Method and system for verifying source address
A verification method and source address technology, applied in the field of network communication, can solve problems such as replay attacks and low source address verification security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
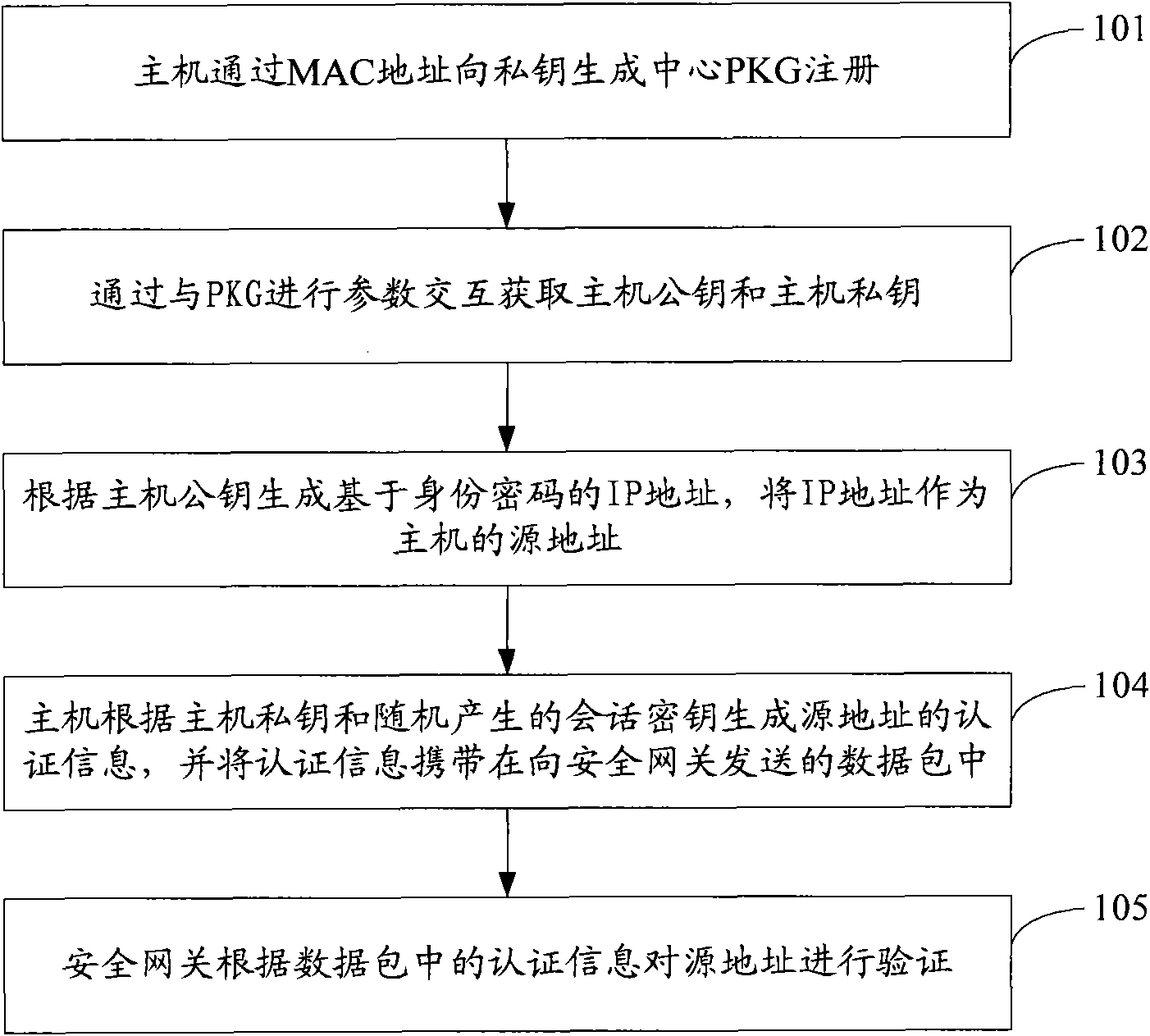
[0082] see figure 1 , which is the flow chart of the first embodiment of the source address verification method of this application:
[0083] Step 101: The host registers with the private key generation center PKG through the MAC address.
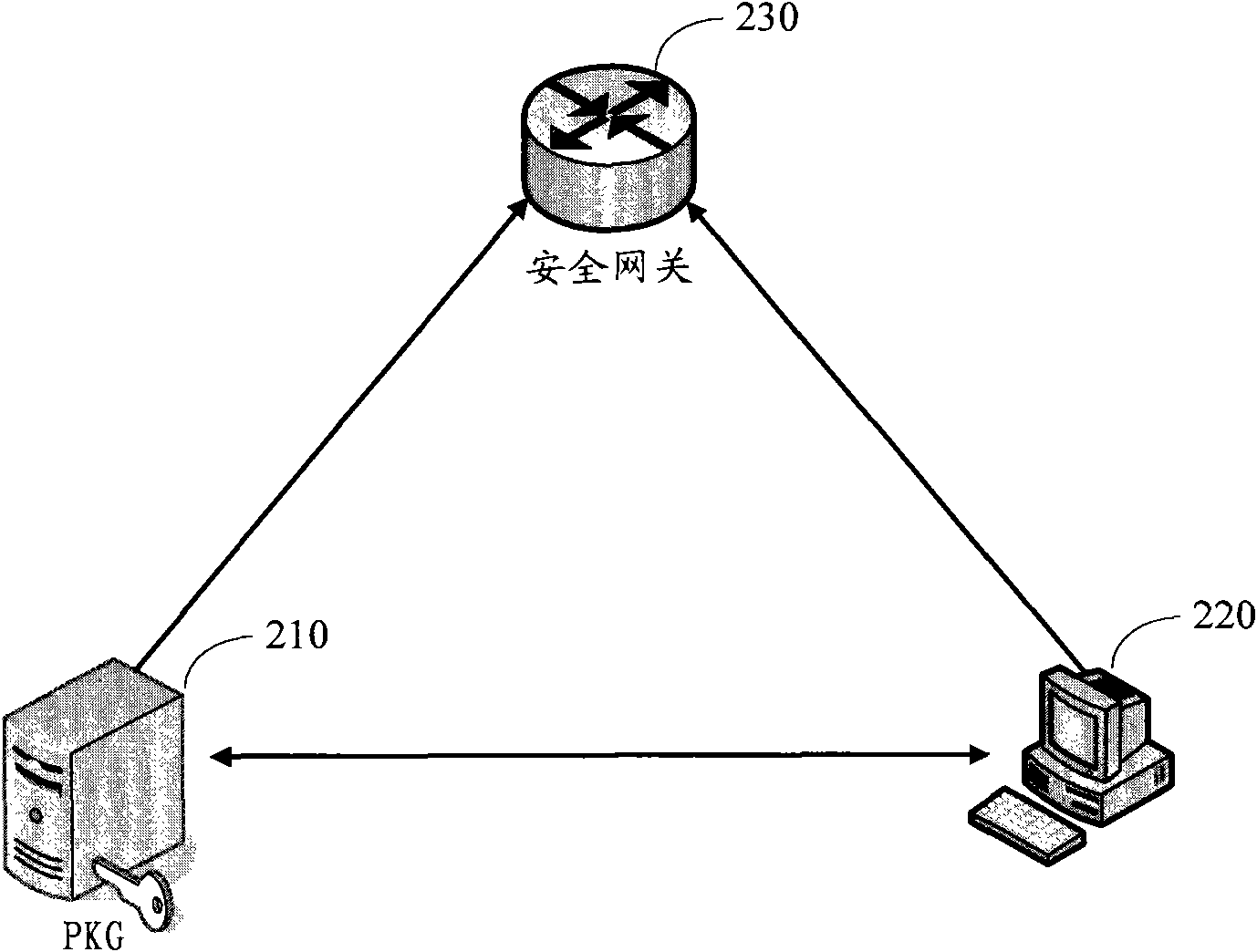
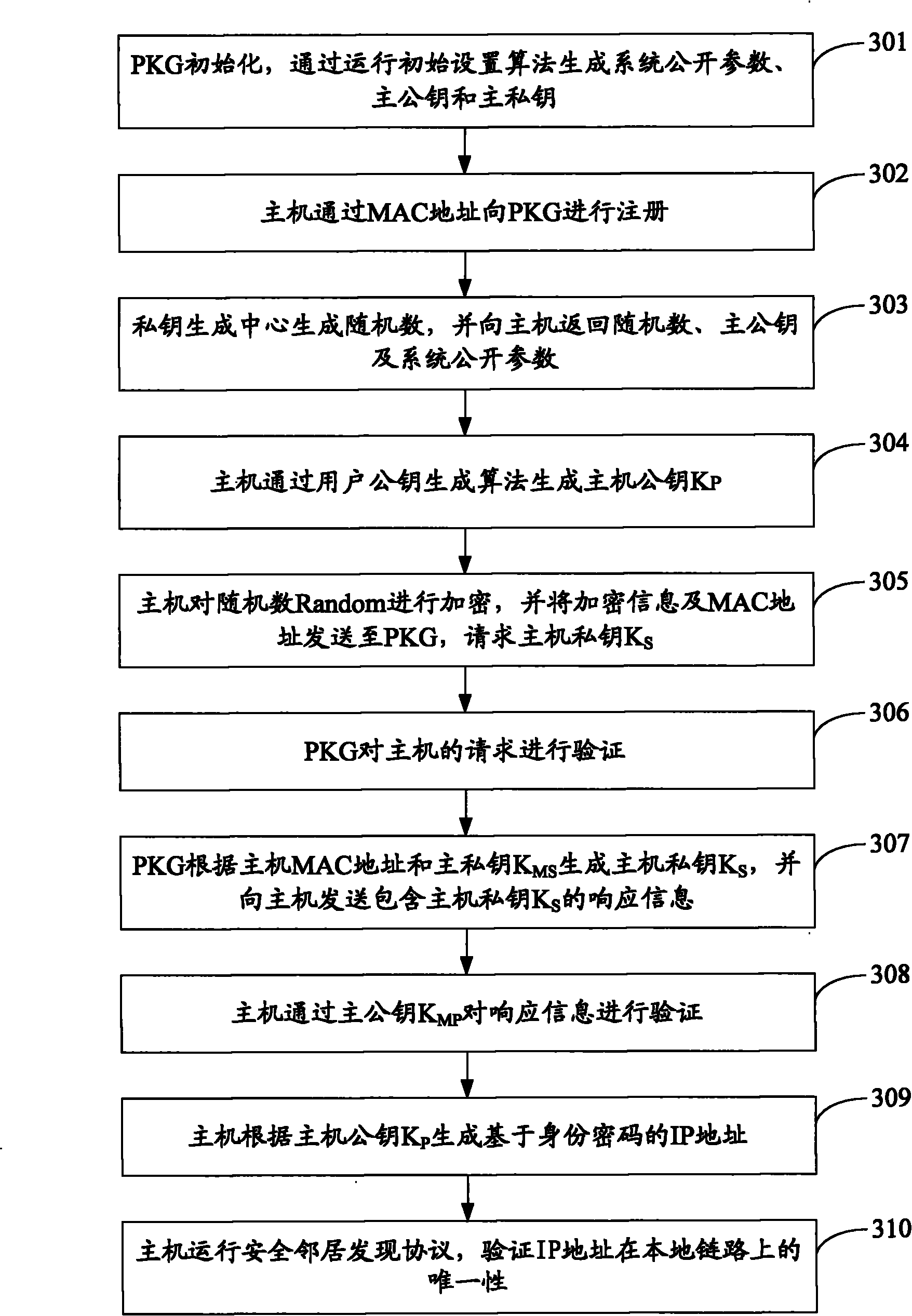
[0084] Before step 101, further, the PKG runs the initial setting algorithm to obtain the system public parameters, the master public key and the master private key, and saves the master private key in the trusted platform module TPM; the security gateway is initialized, by communicating with the PKG communication obtains the master public key and system public parameters.
[0085] Specifically, the host sends a registration request containing the MAC address to the PKG, and the PKG generates a random number for the host, and stores the correspondence between the MAC address and the random number in a static list, and the PKG returns the random number, master public key, and system public parameters to the host.
[0086] Step 102: Obtain...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com