Switching method, device and system
A re-authentication and re-association technology, applied in the field of handover technology, can solve problems such as difficult physical security, high key management overhead, and limited network scale, and achieve small key security, fast and secure handover, and authentication delay small effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
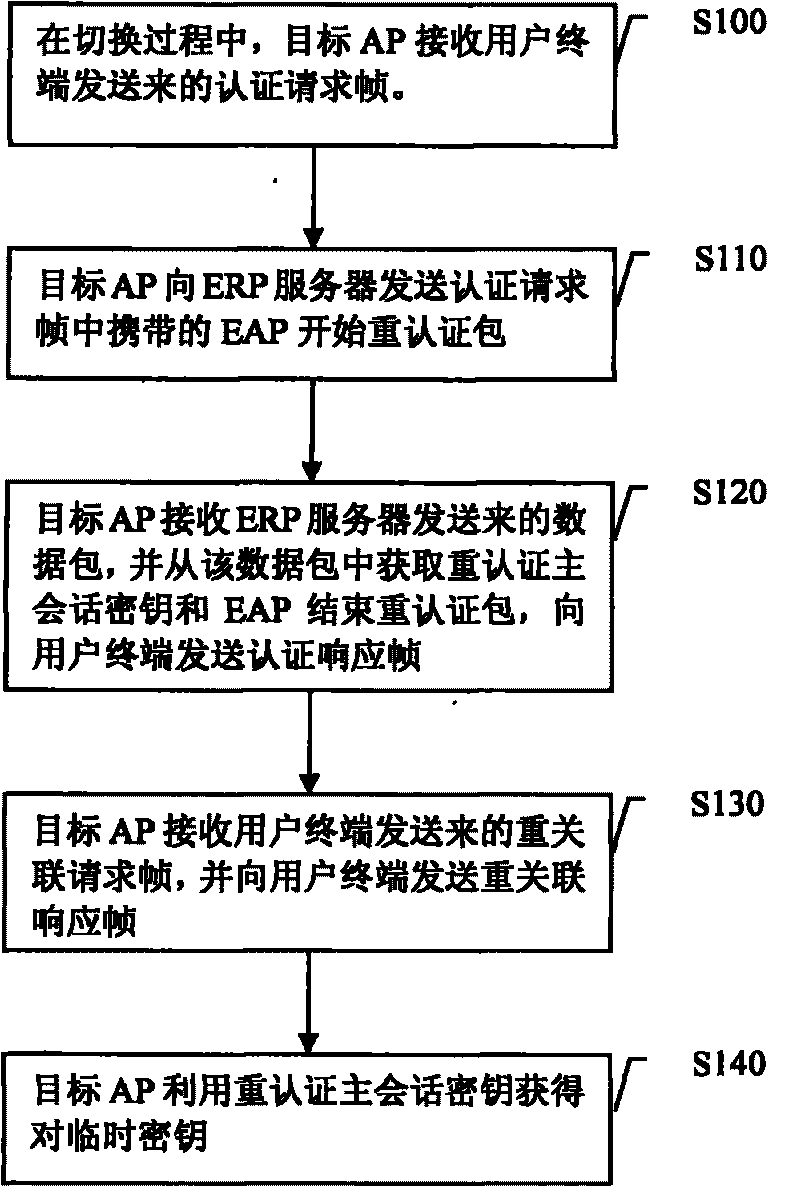
[0037] Embodiment 1, switching method. The flow of the switching method is attached Figure 1A shown.
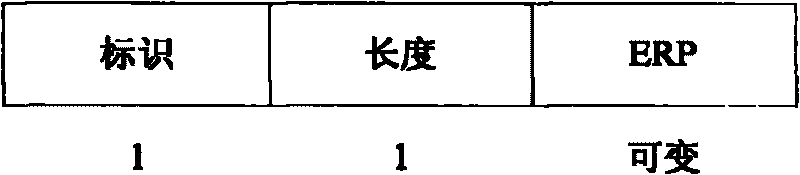
[0038] exist Figure 1A , S100. During the handover process, the target AP receives the authentication request frame sent by the user terminal. The authentication request frame here carries the EAP start re-authentication packet, and the EAP start re-authentication packet can be Extensible Authentication Framework Re-authentication Protocol Information Element (ERPIE, extensible authentication framework re-authentication protocol information element or ERP information element or ERP information element) in the form of the authentication request frame, that is, the authentication request frame carries the ERP information element, and the EAP start re-authentication packet is encapsulated in the ERP information element. A specific example of ERP cells is attached Figure 1B shown.
[0039] Figure 1B The fields included in the ERP information element are: element identific...
Embodiment 2
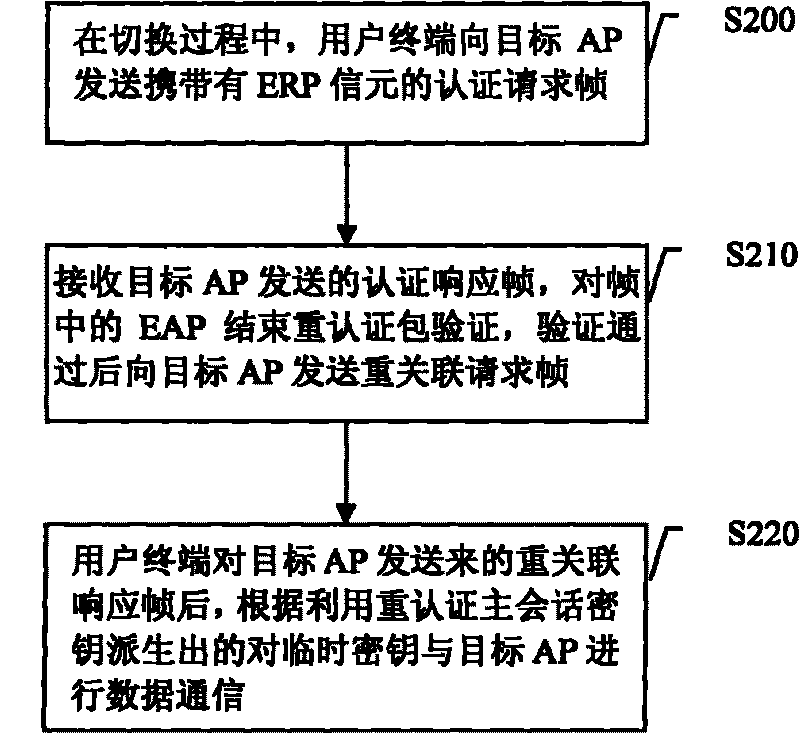
[0055] Embodiment 2, switching method. The flow of the switching method is attached figure 2 shown.
[0056] exist figure 2 , S200. During the handover process, the user terminal sends an authentication request frame carrying an EAP start re-authentication packet to the target AP.
[0057] Specifically, the user terminal carries the EAP start re-authentication packet in the authentication request frame in the form of an ERP cell, that is, the authentication request frame carries the ERP cell containing the EAP start re-authentication packet. A specific example of the ERP information element carried in the authentication request frame is as in the above-mentioned embodiment for Figure 1B description and will not be repeated here.
[0058] S210. The user terminal sends a re-association request frame to the target AP after receiving the authentication response frame carrying the EAP end re-authentication packet sent by the target AP.
[0059] Specifically, after receiving...
Embodiment 3
[0068] Embodiment 3, switching method. The process of handing over the user terminal UE from AP1 to AP2 is shown in the attached image 3 shown.
[0069] exist image 3 , S300, UE and AP1 perform secure data transmission.
[0070] S310. After the UE decides to switch from AP1 to AP2, the UE sends an Authentication Request (authentication request) frame to AP2. The Authentication Request frame carries FT AuthenticationAlgorithm (FT Authentication Algorithm, FTAA), Mobility Domain Information Element (Mobility Domain Information Element, MDIE), Fast Transition Information Element (fast switching information element, FTIE) and ERPIE. The FTIE includes SNonce (such as a 256-bit random bit string provided by the user terminal), and the ERPIE includes an EAP Initiate Re-auth (EAP starts re-authentication) packet.
[0071] S320, AP2 receives the Authentication Request frame sent by the UE, and parses the frame to obtain an EAP Initiate Re-auth packet, AP2 re-encapsulates the EAP ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com