Trusted hardware equipment and using method thereof
A hardware device and reliable technology, applied in the field of information security, can solve the problems of not being able to understand the security situation, not being able to guarantee the security of the design and production process, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0102] The present invention will be described in detail below in conjunction with the accompanying drawings and examples of implementation.
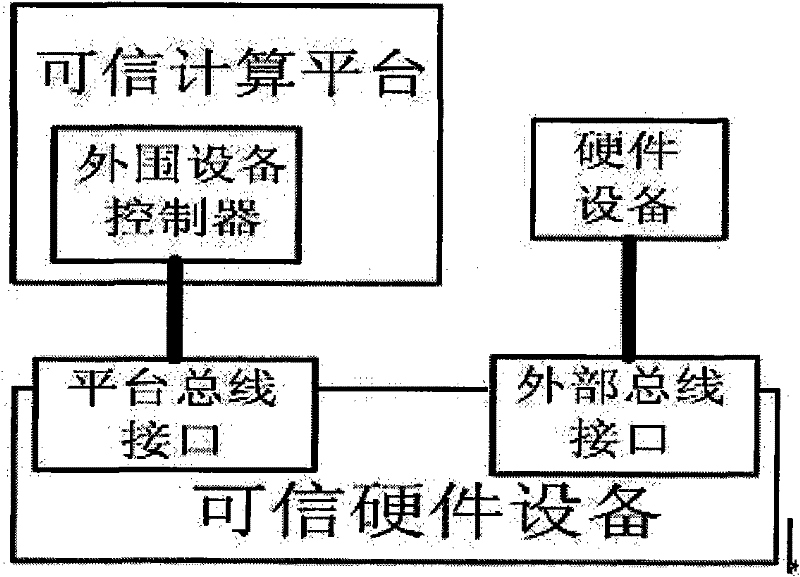
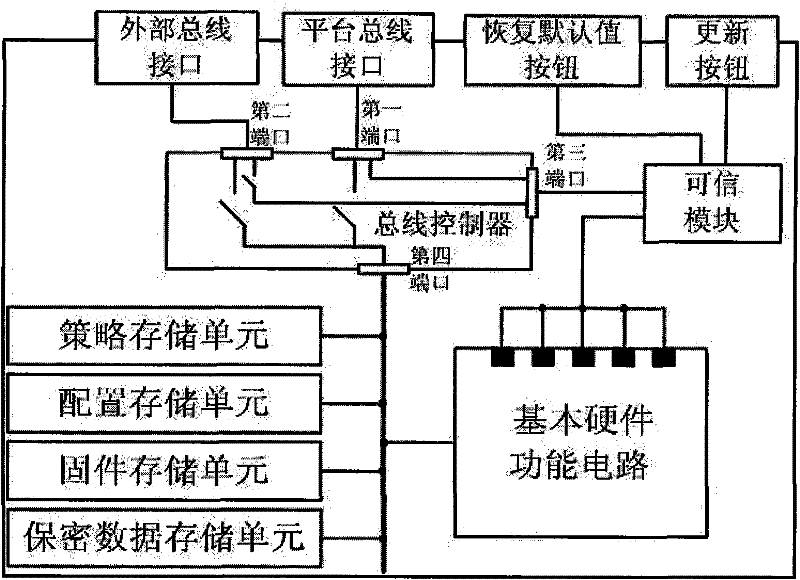
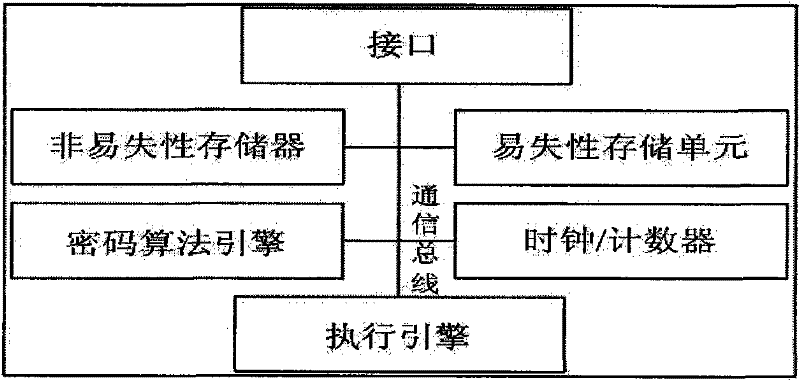
[0103] 1. Composition of trusted hardware devices
[0104] Trusted hardware devices mainly include hardware circuit part, firmware code part, control strategy part and working mode configuration part. like figure 1 As shown, the hardware circuit part includes: trusted module (TM), policy storage unit, configuration storage unit, firmware storage unit, confidential data storage unit, bus controller, basic hardware function circuit, circuit working status checkpoint, external bus interface , platform bus interface, restore default button and update button.
[0105] 1. Implementation method of the hardware circuit part:
[0106] 1) The hardware structure implementation method of the trusted module is as follows:
[0107] Execution engine: choose a 32-bit RISC processor (ARM9 processor).
[0108] Internal bus: use 32-bit AMBA bus.
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com