Method for generating and authenticating hidden video tags based on video characteristics and digital signatures
A video feature and digital signature technology, applied in the field of information security, can solve the problems of lack of effective prevention methods for replay behavior, label generation and embedding behavior denial, etc., to achieve high security, resist replay attacks, and enhance robustness Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] The embodiments of the present invention are described in detail below. This embodiment is implemented on the premise of the technical solution of the present invention, and detailed implementation methods and specific operating procedures are provided, but the protection scope of the present invention is not limited to the following implementation example.
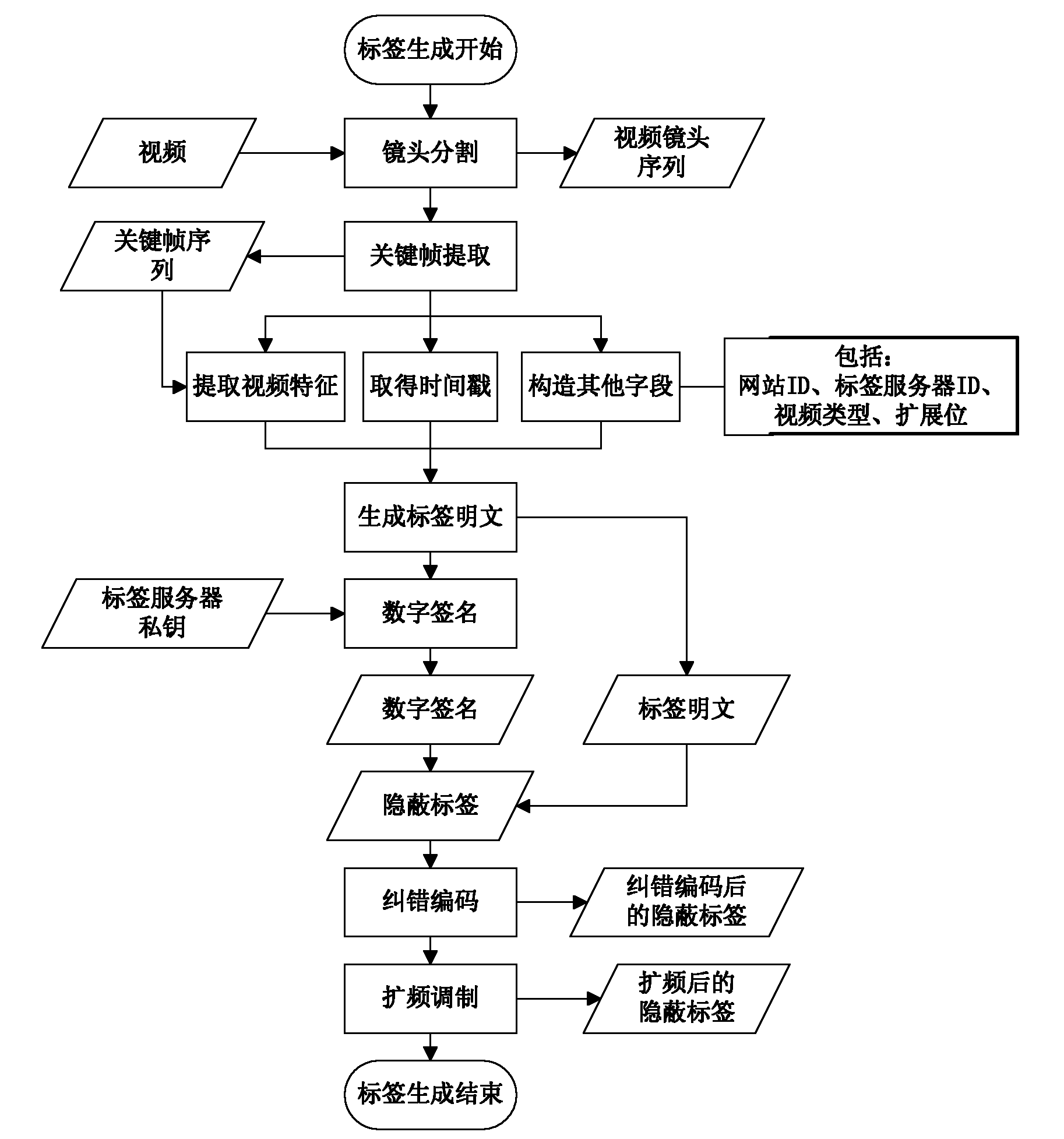
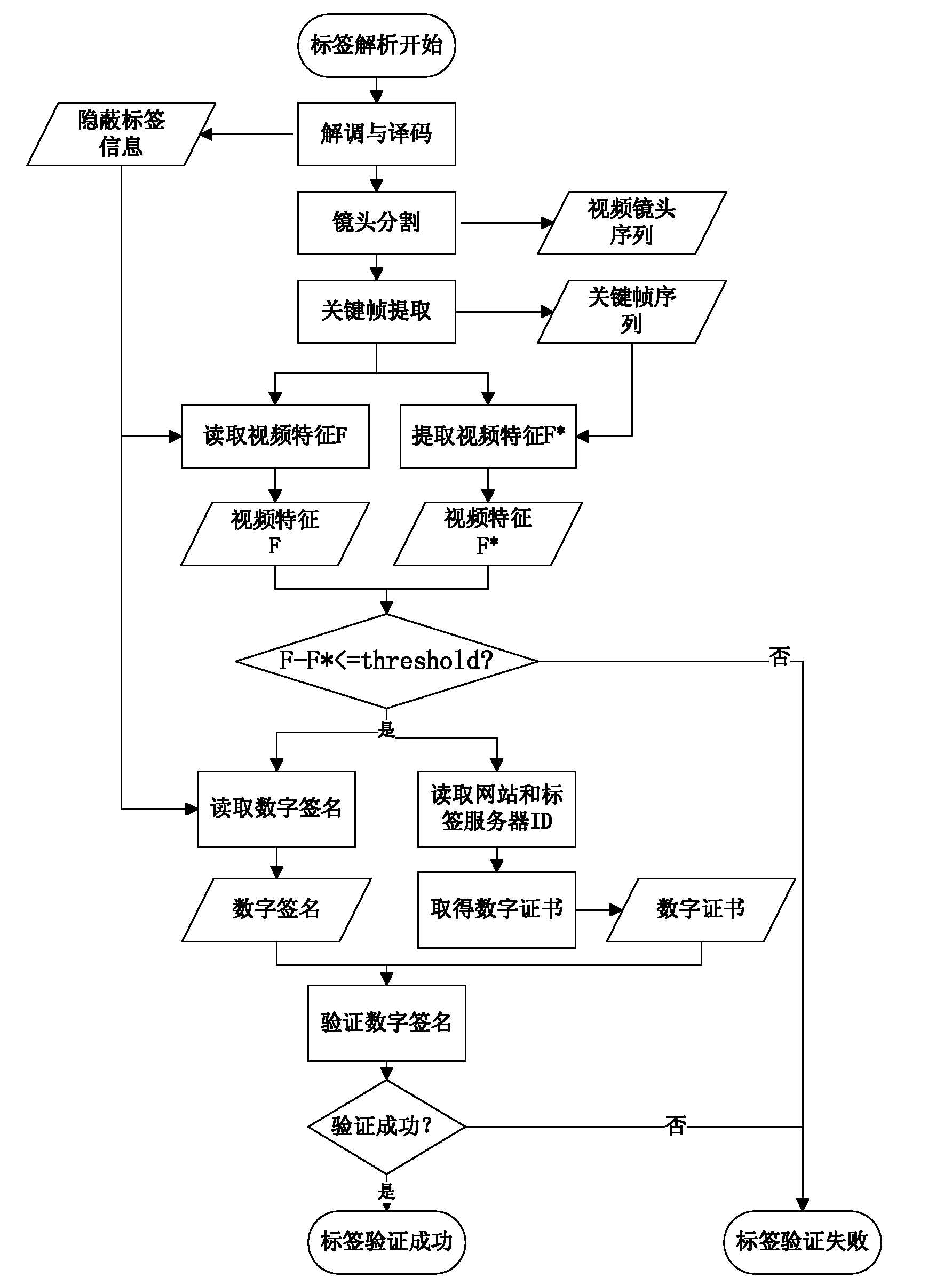
[0046] The present invention relates to a video hidden label authentication method based on video features and digital signatures, the specific steps are as follows:
[0047] The first step is to convert the original video into the grayscale space, segment the video and extract the key frames of each shot, and obtain the key frame sequence KFS at the sending end.
[0048] 1) Segment the carrier video to obtain the video sequence ShtS=(Sht 1 , Sht 2 ,...,Sht t ), where each shot Sht i , i=1, 2, . . . , there is no shot cut in t.
[0049] 2) For each shot Sht i , extract a key frame KF that best represents the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com