Network asset identification method and device, medium and equipment
A network asset and identification method technology, applied in the field of network information security, can solve the problems of reducing company/enterprise network security, difficulty in network equipment asset management, and lack of dedicated management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] In order to make the above objects, features and advantages of the present application more obvious and comprehensible, the present application will be further described in detail below in conjunction with the accompanying drawings and specific implementation methods.
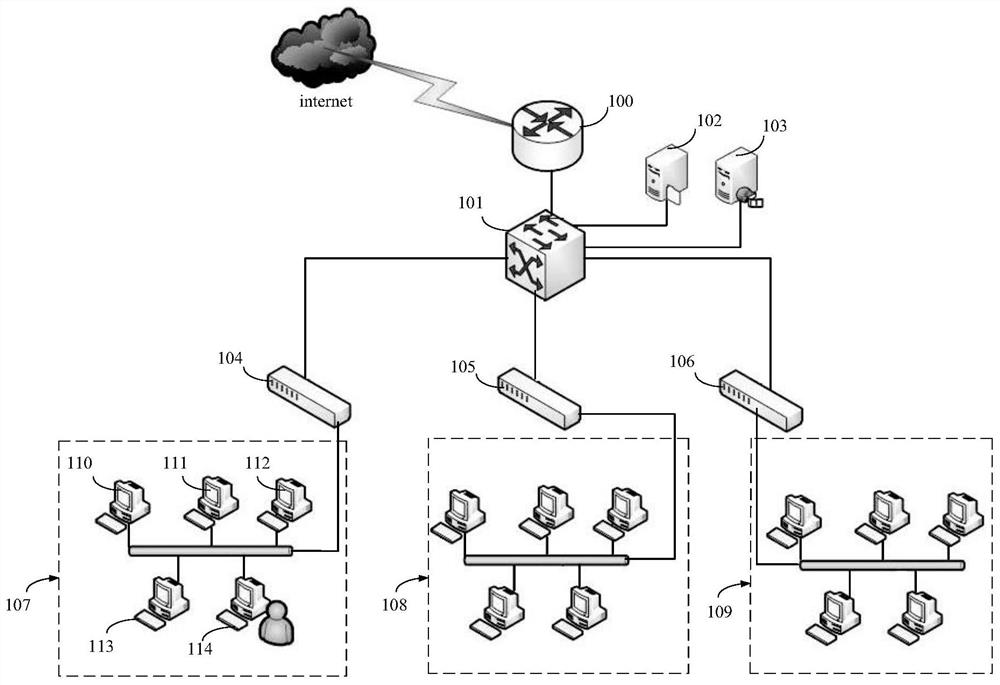
[0038] figure 1 It is a schematic diagram of an implementation environment shown according to an exemplary embodiment. figure 1 A schematic diagram of a network of a company (Company1) is shown in , and the company includes three departments in total: an administrative department, a financial department, and a business department. The local area network (intranet) of the whole company is connected to the Internet (external network) Internet through router 100; , wherein the proxy server 102 is used to act as an agent for the external network access requirements of all network assets (equipment or hosts) in the whole company, and the Web server 103 is used to provide the personnel of the whole company to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com