A honeypot host
A honeypot and host technology, applied in the field of honeypot hosts, can solve problems such as time waste and disadvantages
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
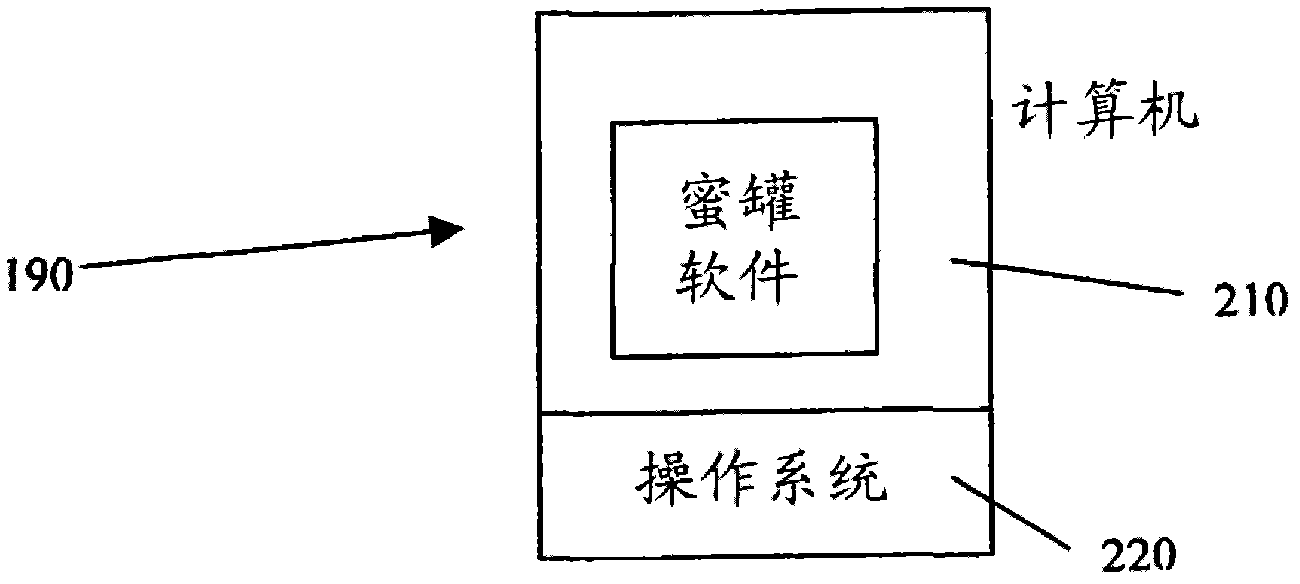
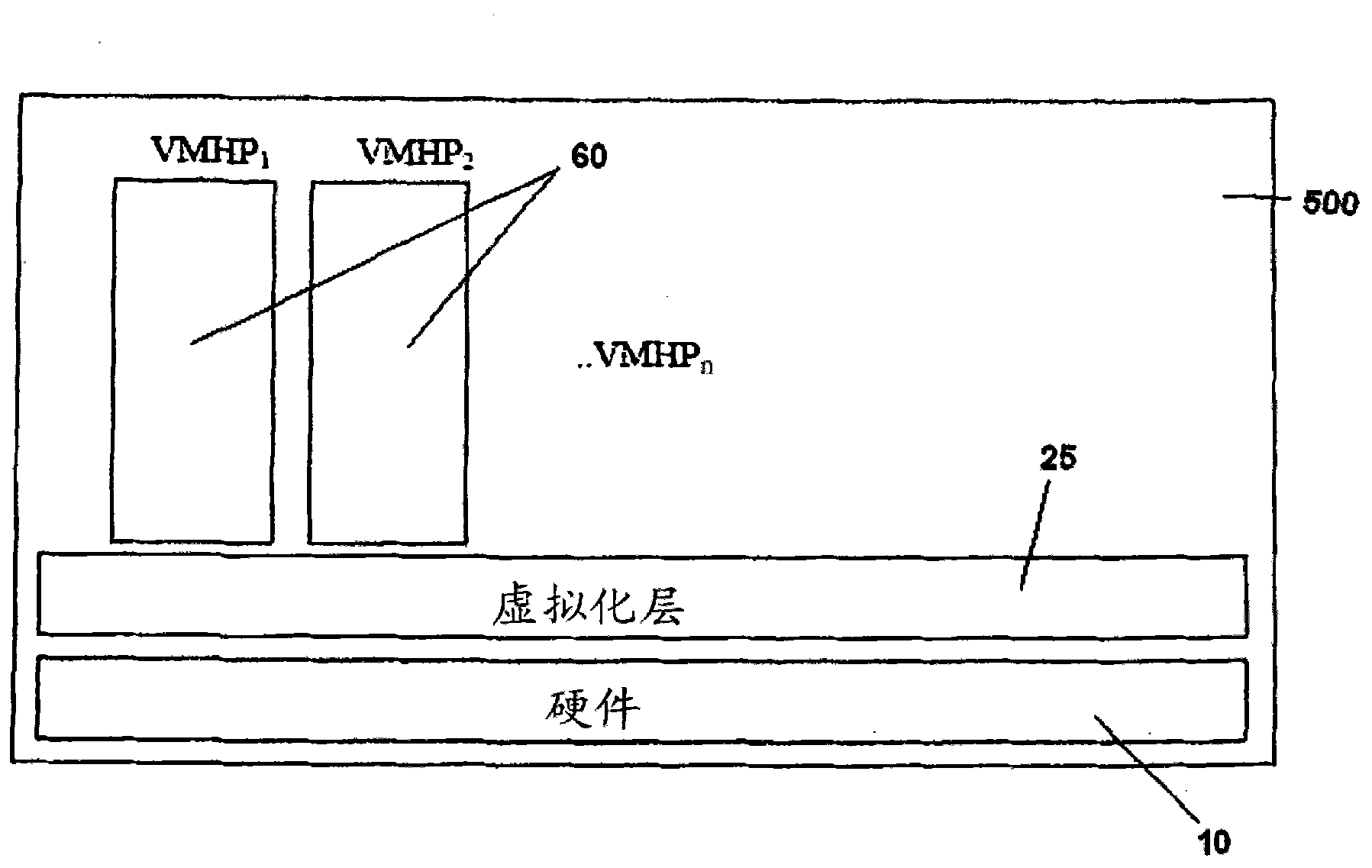
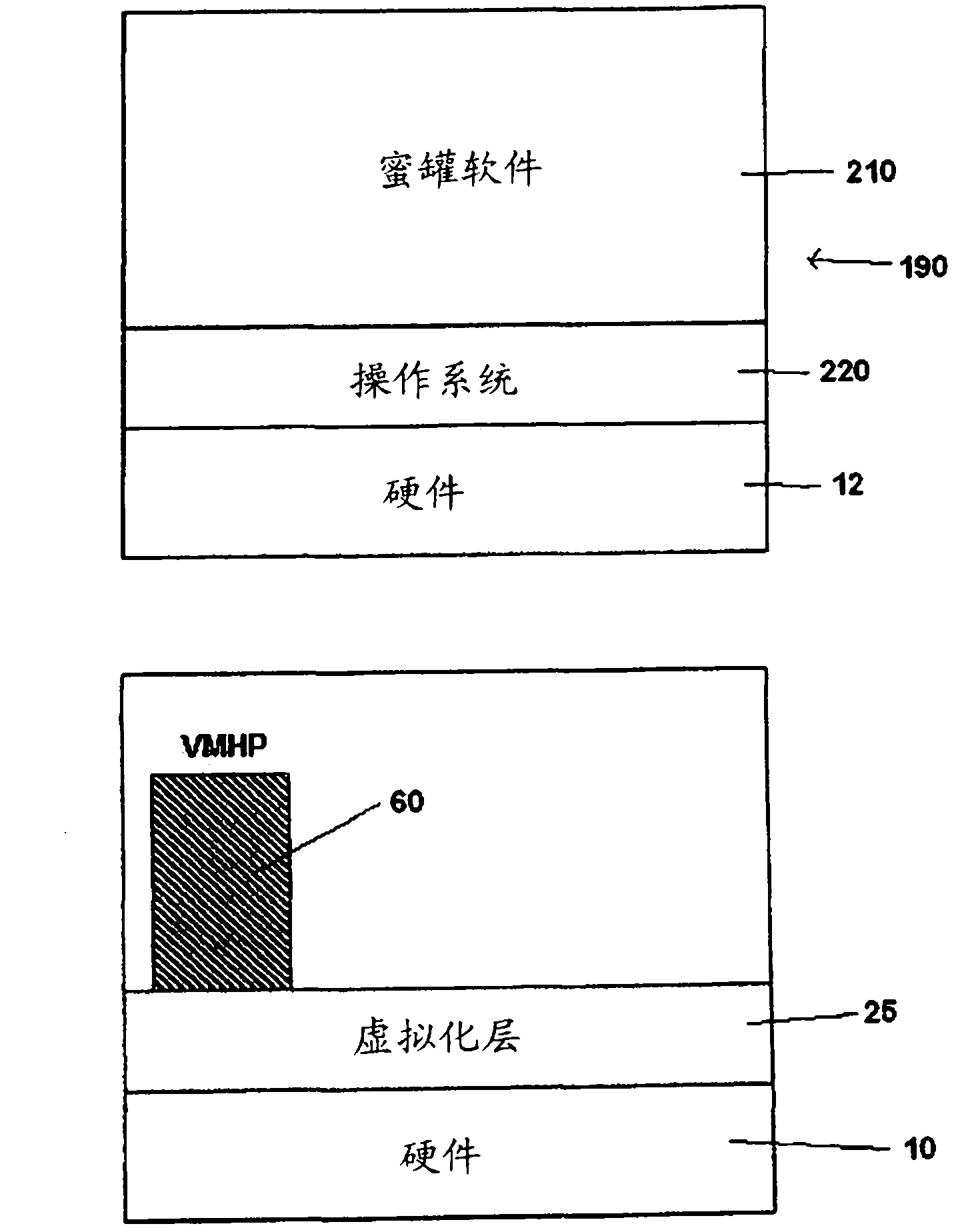
[0030] The present invention relates to a honeypot host 500 . More specifically, the present invention relates to a honeypot host 500 applied in the network 90, in order to distribute the decoy host 80 to unused surrounding network 90 when the current honeypot system 300 has been invaded. Internet Protocol (IP) address 160, and terminate the honeypot system 300 located in the host 500, and generate a new honeypot system 300. Next, the honeypot host 500 will be described according to the preferred embodiment of the present invention and with reference to the attached description and drawings. However, it should be understood that the description of the preferred embodiment of the present invention and accompanying drawings are only for the convenience of discussion of the present invention, and it is foreseeable that various modifications may be made by those skilled in the art without departing from the scope of the claims.
[0031] The honeypot host 500 of the present invent...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com