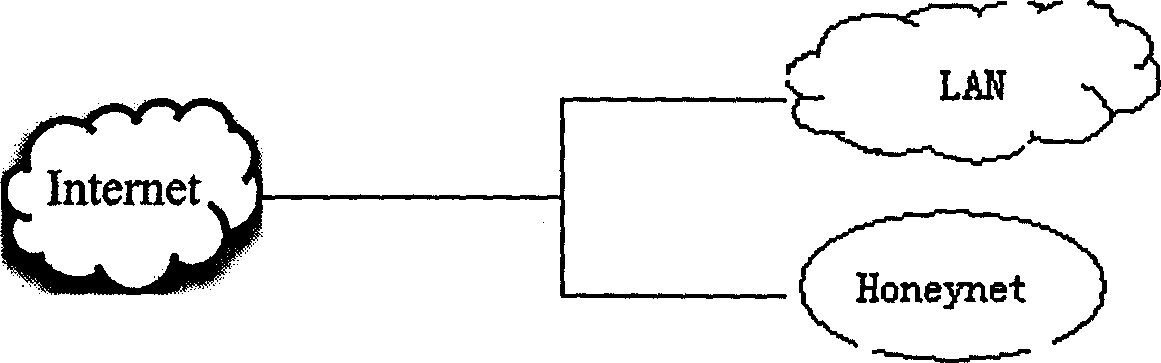
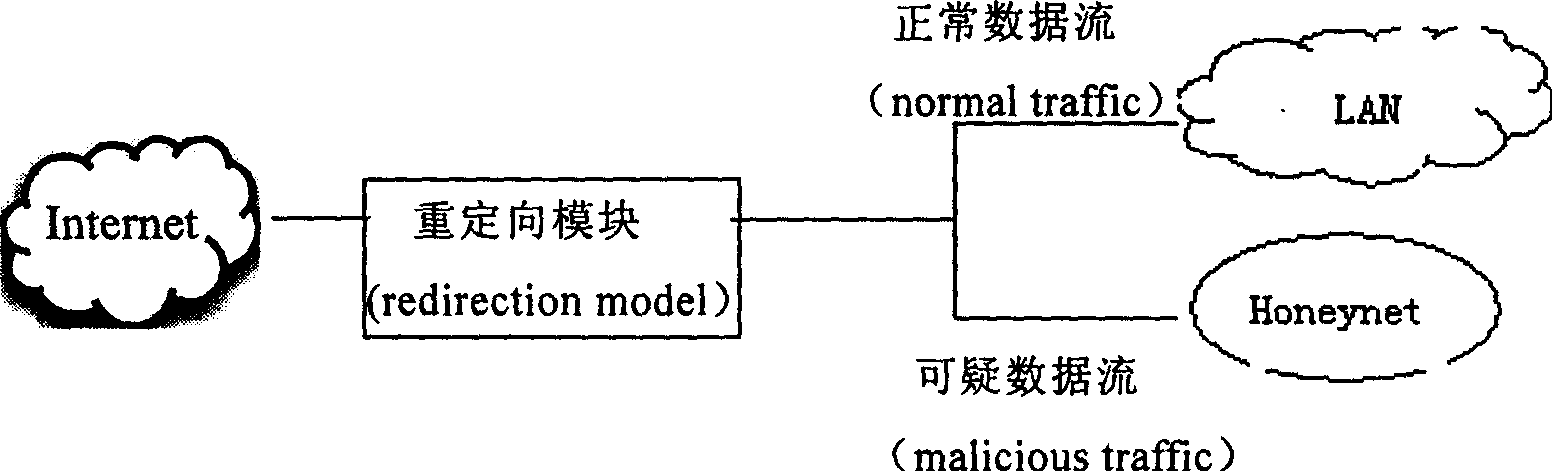
Method for realizing chaff network data flow heavy orientation
A technology of redirection and data flow, which is applied in the direction of data exchange network, digital transmission system, electrical components, etc., can solve the problems of increasing the difficulty and untestability of network security protection, and cannot assist in the protection of local area networks, etc., to achieve fast processing speed , the effect of protecting the local area network
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
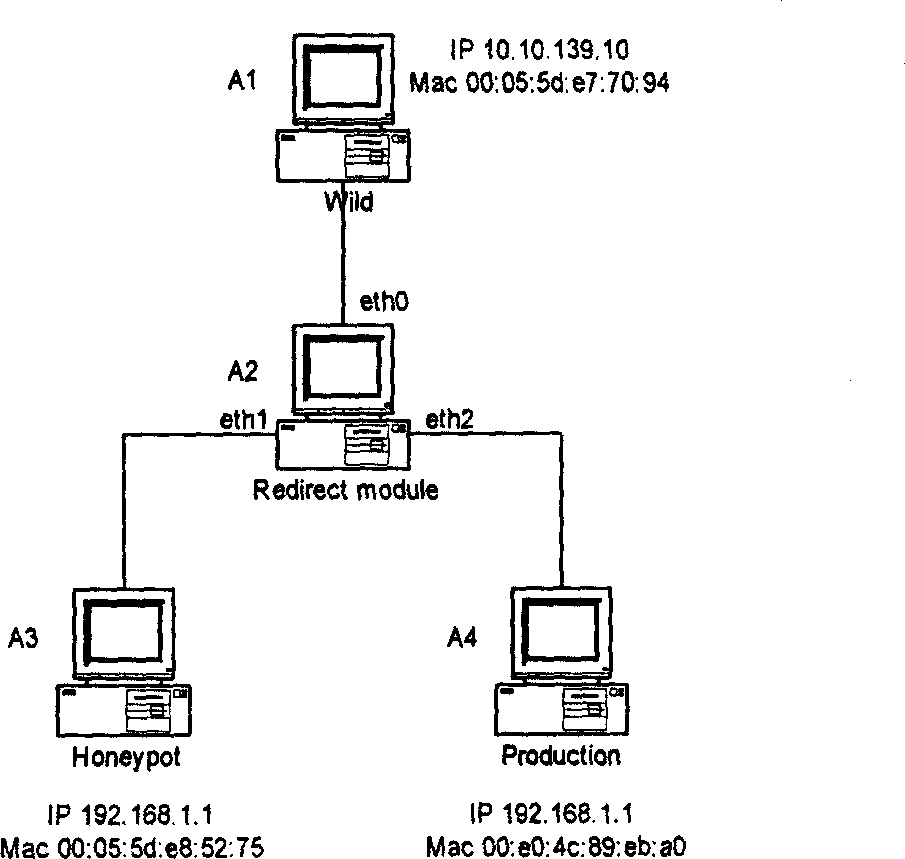
[0042] The system of the present invention is as image 3 shown. It consists of ordinary PCs A1-A4, among which PC A1 imitates the INTERNET data source and sets its IP address as 10.10.139.10 and MAC address as 00:05:5d:e7:70:94. PC A3 is a decoy network, and its IP address is set to 192.186.1.1, and its MAC address is 00:05:5d:e8:52:75 (the decoy network can be formed by installing an operating system on an ordinary PC, or it can be based on this Then, it imitates a local area network to provide services to users through programming, and captures user behavior, and performs analysis and statistics, etc.). The protected network is PC A4 (it can be one or a local area network composed of multiple PCs), set its IP address to 192.186.1.1, and its MAC address to 00:e0:4c:89:eb:a0 . The algorithm of the system can be Figure 4 The flow chart implementation of the flow chart, the HanleOutP function in the flow chart does some MAC address processing work on the packets sent to th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com