Honeypot attacker tracing method based on TCP/UDP transparent proxys
A transparent proxy and attacker technology, applied in the direction of electrical components, transmission systems, etc., can solve the problem of incomplete application log attacker information, and achieve the effect of reducing the difficulty of development
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
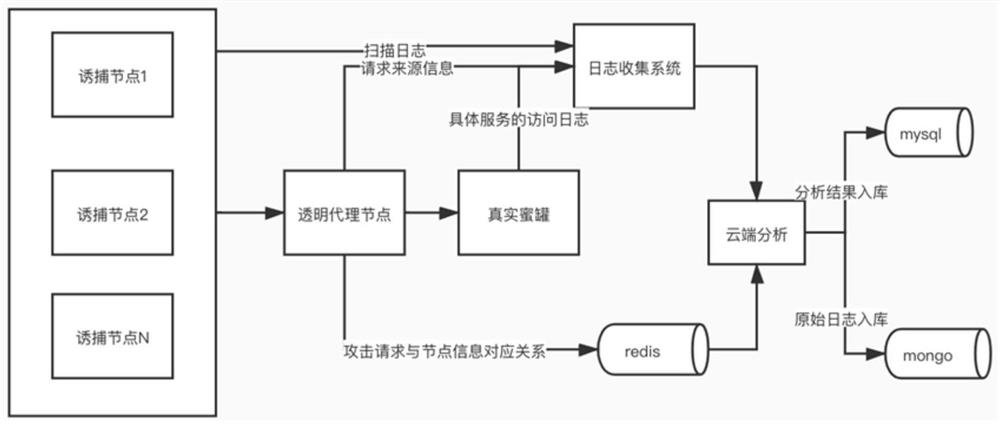
[0021] like figure 1 As shown, a method for tracing the source of a honeypot attacker based on TCP / UDP transparent proxy, including the following steps:
[0022] (1) Business party traps node traffic forwarding:
[0023] The SOCKET+EPOLL architecture is used to implement the node forwarding program. Because the node is designed and deployed in the business network, the network routing cannot be configured, so the common proxy method is used, but the user information and node information need to be forwarded to the transparent proxy node through the proxy protocol. . The principle of ordinary proxy is that after receiving the SOCKET connection, it accepts the data and establishes a corresponding forwarding connection to the back-end transparent proxy server to forward the data. The essential principle of the proxy protocol is to send a fixed format carrying request information after the connection is established and before the data is forwarded, including a specific data pack...
Embodiment 2
[0037] A method for tracing the source of a honeypot attacker based on a TCP / UDP transparent proxy. The hardware structure of this embodiment mainly includes a honeypot trap node, a transparent proxy node, a honeypot service, and a cloud analysis system. Among them, honeypot trapping nodes and transparent proxy nodes are the most basic modules to realize traceability. Specifically include the following steps:
[0038] (1) Business side trapping node configuration pull:
[0039] Implemented in python, by establishing a socket and sending a request to pull the application string, it regularly initiates a configuration pull request to the back-end transparent proxy server, and after receiving the response, decrypts the response to obtain the node configuration.
[0040] (2) The business party traps the virtual IP of the node:
[0041] According to the pulled configuration, use the IPDB class in the python third-party library pyroute2 to virtualize the node IP in the configurati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com