Chaotic video encryption method based on sliding encryption window
An encryption method and video technology, which can be applied to secure communication through chaotic signals, modification of digital video signals, digital transmission systems, etc., can solve the problems of large encryption calculation overhead, and achieve high encryption efficiency, security, and fast computing speed. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
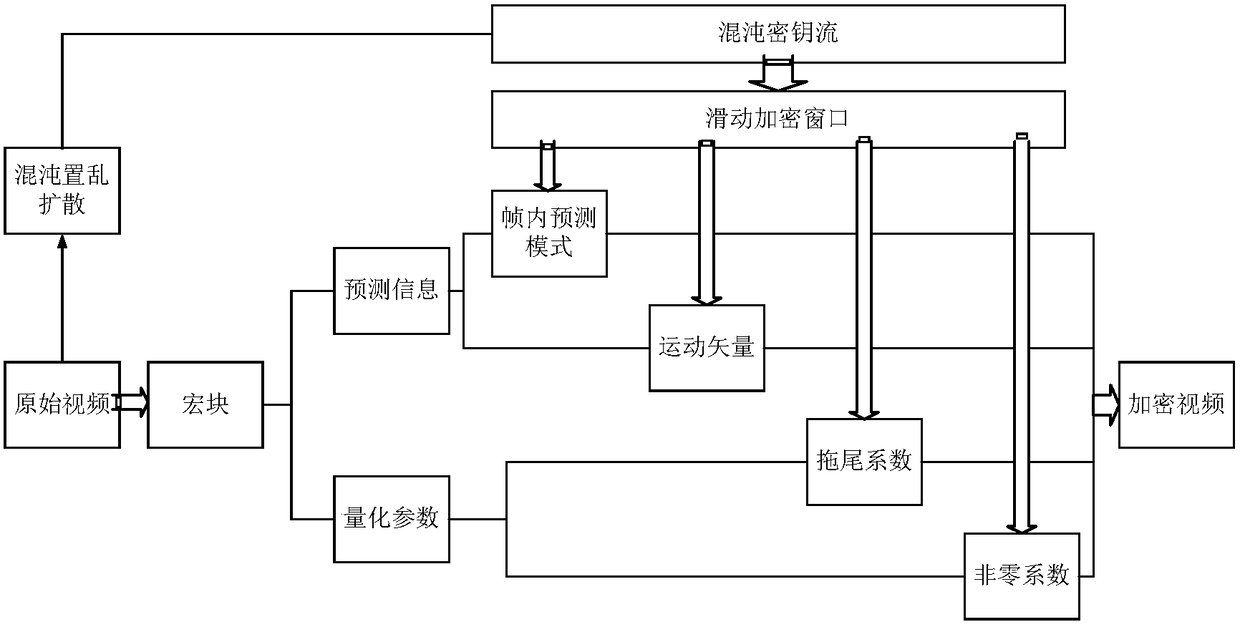
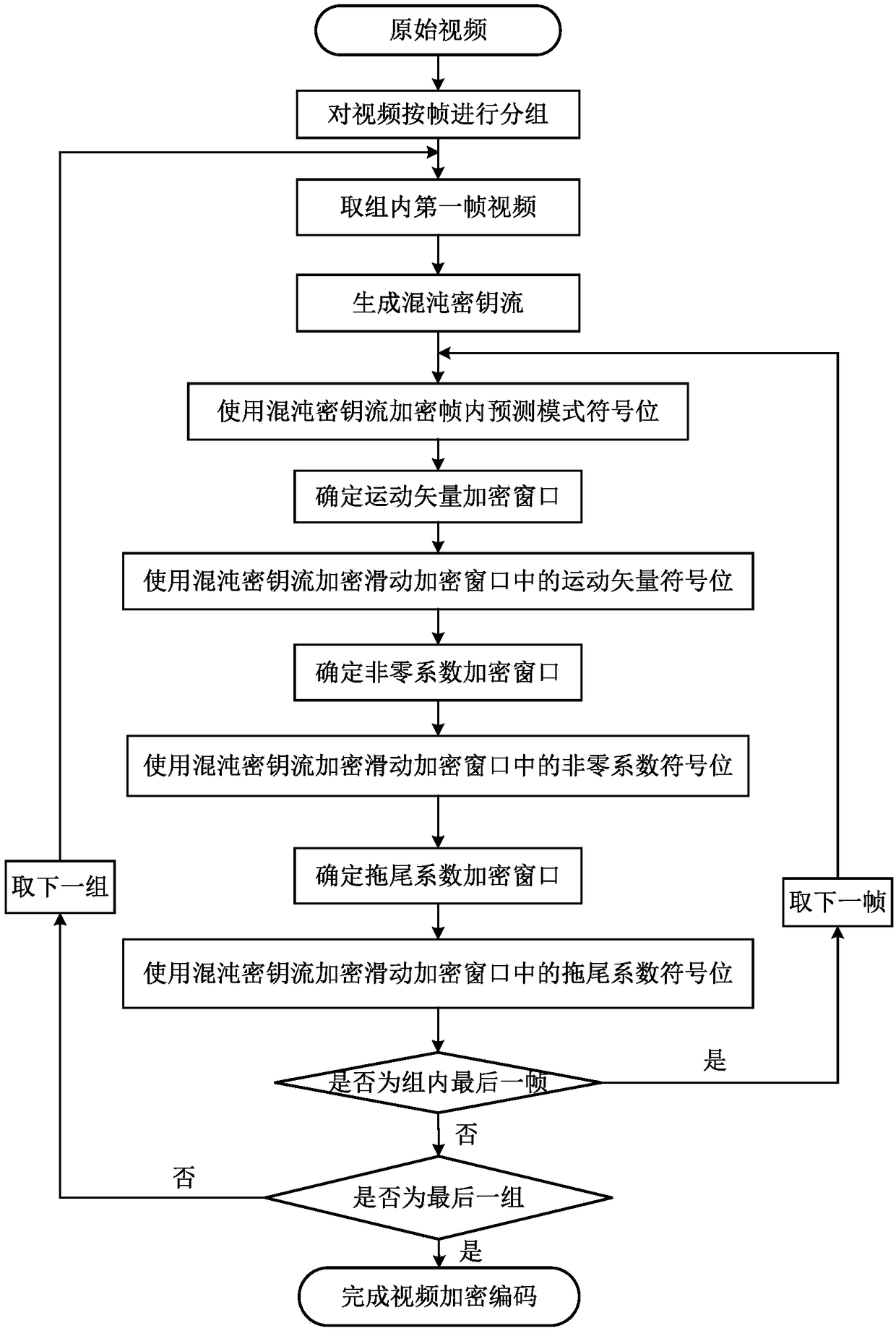
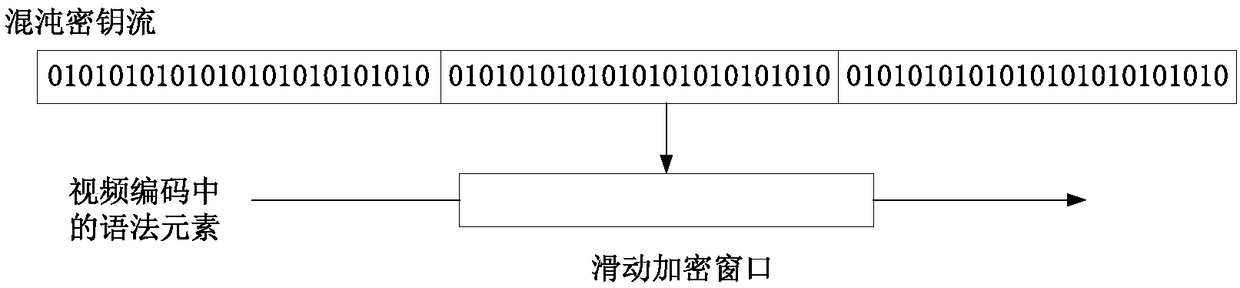
[0034] Specific implementation mode 1. Combination Figure 1 to Figure 7 Describe this embodiment, the chaotic video encryption method based on the sliding encryption window, according to the H.264 video coding standard, the encryption block diagram of the encryption method in this embodiment is as follows figure 1 As shown, the encryption flow chart is as follows figure 2 shown.
[0035] Select bus video data with a size of 352 × 288. This embodiment operates under the JM8.6 basic mode of H.264. The video length is 30 frames, the entropy coding mode is CAVLC, and the I frame interval is 8, wherein the 20th frame is extracted. Frame raw image such as Figure 4 , the ciphertext image of the 20th frame after encryption is as follows Figure 5 shown.
[0036] In this embodiment, the user key is composed of four parts: 1. the control parameters of the composite chaotic map, 2. the initial value of the composite chaotic map, the control parameters of the three-cell quantum cel...
specific Embodiment approach 2
[0078] Specific embodiment two, combine Figure 1 to Figure 7 , based on the chaotic video encryption method, according to the H.264 video coding standard, the encryption block diagram of the encryption method in this embodiment is as follows figure 1 As shown, the encryption process is shown in the flow figure 2 . Select the "calendar" video data with a size of 176×144. This embodiment operates under the JM8.6 basic mode of H.264. The video length is 100 frames, the entropy coding mode is CAVLC, and the I frame interval is 8. 90 frames of original images such as Figure 6 , the ciphertext image of the 90th frame after encryption is as follows Figure 7 shown.
[0079] In this embodiment, the user key is composed of four parts: ① the control parameters of the compound chaotic map, ② the initial value of the compound chaotic map, ③ the control parameters of the three-cell quantum cellular neural network, and ④ the initial value of the three-cell quantum cellular neural net...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com