Method for controlling access to shared component of leveled partition
A technology of access control and sharing group, applied in the field of security authorization and management of computer resources, can solve problems such as errors, tedious authorization changes, heavy workload of system administrators, etc., and achieve the effect of integrity and unity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
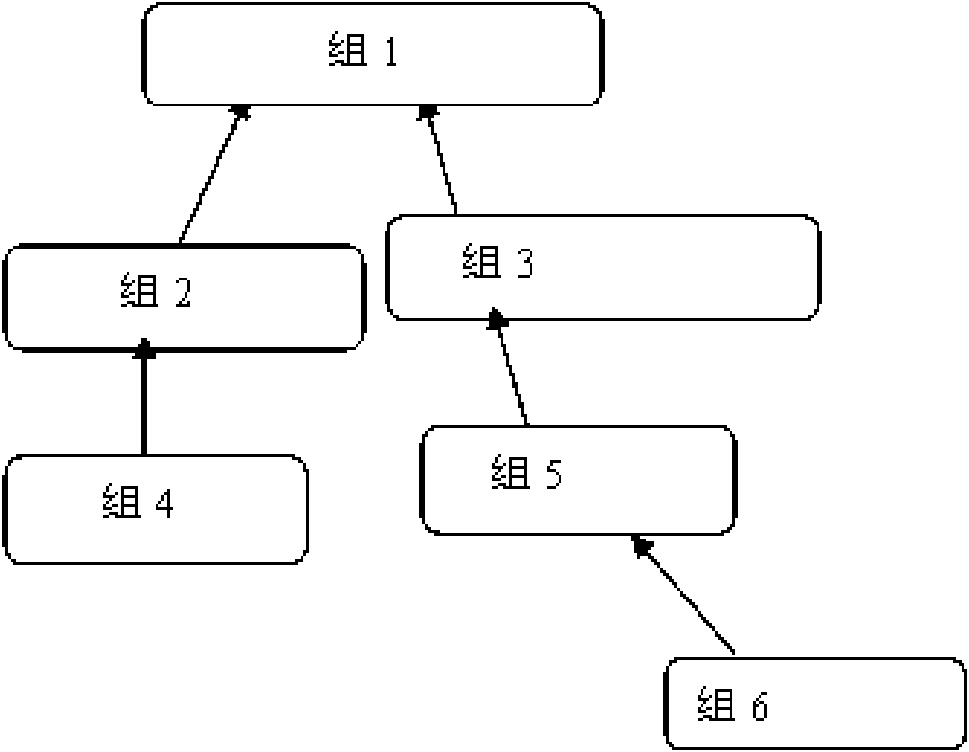
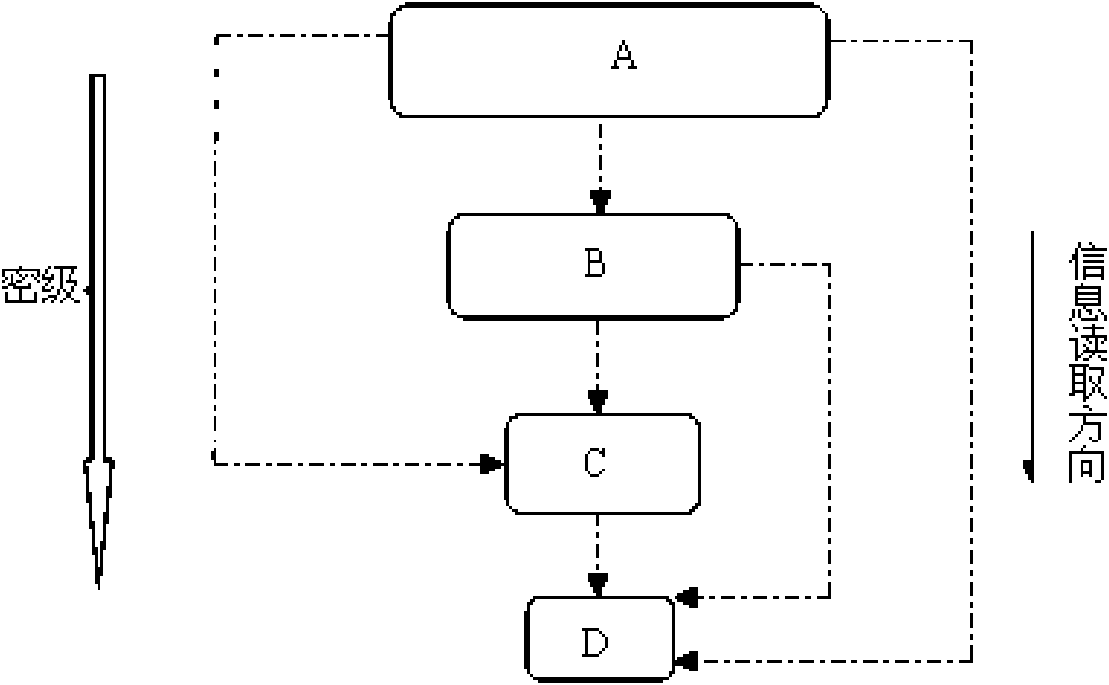
[0032] Now in conjunction with accompanying drawing and embodiment the present invention is described in further detail, embodiment refers to Figures 1 to 5 .
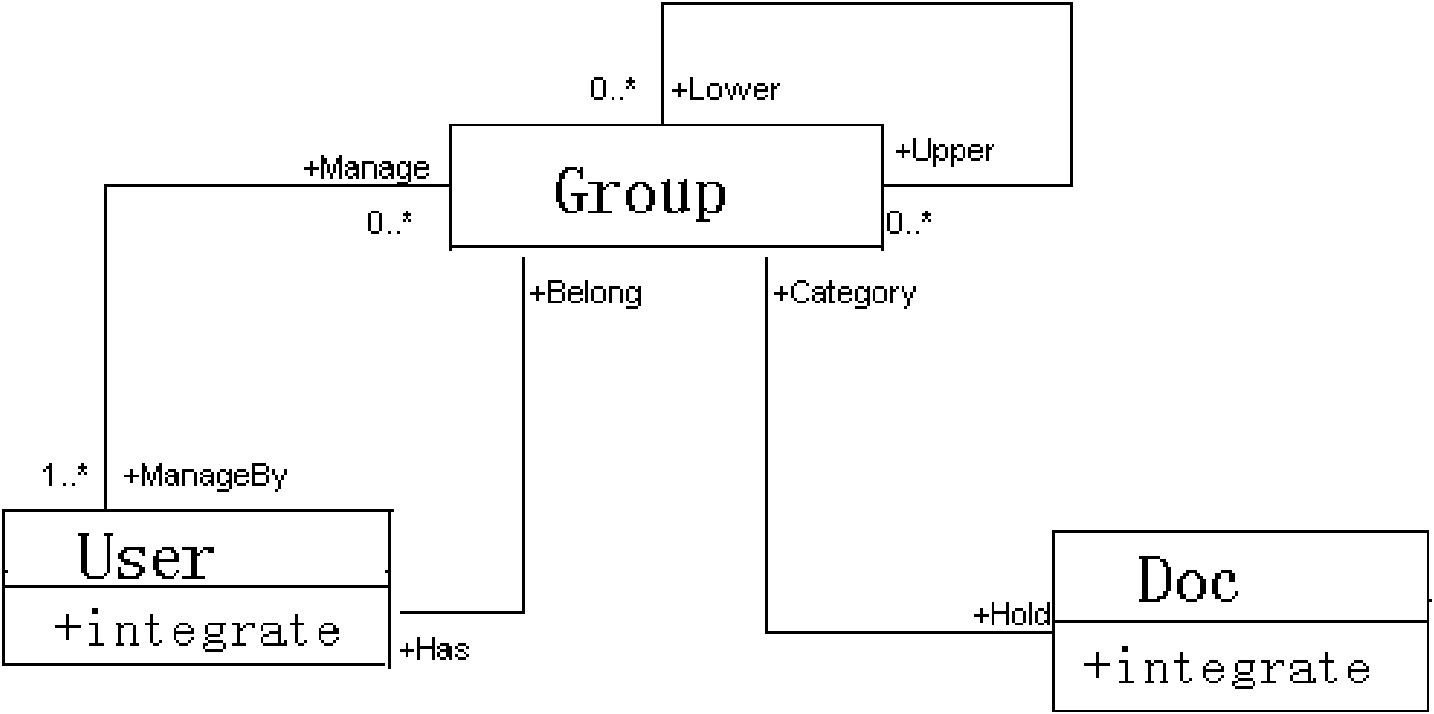
[0033] 1. The system is defined as the sharing group, user, document, and the upper and lower layer relationship network formed between the sharing group ( figure 1 ).
[0034] Systems = {Groups, Users, Documents}.
[0035] 2. A user is a subject that can independently access protected data or resources. It can be a person or a program or process. Here, it is simplified as a person. Users represent a user set, and U represents a user, namely:
[0036] Users={U 1 , U 2 ,...,U n}.
[0037] 3. Documents are protected data or resources, which are simplified as documents here. Documents is used to represent a document set, and D represents a document, namely:
[0038] Documents={D 1 ,D 2 ,...,D n}.
[0039] 4. For security reasons, according to the confidentiality requirements of departments and departments and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com