Password encryption method and system, and cryptographic check method and system
An encryption method and encryption system technology, applied in the transmission system, digital transmission system, user identity/authority verification, etc., can solve the same user information leakage, user information leakage, user password plaintext storage password file access control measures are not strict enough, etc. problem, to achieve the effect of ensuring uniqueness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
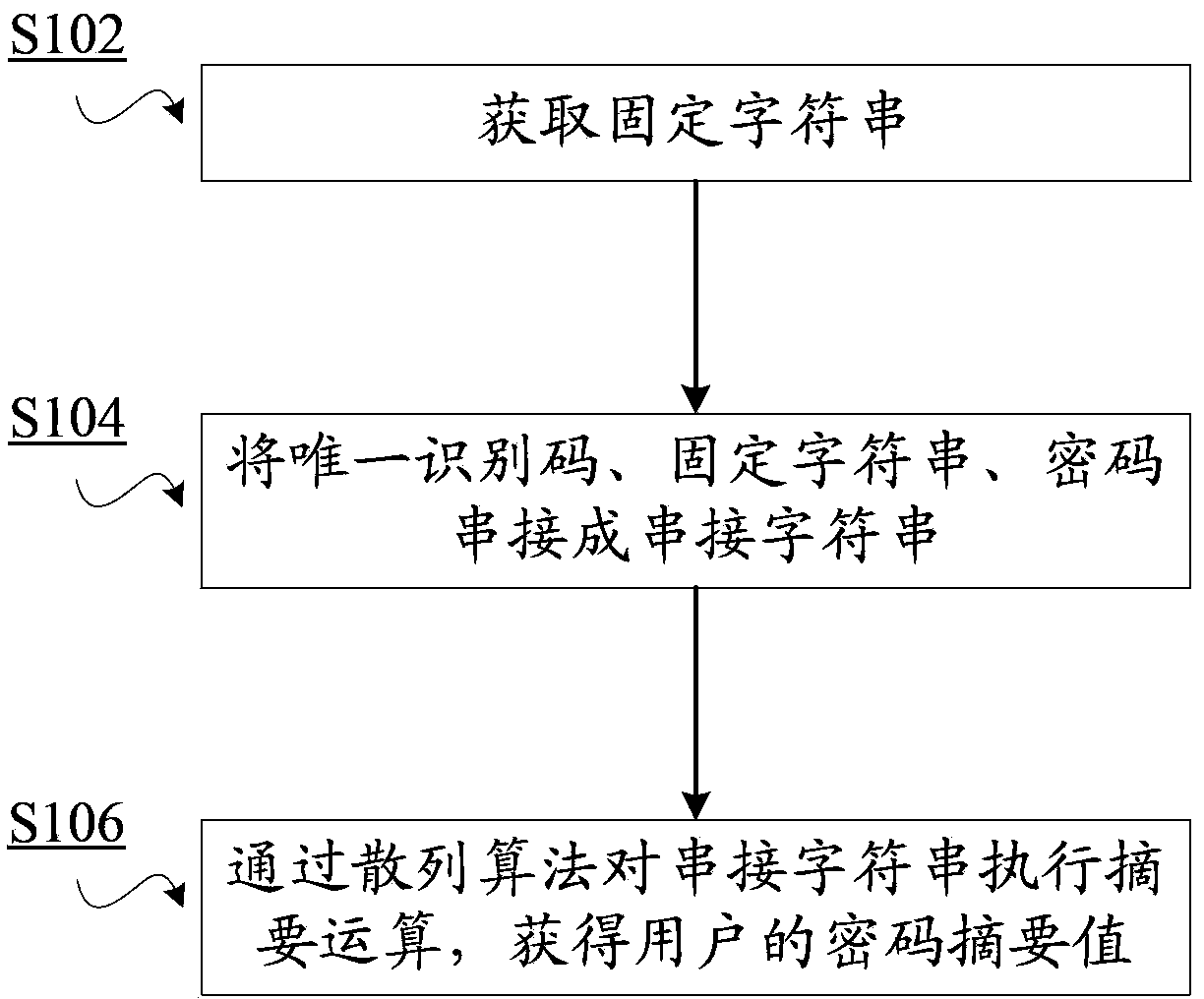
[0051] Combine below figure 1 The password encryption scheme according to the embodiment of the present invention will be described.
[0052] The password encryption method according to the present invention is used to encrypt passwords of users, wherein each user has a unique identification code. This unique identifier can be a username or a user ID (a unique numeric code assigned to each user by the website). The user password that needs to be encrypted corresponds to each user, that is, corresponds to the user's unique identification code.
[0053] In step S102, a fixed character string is obtained. The fixed character string may be a fixed fixed-length character string, which is called a website secret factor or Salt. The character string is preferably stored separately from the user password database, and only authorized users / programs can be read strictly. Optionally, unlike the above-mentioned situation where only the same salt value is used, a salt value correspond...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com