Defense method and system rejecting service attack based on data mining technology
A denial of service attack and data mining technology, applied in the Internet field, can solve problems such as poor practical applicability, achieve the effect of reliable filtering mechanism and reduce manual intervention
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] In order to make the purpose, technical solution, and advantages of the present invention clearer, the technical solution of the present invention will be further described in detail below with reference to the accompanying drawings.
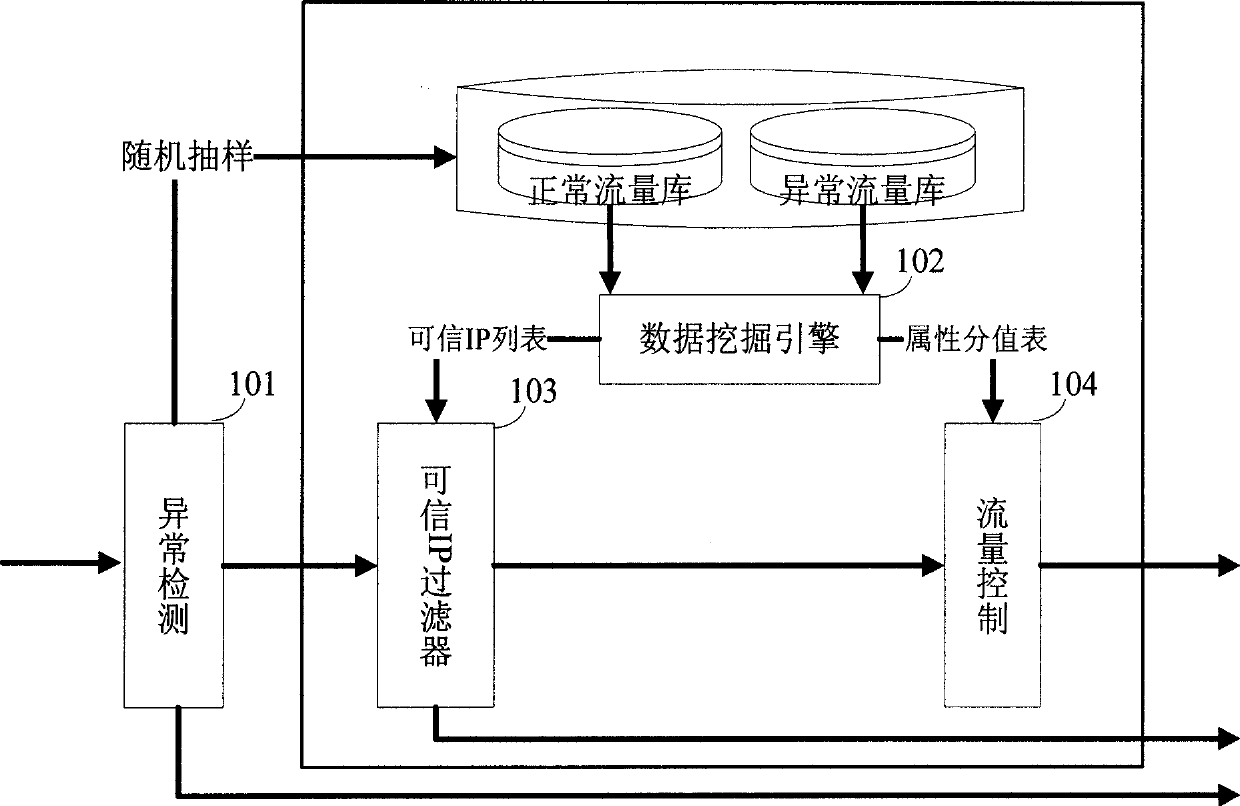
[0020] Such as figure 1 Shown, the system flowchart of defense system of the present invention.
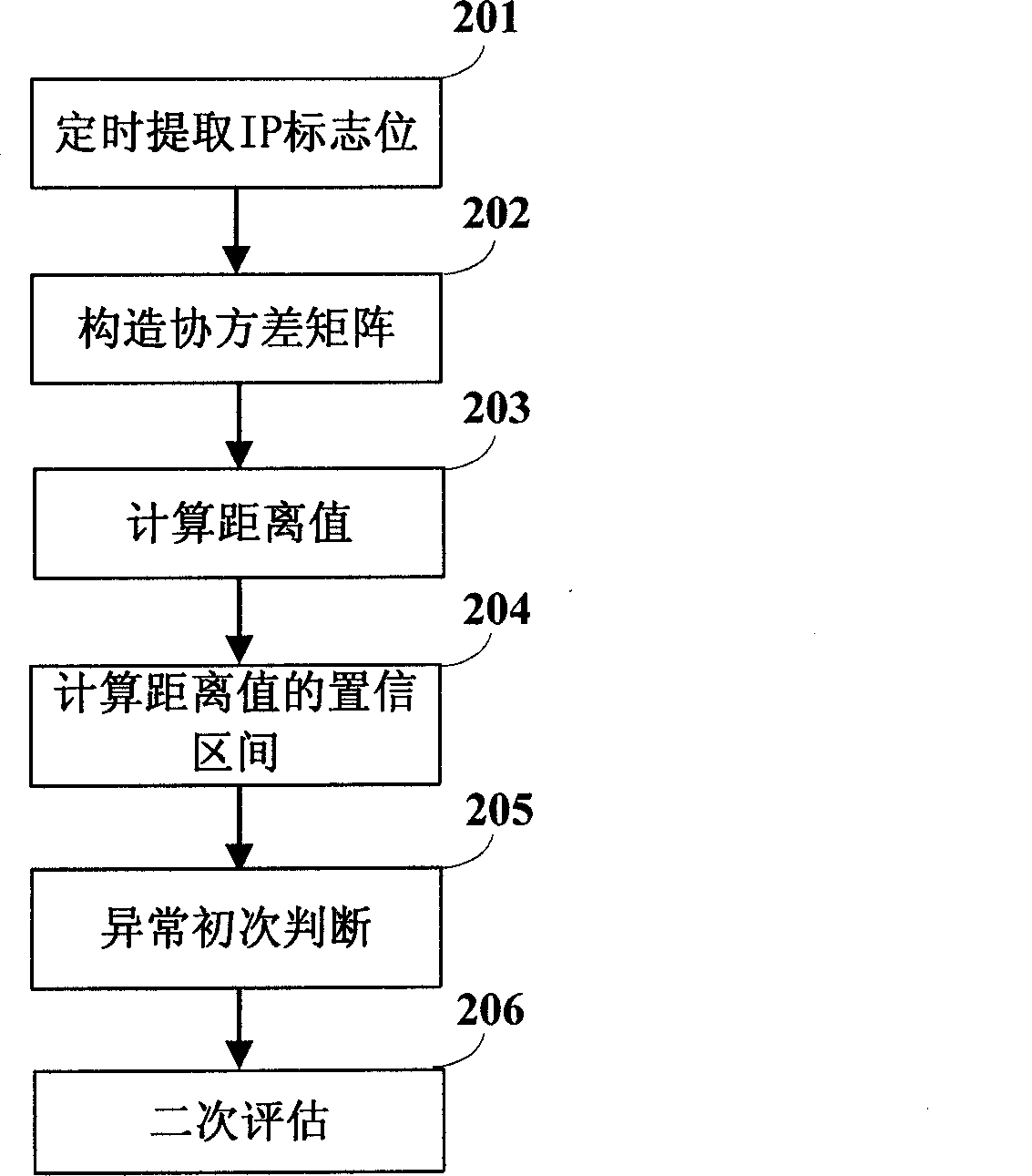
[0021] The defense system is based on anomaly detection (101) of DoS / DDoS attacks. Anomaly detection (101) adopts the covariance analysis method, and conducts secondary evaluation on the detection results to make the judgment results more accurate, effectively and real-time detection of DoS / DDoS attacks, and according to the random sampling theory and system abnormal status signs will be The network traffic is randomly sampled to the normal traffic database and abnormal traffic database of the database server, thus providing a reliable data source for the defense model.
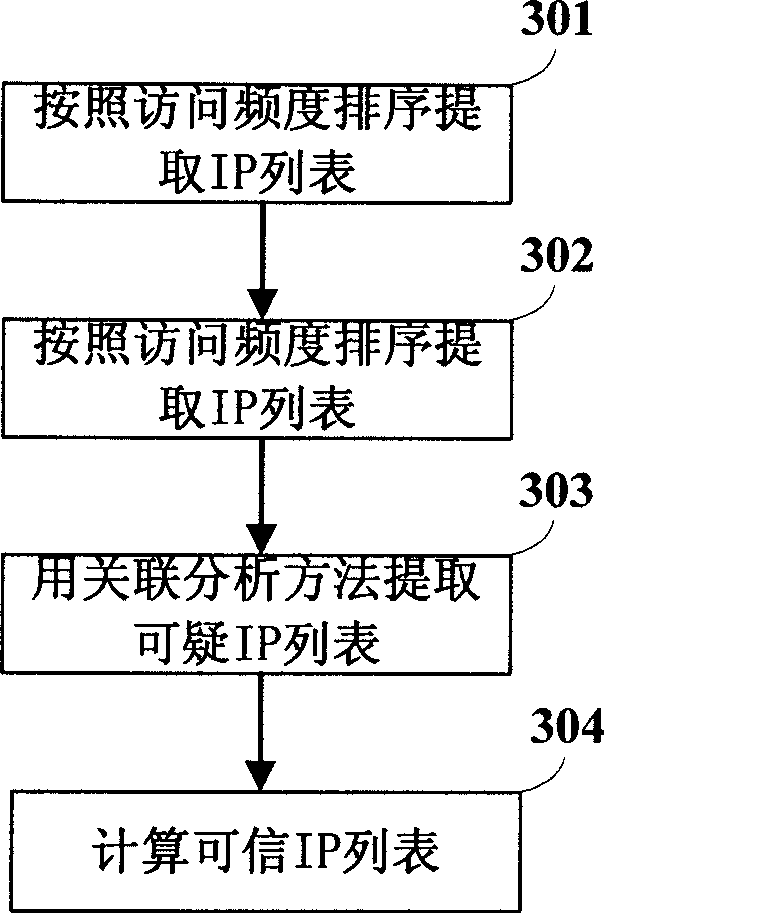
[0022] In addition to the anomaly detection module (101), the defense...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com