Network attack scene generating method based on multi-source alarm logs
A network attack and log technology, applied in data exchange networks, digital transmission systems, electrical components, etc., can solve problems such as incomplete attack scenarios, and achieve the effect of clarifying the attacker's intentions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The present invention will be described in further detail below in conjunction with the accompanying drawings.
[0025] Basic scheme of the present invention is:
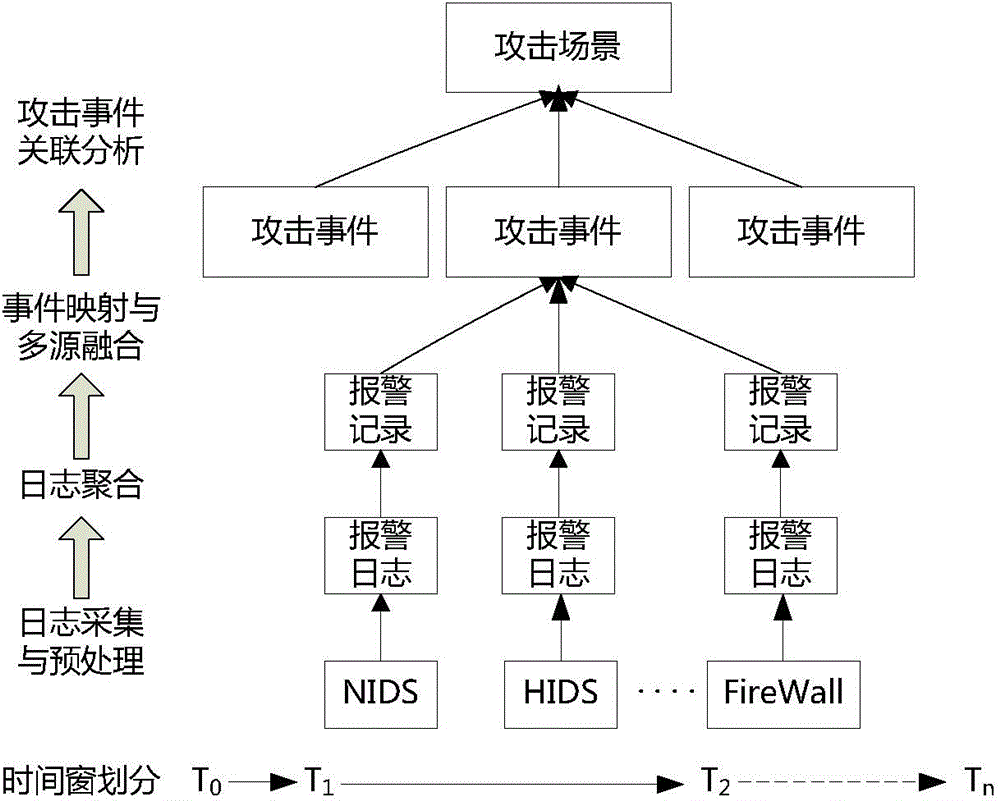
[0026] Step 1), collecting the alarm logs generated by the network security protection equipment;
[0027] Step 2), for the effective alarm log obtained by a single device, through single-source log aggregation and mapping, the difference in the log format of different devices is shielded, and the attack event information is extracted;
[0028] Step 3), performing fusion analysis on the attack event information extracted from different sources, and generating network attack event information with a set credibility;
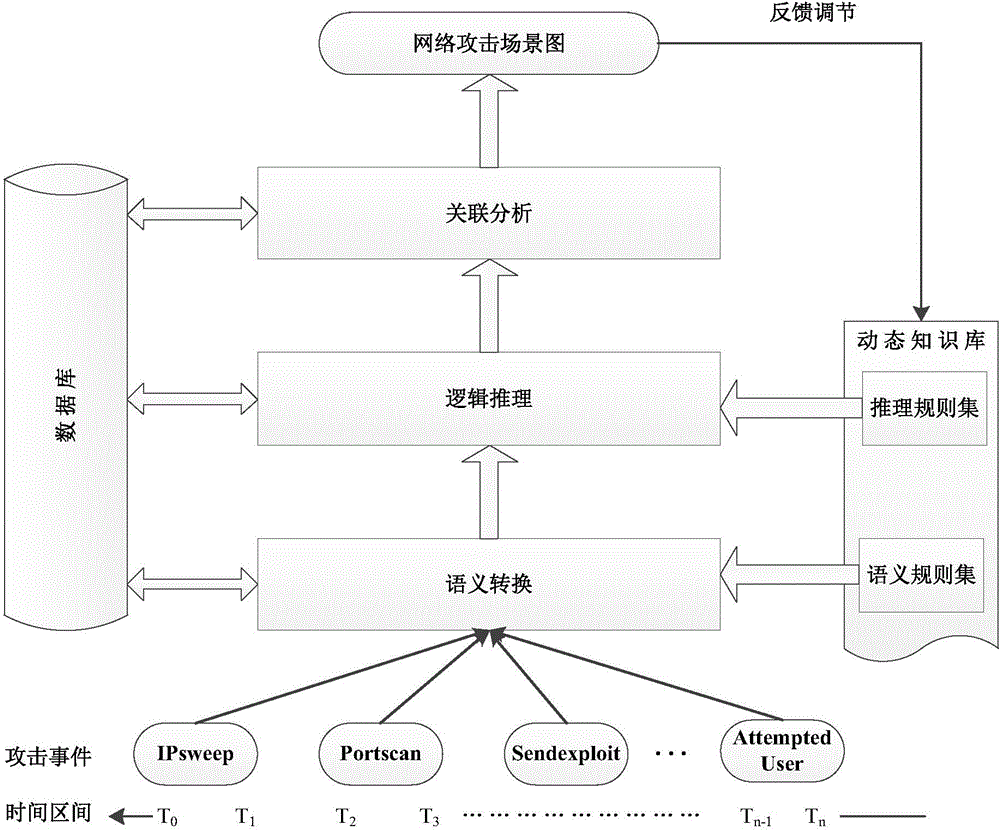
[0029] Step 4), through attack event correlation analysis, generate a network attack scene graph, and analyze the entire attack process of an attack behavior.
[0030] Specifically, a specific implementation manner is given below.
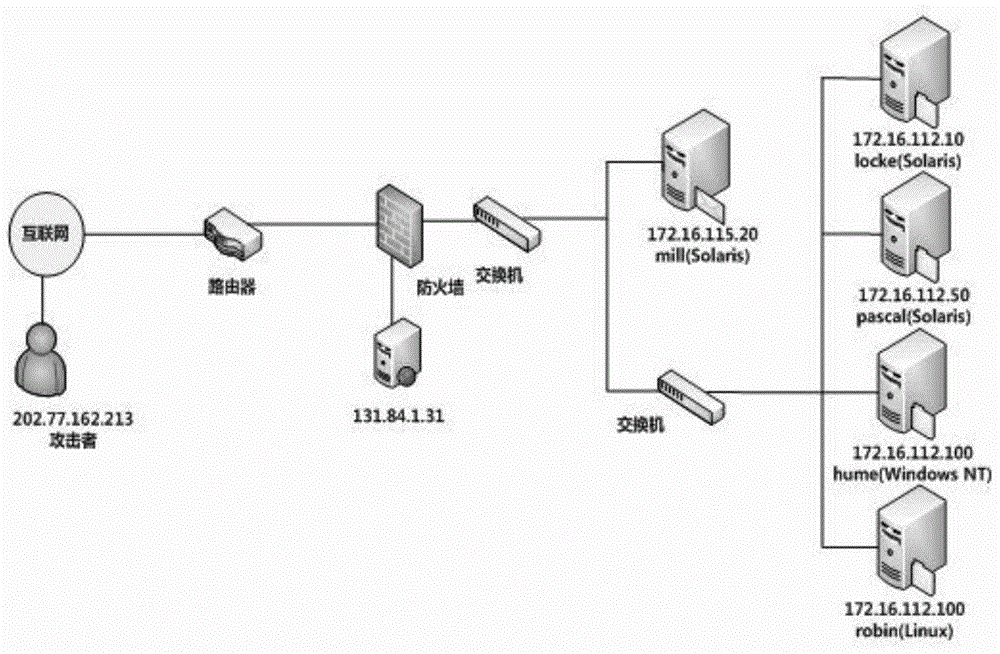
[0031] For step 1), for a specific network environment, colle...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com