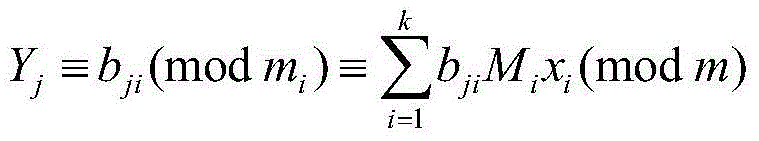Image encryption compression method based on discrete quantum walk and Chinese remainder theorem
A Chinese remainder theorem and encryption compression technology, applied in the field of information security, can solve problems such as inefficiency and insecurity, and achieve the effects of low ciphertext correlation, high security, and large key space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] The present invention will be described in further detail below in conjunction with the accompanying drawings and specific embodiments.
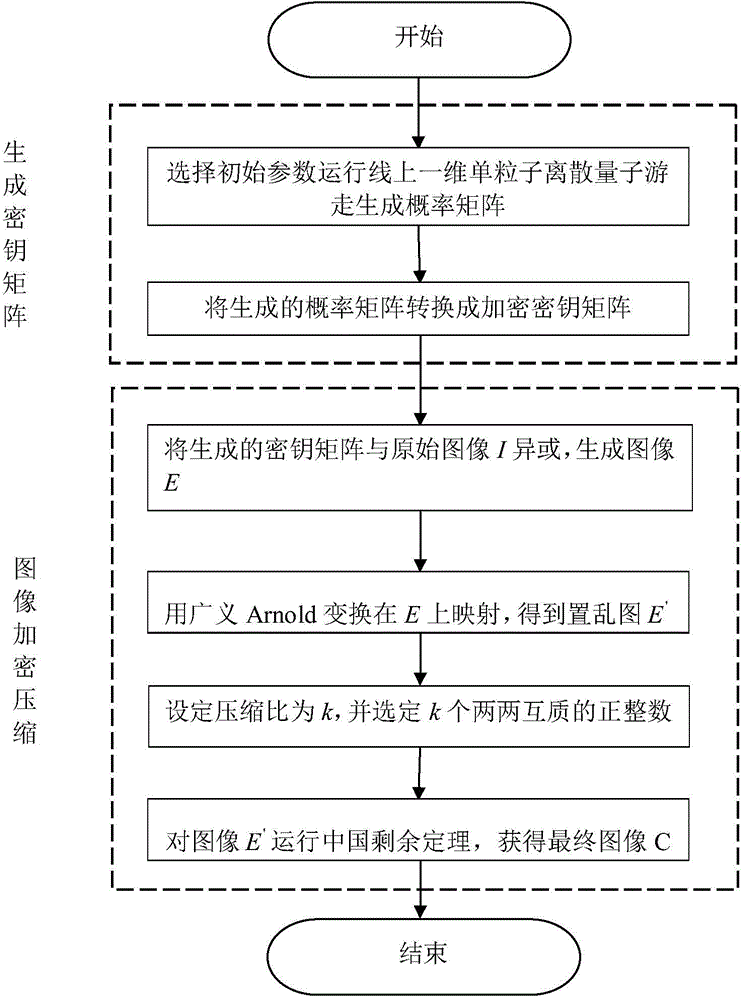
[0019] An image encryption and compression method based on discrete quantum walk and Chinese remainder theorem, the flow chart is as follows figure 1 shown, including the following steps:
[0020] Step 1, generate a key matrix, the specific method is as follows:
[0021] (1) Select the key ((α,β), r), and run the single-particle one-dimensional discrete QRW on the line to generate a probability distribution. Here, α, β represent the coefficients of the initial coin state and satisfy the normalization condition |α| 2 +|β| 2 =1. r is the step size of QRW.
[0022] (2) Multiply all the values in the probability distribution by 108 and modulo 256 to form a random sequence S={S 1, S 2, ..., S M×N}, where M and N are the height and width of the plaintext image I, respectively.
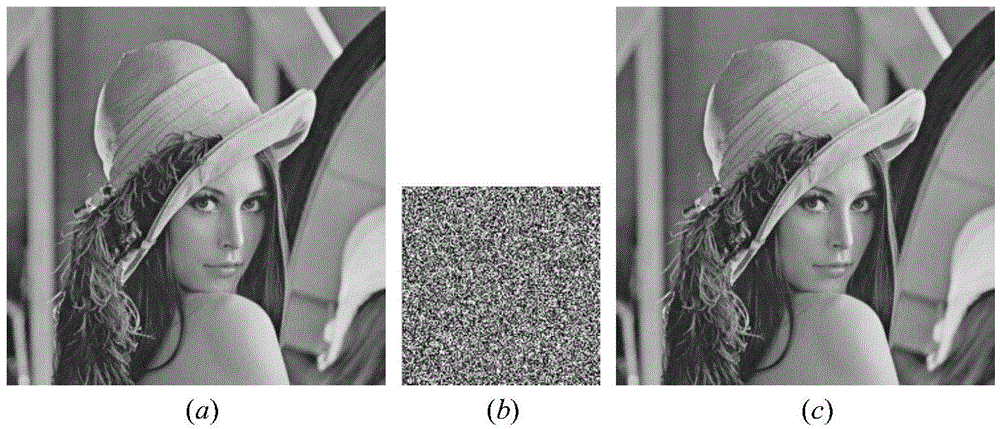
[0023] Step 2, image encryption and compression pro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com