Port scan detection method and device
A port scanning and receiving port technology, which is applied in the field of network security, can solve problems such as low detection accuracy, poor performance, and small detection range of port scanning, and achieve the effects of improving accuracy and performance, expanding range, and avoiding misjudgment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
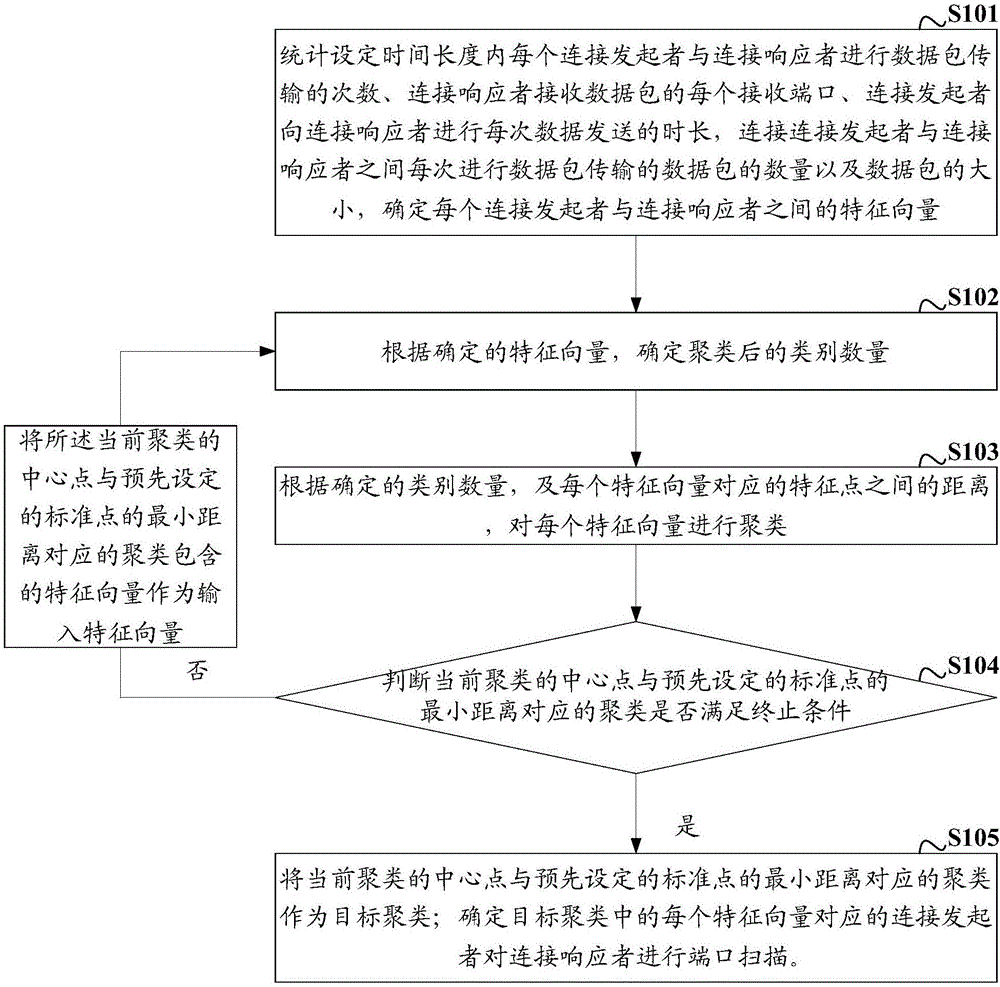
[0042] figure 1 A schematic diagram of a port scanning detection process provided by an embodiment of the present invention, the process includes:
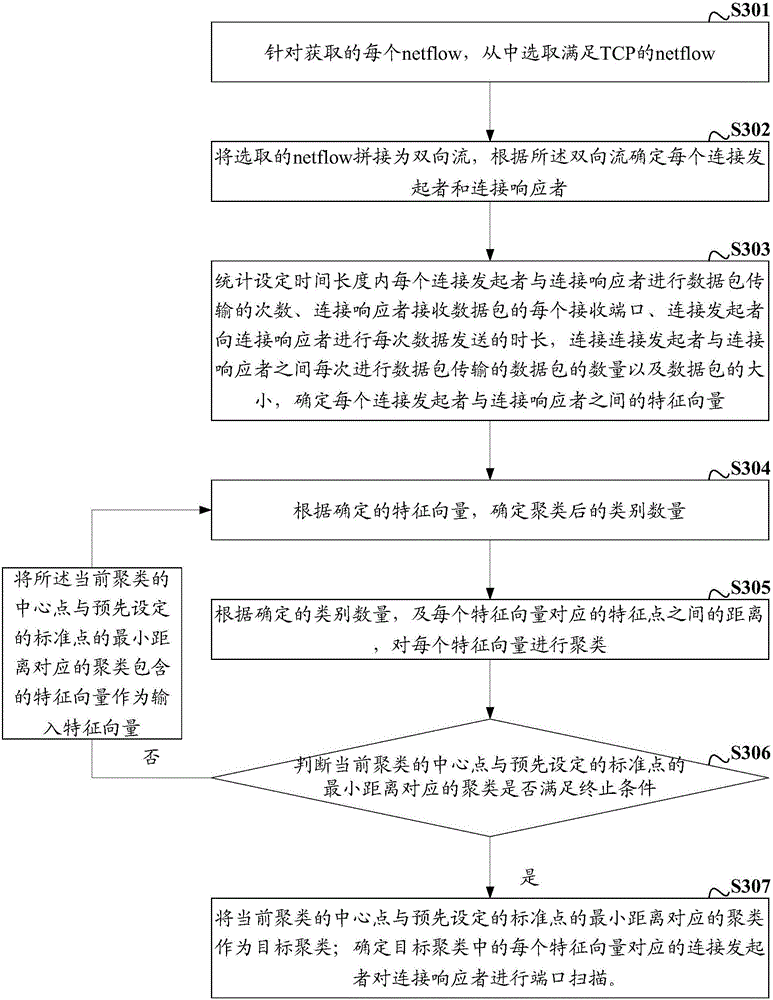
[0043] S101: Count the number of data packet transmissions between each connection initiator and connection responder within the set time period, each receiving port of the connection responder receiving data packets, and the duration of each data transmission from the connection initiator to the connection responder , the number of data packets and the size of data packets transmitted between the connection initiator and the connection responder each time, determine the feature vector between each connection initiator and the connection responder.
[0044] In the embodiment of the present invention, the connection initiator generally refers to a device such as a personal computer (PC) or a server that initiates port scanning, and the connection responder generally refers to a device such as a server whose port is scanned. During...
Embodiment 2
[0057] In order to improve the accuracy of port scanning detection, on the basis of the above embodiments, in the embodiment of the present invention, the determining the feature vector between each connection initiator and connection responder includes:
[0058] For each connection initiator and connection responder, the number of data packet transmissions, each receiving port for the connection responder to receive data packets, the duration of each data transmission from the connection initiator to the connection responder, and the connection initiator and connection response The number of data packets and the size of data packets for each data packet transmission between the two parties, and determine each parameter in the feature vector between the connection initiator and the connection responder, wherein the first parameter is the connection responder The ratio of the second number of data transmissions to the connection initiator and the first number of data transmissio...
Embodiment 3
[0062] On the basis of the above-mentioned embodiments, in order to facilitate the subsequent determination of the feature vector between each connection initiator and connection responder, in the embodiment of the present invention, each connection initiator to the connection within the statistically set time length Before the responder initiates the number of data transfers, the method further includes:
[0063] For each unidirectional network flow program (netflow) obtained, select the netflow that satisfies the Transmission Control Protocol (TCP);
[0064] The selected netflow is spliced into a bidirectional flow, and each connection initiator and connection responder is determined according to the bidirectional flow.
[0065] A netflow is generated every time a data packet is transmitted between the connection initiator and the connection responder, and the information contained in the netflow can be obtained by analyzing each netflow. Such as figure 2 Shown is a sch...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com