Power monitoring active defense method and system based on virtualization dynamic deployment
An active defense and power monitoring technology, applied in the field of network information security, can solve problems such as insufficient network information security defense of the power system, achieve the effect of increasing cost difficulty and timeliness, and improving security assurance capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
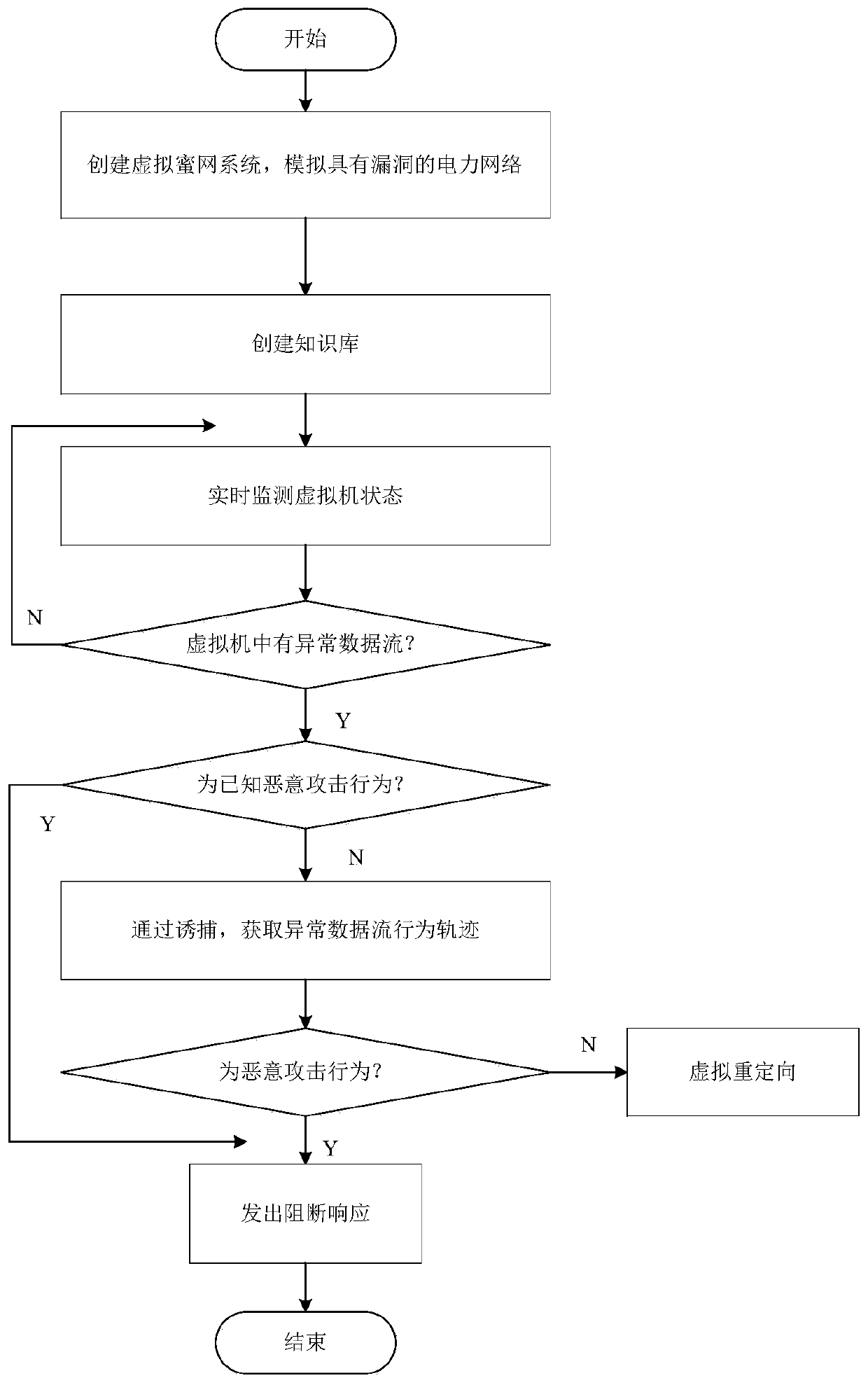
[0044] This embodiment provides an active defense method for power monitoring based on virtualization dynamic deployment, such as figure 1 shown, including the following steps:
[0045] Step 1, deploy the virtual honeynet system
[0046] Deploy a virtual honeynet system for the real business system of the power network, and perform network configuration on the virtual honeynet system, so that the virtual honeynet system is consistent with the network configuration of the real business system of the power network, and simulate a power network with loopholes.
[0047] Step 2, create a knowledge base
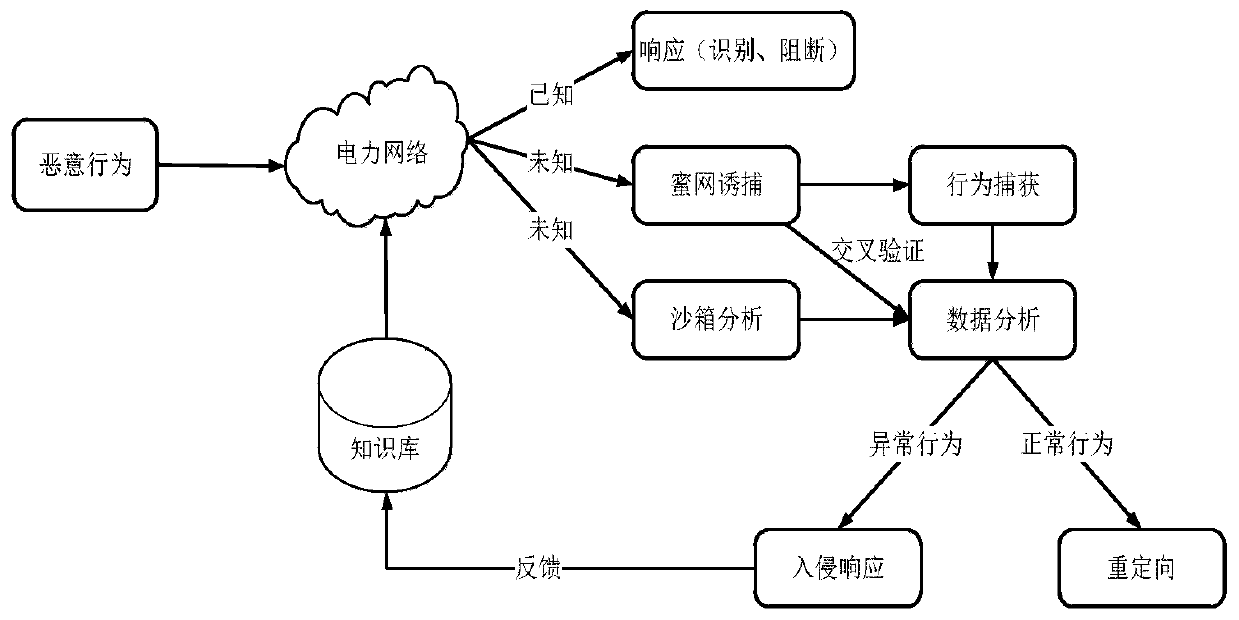
[0048] A knowledge base is created, and information on malicious attacks on the power network by external networks is stored in the knowledge base.
[0049] Step 3, honeynet trapping
[0050] If there is an abnormal data flow accessing the real business system, since the deployed virtual honeynet system is sufficiently realistic to simulate the business system of the power netwo...
Embodiment 2
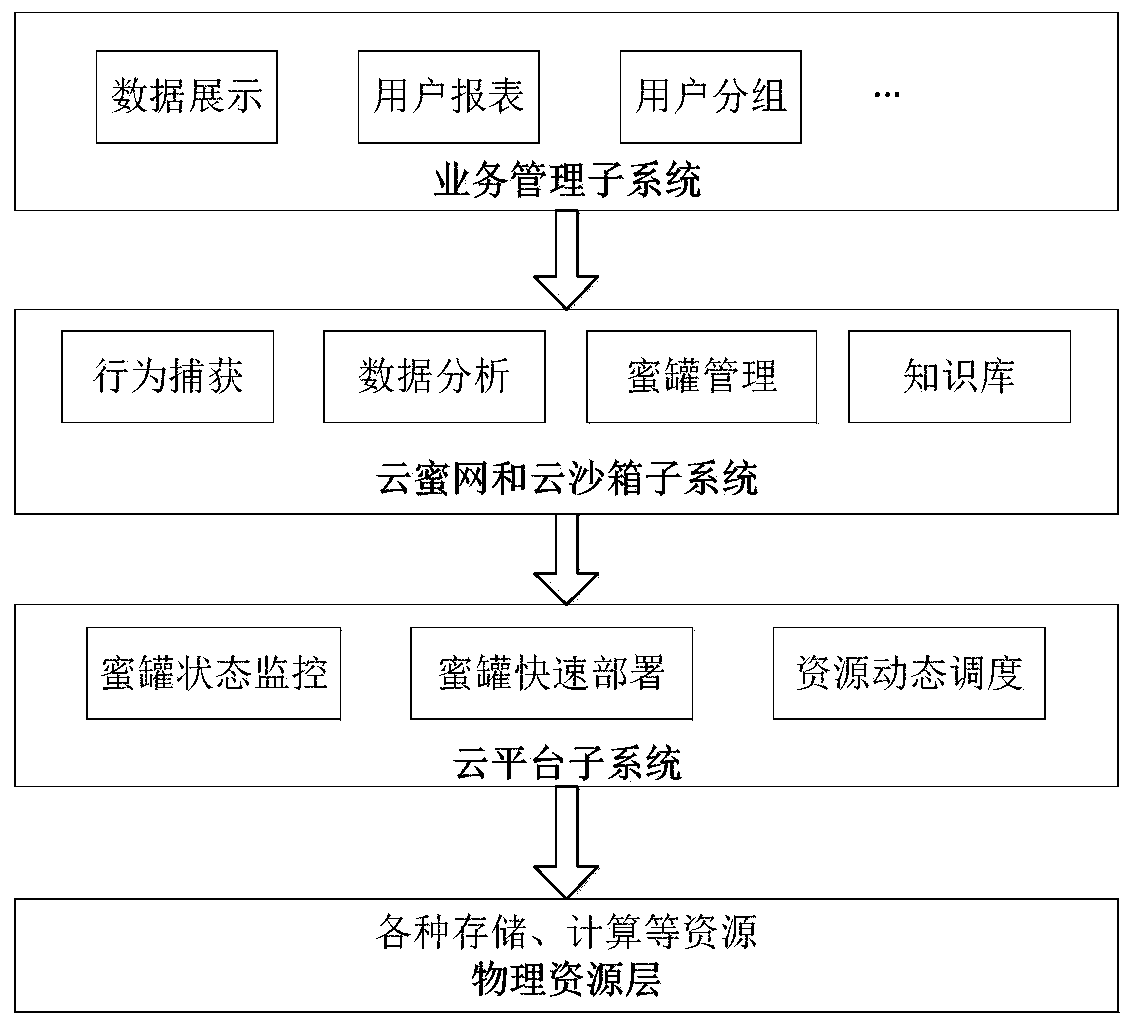
[0058] This embodiment provides an active defense system for power monitoring based on virtualized dynamic deployment. This embodiment simulates a power network with loopholes by building a distributed cloud honeynet and cloud sandbox. This embodiment adopts a layered system architecture Design, including:
[0059] (1) Business management subsystem:
[0060] The business management subsystem includes a cloud honey network management module and a cloud sandbox management module. Among them, the cloud honey network management module is used to simulate the honeypot type, the number of honeypot deployments, network scenarios, real-time data display, historical trend analysis, Manage analysis reports, honeypot groups, user groups, etc.;
[0061] The cloud sandbox management module is used to manage sandbox types, number of sandbox deployments, sandbox operation logs, analysis reports, etc.
[0062] (2) Threat analysis and protection subsystem:
[0063] The threat analysis and p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com