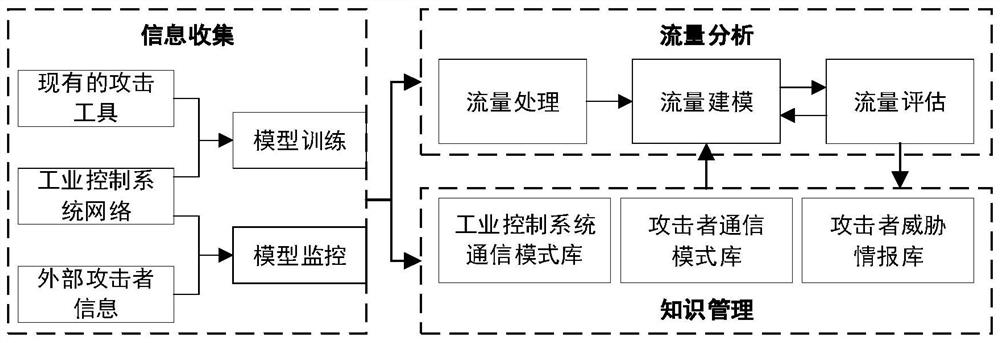
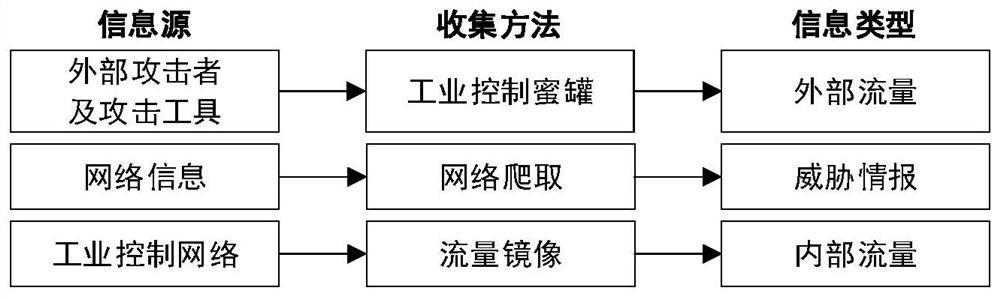
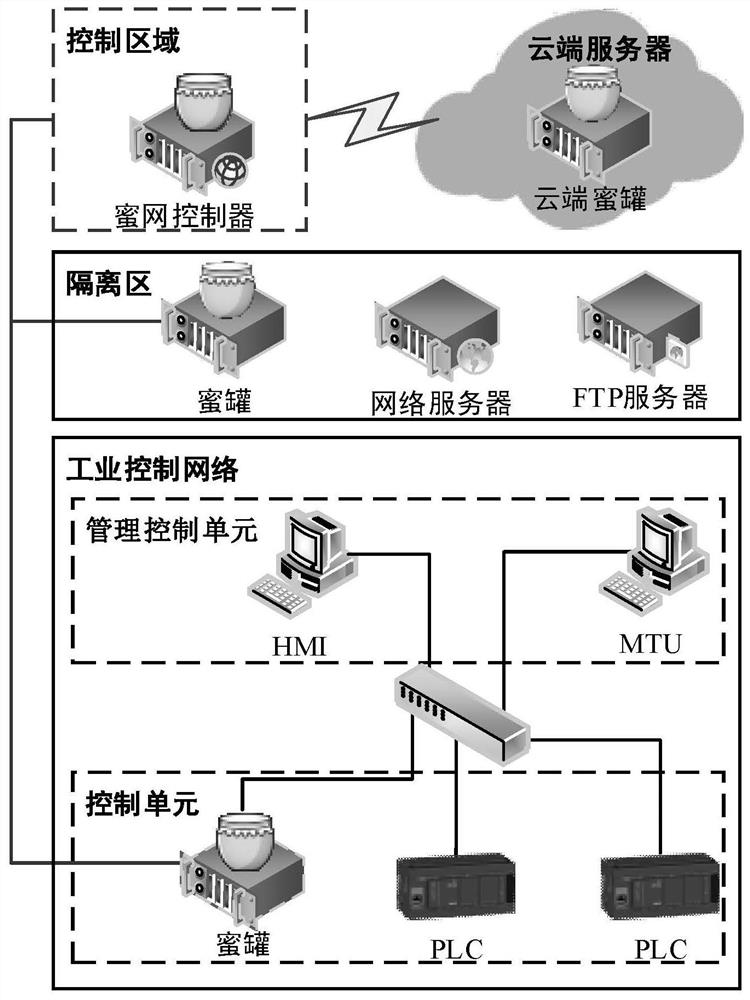
Industrial control network active defense system based on honeynet and method thereof
An industrial control system and industrial control network technology, applied in the field of network security, can solve the problem of insufficient network administrators to understand the network situation and make decisions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0118] Embodiment 1: Extracting network traffic characteristics of an industrial control system
[0119] It is assumed that different network entities have different capabilities and intentions, thus different network entities always generate different communication patterns. The present invention uses these communication patterns as fingerprints of different network entities to detect abnormal traffic in a large amount of industrial control system network traffic. In this embodiment, the effectiveness of the fingerprint industrial control system network traffic of the present invention is studied with the accuracy rate as the main index.
[0120] First, the present invention extracts sessions from the original industrial control system network traffic according to the feature vectors of different industrial control system protocols; 60% of the sessions are used for training, and the remaining 40% of the sessions are used for testing models, wherein the training data and test ...
Embodiment 2
[0121] Embodiment 2: Detect abnormal traffic
[0122] The present invention has two methods of "non-updating" and "updating" in detecting abnormal traffic, and evaluates the effect of detecting traffic with four standards of Accuracy, Precision, Recall and F1 score. The standard is defined as follows:
[0123]
[0124]
[0125]
[0126]
[0127] Among them, TP means that members of the same organization are classified into the same group; TN means that members of different organizations are grouped into different groups; FP means that members of different organizations are grouped into the same cluster; FN means that members of the same Members of an organization are grouped into different clusters.
[0128] First divide the dataset into two parts, train the "non-updating" method with part 1 data, and test with part 2 data; Train and test with the remaining 40% of the data; finally experiment with the "Update" method with a threshold of 0.3, train on the part 1 d...
Embodiment 3
[0131] Example 3: Assessing the degree of threat
[0132] First, this embodiment assigns different threat levels to the data in the second part based on professional knowledge, maliciousness and attack type. Next, use the data in Part 1 as the training data to generate the threshold T of the three characteristics of maximum depth, number of connections, and number of groups MD ,T NoC and T NoP . The present invention evaluates the threat level of the second part data with these three thresholds, and the result precision is 0.948, such as Figure 8 There are four evaluation errors shown: the first error is due to the scanned IC device not returning a correct response, thereby interrupting the subsequent scanning activity, and the remaining three errors are caused by the write operation in the data, because the write operation does not should appear in the data. Experimental results show that the invention can not only accurately evaluate the threat level of industrial cont...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com