Attack behavior monitoring method, device, equipment and storage medium
A behavioral and monitored technology, applied in computer security devices, instruments, electrical and digital data processing, etc., can solve the problems of many hardware resources and low accuracy, and achieve the effect of lightweight settings and improved accuracy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
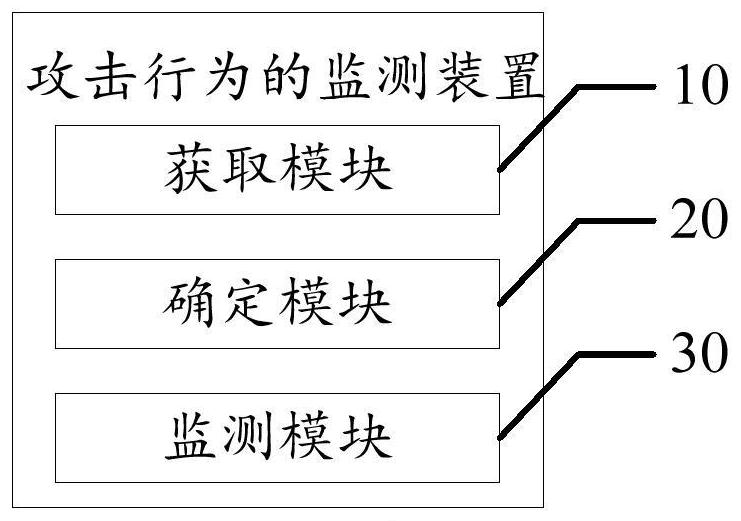
Image
Examples
Embodiment Construction
[0036] It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
[0037] The present invention provides a method for monitoring attack behavior, referring to figure 1 , figure 1 It is a schematic flowchart of the first embodiment of the attack behavior monitoring method of the present invention.
[0038] The embodiment of the present invention provides an embodiment of the attack behavior monitoring method. It should be noted that although the logic sequence is shown in the flow chart, in some cases, the sequence shown here may be executed in a different order. or the steps described.
[0039] Attack monitoring methods include:
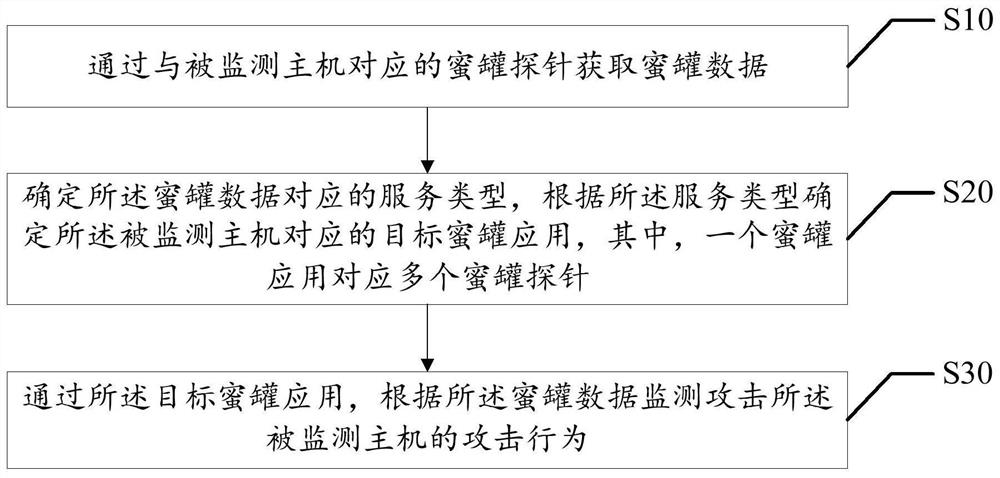
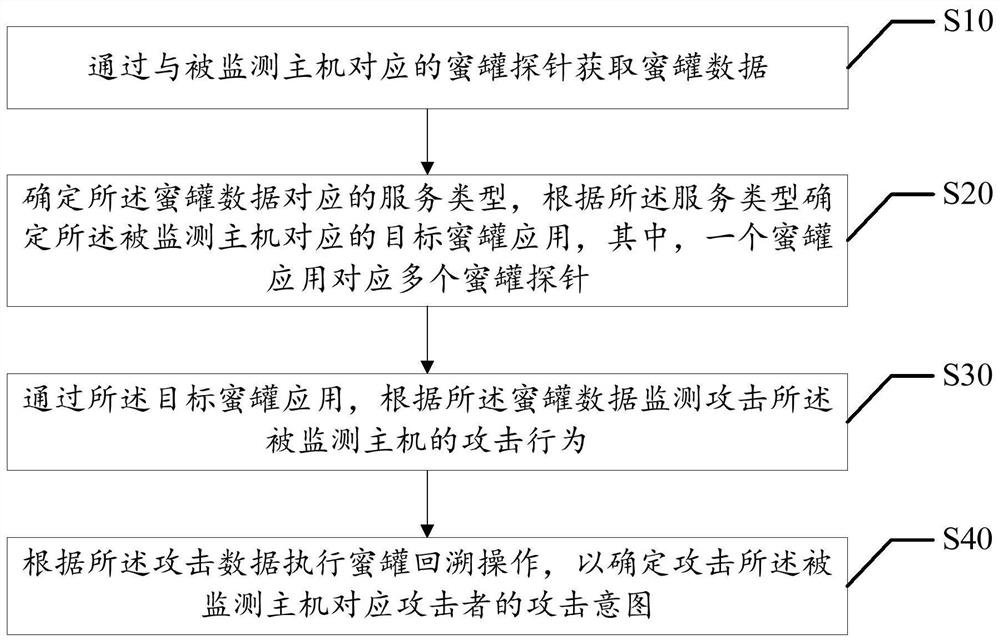
[0040] Step S10, acquiring honeypot data through a honeypot probe corresponding to the monitored host.
[0041] Step S20, determining the service type corresponding to the honeypot data, and determining the target honeypot application corresponding to t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com