Cloud-based intelligent security defense system and defense method
A technology for security defense and client system, applied in the field of computer network information security, can solve the problems of stealing and leakage, unauthorized access of privacy leaks, affecting the security of information resources and social stability, etc., to achieve the effect of enhancing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
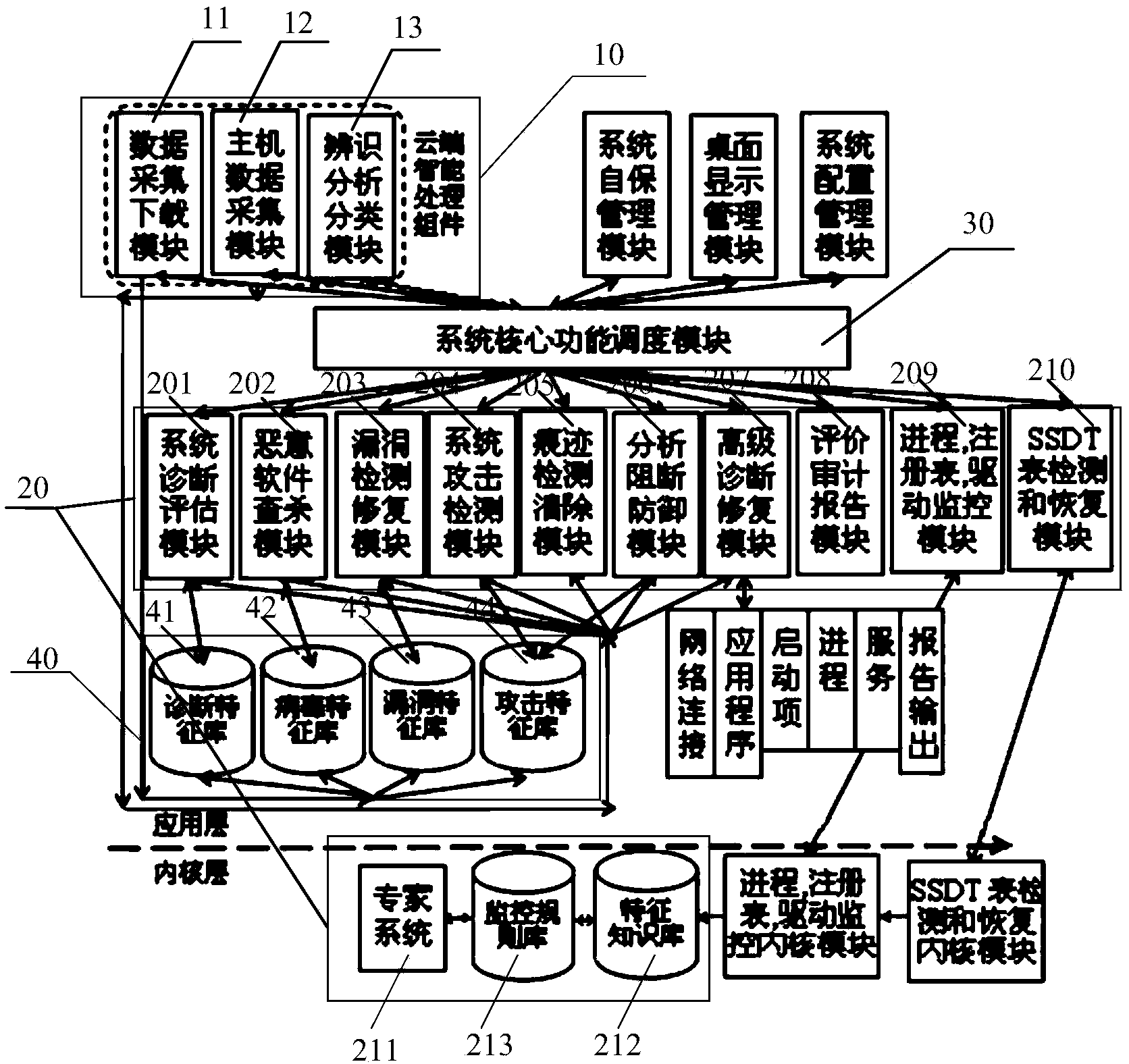
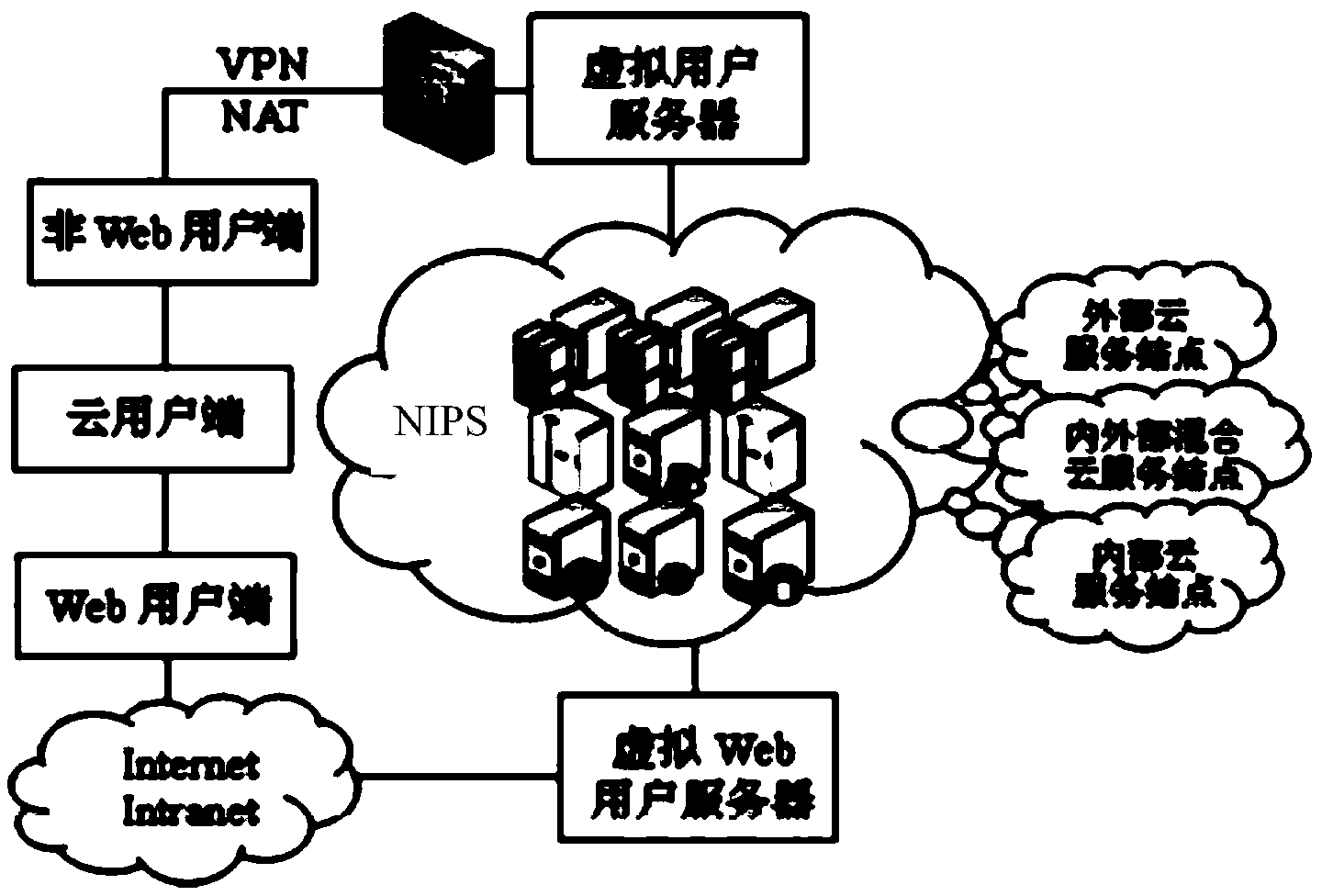
[0052] The encapsulation carrier proposed by the present invention and its manufacturing method will be further described in detail below with reference to the accompanying drawings and specific embodiments. Advantages and features of the present invention will be apparent from the following description and claims. It should be noted that all the drawings are in a very simplified form and use imprecise scales, and are only used to facilitate and clearly assist the purpose of illustrating the embodiments of the present invention.
[0053] Network security has become one of the top ten hot topics in the world in the 21st century, and has attracted widespread attention from the society. With the rapid development of information construction and IT technology, the application of computer network technology is more extensive and in-depth, and network security problems continue to emerge, which makes the importance of network security technology more prominent. Network security has ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com