Method and device for realizing access control
A technology of access control and access rights, applied in the computer field, can solve problems such as improving user satisfaction, increasing management overhead, and additional network burden, so as to achieve the effect of improving user satisfaction and reducing management overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
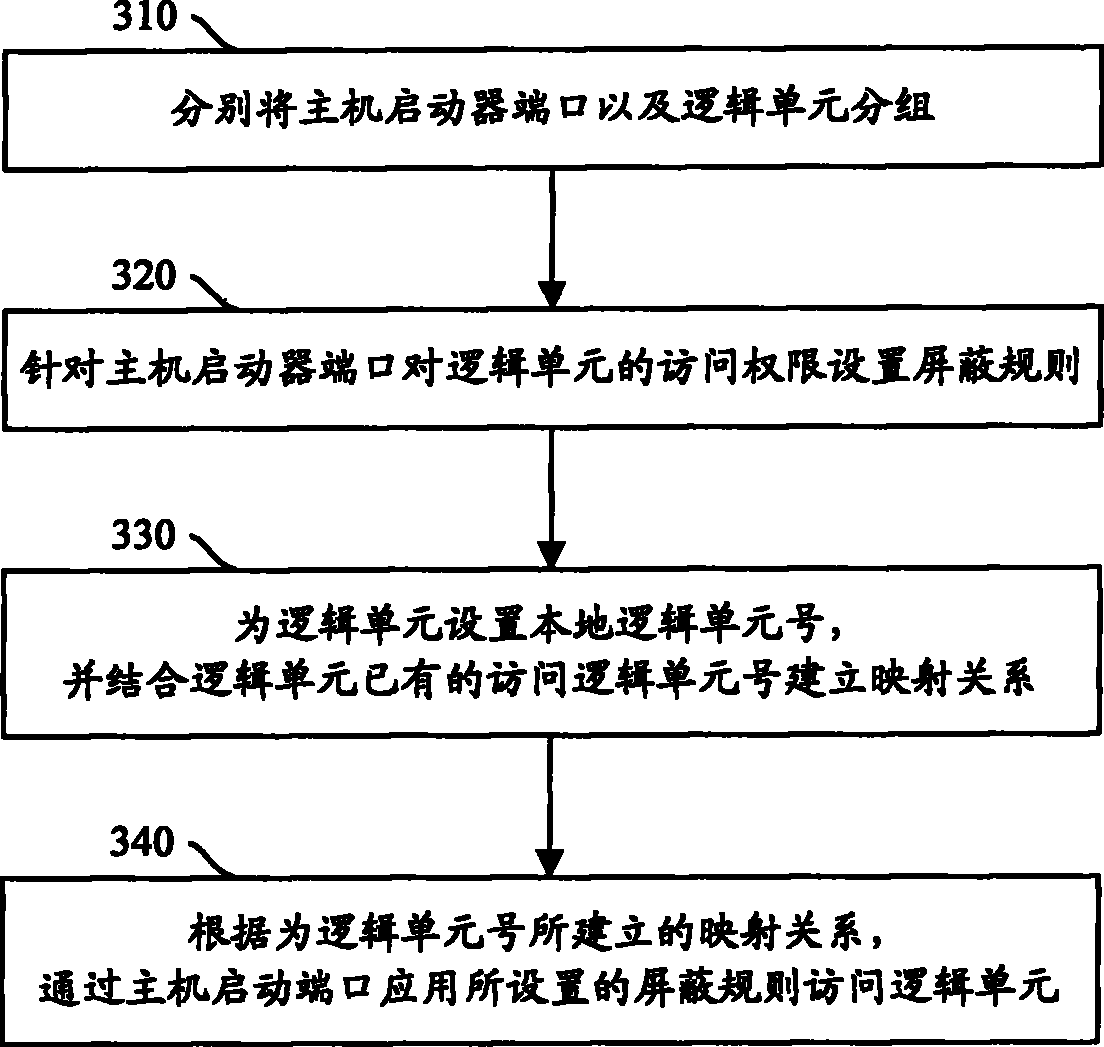
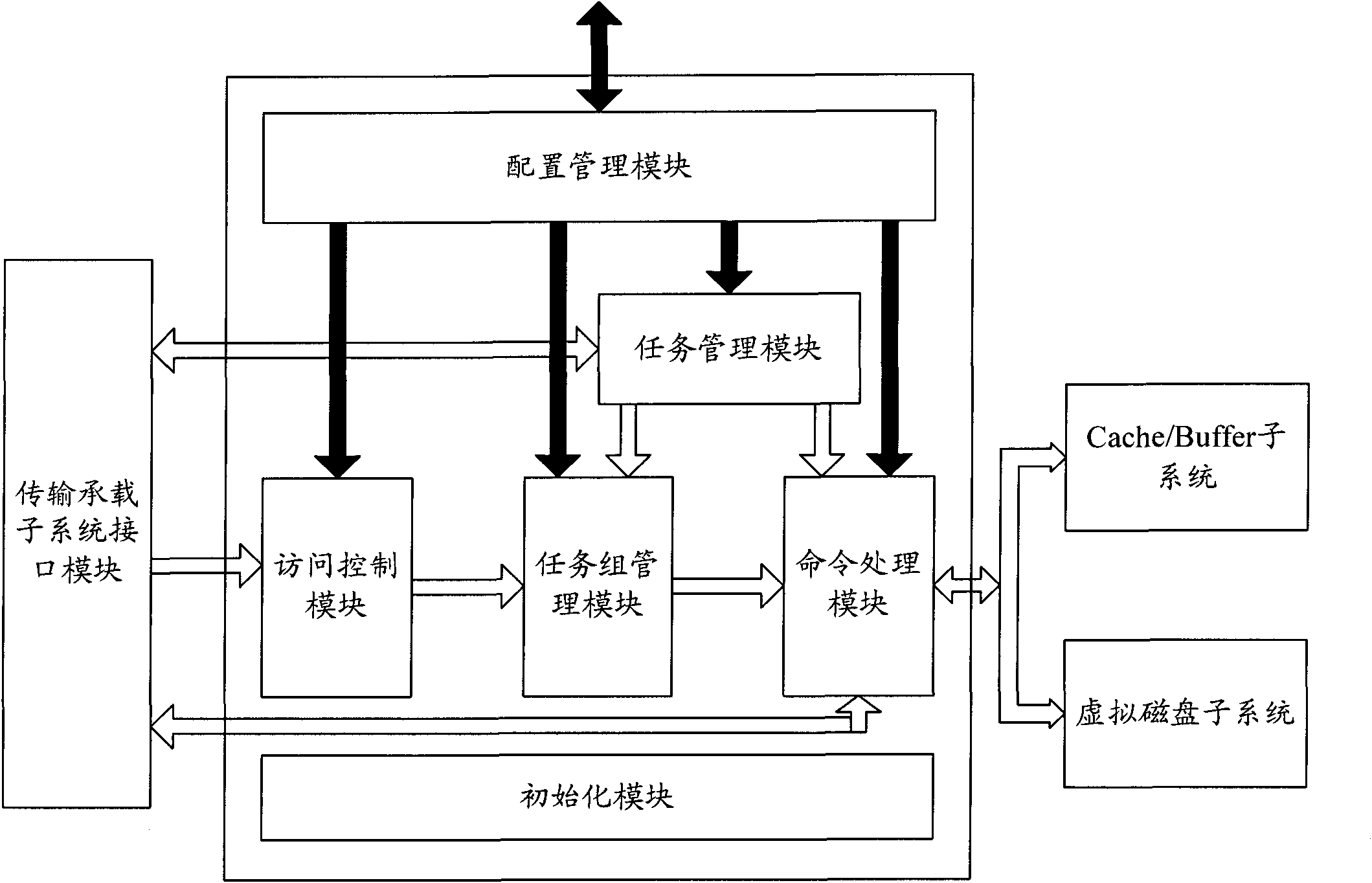
[0031] In actual application, in the IO data flow operation of SCSI command processing, the SCP subsystem is located above the transmission bearer subsystem, and interfaces exist between the Cache / Buffer subsystem and the virtual disk subsystem. In addition, the SCP subsystem interacts with the application management subsystem in user mode by using the operating system service provided by the operation support subsystem, accepts the control, configuration and management of the application management subsystem, and records log information.
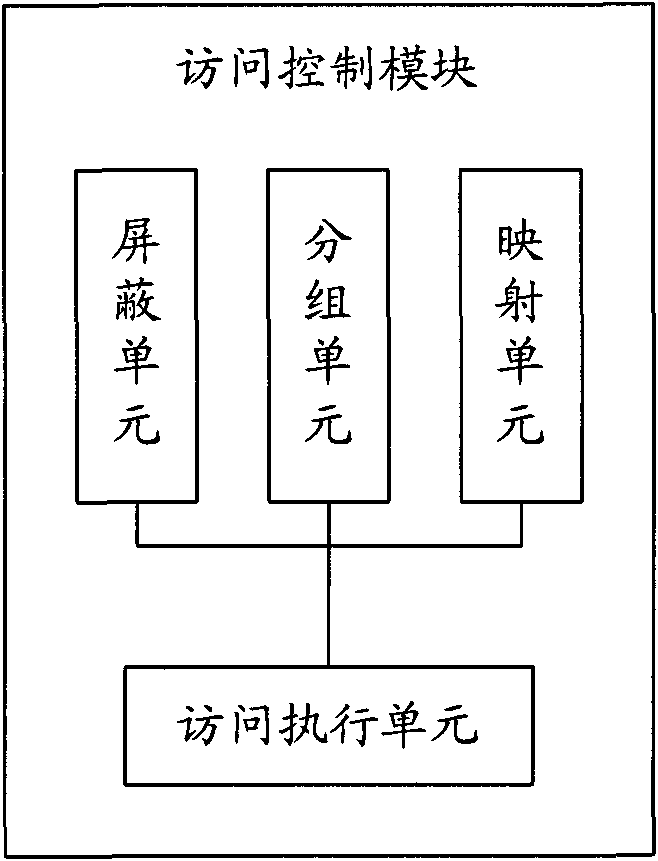
[0032] Referring to FIG. 1, FIG. 1 is a schematic structural diagram of the SCP subsystem. In Figure 1, the SCP subsystem can be divided into the following modules: initialization module, access control module, task group management module, command processing module, task management module and configuration management module. Among them, the initialization module is responsible for the loading and unloading of the entire SCP subsystem, the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com