Patents
Literature
168 results about "Port scan" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
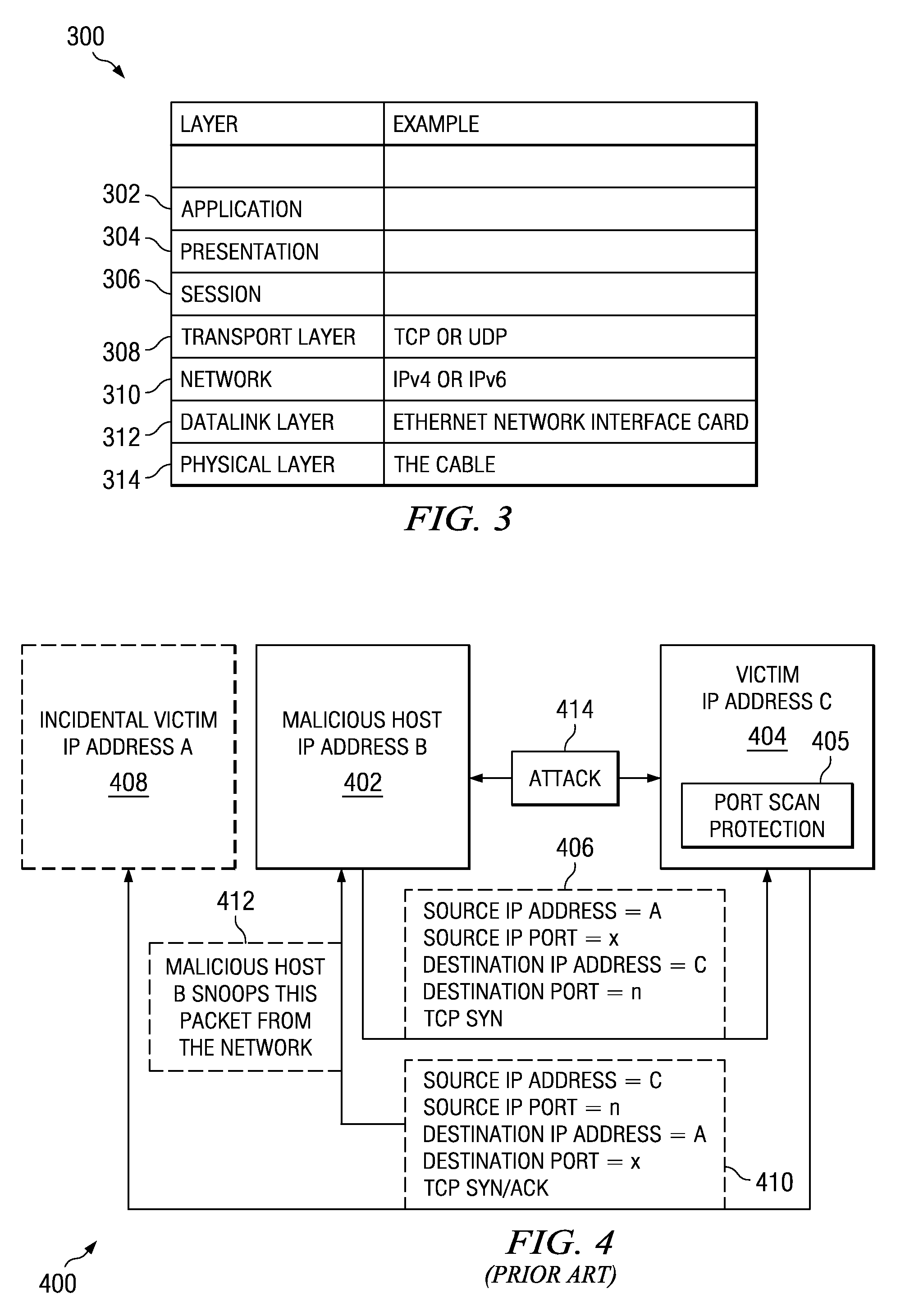
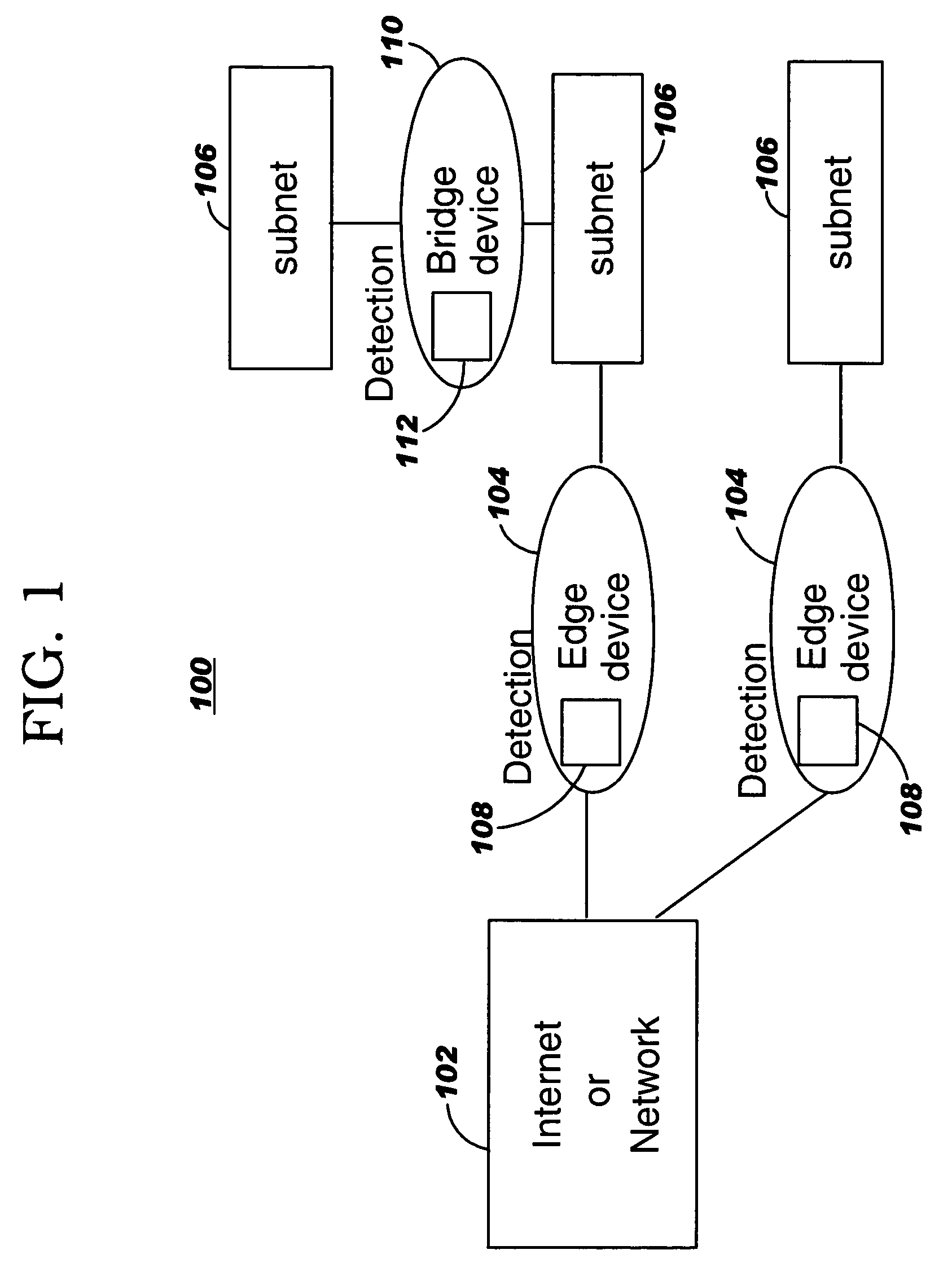
Method and apparatus for detecting port scans with fake source address
Owner:INT BUSINESS MASCH CORP
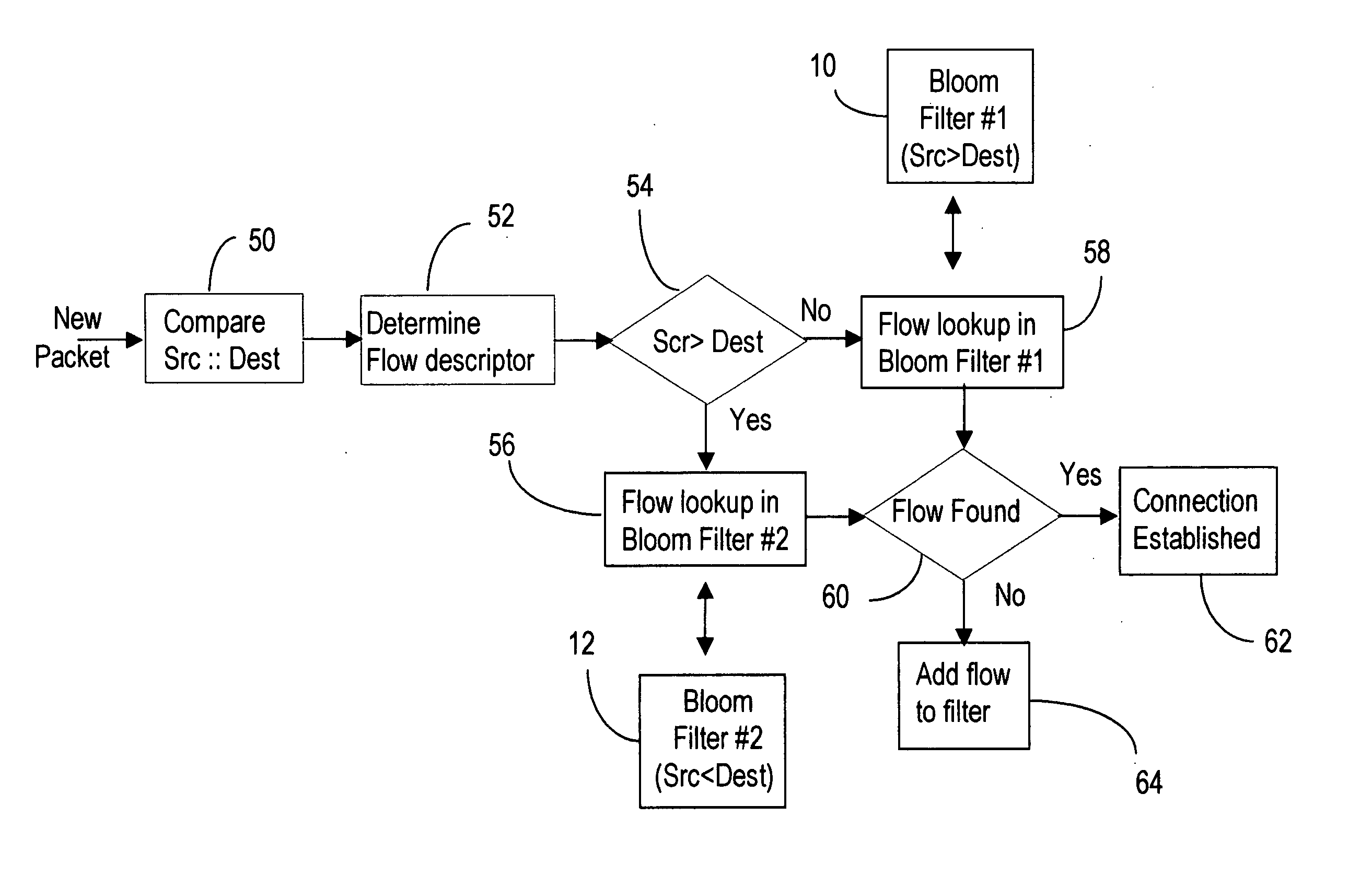
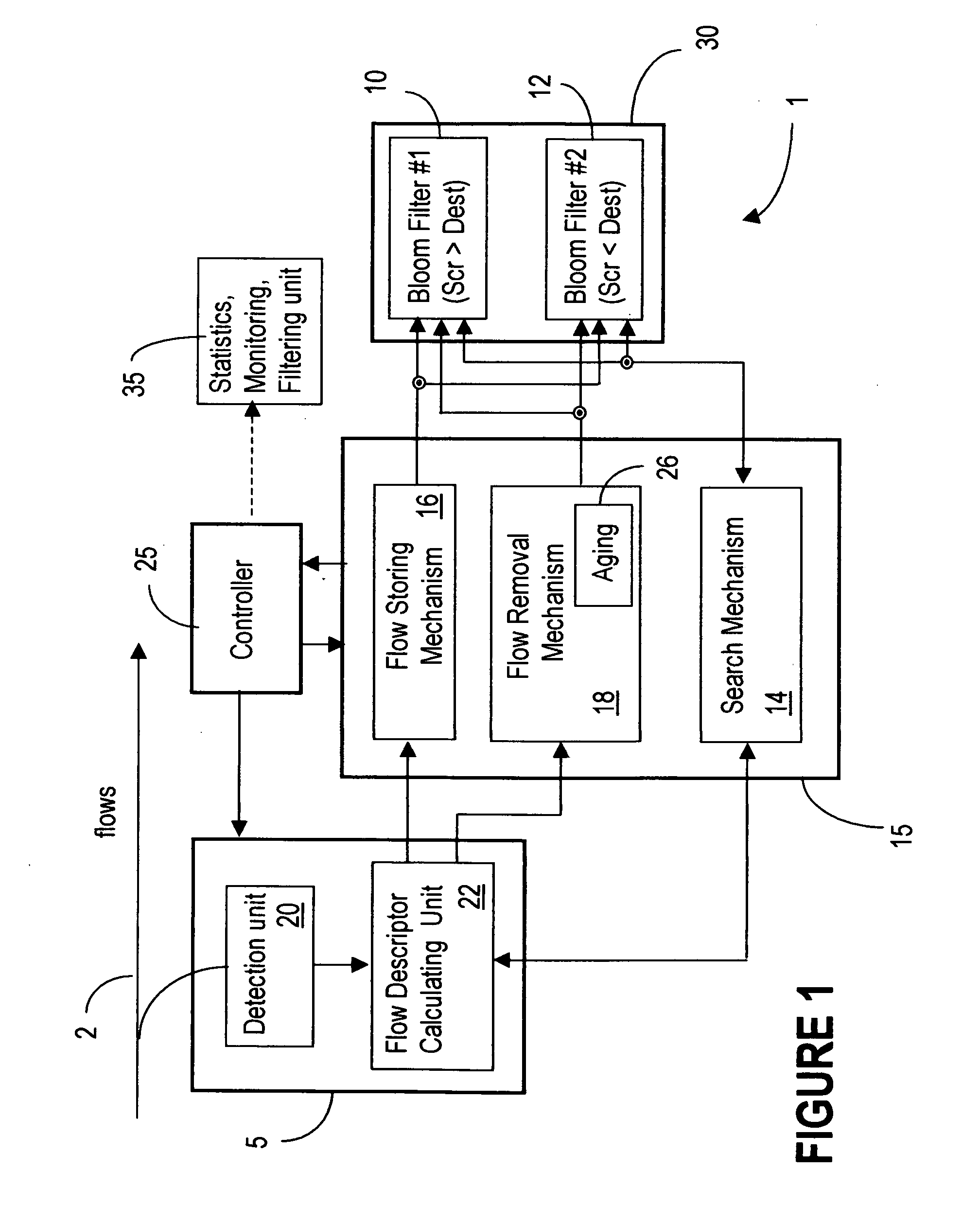
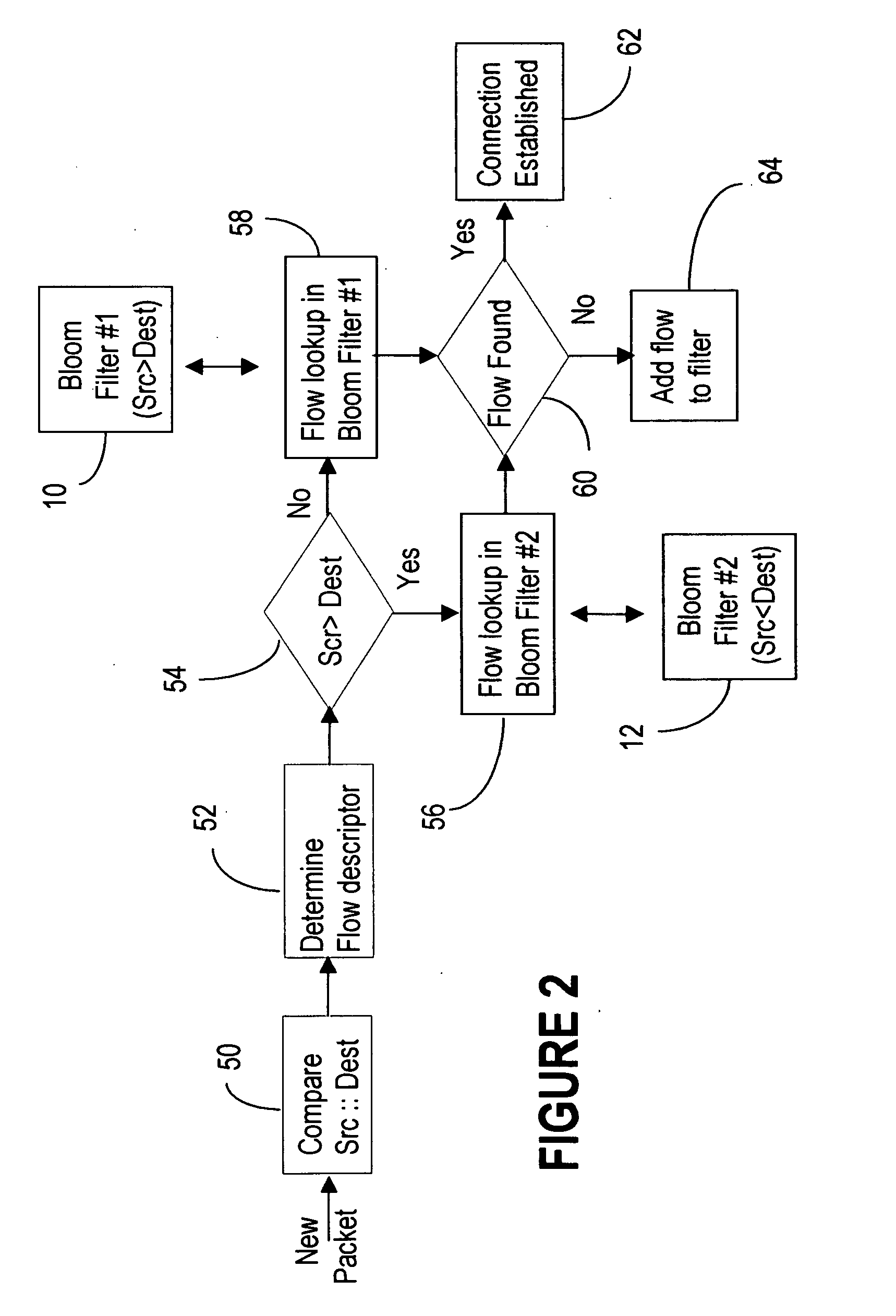
Symmetric connection detection
InactiveUS20070248084A1Mitigate such drawbackAlleviates totallyError preventionTransmission systemsComputer hardwareWire speed
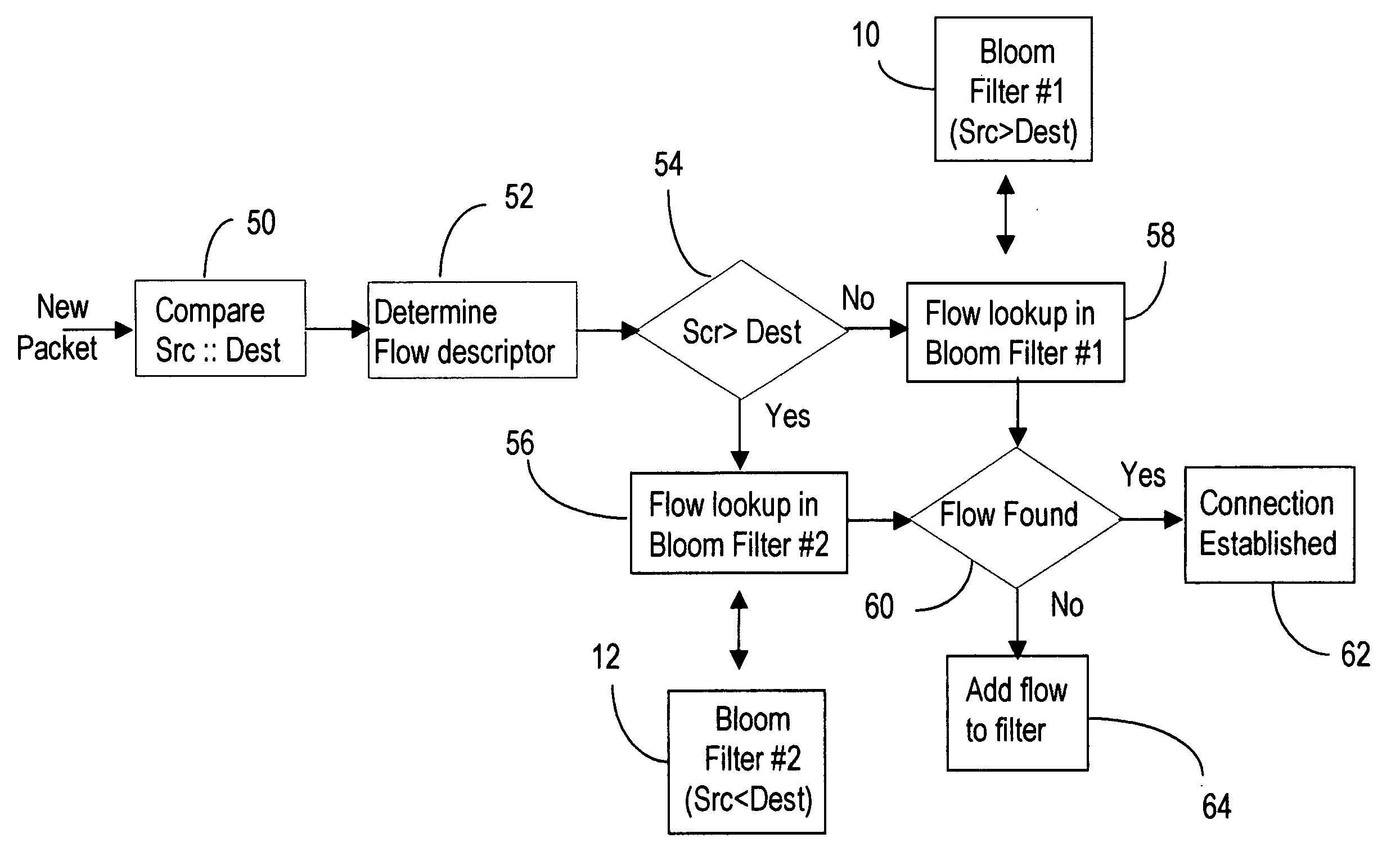
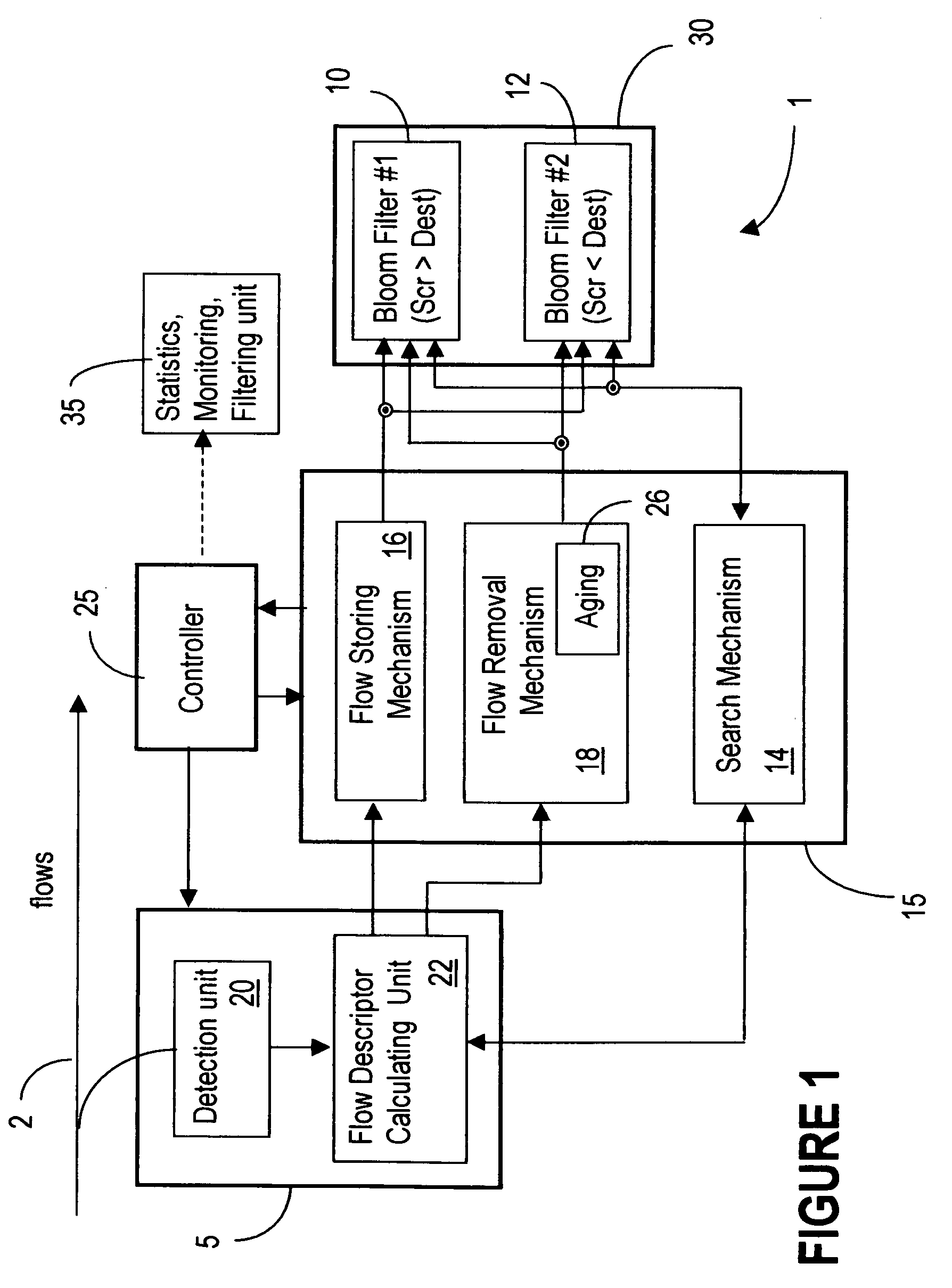
Symmetric Connection Detection (SCD) is a method of detecting when a connection has been fully established in a resource-constrained environment, and works in high-speed routers, at line speed. Many network monitoring applications are only interested in connections that become fully established, so other connection attempts, such as port scanning attempts, simply waste resources if not filtered. SCD filters out unsuccessful connection attempts using a simple combination of Bloom filters to track the state of connection establishment for every flow in the network. Unsuccessful flows can be filtered out to a very high degree of accuracy, depending on the size of the bloom filter and traffic rate. The SCD methodology can also easily be adapted to accomplish port scan detection, and to detect or filter other types of invalid TCP traffic.
Owner:ALCATEL LUCENT SAS
System, method and computer program product for improved efficiency in network assessment utilizing a port status pre-qualification procedure
ActiveUS7003561B1Minimize durationMemory loss protectionError detection/correctionComputer sciencePort scan
A system, method and computer program product are provided for minimizing the duration of a risk-assessment scan. Initially, a plurality of risk-assessment modules are selected each including vulnerability checks associated with a risk-assessment scan. Thereafter, a first set of ports is determined. Such first set of ports is required for communicating with network components subject to the risk-assessment modules associated with the risk-assessment scan. A port scan is subsequently executed on the first set of ports. Based on such port scan, a second set of ports is determined which includes ports unavailable for communicating with the network components subject to the risk-assessment modules associated with the risk-assessment scan. The risk-assessment modules associated with the second set of ports may then be disabled to minimize the duration of the risk-assessment scan.
Owner:MCAFEE LLC
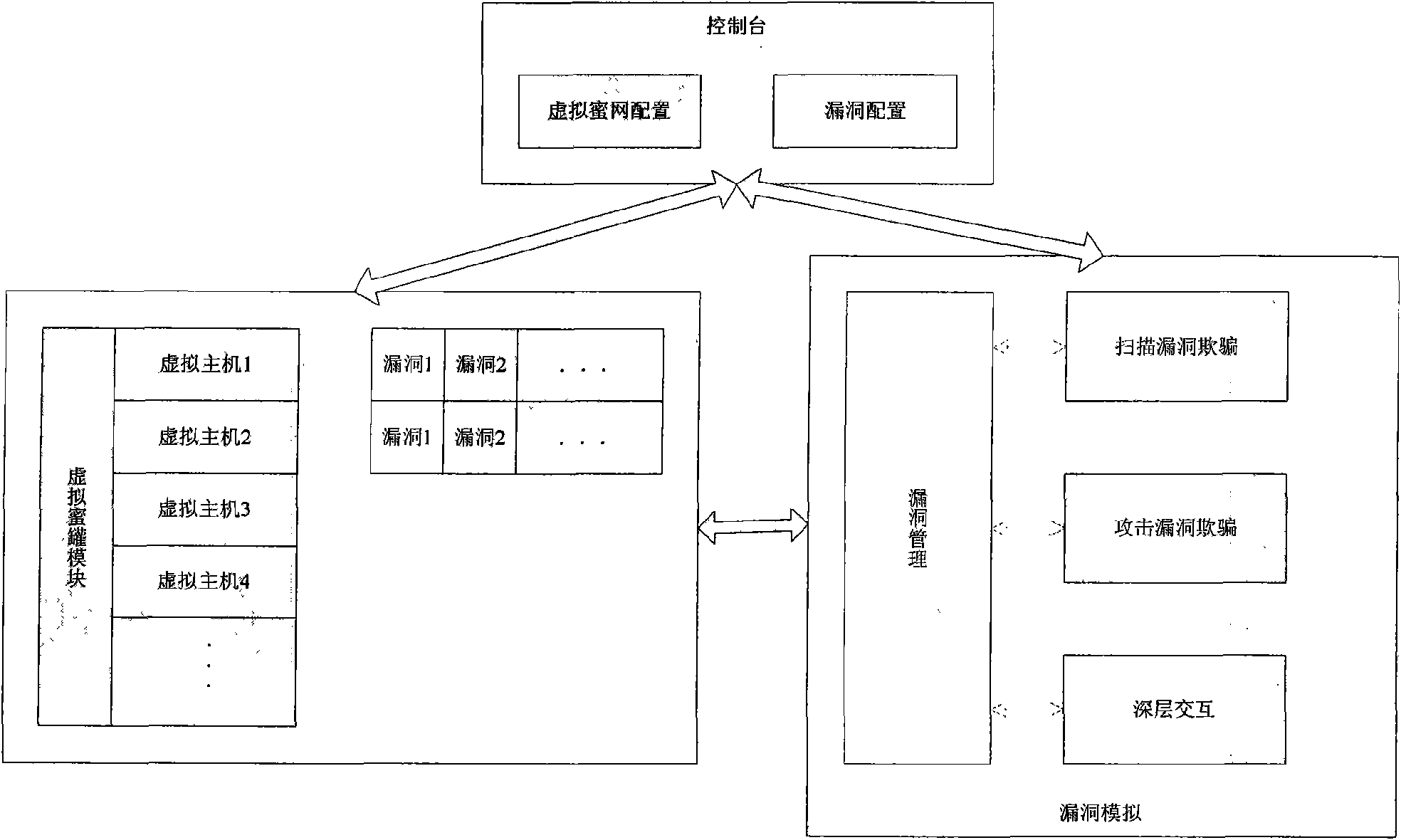
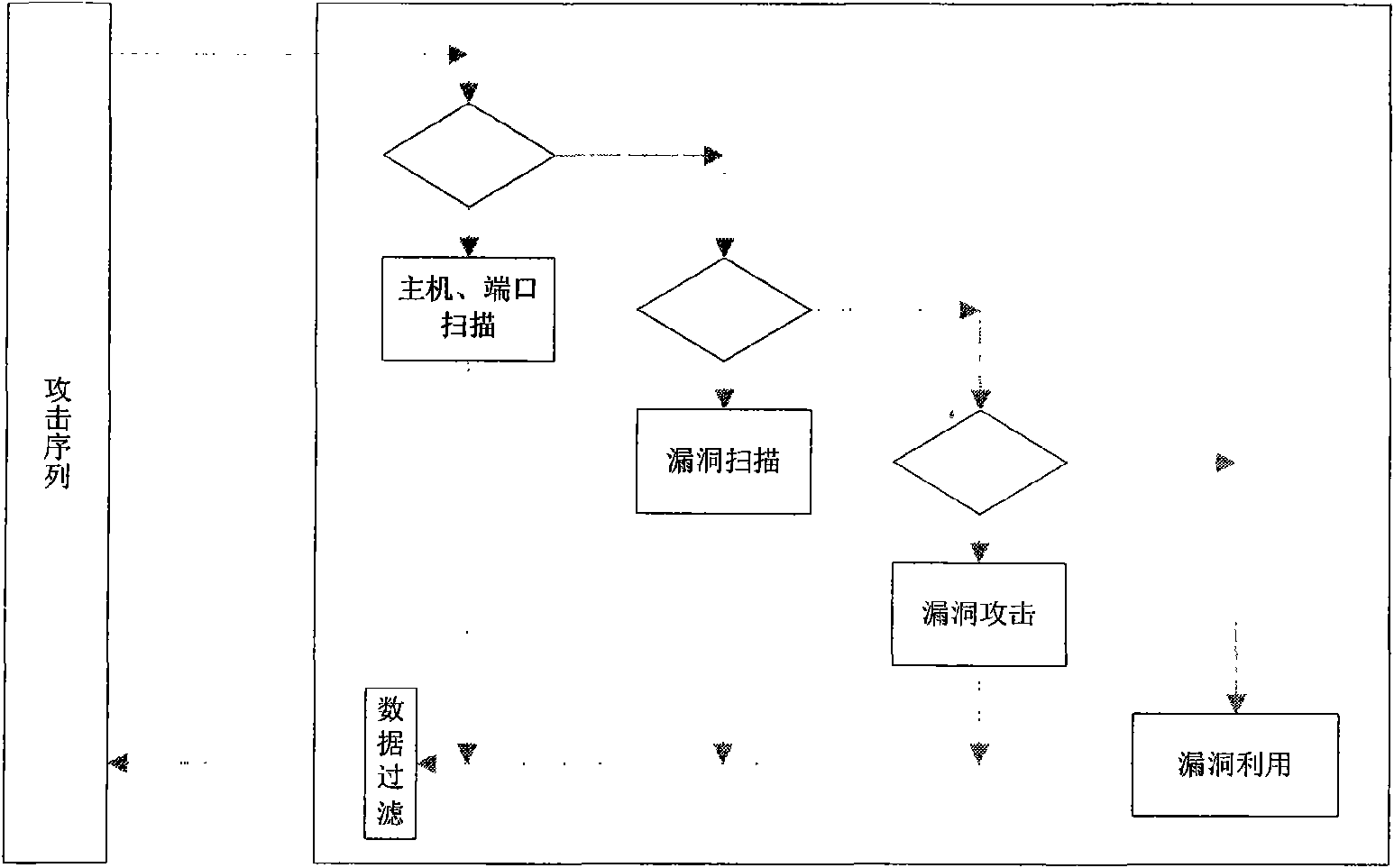
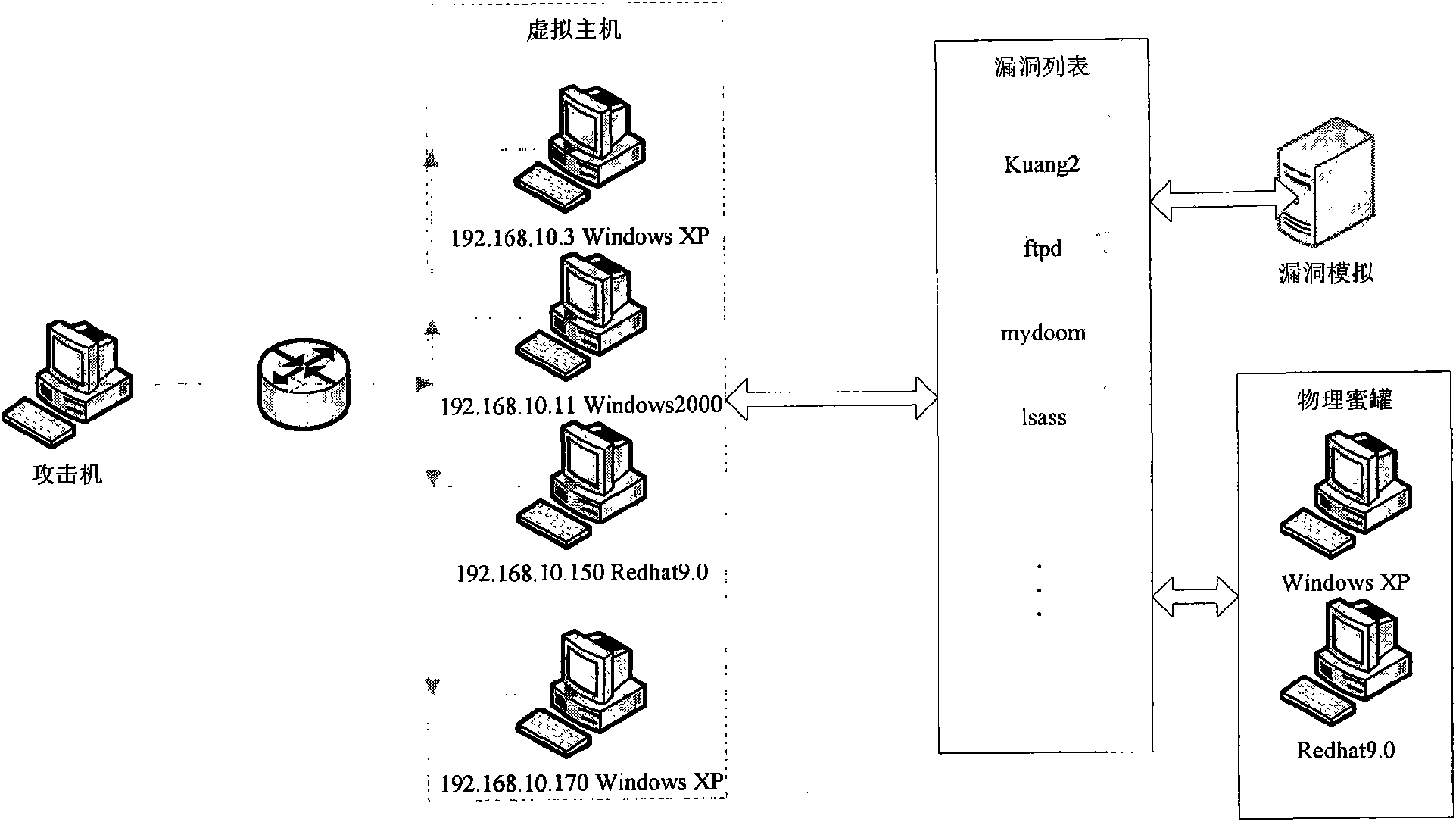
Vulnerability simulation overload honeypot method
InactiveCN101567887AAdd interactive functionComplete Attack DataData switching networksControl powerOperating system
The present invention discloses a vulnerability simulation overload honeypot method which comprises a host computer, a port scanning deception simulating module, a vulnerability scanning deception simulating module, a vulnerability scanning deception simulating module, a vulnerability attach deception simulating module, a data auditing module and a vulnerability utilizing module. When the attach sequence arrives at the simulated honeypot, a simulated honeypot system is used for processing according to the situation. When an attacker executes vulnerability scanning to the virtual host computer, the simulated honeypot responds and processes according to the vulnerability configuration information. Afterwards, these vulnerabilities are used for further attacking. Hereon, the simulated honeypot system transmits the vulnerability attack data flow to a vulnerability honeypot system. The vulnerability utilization attach of the attacker is processed and responded by a vulnerability attack simulating module. Finally, when the attacker successfully obtains the control power through the vulnerability attack, the attack data hereon is transmitted to a physical honeypot module. All attack processes and related data are recorded by a data auditing module for analyzing comprehensively. The method reduces the number of hardware devices in the honeynet and reduces the cost.
Owner:中国人民解放军总参谋部第五十四研究所 +2
Port scanning method and device, port scanning detection method and device, port scanning system, computer program and computer program product
InactiveUS20070044155A1Create efficientlyImprove reliabilityMemory loss protectionError detection/correctionComputer hardwarePort scan
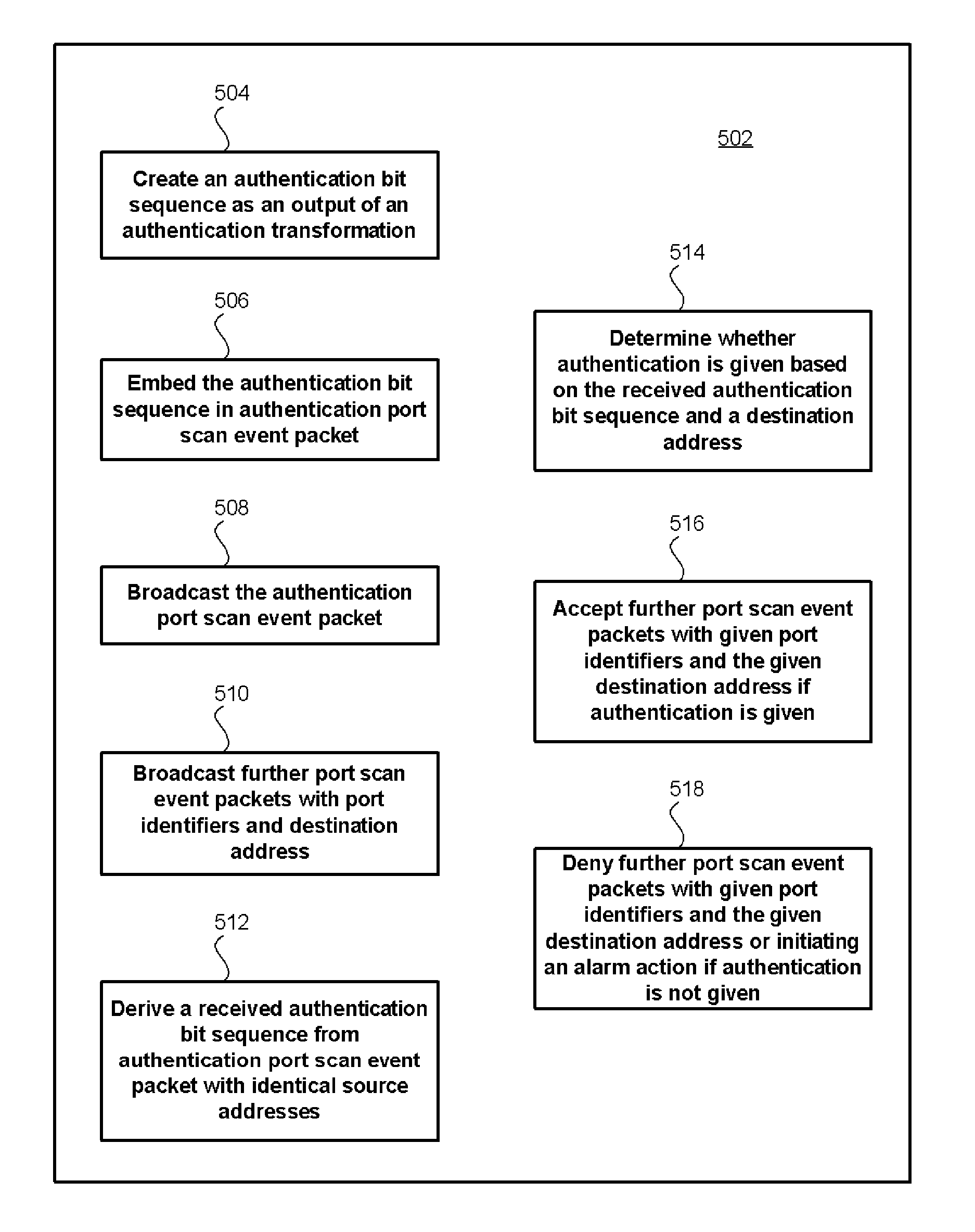
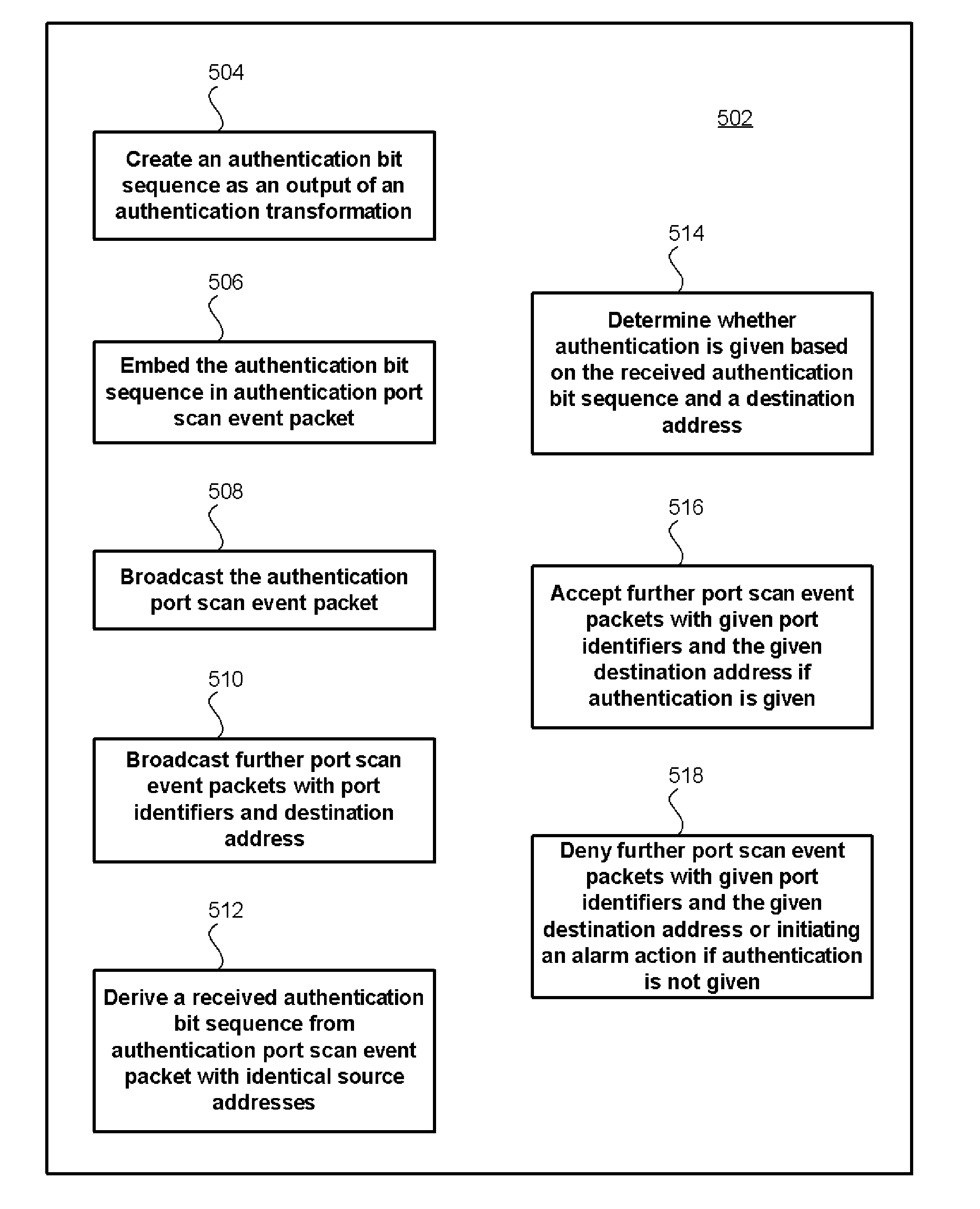
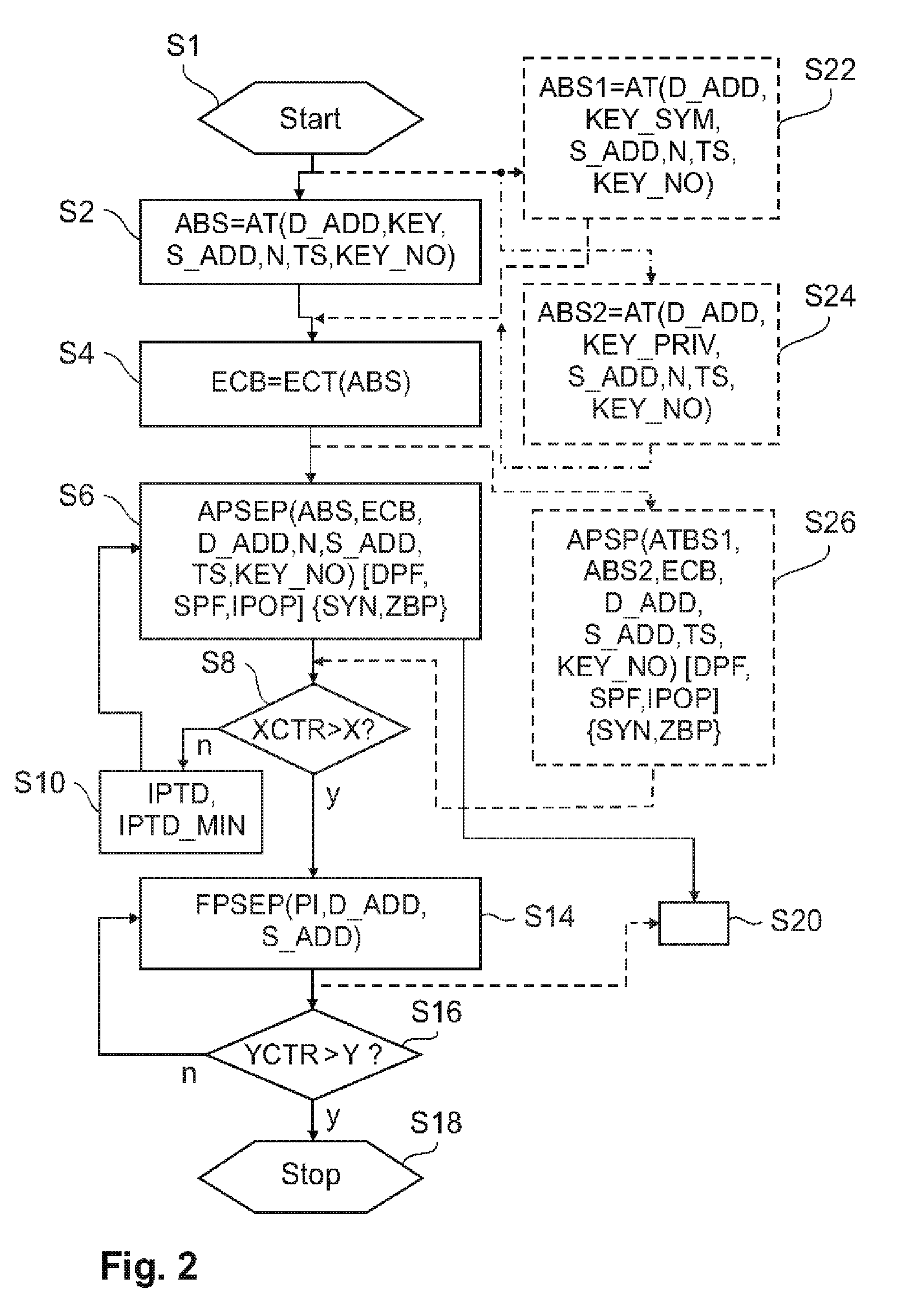
For port scanning an authentication bit sequence is created as an output of an authentication transformation, the authentication transformation having as input at least a given destination address and a given secret key. The authentication bit sequence is embedded in at least one authentication port scan event packet comprising the given destination address. At least one authentication port scan event packet is broadcast. Then, further port scan event packets are broadcast with given port identifiers and the given destination address. For port scanning detection, a received authentication bit sequence is derived from a least one authentication port scan event packet with identical source and destination addresses. Further port scan event packets are accepted with given port identifiers and the given destination address if authentication is given.
Owner:IBM CORP
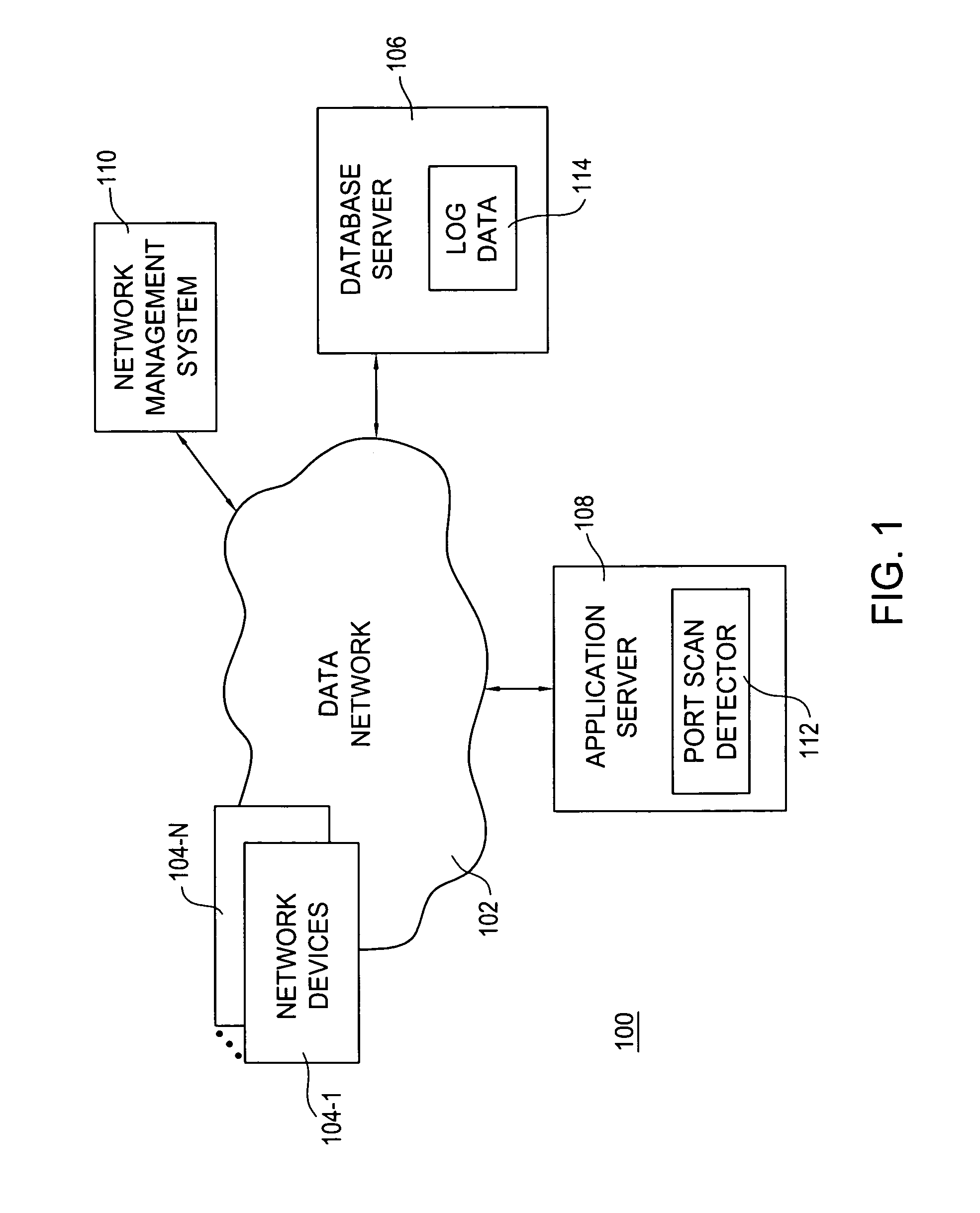
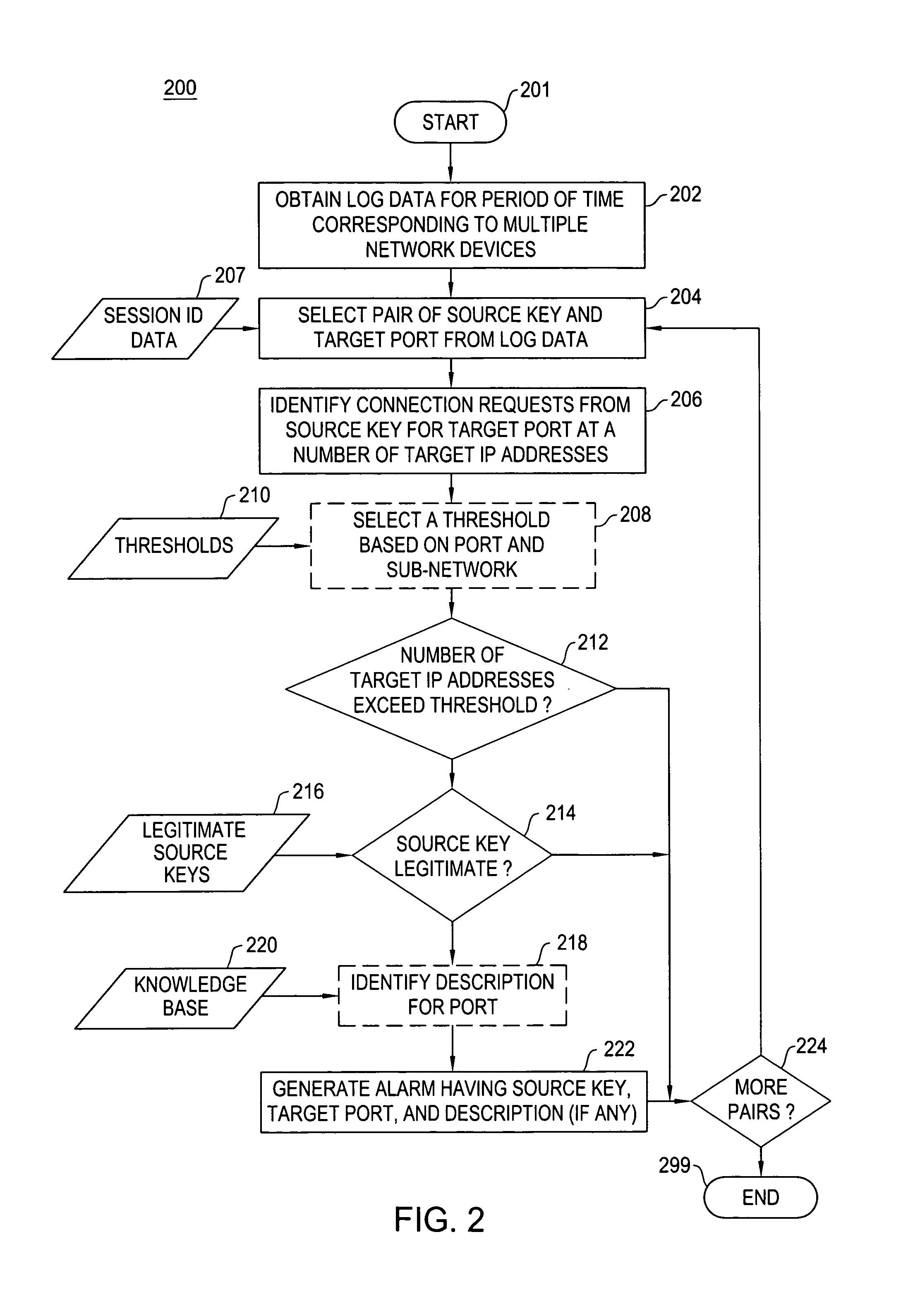
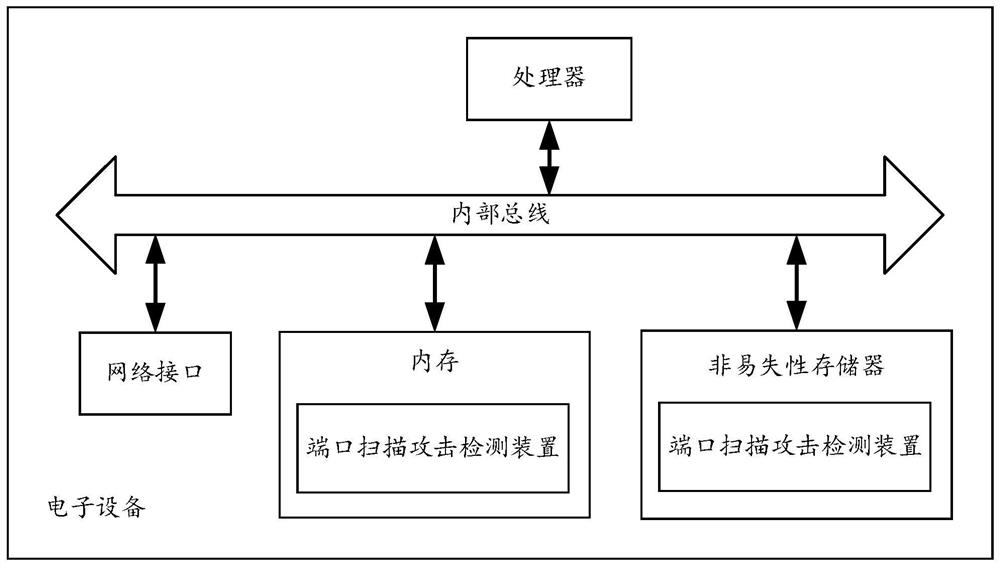
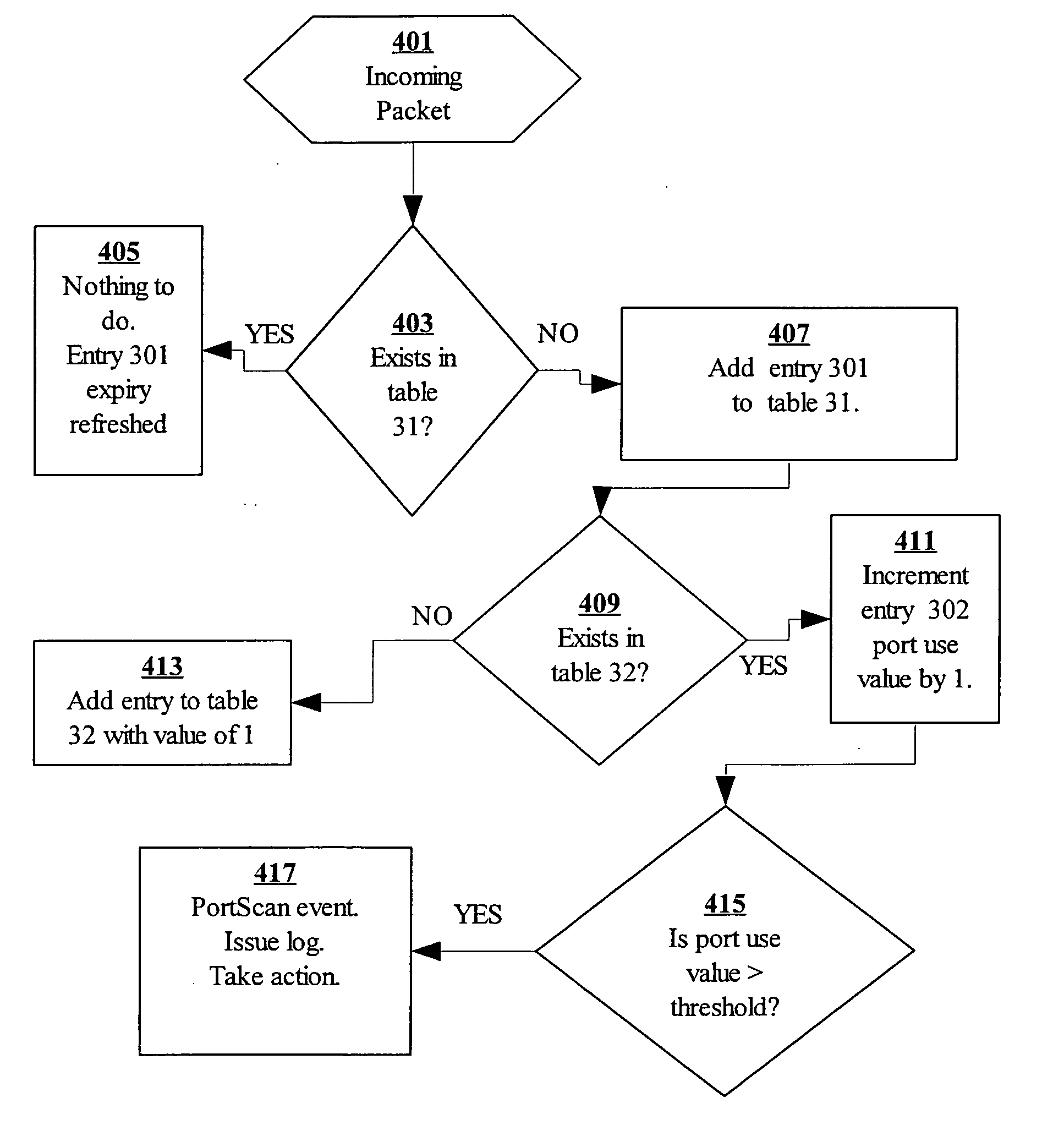
Method and apparatus for port scan detection in a network
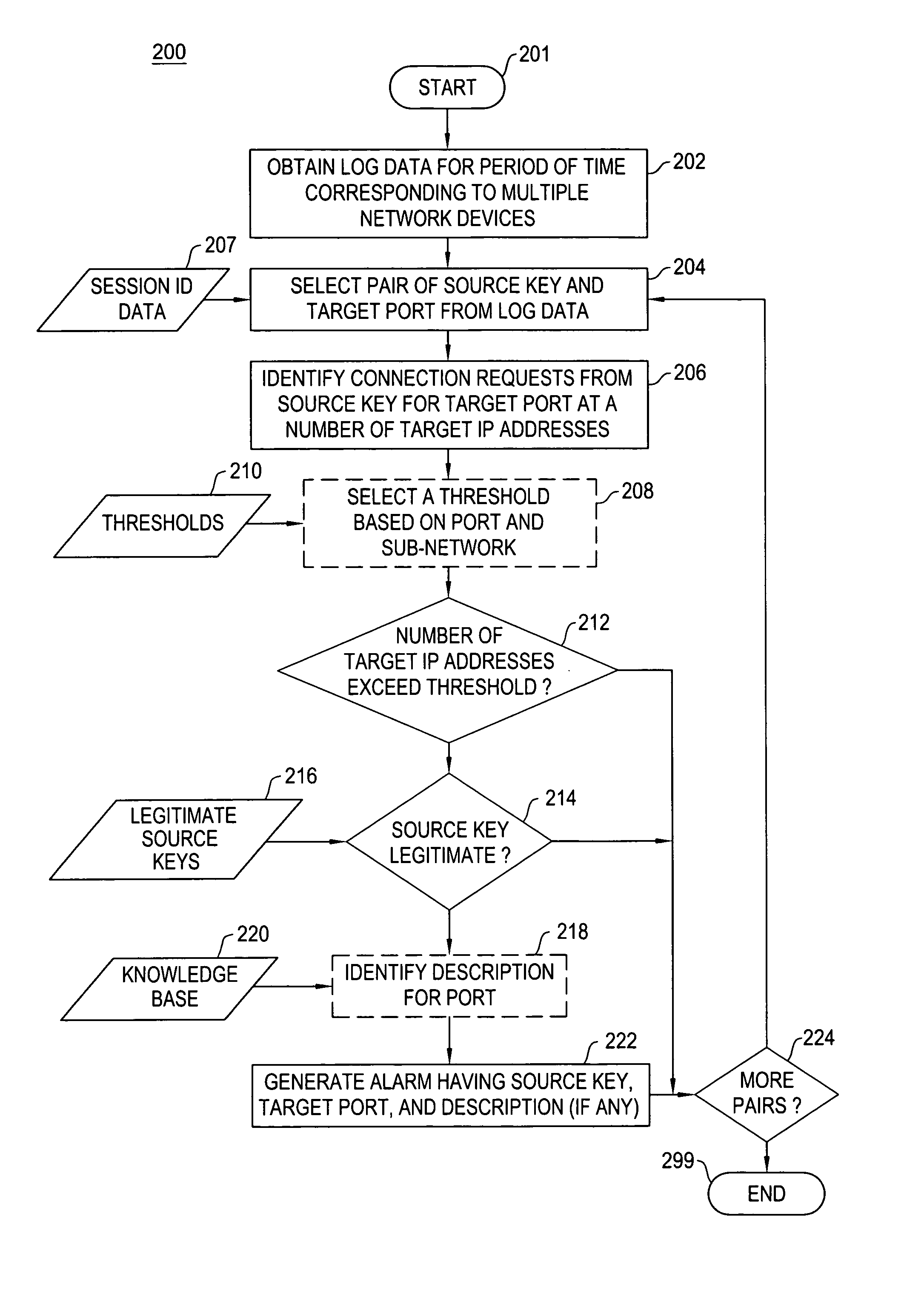
Method and apparatus for port sweep detection in a network is described. In one example, log data is obtained for a period of time. The log data is associated with a plurality of devices in the network. The log data is processed to identify connection requests from a source key for a port at a number of target internet protocol (IP) addresses. An alarm is generated if the number of target IP addresses associated with the connection requests from the source key exceeds a threshold.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
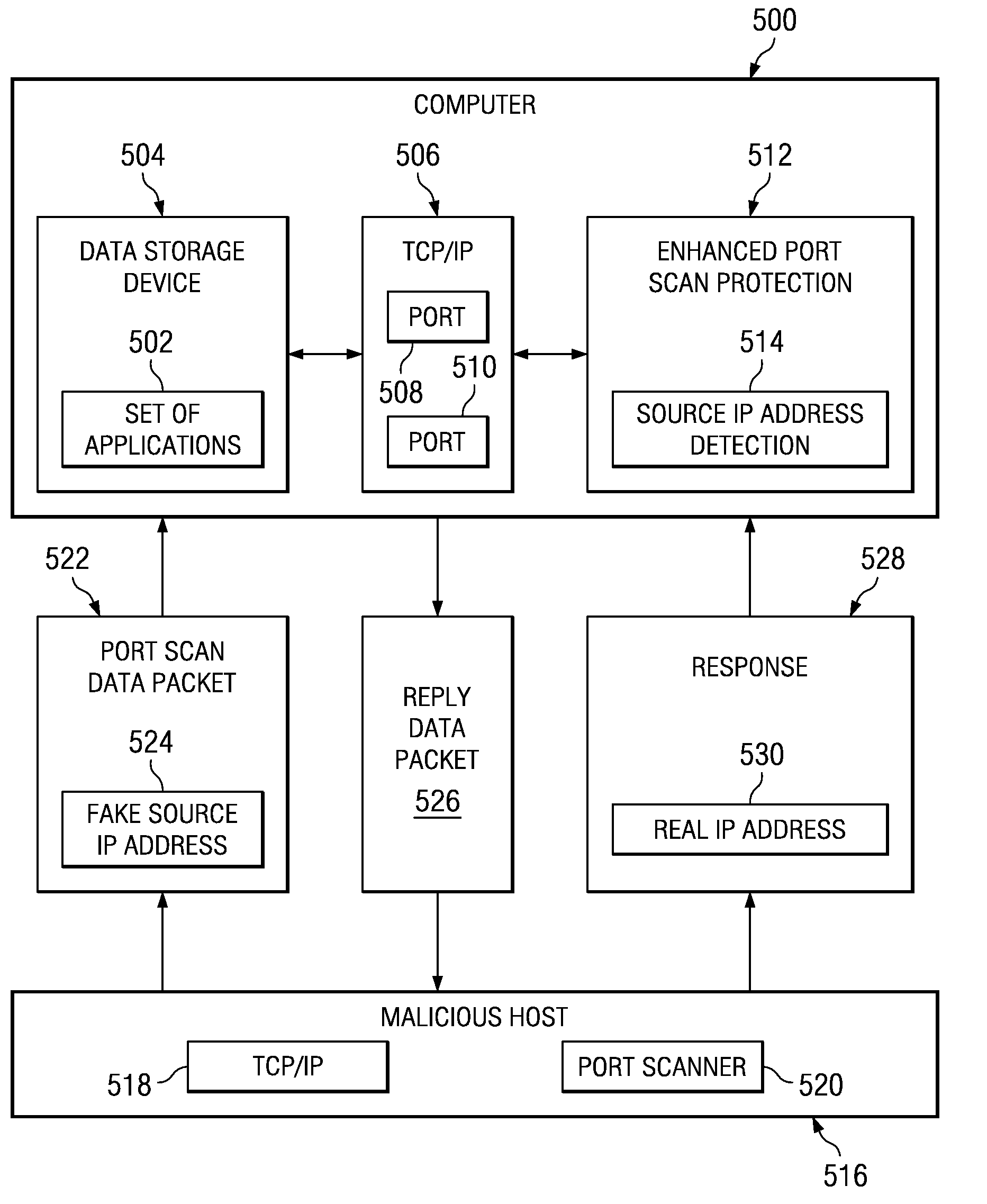
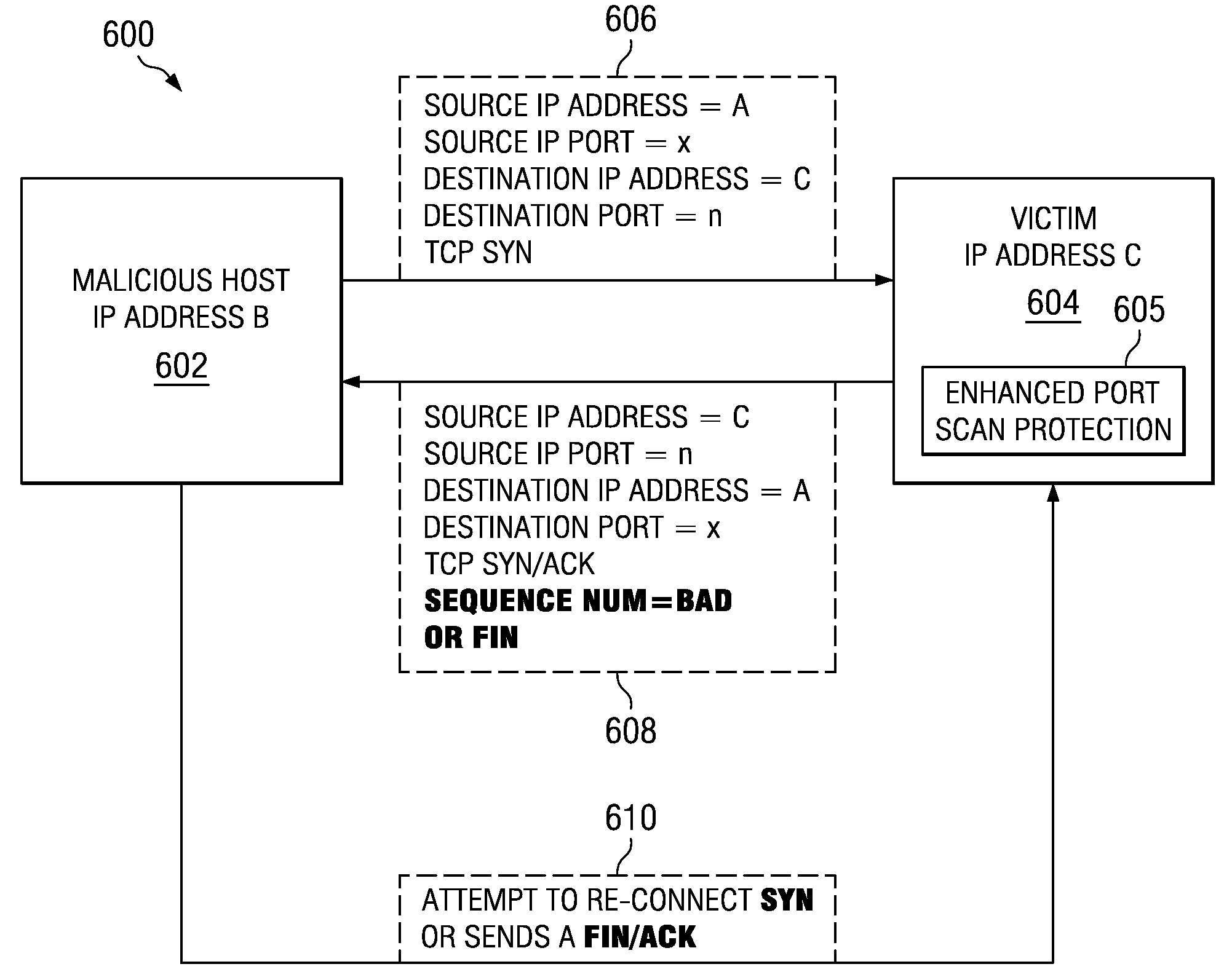
Method and apparatus for detecting port scans with fake source address
A computer implemented method, apparatus, and computer program product for port scan protection. A reply data packet having a modified transmission control protocol header is generated to form a modified reply data packet, in response to detecting a port scan. The modified reply data packet will illicit a response from a recipient of the modified data packet. The reply data packet is sent to a first Internet protocol address associated with the port scan. A second Internet protocol address is identified from a header of the response to the modified reply data packet. The second Internet protocol address is an actual Internet protocol address of a source of the port scan. All network traffic from the second Internet protocol address may be blocked to prevent an attack on any open ports from the source of the port scan.
Owner:IBM CORP
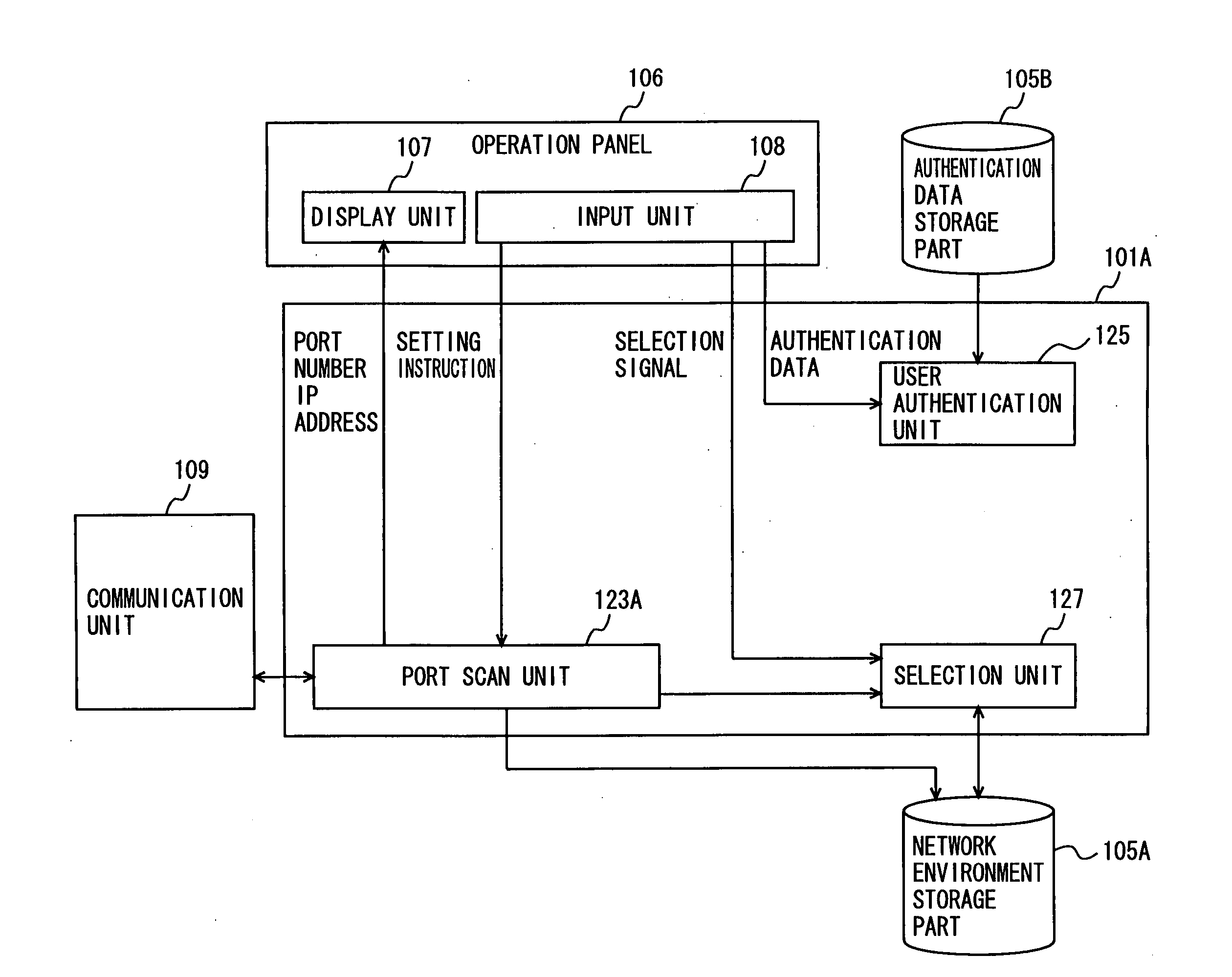
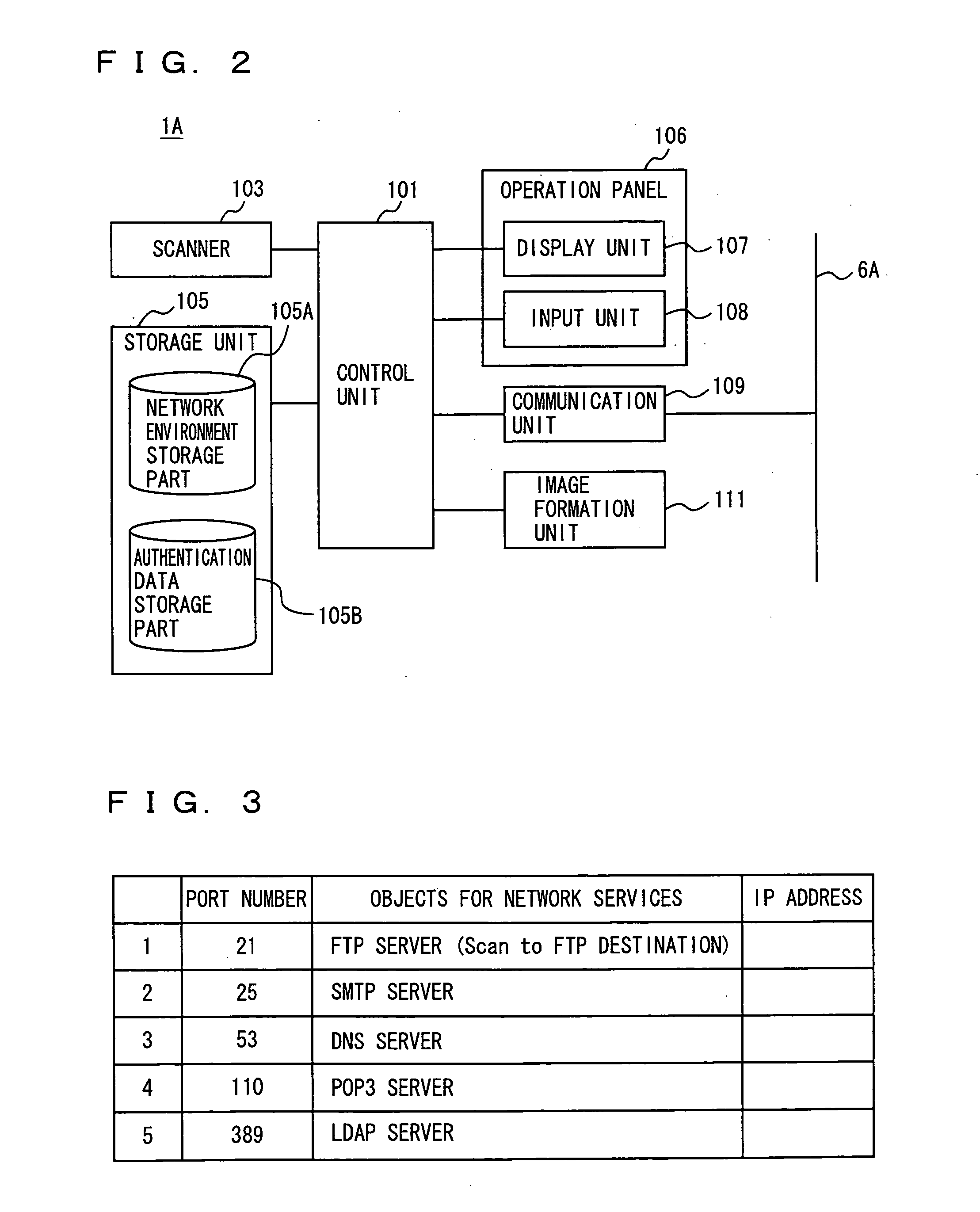
Communication device suitable for setting IP address of server connected to network, network parameter setting method and network parameter setting program product
InactiveUS20060056306A1Easy to set upOvercome problemsError preventionFrequency-division multiplex detailsIp addressPort scan
In order to easily set IP addresses required for communicating with apparatuses connected to a network, an MHP includes a port scan unit for acquiring, by port scanning, an IP address of a server having a predetermined port open from one of the servers connected to the network, and a network environment storage part for storing a set of acquired IP address and a port number of the predetermined port.
Owner:KONICA MINOLTA BUSINESS TECH INC
Port scanning method and device, port scanning detection method and device, port scanning system, computer program and computer program product
InactiveUS8245298B2Create efficientlyImprove reliabilityMemory loss protectionError detection/correctionComputer hardwareComputer science
For port scanning an authentication bit sequence is created as an output of an authentication transformation, the authentication transformation having as input at least a given destination address and a given secret key. The authentication bit sequence is embedded in at least one authentication port scan event packet comprising the given destination address. At least one authentication port scan event packet is broadcast. Then, further port scan event packets are broadcast with given port identifiers and the given destination address. For port scanning detection, a received authentication bit sequence is derived from a least one authentication port scan event packet with identical source and destination addresses. Further port scan event packets are accepted with given port identifiers and the given destination address if authentication is given.
Owner:IBM CORP
Techniques for analyzing network vulnerabilities
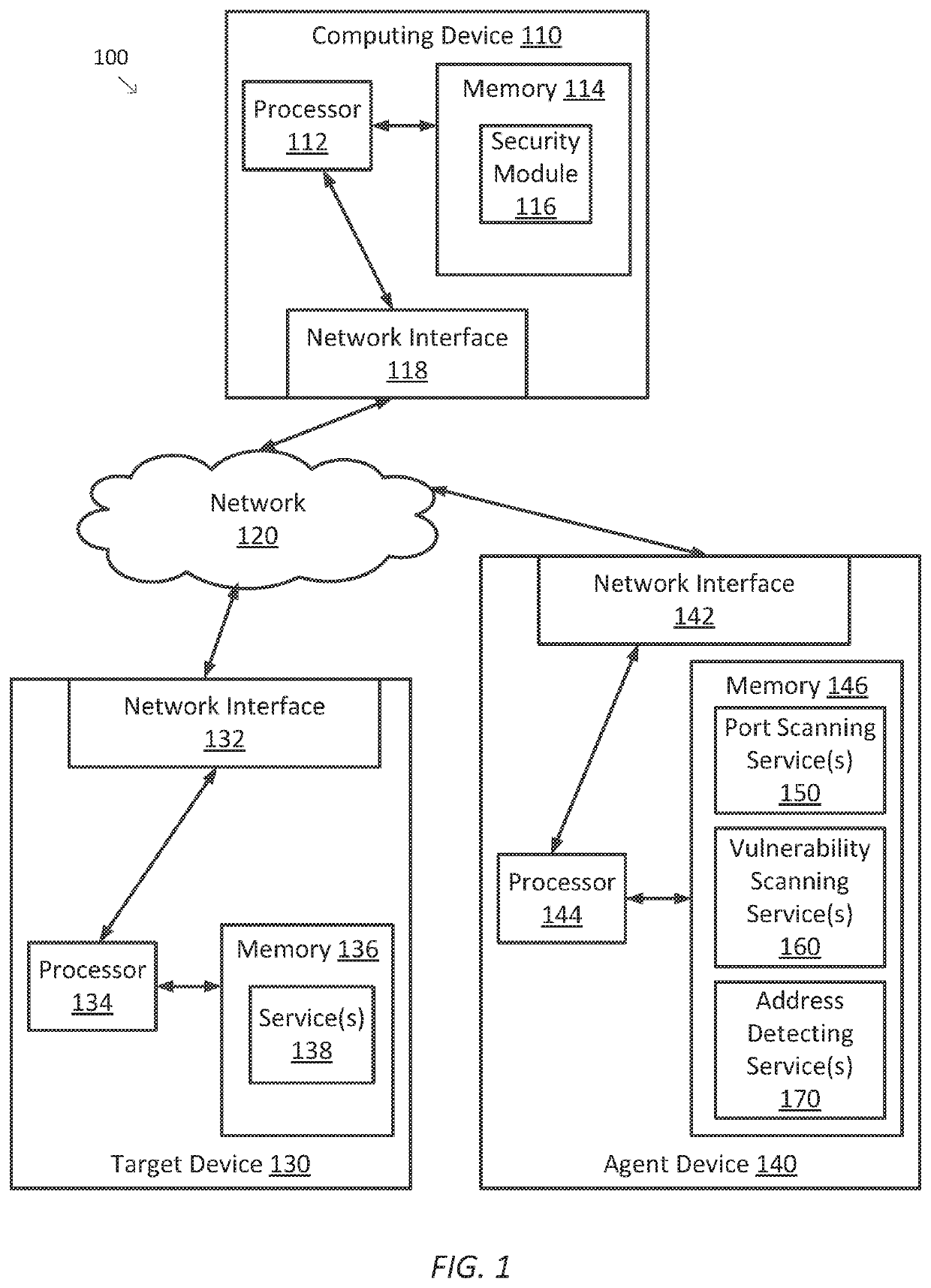
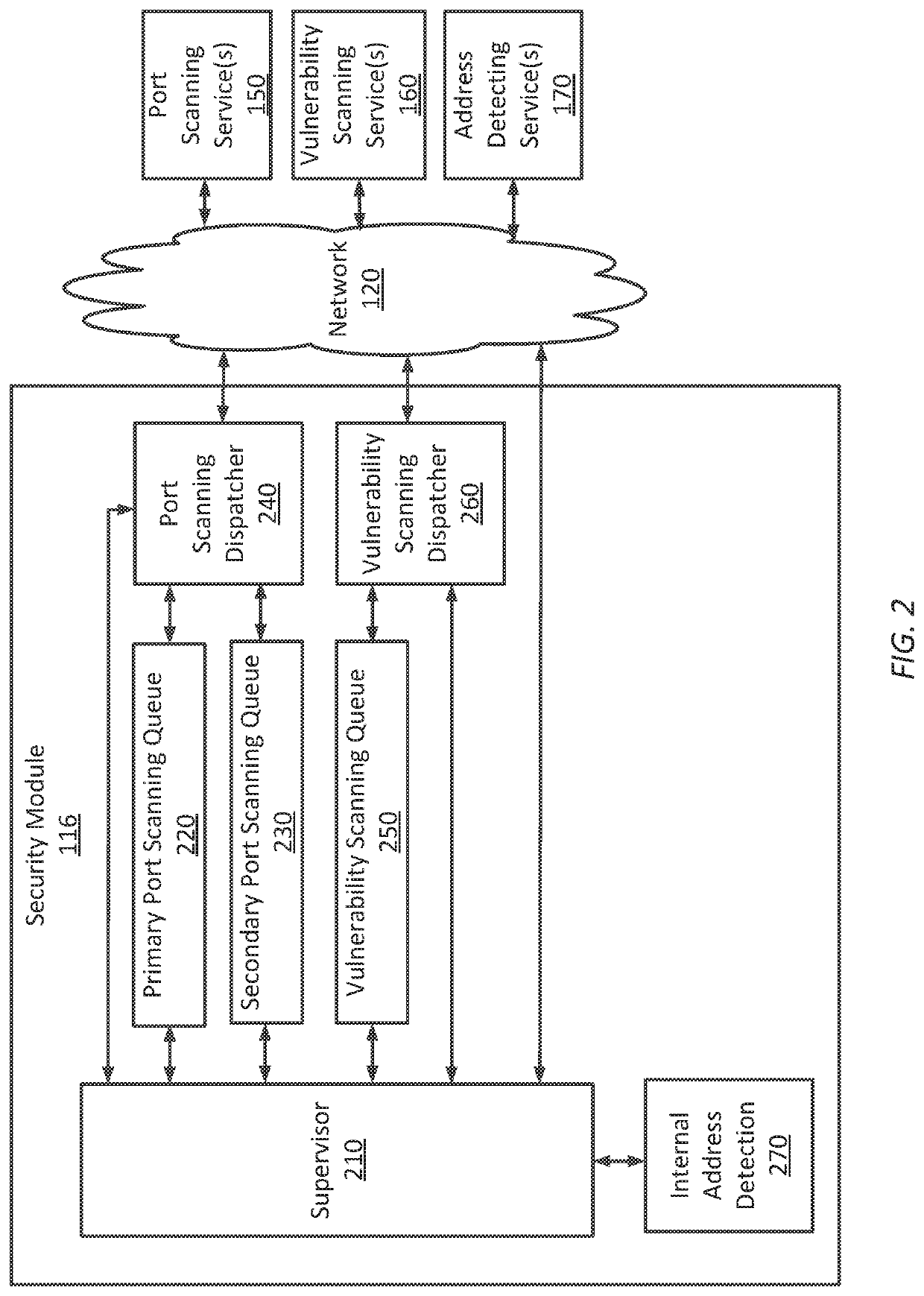
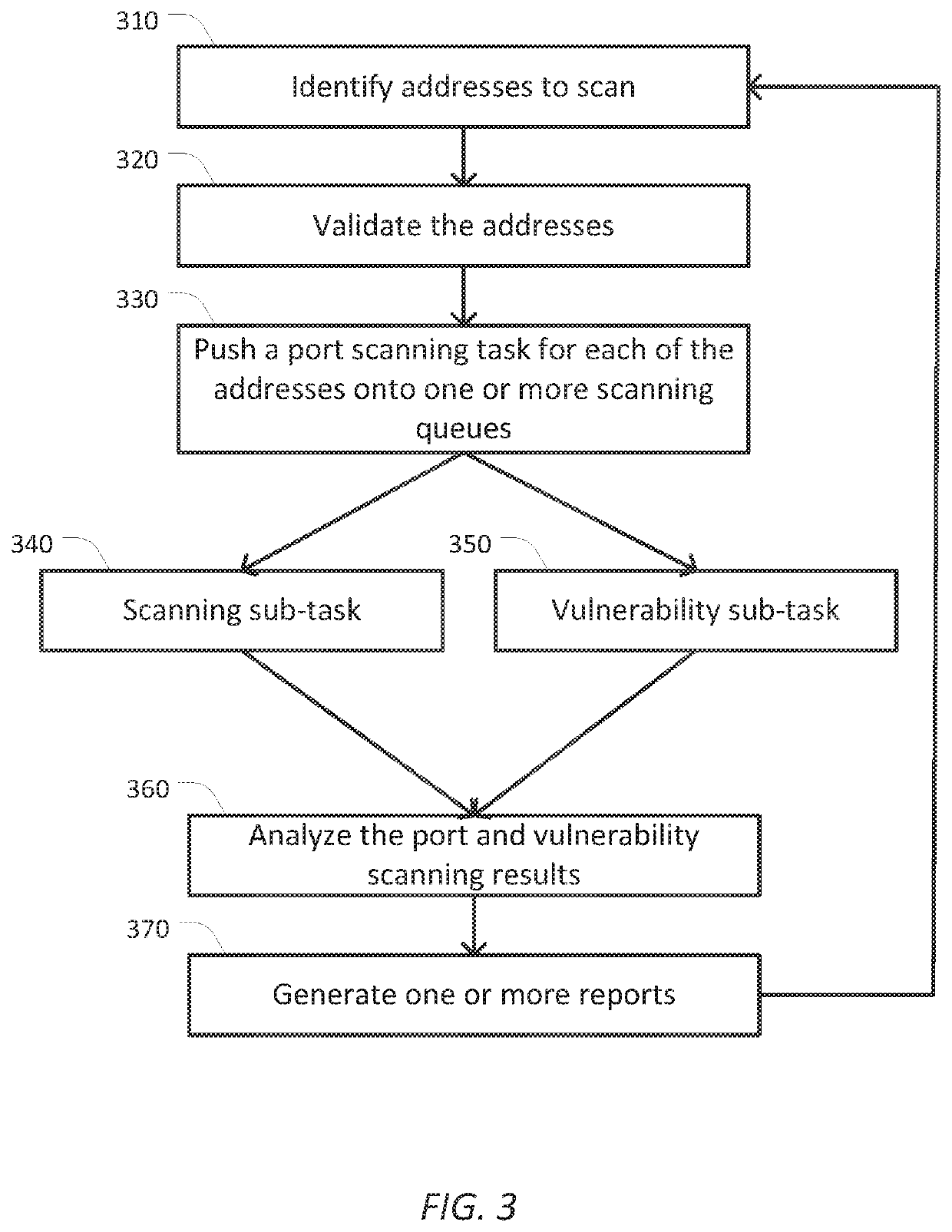
One embodiment of the present disclosure sets forth a technique for analyzing network vulnerabilities. The technique includes determining an address for each target device included in a plurality of target devices; for each target device, assigning a port scanning task to an associated port scanning service, the port scanning task being associated with the target device via the address of the target device; for each port scanning task, receiving a port scanning result from the port scanning service assigned to the port scanning task, the port scanning result including a list of open ports for the target device associated with the port scanning task; for each open port included in each port scanning result, assigning a vulnerability scanning task to an associated vulnerability service; receiving a vulnerability scanning result for each vulnerability scanning task; and generating a report based on the port scanning results or the vulnerability scanning results.
Owner:DISNEY ENTERPRISES INC
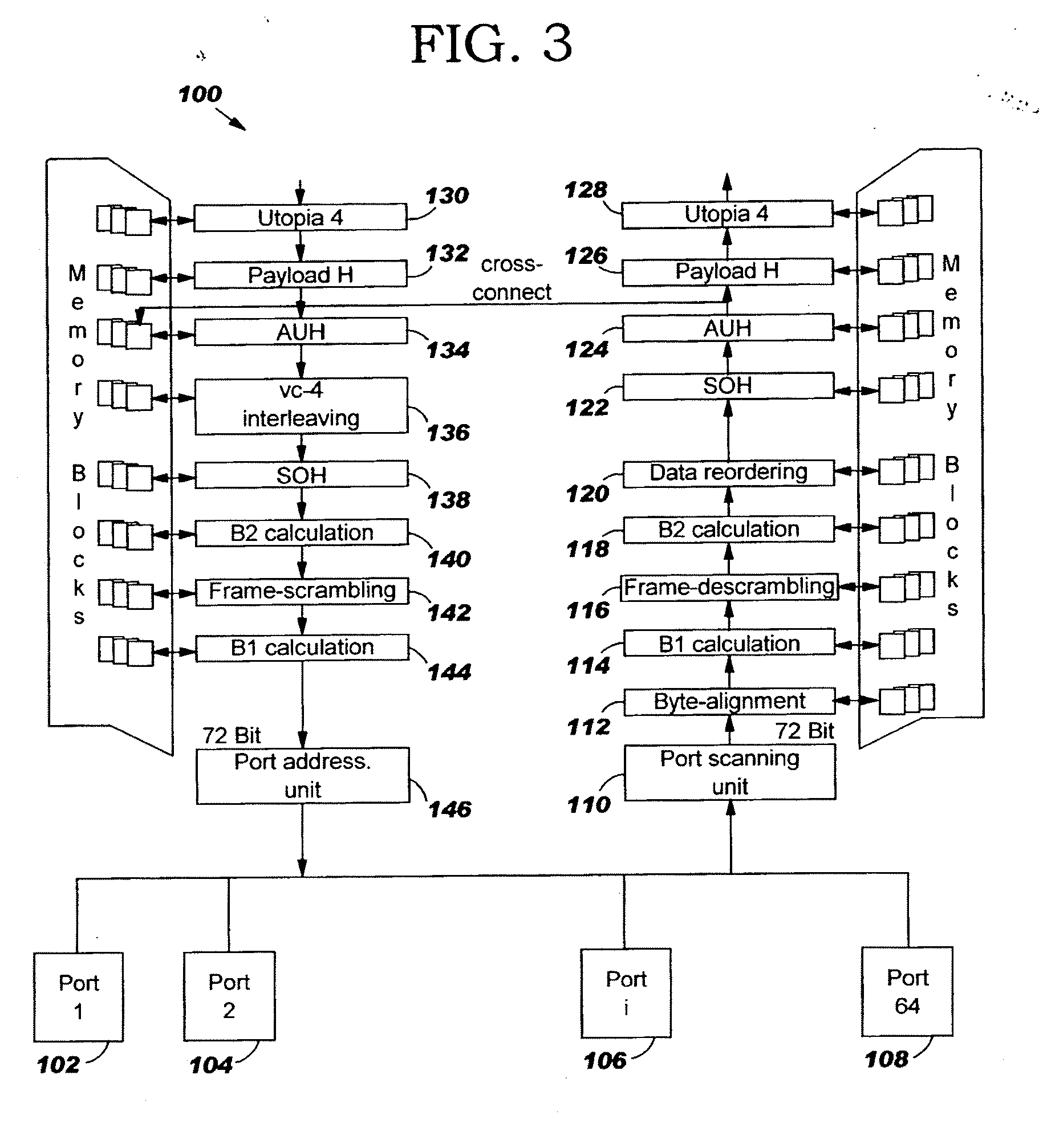
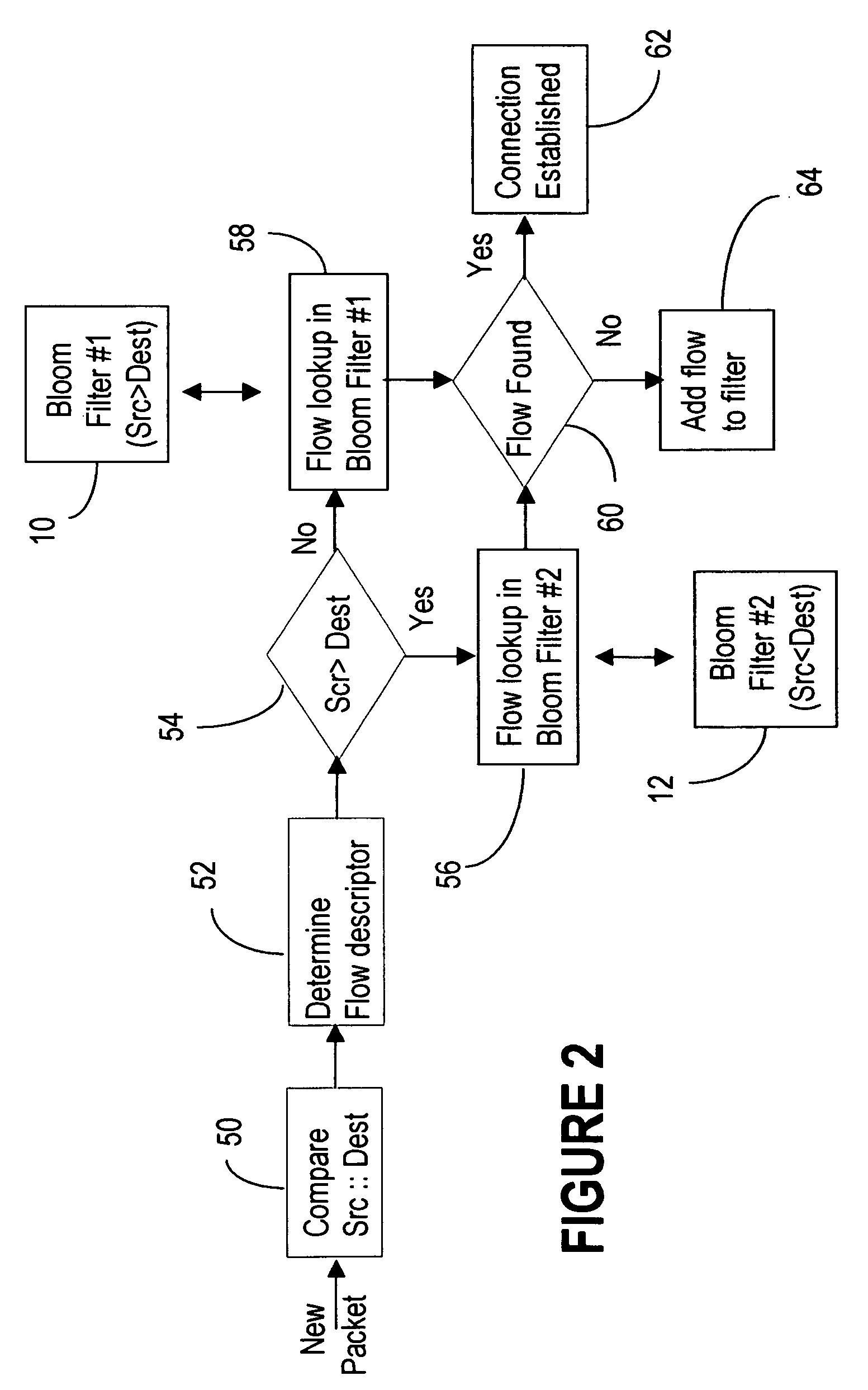
Stm-1 to stm-64 sdh/sonet framer with data multiplexing from a series of configurable I/O ports
InactiveUS20060285551A1Efficient combinationTime-division multiplexTransmissionData streamData signal
The present invention relates to a device for combining at least two data signals having an input data rate into a single data stream having an output data rate being higher than the input data rate for transmission on a shared medium or vice versa, particularly, to a single SDH / SONET framer capable of handling a large range of SDH / SONET frames from STM-i to STM-j with an aggregated total capacity corresponding to an STM-j frame where i and j are integers in the range from 1 to 64 or higher according to the STM-N definition of the SDH / SONET standards. More over, the present invention can also be extended to work with STS-1 as lowest range. STS-1 exists in SONET only not SDH and corresponds to a data rate of 51.5 Mb / s a third of the 156 Mb / s of STM-1. The device according to the present invention comprises at least two ports for receiving and / or sending said at least two data signals, a port snning unit for extracting data from the data signals received by said ports and / or synthesizing data to be transmitted via the ports, respectively, whereby said port scanning unit is configured to extract data from ports providing data streams having at least two different input data rates and / or to synthesize data to be transmitted via the ports taking data streams having at least two different data rates.
Owner:IBM CORP
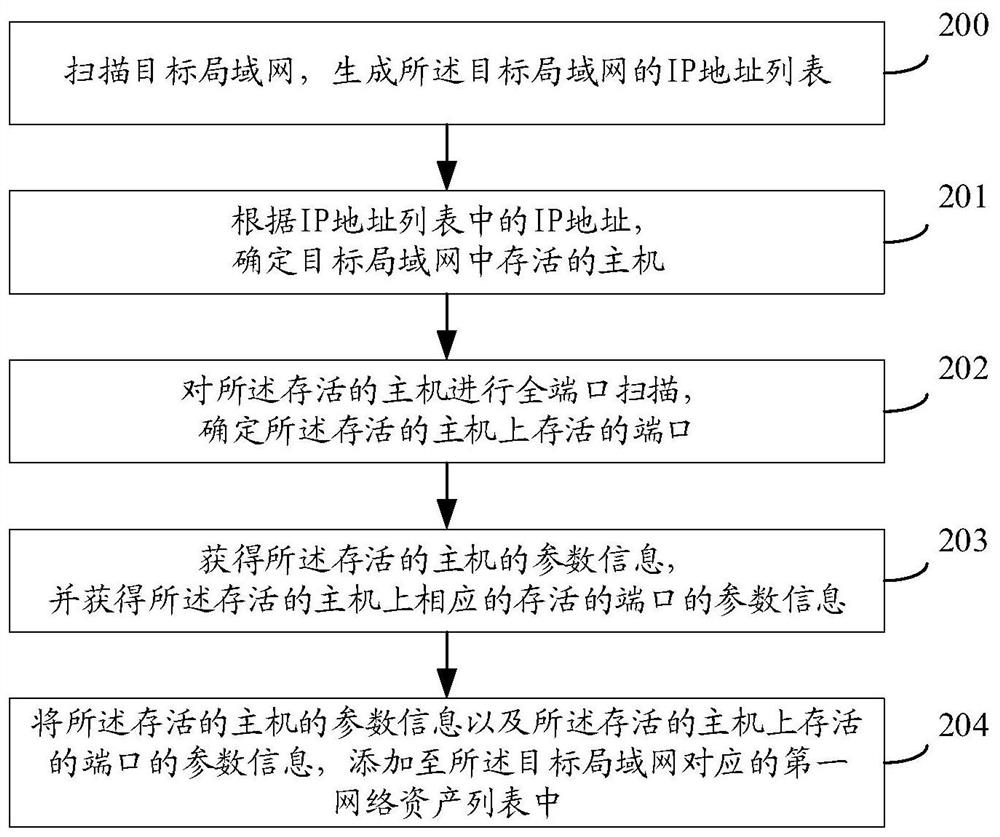
Network asset identification method and device, medium and equipment
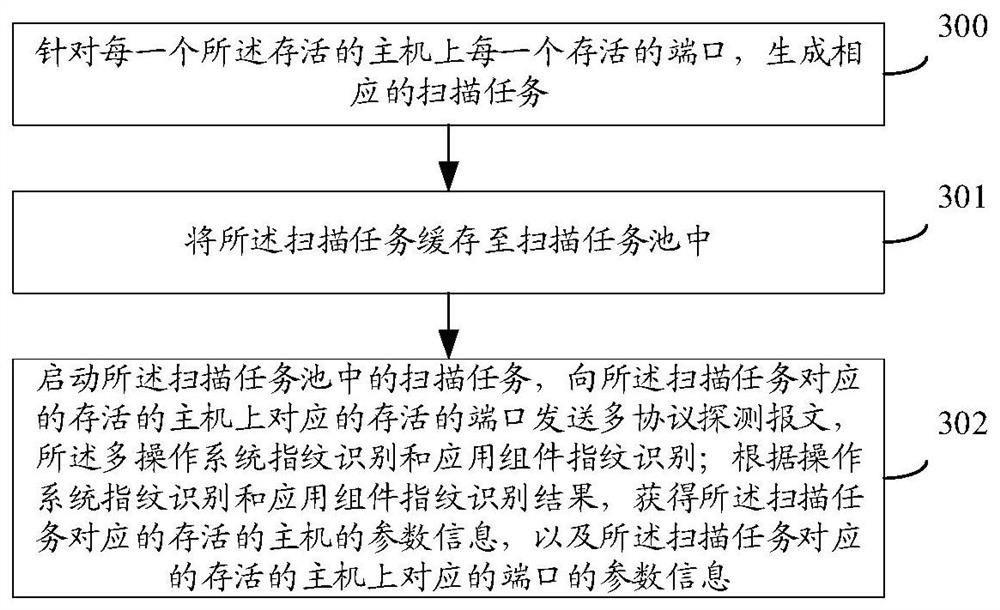
The invention provides a network asset identification method and device, a medium and equipment. The network asset identification method comprises the following steps: acquiring an IP address list ofa target local area network; determining a survival host in the target local area network according to the IP address in the IP address list; performing full-port scanning on the survival host, and determining a survival port on the survival host; obtaining parameter information of the survival host, and obtaining parameter information of a corresponding survival port on the survival host; and adding the parameter information of the survival host and the parameter information of the survivalport on the survival host to a first network asset list corresponding to the target local area network.Through the first network asset list corresponding to the target local area network, network operation and maintenance personnel can conveniently manage the network assets in the target local area network.
Owner:BEIJING GRIDSUM TECH CO LTD
Symmetric connection detection
InactiveUS7623466B2Alleviates totallyError preventionFrequency-division multiplex detailsComputer hardwareWire speed
Owner:ALCATEL LUCENT SAS
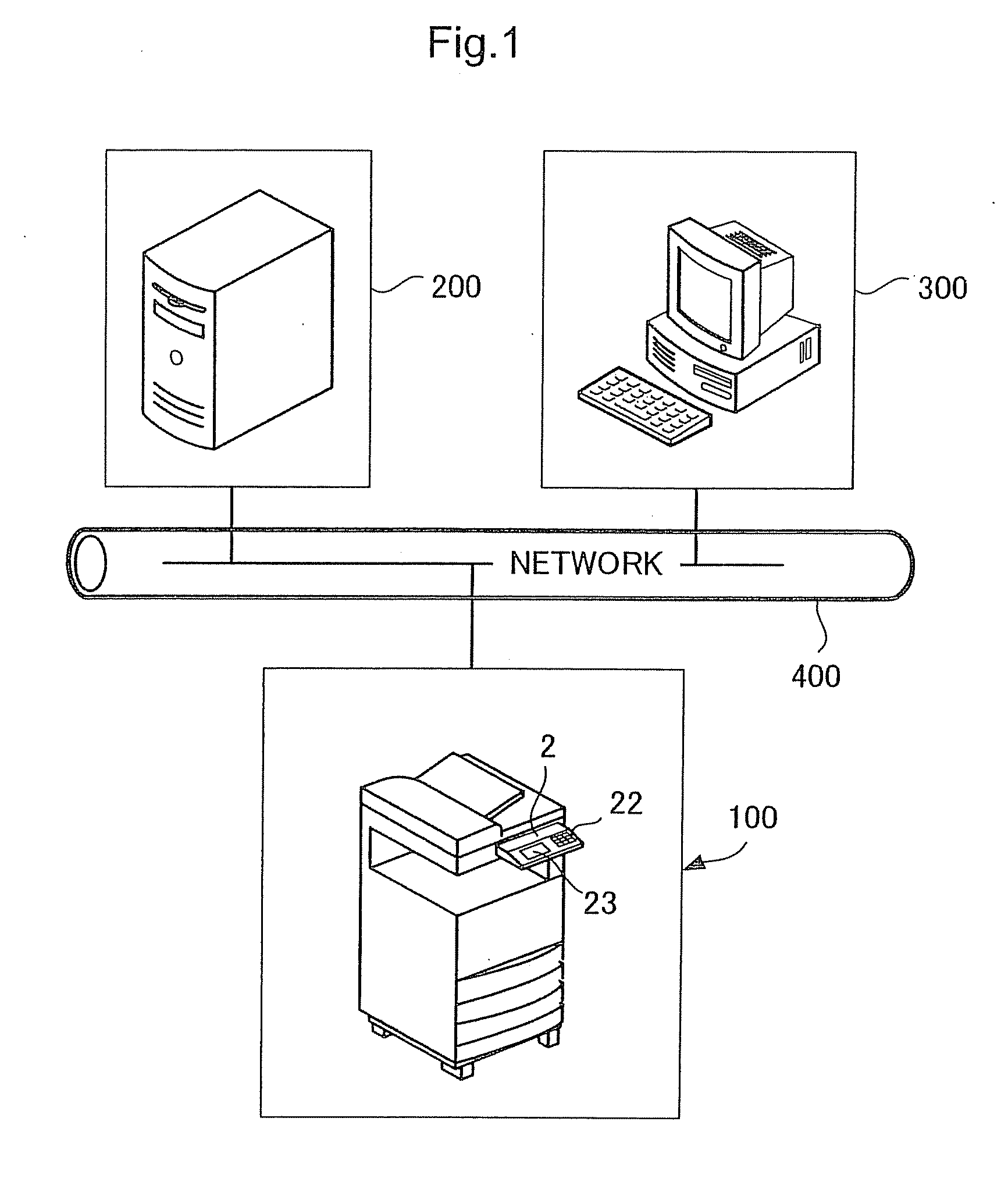
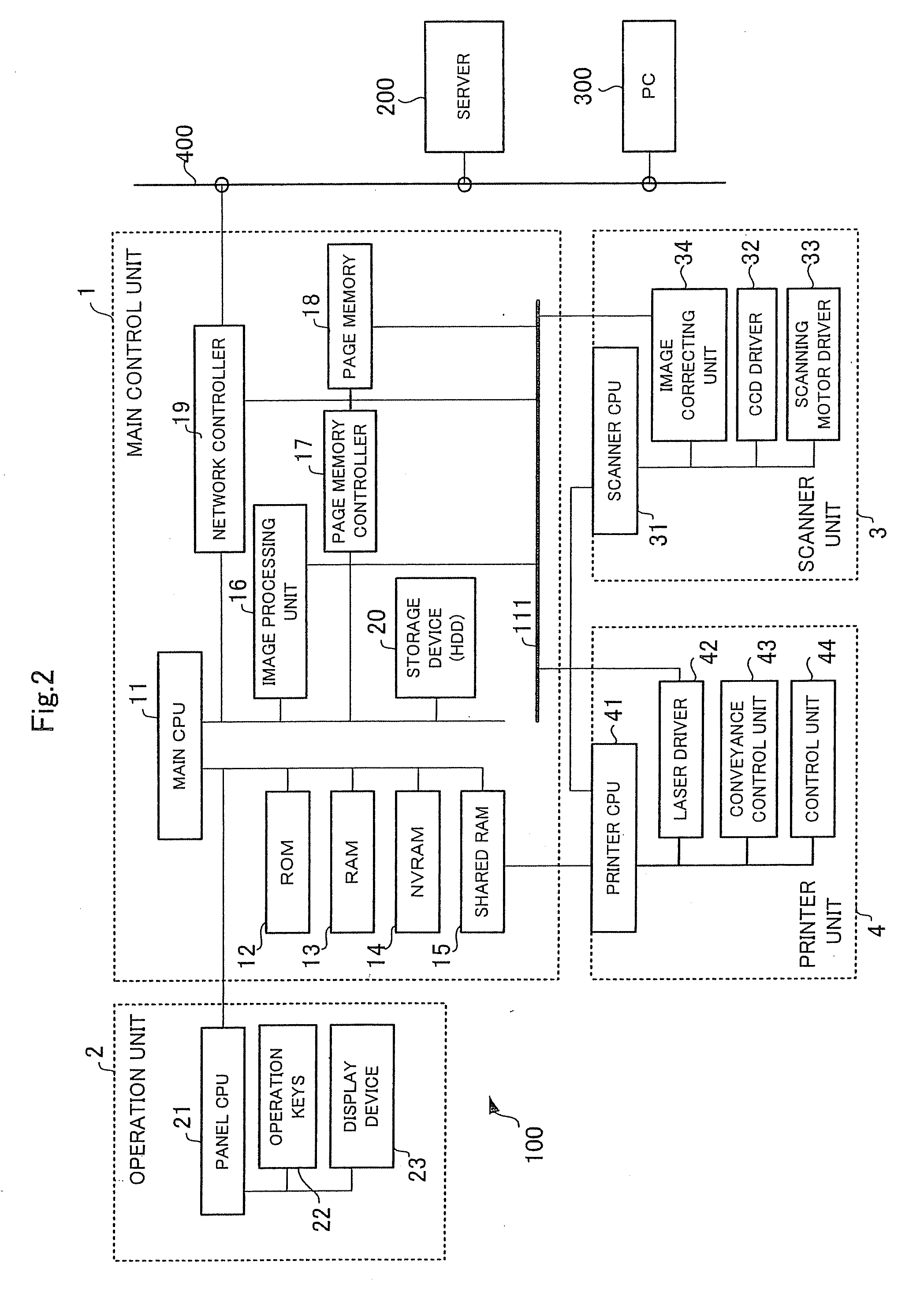
Client server system and image forming apparatus
InactiveUS20080180718A1Multiple digital computer combinationsNon-redundant fault processingNetwork connectionNetwork control
The invention provides an image forming apparatus connectable to a server via a network. The image forming apparatus includes a network controller for connecting the image forming apparatus to the network and a control unit capable of executing check processing for a server. At the time of the check processing for the server, the control unit transmits a connection request packet (SYN) to the server and performs port scan. The control unit checks a state of the server according to presence or absence of a response (ACK) from the server. When there is no response, the control unit reports a connection error to a user after elapse of an arbitrary timeout period set in the image forming apparatus.
Owner:KK TOSHIBA +1
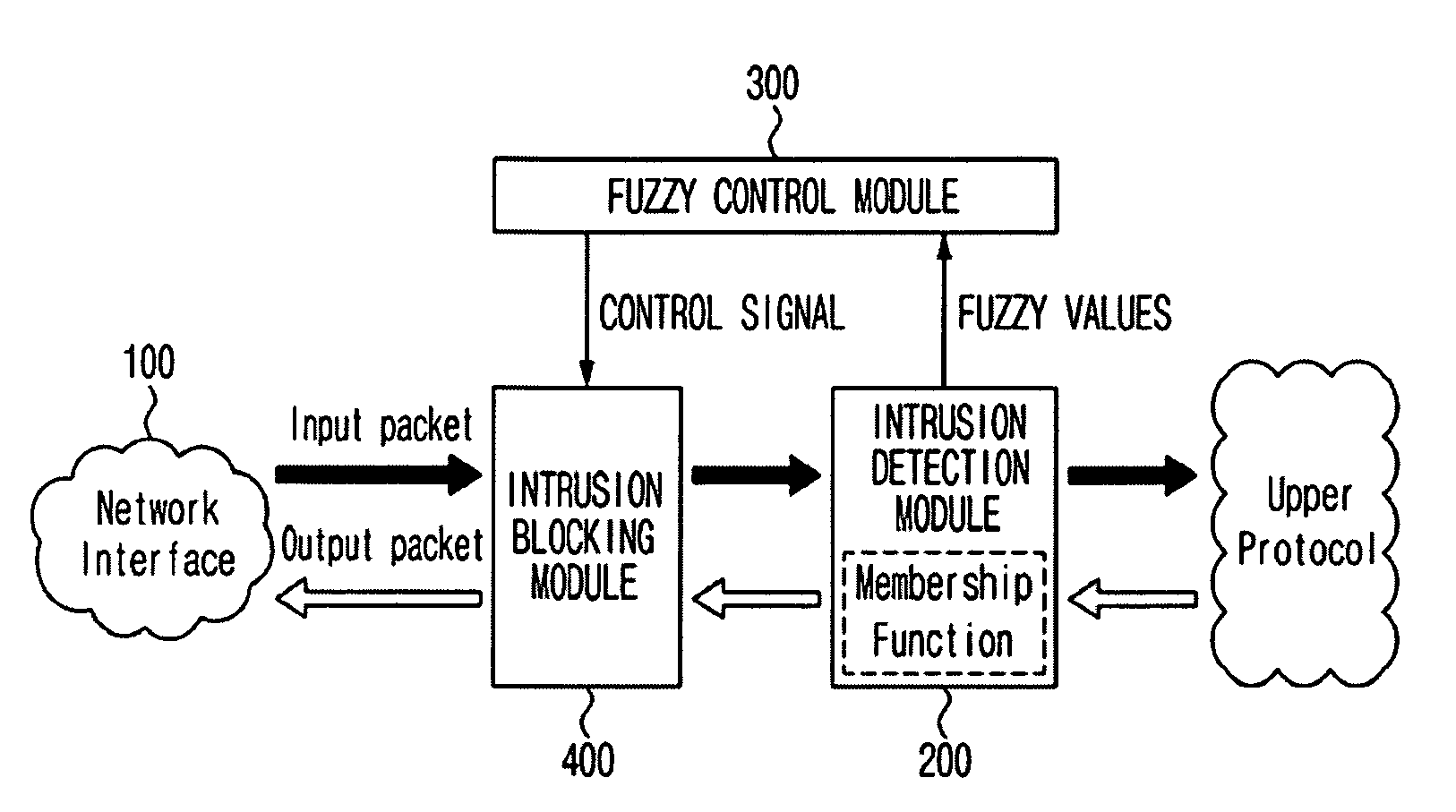
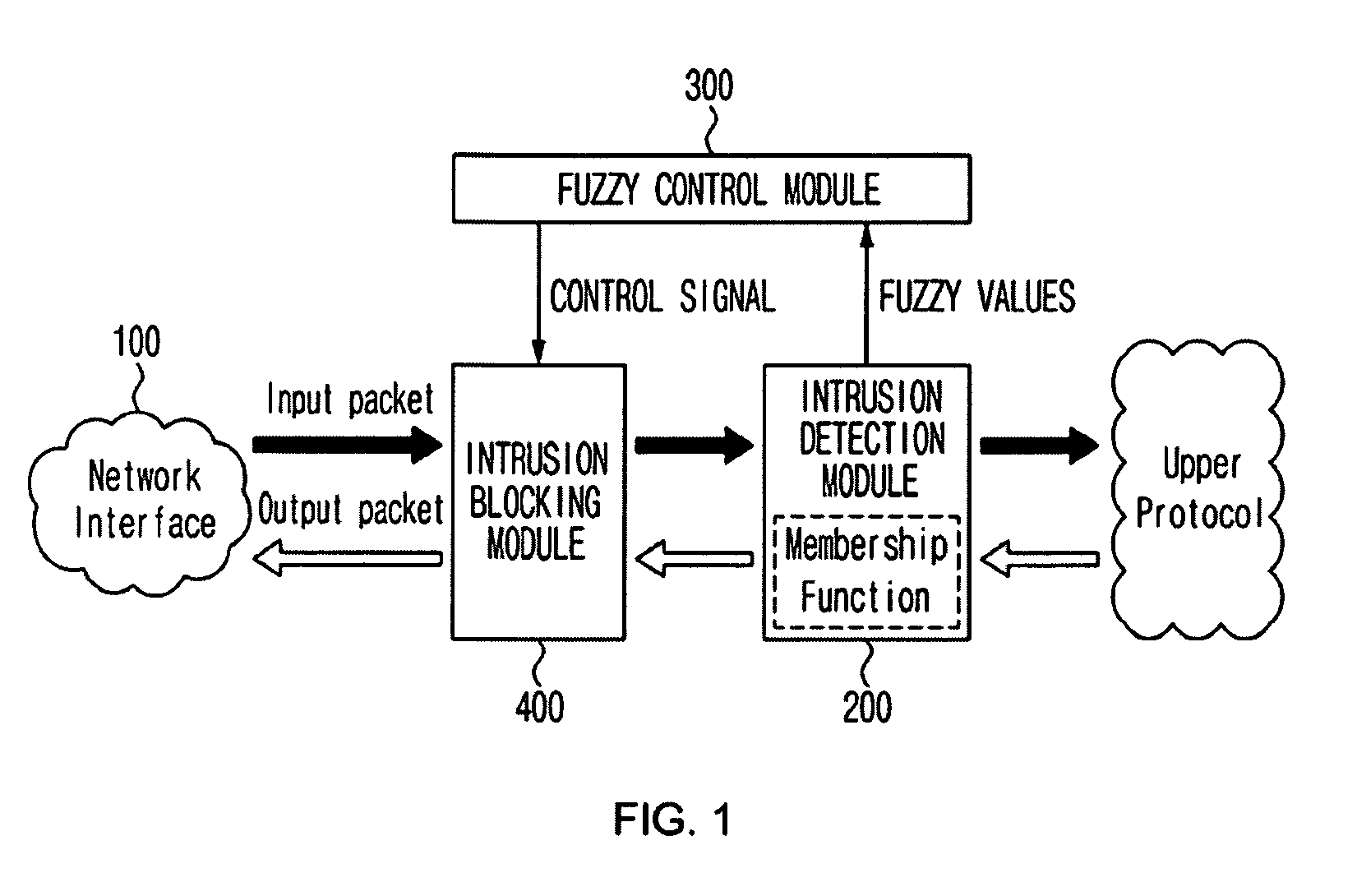
System and method for controlling abnormal traffic based on fuzzy logic
ActiveUS20090187989A1Easy to detectNot easy to detectNetwork traffic/resource managementMemory loss protectionTraffic capacityControl signal
A system for controlling abnormal traffic based on a fuzzy logic includes: an intrusion detection module for analyzing packets incoming from a network interface by means of a membership function defined based on a specific period of time, and outputting a fuzzy value representing a degree of a port scan attack; a fuzzy control module for recognizing the degree of the port scan attack based on the fuzzy value and outputting a control signal for traffic control according to the recognized degree of the port scan attack; and an intrusion blocking module for receiving the control signal and controlling the traffic with the network interface.
Owner:INTELLECTUAL DISCOVERY CO LTD
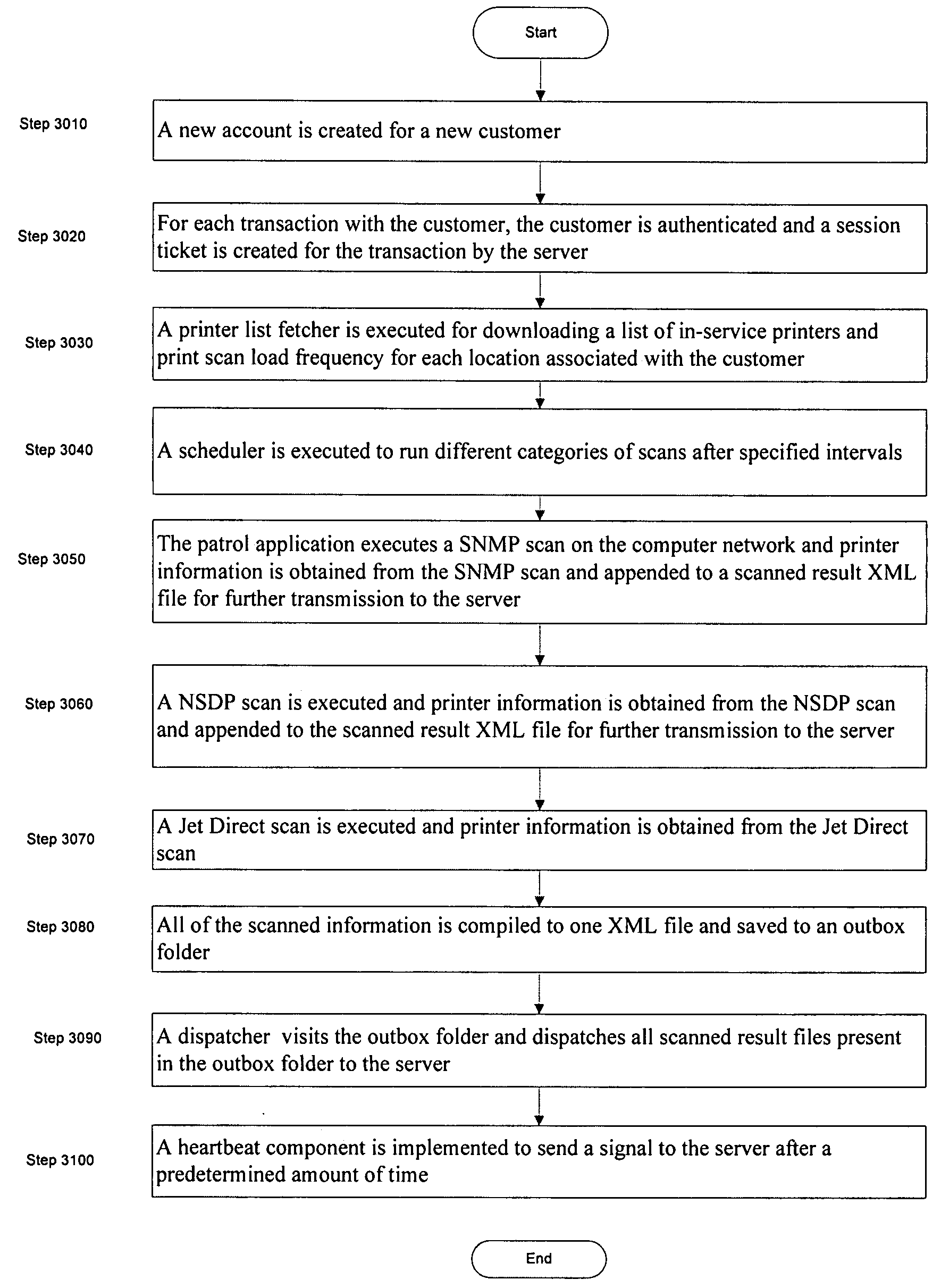
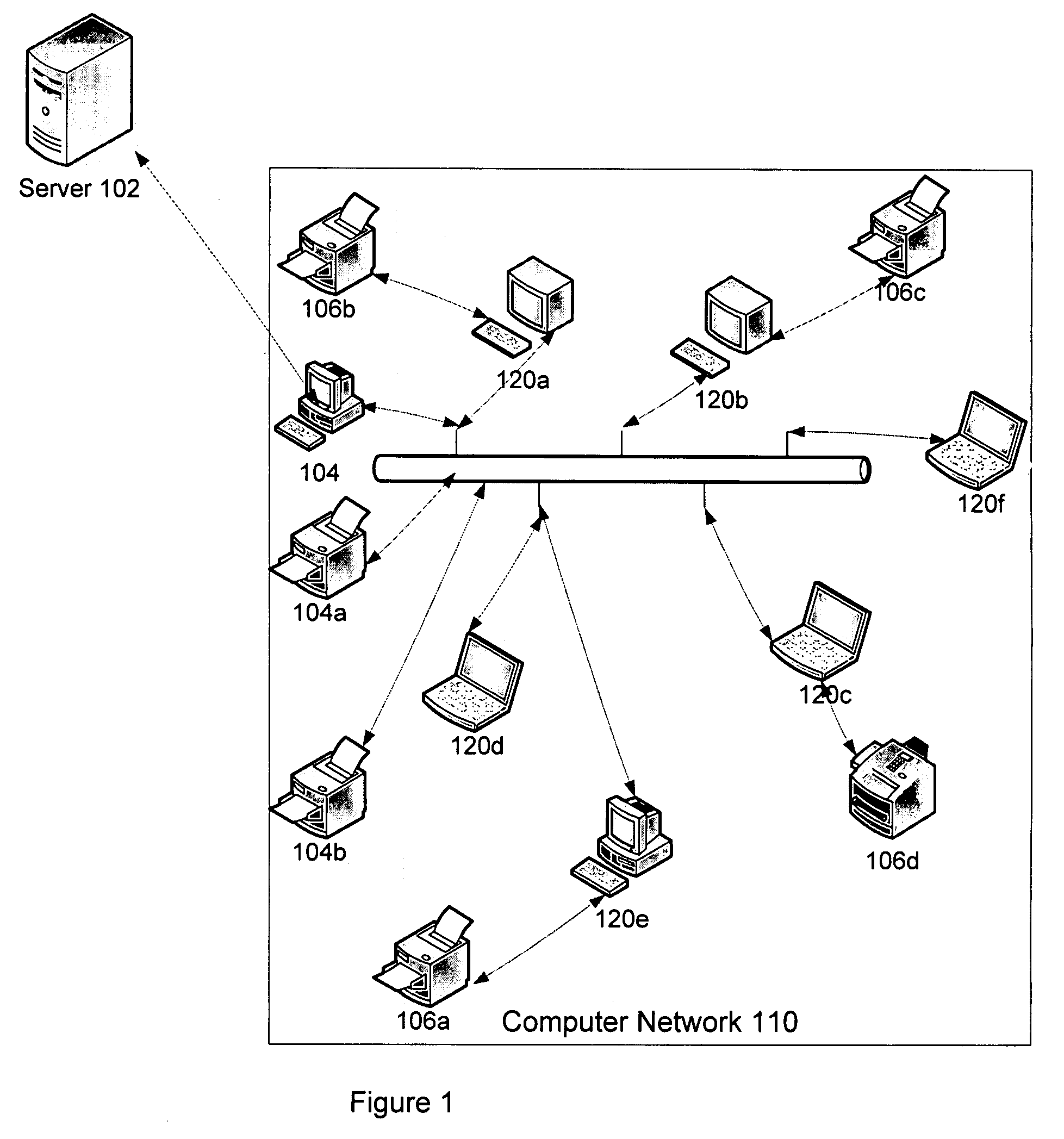
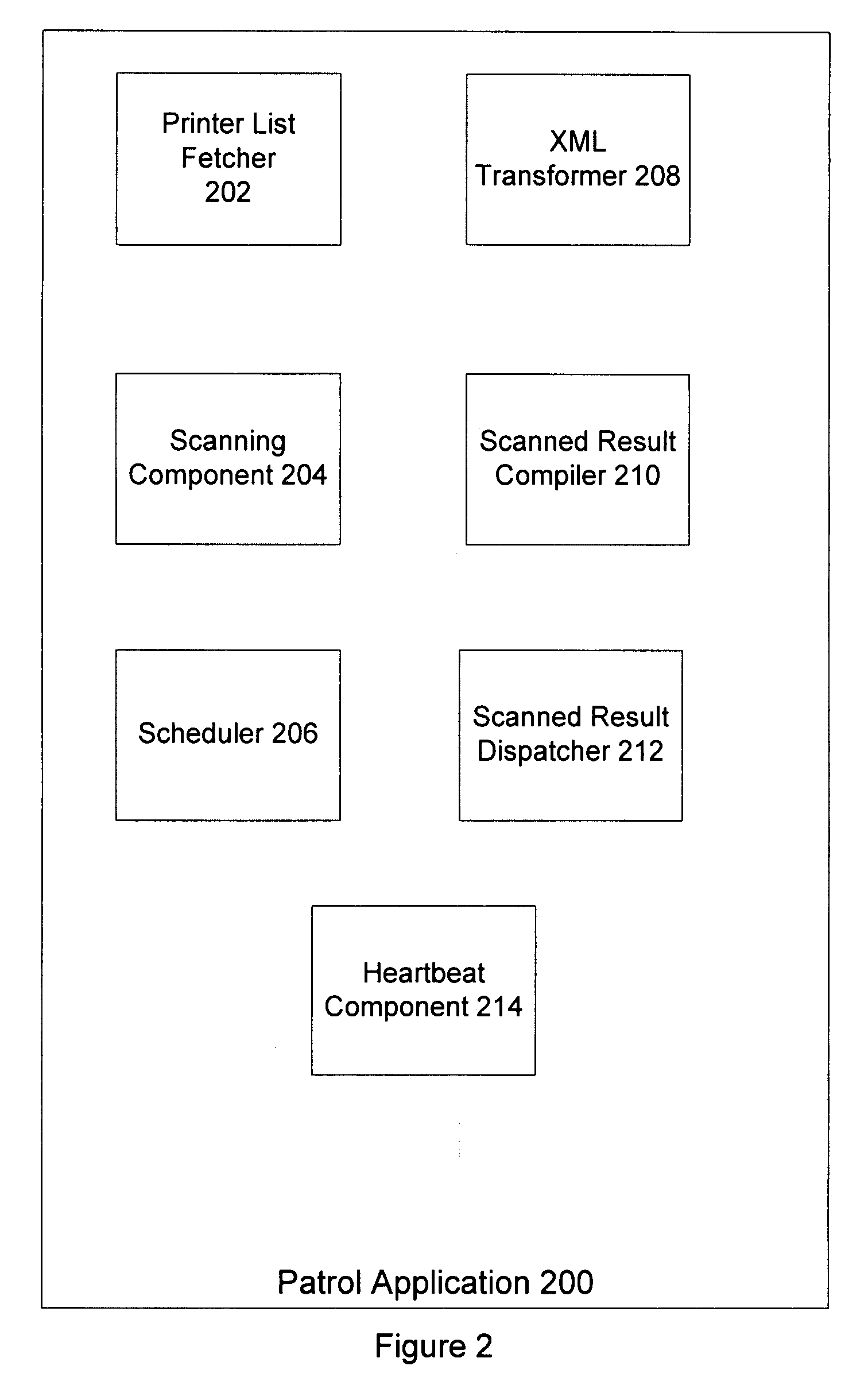
Apparatus and method for metering, monitoring and providing real time enterprise printing information
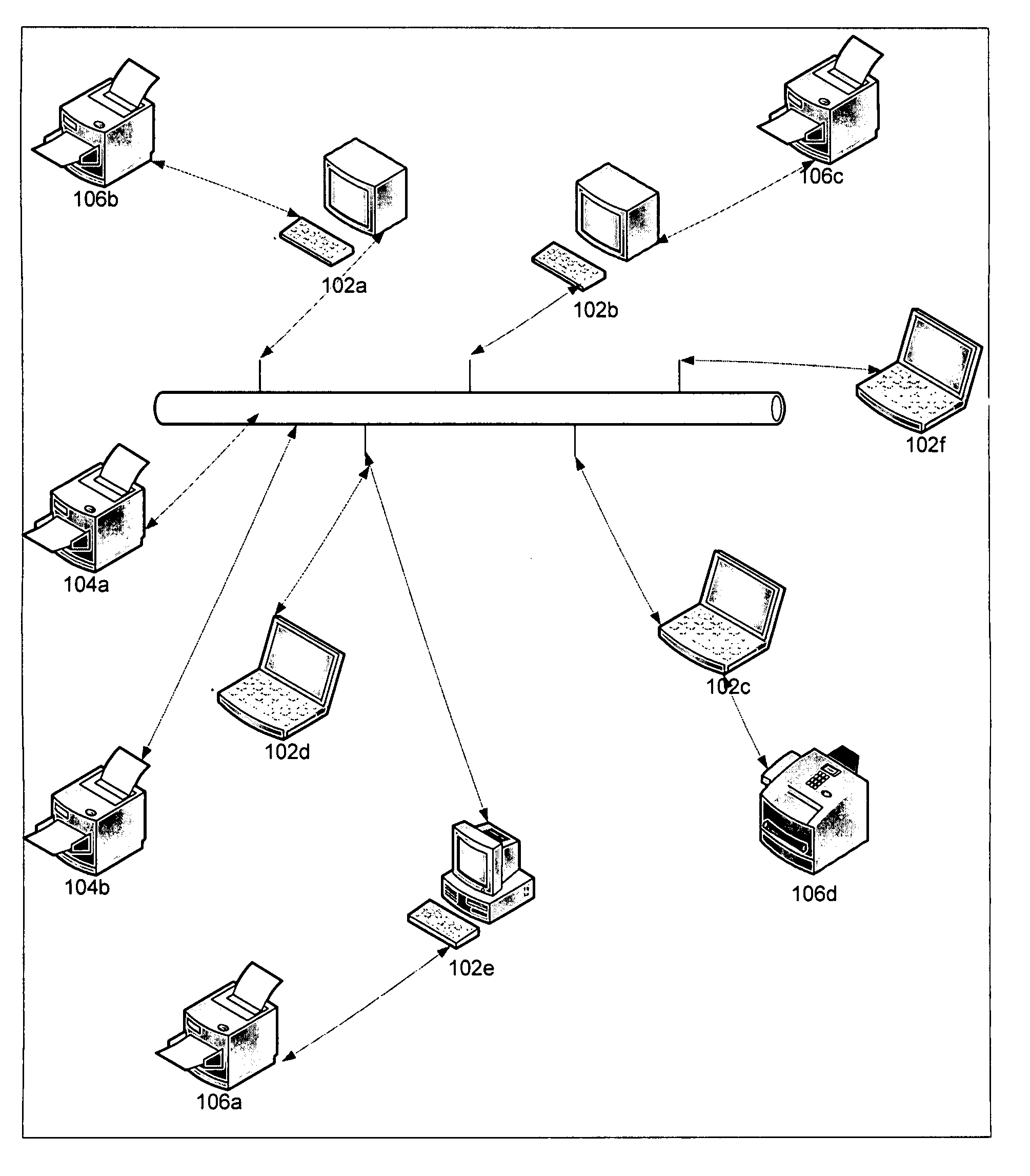
The invention relate to an apparatus and a method for monitoring all printers in an enterprise. The method includes for each transaction, authenticating a customer associated with the enterprise and obtaining a session ticket. The method also includes executing a printer list fetcher for downloading a list of in-service printer and print scan load frequency for each location with in the enterprise and executing a scheduler for implementing different categories of scans. The method further includes executing a network scan on a computer network to obtain information for all printers attached to the computer network, executing a local scan on each computer that is attached to a non-network printer to obtain information for all non-network printers in the enterprise and executing a port scan to obtain information for all non-catalogued printers. The method also includes compiling all scanned information, obtained from executing the network scan, the local scan and the port scan, in a file and dispatching the file to an external server and using the file in the external server to provide printer status information and usages for each printer in the enterprise.
Owner:EMERGE PRINT MANAGEMENT
Apparatus and method for discovering printers within an enterprise
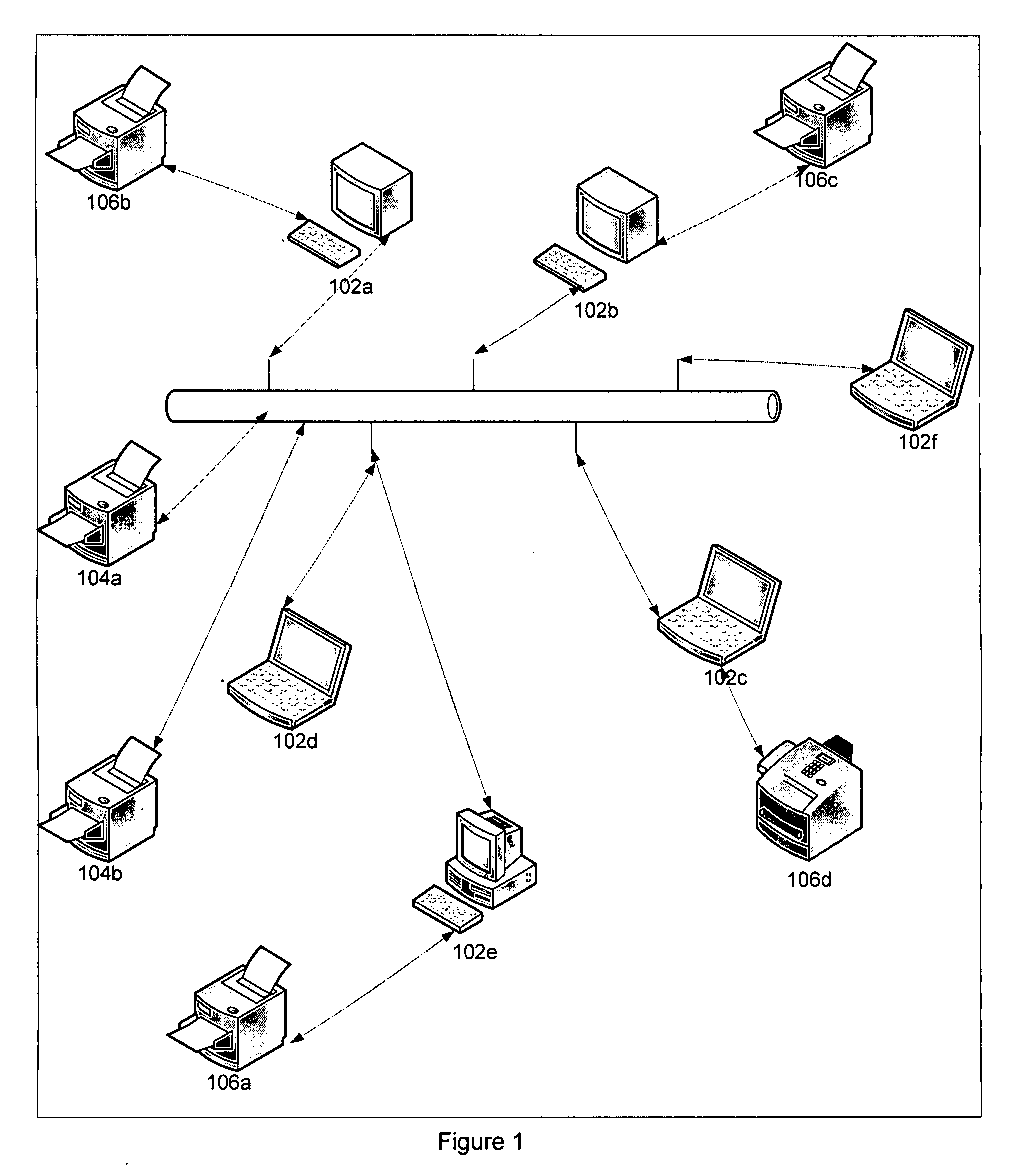
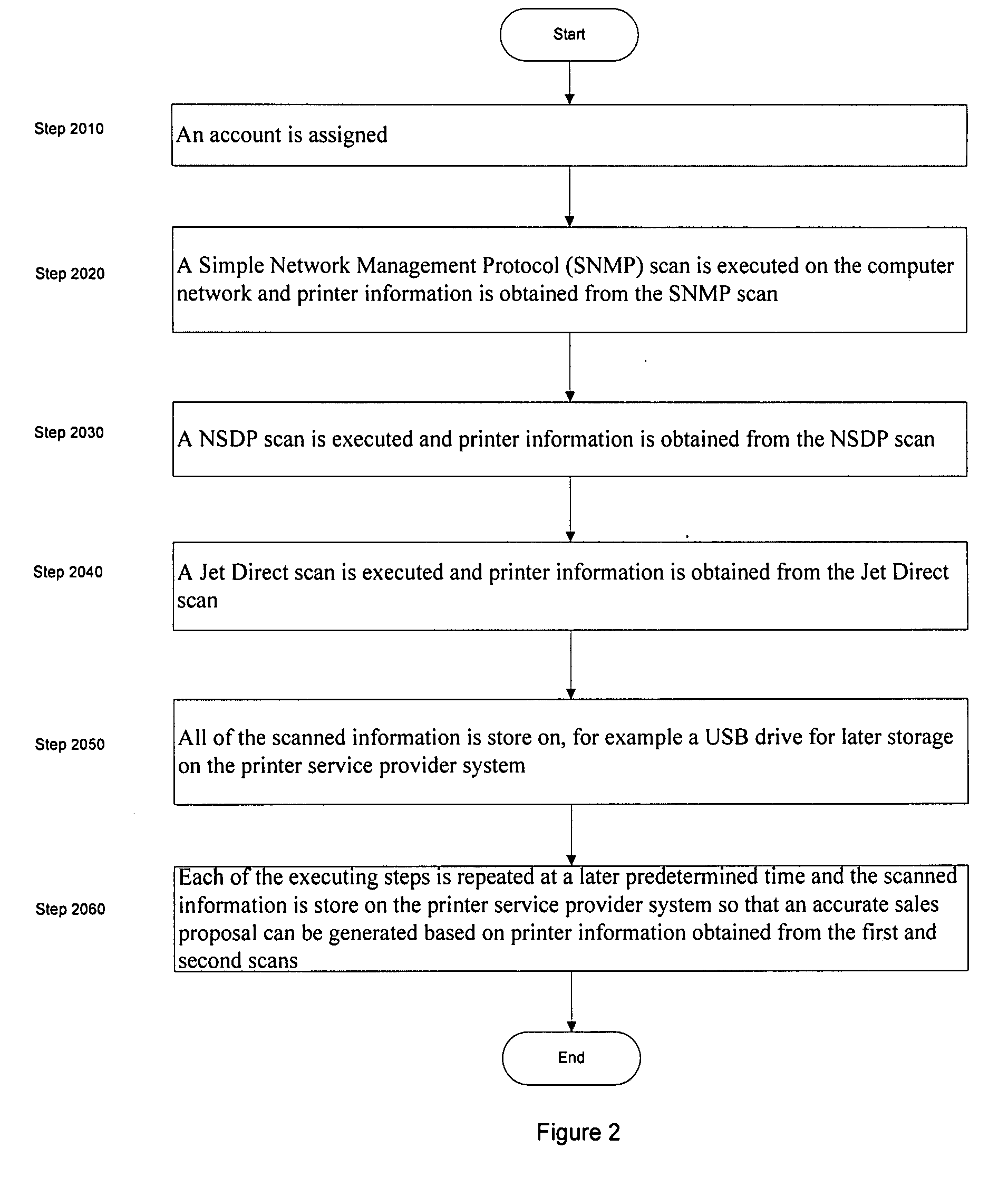
InactiveUS20080309965A1Accurate sale proposalTransmissionDigital output to print unitsPort scanDatabase
The invention relate to an apparatus and a method for determining printer usage of all printers in an enterprise to generate accurate sales proposals. The method includes assigning an account for the enterprise and executing a network scan on a computer network to obtain information for all printers attached to the computer network. The method also includes executing a local scan on each computer that is attached to a non-network printer to obtain information for all non-network printers in the enterprise and executing a port scan to obtain information for all non-catalogued printers. The method further includes storing all of the information obtained from executing the network scan, the local scan and the port scan and performing each of the steps above at least during two predetermined times. The method also includes using the information to generate sales proposals for all printer usage within the enterprise.
Owner:EMERGE PRINT MANAGEMENT +1
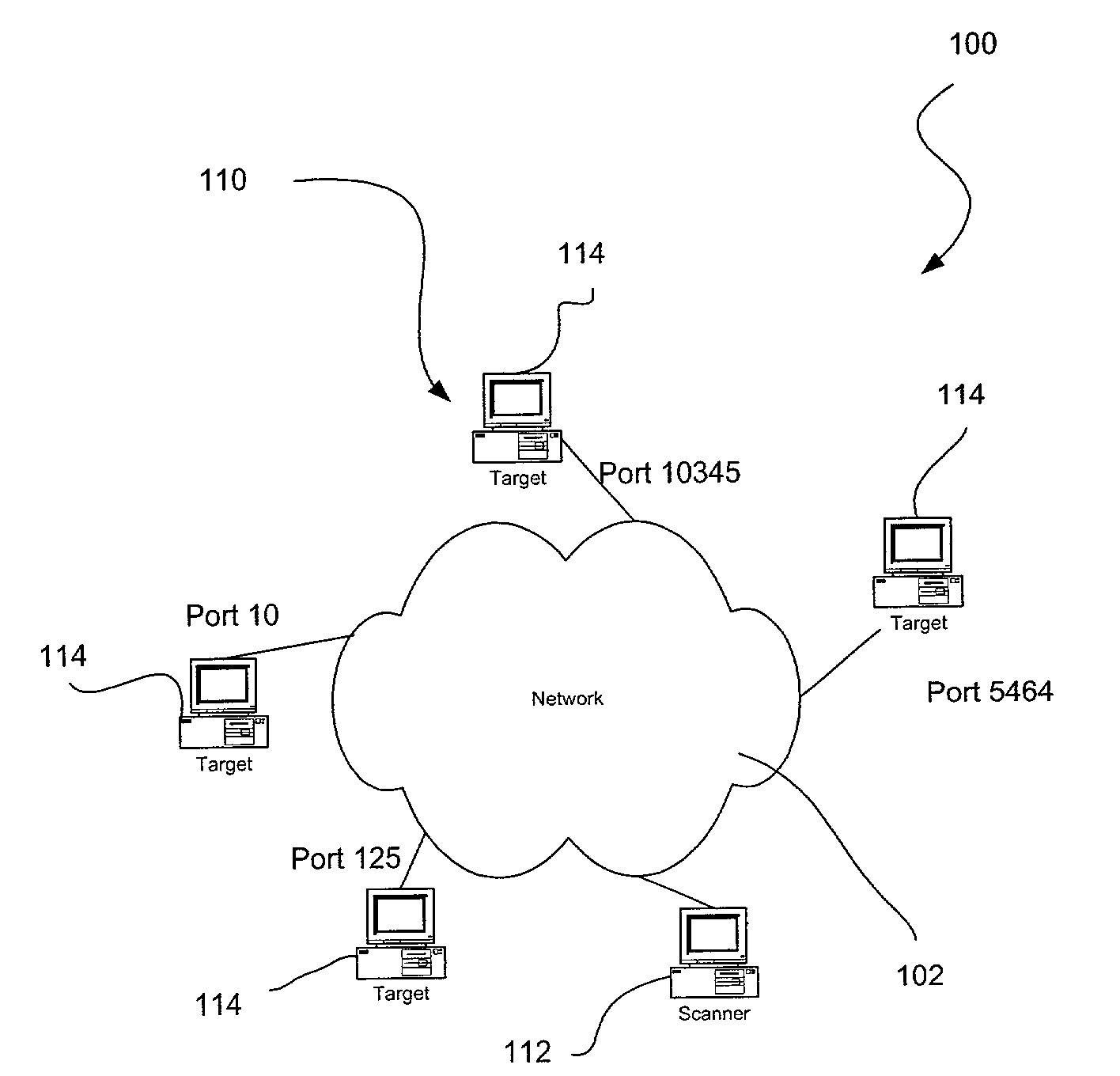
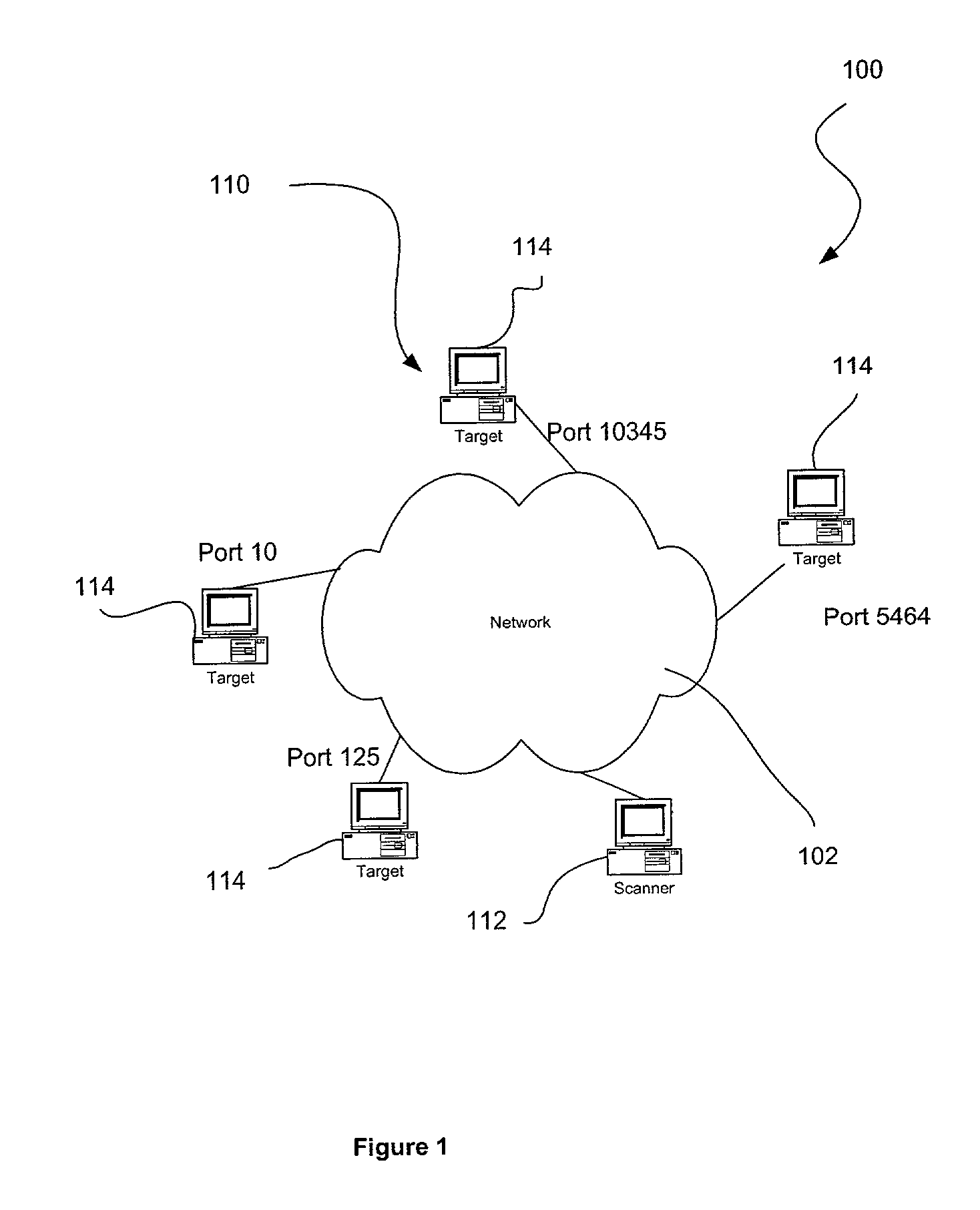
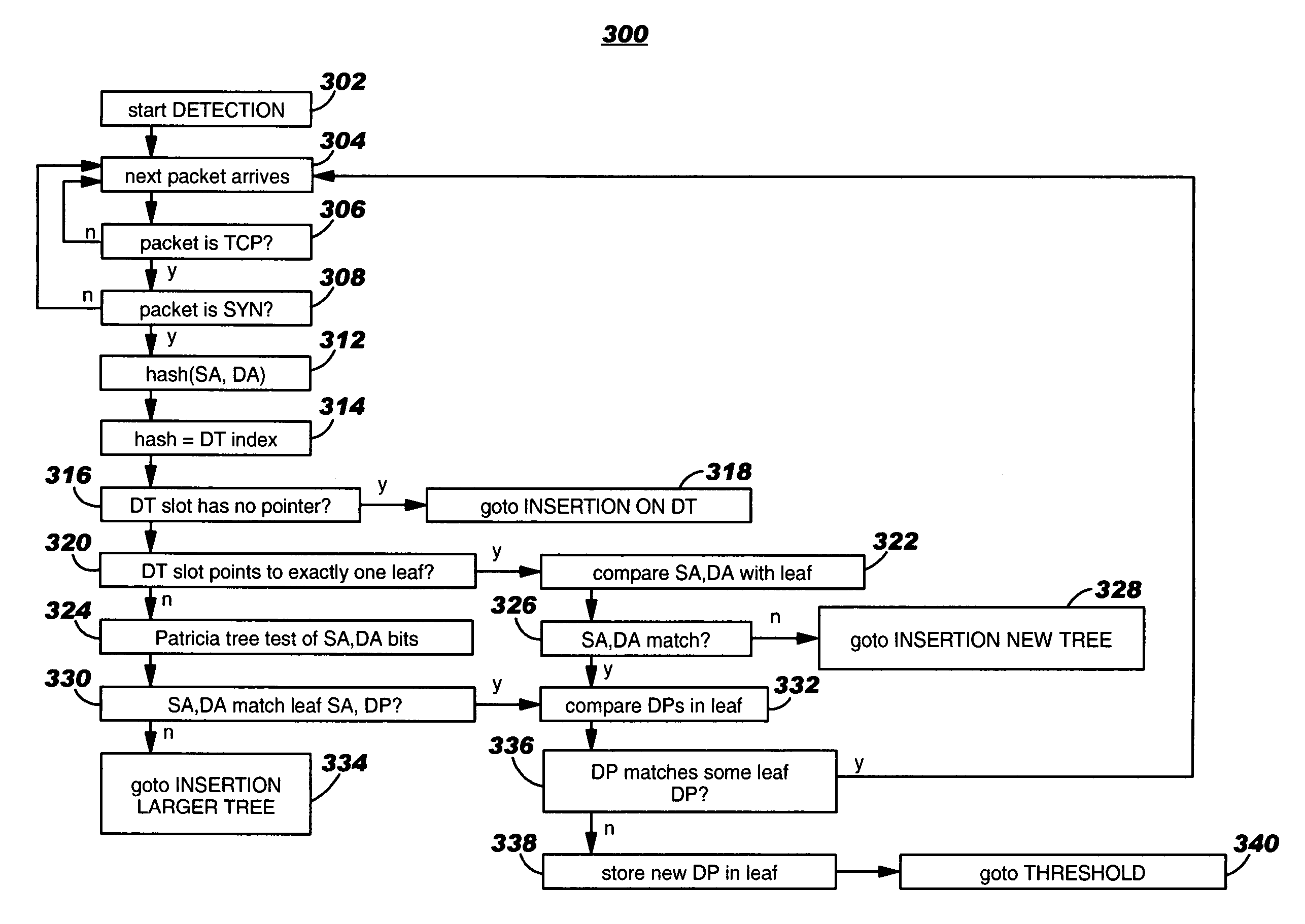
Automatically detecting distributed port scans in computer networks
A detection and response system including a set of algorithms for detecting within a stream of normal computer traffic a subset of (should focus on network traffic eliciting a response) TCP or UDP packets with one IP Source Address (SA) value, one or a few Destination Address (DA) values, and a number exceeding a threshold of distinct Destination Port (DP) values. A lookup mechanism such as a Direct Table and Patricia search tree record and trace sets of packets with one SA and one DA as well as the set of DP values observed for the given SA, DA combination. The detection and response system reports the existence of such a subset and the header values including SA, DA, and multiple DPs of the subset. The detection and response system also includes various administrative responses to reports.
Owner:INT BUSINESS MASCH CORP
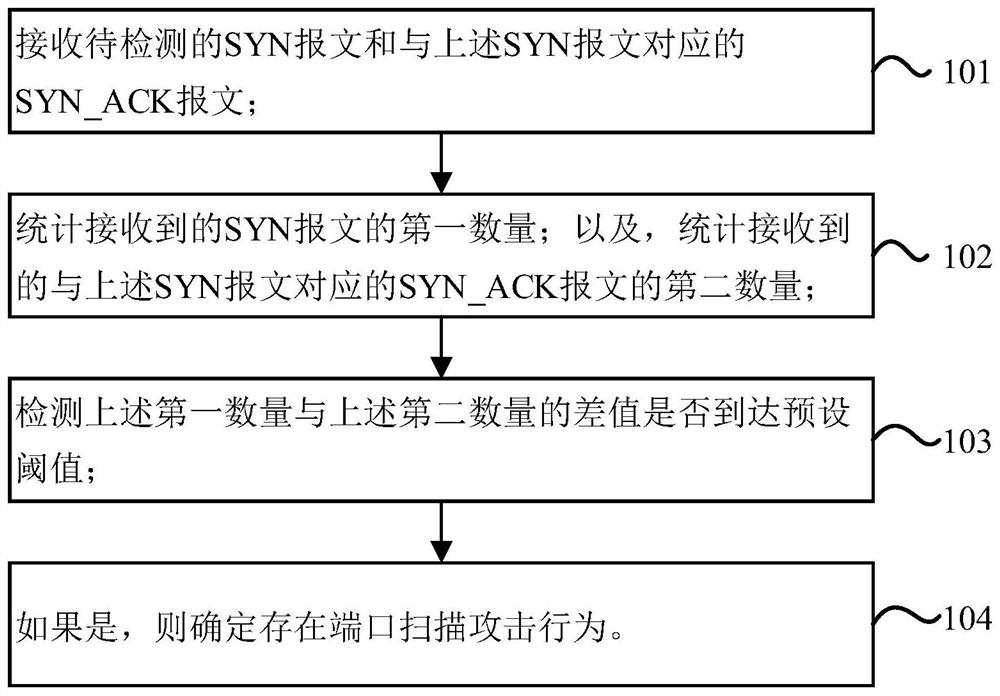
Port scanning attack detection method and device and electronic equipment
PendingCN112751862AAvoid misjudgmentImprove accuracyUser identity/authority verificationComputer networkAttack
The invention provides a port scanning attack detection method and device and electronic equipment. The method is applied to safety protection equipment, and the method comprises the following steps: receiving a to-be-detected SYN message and an SYN_ACK message corresponding to the SYN message; counting a first number of the received SYN messages; counting the second number of the received SYN_ACK messages corresponding to the SYN message; detecting whether a difference value between the first number and the second number reaches a preset threshold value or not; and if yes, determining that the port scanning attack behavior exists. According to the method and the device, under the condition of ultra-large flow, a normal TCP connection establishment process can be prevented from being misjudged as the port scanning attack, so the accuracy of port scanning attack detection is improved.
Owner:HANGZHOU DPTECH TECH
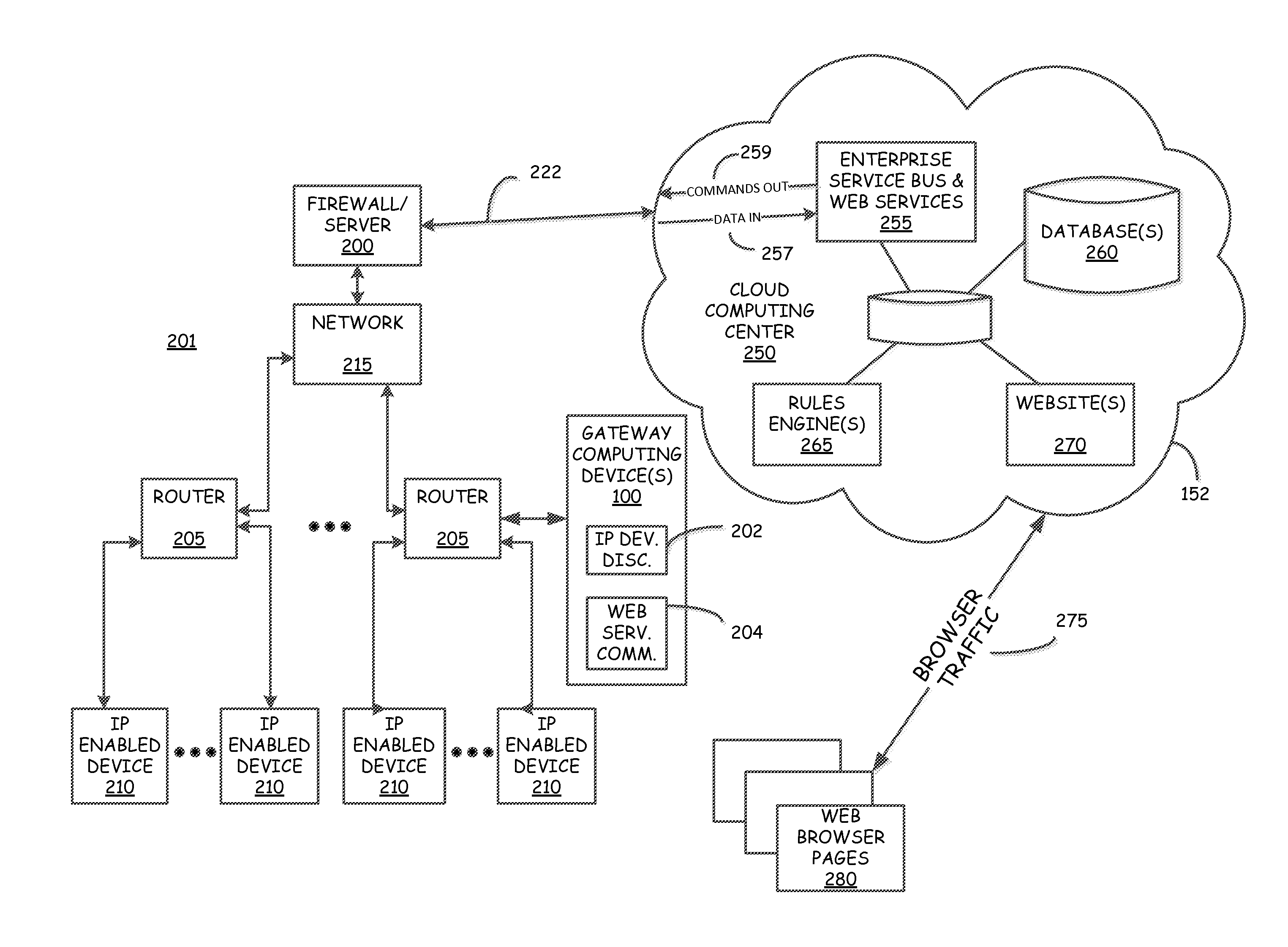
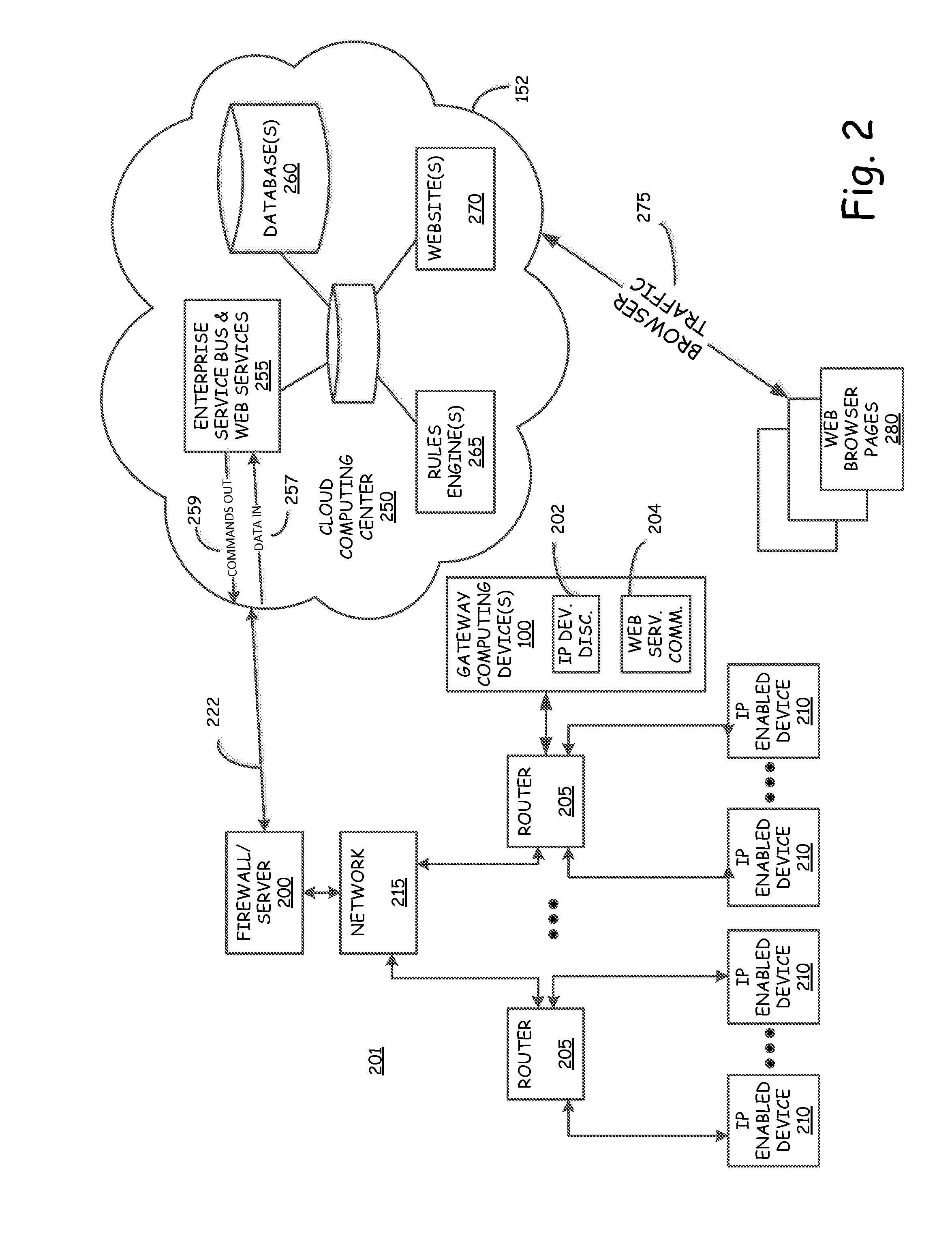
Gateway system and process for IP enabled devices
A computer implemented method is provided for monitoring and controlling a plurality of internet protocol (IP) enabled devices on a network. Each of the plurality of IP enabled devices has an internal IP address on the network, but does not have an external IP address for use on the Internet. The method includes the step of performing a port scan to obtain internal IP addresses for the plurality of IP enabled devices on the network. An HTML page is retrieved from each of the plurality of IP enabled devices on the network using the internal IP addresses. A data file name is extracted from each of the retrieved HTML pages and in some embodiments is translated to a new data file name. The method also includes retrieving data from each of the plurality if IP enabled devices on the network as a function of the extracted data file names or using the new data file names. Computer readable storage medium and gateway computing devices, for example in the form of a plug computer, are also disclosed.
Owner:GREENMETRIC L L C
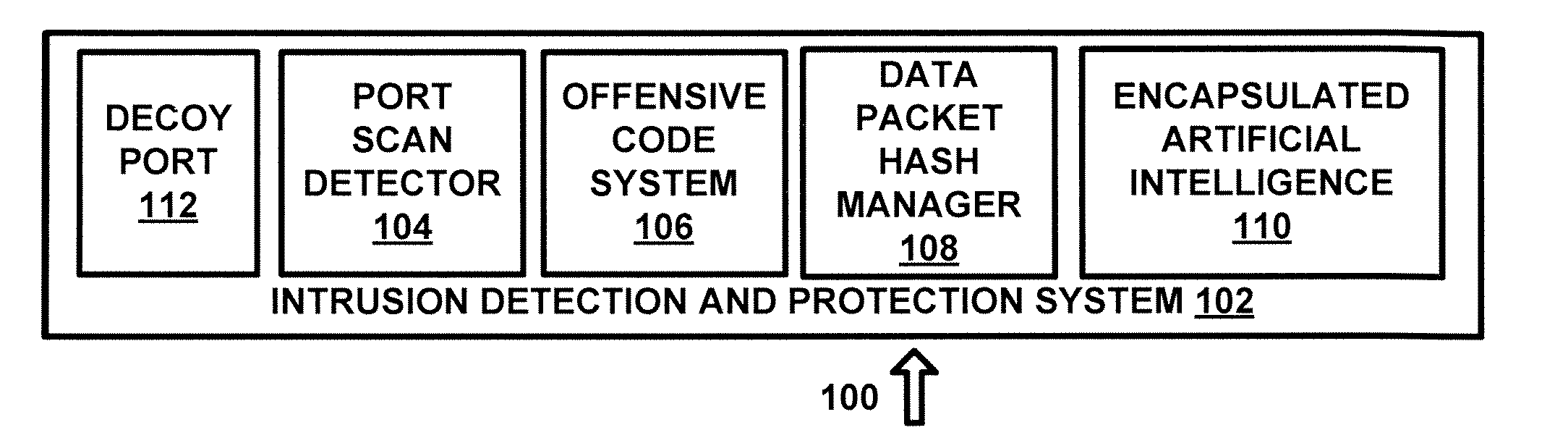
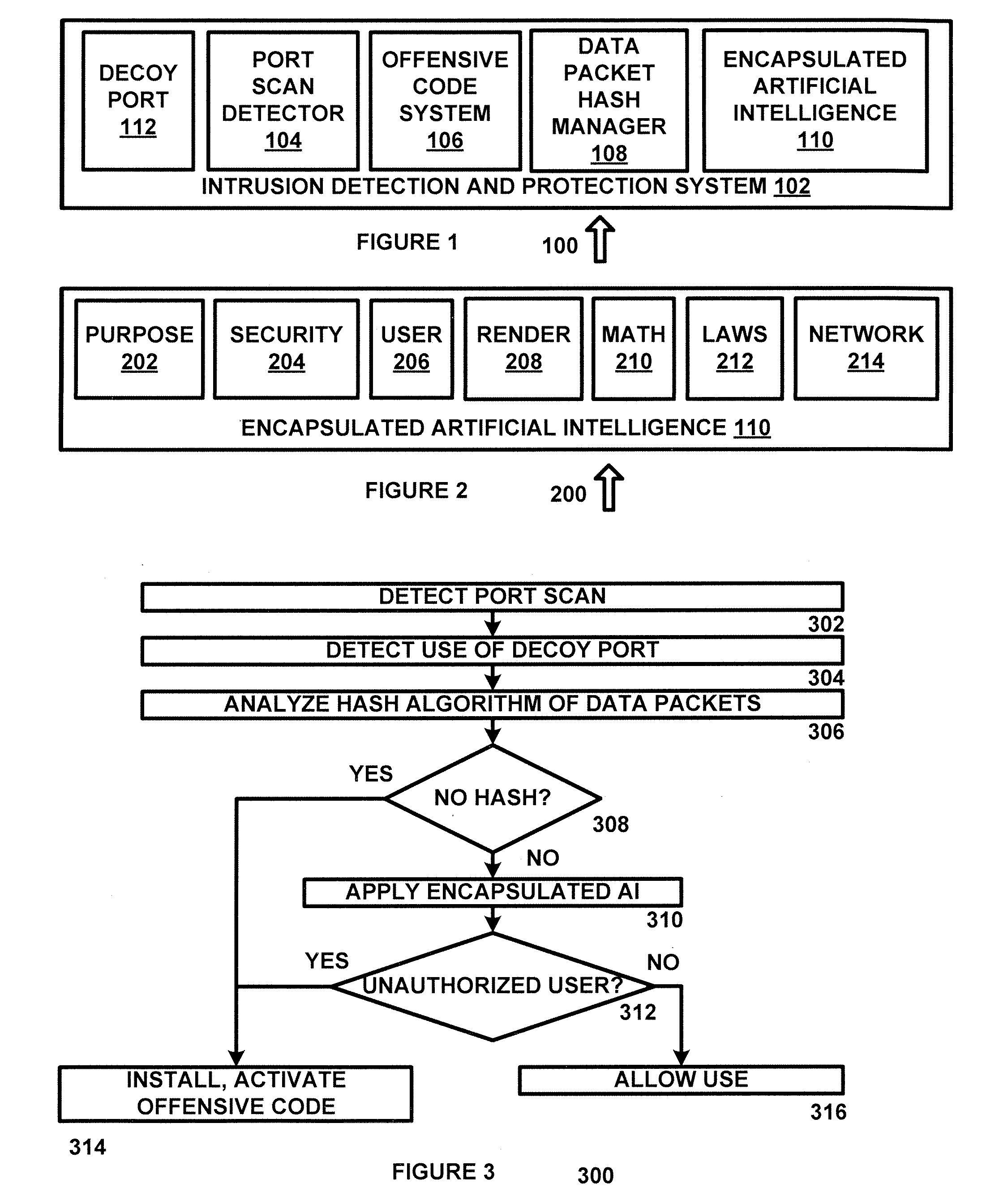
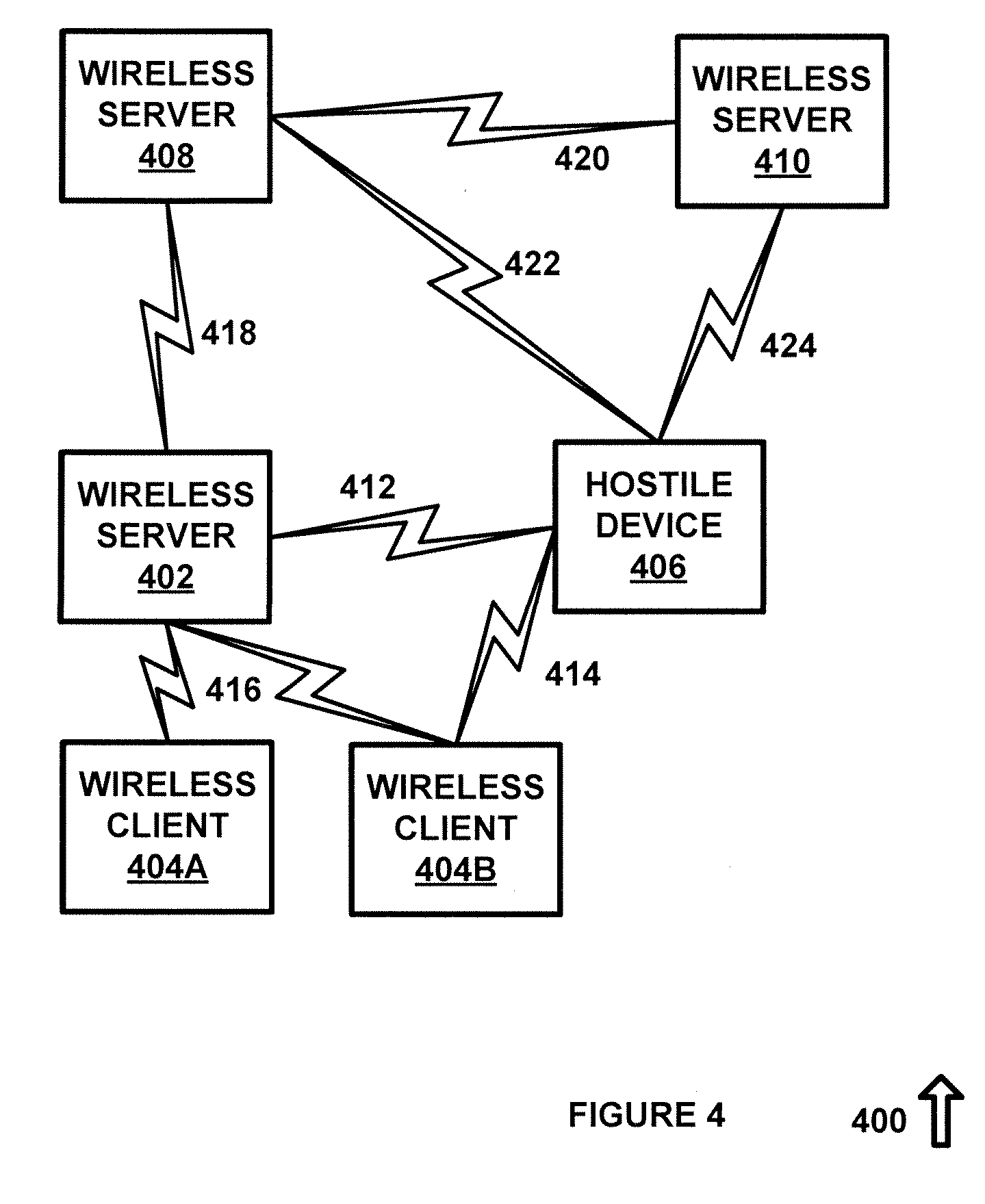
System and method for intrusion detection and suppression in a wireless server environment
A system for data communications comprising a port scan detector configured to receive port access requests from a plurality of ports and to determine whether a port scan by a hostile device is in progress. A decoy port system configured to open a designated decoy port if the port scan detector determines that the port scan by a hostile device is in progress. A data packet hash manager configured to read a series of hash data fields in a corresponding series of data packets and to generate a flag if a sending device is not operating a hash increment system. An encapsulated artificial intelligence system configured to receive the flag and to monitor data communications from the sending device to determine whether the data communications are consistent with a levelling algorithm. An offensive code system configured to implant offensive code in the sending device and to control operation of the sending device if the sending device is the hostile device, if the sending device is not operating the has increment system and if the data communications are not consistent with the levelling algorithm.
Owner:MYTH INNOVATIONS
Method and device for monitoring abnormal connection and scanning behaviors of server
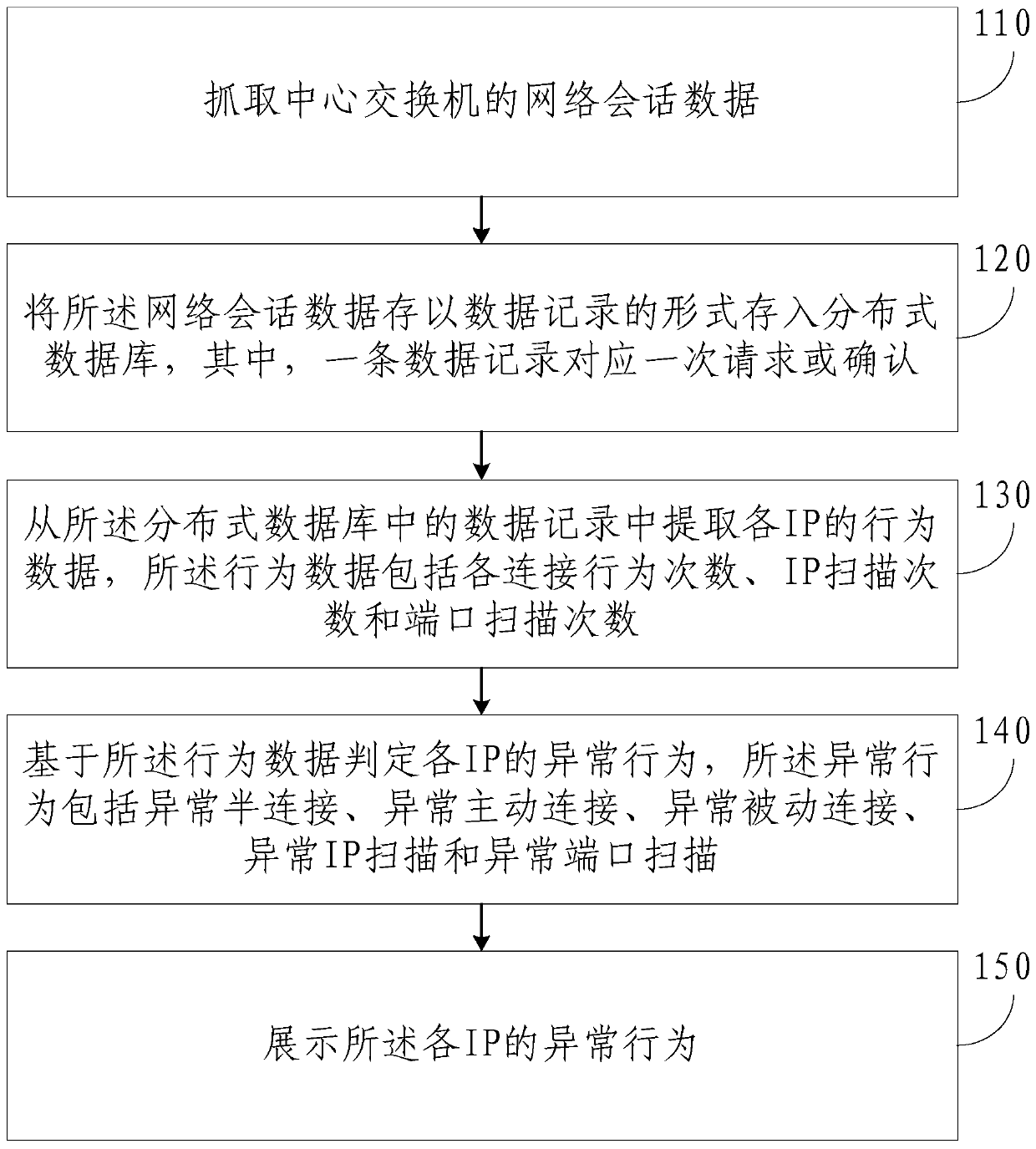
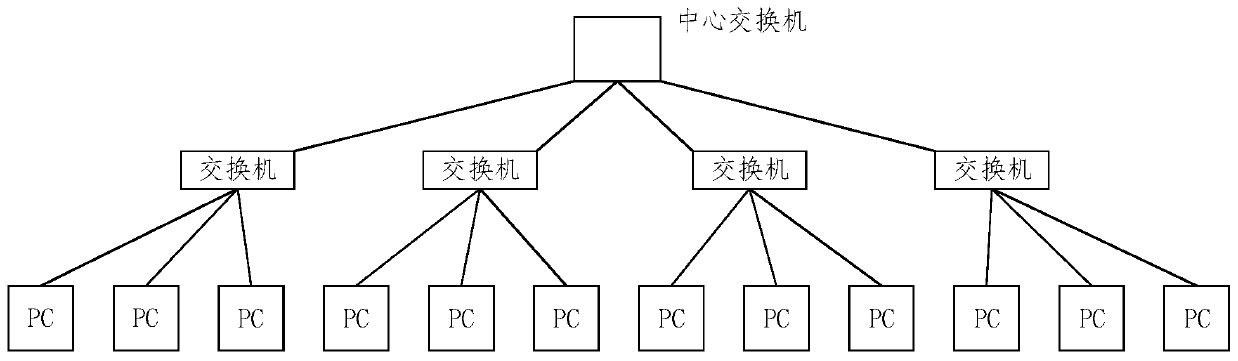
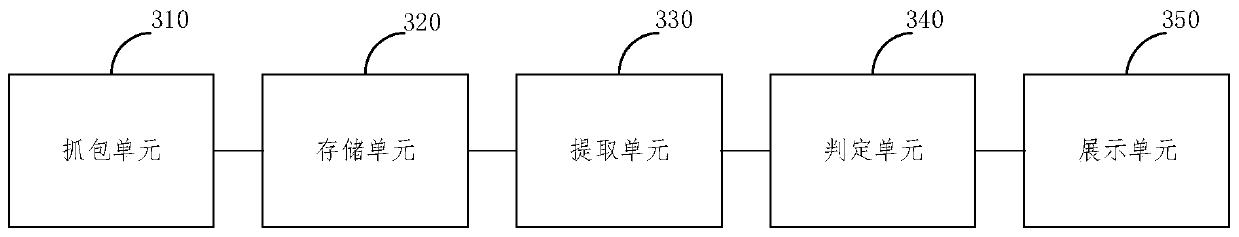
ActiveCN111092900AImplement storageImprove monitoring efficiencyDatabase distribution/replicationTransmissionEngineeringDistributed database
The embodiment of the invention provides a method and a device for monitoring abnormal connection and scanning behaviors of a server. The method comprises: capturing network session data of a centralswitch; storing the network session data in a distributed database in the form of data records, wherein one data record corresponding to one request or confirmation; extracting behavior data of each IP from data records in the distributed database, wherein the behavior data comprises each connection behavior frequency, IP scanning frequency and port scanning frequency; judging abnormal behaviors of each IP based on the behavior data, wherein the abnormal behaviors comprise abnormal semi-connection, abnormal active connection, abnormal passive connection, abnormal IP scanning and abnormal portscanning; and displaying the abnormal behavior of each IP. According to the method and the device provided by the embodiment of the invention, a large amount of network session data can be processed,the network abnormal behavior is updated in real time, and the network abnormal behavior monitoring efficiency is improved.
Owner:BEIJING VRV SOFTWARE CO LTD
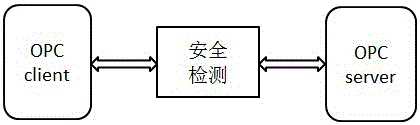
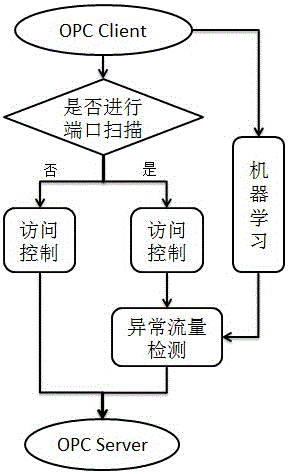
Self-learning-based safety detection method for OPC Classic protocol
InactiveCN105959289AEnsure safetyReliable detection methodTransmissionEngineeringArtificial intelligence
The invention relates to the industrial control system network information safety field, and discloses a self-learning-based safety detection method for an OPC Classic protocol. The flow of the method includes the steps: detecting whether port scanning is being operated in the network of an OPC client, wherein if not, the data is filtered through access control and if so, the data is filtered through access control and an anomaly flow detection model which is generated through self-learning; transmitting the filtered data to an OPC server; and performing safety detection through the anomaly flow detection model which is generated through self-learning and access control. Therefore, a more reliable detection method is provided for stabilization and safety of connection of the OPC Classic protocol, and the safety for OPC communication is maximumly guaranteed.
Owner:中国东方电气集团有限公司
Network anomaly detection method based on traffic data sample statistics and balanced information entropy estimation
ActiveCN109361673AReduce the degree of deviationFacilitate subsequent calculation and processingTransmissionSmall sampleAnomaly detection
The invention discloses a network anomaly detection method based on traffic data sample statistics and balanced information entropy estimation. The invention belongs to the technical field of networksecurity, comprises the steps of flow data collection, data format unification, data feature analysis and network anomaly determination, and is a detection method for estimating the overall situationby using a balance method of the sample information entropy based on network traffic small sample data features to identify the DoS and Port Scan attack rejection in the network.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
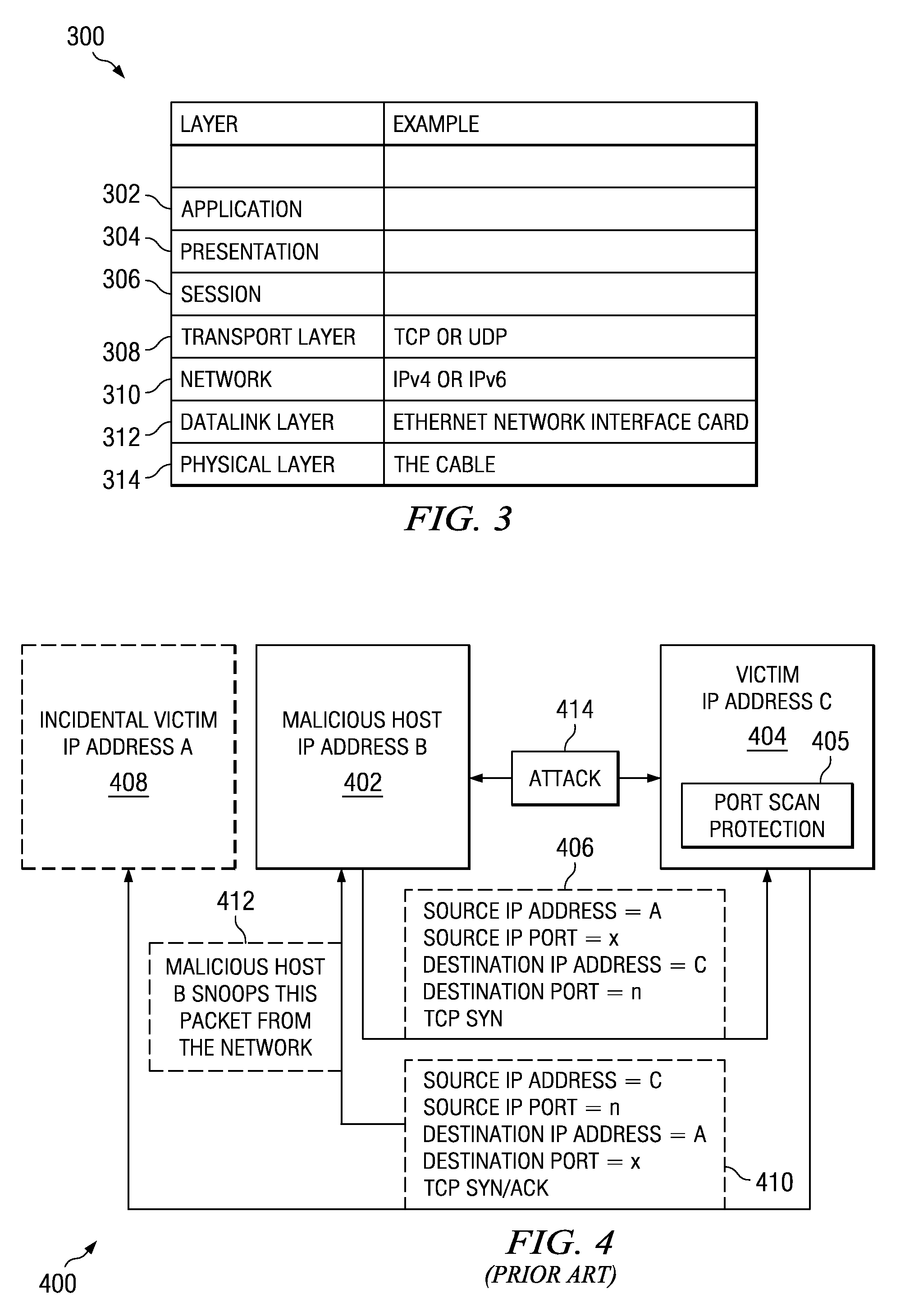
Scan detection
InactiveUS20050147037A1Error preventionFrequency-division multiplex detailsComputer hardwareNetwork connection
A method for detecting a scan in network connections, each connection to a respective destination determined by a destination key and a destination parameter. For each of the connections, an active-connection entry is logged in a first table. The active-connection entry includes the destination key and the destination parameter. For each destination key entered in the first table, each active-connection entry is counted by: (i) entering in a second table a new-connection entry including the destination key, and (ii) assigning to the new-connection entry a use value; the use value equals a number of the active-connection entries with the destination key. A scan event is generated when the use value exceeds a previously determined new-connection-threshold. If the scan is an “address scan”, the destination key is a destination port and the destination parameter is a destination address (IP); and if the scan is a “port scan” then the destination key is a destination address and the destination parameter is a destination port.
Owner:CHECK POINT SOFTWARE TECH LTD
Port scanning method and device
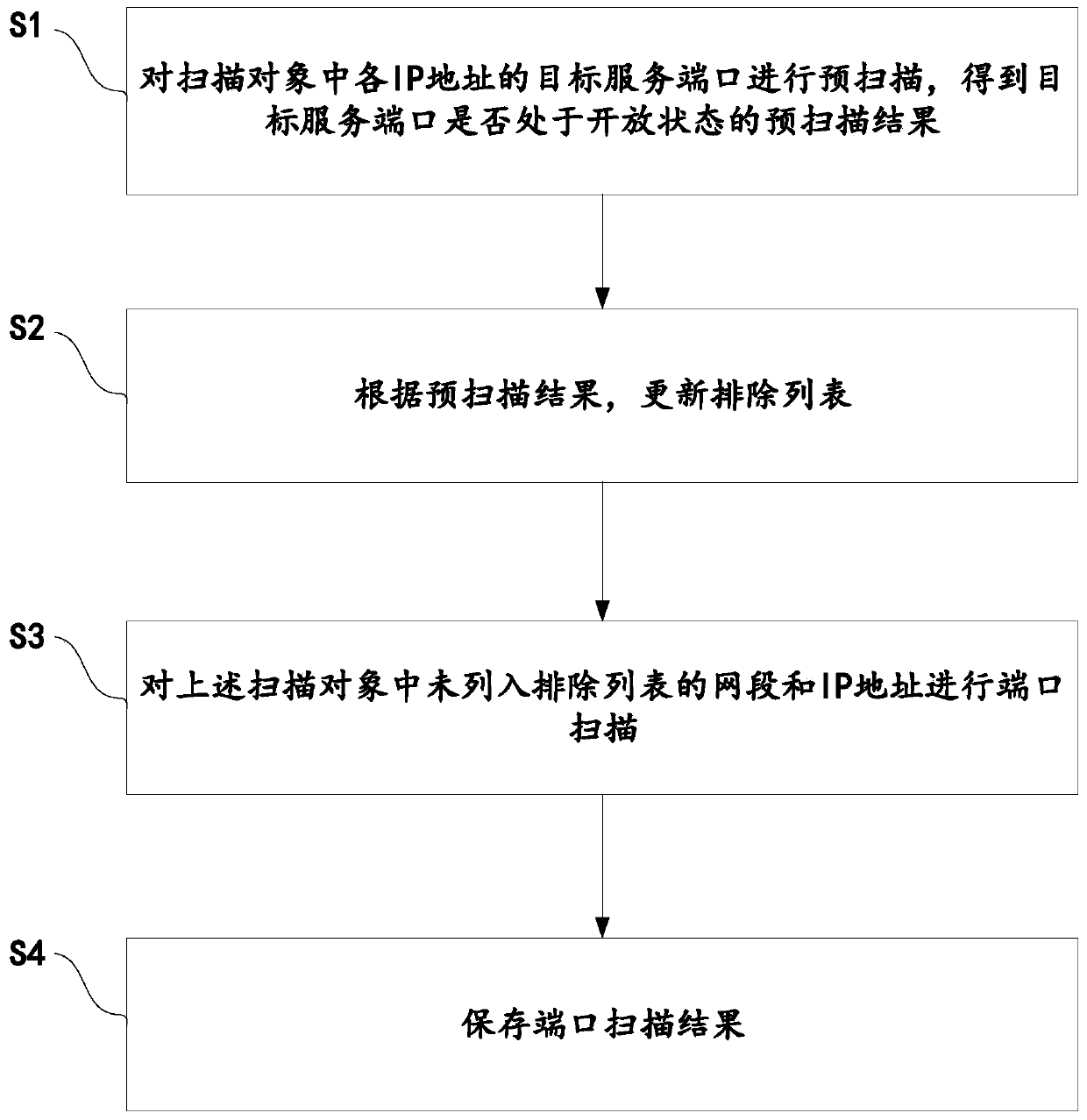
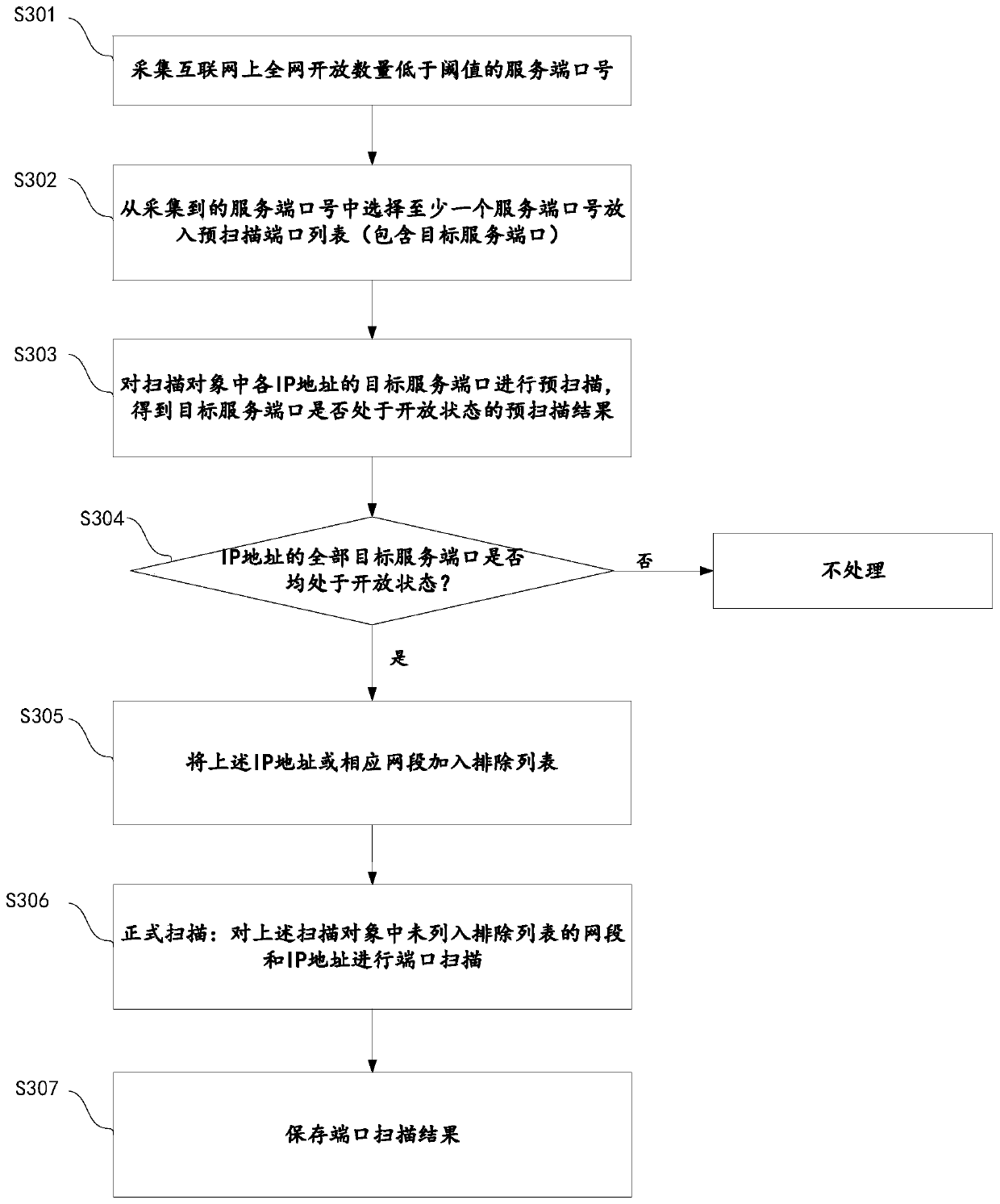
ActiveCN110380935AReduce false positivesGuaranteed accuracyData switching networksIp addressMisinformation
The embodiment of the invention provides a port scanning method and device so as to reduce scanning misinformation. According to the port scanning method, ports are scanned in two times, the first time of scanning is pre-scanning, in the pre-scanning process, all the ports of IP addresses are not scanned one by one, a target service port is scanned according to a pre-scanning port list, and a pre-scanning result indicating whether the target service port is opened or not is obtained. And then, the exclusion list is updated according to the pre-scanning result, and the second scanning carried out after the exclusion list is updated is formal scanning. Due to the fact that the IP addresses and the network segments in the exclusion list are pre-judged, the IP addresses and the network segments which are misreported at a large probability cannot be scanned in formal scanning, misreporting of formal scanning can be reduced, and the scanning efficiency and accuracy are guaranteed.
Owner:HANGZHOU DT DREAM TECH
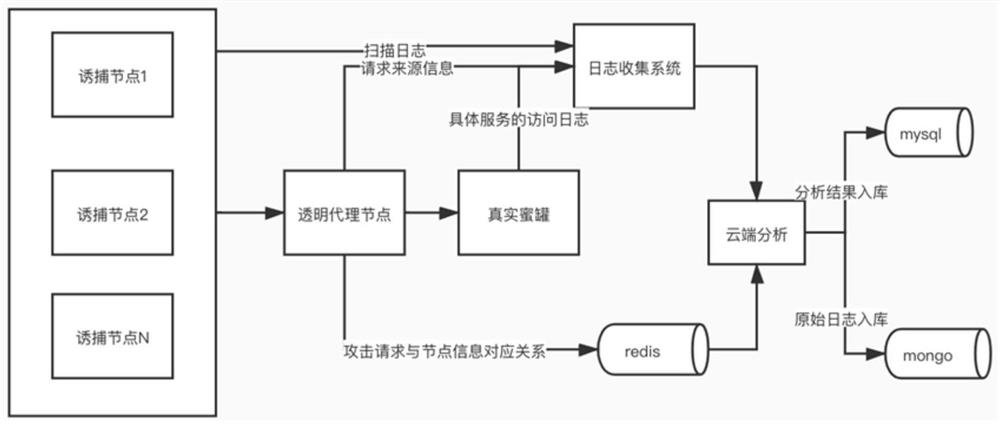
Honeypot attacker tracing method based on TCP/UDP transparent proxys
The invention discloses a honeypot attacker tracing method based on TCP / UDP transparent proxys. The honeypot attacker tracing method comprises the following steps that a service party trap node forwards traffic; the service party trap node dynamically realizes virtual IP simulation; a trap node port achieves scanning and monitoring; the transparent proxy node forwards TCP / UPD traffic; corresponding node positioning is realized through traffic under a multi-forwarding-node scene. According to the method, head information of a transport layer protocol is read at a transparent proxy, attack traffic tracing is achieved, attack traffic is transparently forwarded to a real honeypot service through a real IP of an attacker, and correct request analysis and response of an application layer are achieved; the proxy layer is realized based on TCP / UDP, so that honeypots of all TCP / UDP protocol types are supported.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
Access control device, method, computer program product and computer readable medium
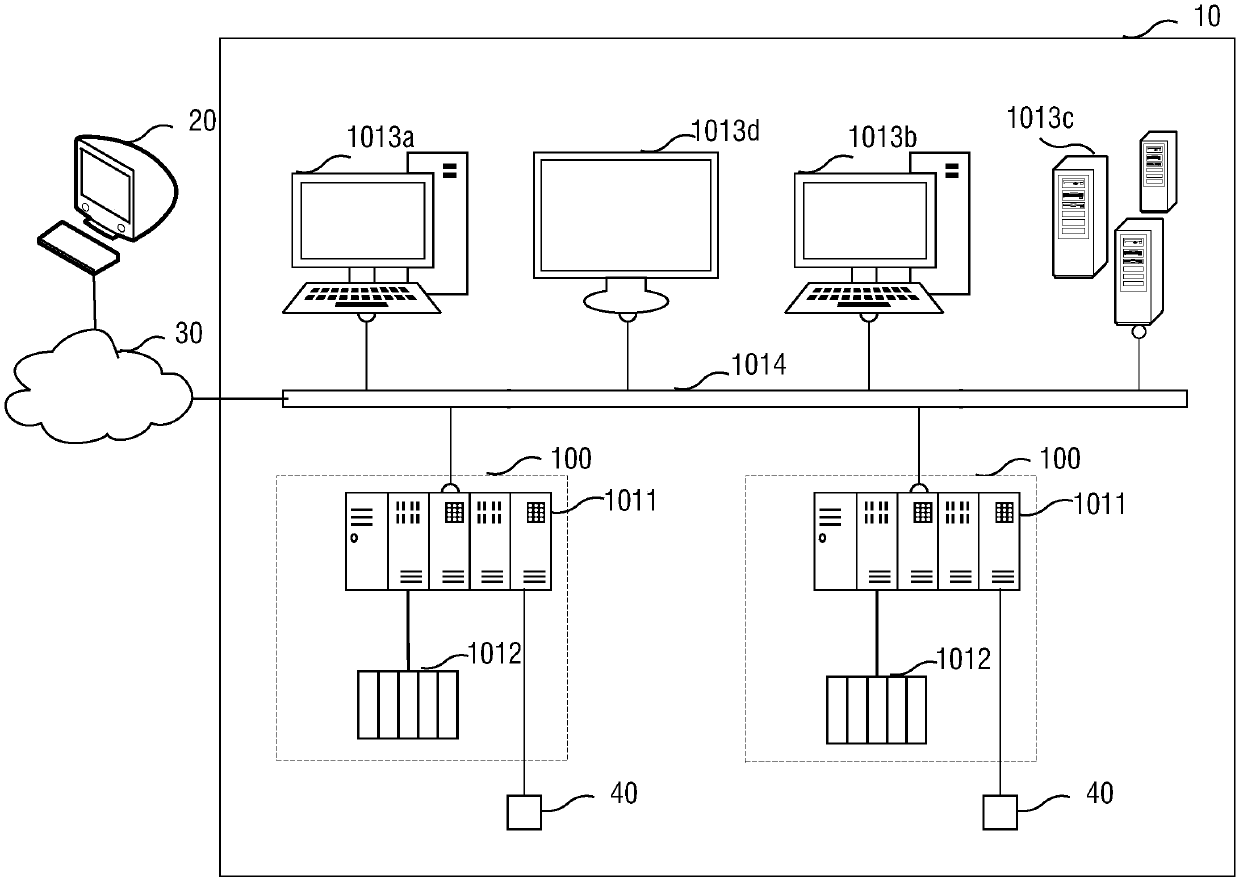
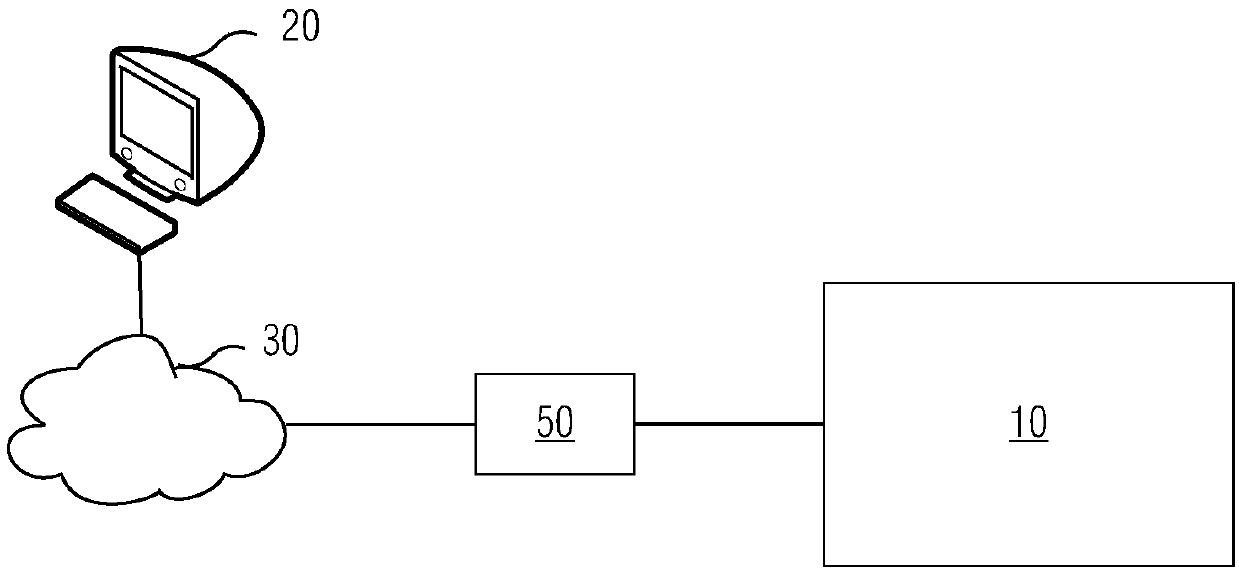
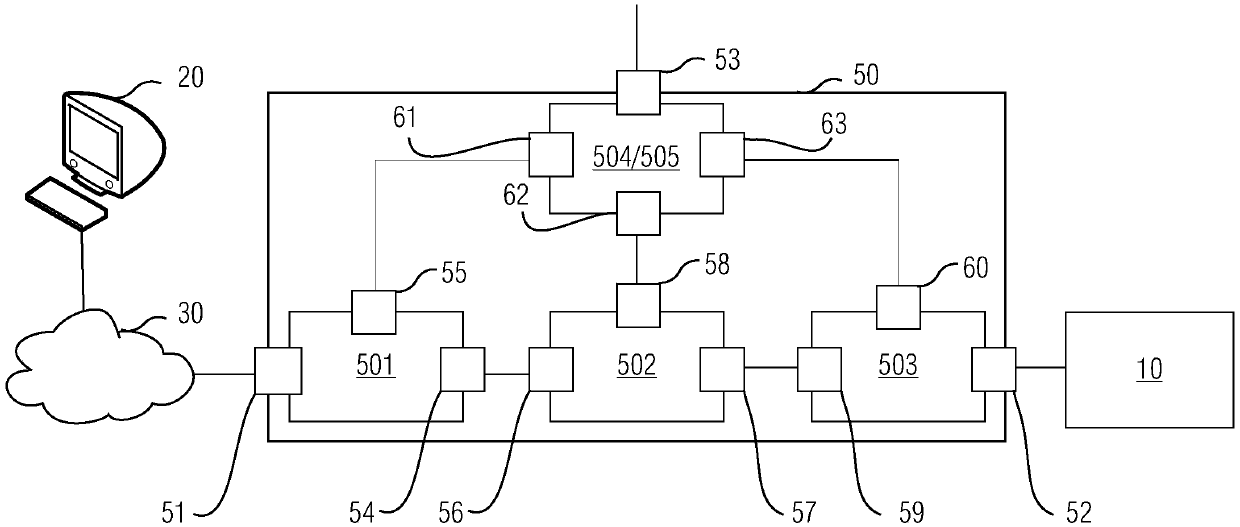
The invention relates to the technical field of industrial safety, in particular to access control device and method, which can provide effective safety protection in the remote access process of a system. An access control device (50) comprises a front-end firewall (501), a first network port (51) is provided to be connected with a remote computer (20); a bastion host (502) connected with the front-end firewall (501); a rear-end firewall (503) connected with the bastion host (502) and provides a second network port (52) to be connected with the system (10); and a back-end firewall (503) which scans resources allowed to be remotely accessed in the system (10) through the second network port (52) and determines the resources which can be remotely accessed by a computer (20) from the resources; and the bastion host (502) provides information that the computer (20) can remotely access resources to the computer (20) through the front-end firewall (501) via the first network port (51). The invention has the advantages of safety and simplicity in use and plug-and-play performance.
Owner:SIEMENS AG
Host port scanning behavior detection method and device
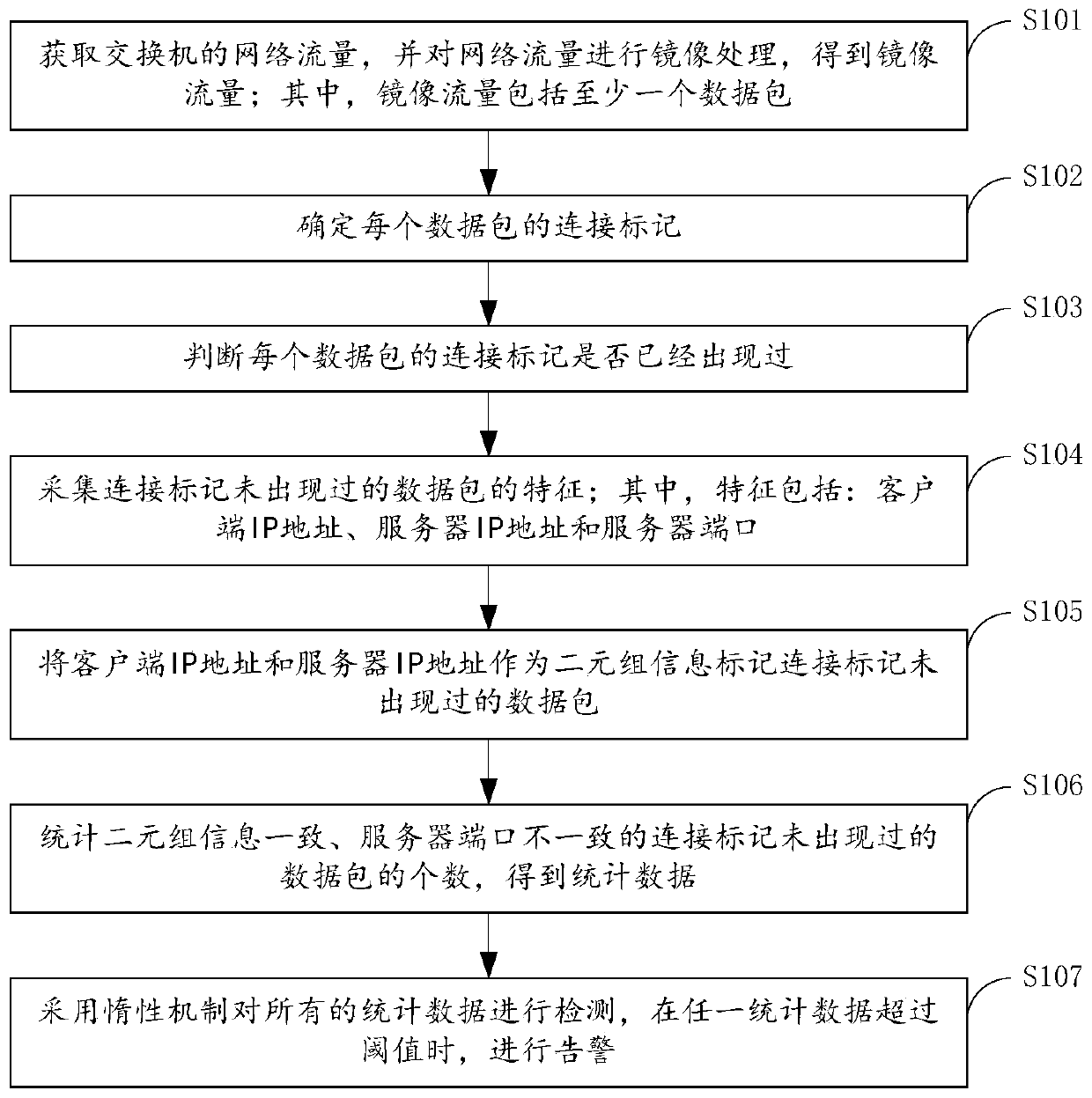
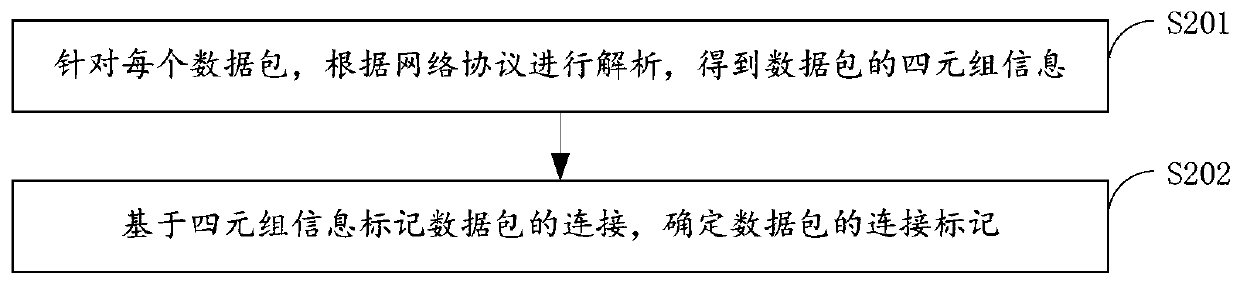
ActiveCN110750785AAccurately determineImprove statistical accuracyPlatform integrity maintainanceTransmissionData packInternet traffic
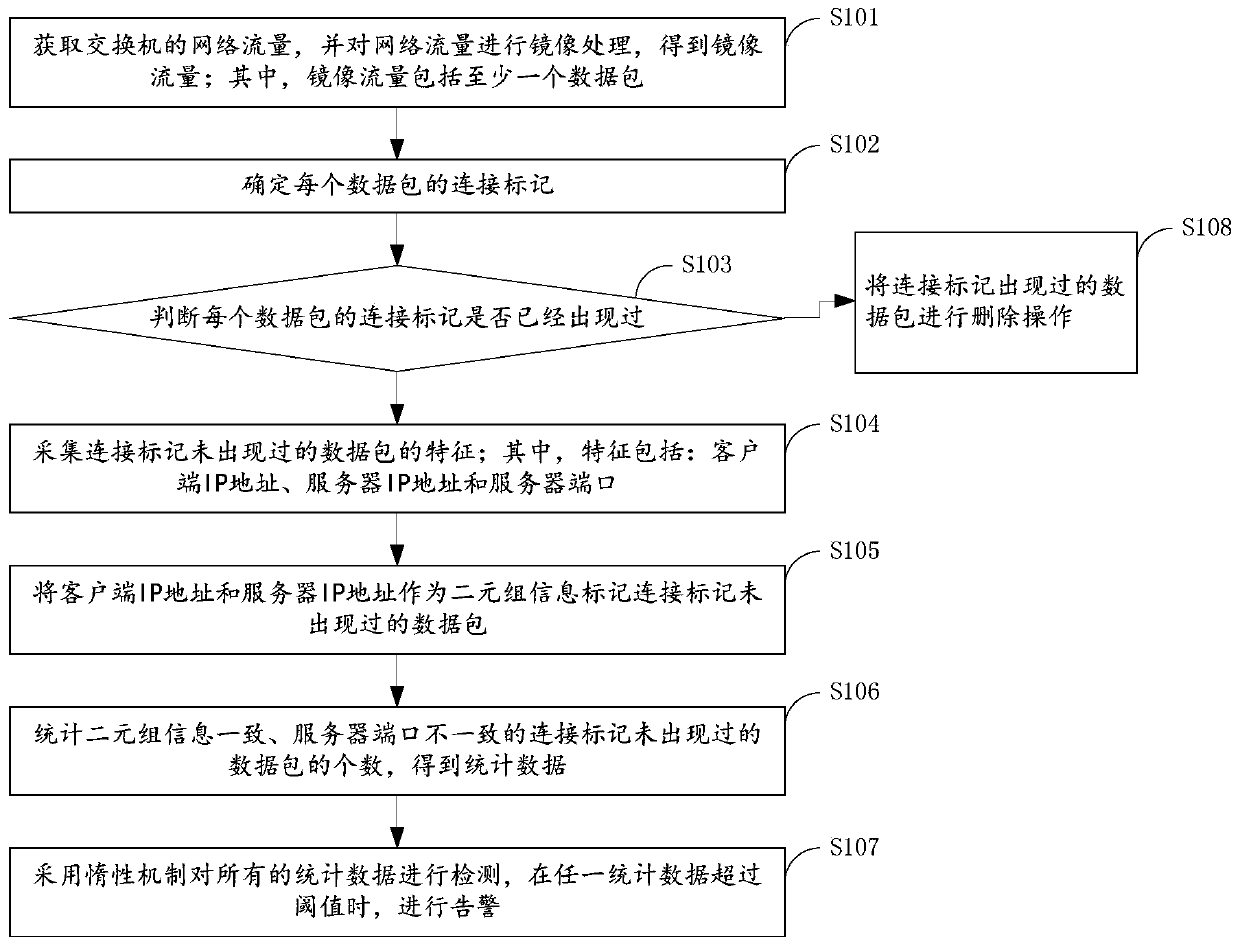
The invention provides a host port scanning behavior detection method and device, and relates to the technical field of information security, and the method comprises the steps: obtaining the networkflow of a switch, and carrying out the mirroring of the network flow, and obtaining the mirroring flow, wherein the mirror image traffic comprises at least one data packet; then collecting the characteristics of the data packets of which the connection marks do not appear, wherein the characteristics comprise a client IP address, a server IP address and a server port; taking the client IP addressand the server IP address as two-tuple information to mark data packets which do not appear in the connection mark; counting the number of data packets of which the two-tuple information is consistentand the server ports are inconsistent and the connection marks do not appear to obtain statistical data; and finally, detecting all statistical data by adopting an inertia mechanism, and giving an alarm when any statistical data exceeds a threshold value. According to the invention, the scanning behavior can be rapidly detected, and the scanned server can be accurately determined.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Port scan detection method and device
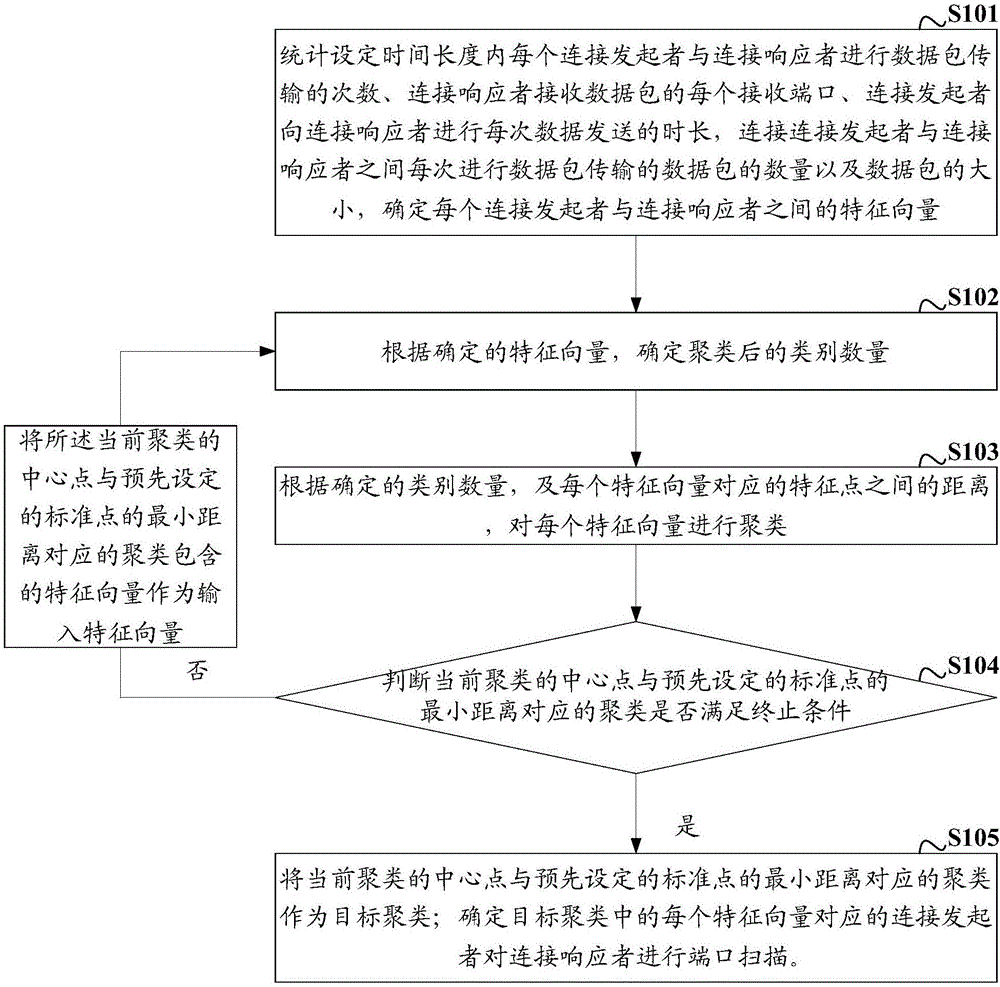
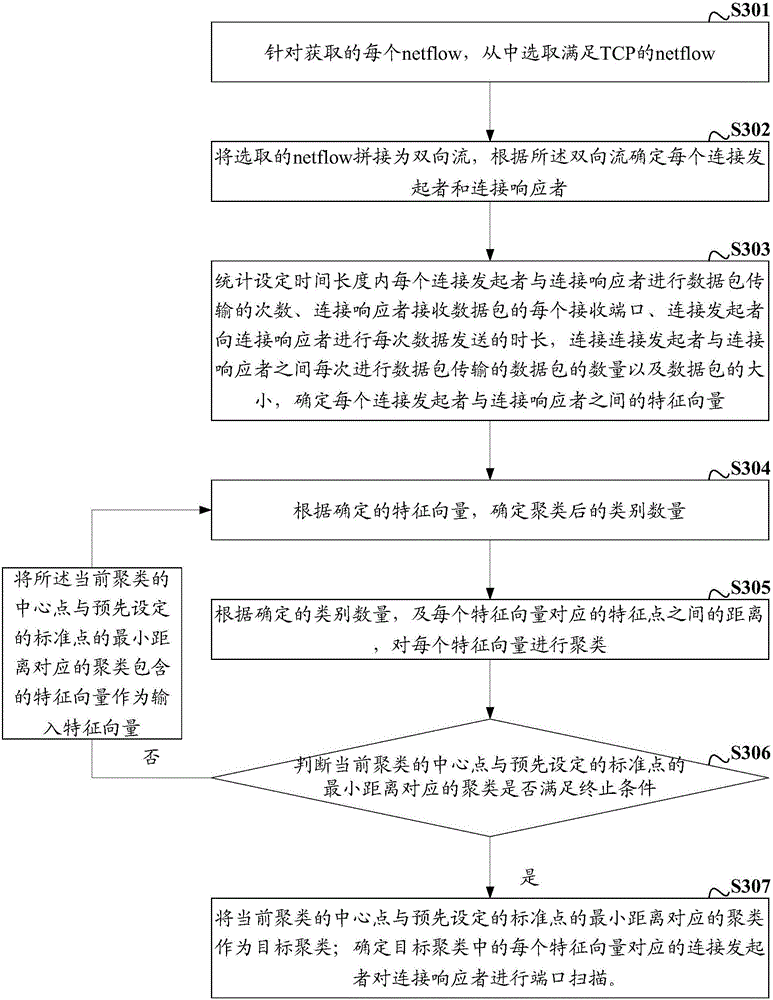
ActiveCN106506557AExpand the scope of scan detectionAvoid misjudgmentTransmissionFeature vectorPort scan
Embodiments of the invention disclose a port scan detection method and device. The method comprises the following steps of (A) counting information for carrying out data packet transmission between each connection initiator and each connection responder within a set time duration; (B) determining a number of categories after clustering; (C) clustering feature vectors according to the determined number of categories and a distance between feature points corresponding to the feature vectors; judging whether a cluster corresponding to a minimum distance between a central point of a current cluster and a preset standard point meets a termination condition; if no, carrying out (B); and (D) if yes, taking the cluster corresponding to the minimum distance between the central point of the current cluster and the preset standard point as a target cluster; and determining the connection initiator corresponding to each feature vector in the target cluster to carry out port scan on the connection responder. The method and the device are used for solving the problems of small port scan detection range, low detection precision and bad performance of the existing technology.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com