Image encryption algorithm based on memoristor hyper-chaotic system, cellular automaton and DNA calculation
A technology of cellular automaton and encryption algorithm, which is applied in the field of image encryption algorithm based on memristive hyperchaotic system, cellular automata and DNA computing, which can solve the problem of small key space, lack of connection between algorithms and plaintext, and DNA encryption implementation Difficulty and other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
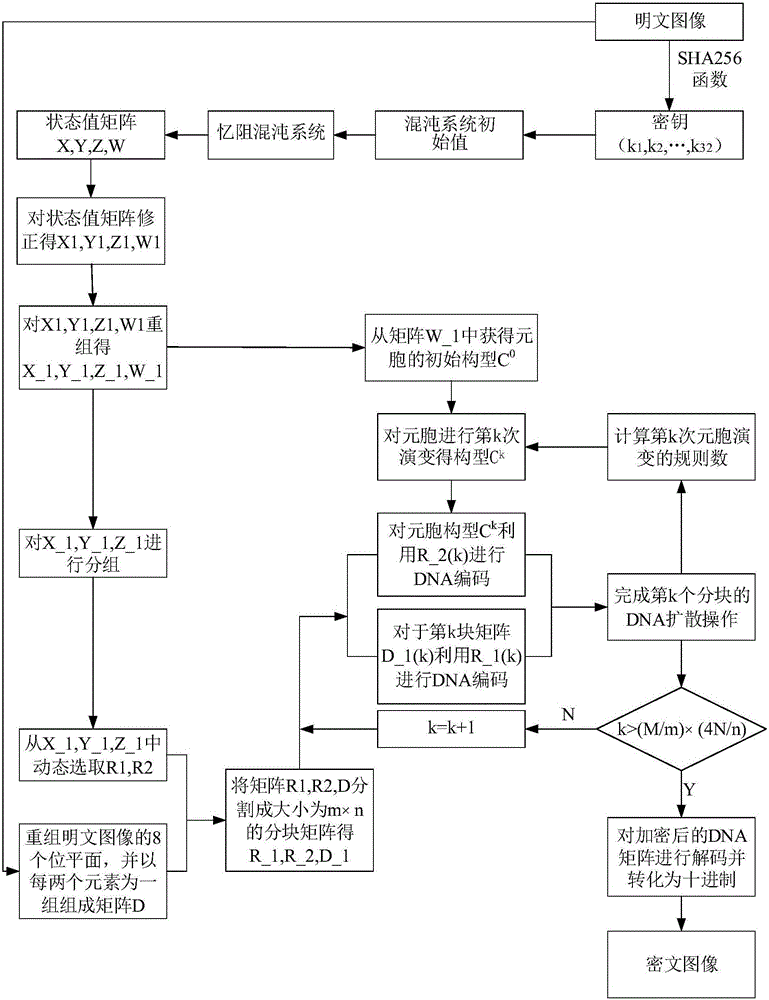
[0078] Embodiment one, see figure 1 As shown, an image encryption algorithm based on memristive hyperchaotic system, cellular automata and DNA computing includes the following steps:
[0079] Step 1. Use the SHA256 function to calculate the plaintext image P with a size of M×N, obtain a set of 256-bit hash values and use it as the image key Key, and convert the 256-bit image key Key into 32 decimals number k 1 , k 2 ,...,k 32 , calculate the initial state value of the four-dimensional memristive hyperchaotic system based on Chua circuit;
[0080] Step 2. Bring the obtained initial state value into the memristive hyperchaotic system for iteration, and obtain 4 state value matrices X=[x 1,1 ,x 1,2 ,...,x 1,4MN ], Y=[y 1,1 ,y 1,2 ,...,y 1,4MN ], Z=[z 1,1 ,z 1,2 ,...,z 1,4MN ], W=[w 1,1 ,w 1,2 ,...,w 1,4MN ], modify the state value matrix X, Y, Z to get the matrix X1=[x 1 ' ,1 ,x 1 ' ,2 ,...,x 1 ' ,4MN ], Y1=[y 1 ' ,1 ,y 1 ' ,2 ,...,y 1 ' ,4MN ], Z1=[z...
Embodiment 2
[0091] Embodiment two, see figure 1 As shown, an image encryption algorithm based on memristive hyperchaotic system, cellular automata and DNA computing includes the following steps:
[0092] Step 1. Use the SHA256 function to calculate the plaintext image P with a size of M×N, obtain a set of 256-bit hash values and use it as the image key Key, and convert the 256-bit image key Key into 32 decimals number k 1 , k 2 ,...,k 32 , calculate the initial state value of the four-dimensional memristive hyperchaotic system based on the Chua circuit, the specific expression of the four-dimensional memristive hyperchaotic system based on the Chua circuit is:
[0093] ,
[0094] where h(x)=m 1 x+0.5(m 0 -m 1 )×(x+1|-|x-1), x, y, z, w represent the state variables of the chaotic system, a, b, c, d, e, m 0 、m 1 is the control parameter of the chaotic system, and when a=30, b=36, d=2.5, e=3.5, m 0 =-0.5, m 1 =-0.1 and c∈[0.073,0.162], the system is in a super chaotic state;...
Embodiment 3
[0130] Embodiment three, see Figure 2 (a) ~ 4 (b) As shown, in this embodiment, the programming software used is MatlabR2014a, and the Lena grayscale image with a size of 256×256 is selected as the experimental object. The specific encryption process is as follows:
[0131] Step 1. Input the Lena grayscale image with the original size of 256×256, use P=imread('lena.bmp') to read the image information, use the SHA256 function to calculate the plaintext image P, and obtain a set of 256-bit hashes Value and use it as the image key Key, and then convert the 256-bit Key to 32 decimal numbers k 1 , k 2 ,...,k 32 , the specific steps used to calculate the initial state value of the four-dimensional memristive hyperchaotic system are as follows:
[0132]1.1) The four-dimensional memristive hyperchaotic system based on Chua circuit is used to generate the pseudo-random sequence required by the encryption algorithm, and its expression is as follows:
[0133] ,
[0134] h(x)=m 1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com