Encrypted Huffman encoding method and decoding method
An encoding method and an encoding technology, which are applied in the fields of information security and digital content protection, can solve problems such as the impact of encoding length, MHT insecurity, and inability to resist synchronization attacks, and achieve the effects of increasing key space, improving performance, and high efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0062] The method of the present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
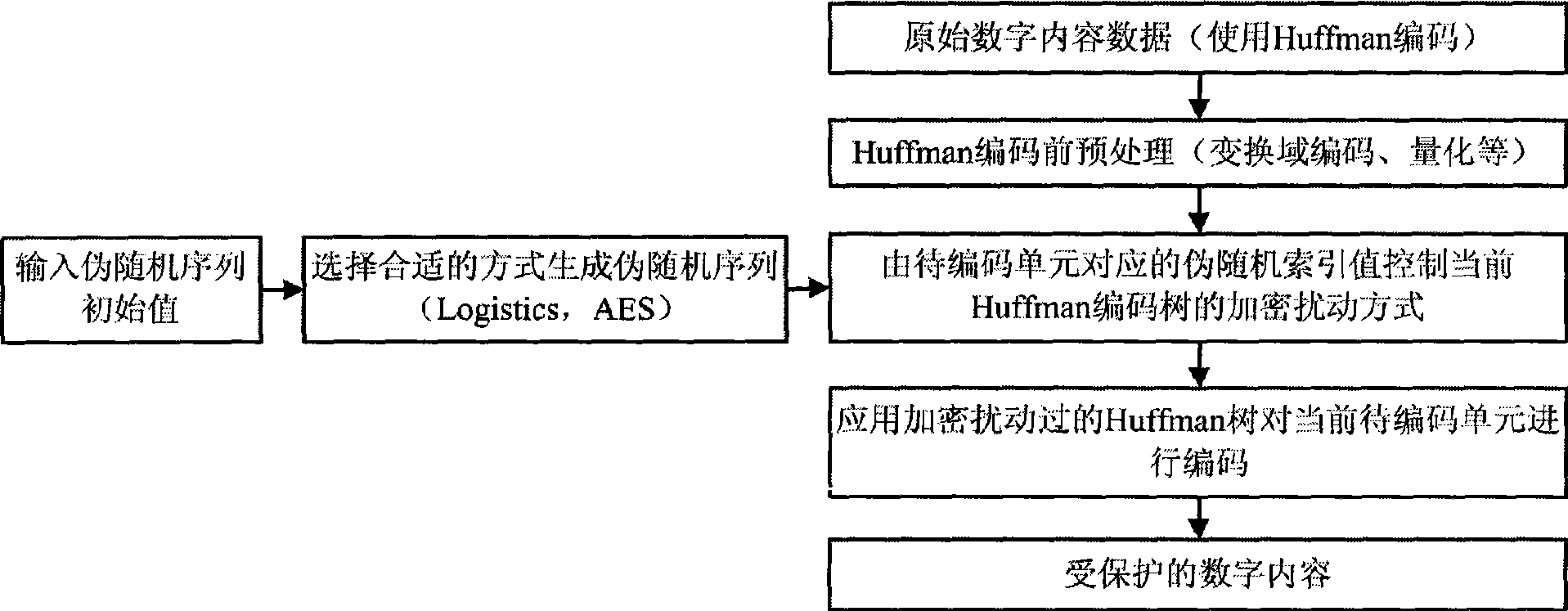
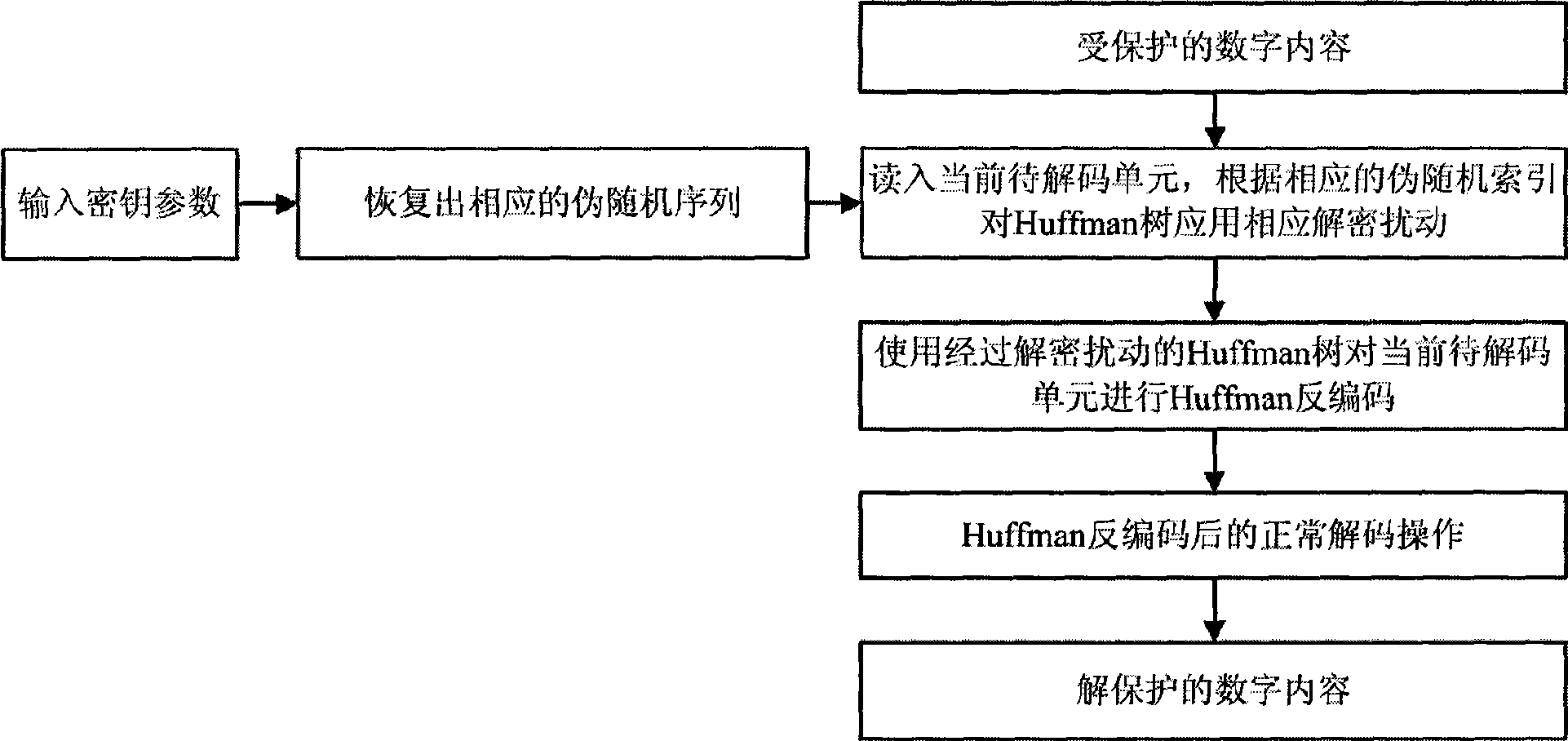
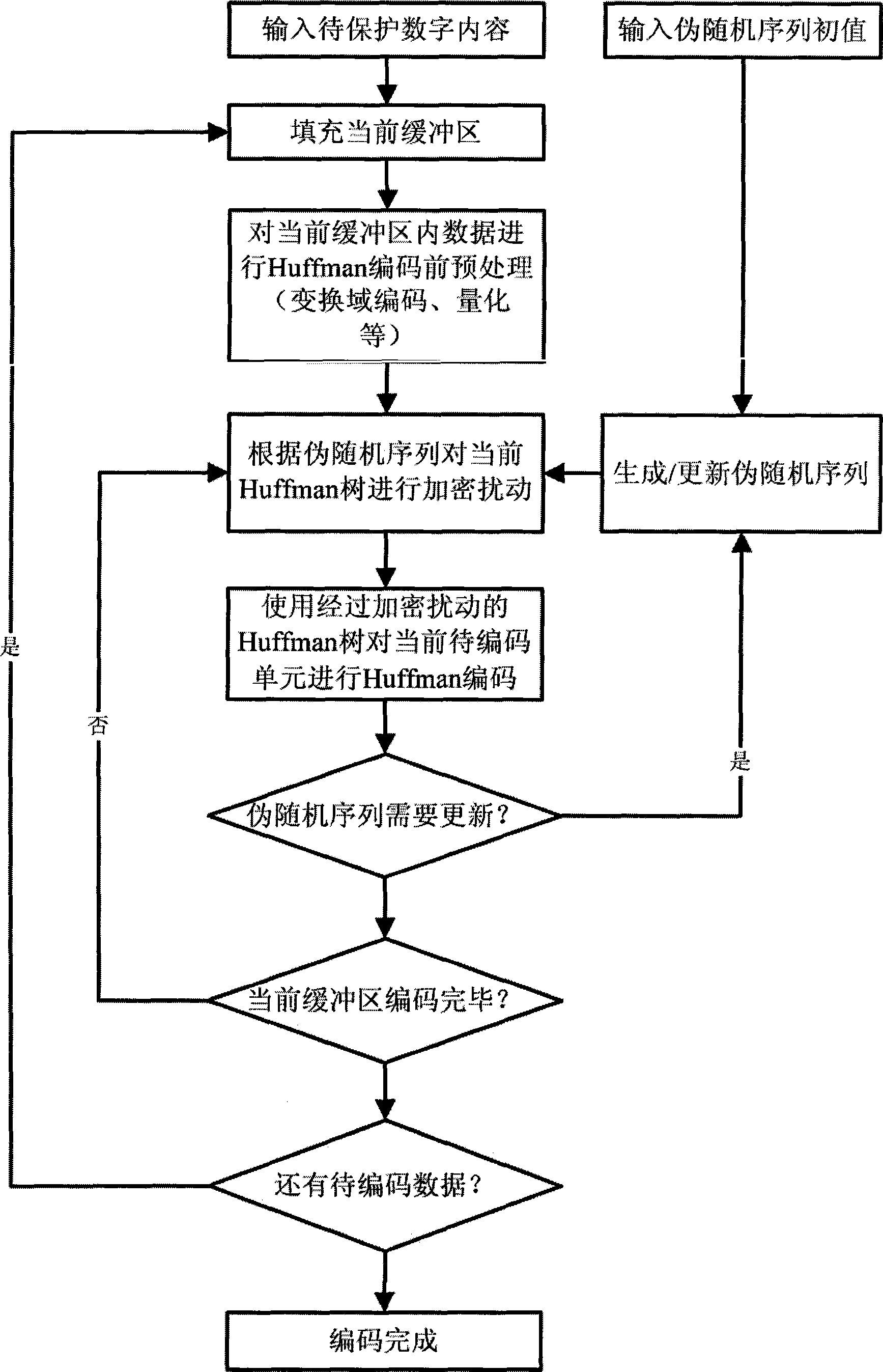
[0063] The following combination Figure 5-9 , by comparing with the general Huffman encoding process, describe a complete pseudo-random Huffman encoding encryption process.
[0064] Figure 5 Shown is a typical Huffman tree, for the convenience of explanation, it is assumed that the coding unit sequence to be encoded is M=[5, 10, 2, 6, 9], and the general Huffman encoding process is described in detail as follows:
[0065] Find the codeword corresponding to each coding unit according to the Huffman coding tree: the codeword corresponding to 5 is 000111, 10 corresponds to 00000001, 2 corresponds to 100, 6 corresponds to 000110, and 9 corresponds to 0000001, then the encoded bit stream is: 000111000000011000001100000001.
[0066] The scheme adopted in this embodiment performs pseudo-random encrypted perturbation on the Huffman co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com