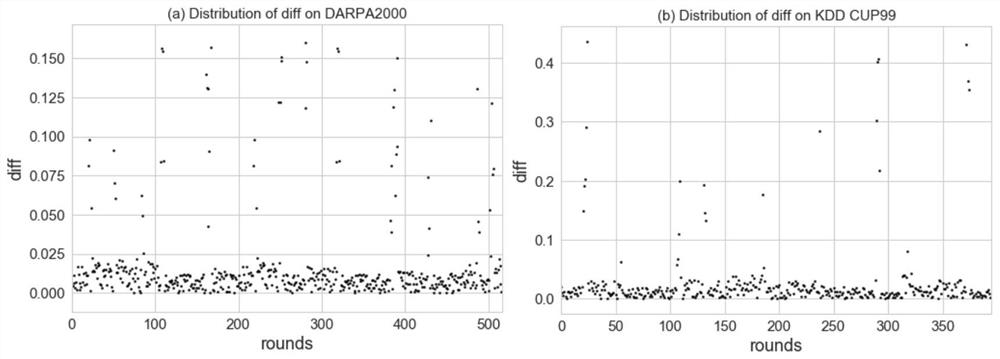
Patents
Literature
127 results about "Defence system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Specific Defence System. This defence system is called the specific defence system because the system attacks specific invaders. This can happen by the production of antibodies or by white blood cells engulfing a particular pathogen.
Ballistic target defense system and methods
InactiveUS7137588B2Convenient distanceKeep for a long timeDefence devicesDirection controllersTarget engagementEngineering
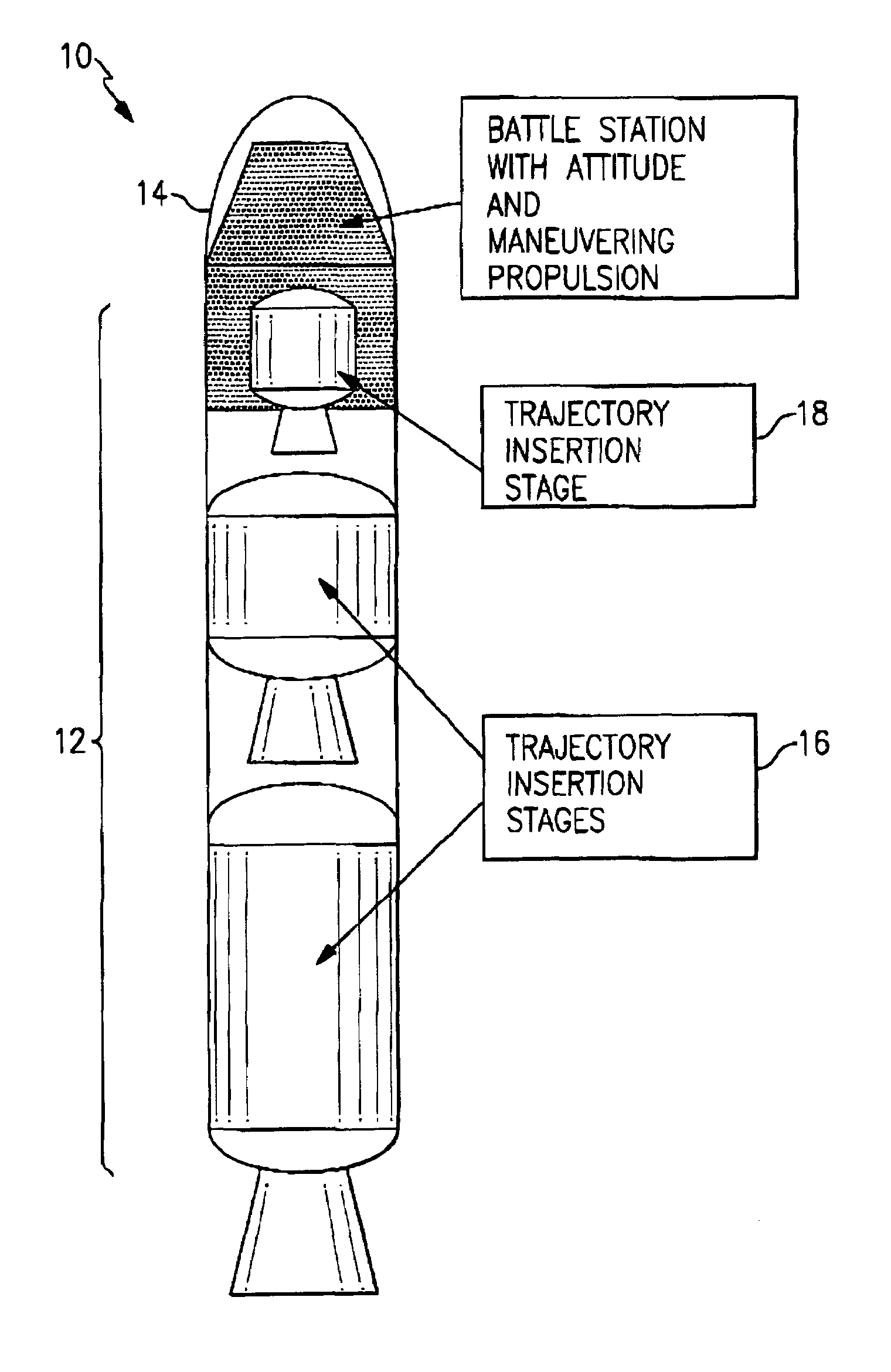
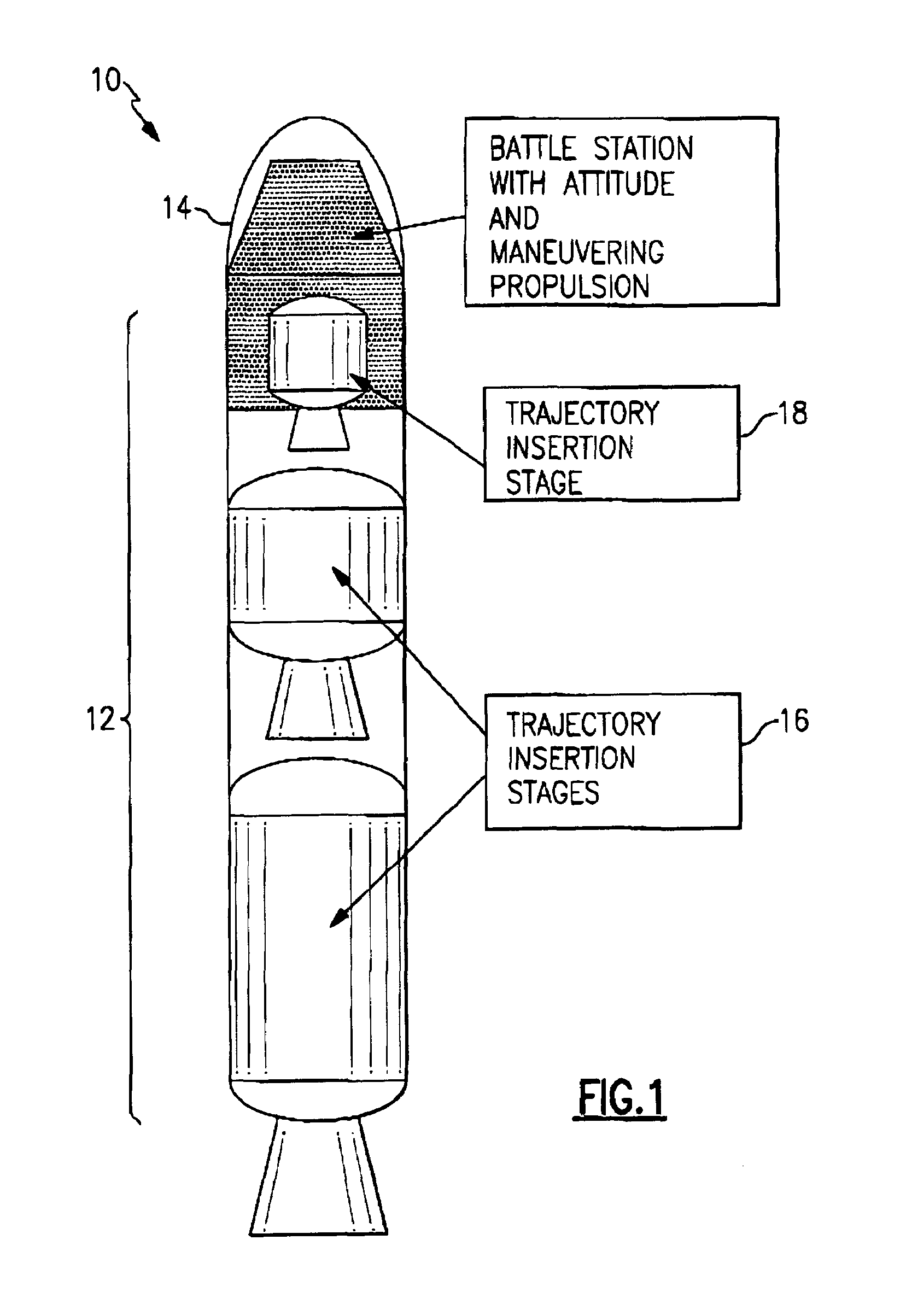
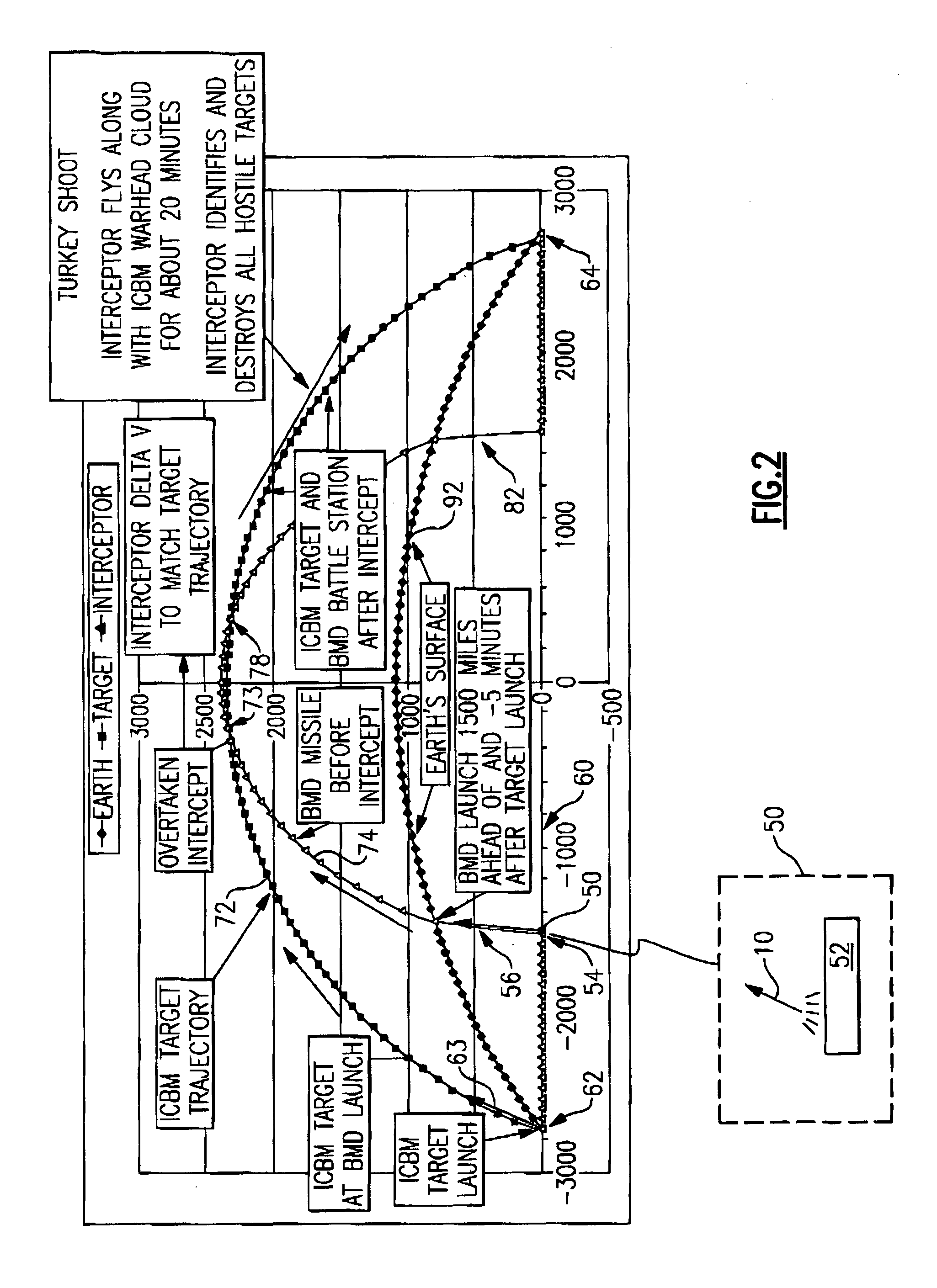
A method for ballistic target defense including identifying a launched ballistic target having a target launch point, a target launch direction, a target speed, and a target trajectory; launching a target interceptor in a launch direction that is generally the same as the target launch direction and with a speed that is less than the target speed; providing the interceptor with an approximate target intercept trajectory; and accelerating the interceptor at an approximate point of intercept to substantially match the target trajectory. During a relatively long target engagement time, the interceptor has approximately a zero net relative velocity with respect to the target. The interceptor will have a speed change capability sufficient to maneuver the interceptor around and / or in a target object cloud, providing the interceptor with the ability to inspect an object of the object cloud, capture an object of the object cloud, nondestructively engage in object of the object cloud, and / or destructively engage in object of the object cloud. Embodiments are also directed to a ballistic target defense system and a ballistic target interceptor.
Owner:UNITED TECH CORP
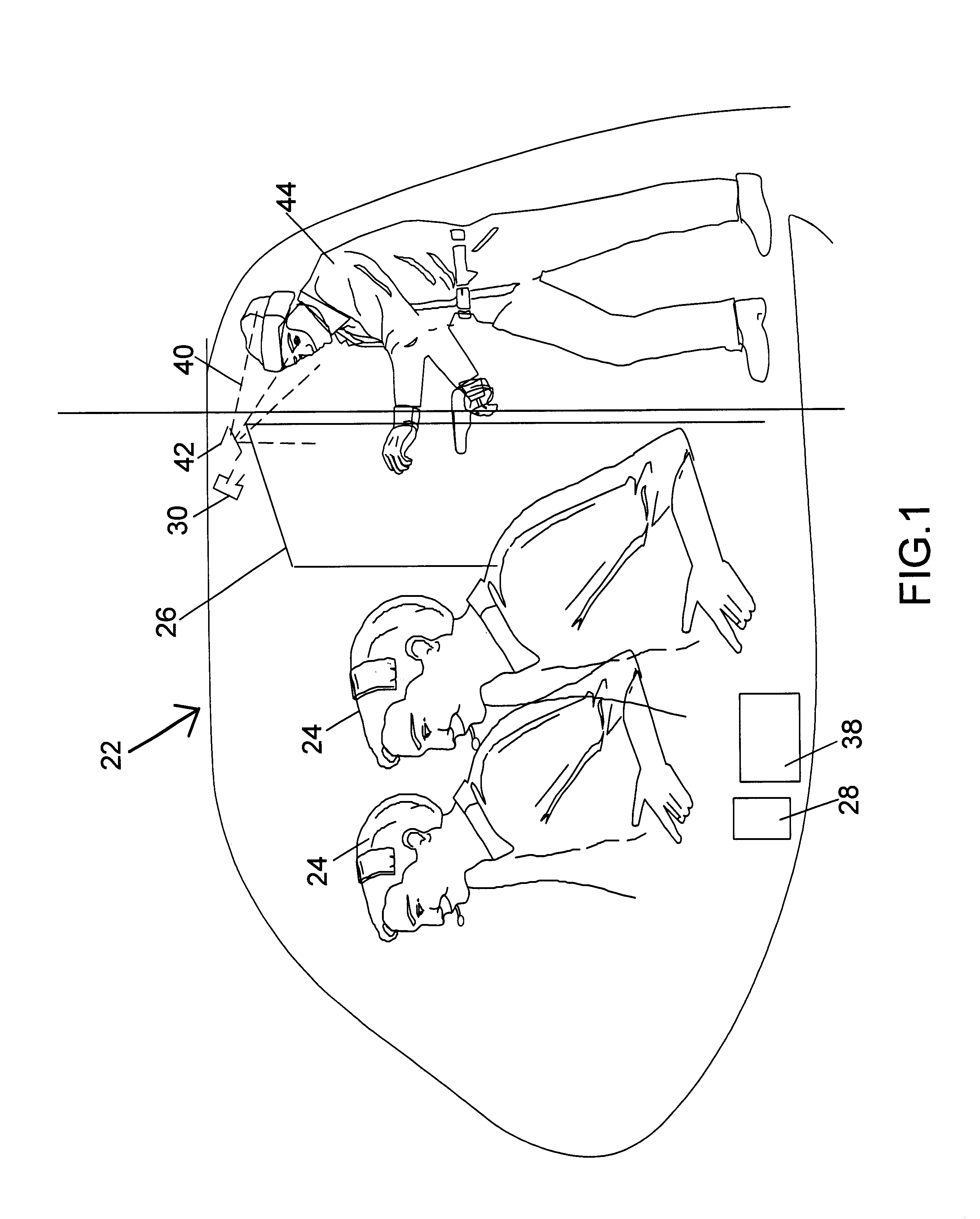
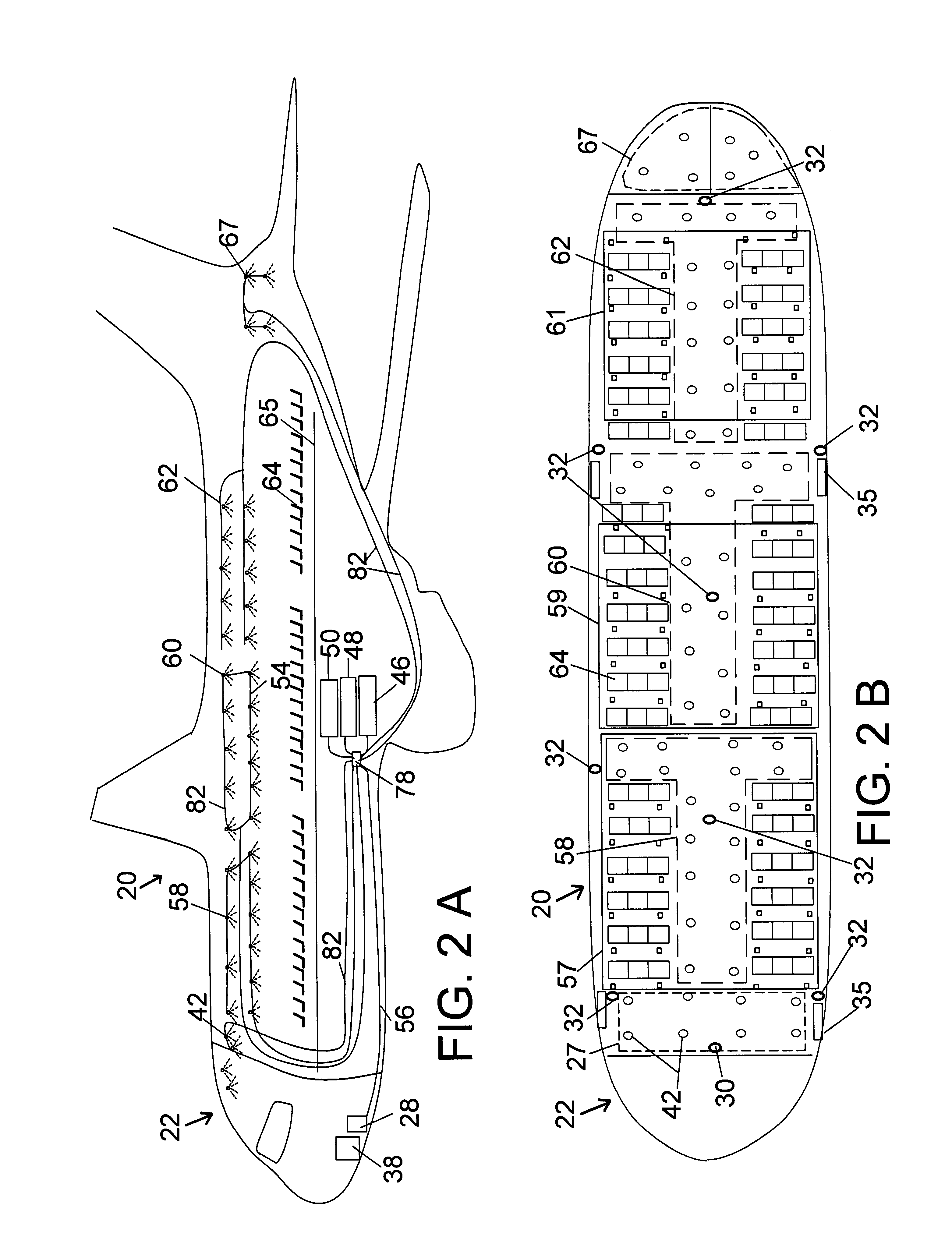
Method and system for countering hostile activity aboard an airplane
InactiveUS6696928B1Not limitedElectric signal transmission systemsDigital data processing detailsJet aeroplaneWhole body
A method of countering terrorism or hostile activity in an airplane by using a built-in defense system within the aircraft. The defense system includes chemical sprays, laser guns, and pre-programmed sound alarm systems. The aerosol chemicals range from benign fogging agents to non-lethal incapacitating agents from the categories of inhalants, general anesthetics, and irritants. Any of the systems can be used singly or in any combination. These systems can be activated manually from the control panel in the cockpit, or via a remote wireless system by the flight crew from anywhere within the plane. Such activation being password and code protected.
Owner:BOVEJA BIRINDER R +1
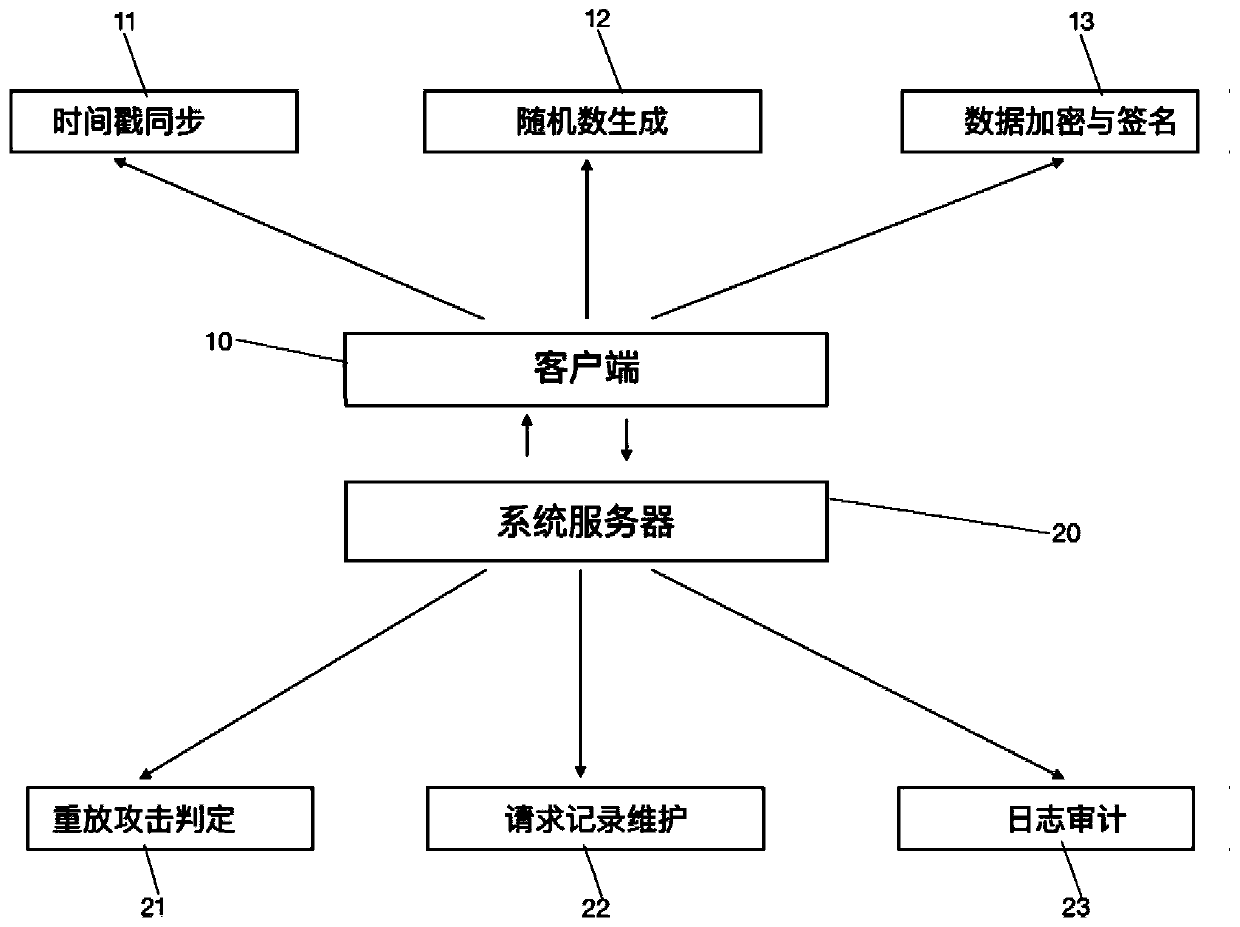
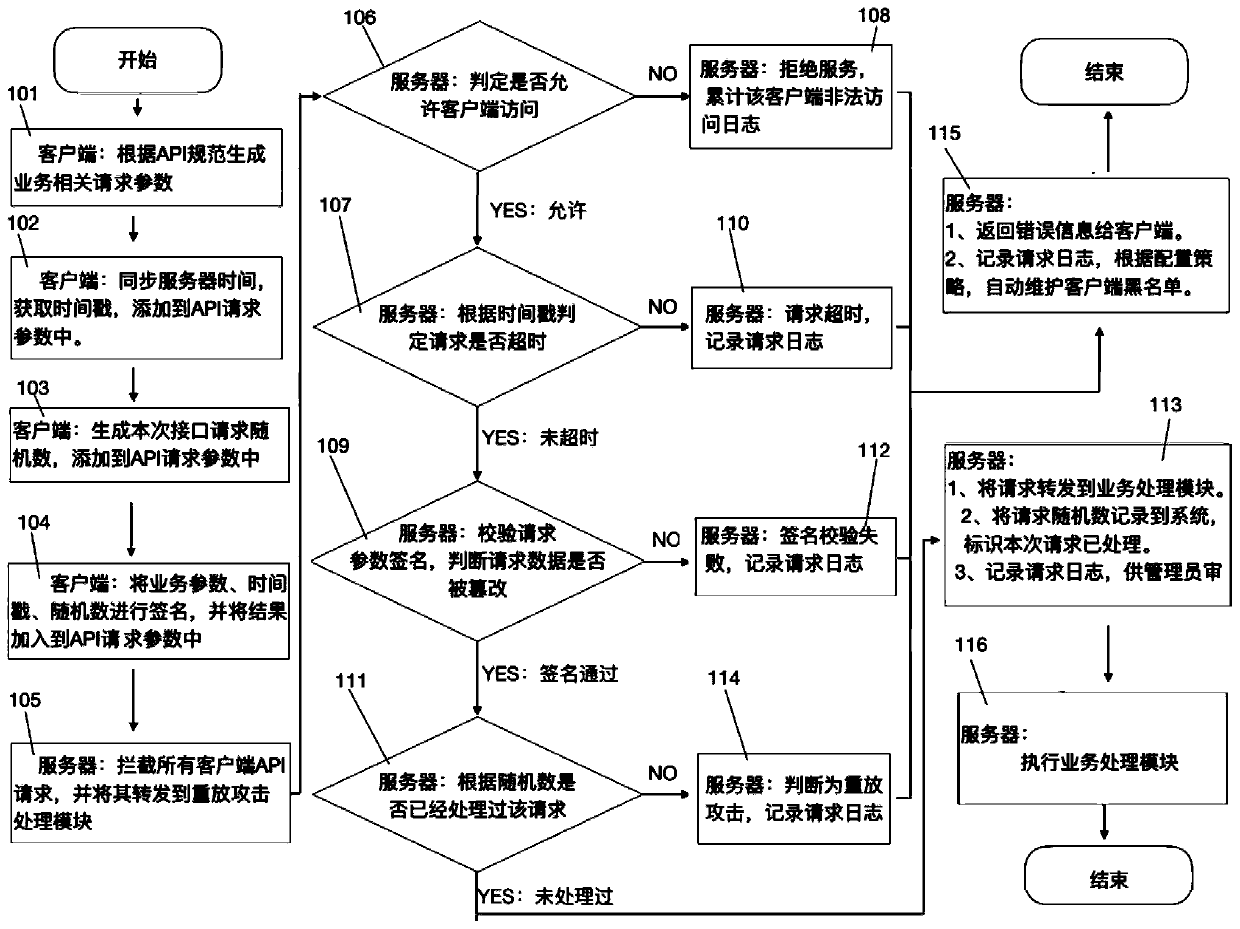
Timestamp-based API replay attack defense system and method
ActiveCN110611564AReduce loadGuaranteed normal loadingKey distribution for secure communicationUser identity/authority verificationTimestampClient-side
The invention discloses a timestamp-based API replay attack defence system and a method, and aims to provide the defense system and the method capable of improving system security. The defense systemcomprises a client and a system server. The client is used as an API request initiator, and the client initiates API access to the system server according to service requirements; assembling interfacerequest parameters according to an established communication protocol, processing a result fed back by the server, and driving the trend of a business process; the client comprises a timestamp synchronization module, a random number generation module and a data signature and encryption module; the system server is used for receiving an API access request from a client and providing an open service; for replay attack defense, intercepting all API requests, judging whether to replay attacks according to request parameters and system records, and recording related request information to form anaudit log module; and the system server comprises a replay attack judgment module, a request record maintenance module and an audit log module.
Owner:YUNNAN KUNGANG ELECTRONICS INFORMATION TECH CO LTD
Cloud-based intelligent security defense system and defense method
InactiveCN103905459AImprove recognitionImproving the performance of blocking defensesTransmissionCore functionRecovery function
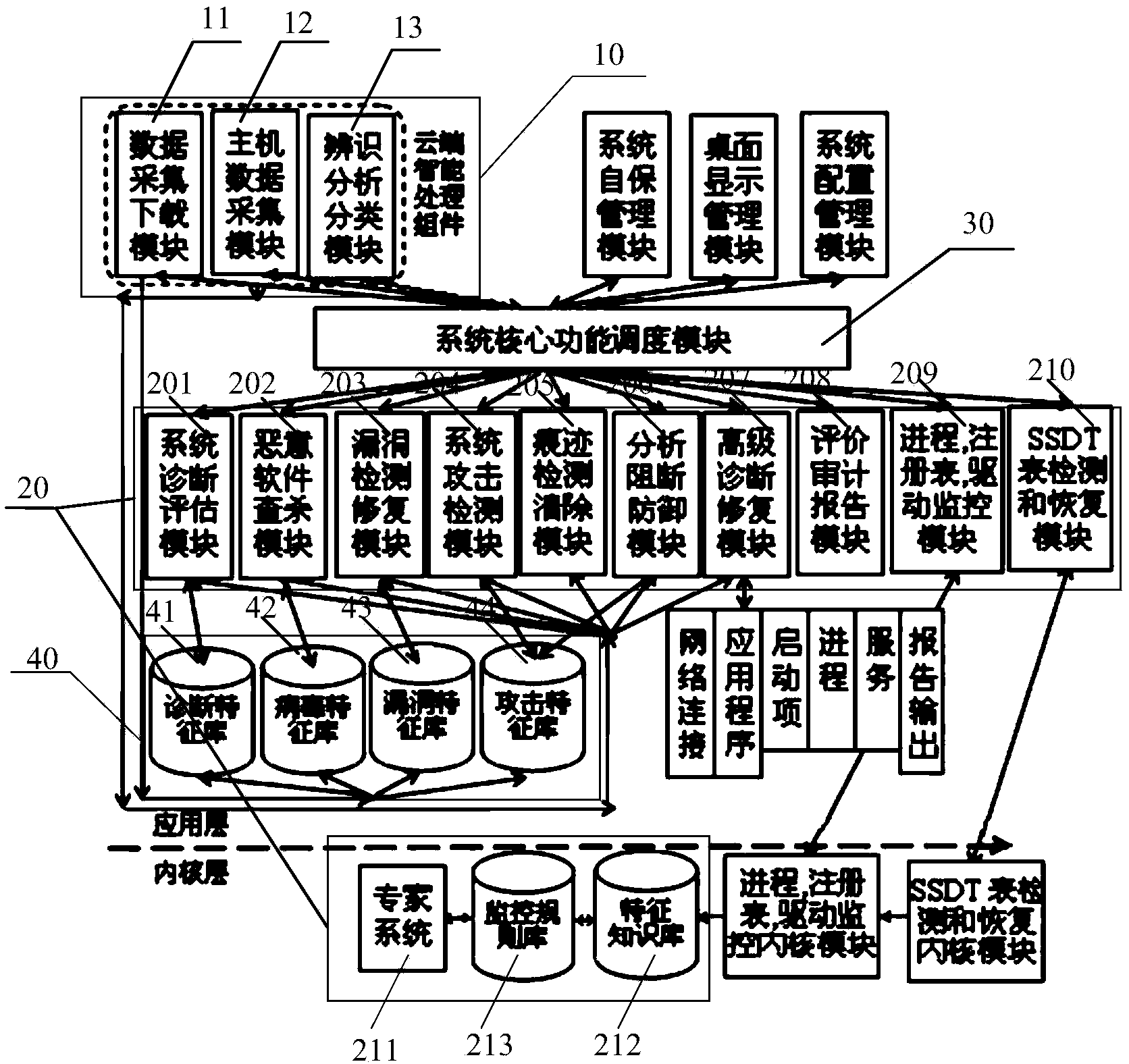
The invention provides a cloud-based intelligent security defense system and defense method. Intelligent processing platforms are mutually dispatched through a system core function dispatching module according to a cloud-based intelligent processing assembly, the network security defense system capable of detecting, monitoring, checking, killing, blocking, auditing and recovering abnormal information is formed, the dynamic intelligent detection, identification and blocking and defense performance of the whole network is effectively improved, and the overall intelligent defense performance is improved.
Owner:SHANGHAI DIANJI UNIV
Humanized anti-CD47 monoclonal antibody and application thereof
ActiveCN110872348AGrowth inhibitionBlocking the "Don't Eat Me" SignalImmunoglobulins against cell receptors/antigens/surface-determinantsAntibody ingredientsHuman tumorAntiendomysial antibodies
The invention relates to the technical field of antibody drugs, in particular to a humanized anti-CD47 monoclonal antibody and an application thereof. The humanized anti-CD47 monoclonal antibody provided by the invention can effectively inhibit tumor growth, dose-dependently block the binding of human SIRP alpha and human CD47, promote the phagocytosis effect of macrophages on tumor cells, preventthe tumor cells from evading a defense system of tumor immunity, and play an anti-tumor role; the monoclonal antibody can block the binding of the CD47 on the surfaces of the tumor cells and the SIRPalpha on the surfaces of the macrophages, block a ''do not eat me'' signal of the tumor cells, promote the recognition and uptake of the tumor cells by the macrophages, and promote the progress of phagocytizing the tumor cells; and the binding of the CD47 on the surfaces of the tumor cells and the SIRP alpha on the surfaces of the macrophages is a universal ''do not eat me''signal, and the CD47 can be used as a very promising target in the tumor immune system, and can play a powerful and effective role in human tumor treatment.
Owner:CHANGCHUN GENESCIENCE PHARM CO LTD
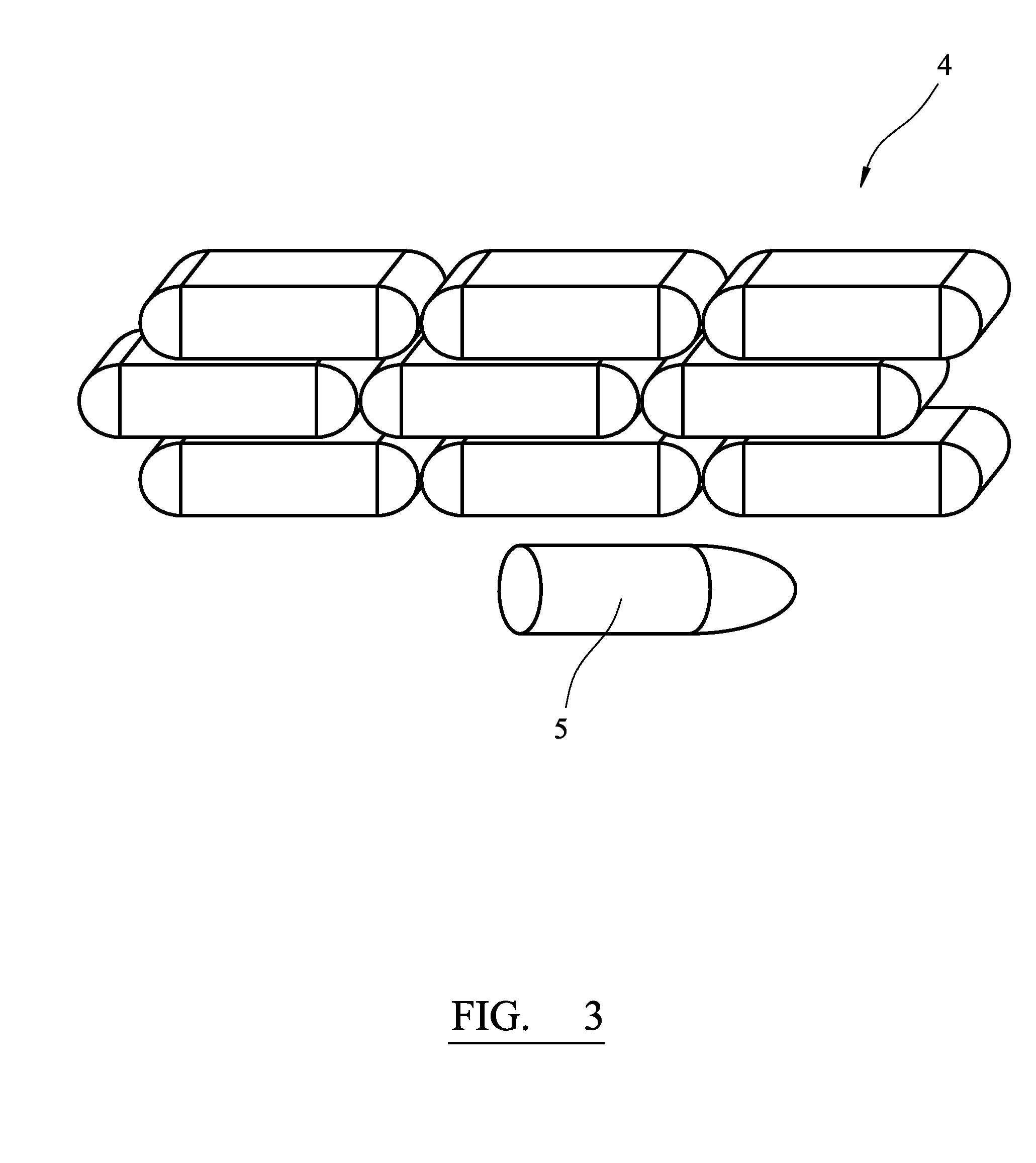
Projectile for radially deploying sub-projectiles
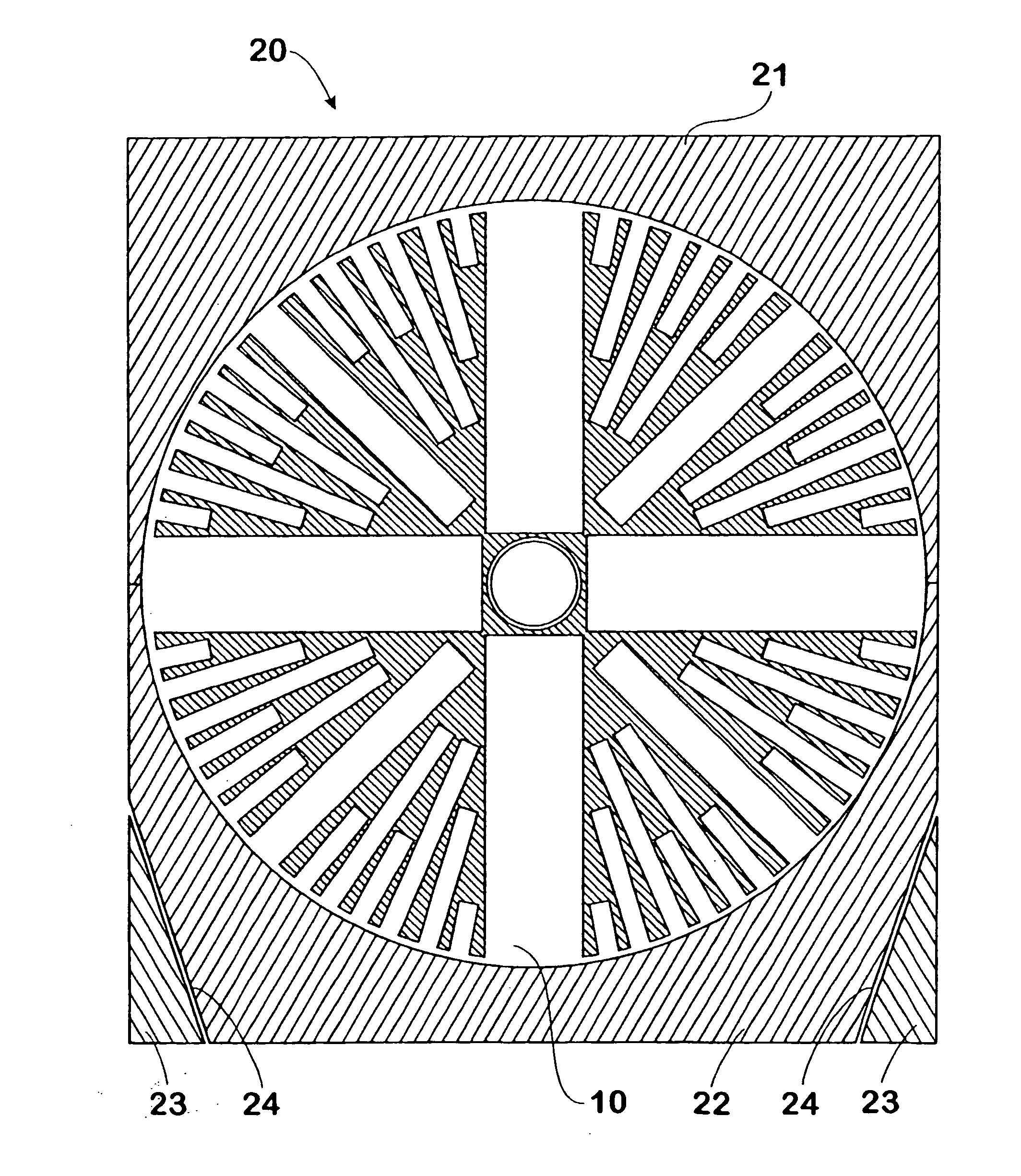
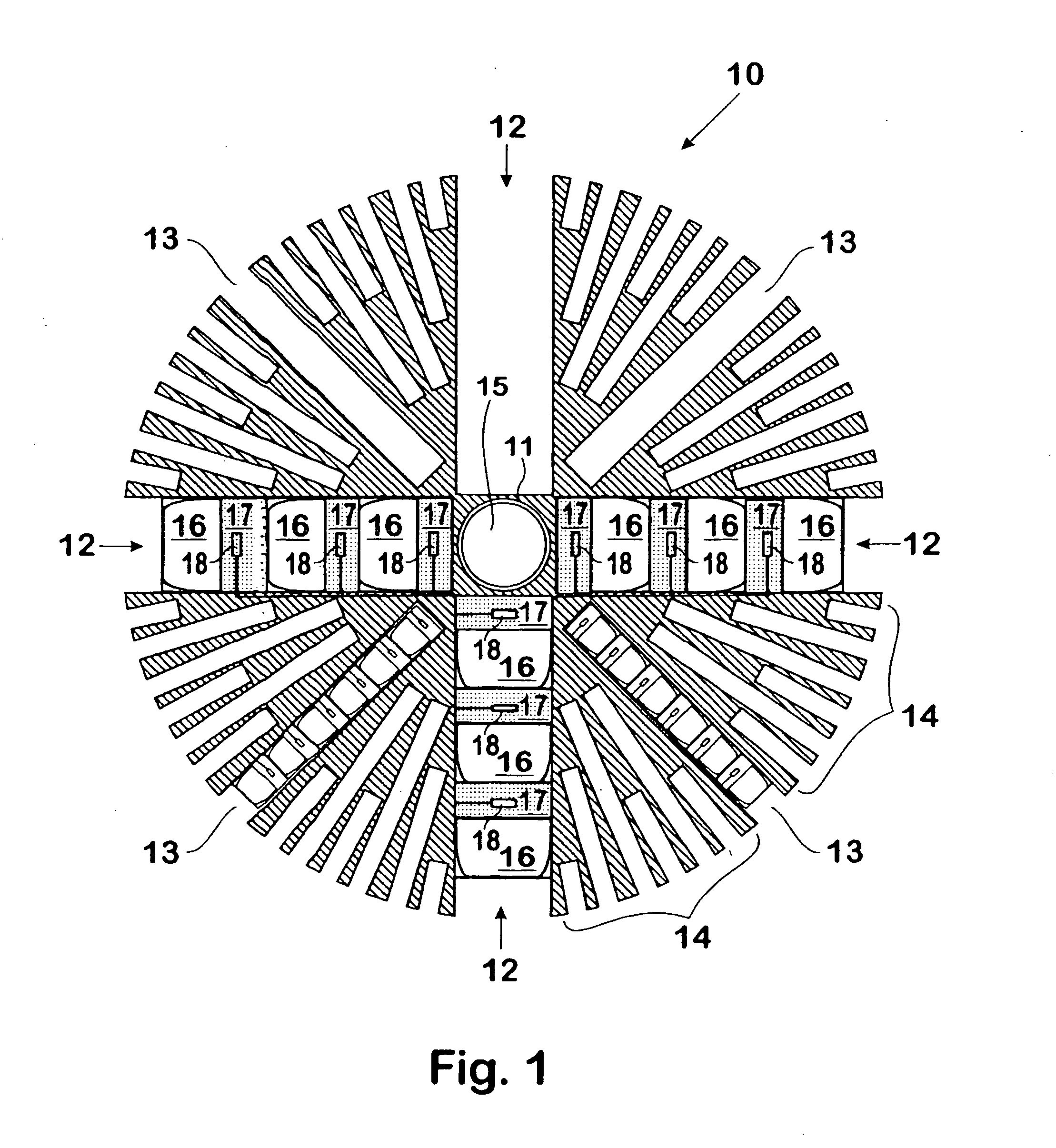
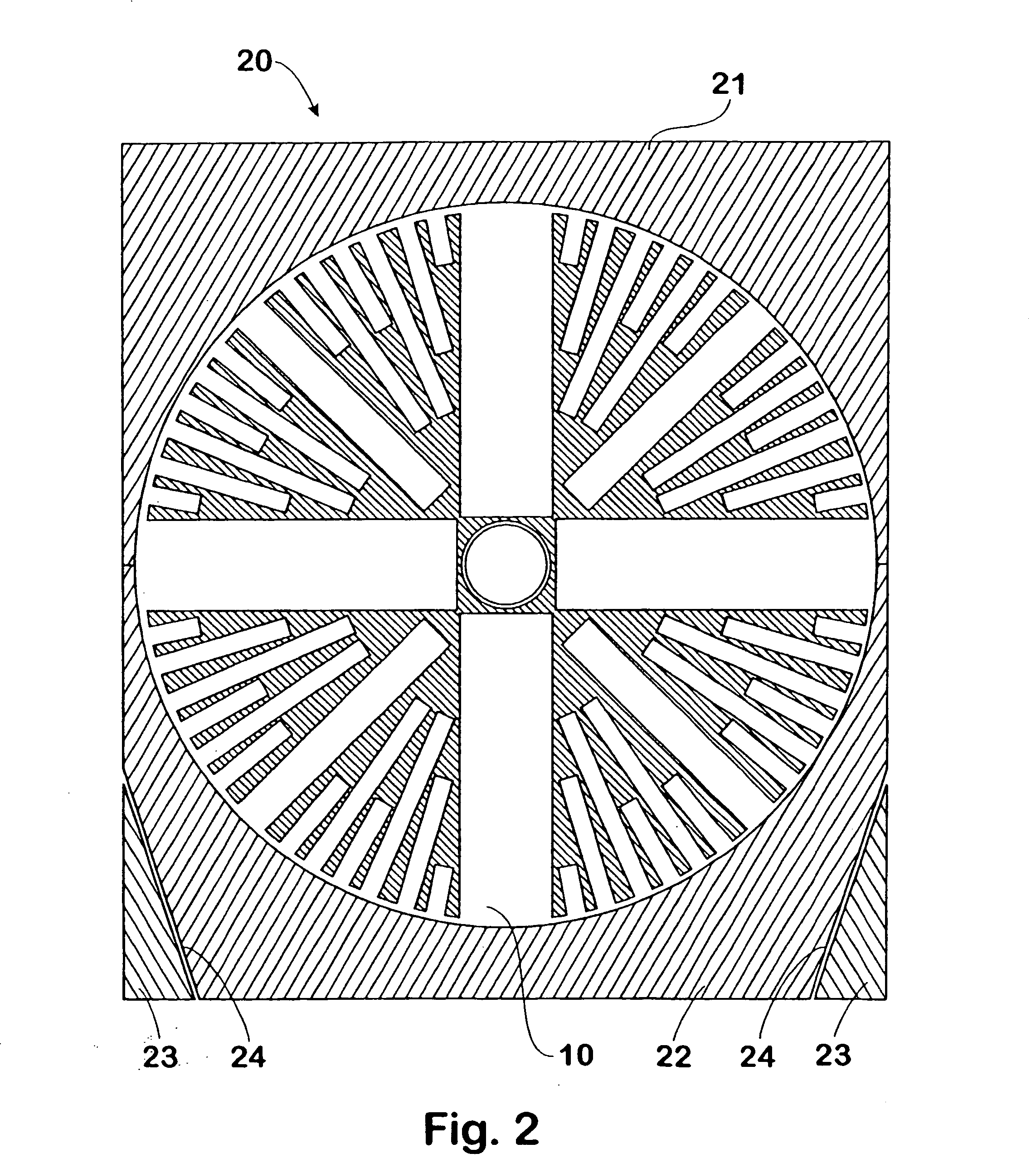
InactiveUS20040244628A1Easy to shapeIncrease in muzzle velocityDefence devicesAmmunition projectilesElectronic controllerEngineering
A projectile (10) for firing from a barrel, said projectile including a multiplicity of barrel assemblies (12, 13, 14) radially disposed from the centre of mass of the projectile, wherein each of said multiplicity of barrel assemblies includes a plurality of sub-projectiles (16) axially disposed within a barrel; each of said sub-projectiles associated with a discrete propellent charge (17) for propelling a respective sub-projectile from the barrel, wherein said projectile is capable of selectively firing sub-projectiles (16), suitably with the aid of primers (18) each coupled to an electronic controller (15). to provide a predetermined pattern of deployed sub-projectiles. A defence system employing projectiles of the type described is also disclosed, together with a method for disguising the launch location of a projectile utilising divert propulsion.
Owner:METAL STORM LTD
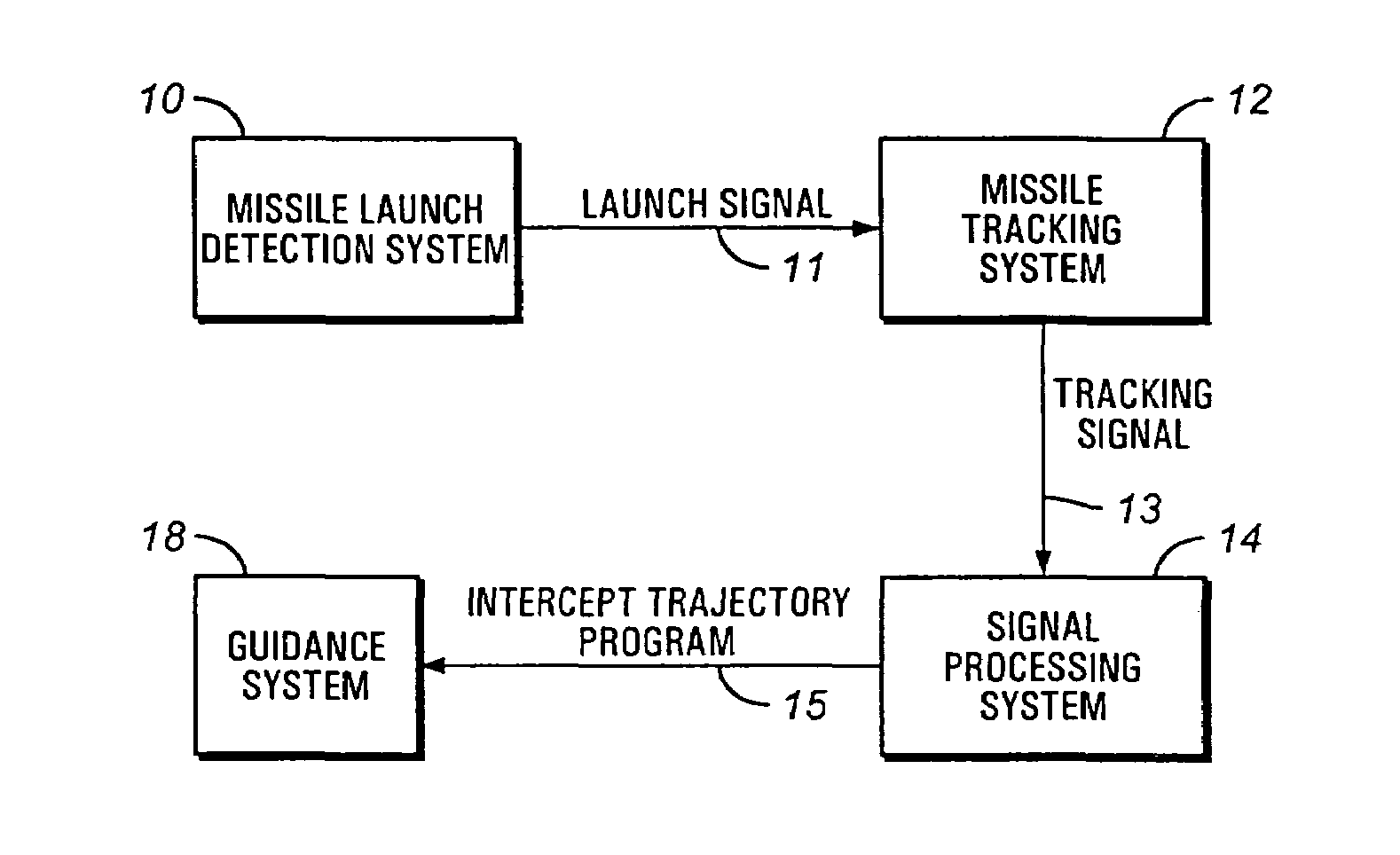
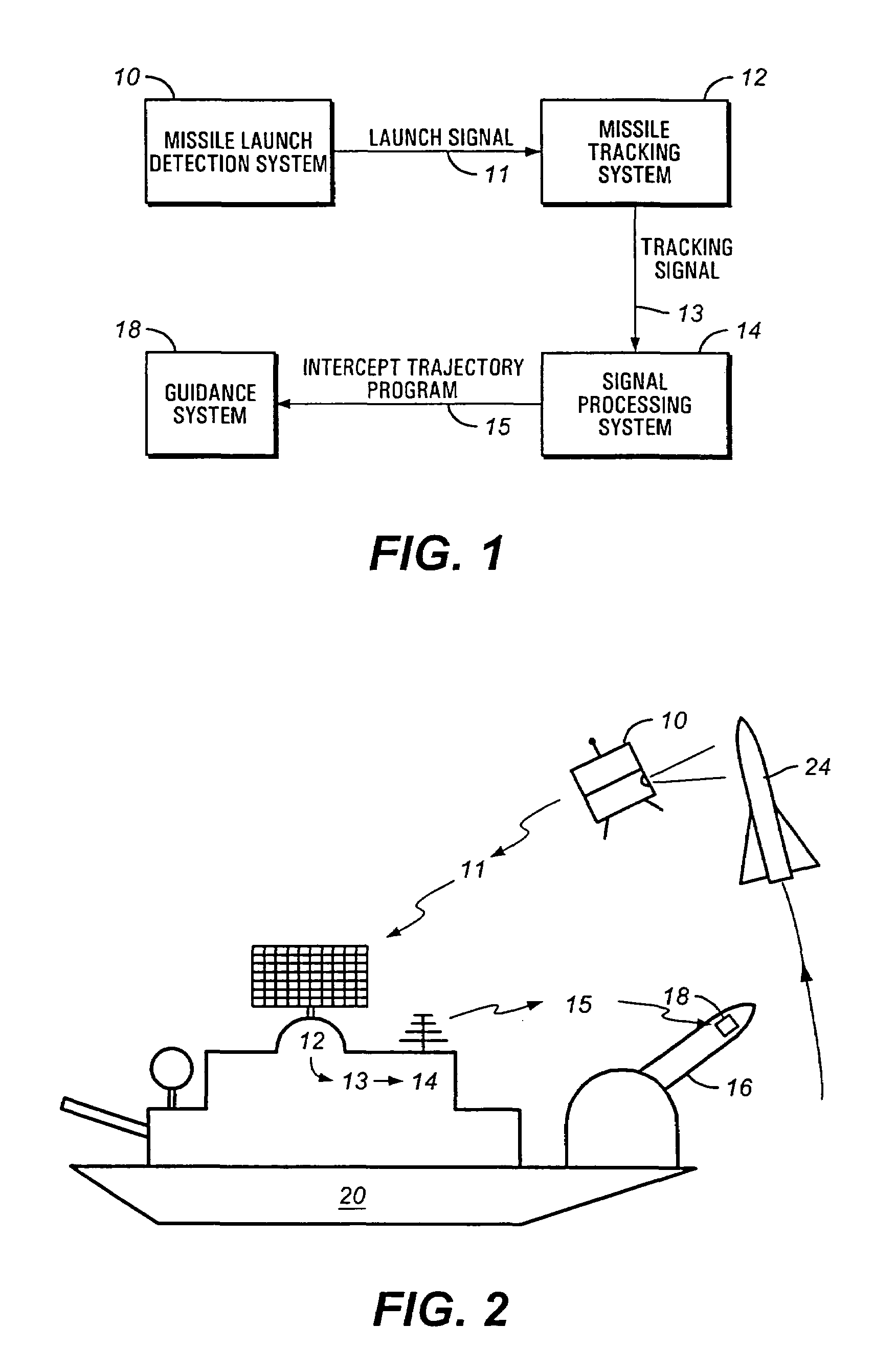
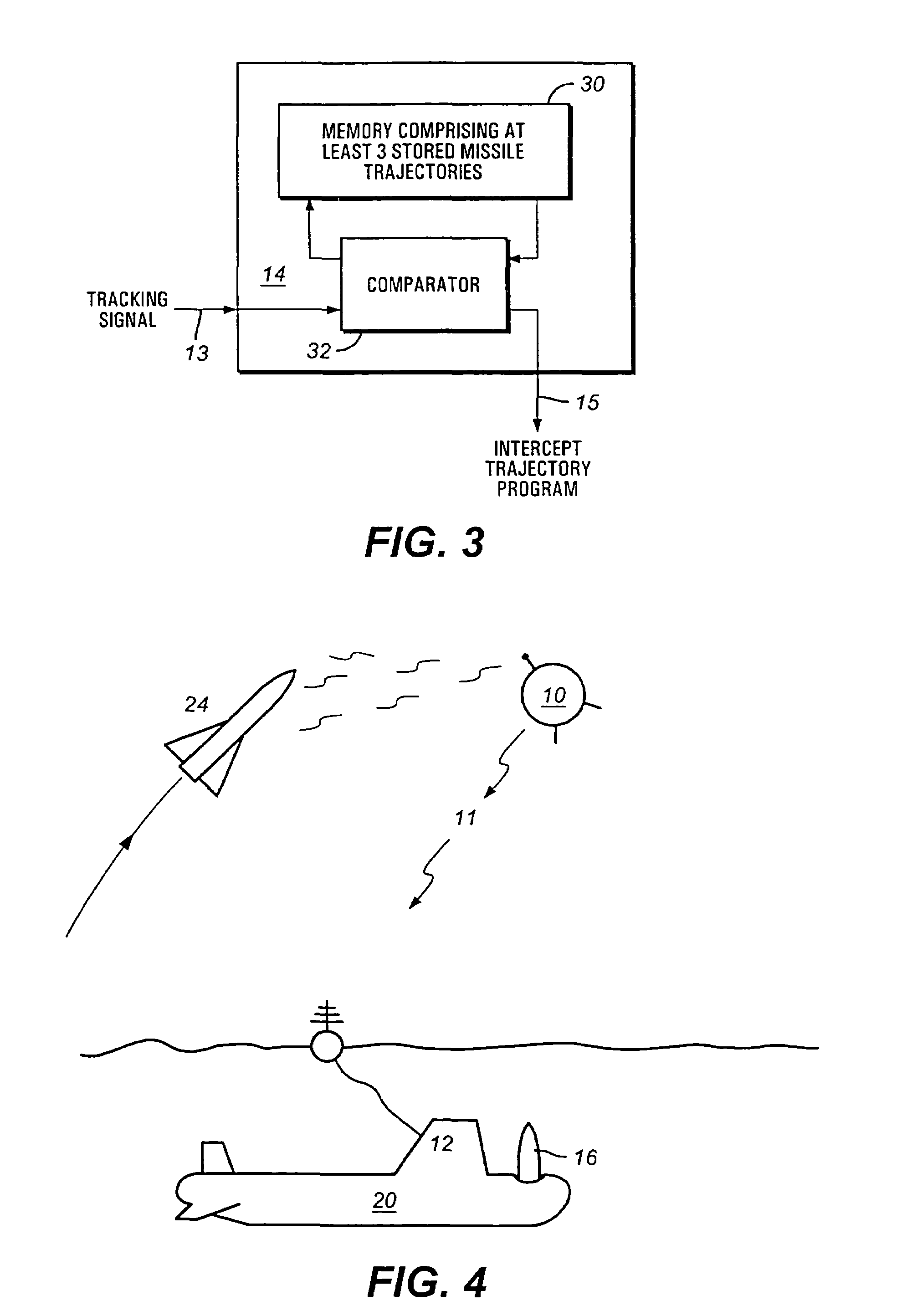
Mobile ballistic missile detection and defense system
The present invention is directed towards a ballistic missile detection and defense system. The system of the present invention comprises a ship based interceptor or antiballistic missile, a missile launch detection and tracking system, and a signal processing system capable of receiving said tracking signal calculating an intercept trajectory for an antiballistic missile to intercept a ballistic missile, and further capable of outputting an intercept trajectory program to an antiballistic missile.
Owner:LOCKHEED MARTIN CORP
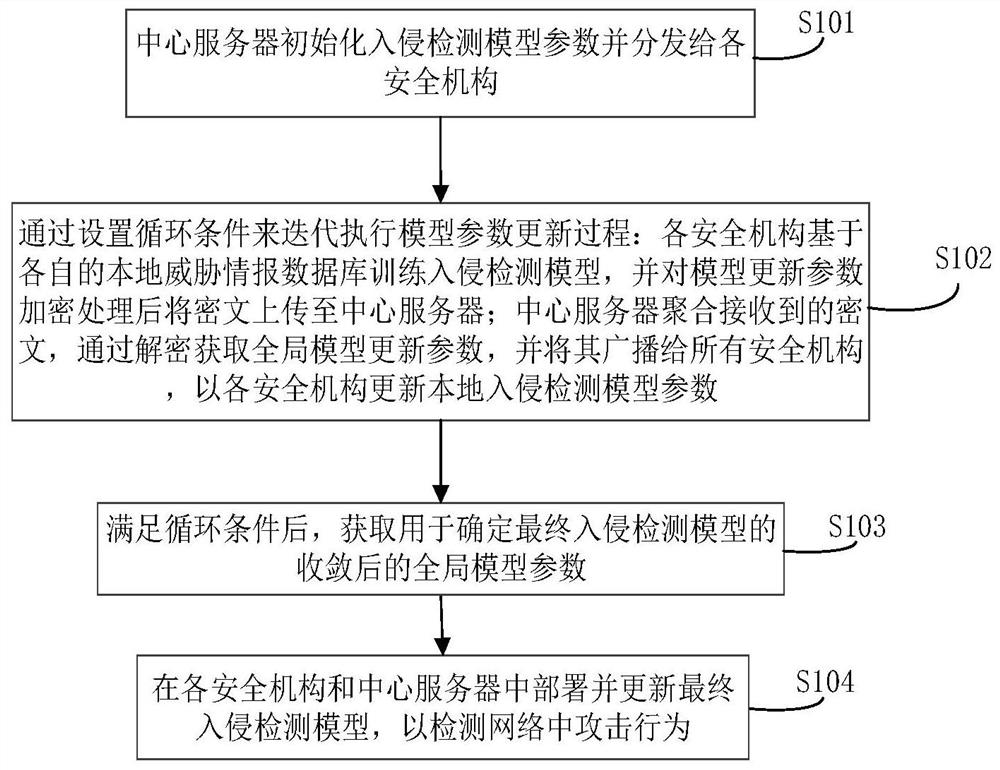
Network threat collaborative defense system and method based on information sharing
ActiveCN112217626AImprove training efficiencyEfficient sharingKey distribution for secure communicationCommunication with homomorphic encryptionCiphertextAttack
The invention belongs to the technical field of network security, and particularly relates to a network threat cooperative defense system and method based on information sharing. The method comprisesthe steps: deploying a central server and a plurality of safety mechanisms which train an intrusion detection model based on respective local threat information databases; after the model updating parameters are encrypted, uploading the ciphertext to a central server; and employing the central server for aggregating the received ciphertext to obtain global model updating parameters through decryption and broadcasting the global model updating parameters to all security mechanisms so as to update the local intrusion detection model of each security mechanism. Based on the federated learning framework, multiple security mechanisms can be helped to jointly establish a system defense model, the method can be suitable for multiple machine learning models, multiple collusion attack scenes can beresisted, the applicability is high, and the anti-attack performance of the network is improved.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
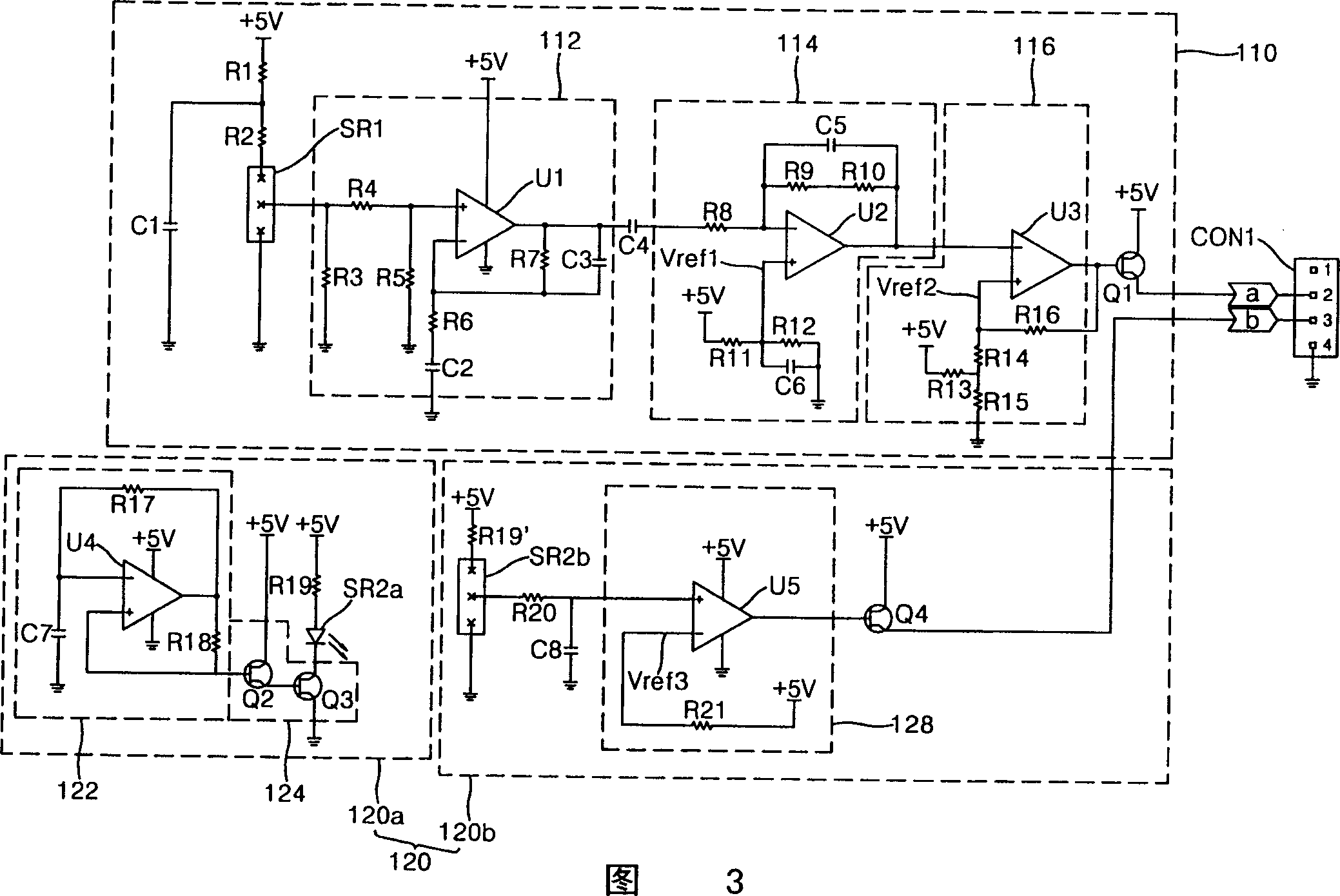
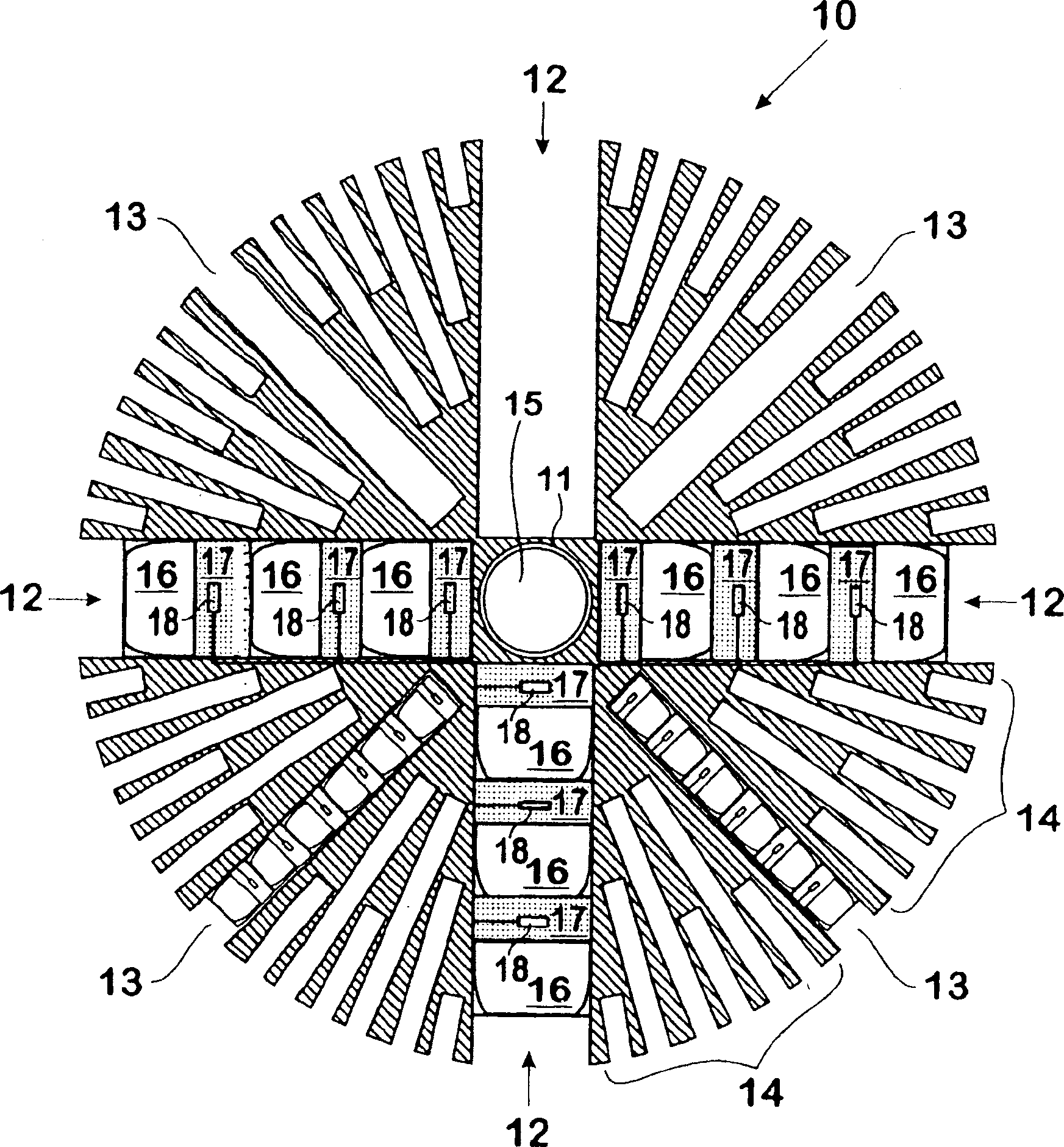
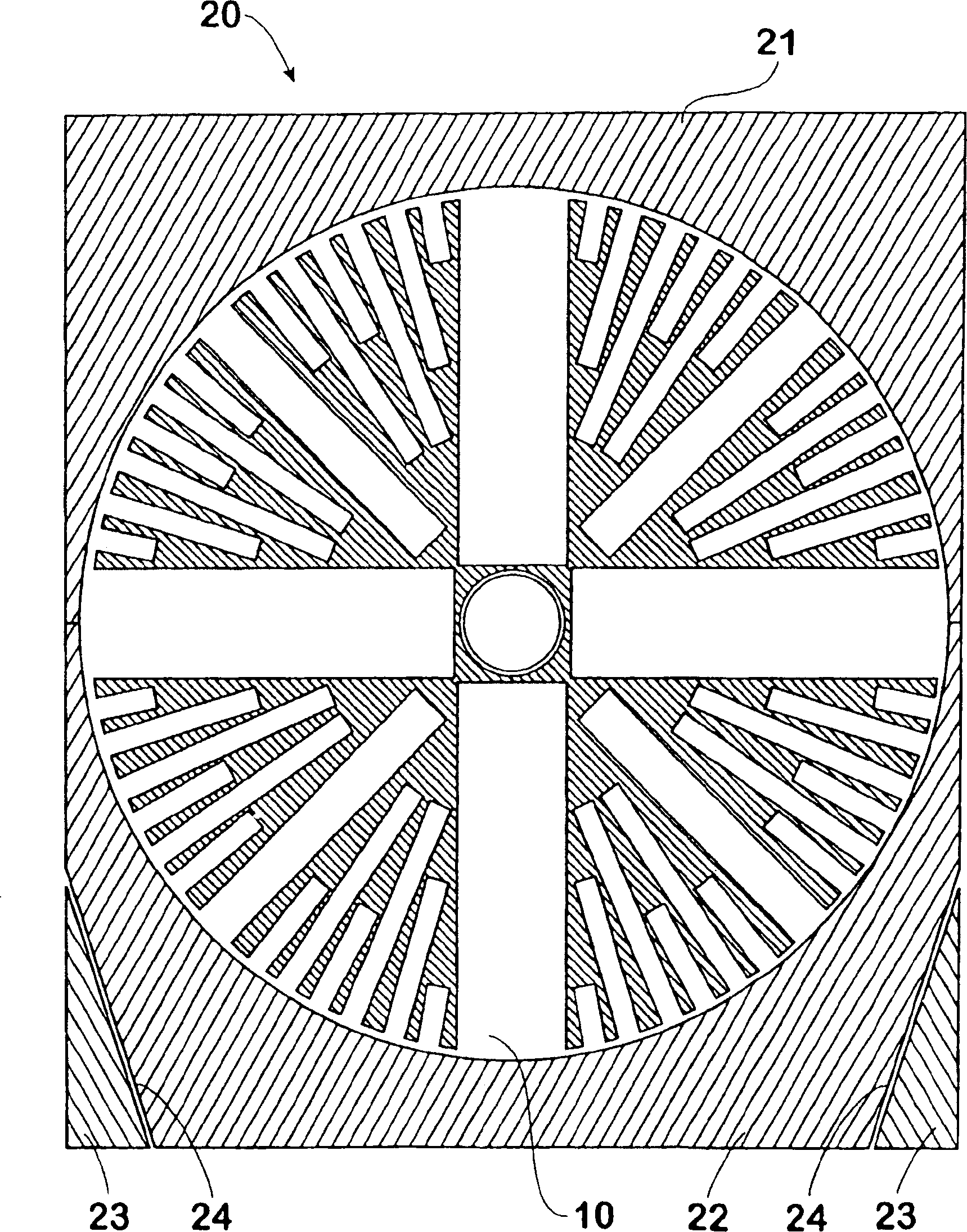
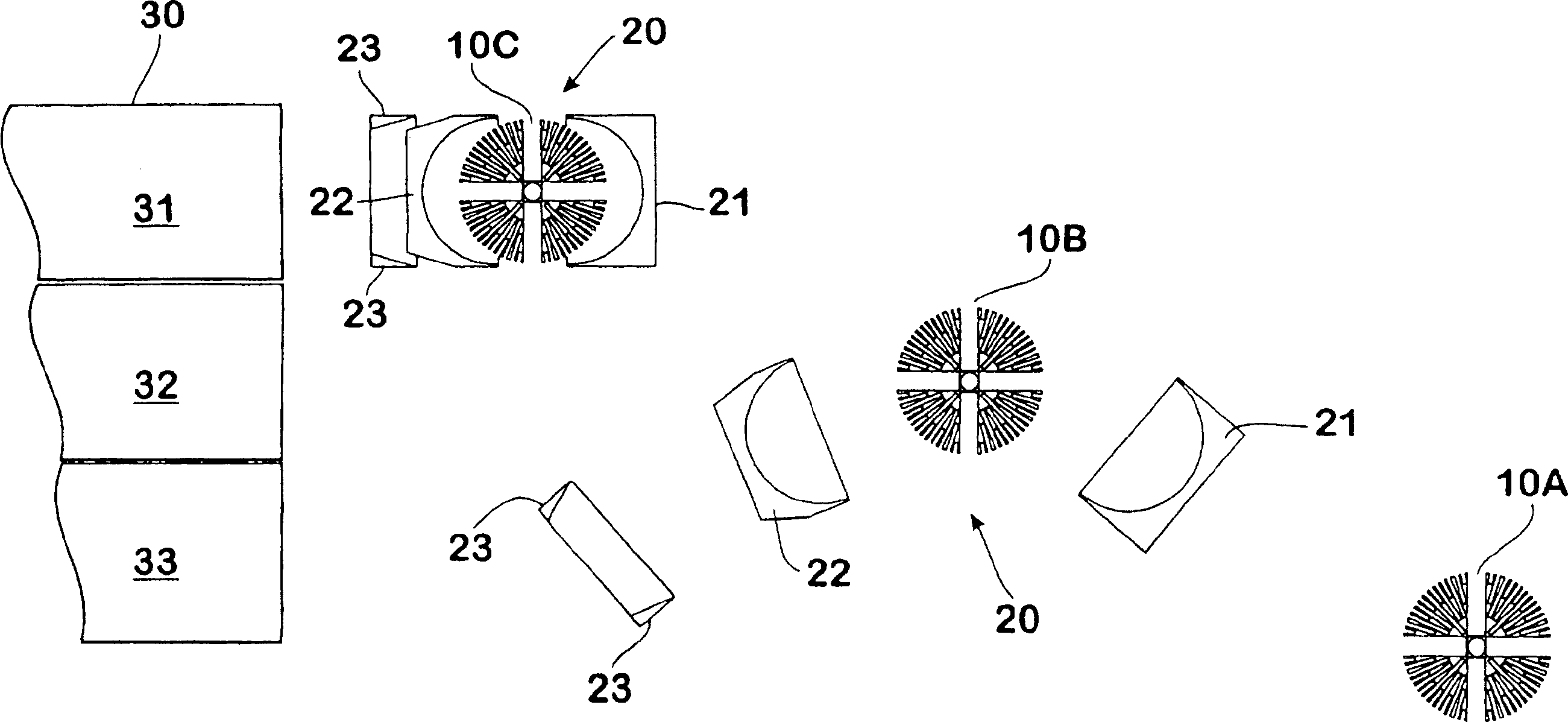
Defence system
InactiveUS20080250916A1Reduce in quantityEasy constructionDefence devicesBarrages/weirsFiberCrystalline materials
Owner:ENVIRONMENTAL DEFENCE SYST
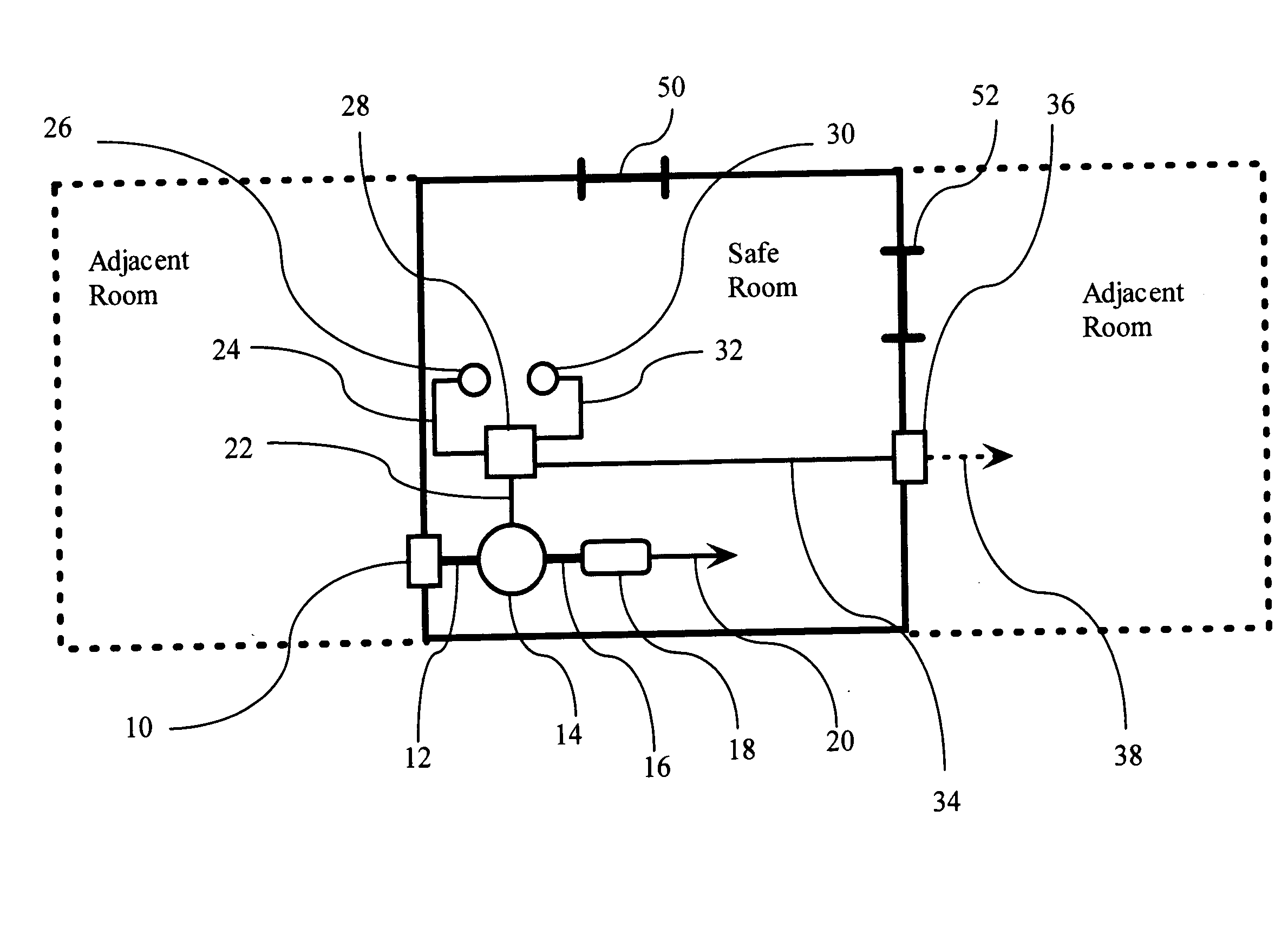
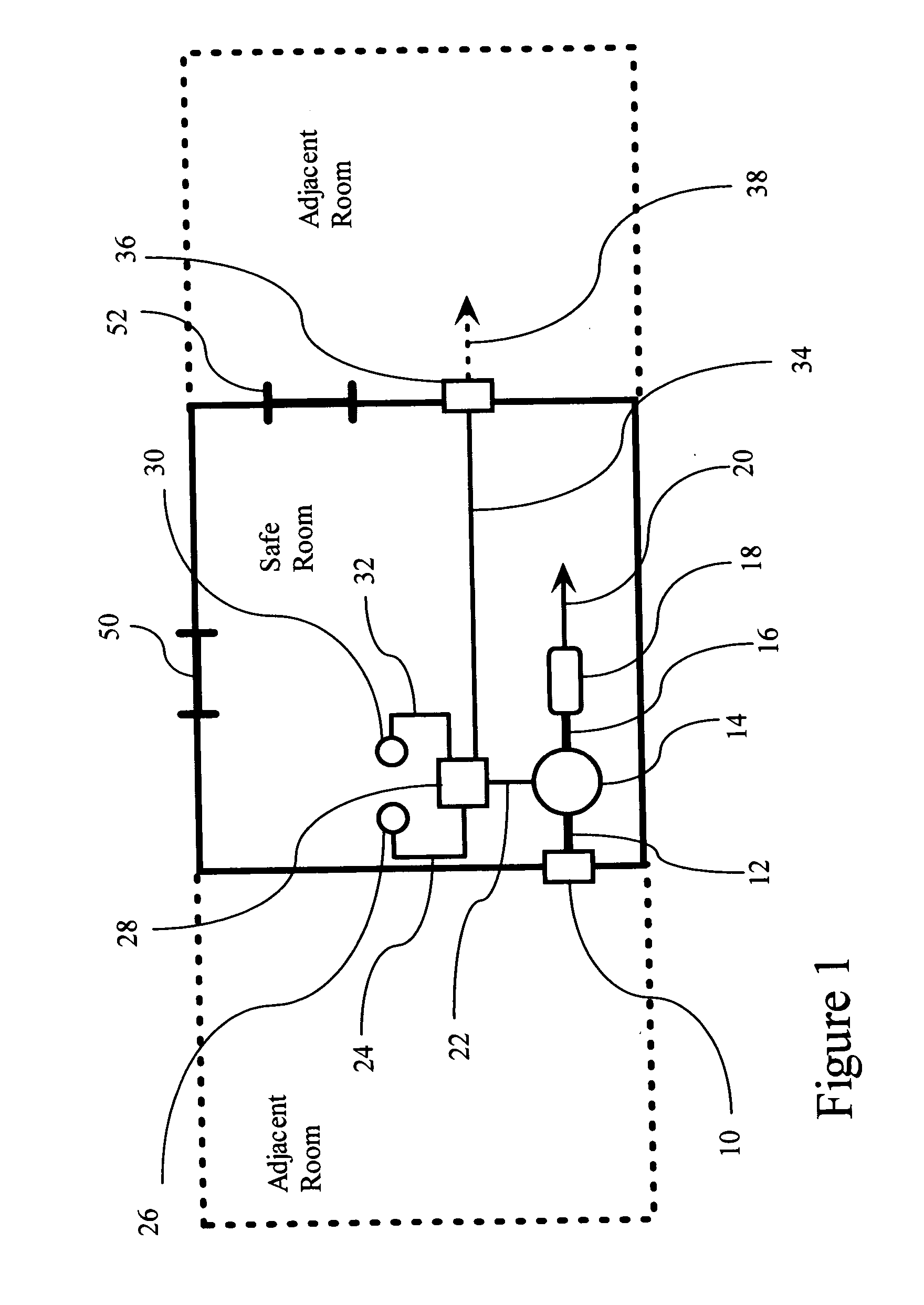
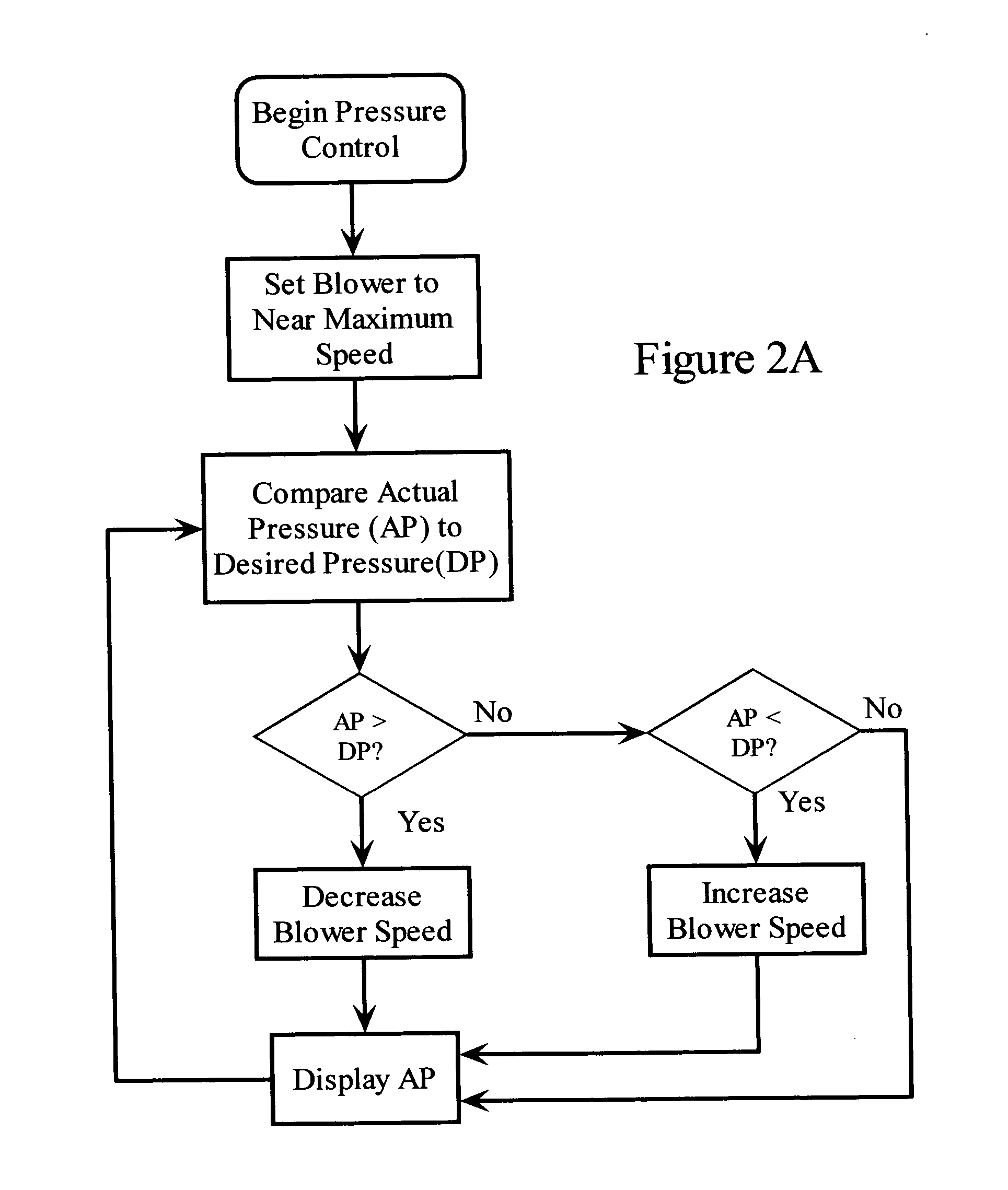
Biological home defense system
InactiveUS20070068391A1Quickly and inexpensively roomQuickly and inexpensively createCombination devicesGas treatmentEngineeringCrowds
The invention relates to biological home defense systems for use by populations at risk of widespread biological attack via biological weapons of mass destruction, especially biological weapons involving aerosol attacks. The present invention is also related to methods for using such biological home defense systems wherein meteorological data is used to issue advisories with regard to the use of such biological home defense systems to a population at risk of exposure to biological weapons of mass destruction.
Owner:CIVILIAN BIODEFENSE GROUP
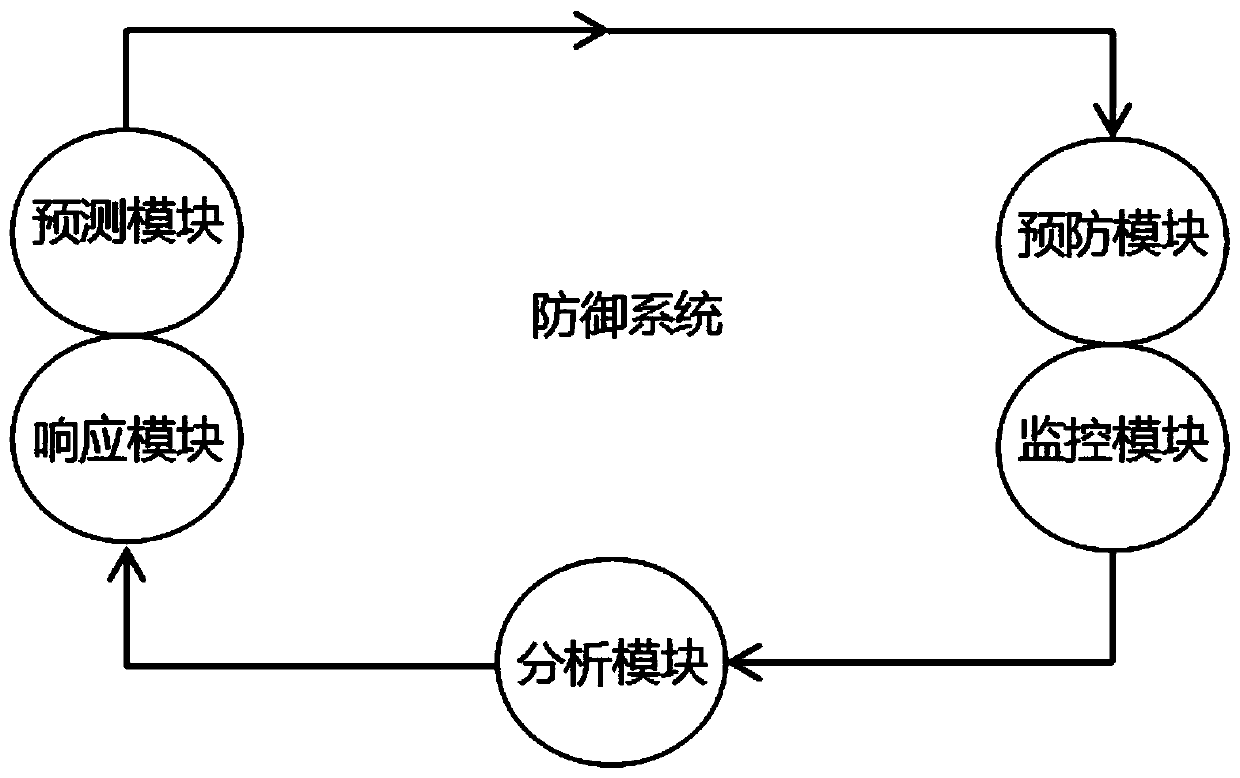
Defense system and method for solving network threats in self-adaptive closed-loop mode
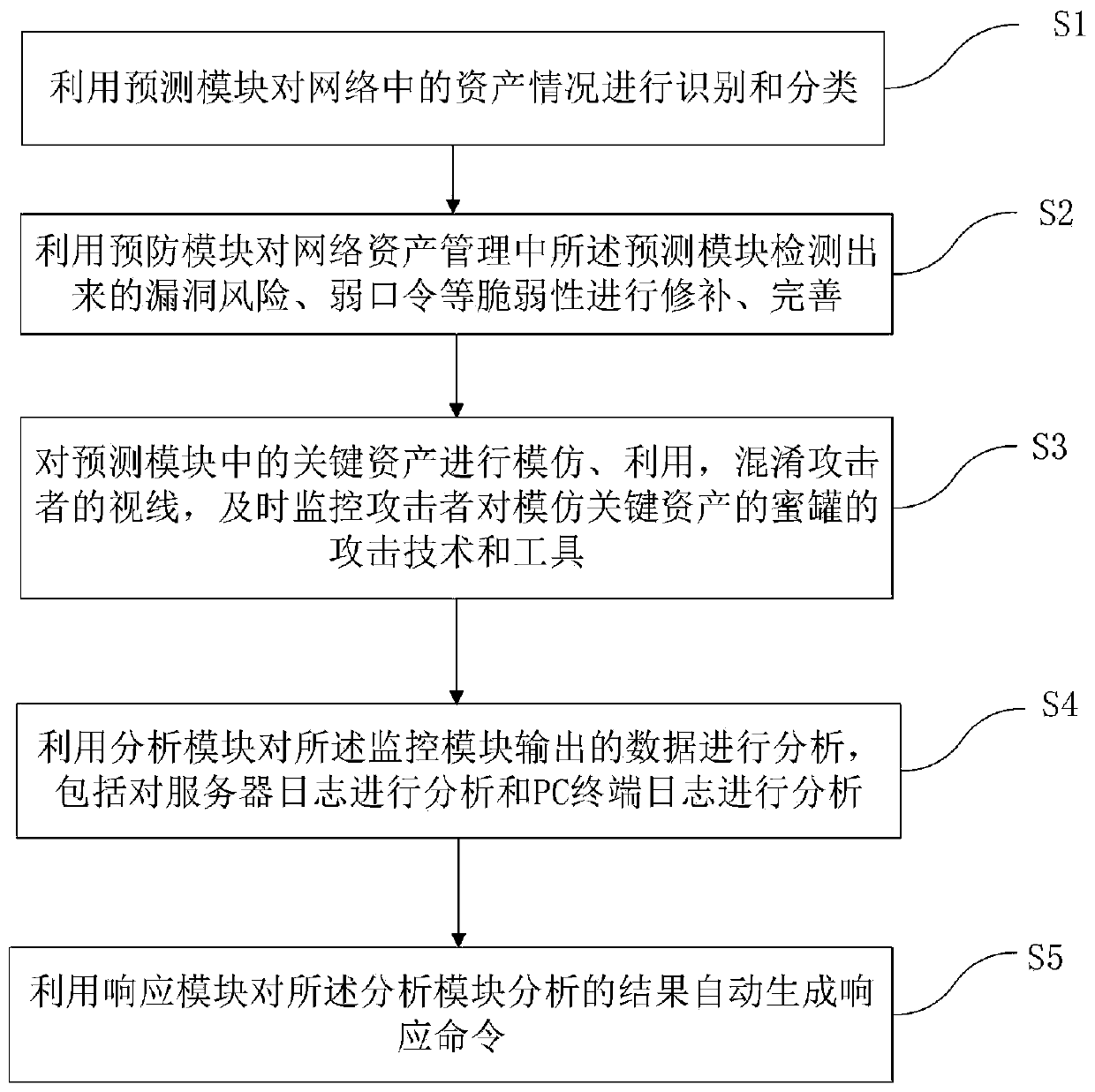
The invention relates to a defense system and method for solving network threats in a self-adaptive closed-loop mode, and the system comprises a prediction module which is used for the recognition andclassification of asset conditions in a network on one hand, and is also used for the vulnerability scanning and weak password scanning of the network on the other hand; a prevention module which isused for repairing and perfecting vulnerability such as vulnerability risks and weak passwords detected by the prediction module in network asset management; a monitoring module which is used for simulating the key assets in the prediction module, utilizing and confusing the sight of an attacker, and monitoring the attack technology and tool of the attacker on honeypots simulating the key assets in time; an analysis module which is used for analyzing the data output by the monitoring module, and a response module which is used for automatically generating a response command for an analysis result of the analysis module. The defense system and method for solving the network threats in the self-adaptive closed-loop manner are specifically adapted to environments with different network resources and can effectively solve the threats in a network.
Owner:南京经纬信安科技有限公司
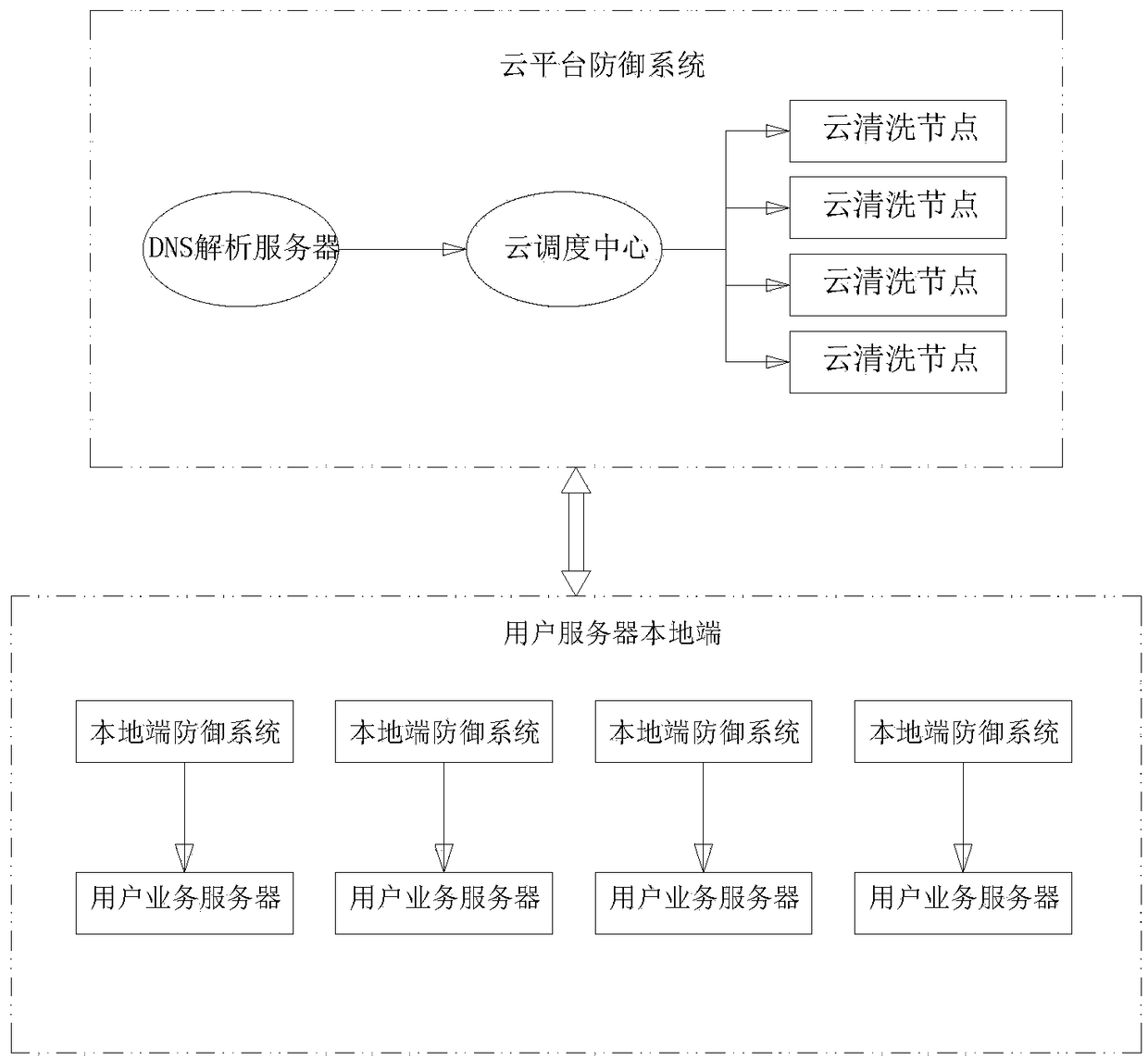
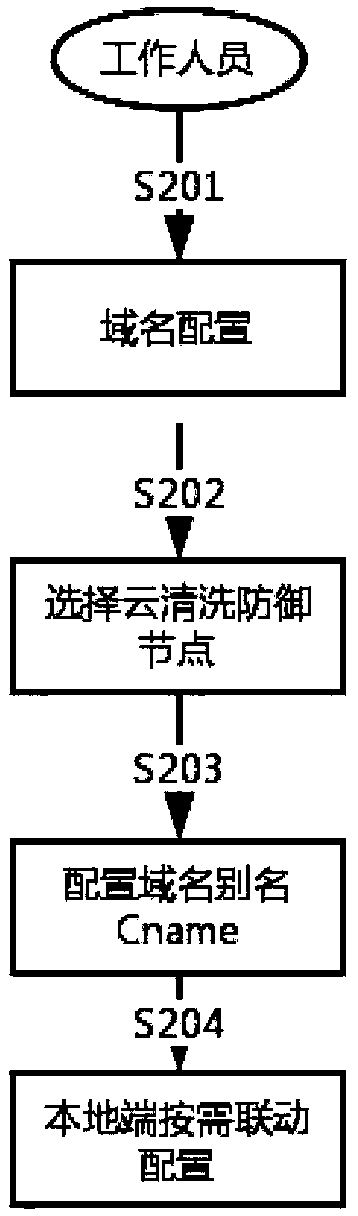
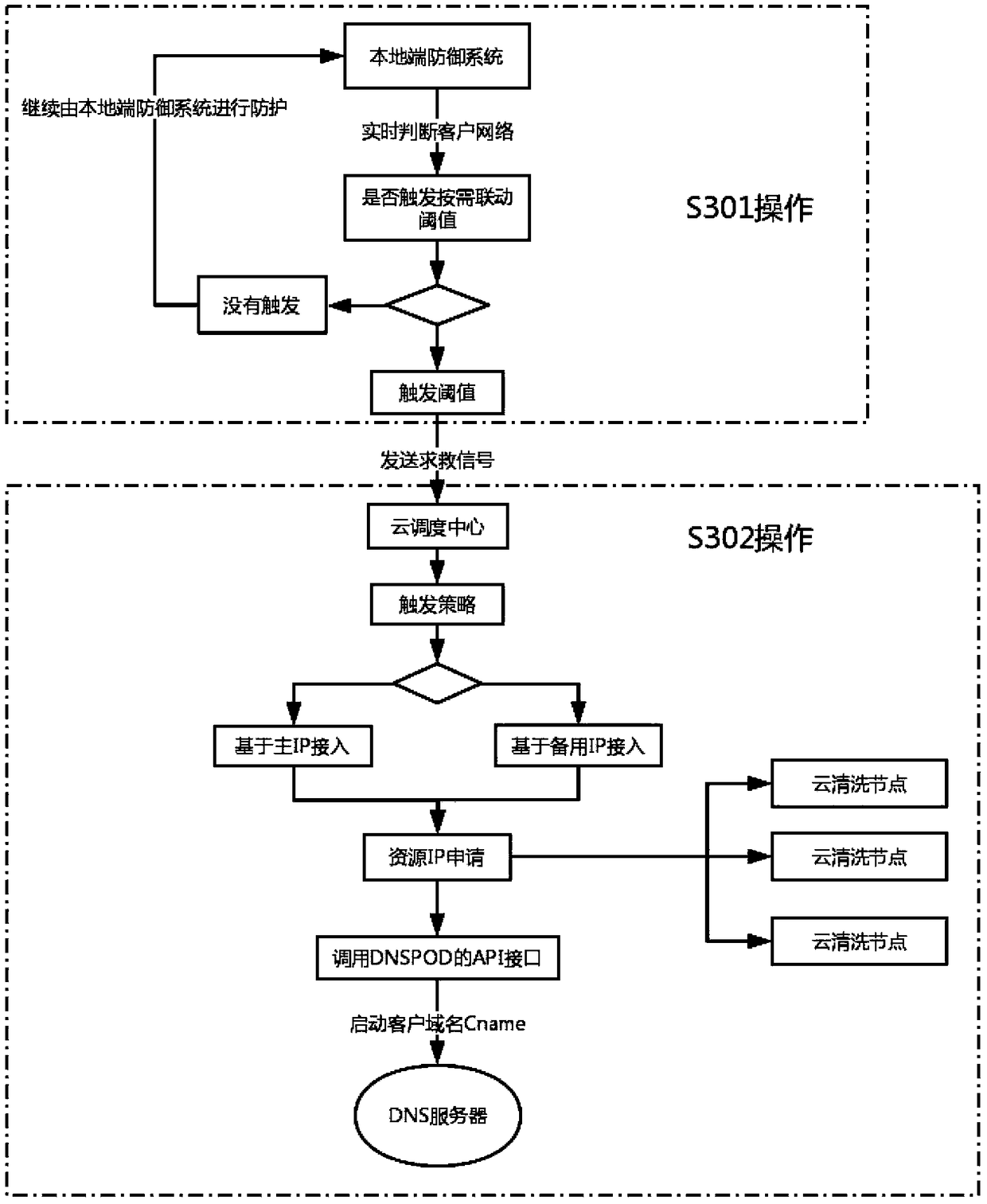
Large-scale DDoS attack detection and defense system based on cloud + end device on-demand linkage mode, and defense method
ActiveCN109450841ABreak through the bottleneck of anti-D defenseComprehensive defense against DDoS attacksTransmissionGranularitySystem protection
The invention relates to the technical field of network cloud security protection, and specifically relates to a large-scale DDoS attack detection and defense system based on a cloud + end device on-demand linkage mode. The system comprises a cloud platform defense system and a local end defense system, the cloud defense system comprises a cloud scheduling center, a cloud cleaning node device anda DNS near-source resolution server, and the local end defense system is used for performing fine-granularity cleaning protection for access service server traffic, performing cooperative processing with the cloud cleaning node device and performing message forwarding. Relative to single local end defense system protection, the large-scale DDoS attack detection and defense system provided by the invention can take advantages of high-capacity cleaning capability of cloud distributed cleaning nodes, and can break anti-D defense bottleneck of local bandwidth limit; and relatively to single continuous access cloud protection, the large-scale DDoS attack detection and defense system provided by the invention can realize more comprehensive defense to DDoS attacks and better cleaning effects through cloud node distributed cleaning and secondary fine filtering of the local end defense system.
Owner:ANHUI ZHONGXIN SOFTWARE
Power grid Web application mimicry defense system
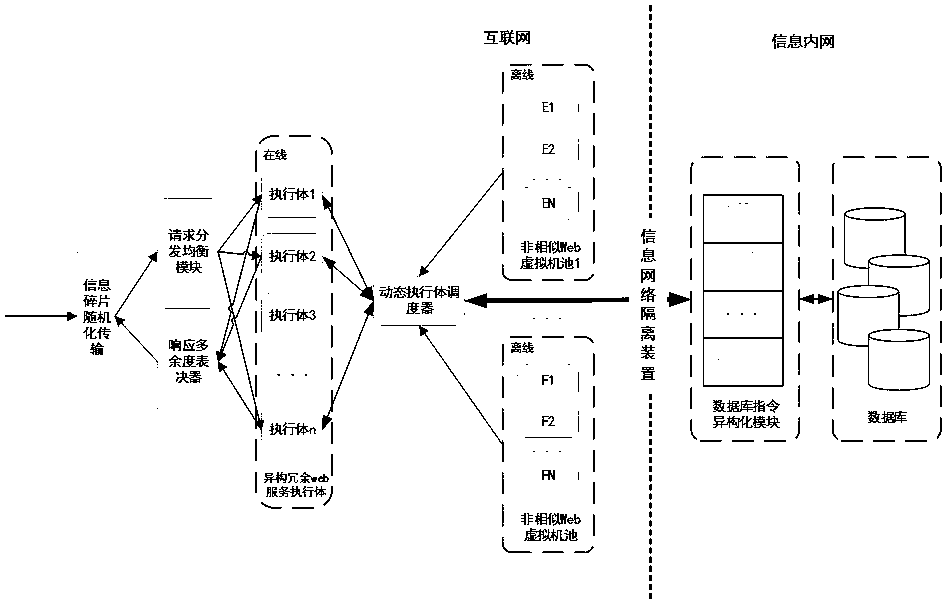
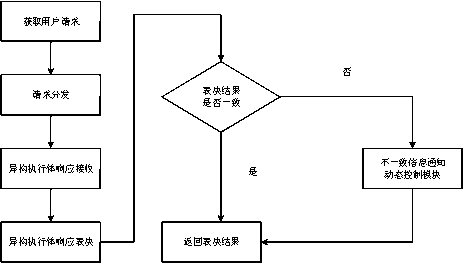
PendingCN111478970APrevent leakageIncrease uncertaintyPlatform integrity maintainanceTransmissionWeb serviceAttack
The invention relates to a power grid Web application mimicry defense system. A heterogeneous virtual Web server pool which is equivalent in function, diversified and dynamic is constructed, technologies such as redundancy voting, dynamic executor scheduling and database instruction isomerization are adopted, an attack chain is blocked, the utilization difficulty of vulnerabilities or backdoors isincreased, and the availability and safety of Web services are guaranteed. A dynamic environment is realized through active change of software and hardware elements of different layers such as a network, a platform, a system, software and an application, and therefore, the dependency condition of the network attack on the determinacy and continuity of the operating environment is destroyed, controllable active defense is realized in the toxic bacteria-carrying software and hardware element environment with the vulnerability and the backdoor, the unknown attack defense problem by using the unknown vulnerability and the unknown backdoor is solved, and the network security of the key Web application system in the power industry is effectively enhanced.
Owner:STATE GRID FUJIAN ELECTRIC POWER CO LTD
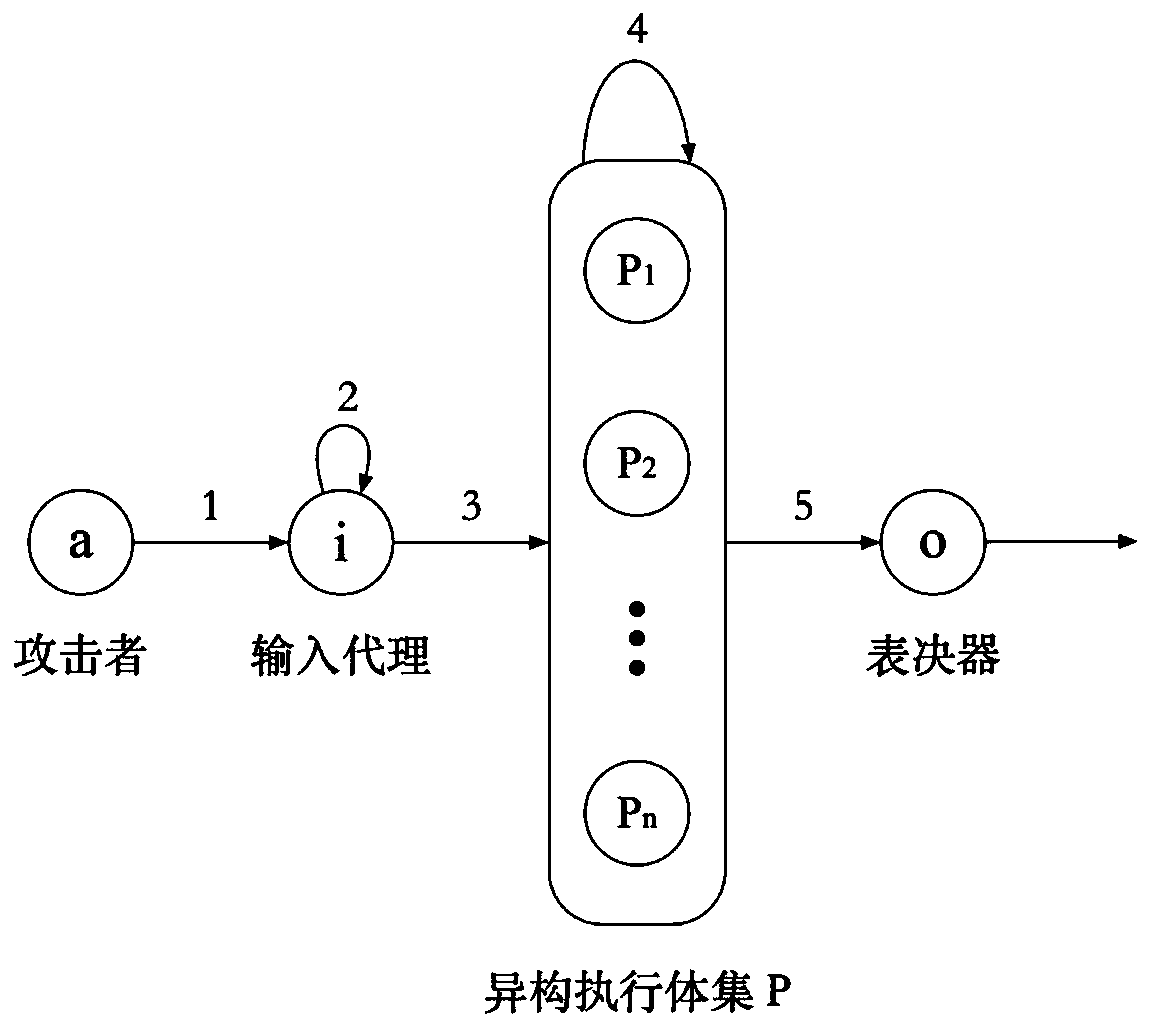
Security analysis method for mimicry defense architecture
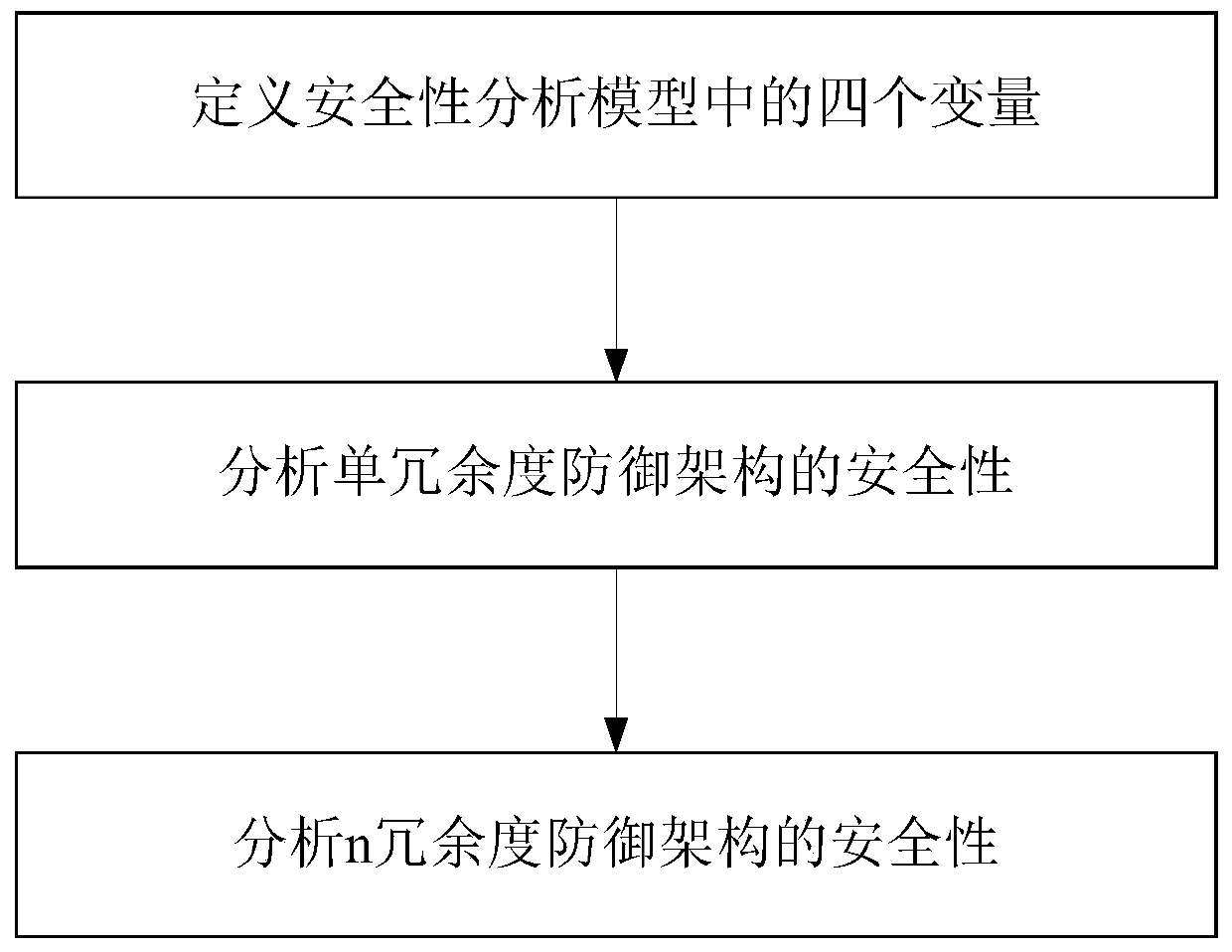
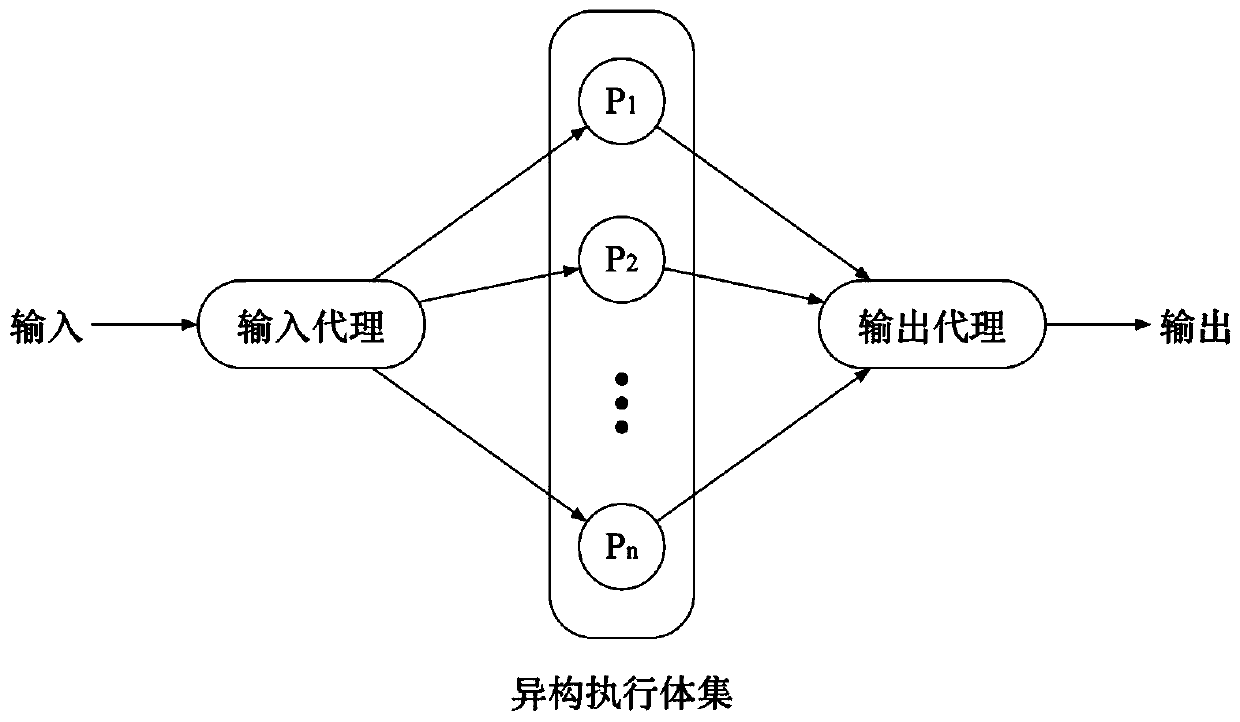
ActiveCN110830462AAnalytical results are reliableAnalysis results are efficientData switching networksSecurity analysisMimicry
The invention discloses a security analysis method for a mimicry defense architecture. The method comprises the following steps: defining the dynamic transformation period of an executor in a securityanalysis model, the time required for successful attack implementation, the probability that the executor shows difference after being attacked, and the probability that an attacker successfully transfers the attack; analyzing the security of the single redundancy defense architecture; obtaining the probability of invading the input proxy component, the probability that the attack continues to stay in the input agent component, the probability that the attack invades into the heterogeneous execution body set from the input agent component, the probability that the attack continues to stay inthe heterogeneous execution body set, the probability that the attack invades into the voter component from the heterogeneous execution body set and the probability that an attacker successfully invades into the voter component from the input agent component are set; and analyzing the security of the n redundancy defense architecture to obtain general values corresponding to the six probability values. According to the method, different parameters are used for analyzing the security defense effectiveness of the mimicry defense system, and a theoretical analysis basis is provided for the security of the mimicry defense model.
Owner:NANJING UNIV OF SCI & TECH
Multi-weapons system
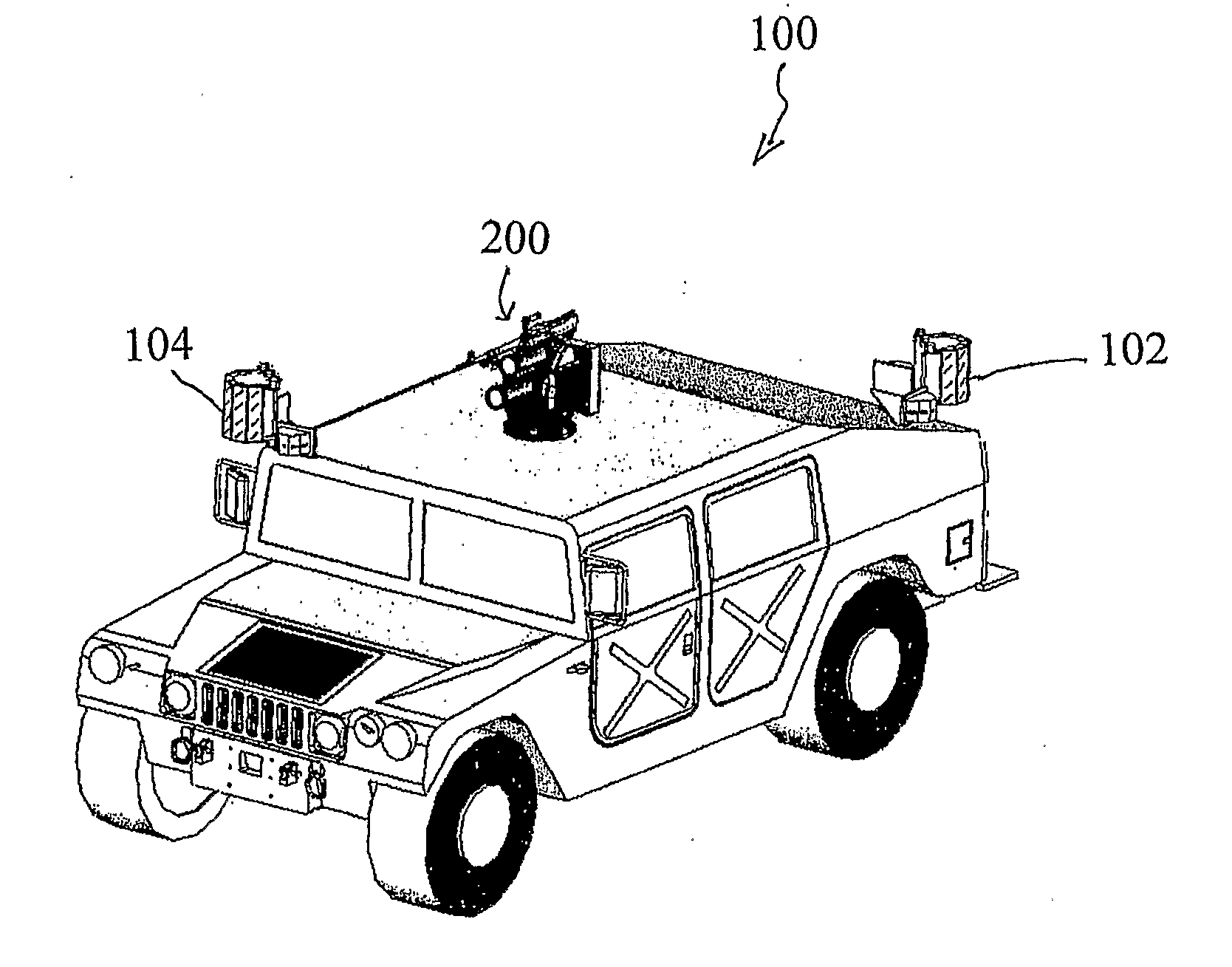
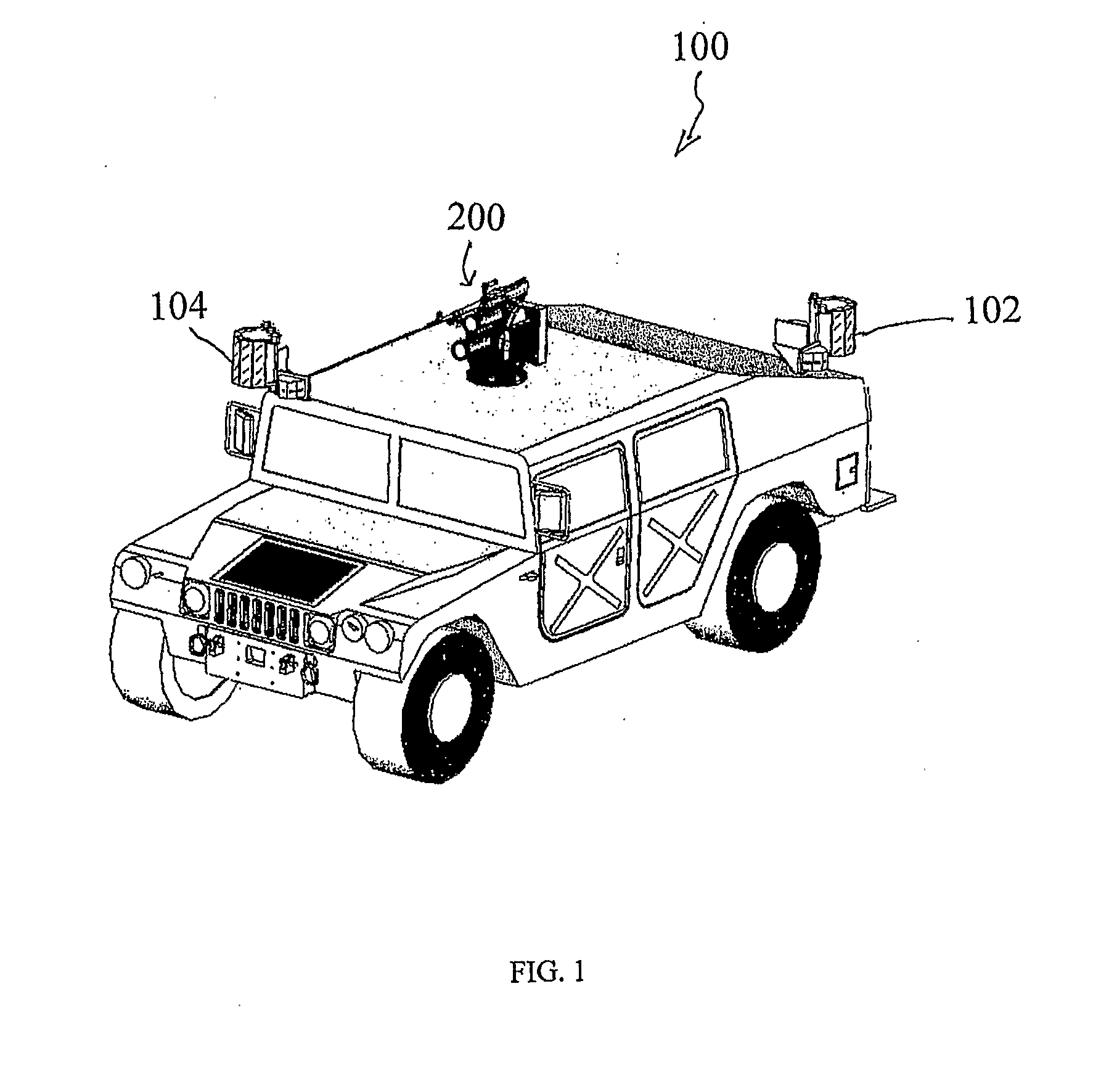
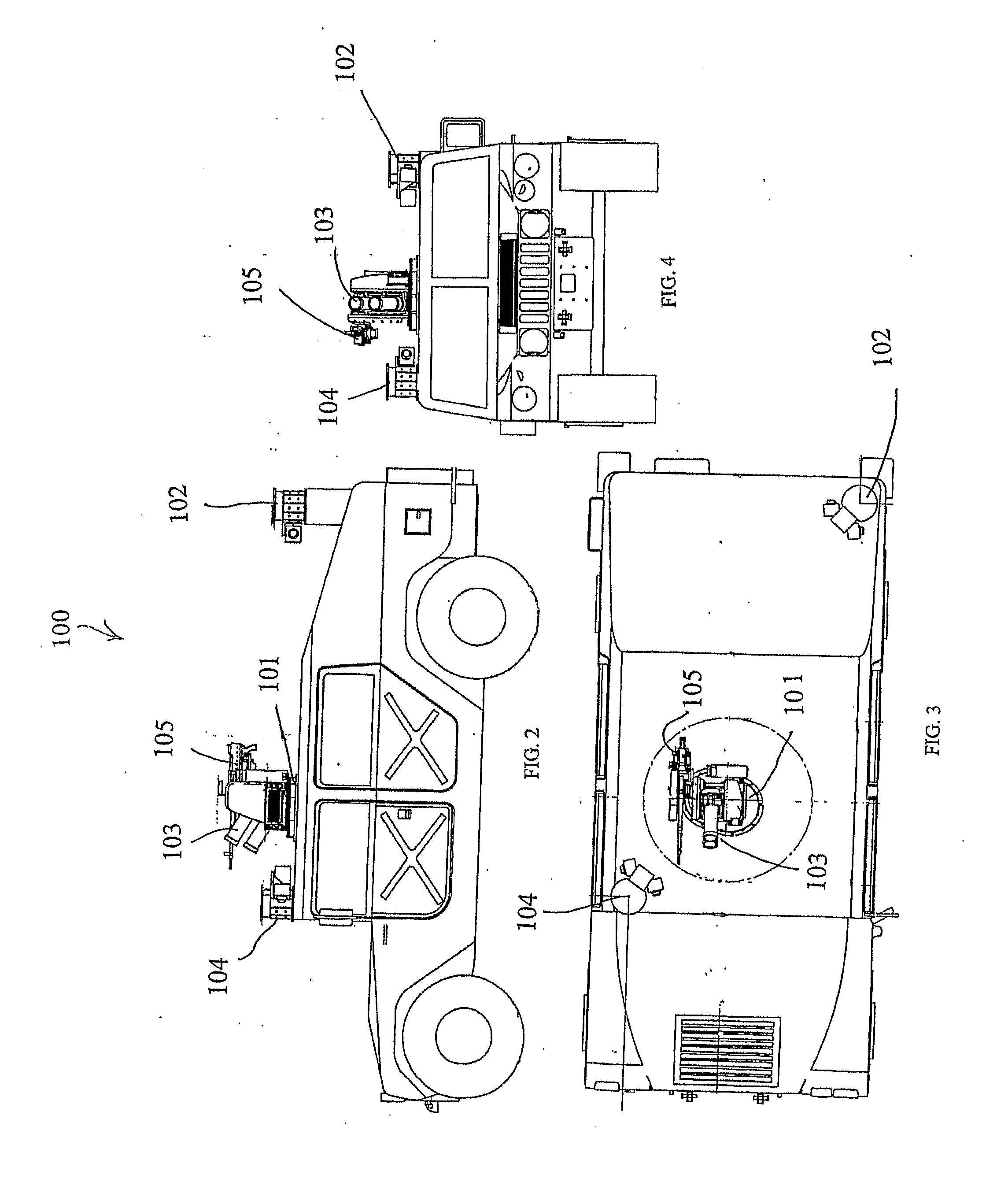
ActiveUS20120247317A1Increase inertiaIncrease speedFiring/trigger mechanismsSighting devicesEngineeringWeapon system
A multi-weapons system comprising: an active defence system (ADS) comprising a mortar launch tube mounted on a support base-plate rotatable 360 degrees; a weapons system comprising a machine gun mounted alongside the active defence system (ADS) on the support base, a motor with mechanism to rotate the support base-plate with the active defence system (ADS) 360 degrees, drive means to adjust the power capacity of the motor between that required for the active defence system and that required for the machine gun, control means to rotate and adjust the elevation of the launch tube and adjust the directional movement of the machine gun, computer and electronic means to automatically rotate and fire the active defence system display and control means to manually operate the machine gun, control means to override the manual operation of the machine gun and prevent its firing when the active defence system is automatically activated.
Owner:IMI SYST LTD
Plant growth nutrient solution and its preparation method
InactiveCN1762922AReduce active oxygen contentToxic reductionFertilisers by pryogenic processesOrganic fertilisersAntioxidant capacityFruit tree
The present invention discloses one kind of plant growth nutrient liquid and its preparation process. During growth of plant, cell and tissue will produce active oxygen and the active oxygen should be eliminated timely to avoid plant presenility, slow growth or death. The enzymatic defense system protecting enzyme can eliminating active oxygen to promote plant growth, and the present invention compounds the plant growth nutrient liquid with SOD and other nutritious matters. The plant growth nutrient liquid has powerful antioxidant capacity and can lower active oxygen content in crop to reduce harm of active oxygen on crop. The present invention is used in tobacco, cotton, fruit tree, vegetable, etc. to reach the effects of raising yield and quality.
Owner:庄义达
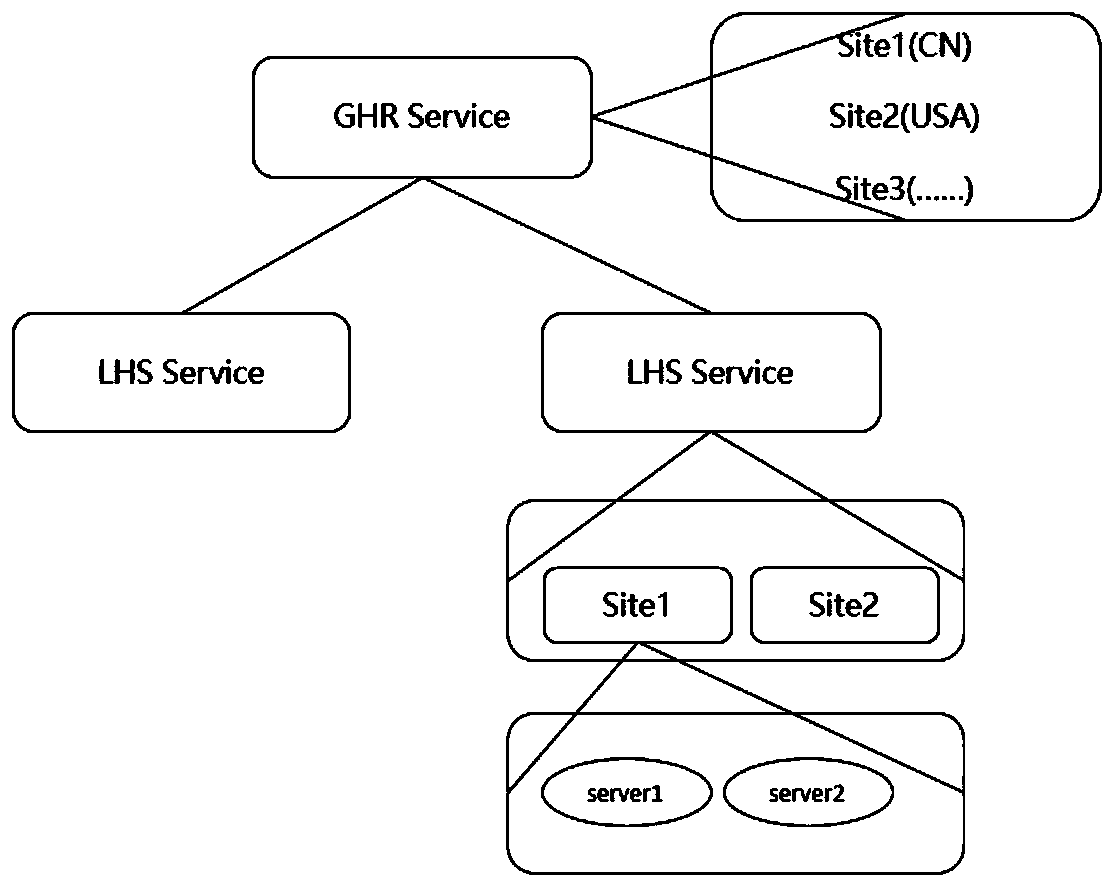
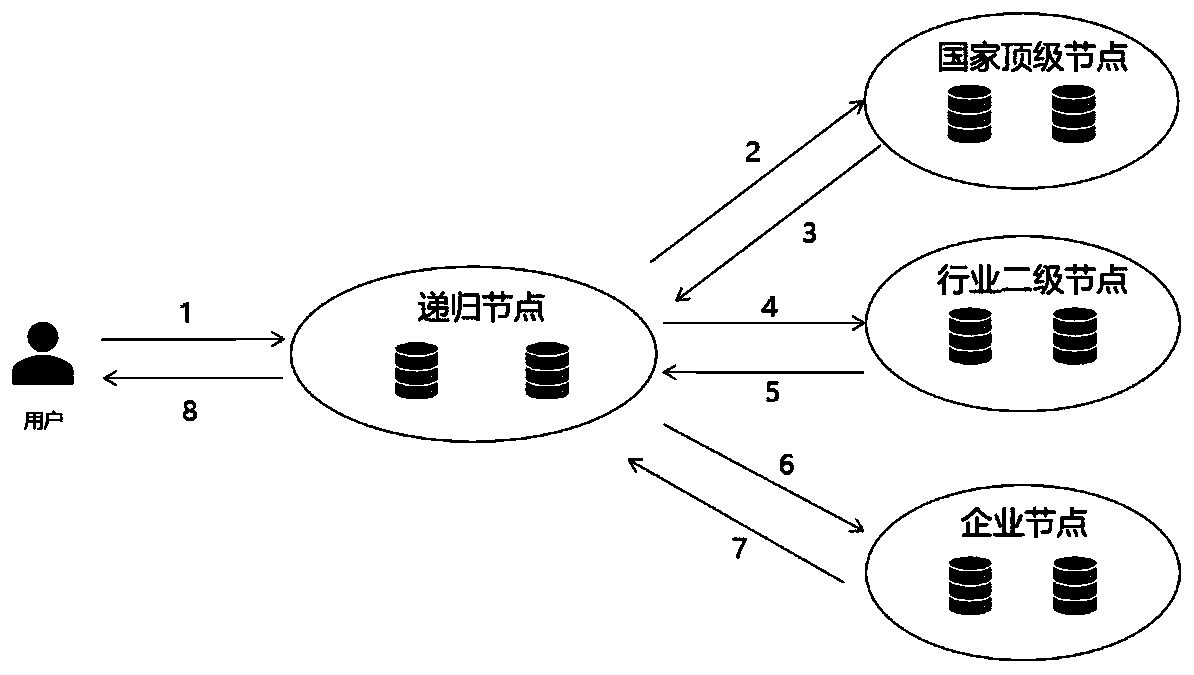
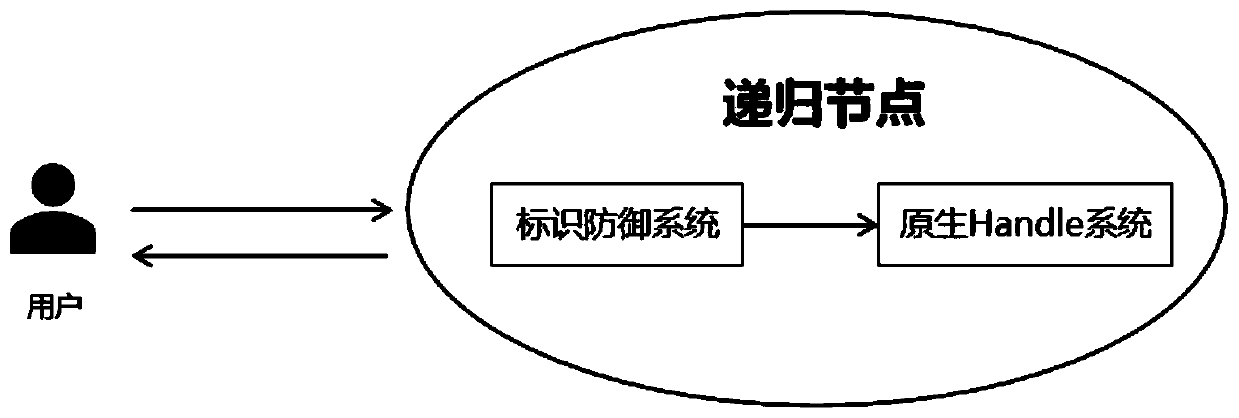
Malicious identifier defense method and system based on Handle system
ActiveCN111200605AImprove the quality of analysis servicesTransmissionQuality of serviceInternet privacy
The invention discloses a malicious identifier defense method and system based on a Handle system, and aims at solving the problem that an existing Handle native system of a recursive node cannot normally respond to a user request under the condition of facing a large-scale sub-deployment denial of service attack. The identifier defense system is added at the entrance of the native Handle system,and malicious access identifiers are identified in advance, so that the aims of defending malicious identifier attacks, normally responding to a request of a user and improving the analysis service quality are fulfilled.
Owner:PURPLE MOUNTAIN LAB
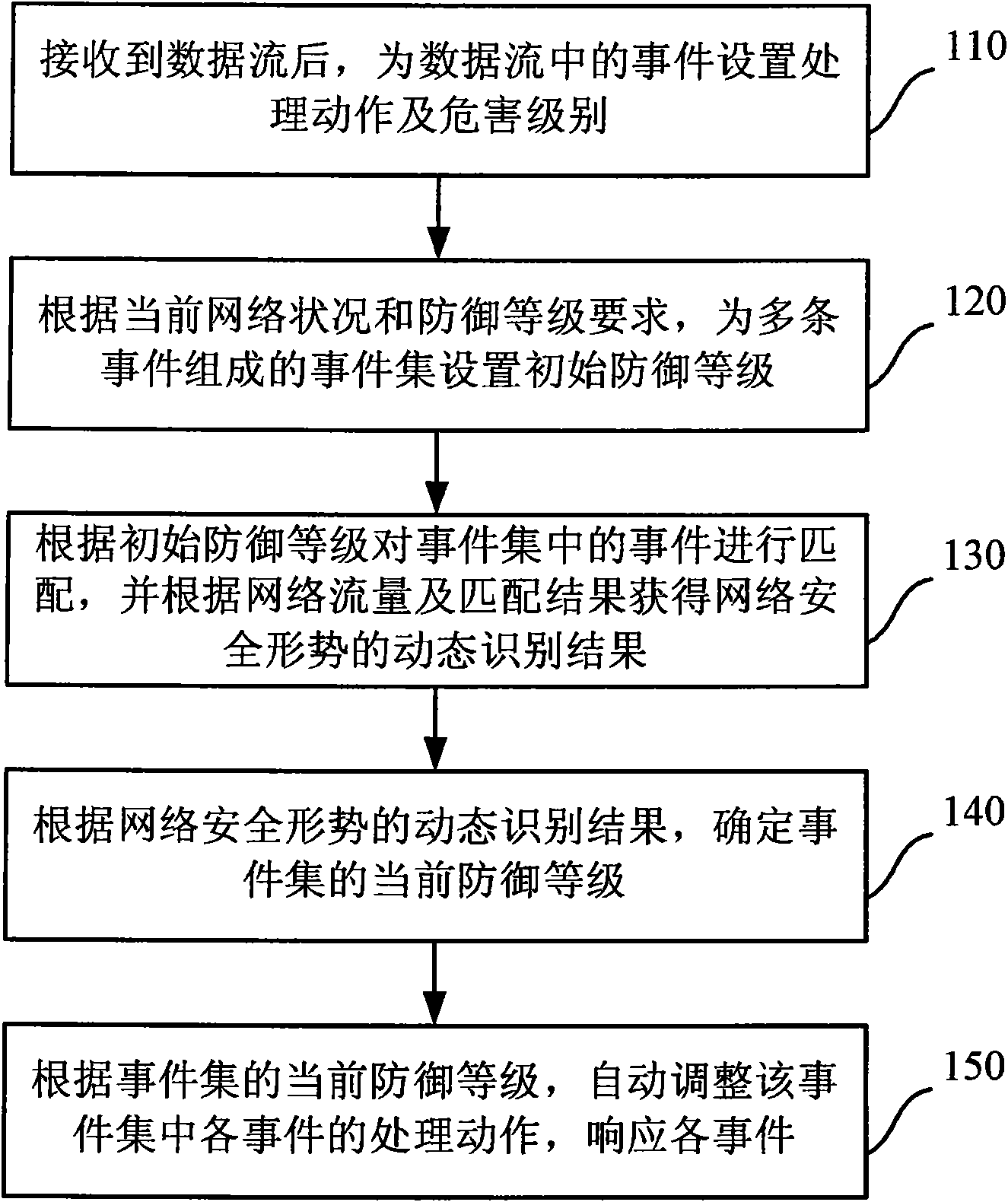
Intrusion defence system having active defence capability and method thereof
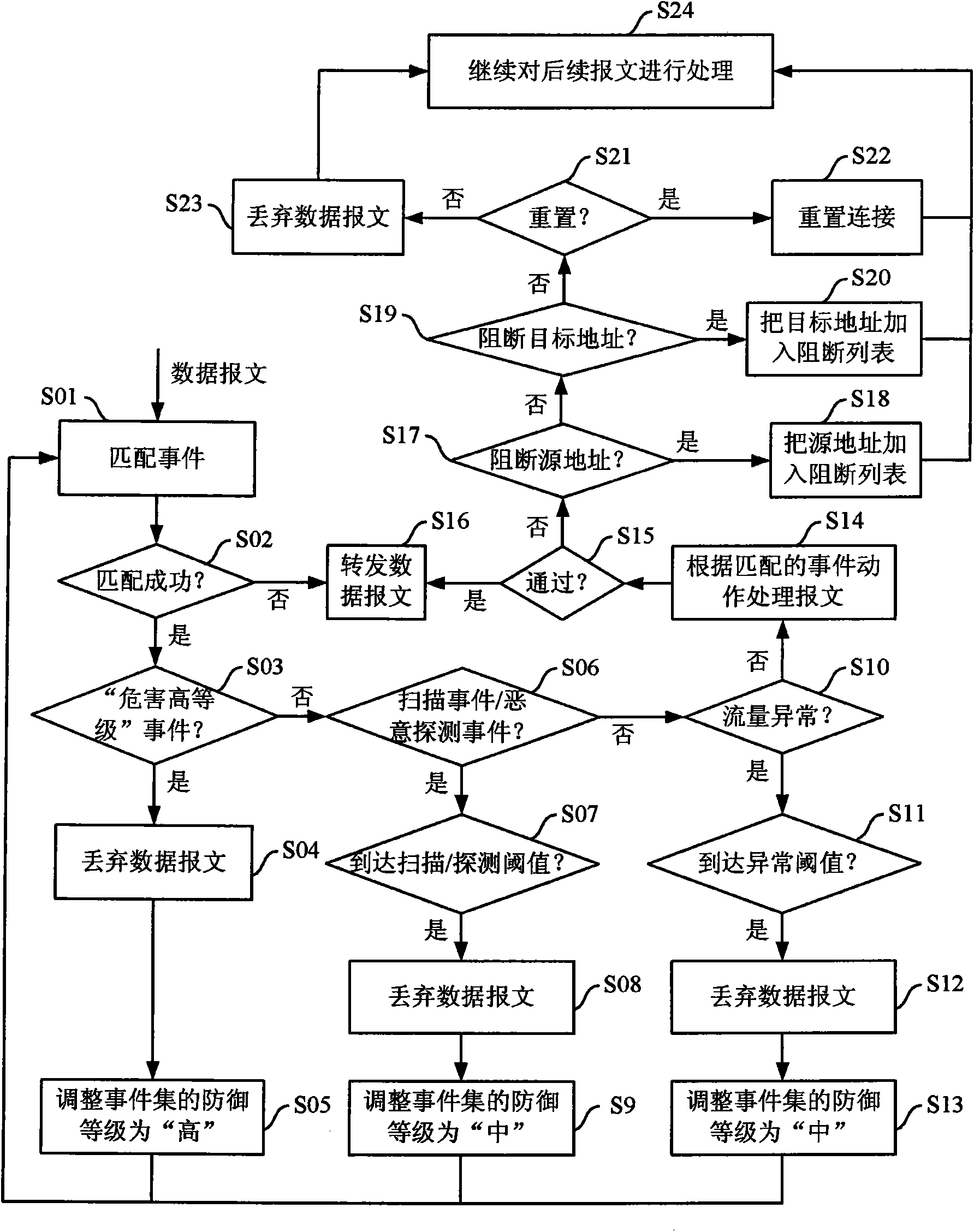
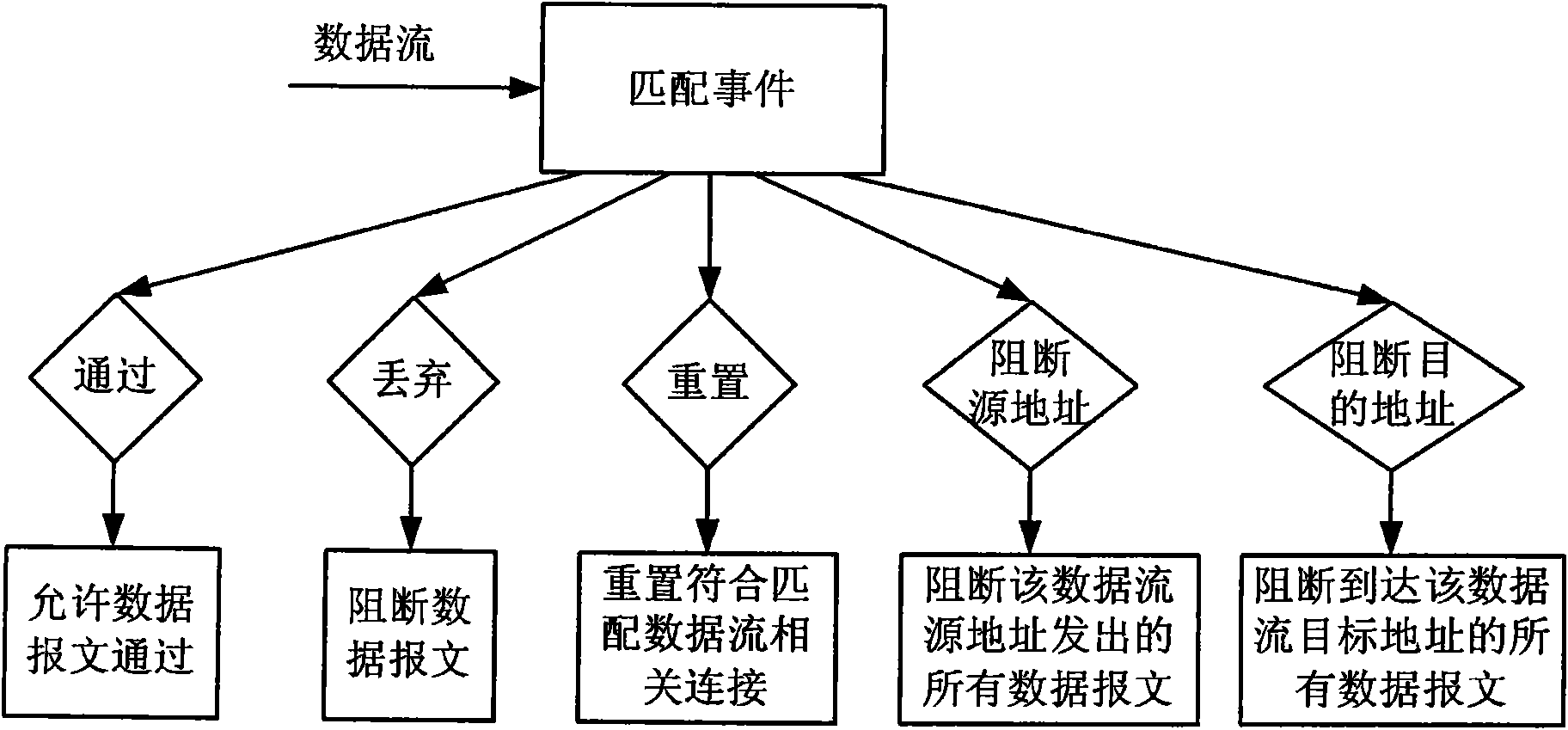
InactiveCN101808078AAutomatically adjust the defense levelAvoid attackData switching networksData streamNetwork conditions
The invention discloses an intrusion defense system having an active defense capability and a method thereof to actively defend security threats in a network. The method comprises the following steps: after receiving a data stream, setting a processing operation for an event in the data stream; setting an initial defense level for an event set consisting of multiple events based on the current network condition and the defense level requirements; matching the event in the event set based on the initial defense level, and obtaining a dynamic identification result with respect to network security situation based on a network flow and a matching result; determining the current defense level of the event set based on the initial defense level and the dynamic identification result; determiningthe current defense level of the event set based on the dynamic identification result; and automatically adjusting the processing operation of each event in the event set based on the current defenselevel, and responding to each event. The defense level can be automatically adjusted so as to actively prevent the further generation of attacks by using the various implementation manners of the invention.
Owner:BEIJING VENUS INFORMATION TECH +1
Cyberspace security situation awareness detection and analysis system and method
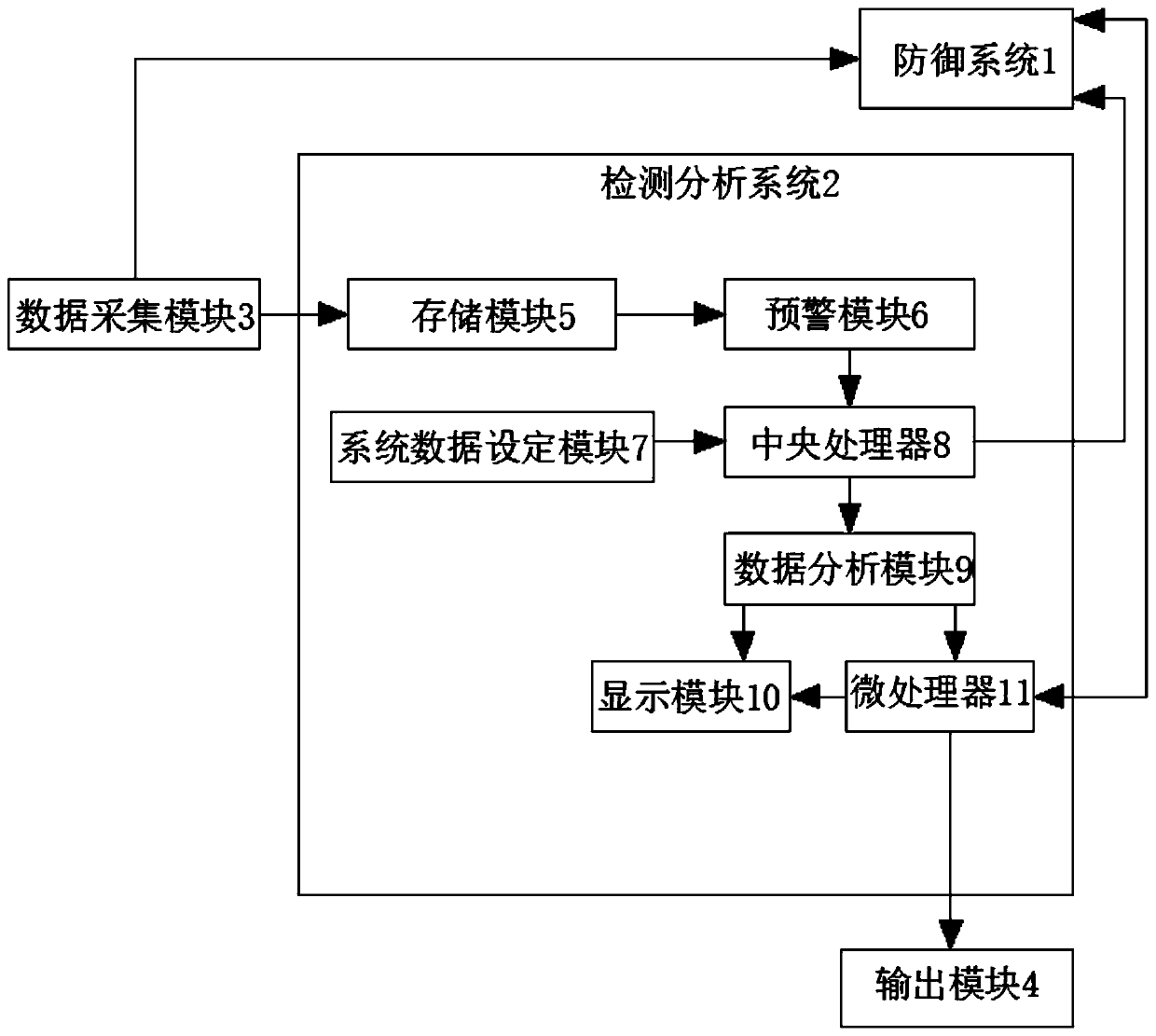
The invention discloses a cyberspace security situation awareness detection and analysis system and method. The invention discloses a cyberspace security situation awareness detection and analysis system and method, and relates to the field of network detection, the cyberspace security situation awareness detection and analysis system comprises a defense system, a detection and analysis system, adata acquisition module and an output module, and the detection and analysis system comprises a storage module, an early warning module, a system data setting module, a central processor, a data analysis module, a display module and a microprocessor. According to the invention, the defense system, the data analysis module, the display module, the visualization unit and the data calculation unit are arranged; the problems that an existing cyberspace security situation awareness detection and analysis system is poor in cyberspace security continuous monitoring capability; and when various attackthreats and anomalies are found, the threat investigation, analysis and visualization capabilities, and the capability of quickly judging the influence range, attack path, purpose and means related to the threats need to be further developed.
Owner:HUIZHOU UNIV
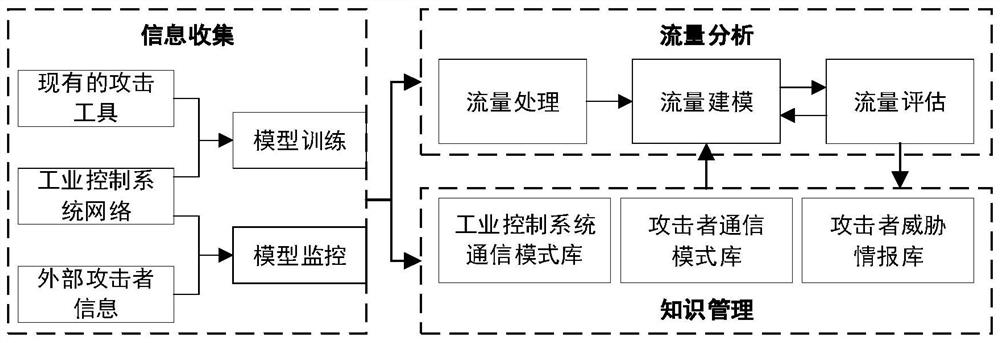
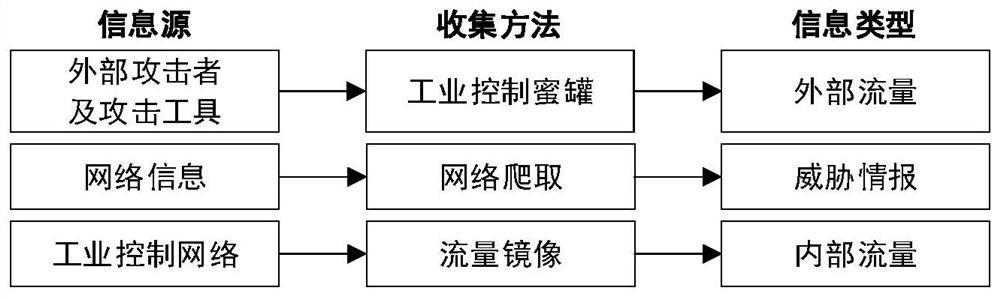
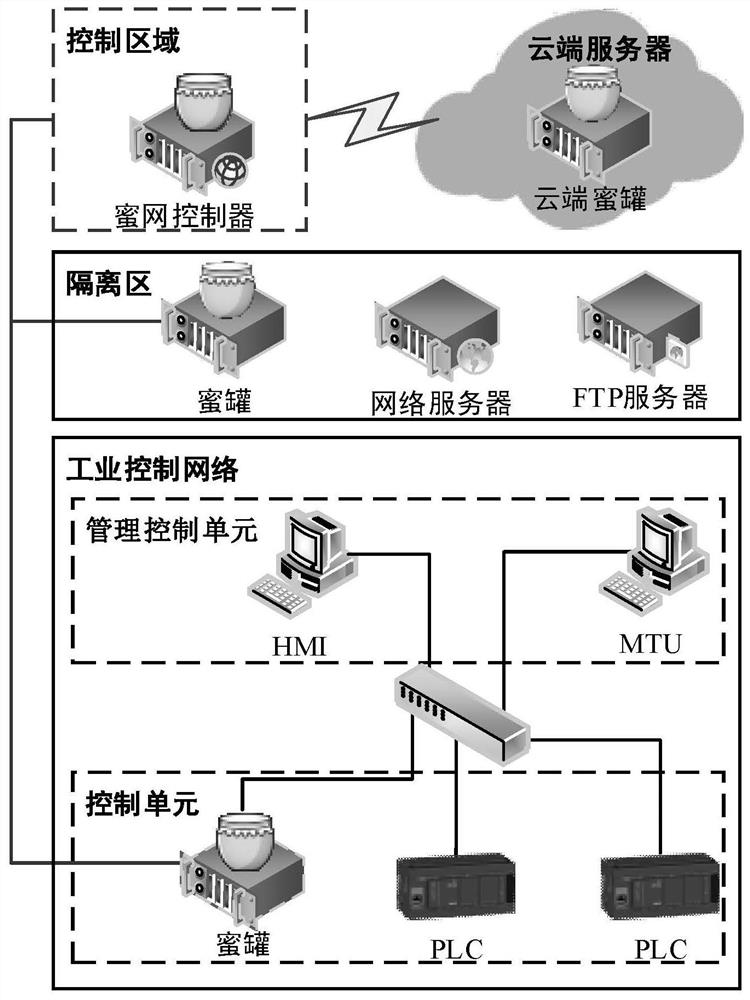
Industrial control network active defense system based on honeynet and method thereof
ActiveCN111641634AImprove scalabilityVerify validityCharacter and pattern recognitionTransmissionInternet trafficAttack
The invention discloses an industrial control network active defense system based on a honeynet and a method thereof. The system comprises an information collection assembly, a flow analysis assemblyand a knowledge management assembly. The information collection assembly comprises an industrial control system honeynet, a web crawler and a flow mirror image; the flow analysis assembly comprises aflow processing module, a flow modeling module and a flow evaluation module; the knowledge management component manages all information of an industrial control system network through a knowledge graph, and is divided into an internal network knowledge graph and an external network knowledge graph which are stored in a graph database. The honeynet-based industrial control network active defense system and the method thereof provided by the invention not only can accurately detect the abnormal condition in the network flow of the industrial control system, but also can evaluate the threat degree of the industrial control system and find the attack organization associated with the industrial control system.
Owner:NORTHEASTERN UNIV
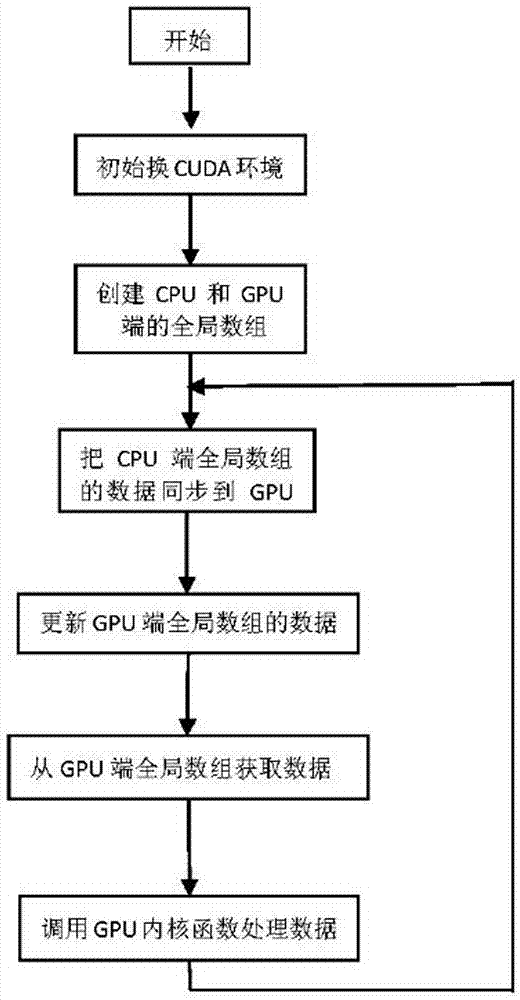
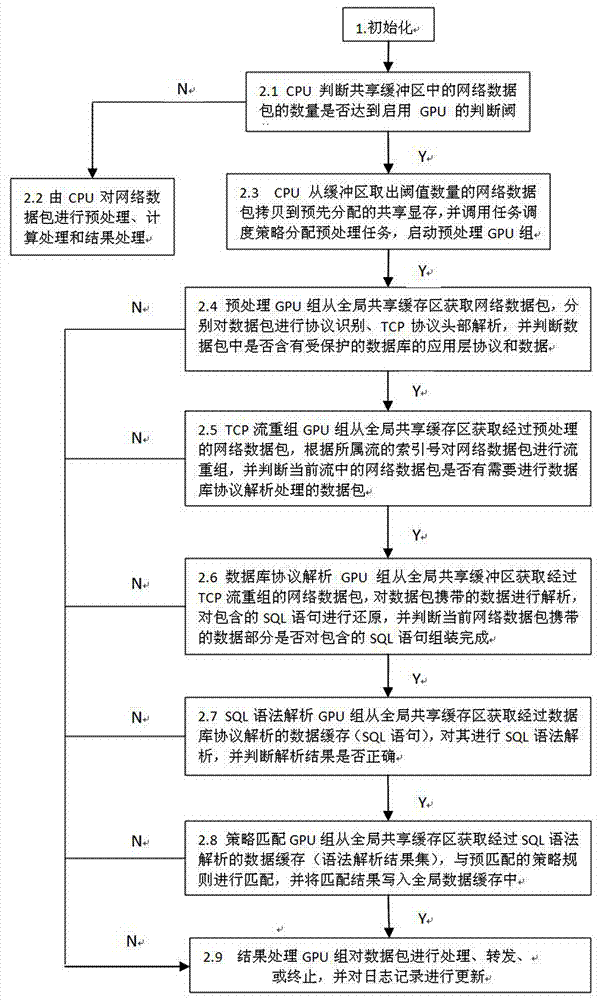
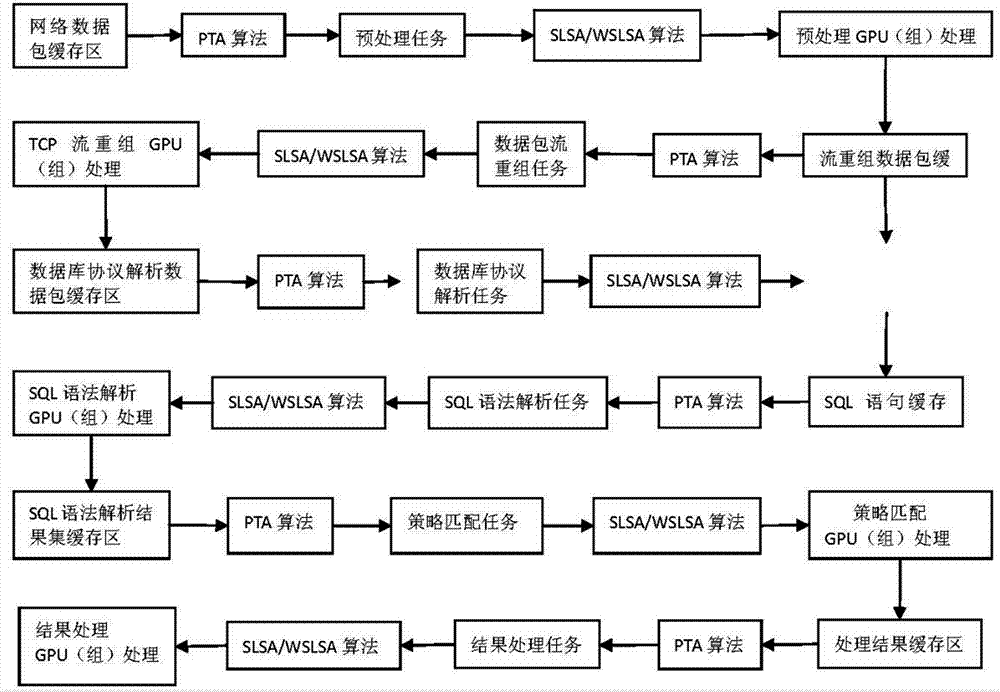
Method for active database defence for multi-GPU parallel processing
ActiveCN107102897ASolve the speed problemLower latencyResource allocationVideo memoryArray data structure
The invention discloses a method for active database defence for multi-GPU parallel processing. The method is characterized in that video memories of all the GPUs are virtualized into a shared video memory and established into a global array of a GPU side; a shared cache area is set in CPU; when a network data packet in the shared cache area reaches a judgment threshold for starting GPU processing, a data packet of the shared cache area will be synchronized to the global array of the GPU side; and then, the CPU will dispatch kernel processing functions of the multiple GPUs to process the network data packet. According to the invention, multi-GPU acceleration processing is adopted when the database active defence system faces a high parallel network flow rate, so that overall performance can be improved, and problems such as high rate and low delay faced by the CPU at the moment can be solved.
Owner:深圳市知穹科技有限公司
Set defence means
InactiveUS20040237762A1Reduce disadvantagesEasily concealedDefence devicesLand minesLand mineProjectile
A defence system for a land area, intended as an alternative to land mines. The system includes sensors for detecting intrusions in the area, a weapon having multiple barrels and multiple projectiles ready for firing, and a controller that receives signals from the sensors to fire the weapon. The controller preferably requires intervention of an operator in order to trigger the weapon. The weapon may contain a range of projectiles for different purposes.
Owner:METAL STORM LTD
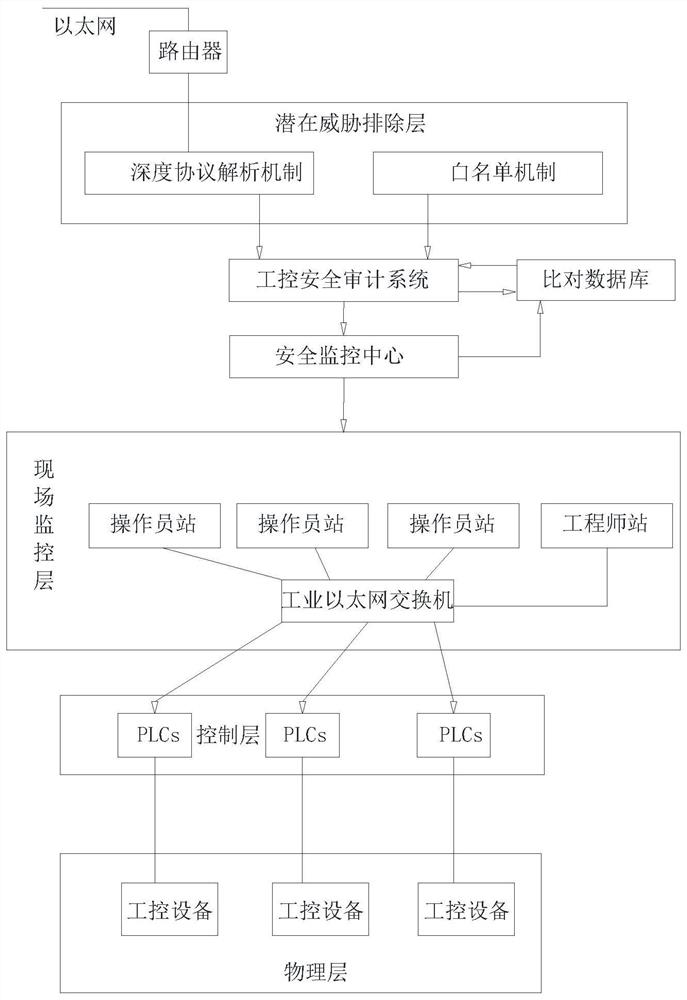
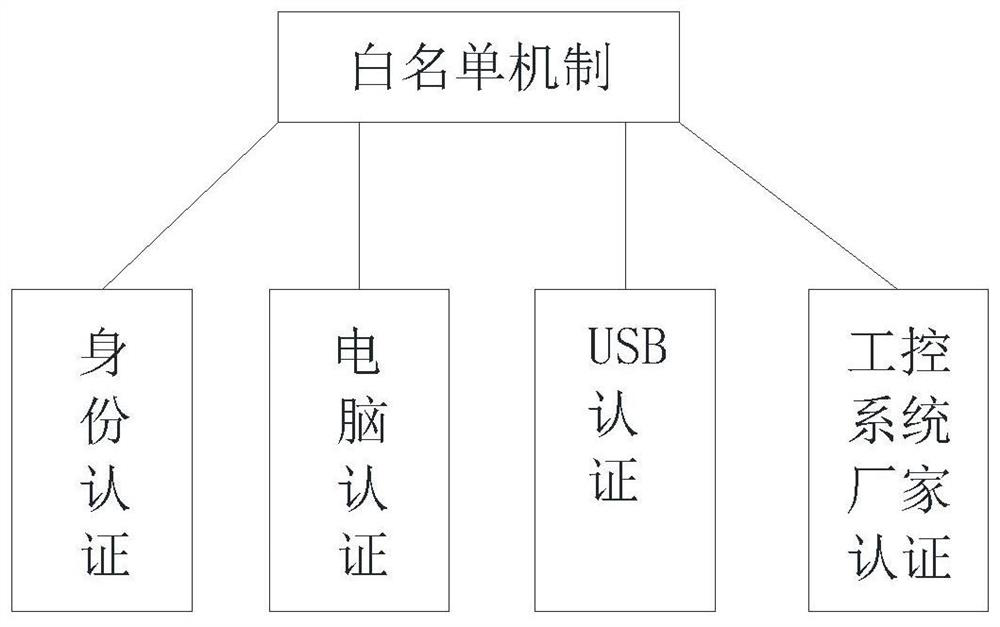
Industrial control security defense system
ActiveCN112799358AOccupies less than BillyImprove the protective effectTotal factory controlProgramme total factory controlBehavior controlControl layer
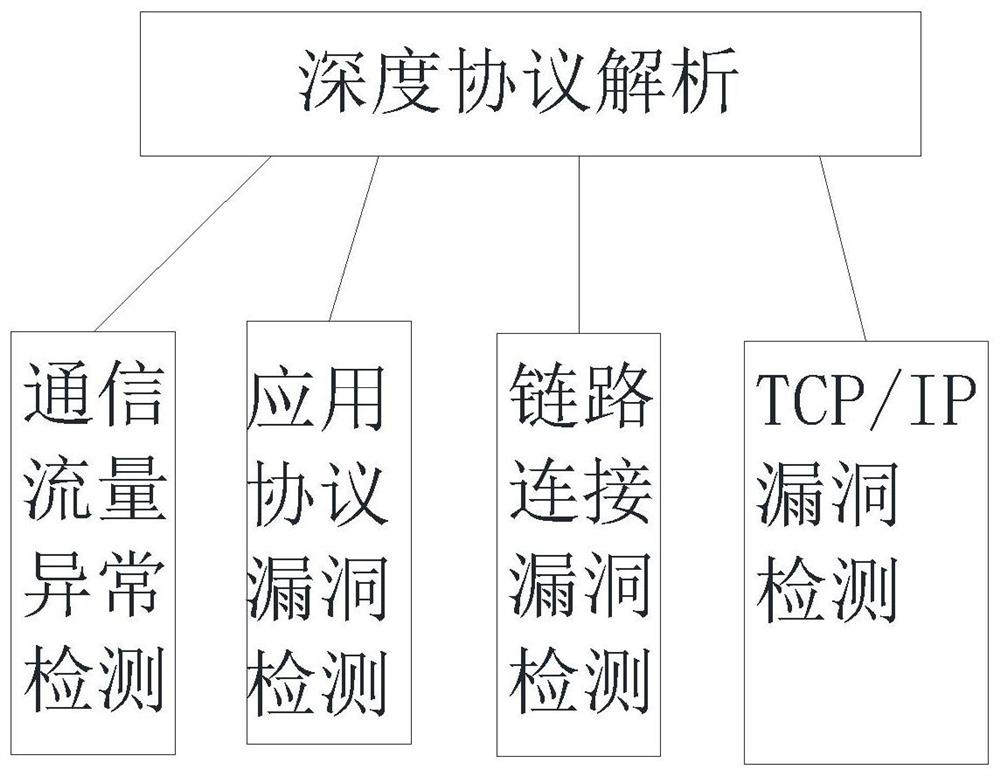
The invention discloses an industrial control security defense system which comprises a potential threat exclusion layer, an industrial control security audit system, a monitoring center, a field monitoring layer, a control layer and a physical layer. The potential threat elimination layer comprises a deep protocol analysis mechanism and a white list mechanism; the field monitoring layer performs data exchange and behavior control on the control layer and the physical layer through an industrial Ethernet; the industrial control security auditing system can analyze and identify illegal operation, abnormal events and external attacks in an industrial control network from multiple angles and give an alarm in real time; identity recognition is carried out through multiple means, system operation authority can be limited, override operation and malicious operation are avoided, it is avoided that external equipment carries viruses to affect system safety, meanwhile, exclusive detection can be carried out on common attack means, and the operation resource occupancy is small. The alarm response time of the whole system can be prolonged through unified monitoring management of the monitoring center, and the accident handling speed is increased.
Owner:上海磐御网络科技有限公司
Hardware-assisted code-reuse-attack-resistant defence system and method
ActiveCN107590385AEliminate security concernsImprove securityInternal/peripheral component protectionPlatform integrity maintainanceCode moduleChosen-plaintext attack
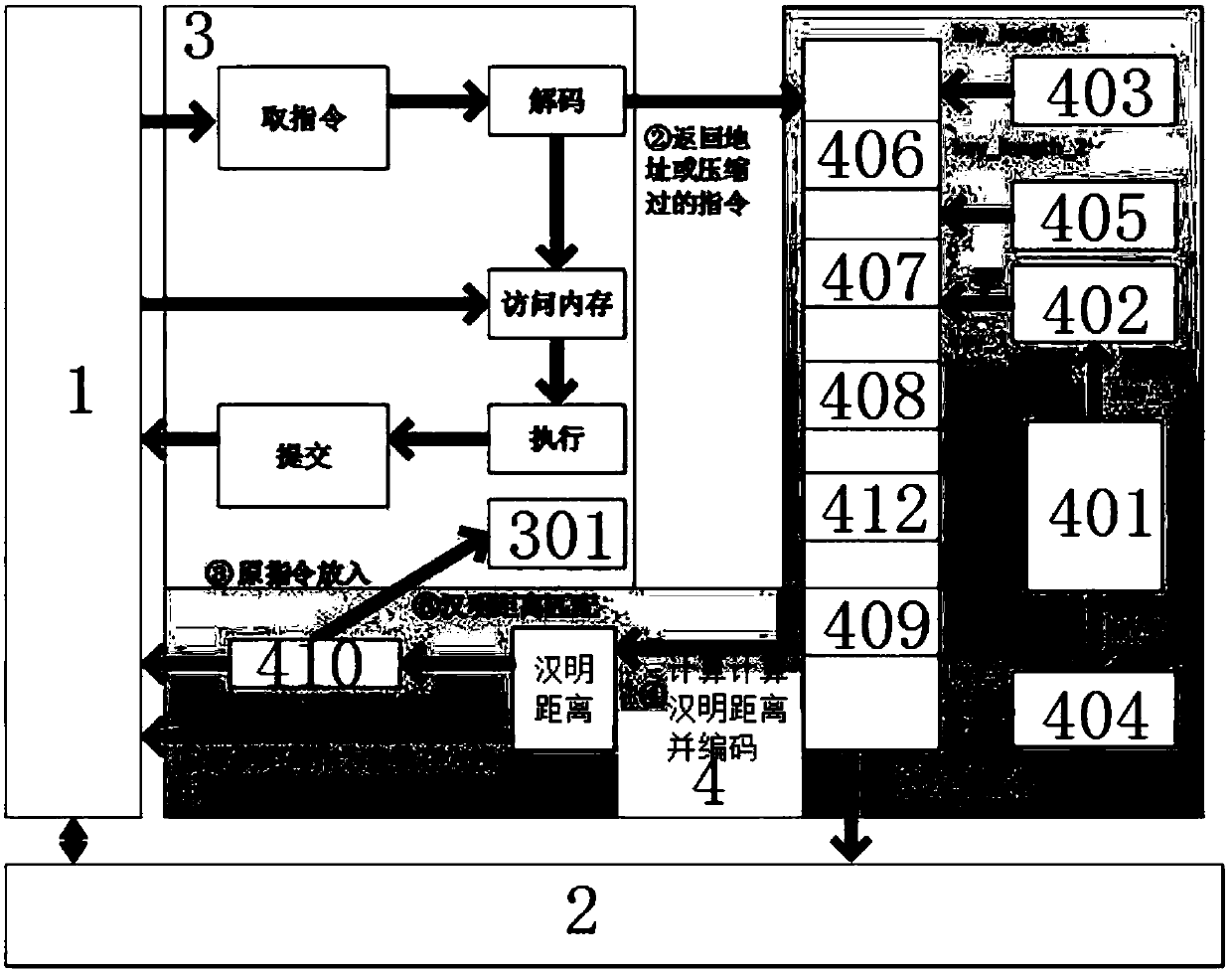
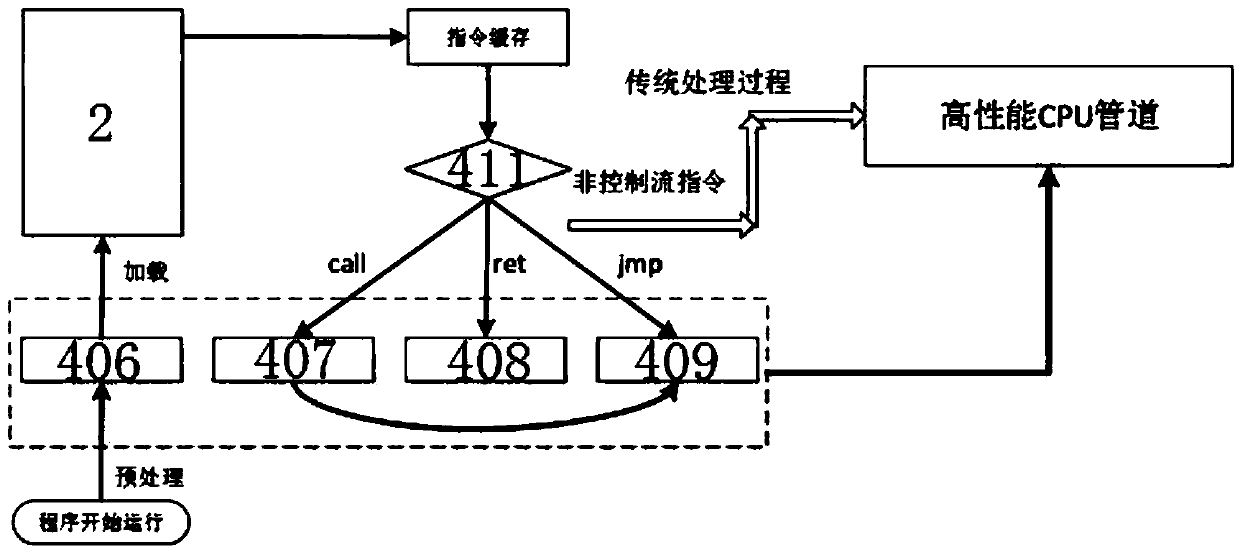
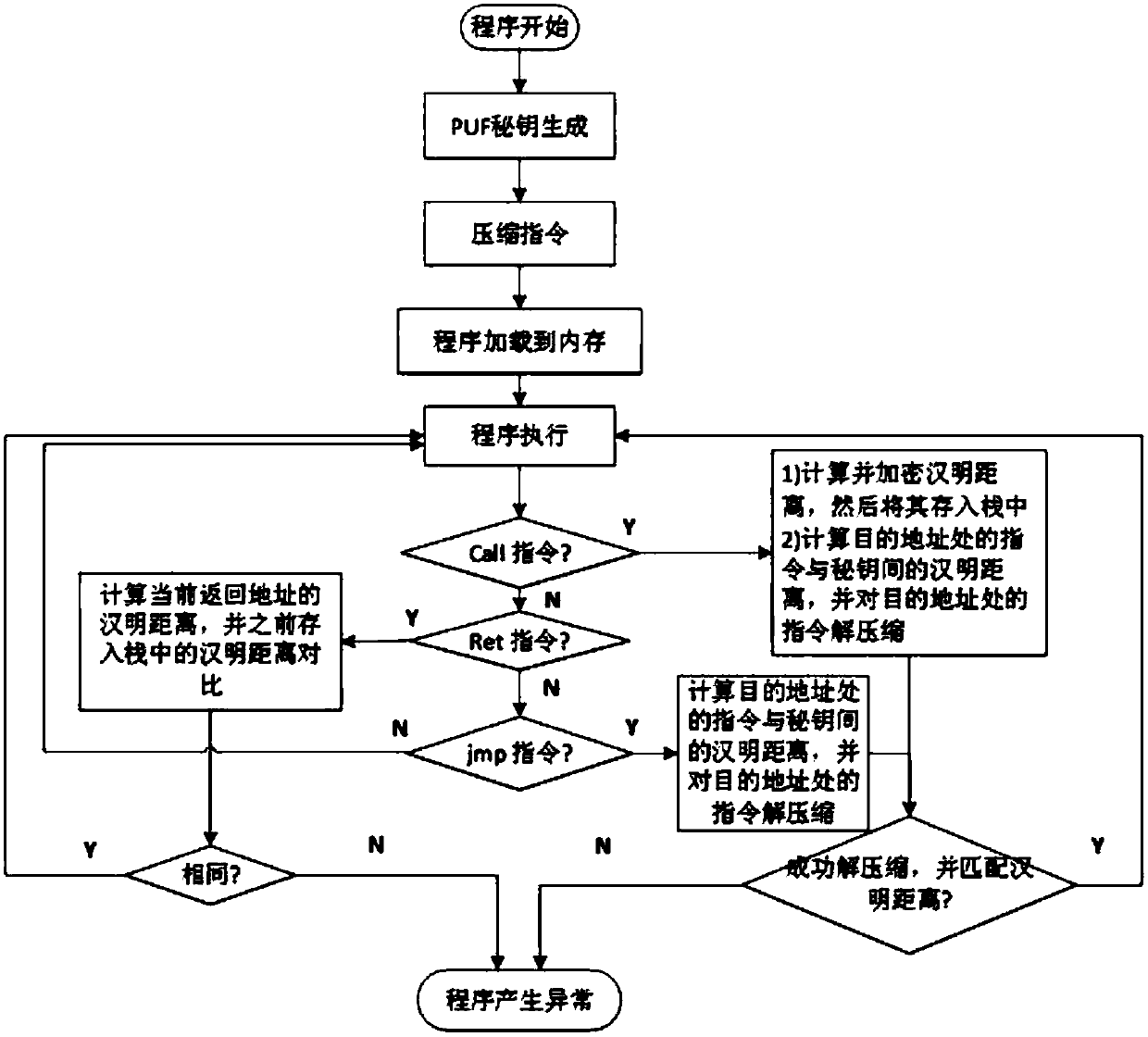
The invention discloses a hardware-assisted code-reuse-attack-resistant defence system and method, wherein the defence system comprises a pre-processing module, a cache, a memory, a CPU and an encryption and decryption architecture; and the encryption and decryption architecture comprises a PUF module, a first key register, a first length register, a second key register, a second length register,a PUF encryption module, a Hamming distance coding module, a Hamming distance decoding module, a decompression module and a judgment module. According to the hardware-assisted code-reuse-attack-resistant defence system and method disclosed by the invention, the ROP attack is resisted by utilizing and matching the Hamming distance between the return address of a program and a key; because the Hamming distance is coded, the security problem that an attacker can guess a key generated by the PUF module in a plaintext attack manner in the past work can be eliminated; therefore, the security is high; simultaneously, an instruction-level data hiding technology is applied to JOP attack defence; therefore, the performance cost is low; an instruction set does not need to be changed; the universalityis good; and the security is high.
Owner:HUNAN UNIV
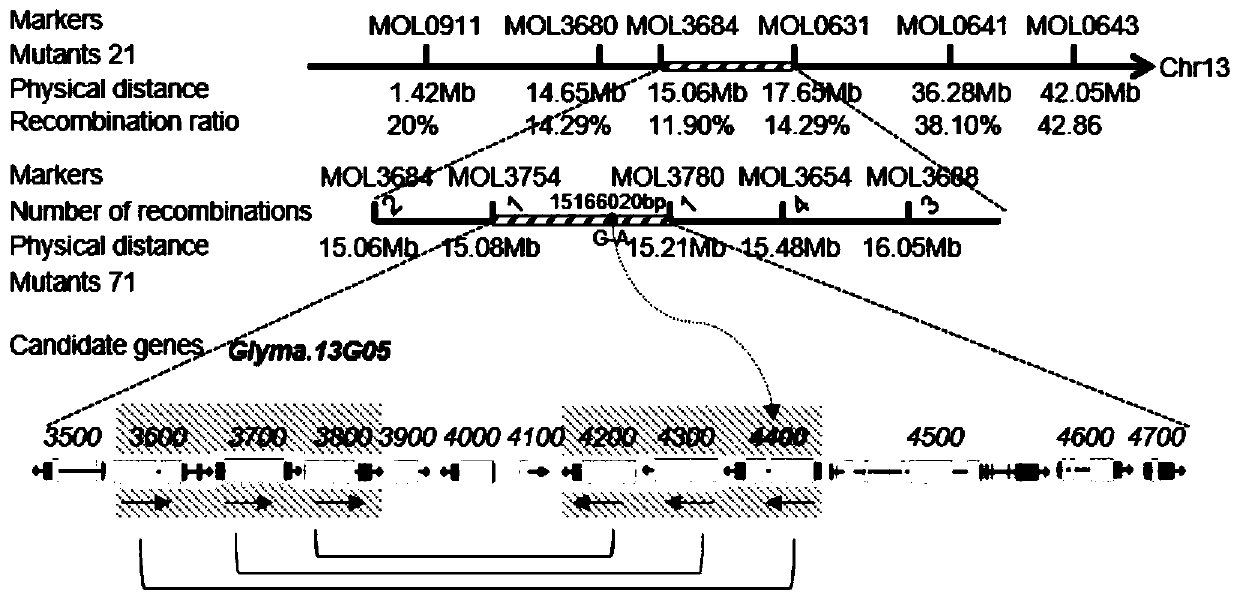
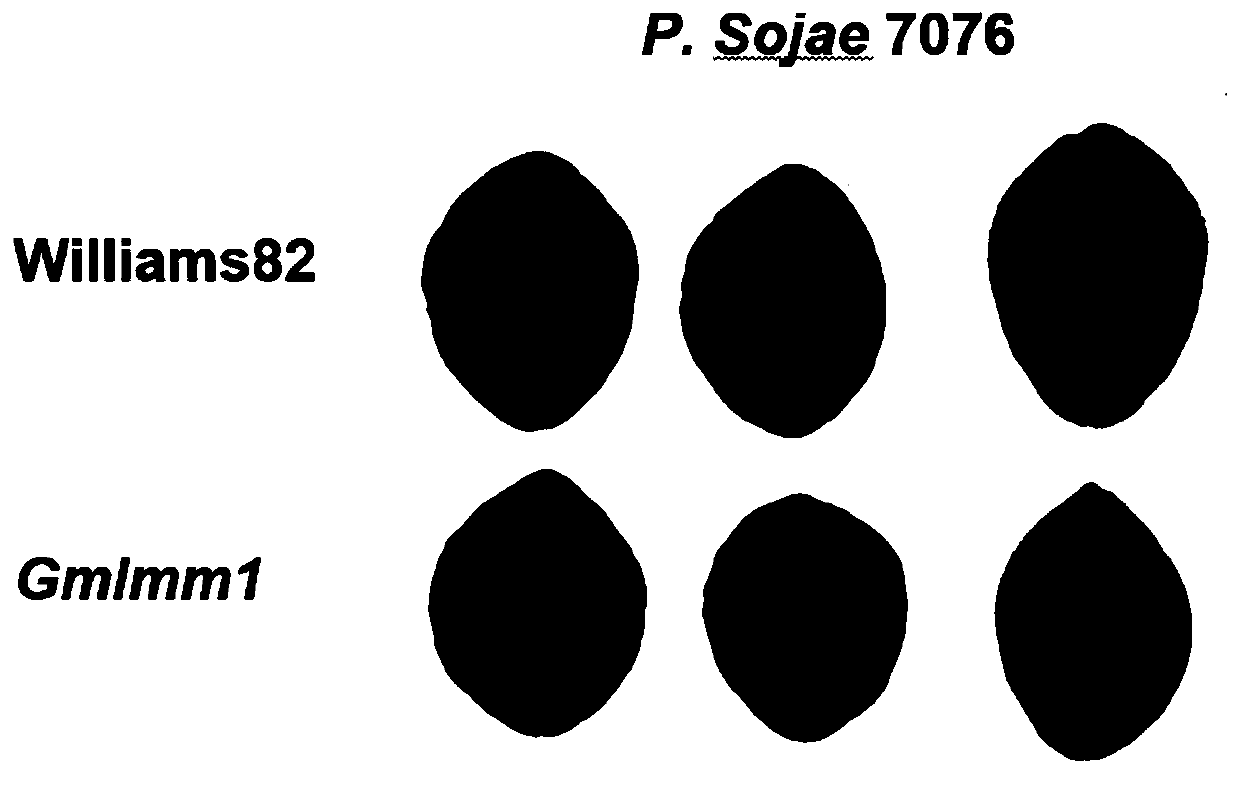
Application of gene GmLMM1 related to soybean phytophthora resistance
ActiveCN110713528AHigh expressionSuppress deathPlant peptidesGenetic engineeringBiotechnologyResistant genes
The invention relates to the technical field of plant genetic engineering, and specifically relates to application of a gene GmLMM1 related to soybean phytophthora resistance. According to the presentinvention, the gene GmLMM1 involved in the regulation of soybean cell death, immune response and phytophthora resistance is cloned in soybean. PTI immune response and phytophthora resistance of plants can be negatively regulated by the GmLMM1 gene; and by reducing the expression of the GmLMM1 gene, PTI immune response of plant can be effectively enhanced, and phytophthora resistance of plants canbe increased. The clone and functional discovery of the GmLMM1 gene provide important gene foundations and theoretical support for the related mechanisms research of phytophthora resistance, providevaluable gene resources for advancing the research and application of plant defense systems and for breeding new soybean varieties with high disease resistance, and has important application value ingenetic engineering breeding of soybean disease resistance.
Owner:NORTHEAST INST OF GEOGRAPHY & AGRIECOLOGY C A S
Window defence system
InactiveCN1359091APrevent intrusionBurglary protectionWar-like protectionWireless transmissionEngineering
Owner:WINDOWCOM E&C CORP
Projectile for radially deploying sub-projectiles
InactiveCN1653313APrevent havingStable positionAmmunition projectilesDefence devicesElectronic controllerEngineering
A projectile (10) for firing from a barrel, said projectile including a multiplicity of barrel assemblies (12, 13, 14) radially disposed from the centre of mass of the projectile, wherein each of said multiplicity of barrel assemblies includes a plurality of sub-projectiles (16) axially disposed within a barrel; each of said sub-projectiles associated with a discrete propellent charge (17) for propelling a respective sub-projectile from the barrel, wherein said projectile is capable of selectively firing sub-projectiles (16), suitably with the aid of primers (18) each coupled to an electronic controller (15), to provide a predetermined pattern of deployed sub-projectiles. A defence system employing projectiles of the type described is also disclosed, together with a method for disguising the launch location of a projectile utilising divert propulsion.
Owner:METAL STORM LTD
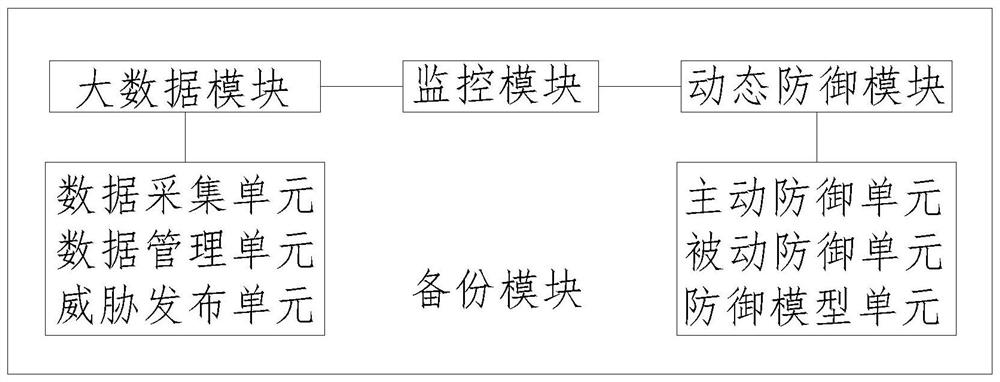
Network security dynamic defense system and method based on big data
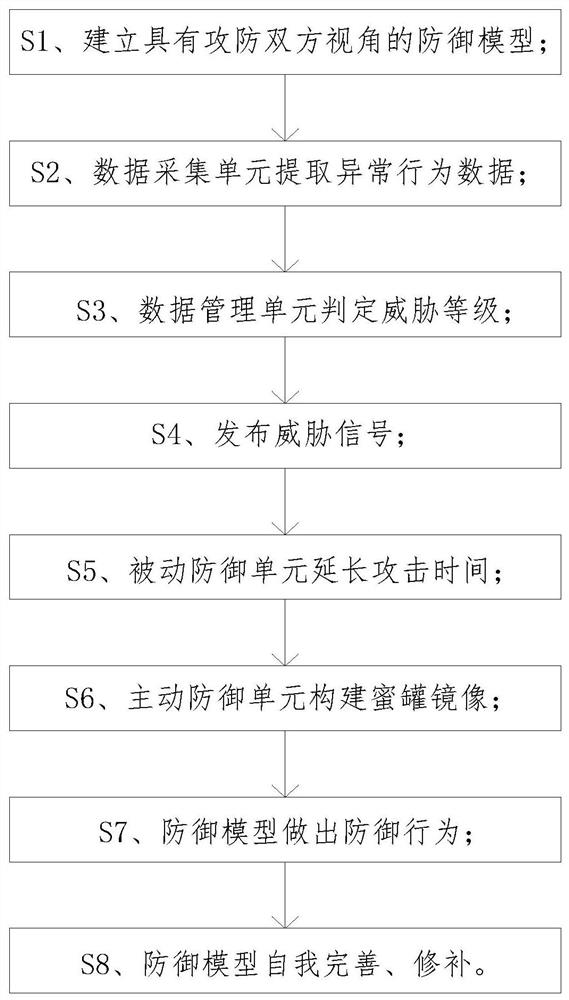
The invention discloses a network security dynamic defense system and method based on big data. The system comprises a big data module, a dynamic defense module, a backup module and a monitoring module, the big data module and the dynamic defense module are both bidirectionally connected with the monitoring module; and the backup module is used for all data and attack behavior data in the data module, the dynamic defense module and the monitoring module. Abnormal behaviors in a data packet are positioned and analyzed through a big data module, active defense and passive defense are matched, a dynamic defense model with attacking and defending view angles is established, an attacker is actively spoofed, the sight of the attacker is disturbed, and the attacker is decoy to carry out attack by setting a honeypot, so that the attack time is prolonged and the attack efficiency is improved. The opportunity is provided for the defense model to implement the defense scheme, the dynamic, real-time and active defense of the defense system is finally realized, and the defense effect is good.
Owner:上海磐御网络科技有限公司
Defence system
InactiveUS7841268B2Large amount of fragmentation-andReduce in quantityDefence devicesBarrages/weirsFiberCrystalline materials
Owner:ENVIRONMENTAL DEFENCE SYST
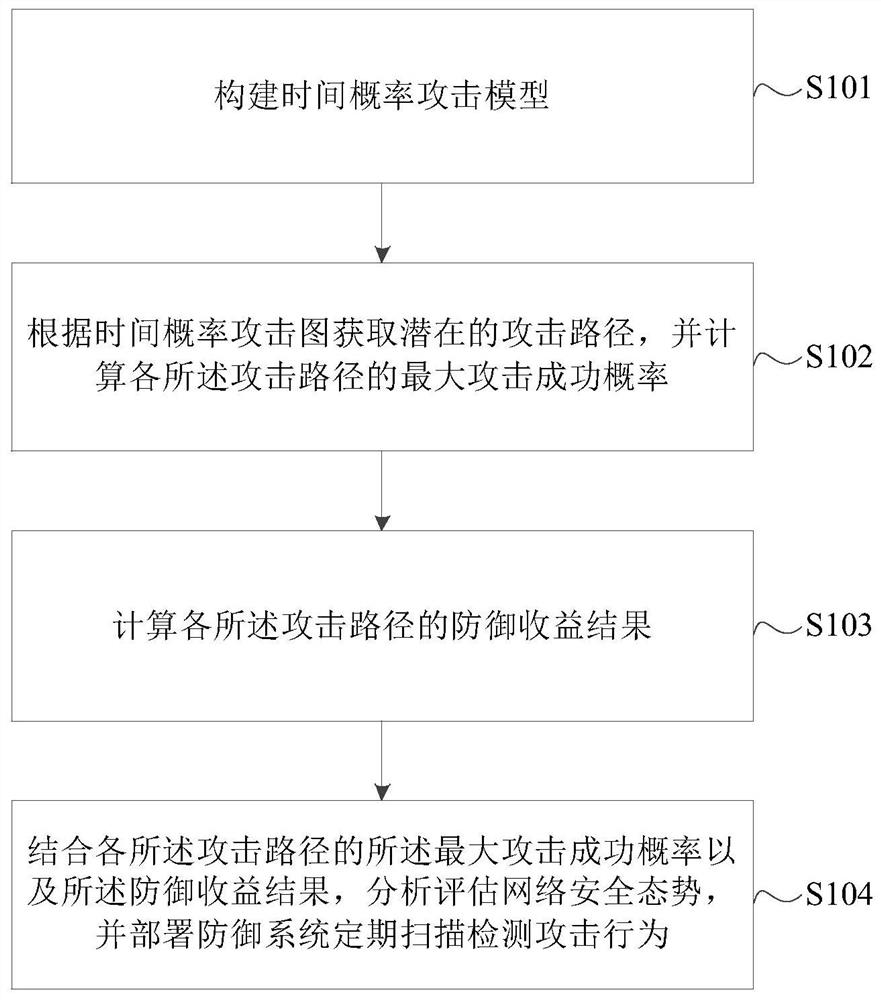
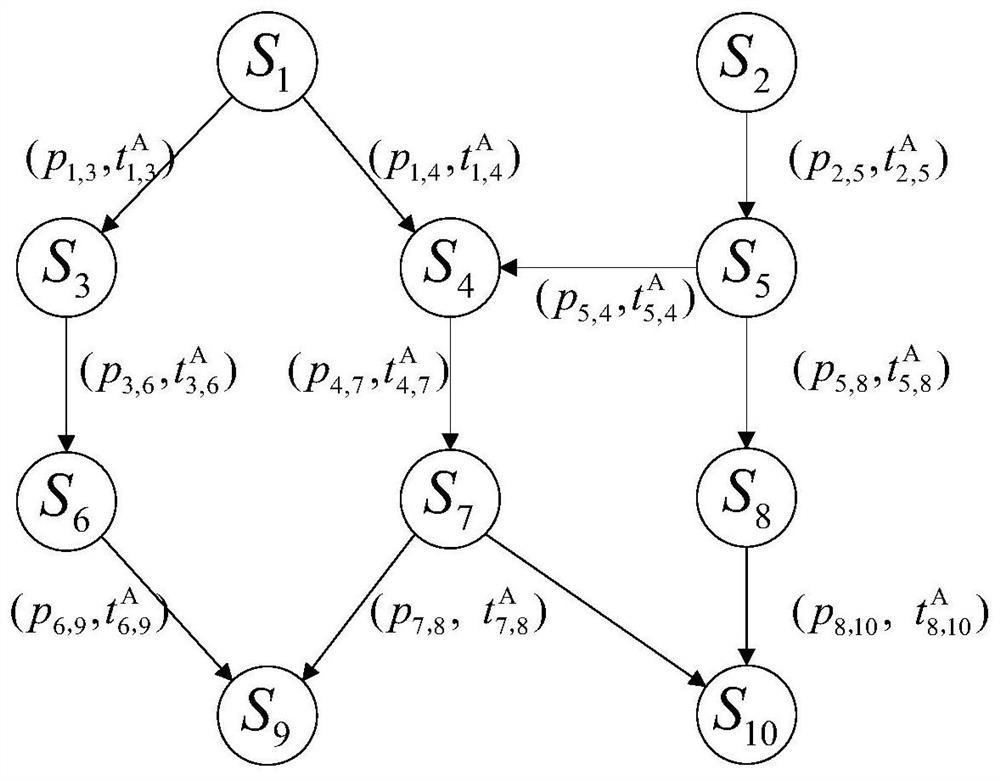
Virus attack defense method based on time probability attack graph
PendingCN112926055AImprove accuracyPlatform integrity maintainanceAttack graphReliability engineering
The invention relates to a virus attack defense method based on a time probability attack graph. The method comprises the following steps: constructing a time probability attack model; obtaining potential attack paths according to the time probability attack graph, and calculating the maximum attack success probability of each attack path; calculating a defense income result of each attack path; and in combination with the maximum attack success probability of each attack path and the defense income result, analyzing and evaluating a network security situation, and deploying a defense system to regularly scan and detect attack behaviors. According to the virus attack defense method provided by the invention, the network security situation is analyzed and evaluated, so that the deployment position of the defense system can be deployed in a targeted manner according to the path and the node which need to be protected, and the deployment accuracy of the defense system is further improved.
Owner:AIR FORCE UNIV PLA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com