Method of forwarding attack traffic to honeypot
A technology for attacking traffic and traffic forwarding, applied to electrical components, transmission systems, etc., can solve problems such as complex data transmission process, high deployment cost, and high cost of masquerading agents, and achieve simple deployment, network security maintenance, and strong operability Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] The technical solutions of the present invention will be described in detail below, but the protection scope of the present invention is not limited to the embodiments.
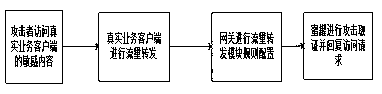
[0020] A method of forwarding attack traffic to a honeypot, such as figure 1 As shown, the attacker accesses the sensitive content of the real business client, and the real business client forwards the traffic after receiving it. After receiving the request, the honeypot will attack and obtain evidence and reply to the access request. In the present invention, unlike the prior art, what the client visits at the beginning is the real business. However, if the sensitive port of the real business is accessed, the gateway will Convert this access request to a honeypot. In the existing technical solution, the client first accesses the honeypot agent, and the honeypot agent decides whether to send the access request to the honeypot or real business, which increases the deployment cost. .
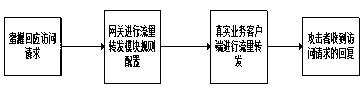
[0021] Such as ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com