Host port scanning behavior detection method and device
A detection method and host port technology, applied in the field of information security, can solve problems such as the inability to determine the server, achieve the effect of improving statistical accuracy and reducing misjudgment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
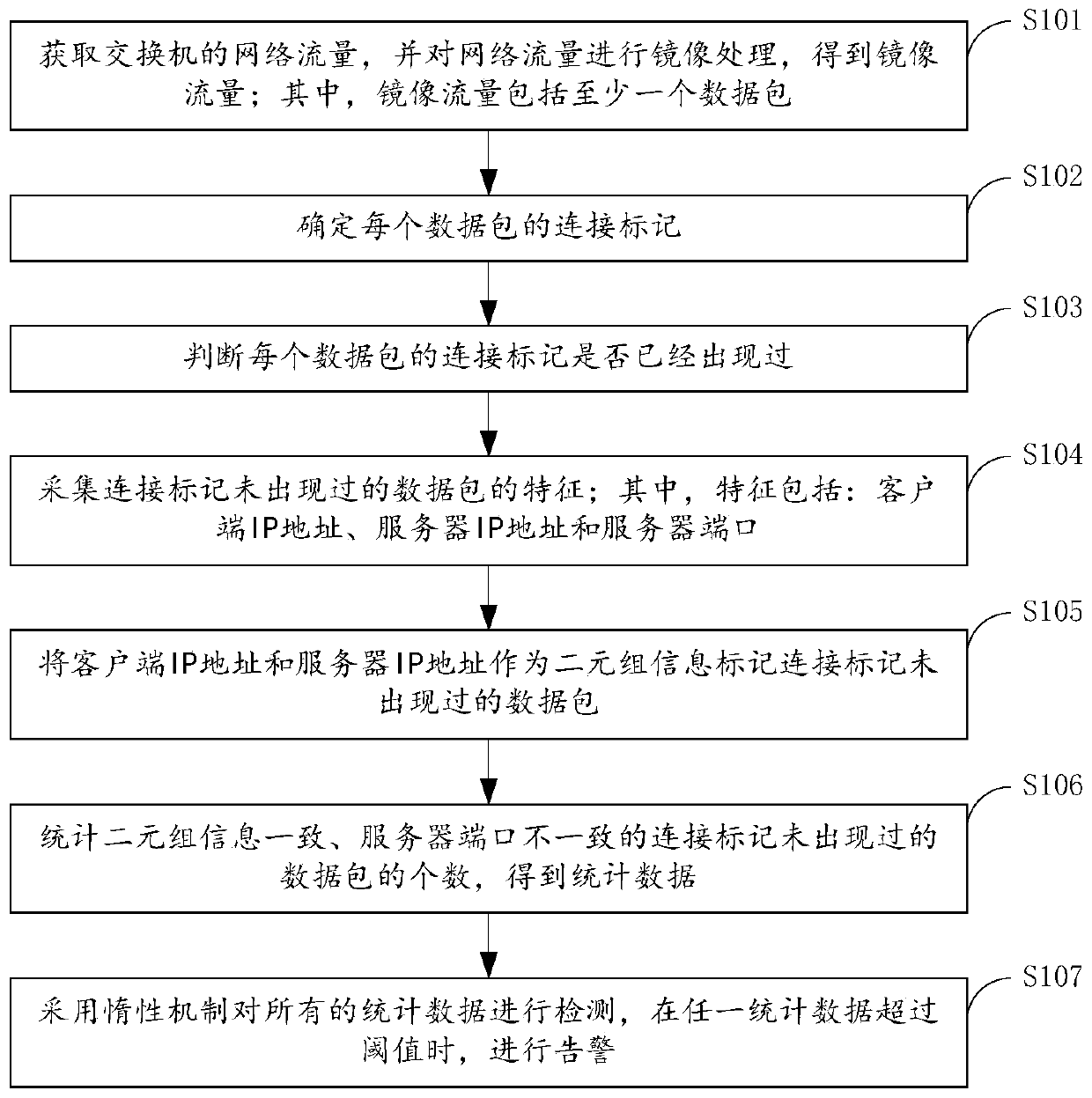
[0029] figure 1 A detection method for a host port scanning behavior provided by an embodiment of the present invention. refer to figure 1 , where the method includes the following steps:
[0030] Step S101 , acquiring network traffic of a switch, and mirroring the network traffic to obtain mirrored traffic; wherein, the mirrored traffic includes at least one data packet.
[0031] In the embodiment of the present invention, in order to obtain the network traffic of the switch, the embodiment of the present invention first adopts the bypass monitoring mode to realize network monitoring. Wherein, the bypass monitoring mode may refer to realizing monitoring through a "port mirroring" function of a network device such as a switch. The deployment of the bypass monitoring mode is flexible and convenient, and the network traffic can be obtained by configuring the mirror port on the switch without affecting the existing network structure. In addition, the mirrored traffic is analy...
Embodiment 2
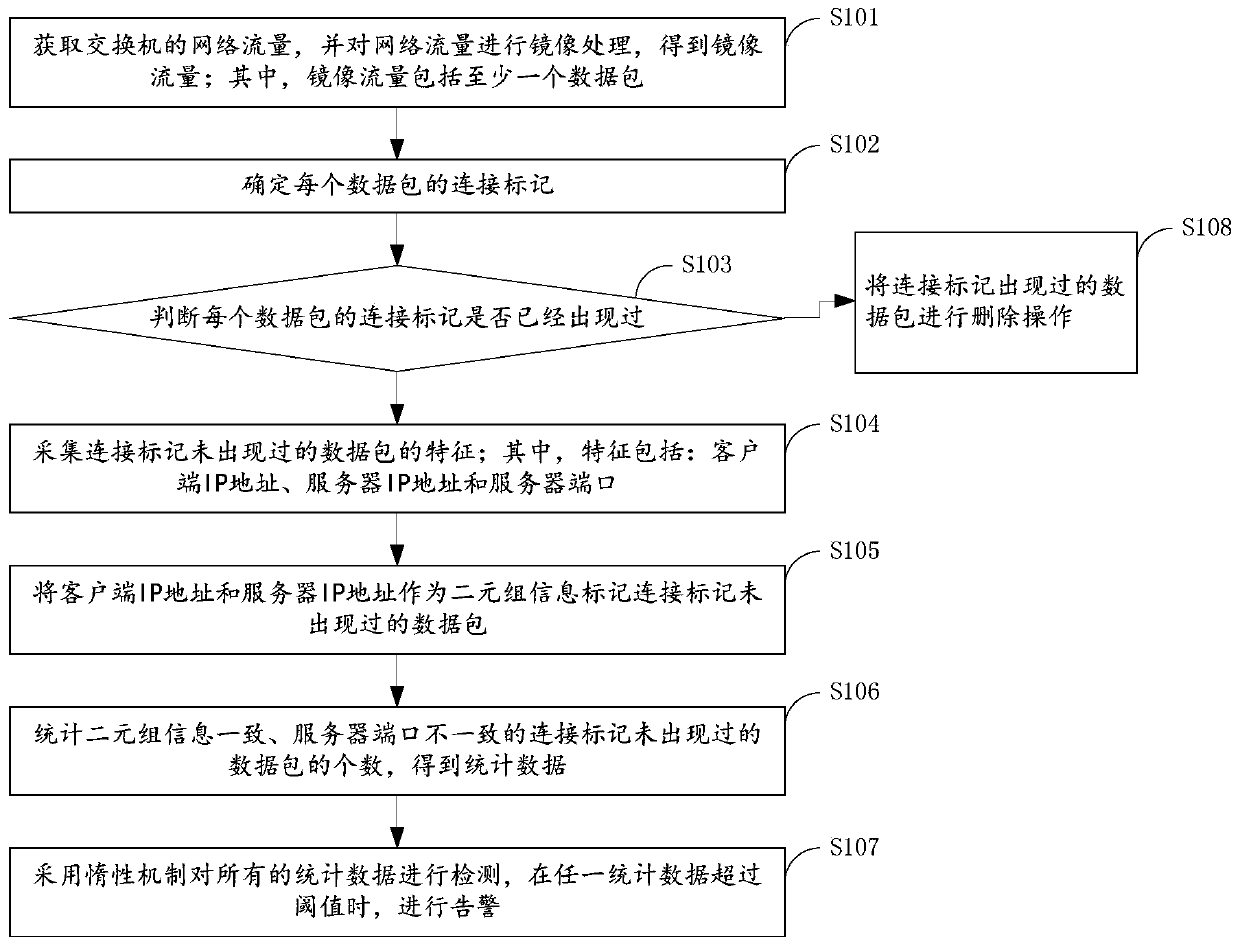
[0059] Figure 4 A device for detecting host port scanning behavior provided by an embodiment of the present invention. refer to Figure 4 , the above device may include the following modules:
[0060] The acquiring module 11 is configured to acquire network traffic of the switch, and perform mirroring processing on the network traffic to obtain mirrored traffic; wherein, the mirrored traffic includes at least one data packet;
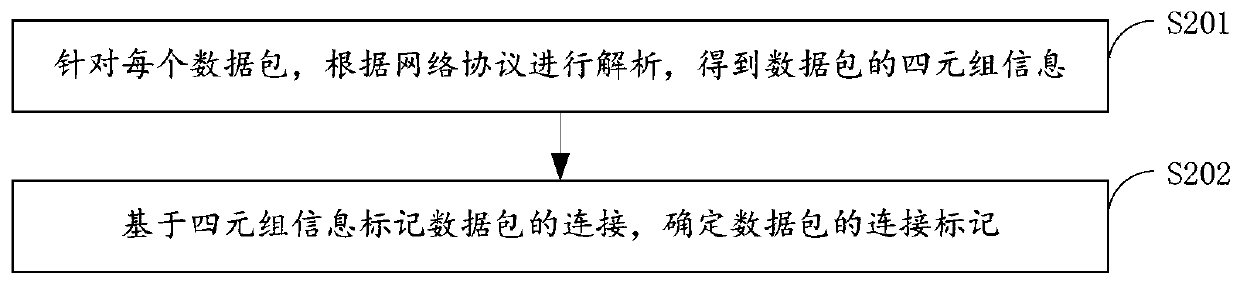
[0061] The acquisition module 11 may refer to the traffic collection module, the purpose of which is to obtain the mirrored traffic obtained by the switch for mirroring the network traffic, that is to say, to copy the network traffic and pass it to the preprocessing module, wherein the preset module refers to the processing of data packets The preprocessing module, the purpose of the preset module is to mark different connections according to different client IP addresses, client ports, server IP addresses, and server ports. At the same time, it is ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com