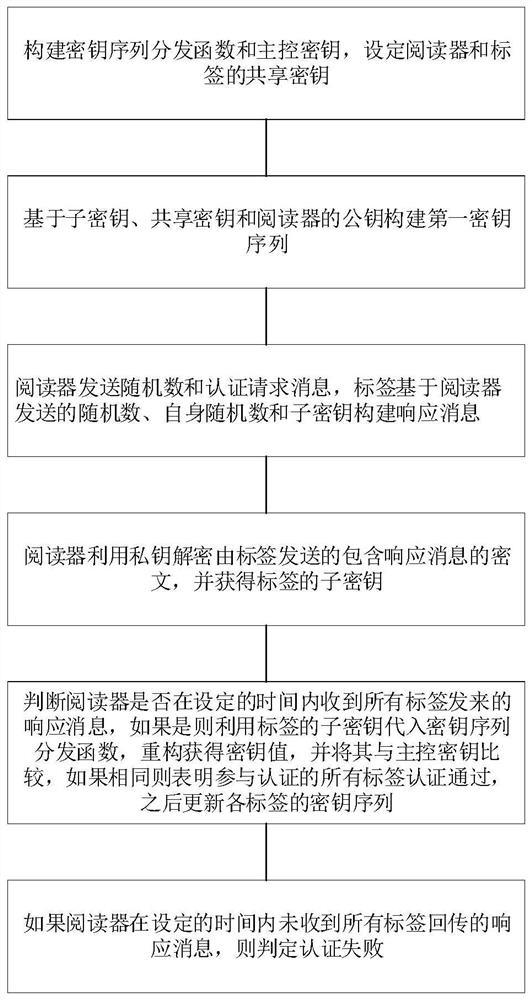
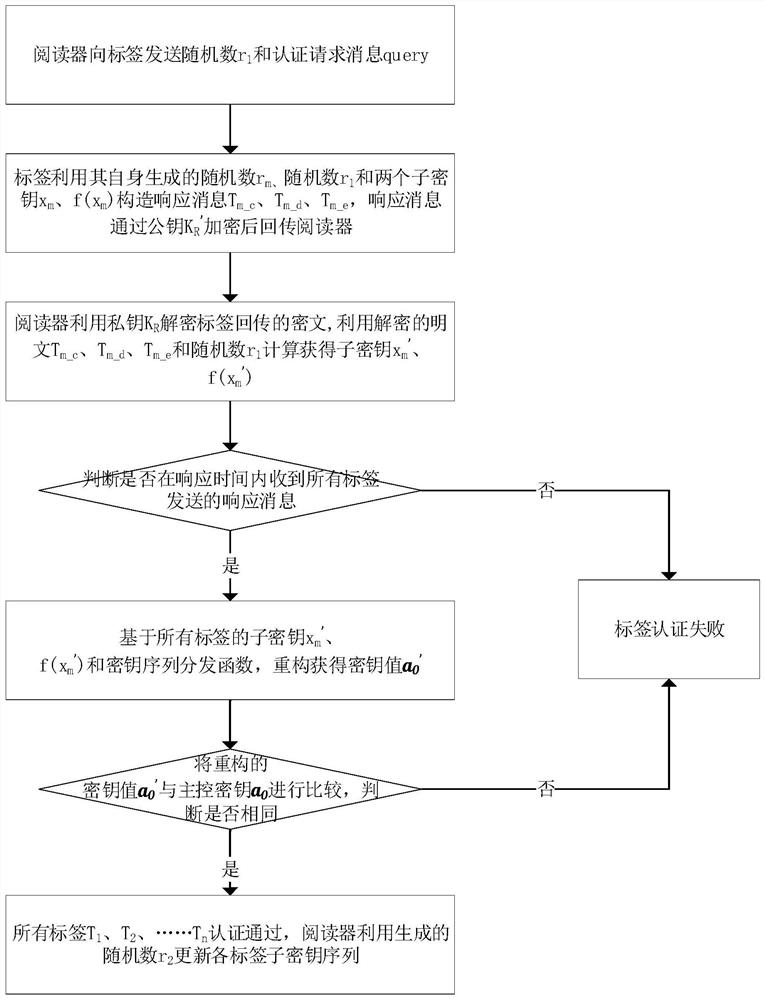
[0063] In order to make the object, technical solution and advantages of the present invention clearer, the implementation manner of the present invention will be further described in detail below in conjunction with the accompanying drawings.
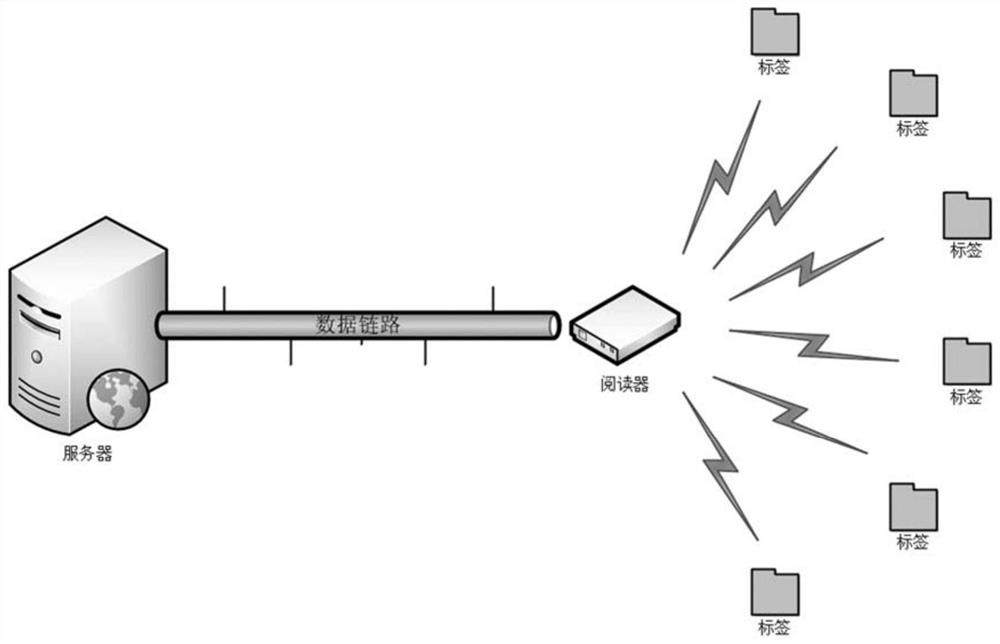
[0064] With the wide application of radio frequency identification (RFID) systems, it is found that multiple tags need to be authenticated simultaneously in some specific scenarios. For example: in the commodity supply chain, many goods need to be transmitted and sold in groups or in wholesale; in the distribution of medicines, it is necessary to put the doctor's prescription and specific medicines together, which must be required to leave the medicine warehouse at the same time; Commodities that consist of kits are packaged together and sold in bundles, each of which is unique and indispensable during use.
[0065] In the case where multiple tags bound together need to be authenticated, it is not enough to ensure the security of a sin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com