Virtual honeypot
A honeypot and virtual machine technology, applied in the field of computer network honeypots, can solve problems such as computer users unintentionally downloading or executing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
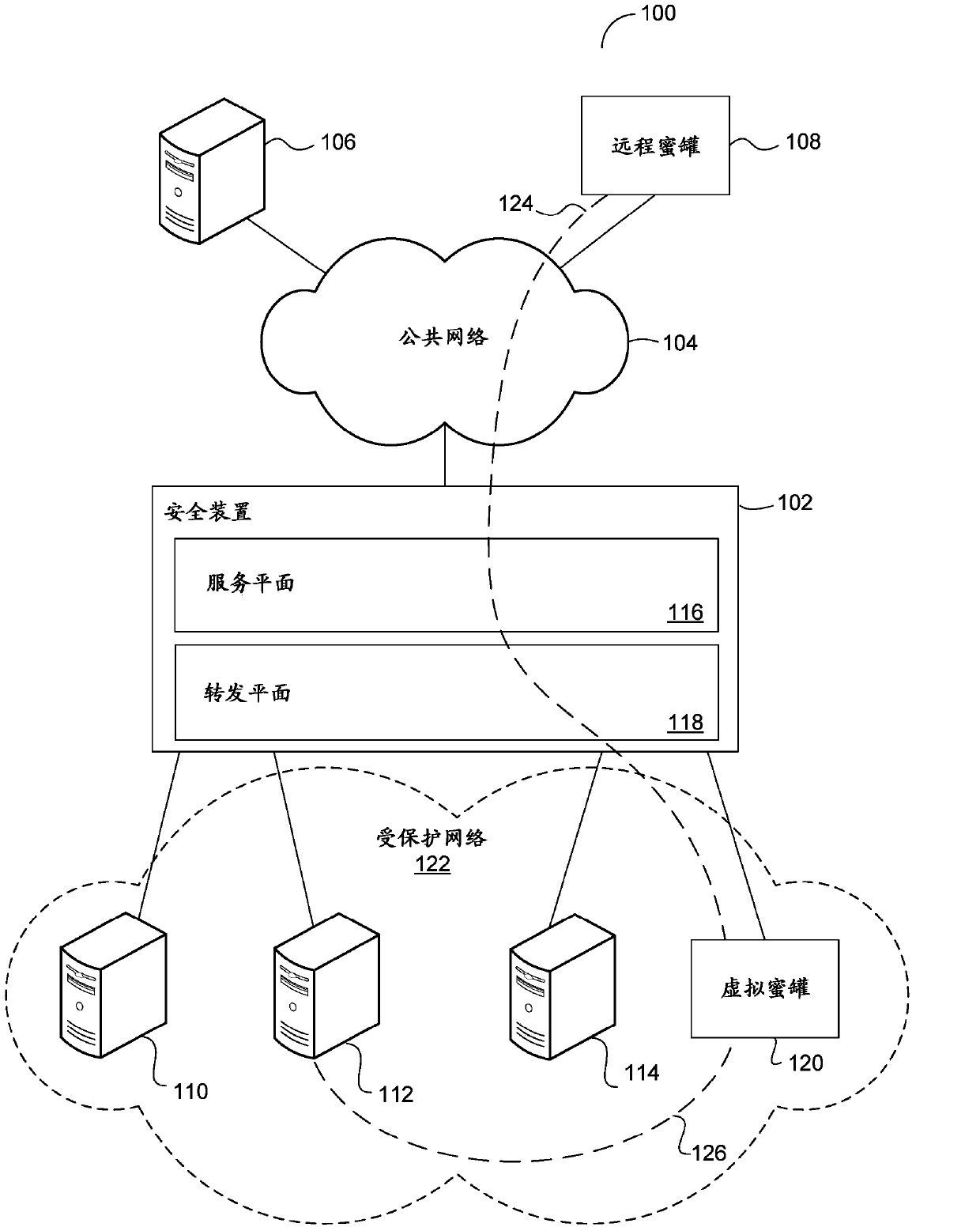
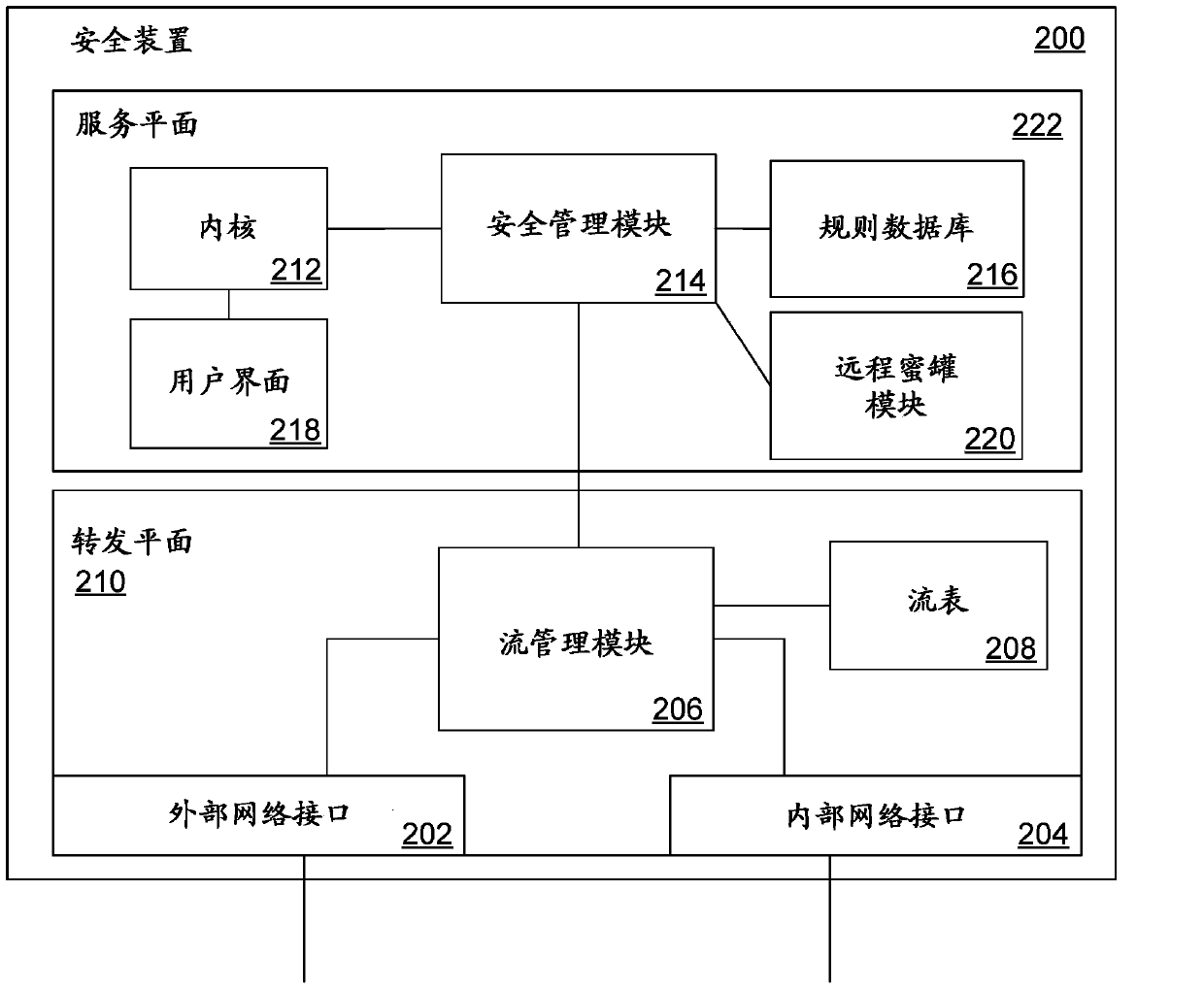
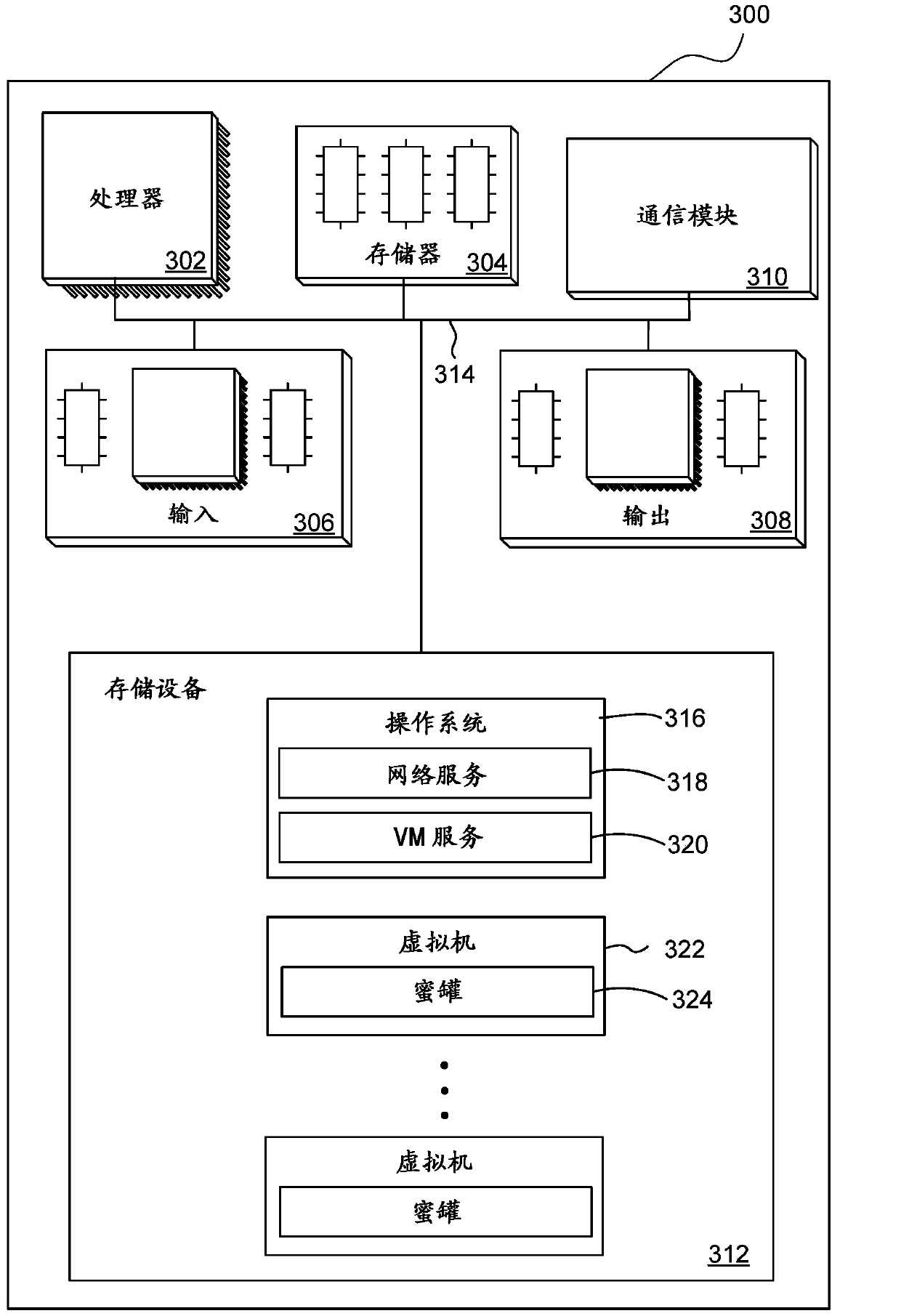
[0018] Security systems such as firewalls and anti-virus software provide significant protection in a typical network environment. In this environment, firewalls provide defense against unauthorized access to private networks, and anti-virus software protects individual computer systems from viruses, Trojans, Root program viruses and other threats provide defenses. Although such a security system provides defenses against many types of computer attacks, even if the event log is carefully checked, the information provided about how the attack is loaded is very limited.
[0019] For reasons such as this, a bait system called a honeypot is sometimes used to collect information about the attacker or intruder. Honeypots can be set up inside or outside the private network, such as by using custom software that is configured to look the same as the vulnerable system, or by using such as Windows TM Standard operating systems and software for servers, database servers, or other such sys...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com