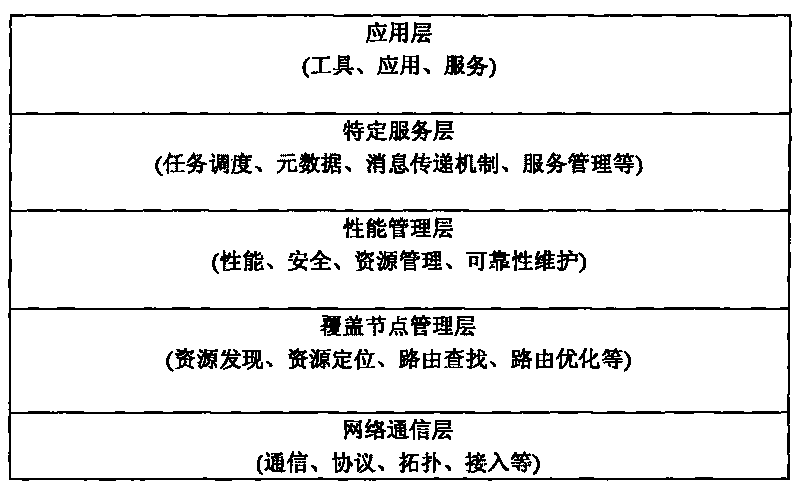
Patents
Literature
37 results about "Peer to peer computing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
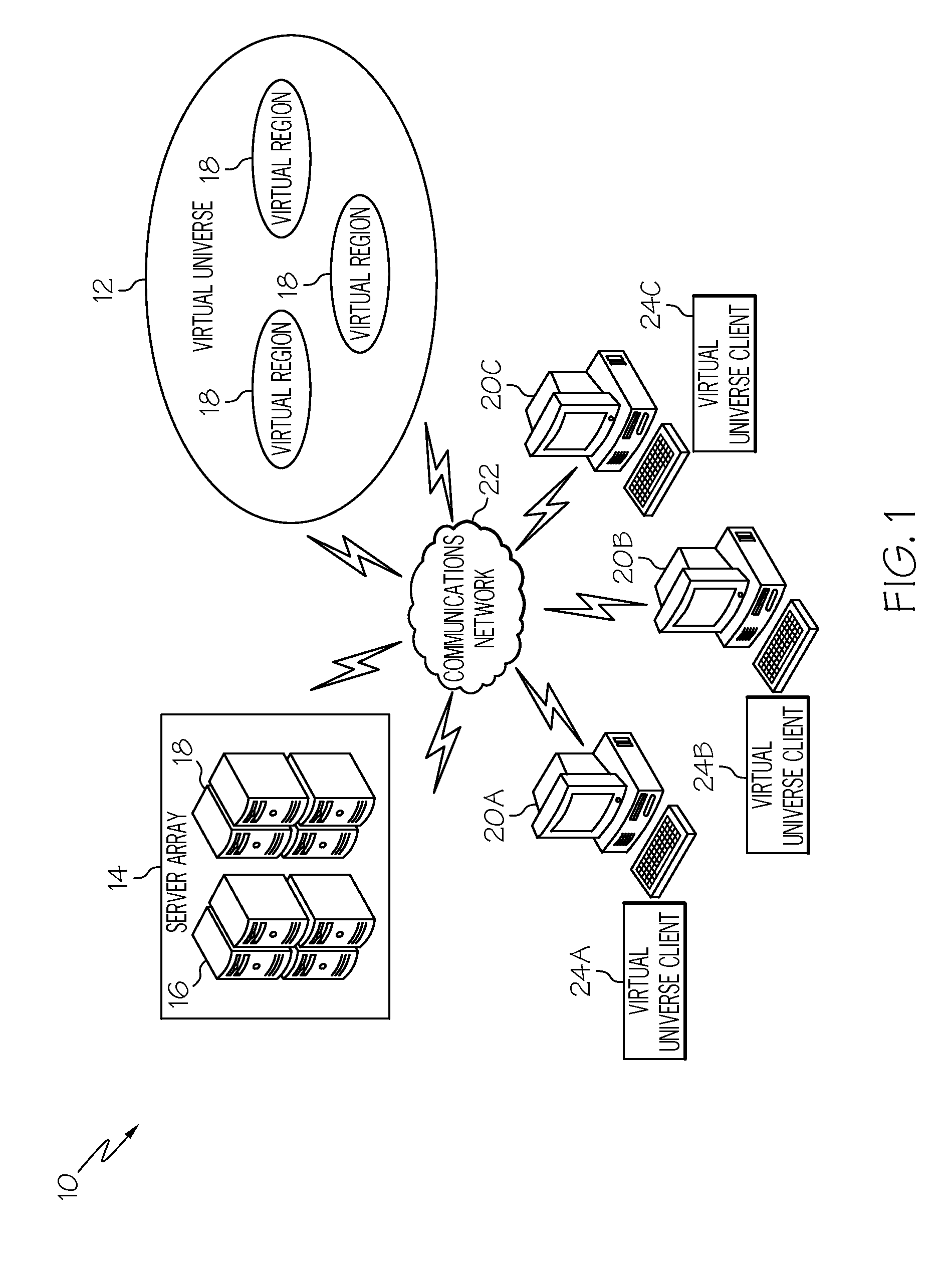
Peer to peer communications allow people to communicate with each other directly, with each computer in the network acting as both a client and a server. These systems can be designed to be permanent or transient in nature, depending on the needs of the users and the system.
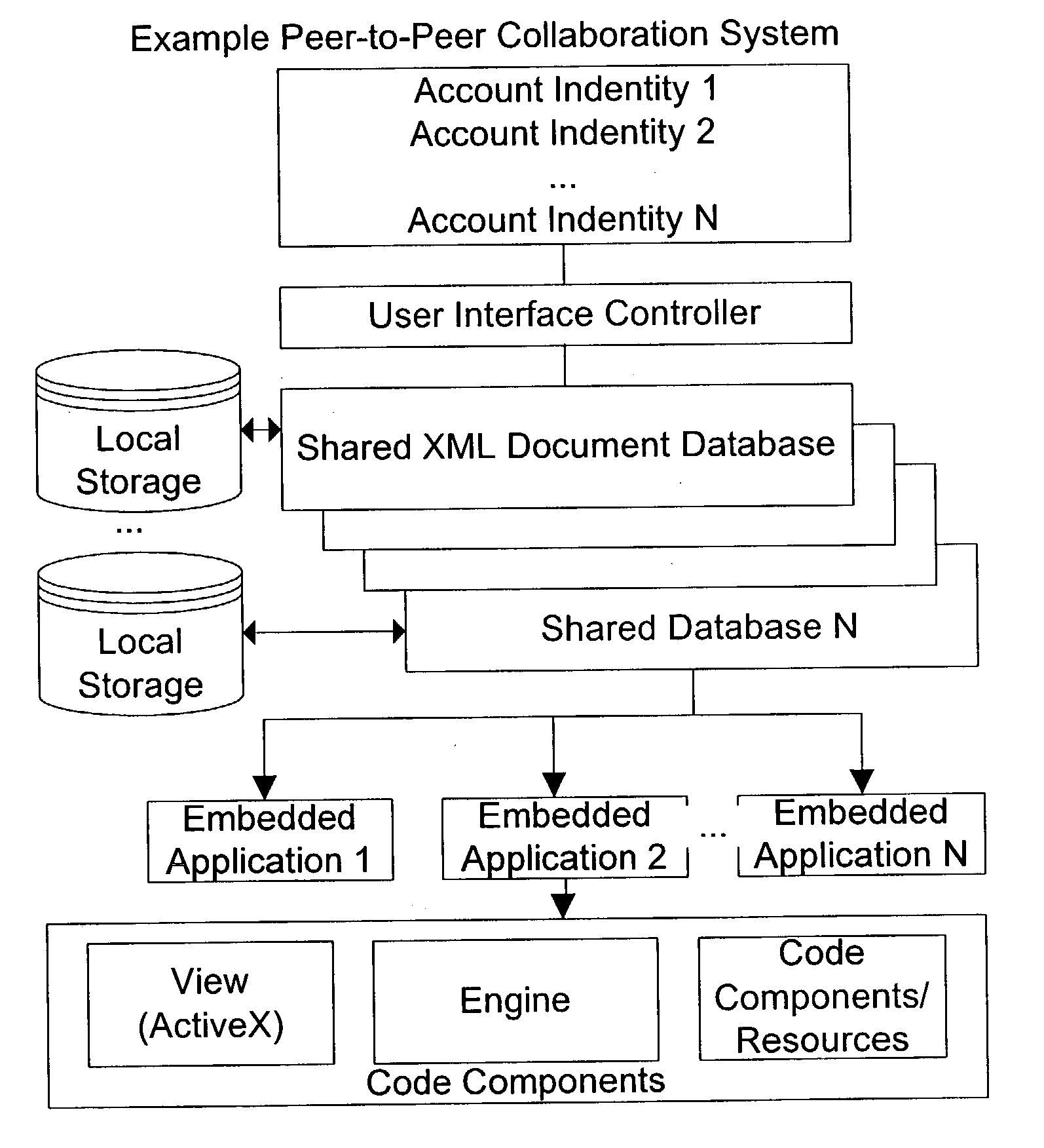
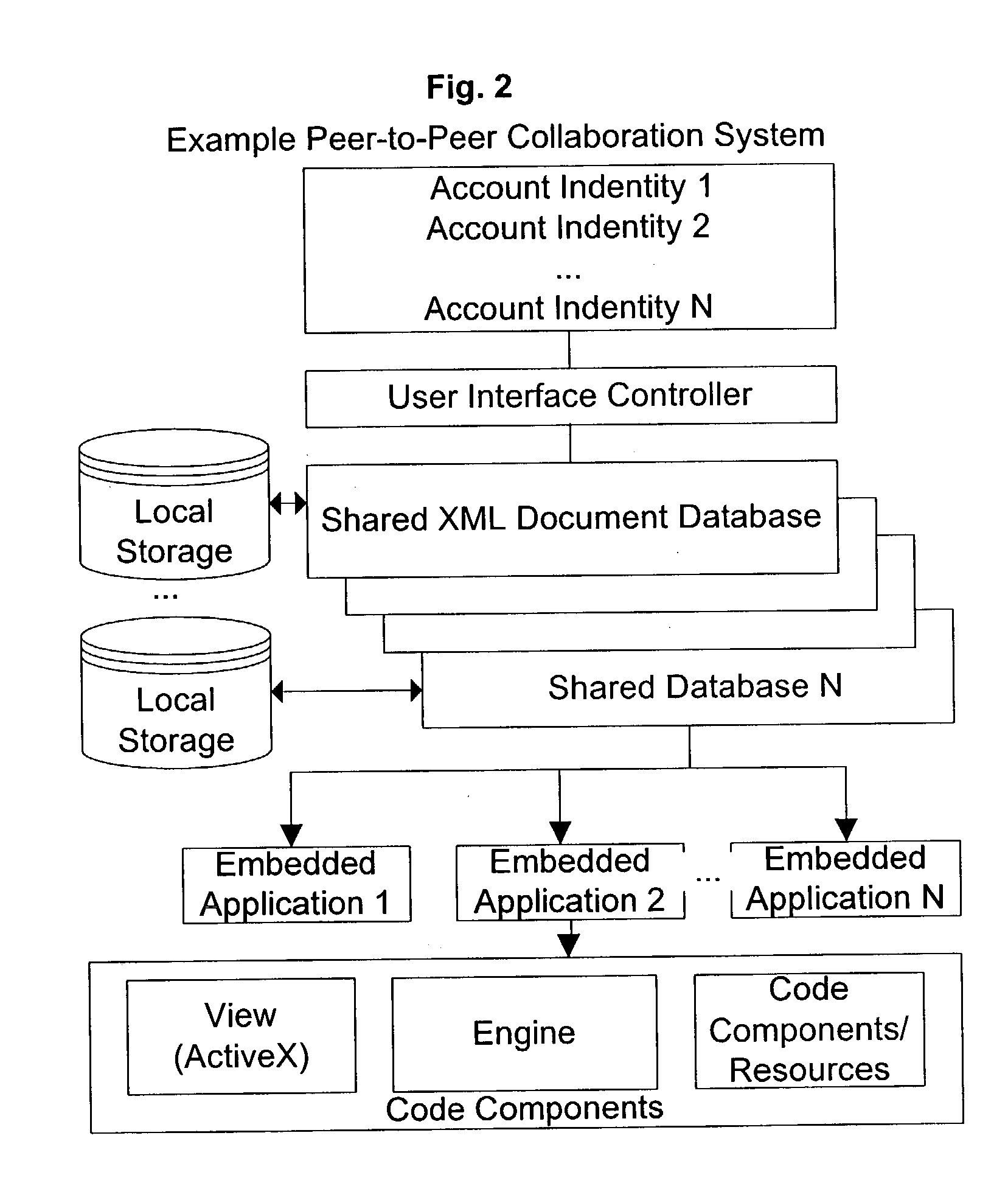
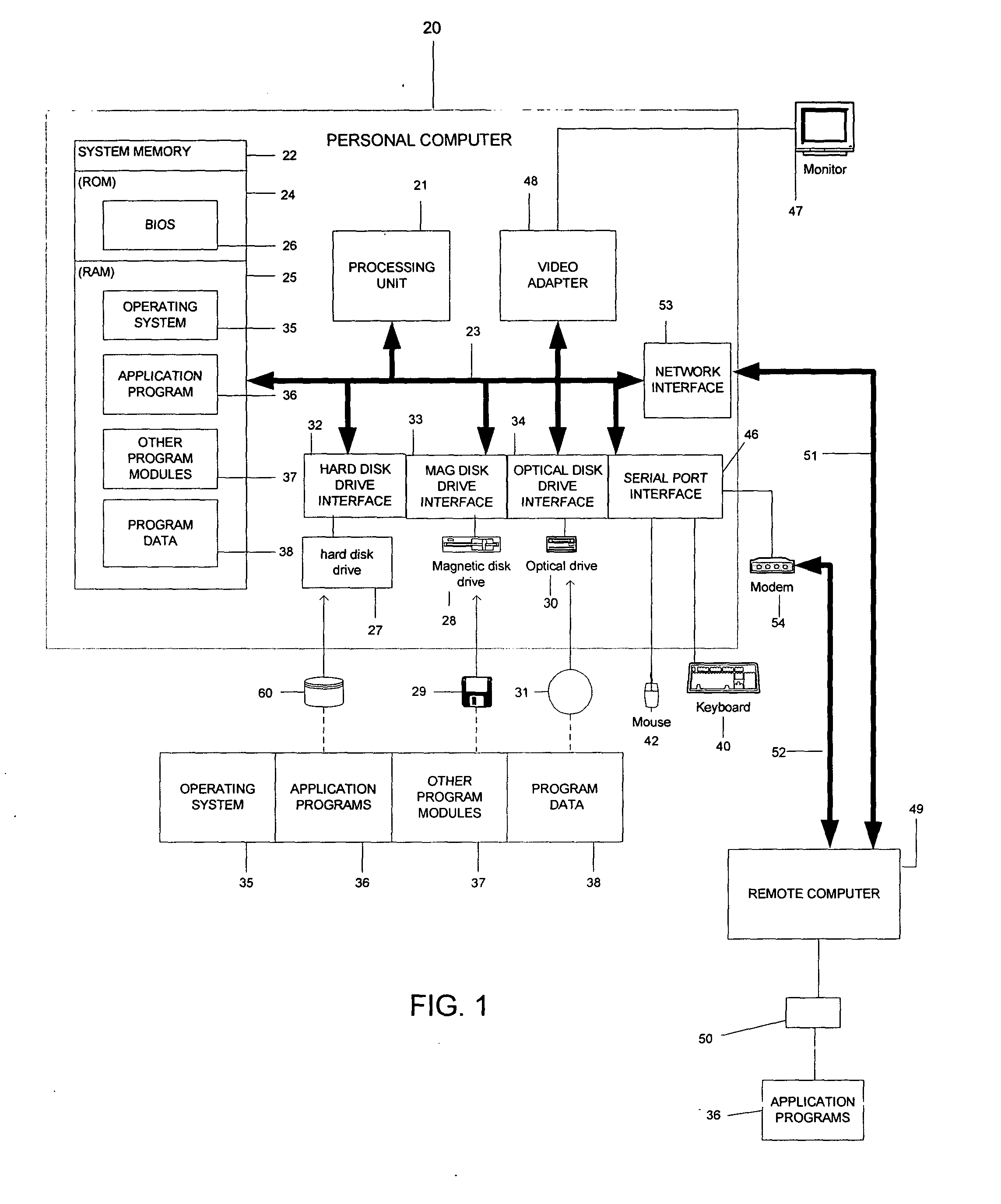
Self-replicating and self-installing software apparatus
InactiveUS20030217171A1Special service provision for substationElectronic editing digitised analogue information signalsContent creationRemote control
Self-replicating and self-installing software apparatus for content-creation, manipulation, and static or dynamic exhibition with a self-regulating license management component with methods for remote controlled and synchronized functionality and license binding to a Peer-to-Peer computing paradigm derived communication and collaboration platform's unique User ID.
Owner:VON STUERMER WOLFGANG R +1
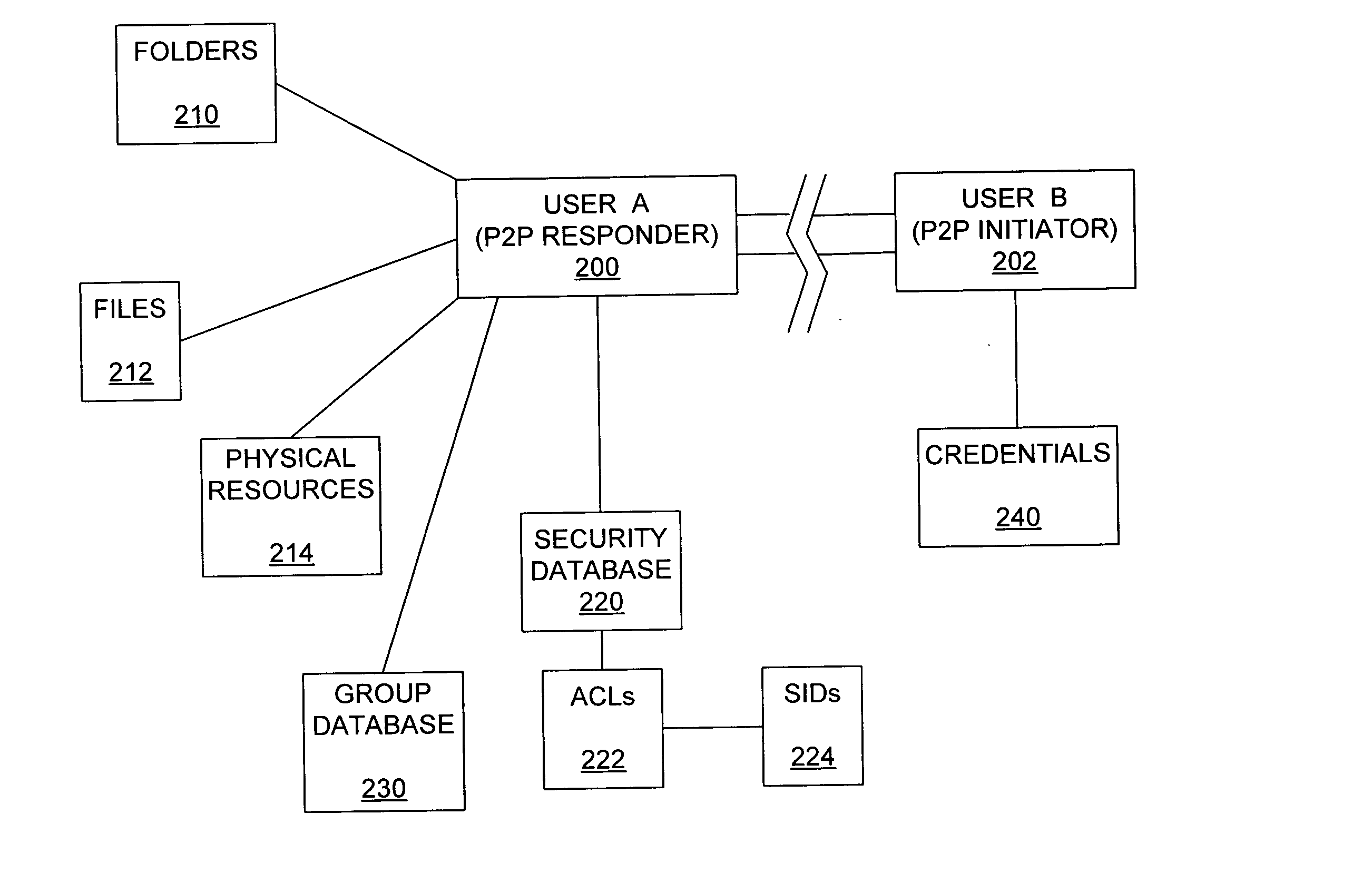
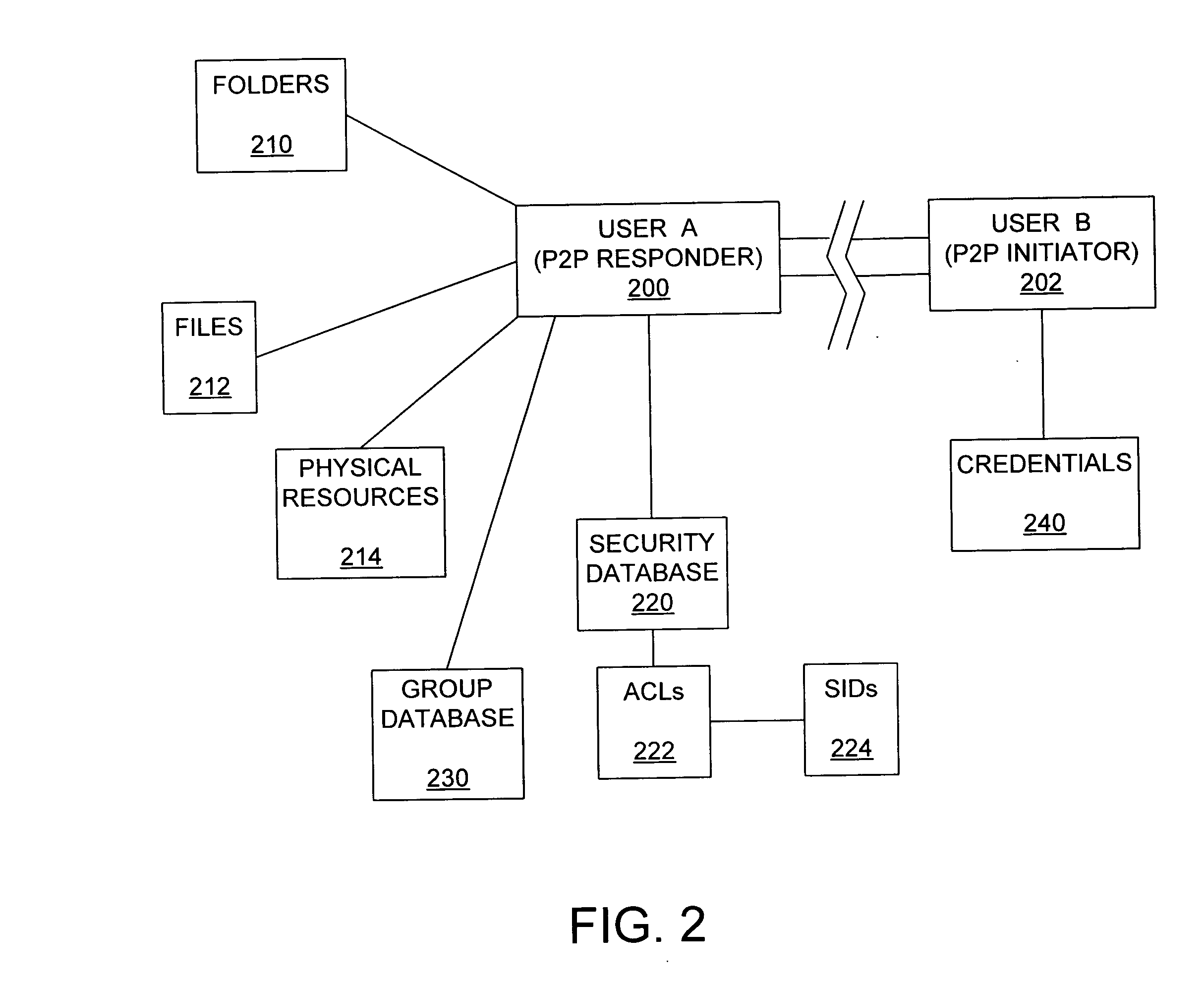
Peer-to-peer authorization method
ActiveUS20050044411A1Digital data processing detailsUnauthorized memory use protectionControl systemPeer to peer computing
Disclosed are peer-to-peer computer program products, methods, and systems in which a remote peer on a peer-to-peer network is granted or denied access to a resource based on the credentials presented by the remote peer. In accordance with the disclosed subject matter, an access token that includes one or more security identification values which represent respectively one or more access rights in an access control system is generated. An execution thread that is associated with the access token thus generated attempts to access the resource on behalf of the remote peer. In some embodiments, the access control system includes a generic user account, and the access token that is generated for the remote peer includes the security identification value associated with the generic user account in the access control system.
Owner:MICROSOFT TECH LICENSING LLC
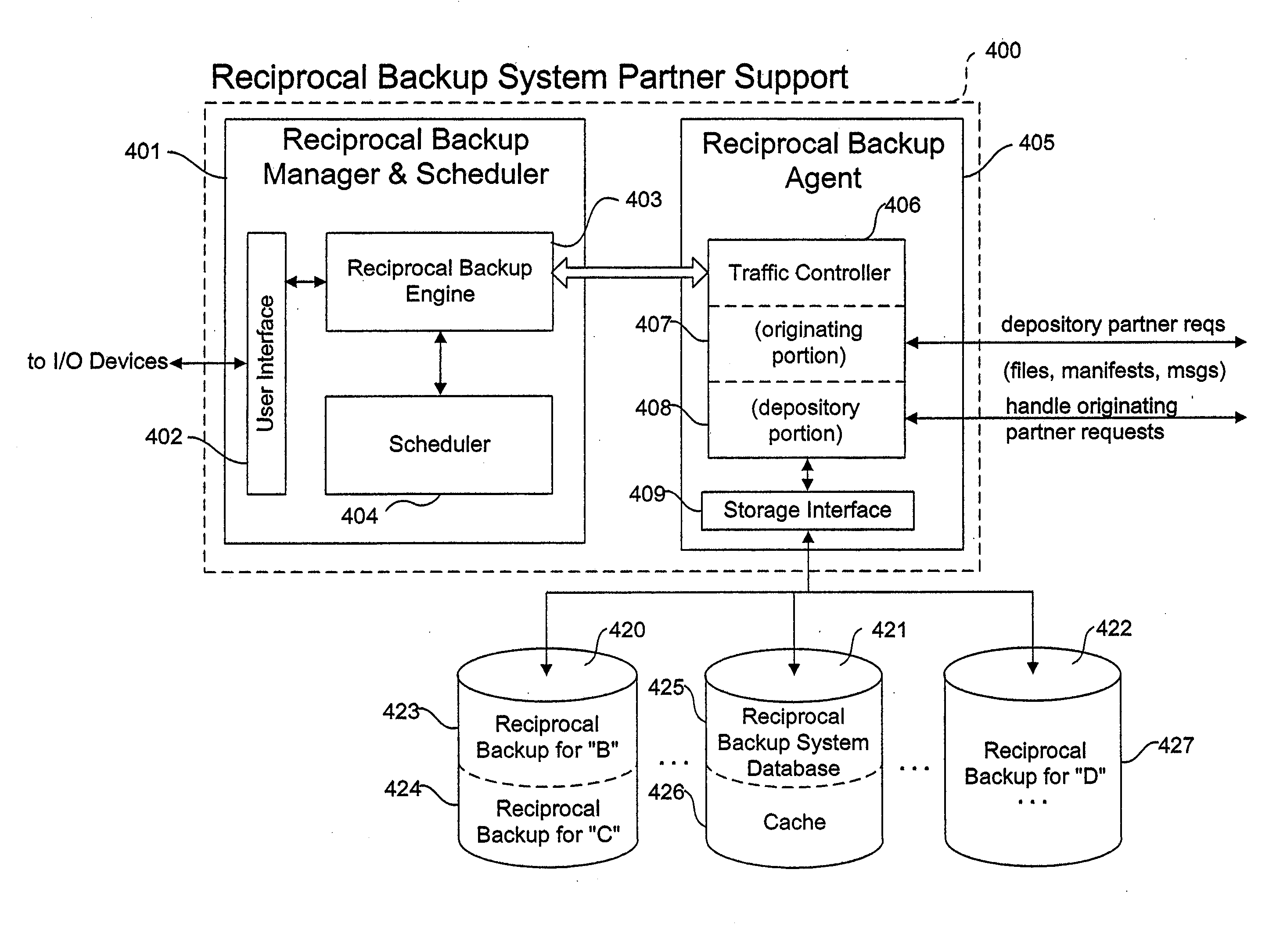
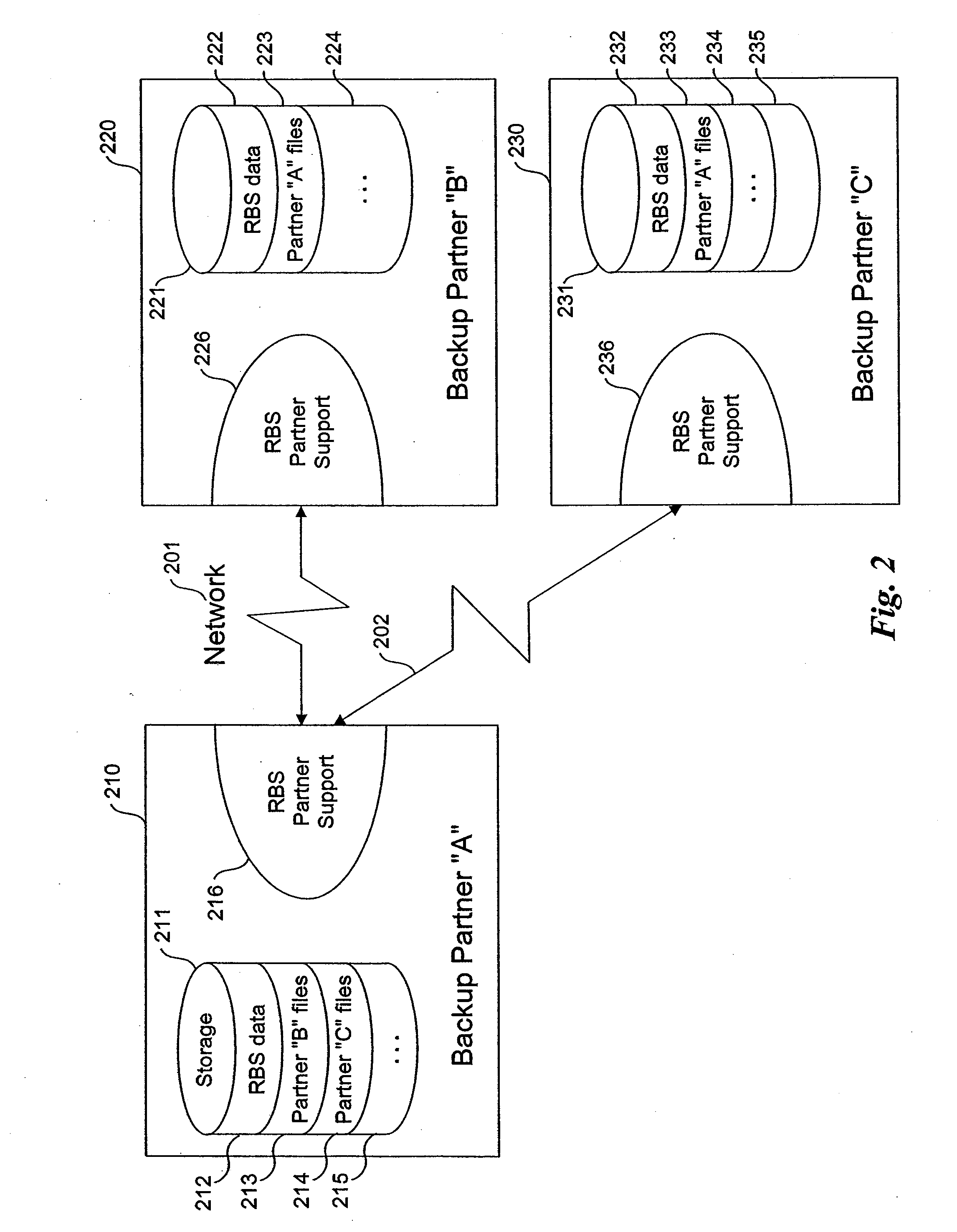
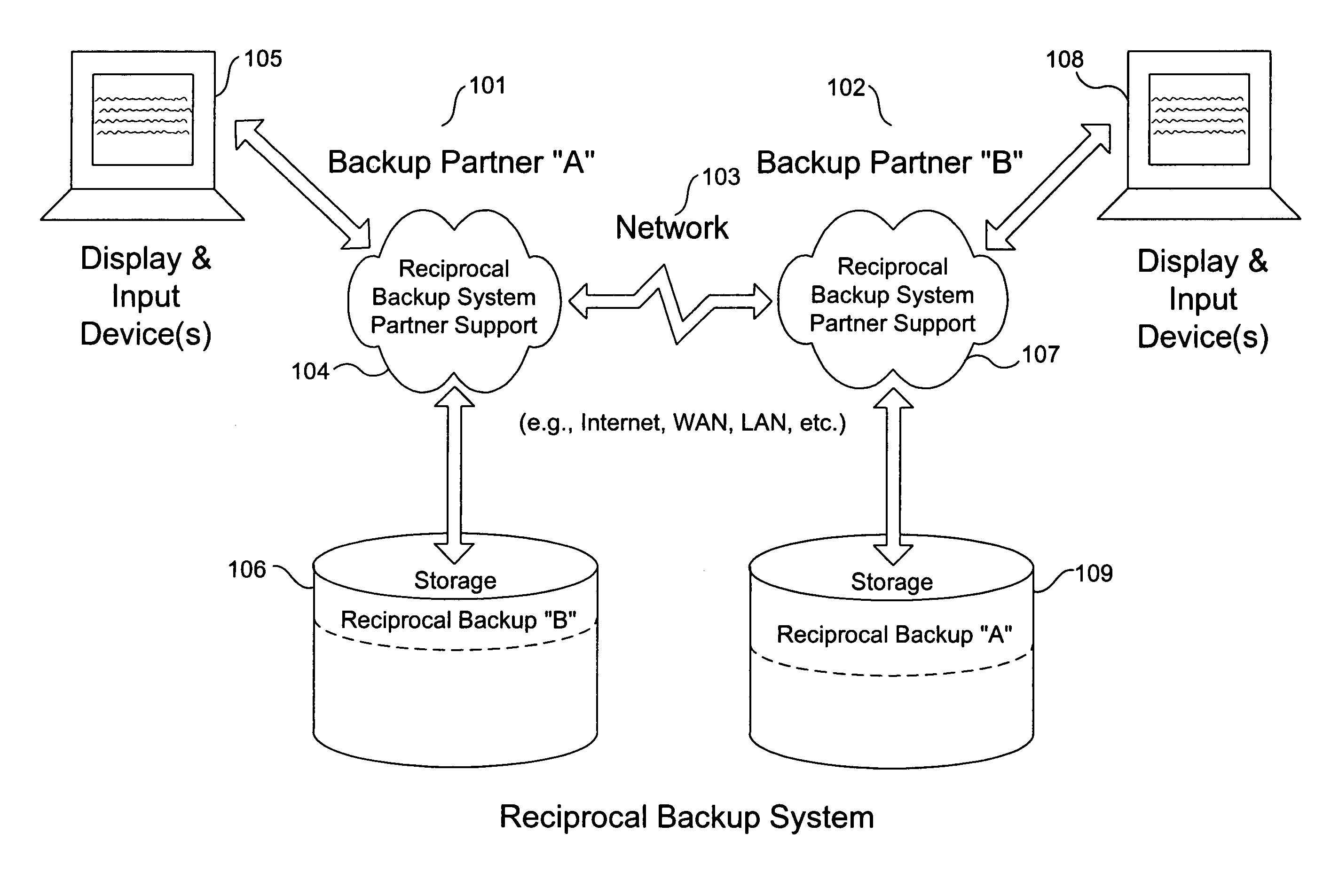
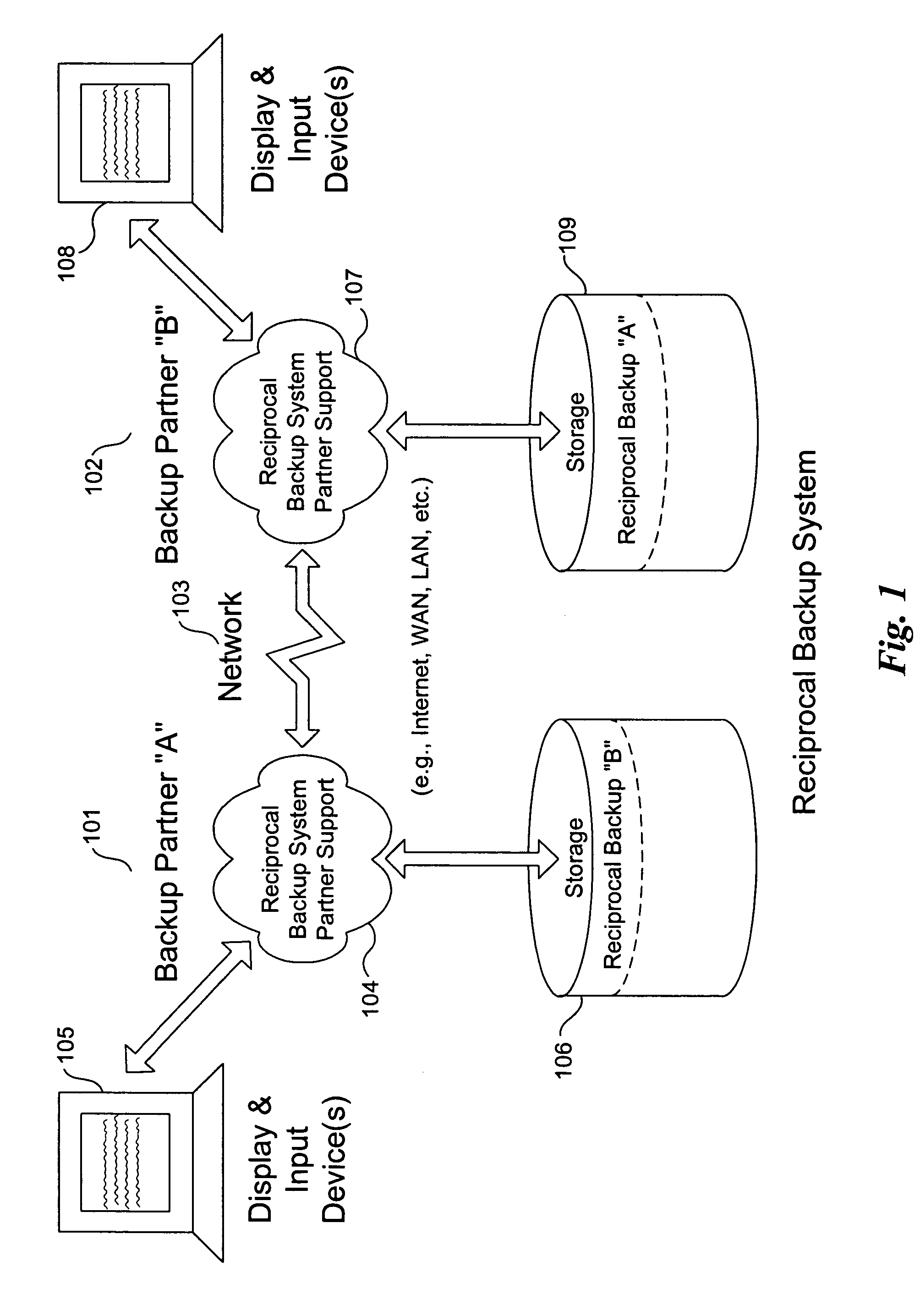
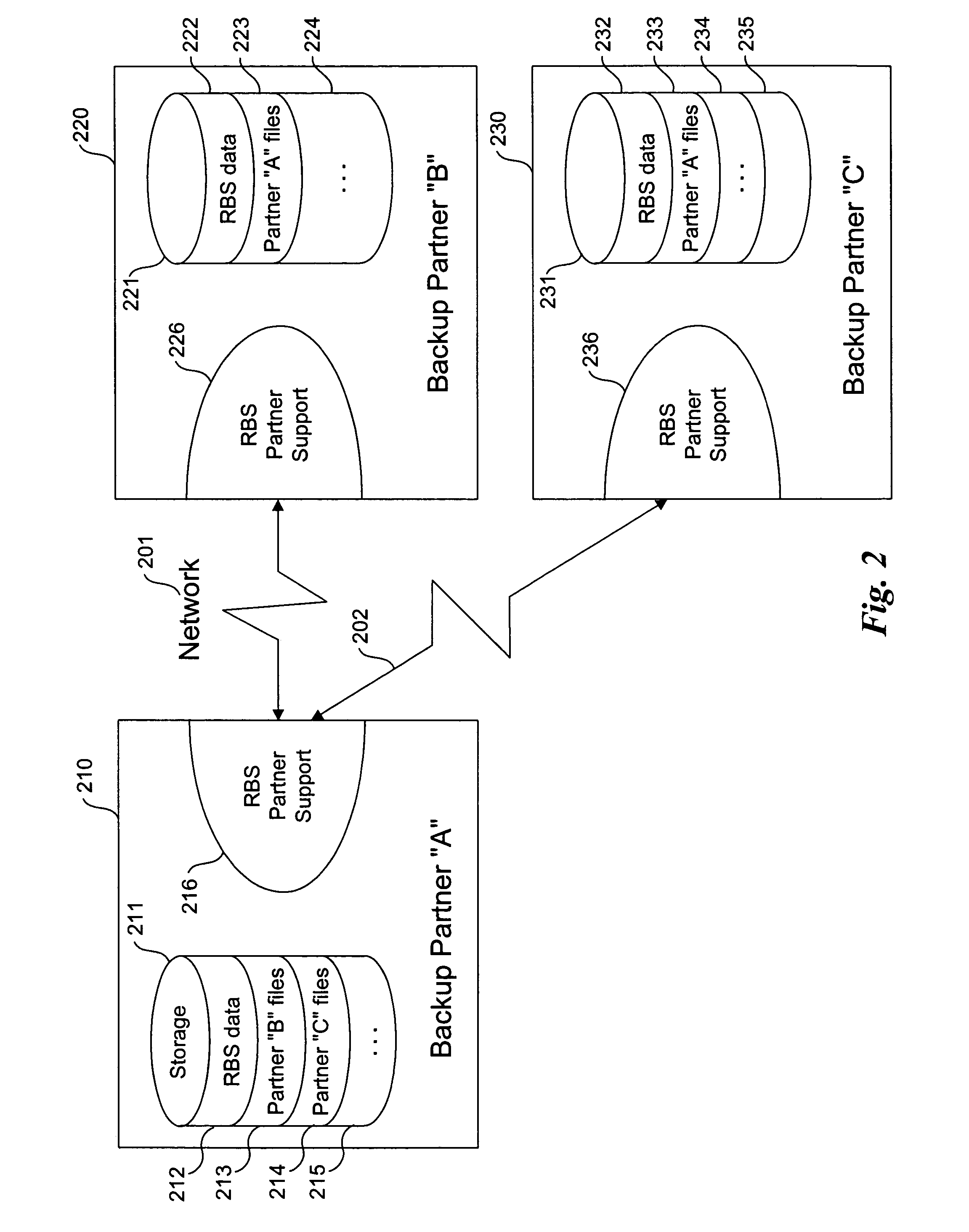
Method and system for reciprocal data backup
InactiveUS20080126445A1Little effortNo costEmergency protective arrangements for automatic disconnectionRedundant operation error correctionNetwork connectionProgram planning
Methods and systems for a reciprocal backup of data, including files, directories, and application data are provided. Example embodiments provide a Reciprocal Backup System (“RBS”), which enables users of two or more computer systems connected over a network to engage each other for automated reciprocal backup needs using peer-to-peer computing techniques. The peer computer systems negotiate a reciprocal backup relationship where each provides the other with backup storage in a secure fashion. The intermittent nature of some partners is handled automatically by the RBS, which supports fully automated and scheduled backups as well as immediate backup and restoration of data objects. In one embodiment, the RBS comprises reciprocal backup system partner support and one or more storage repositories. The RBS partner support includes a reciprocal backup manager and scheduler and a reciprocal backup agent. These components cooperate to provide the backup and restoration operations of the RBS.
Owner:MICHELMAN ERIC
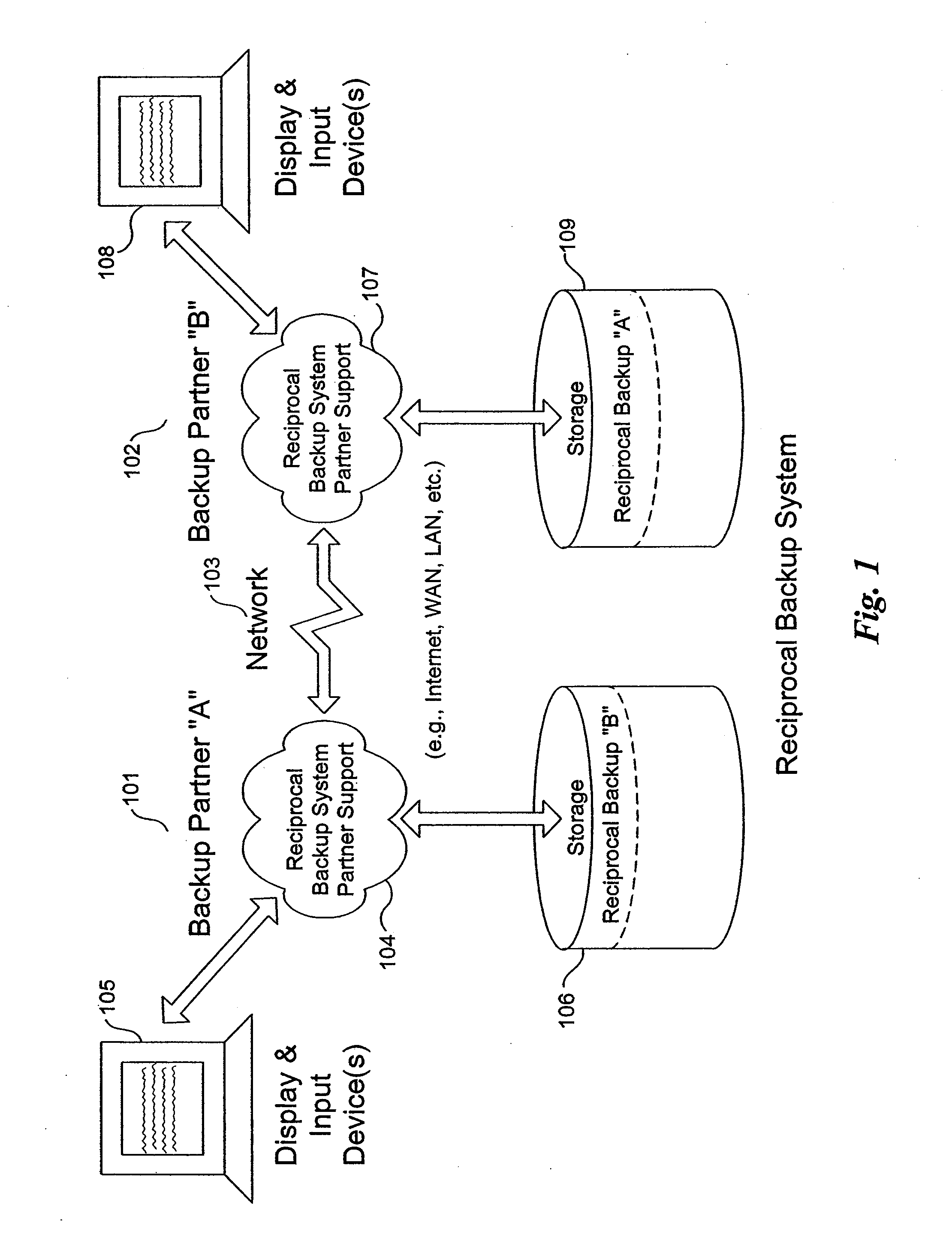
Method and system for reciprocal data backup
InactiveUS7328366B2Little effortNo costEmergency protective arrangements for automatic disconnectionRedundant operation error correctionProgram planningPeer to peer computing
Methods and systems for a reciprocal backup of data, including files, directories, and application data are provided. Example embodiments provide a Reciprocal Backup System (“RBS”), which enables users of two or more computer systems connected over a network to engage each other for automated reciprocal backup needs using peer-to-peer computing techniques. The peer computer systems negotiate a reciprocal backup relationship where each provides the other with backup storage in a secure fashion. The intermittent nature of some partners is handled automatically by the RBS, which supports fully automated and scheduled backups as well as immediate backup and restoration of data objects. In one embodiment, the RBS comprises reciprocal backup system partner support and one or more storage repositories. The RBS partner support includes a reciprocal backup manager and scheduler and a reciprocal backup agent. These components cooperate to provide the backup and restoration operations of the RBS.
Owner:CASCADE BASIC RES CORP
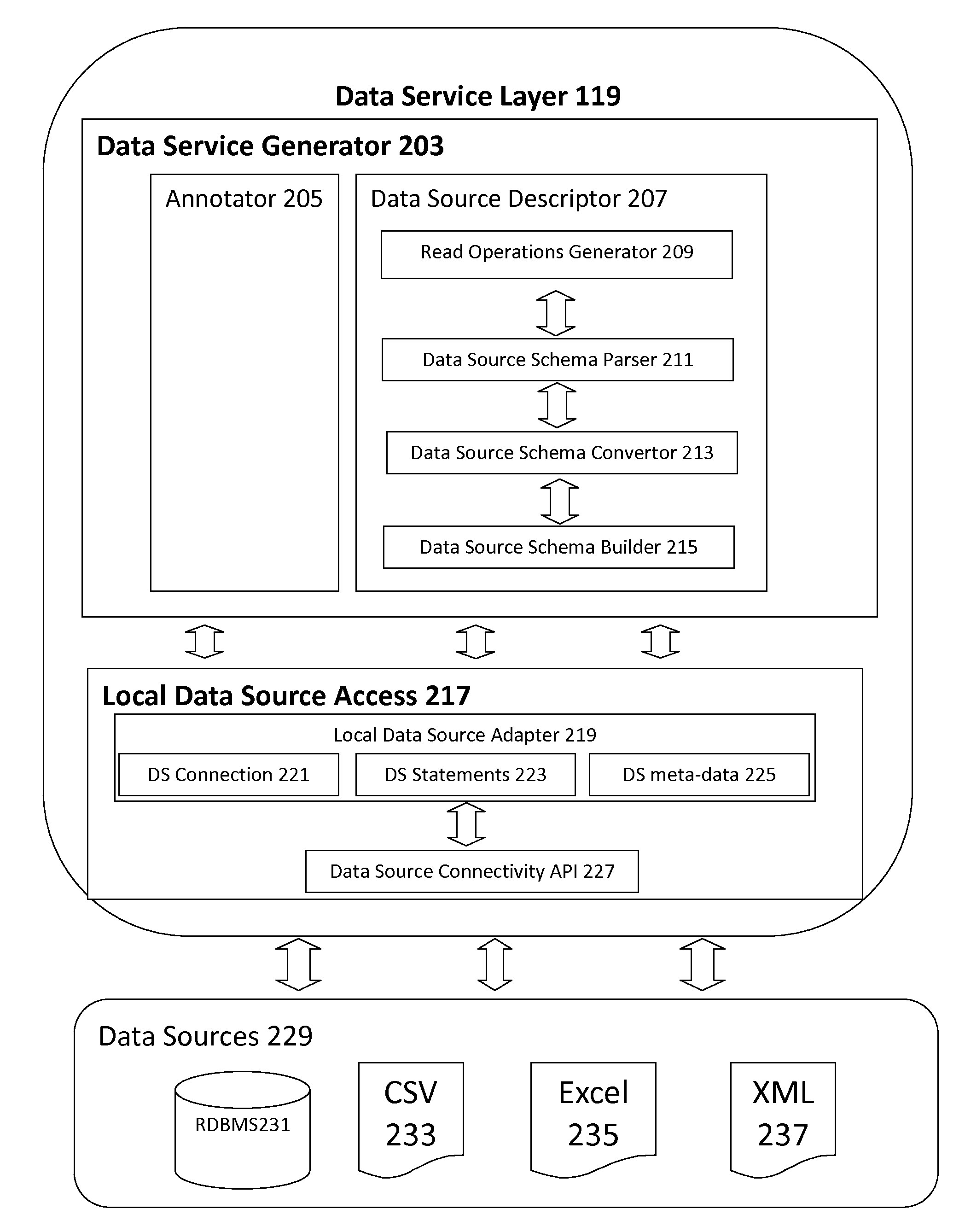
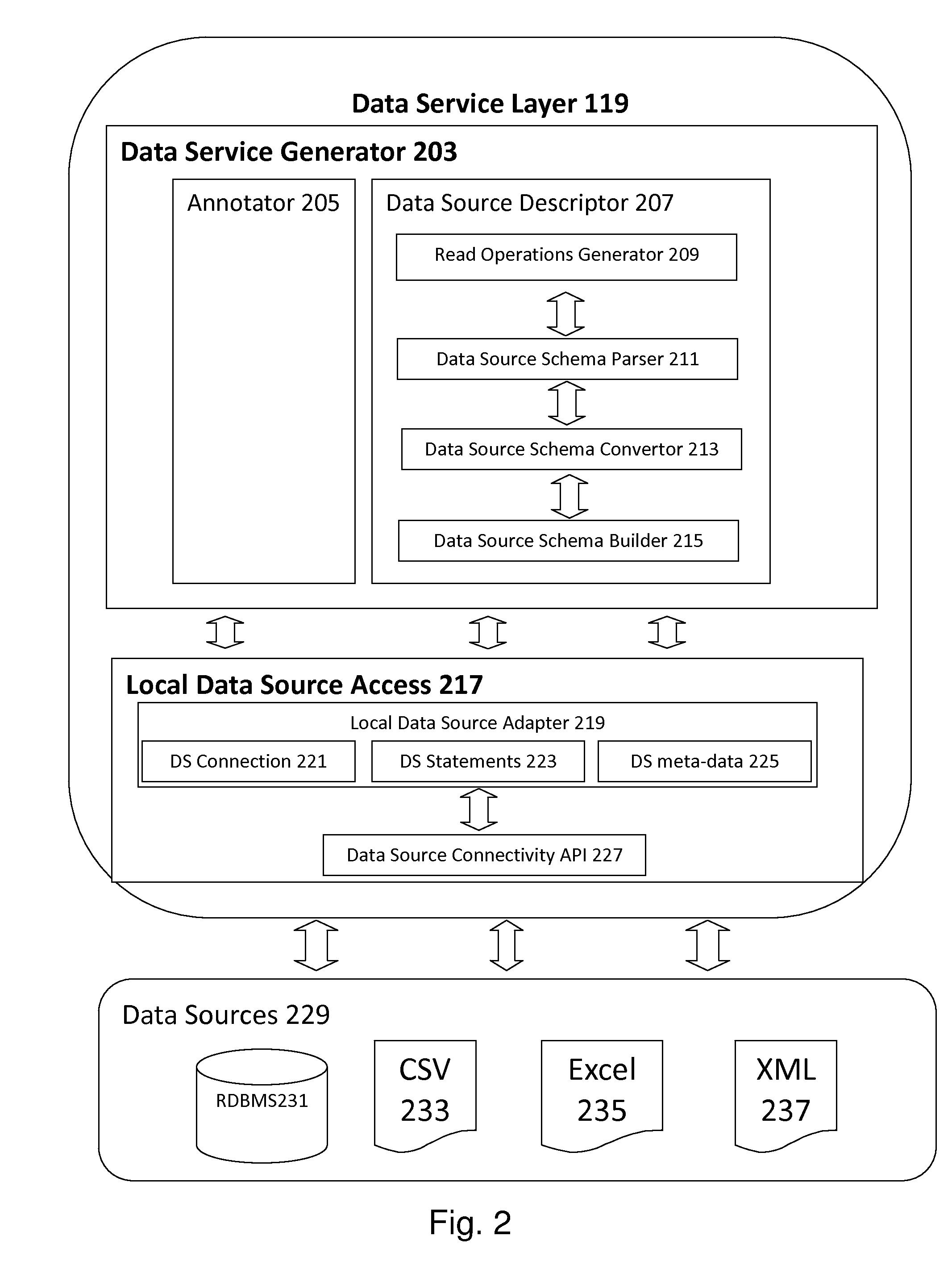
Device and Method for Sharing Data and Applications in Peer-to-Peer Computing Environment
InactiveUS20130318160A1Promote productionUniform accessMultiple digital computer combinationsTransmissionService compositionPeer to peer computing
The current invention provides a simple yet efficient Data Service Middleware or DSM computing device and method that provides access to remote, heterogeneous and autonomous peer-to-peer (P2P) data sources, thereby allows users to share and exchange files. The current invention allows non-expert users to share and integrate their data and can meet the growing need of sharing existing widespread data-sources. In the current invention data sources are exported and deployed as services and as such, data sources easily discovered and uniformly accessible using standard SOAP requests and are integrated through service composition.
Owner:BERAKA MUTAZ SELEAM +2
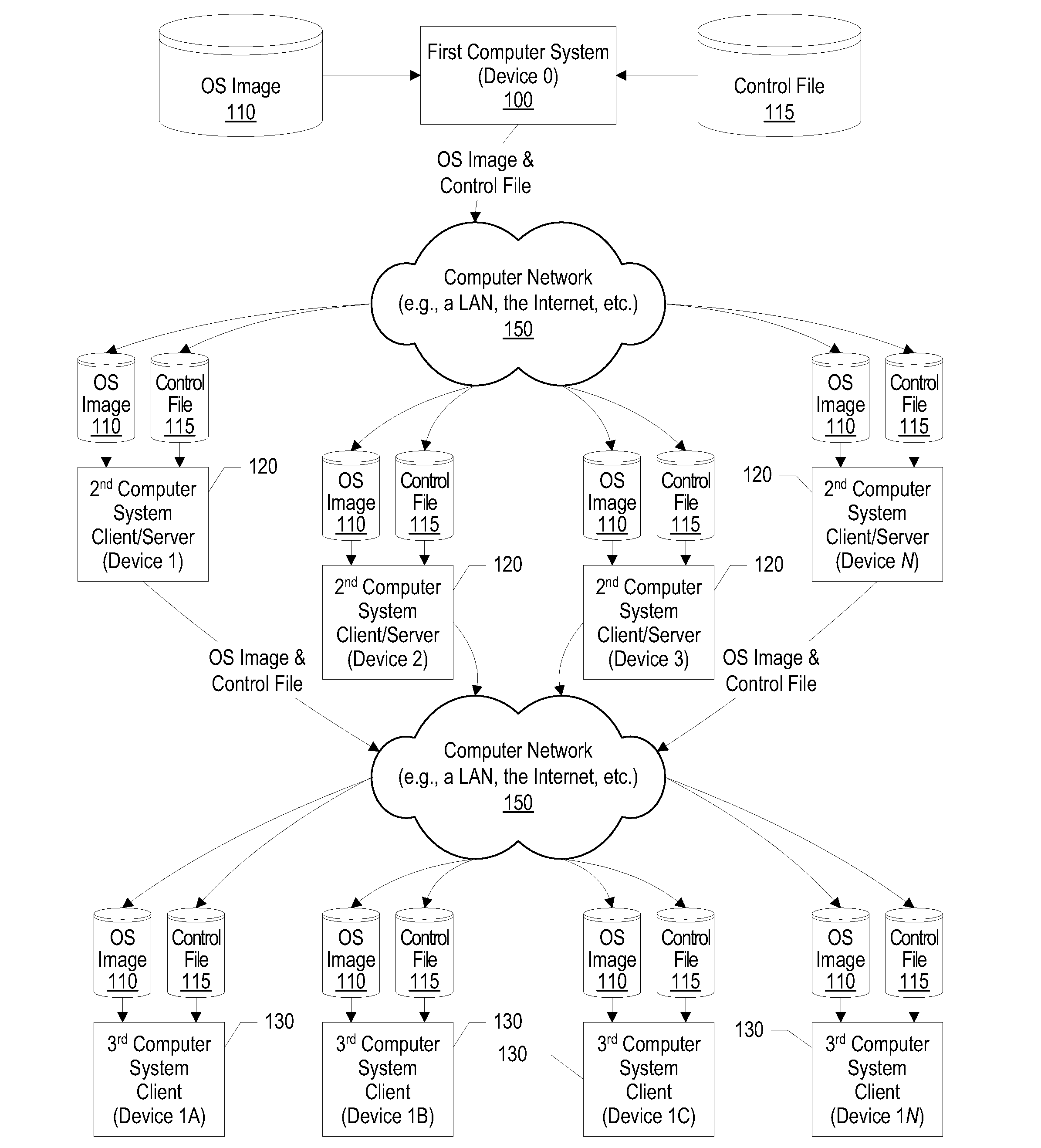
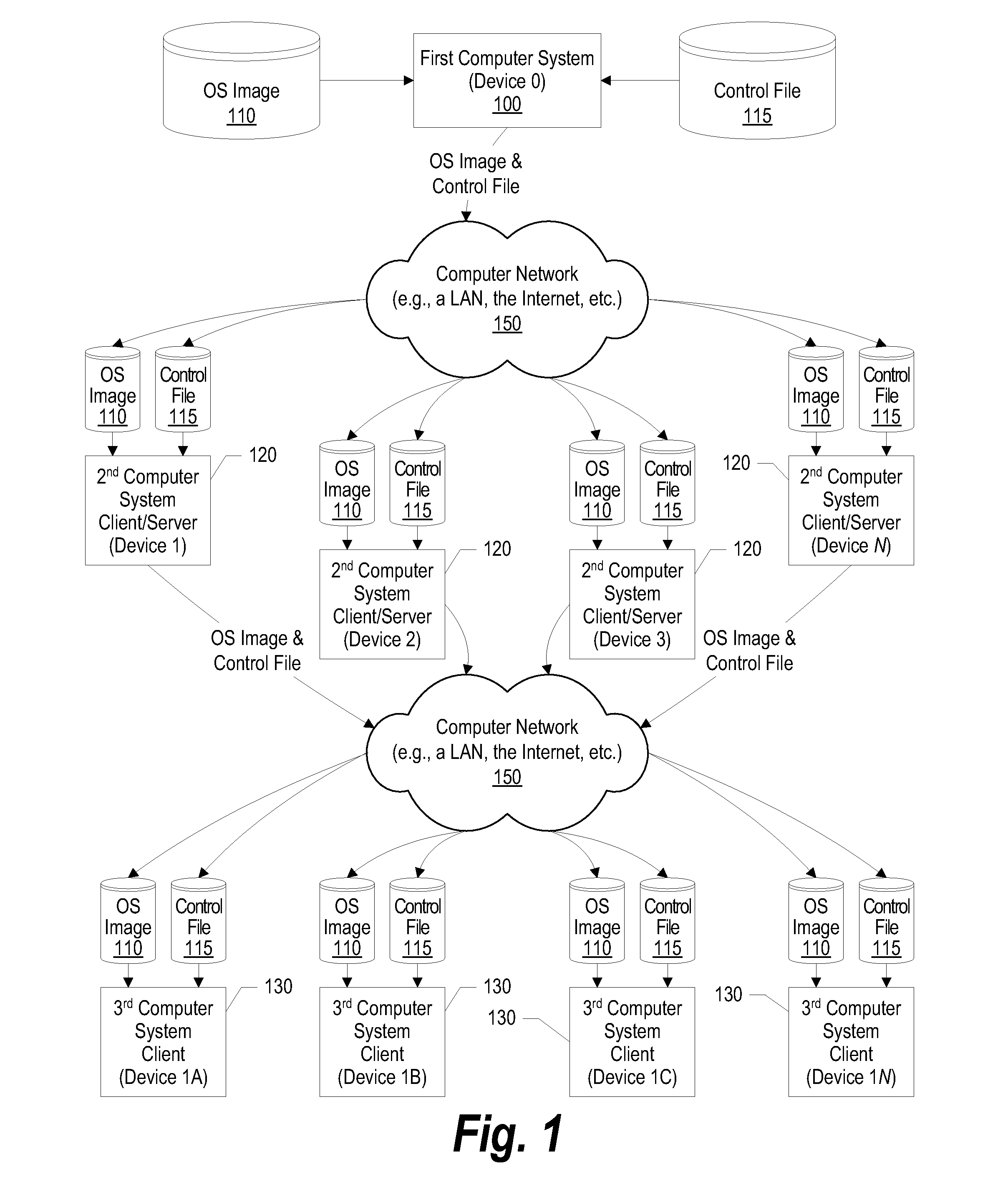
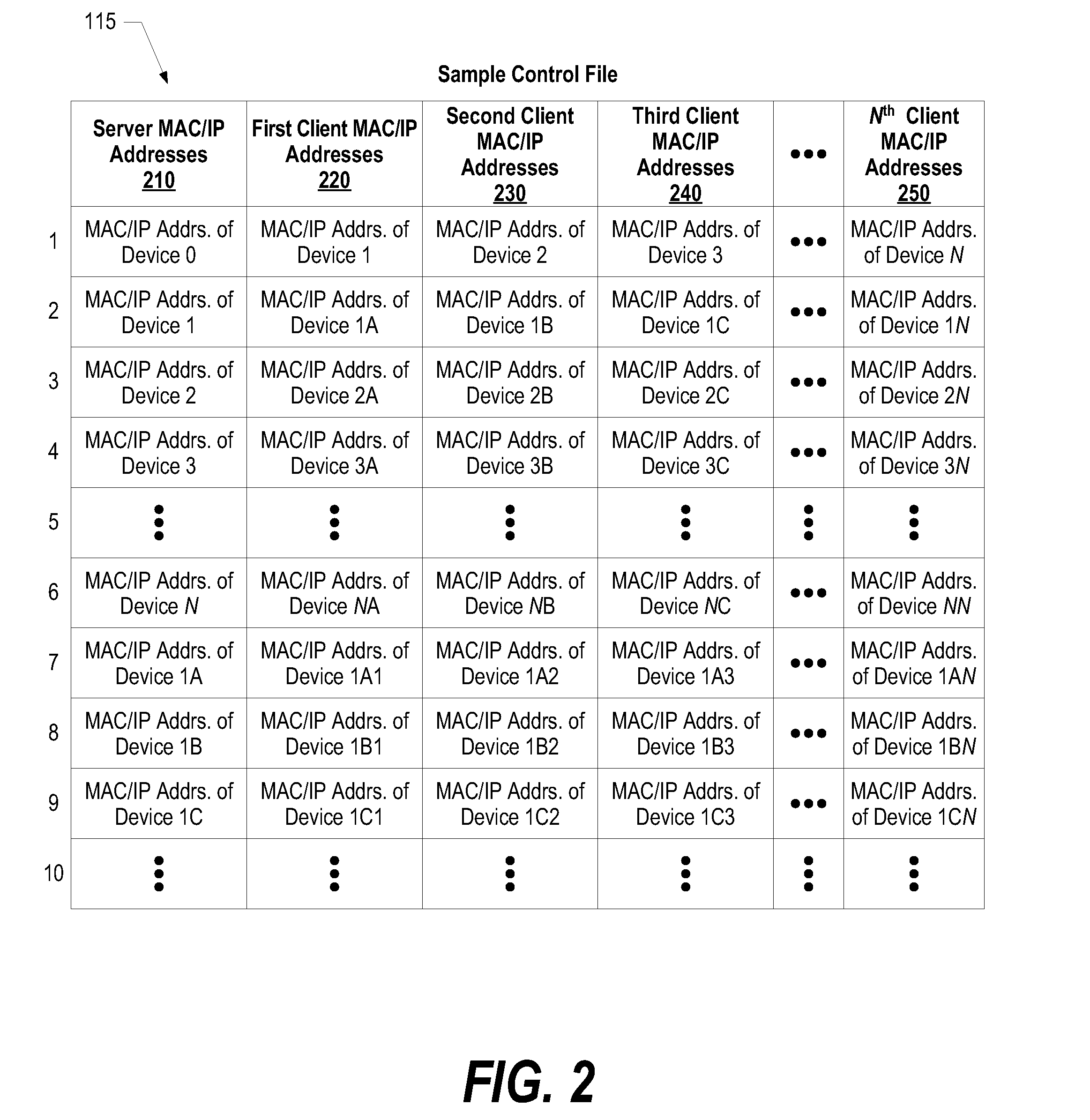
System and method for operating system deployment in a peer-to-peer computing environment
InactiveUS20080141015A1Digital computer detailsProgram loading/initiatingOperational systemPeer to peer computing
A system, method, and program product is provided that deploys an operating system. The first computer system sends a Wake-on-LAN instruction and boots each of the second computer systems. The second computer system identifies a set of third computer identifiers that corresponds to each of the selected second computer systems. The second computer systems send the Wake-on-LAN instruction to each of the third computer systems, and the third computer systems are booted over the computer network from the second computer systems. A control file lists the first computer system as a “server” of the second computer systems and lists the second computer systems as “servers” of the third computer systems. The control file is transmitted from a server to each of the server's clients. When a client is booted, it checks the control file to determine if the client is also a server to other computer systems.
Owner:IBM CORP
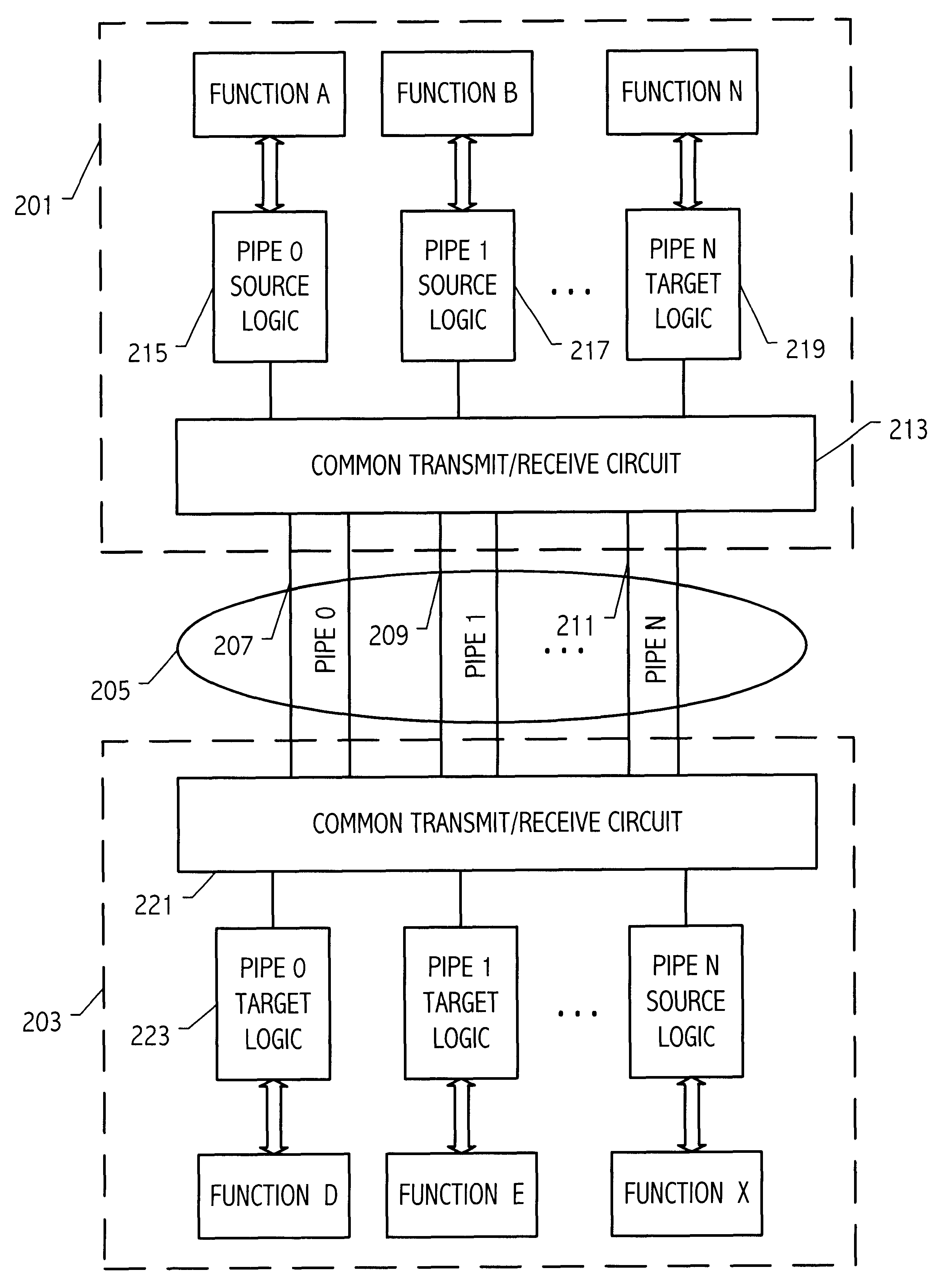
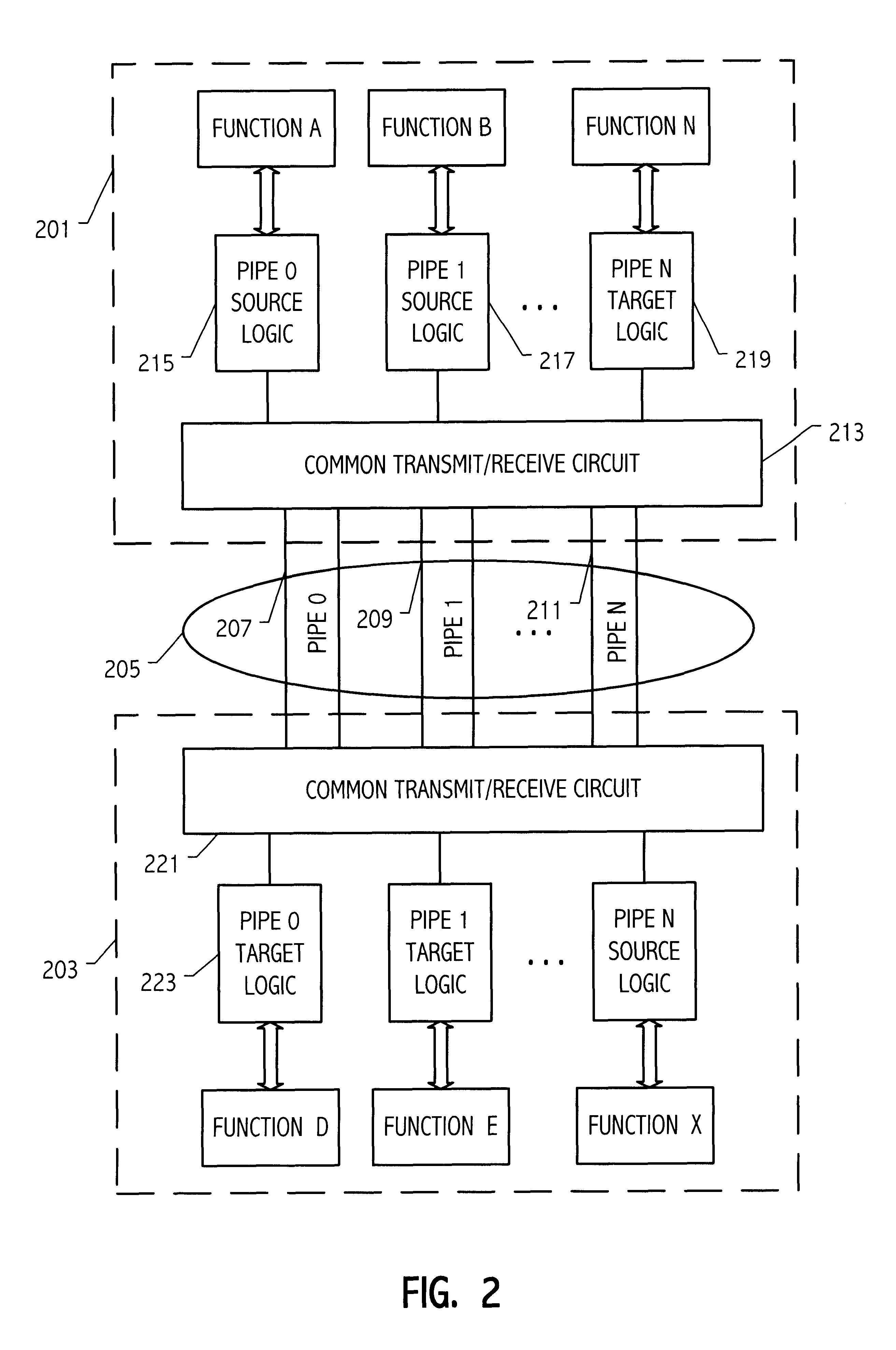
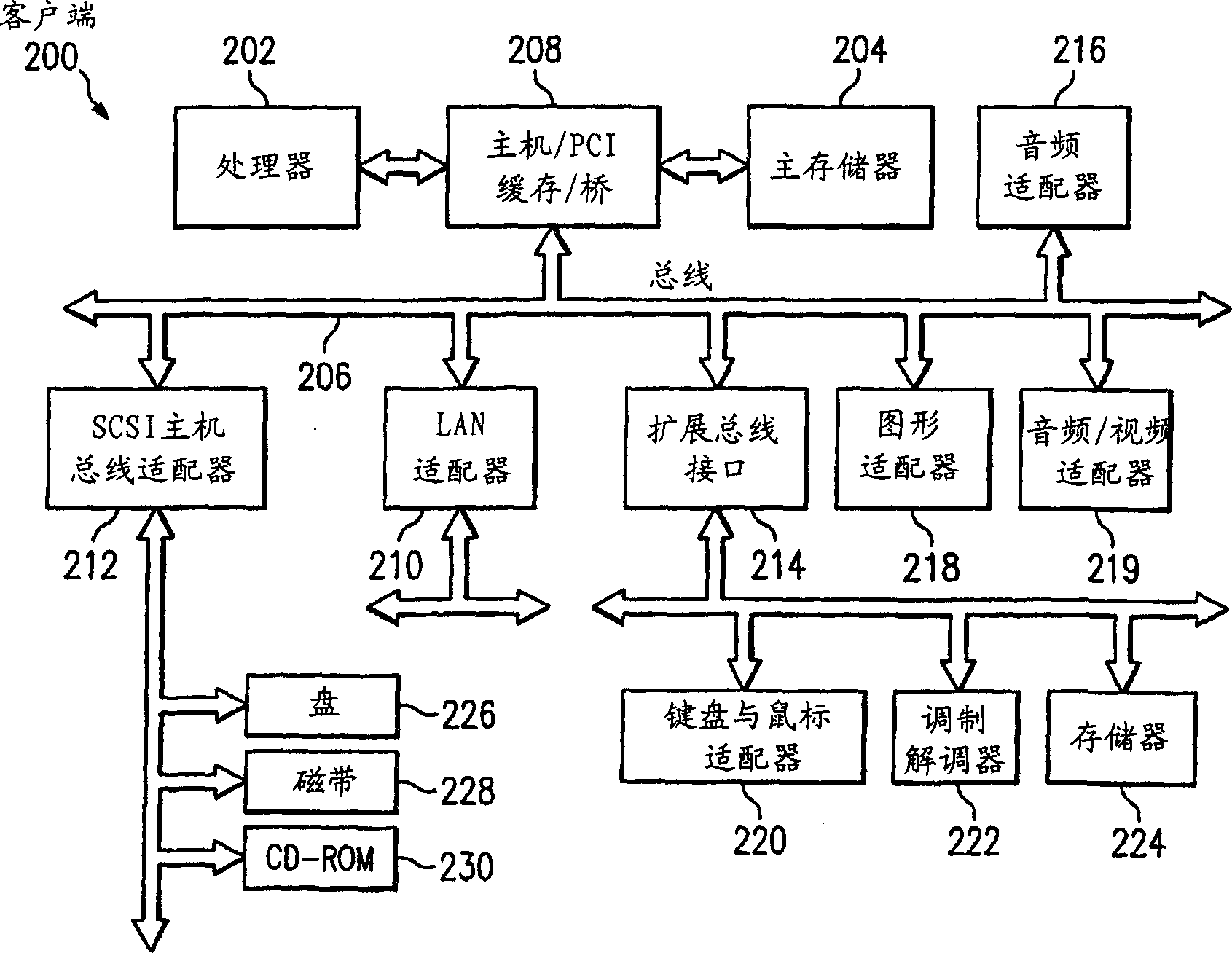
Subordinate bridge structure for a point-to-point computer interconnection bus
A communication link is used both as a primary communication link and as a subordinate link in a computer system. A first integrated circuit having a plurality of first functions and a second integrated circuit having a plurality of second functions, are connected via a first communication link. The first communication link includes a plurality of first logical pipes carrying transactions on the first communication link, each of the first logical pipes having a source end in one of the first and second integrated circuits and a target end in the other of the first and second integrated circuits. A second communication link is coupled to the first communication link and includes a plurality of second logical pipes carrying transactions on the second communication link, each of the second logical pipes has a source end and a target end. A target (or source) end of one of the first pipes is communicatively coupled on the second integrated circuit to a source (or target) end one of the second pipes.
Owner:GLOBALFOUNDRIES INC
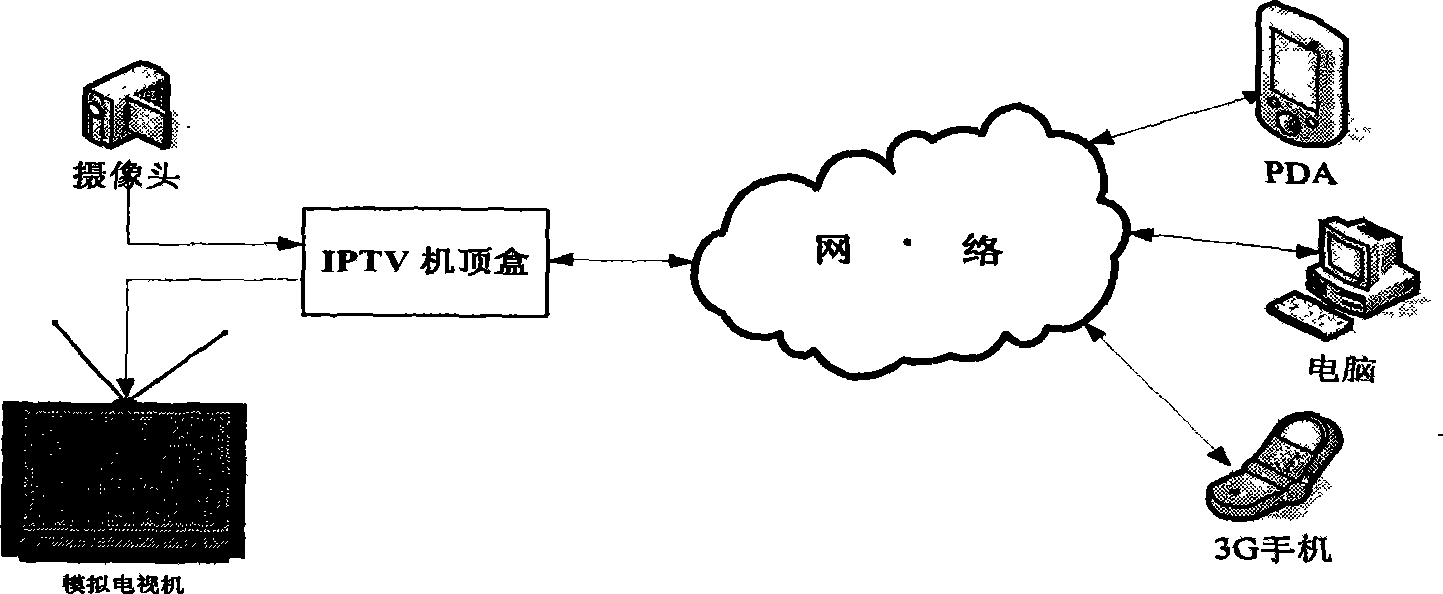
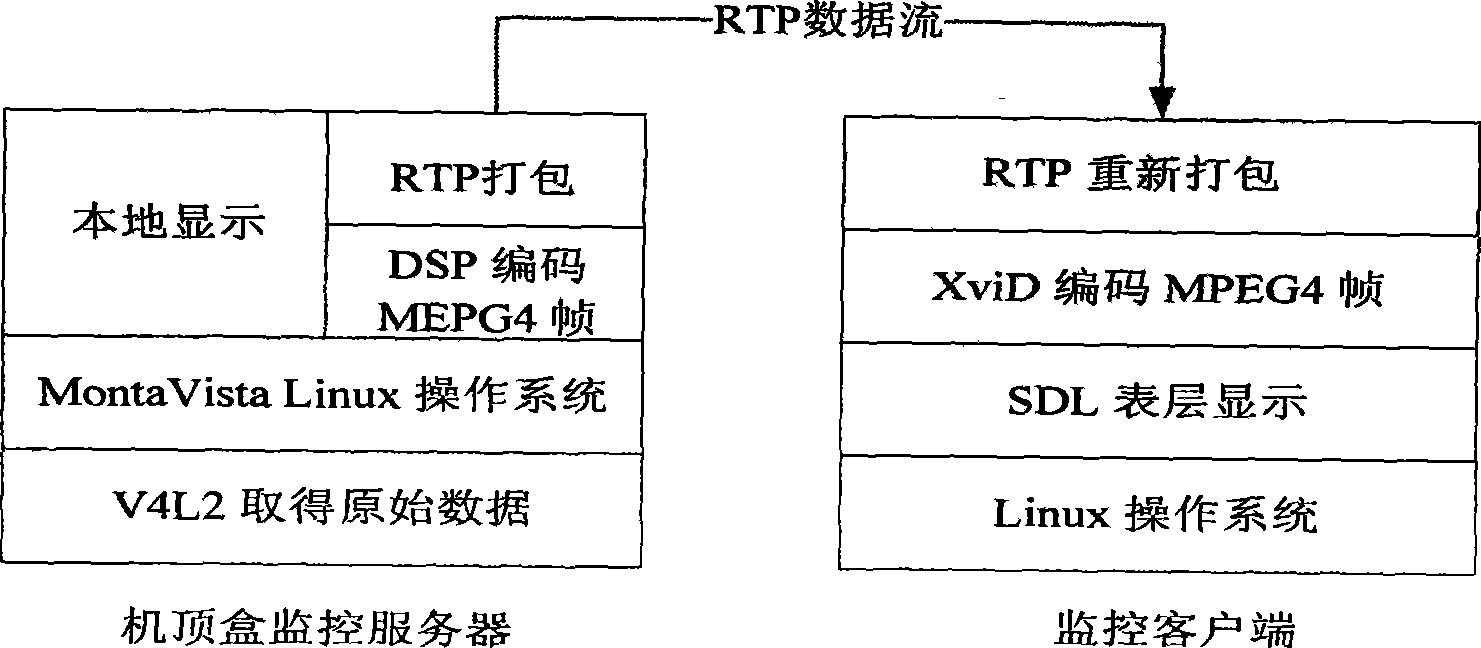
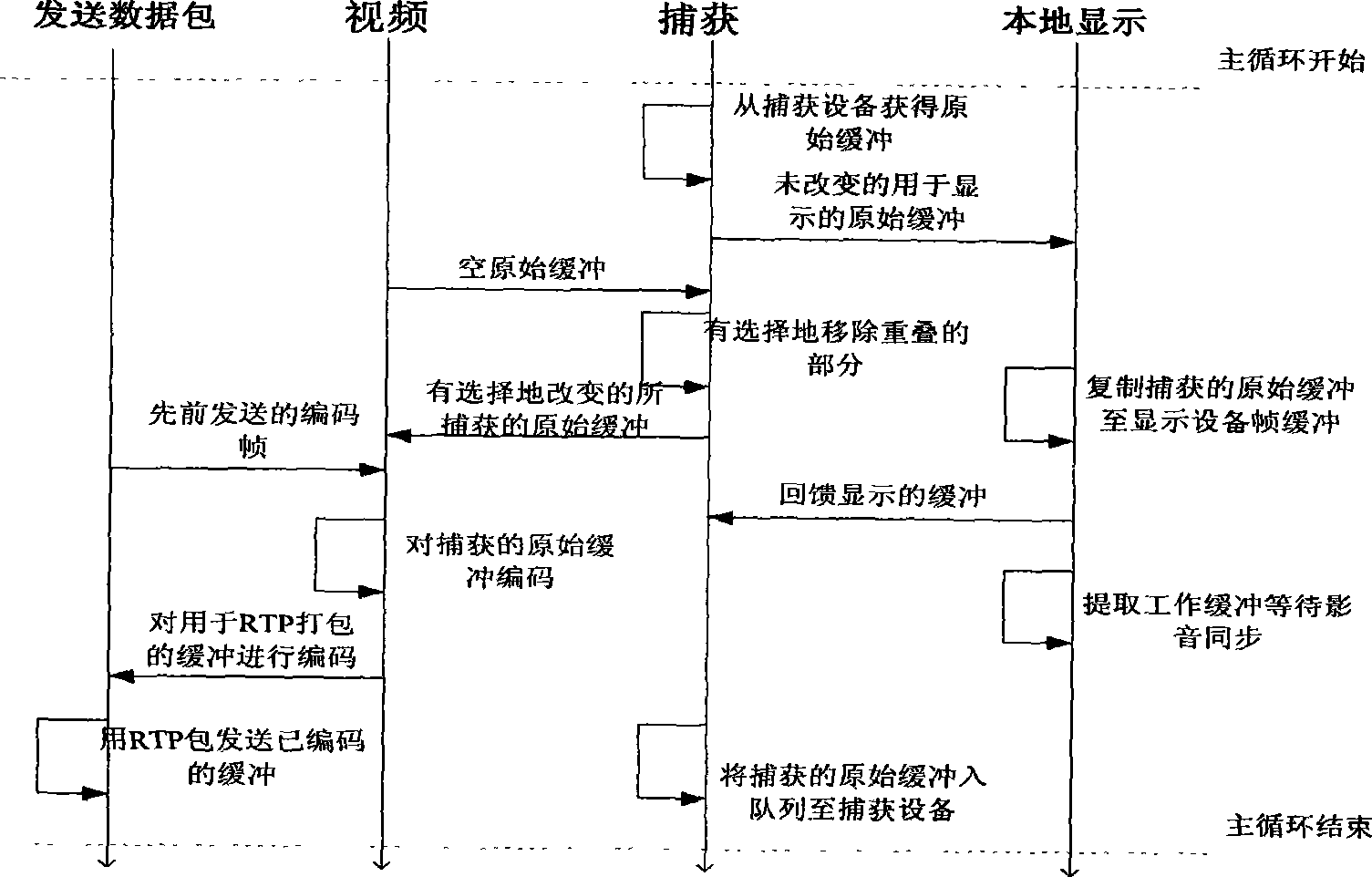
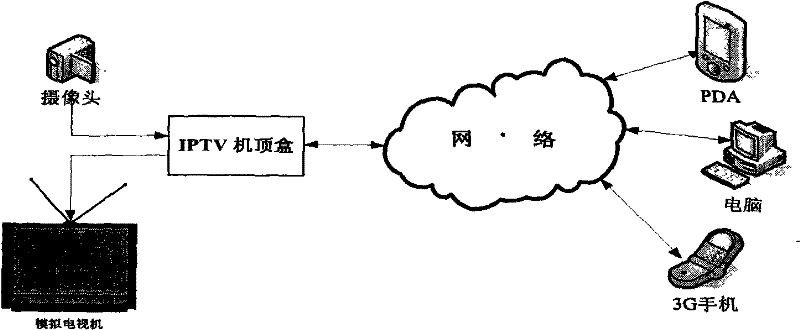
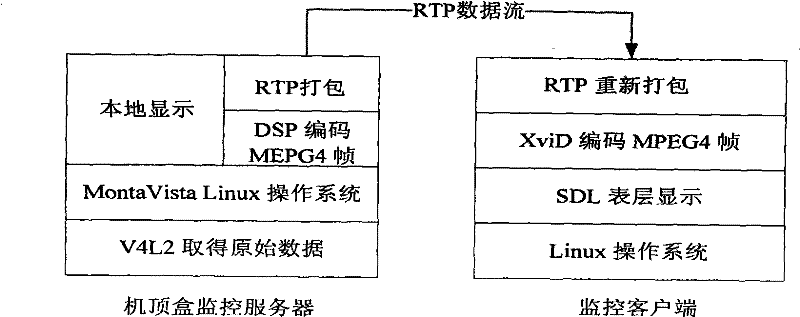
Real-time video monitoring system implementing method based on network television set-top box
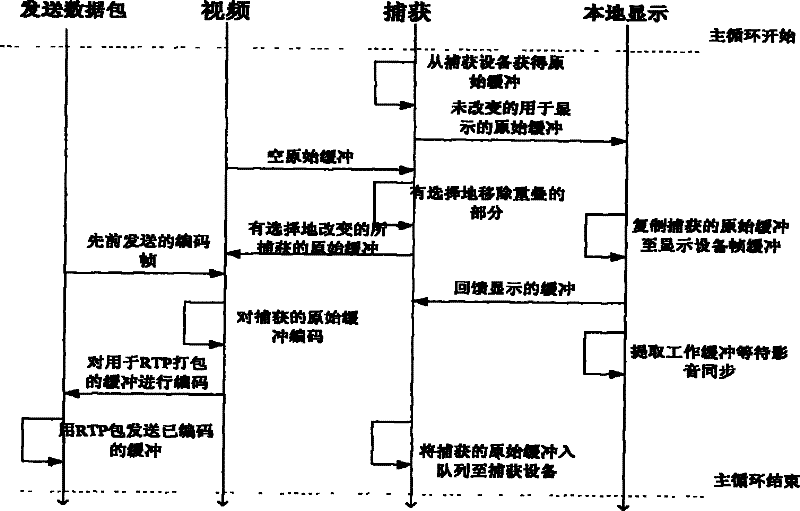
InactiveCN101505365AAdjustable definitionLower latencyTelevision system detailsColor television detailsVideo monitoringDual core
The invention relates to a method for achieving a real-time video monitoring system based on an internet protocol television top-set box, which is a method for achieving the function of real-time video monitoring on the internet protocol television (IPTV) top-set box. Based on an added-value extended function provided by an IPTV peer-to-peer computing top-set box developed on a dual-core development platform TMS320DM6446 (Vinci digital platform), the invention provides the method for achieving the real-time video monitoring system based on the internet protocol television top-set box for achieving a household real-time video monitoring system on the IPTV top-set box developed on the basis of the DM6446 platform so as to solve the problems of the read-write operations driven by a video capture device, the call of a DSP MPEG-4 coding interface, the transmission and the control of a RTP (Real-time Transport Protocol) data pack, the achievement of MPEG-4 decoding, and the multimedia interface display based on SDL. The proposal has the advantages of novelty, flexibility, easy expansibility, easy operability, low cost and the like.
Owner:NANJING UNIV OF POSTS & TELECOMM
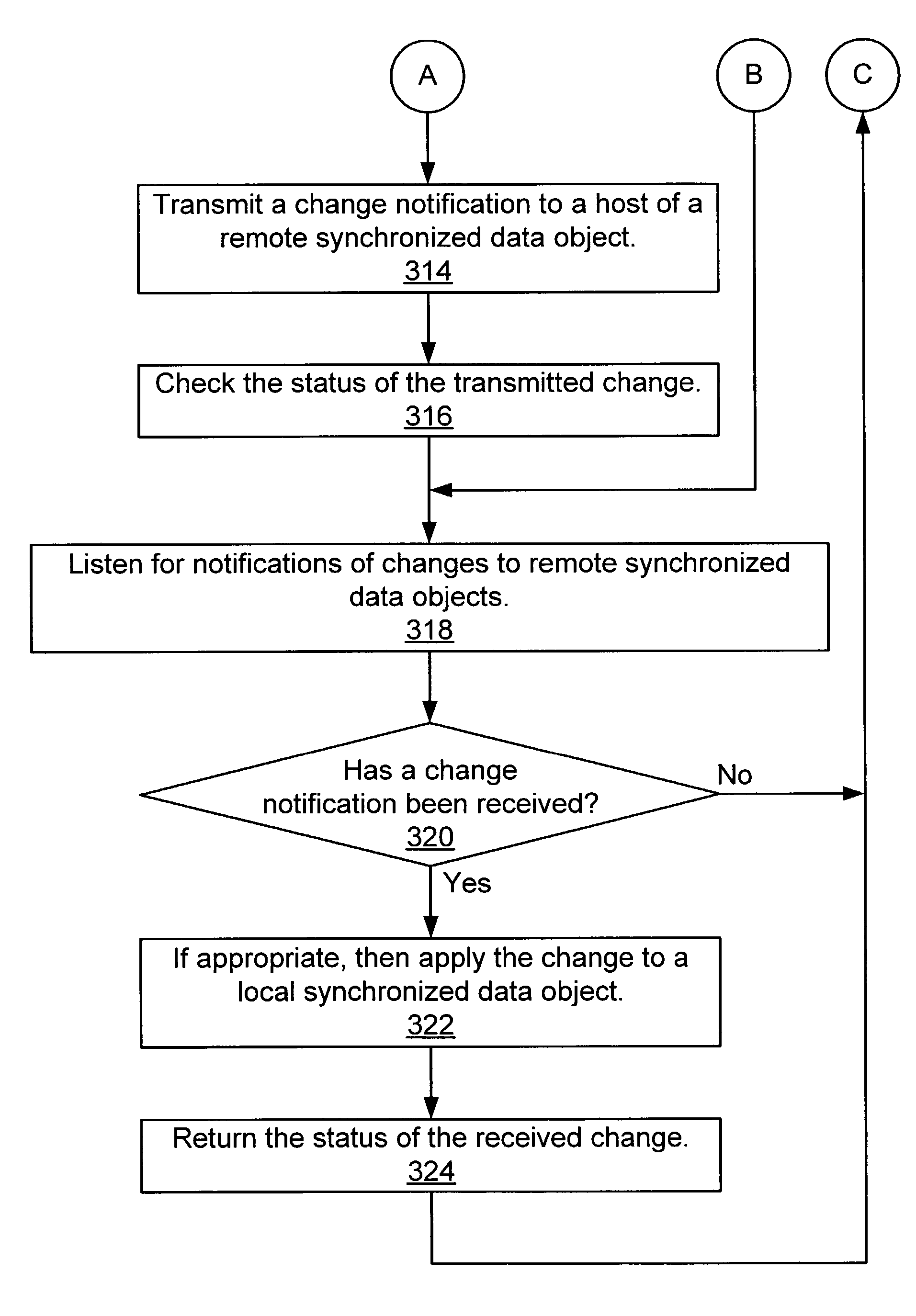
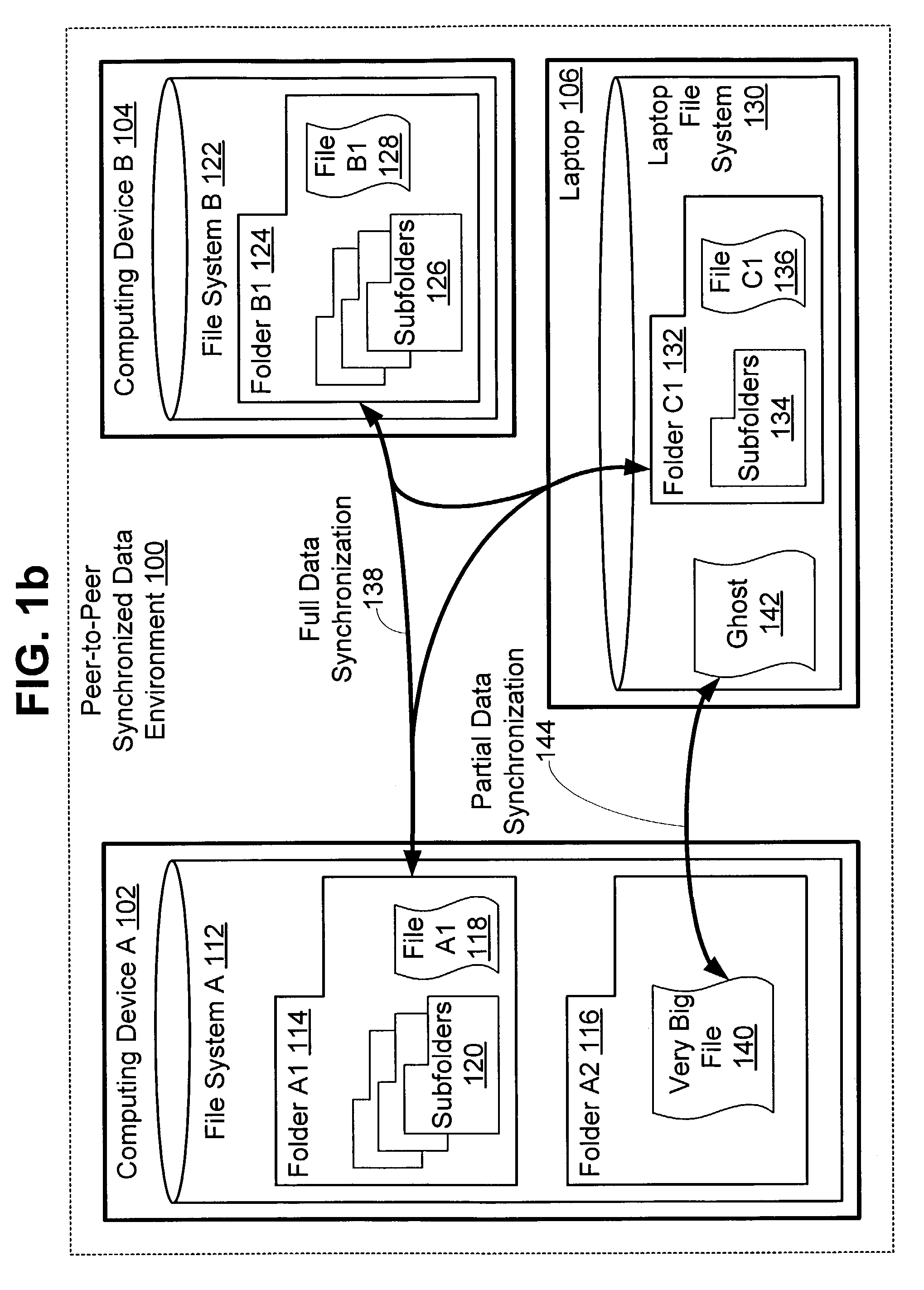
Method and system for synchronizing data shared among peer computing devices
InactiveUS7743022B2Digital data information retrievalDigital data processing detailsData synchronizationDevice Monitor
Disclosed is a data synchronization service for use in a peer-to-peer computing environment. Selected data objects are copied onto selected computing devices. A service running on each device monitors data objects for changes. When a change is detected, the service sends a change notification to the other devices so that they can update their copies of the data object. A user can access a data object from any device, knowing that he will retrieve the latest version of the data object. Instead of incurring the costs of storing a large file on every device, a user “ghosts” the file on some devices. A ghosting device stores only metadata about the file rather than the entire file. The user accesses the file through the ghost: access requests are sent to a device that holds the actual contents, and those contents are presented to the user as if they were stored locally.
Owner:MICROSOFT TECH LICENSING LLC
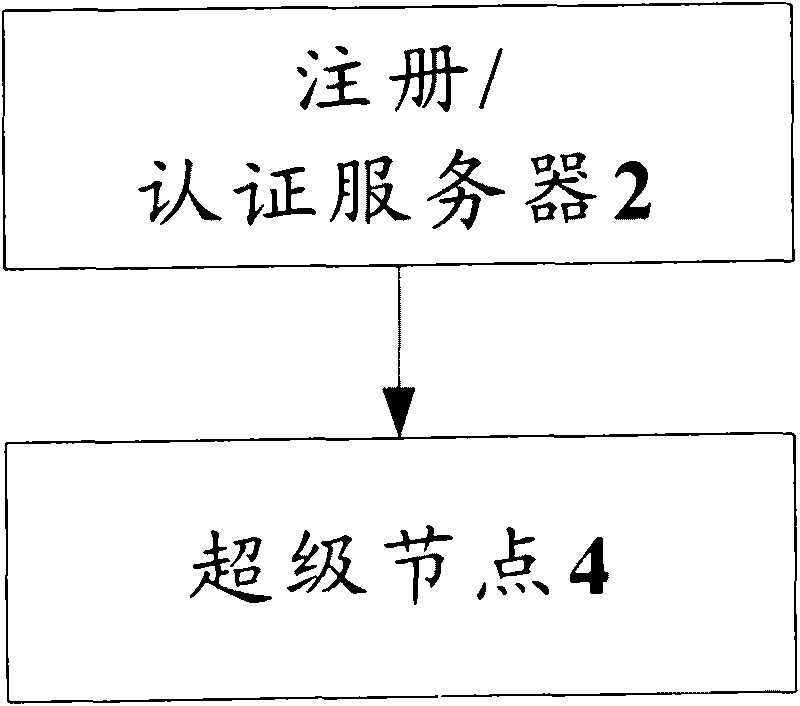
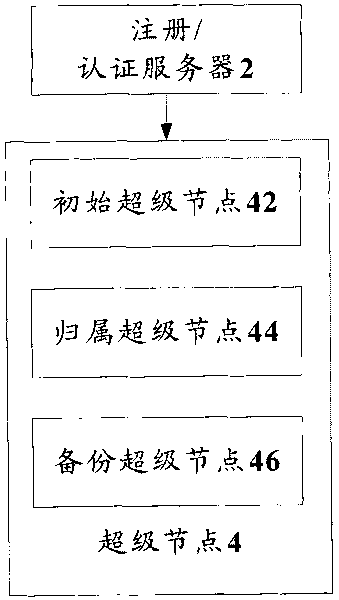
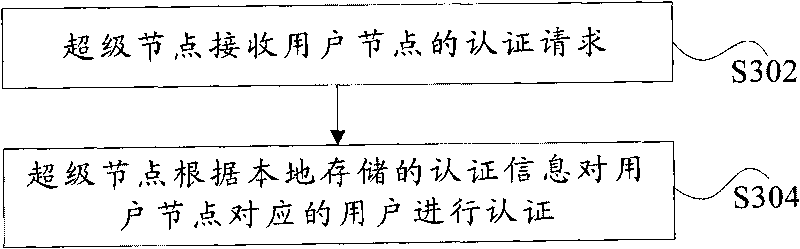
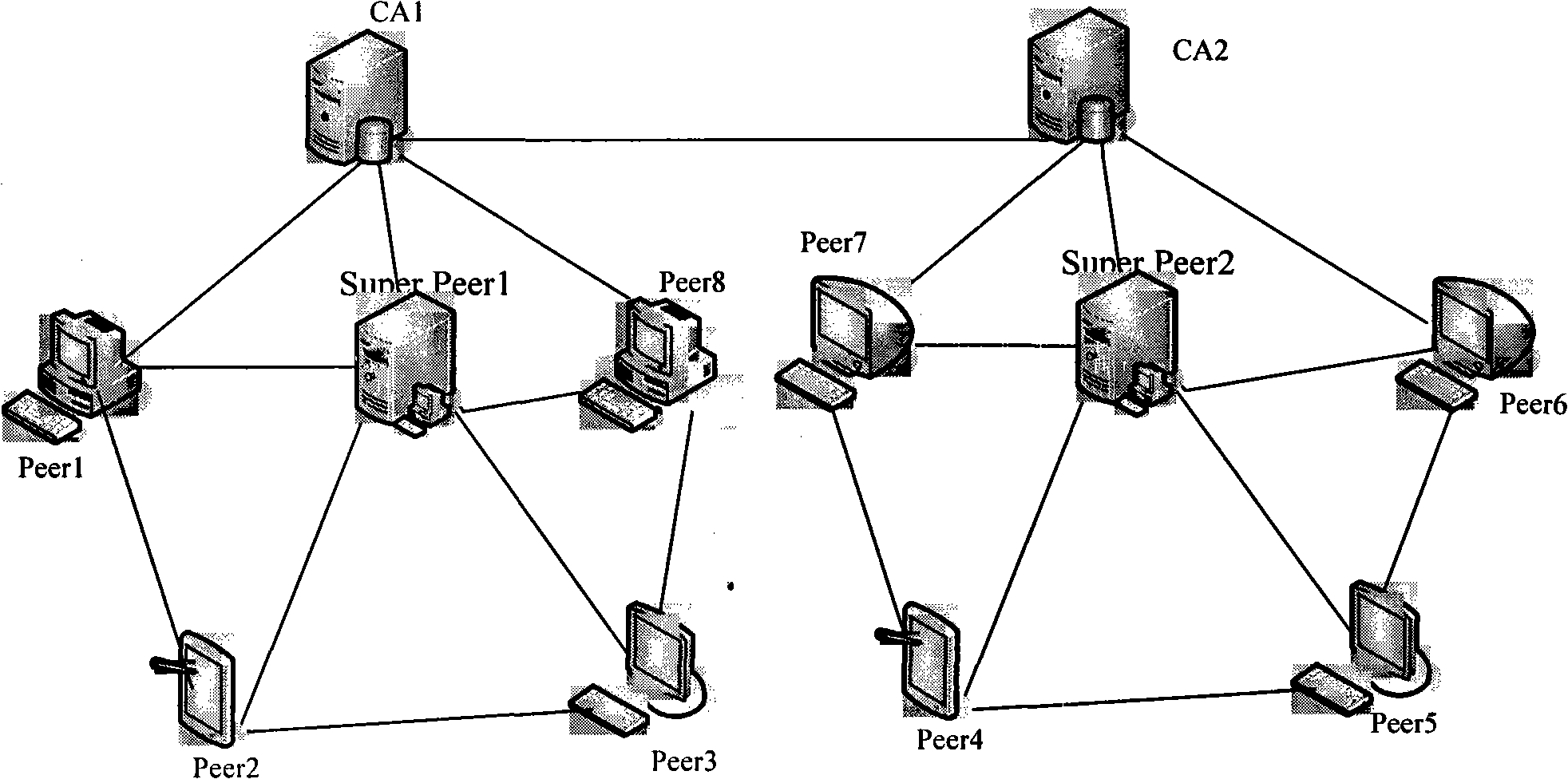
Authentication system and method based on peer-to-peer computing network
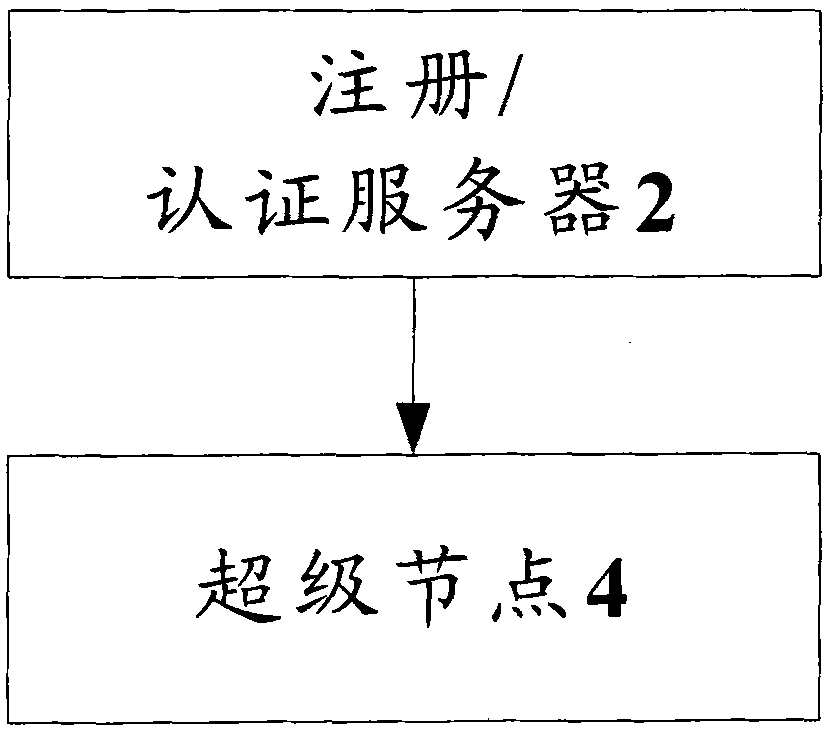
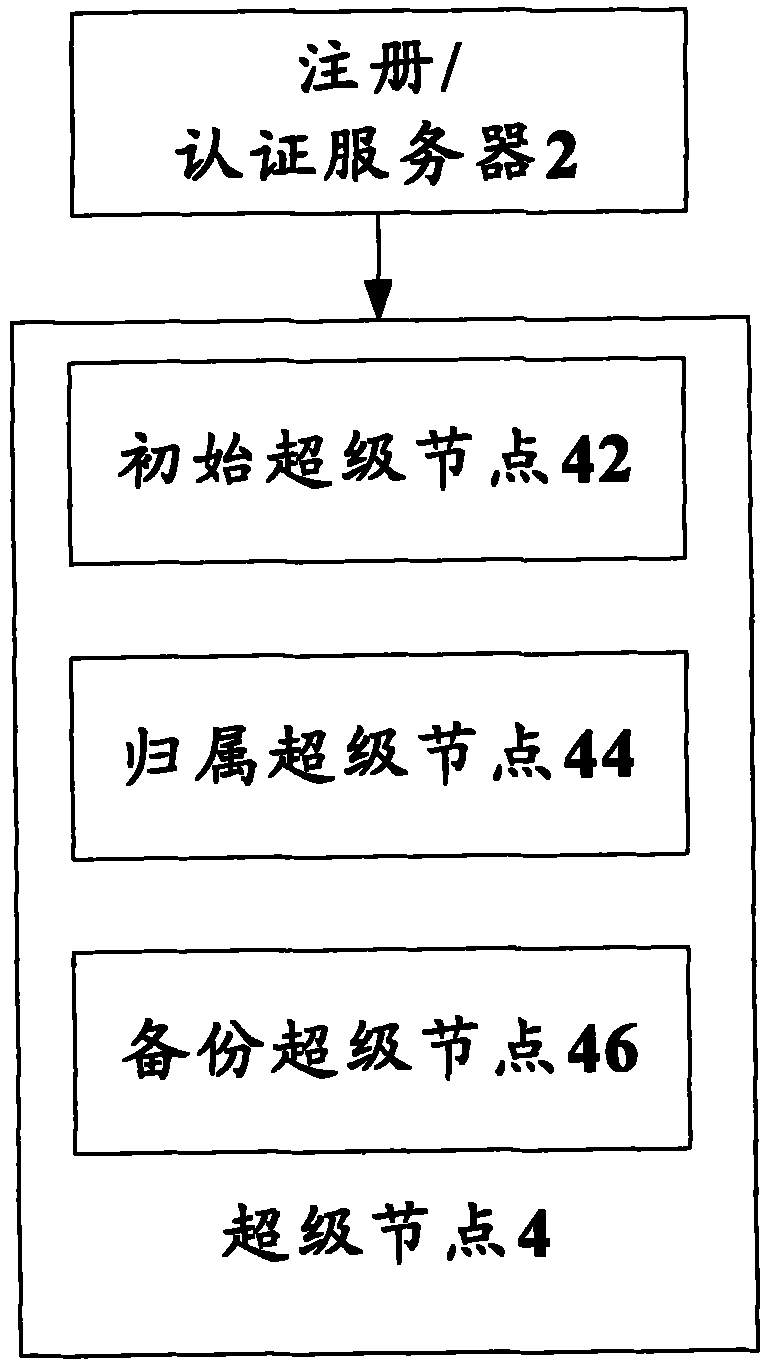
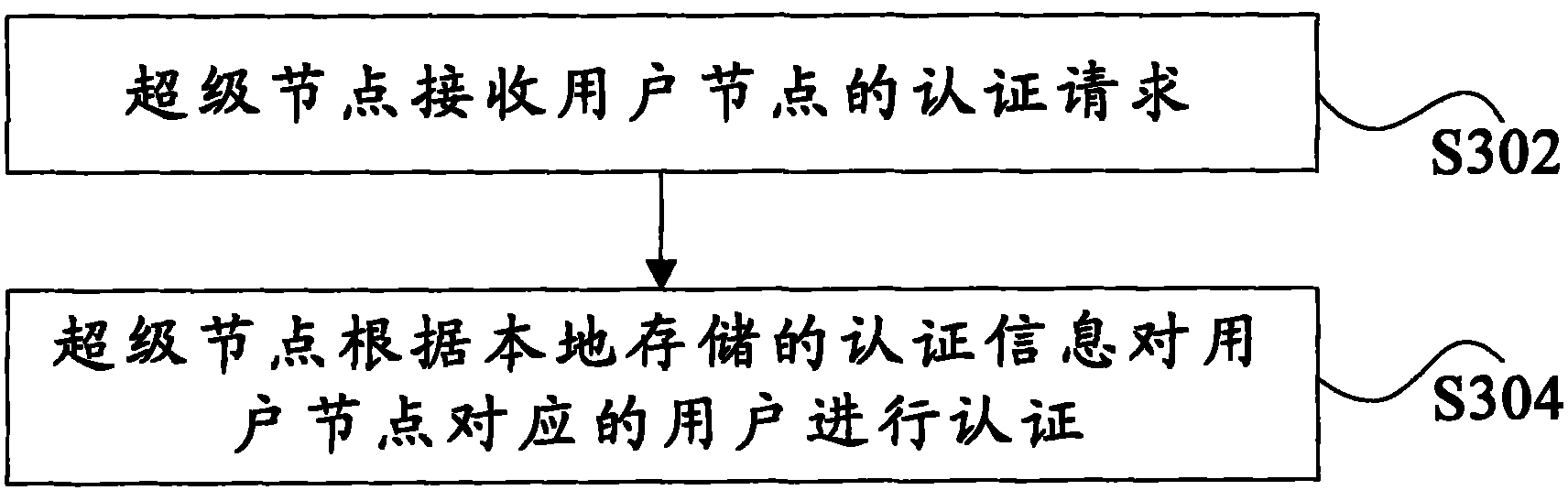
InactiveCN101714996ASolve the problem of single point of failureImprove resource utilizationTransmissionResource utilizationPeer to peer computing
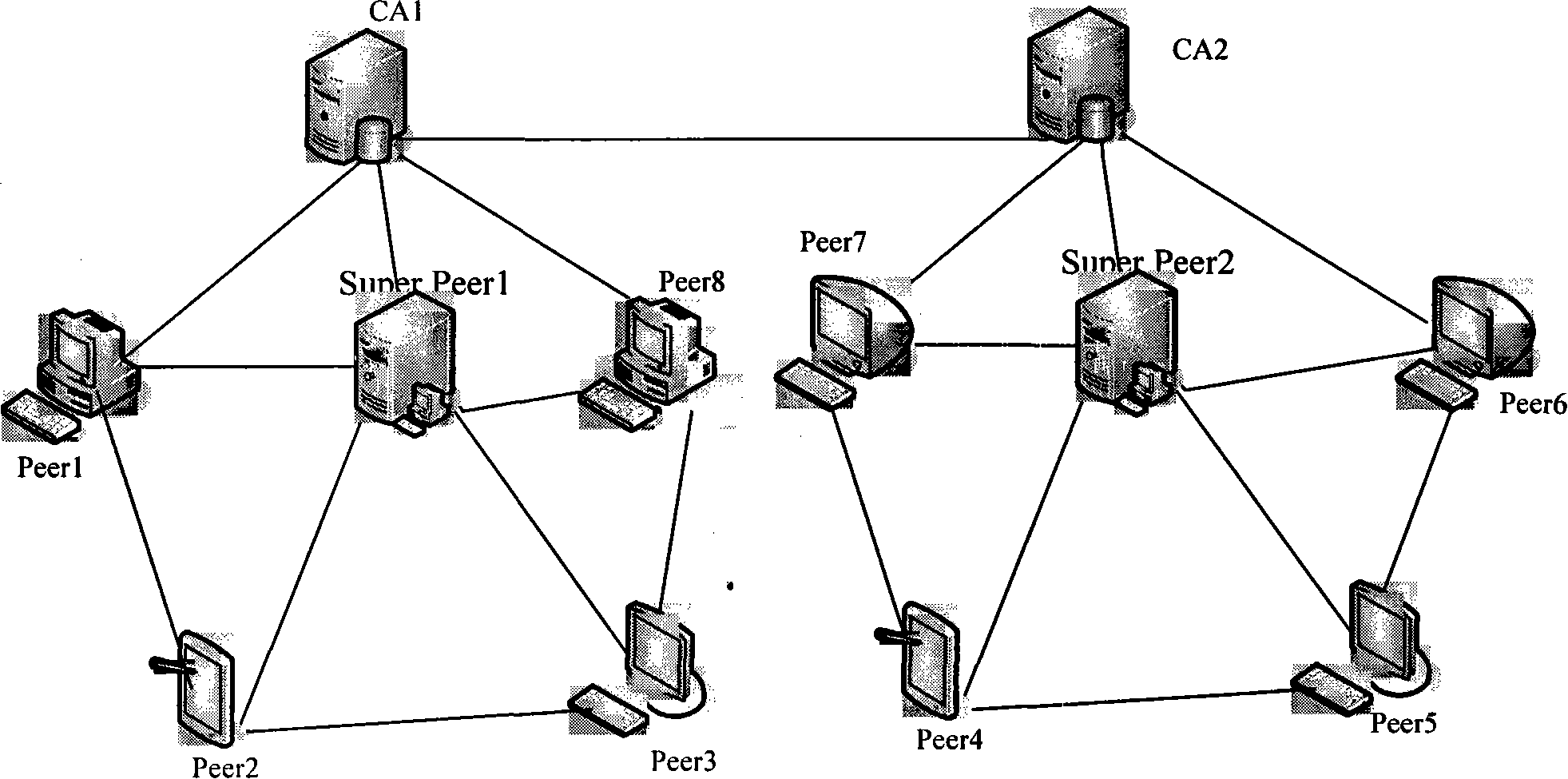
The invention discloses authentication system and method based on a peer-to-peer computing network. The authentication system comprises a super node, and the super node is used for receiving an authentication request of a user node and authenticating a user which corresponds to the user node according to locally stored authentication information. The invention achieves the effect of enhancing resource utilization rate.
Owner:ZTE CORP
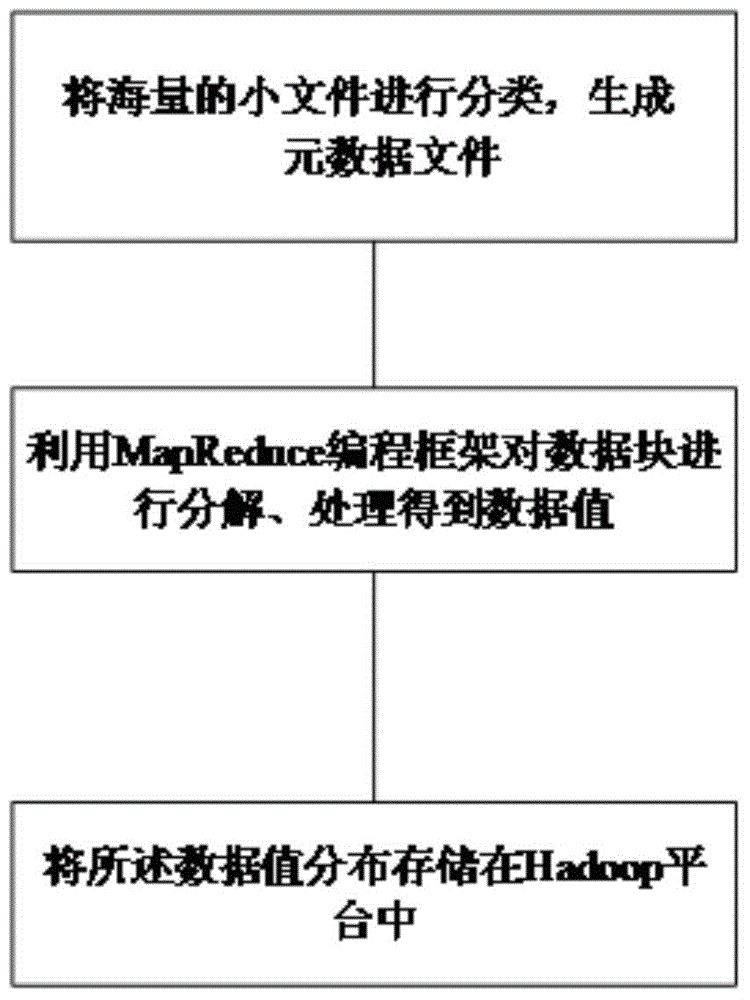
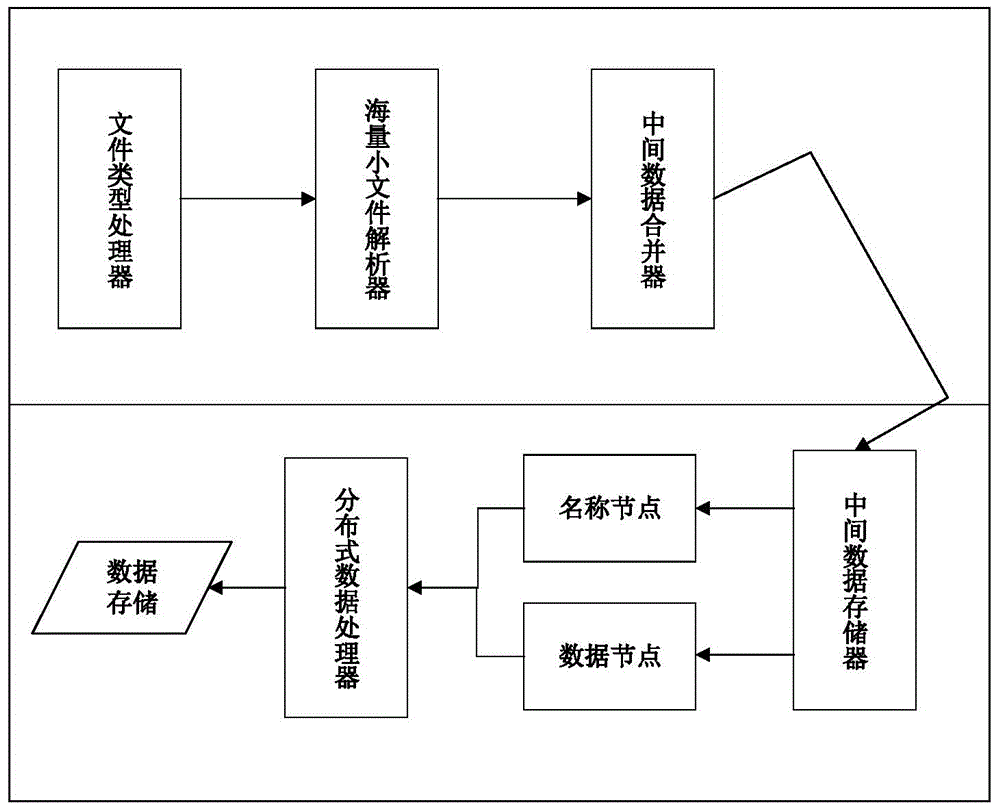
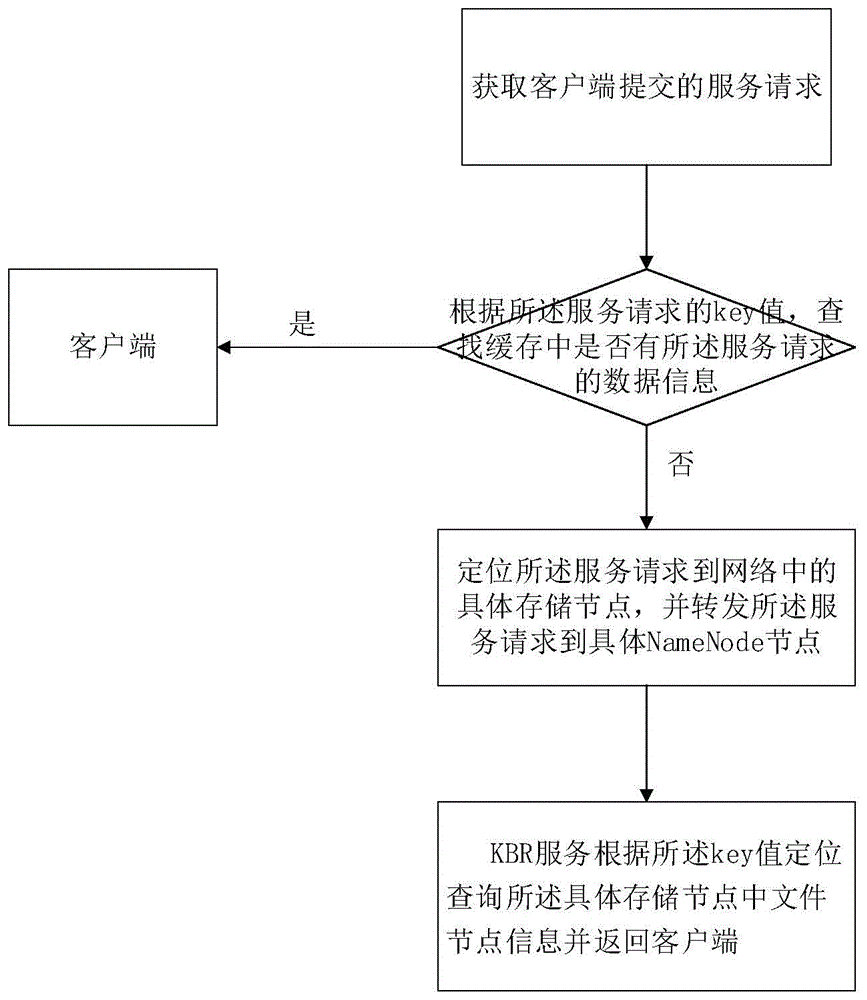
Massive small file storage and management method and system
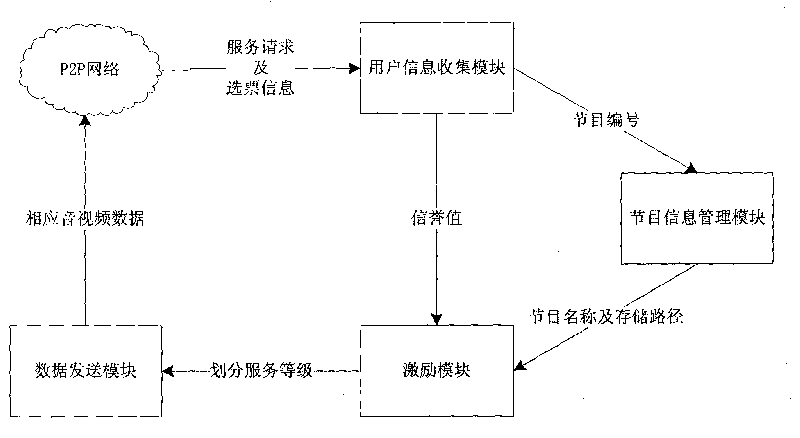
ActiveCN104820717ALoad balancingImprove processing efficiencySpecial data processing applicationsBalancing networkPeer to peer computing
The invention provides a massive small file storage and management method and a system, wherein the massive small file storage and management method comprises that massive small files are stored, and metadata is written into a name node service network, and is managed through the name node service network, thereby achieving access request response of a client. The system comprises the name node service network and a massive small file storage system. The massive small file storage and management method and the system use peer-to-peer computing technology, prevent the problem of single point failure, provide routing lookup method based on keywords, effectively balance network load, and improve query efficiency.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +3
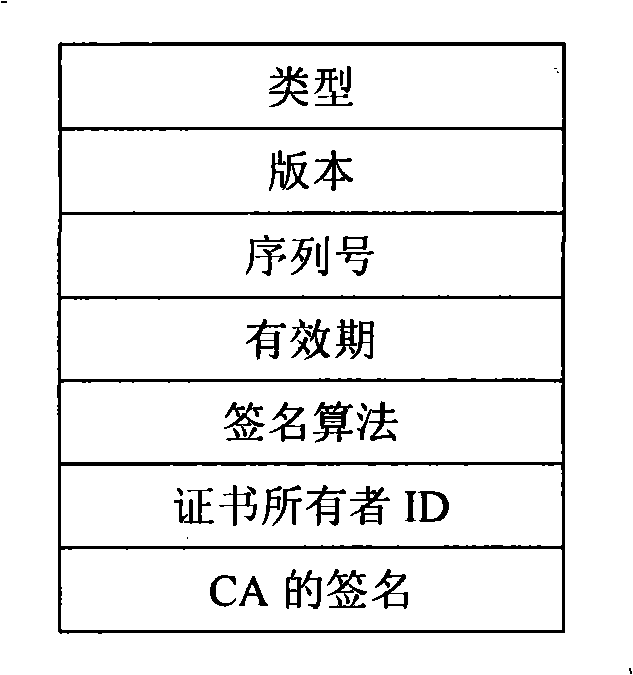
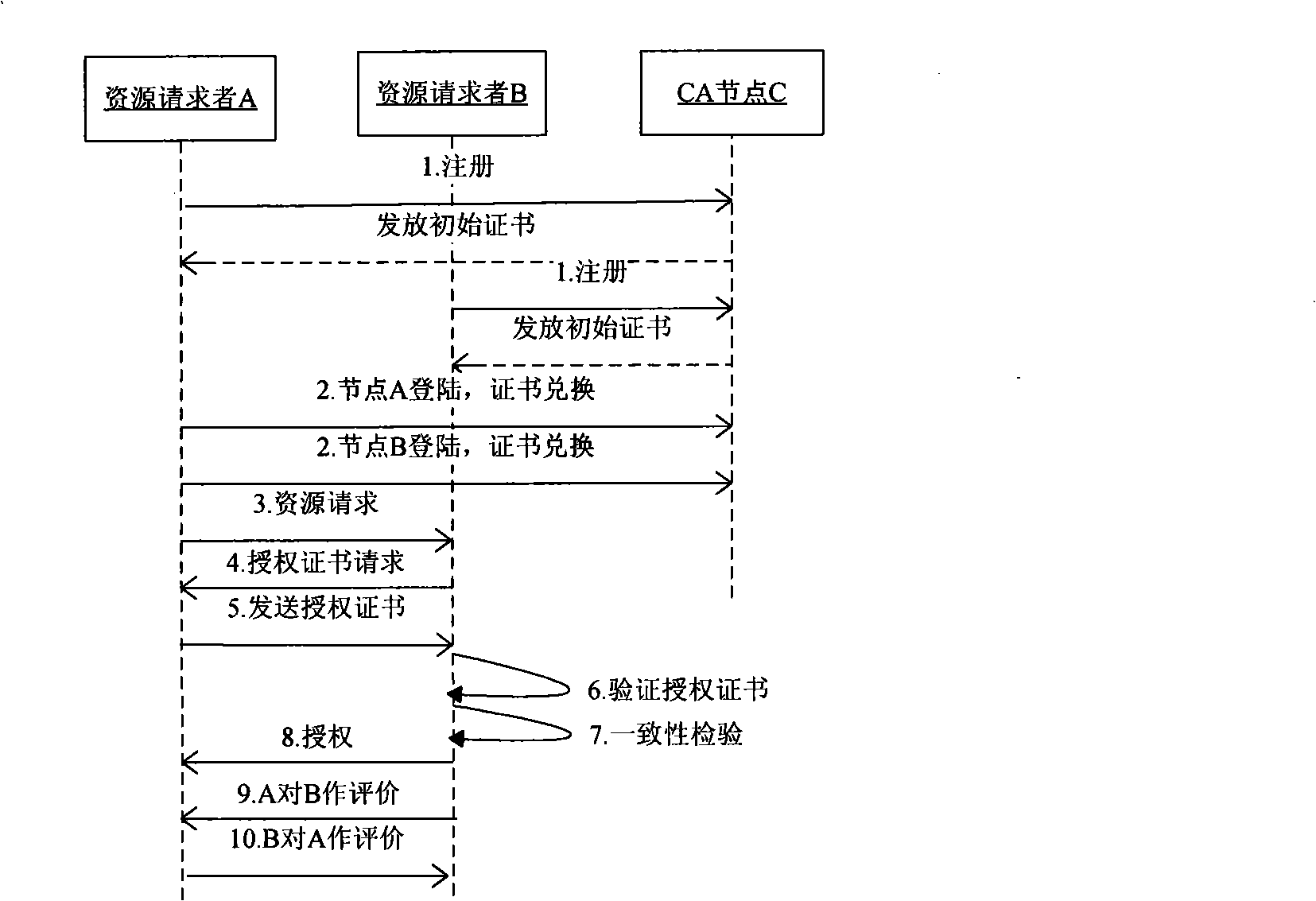
Method for evaluating and authorizing peer-to-peer network node by certificate
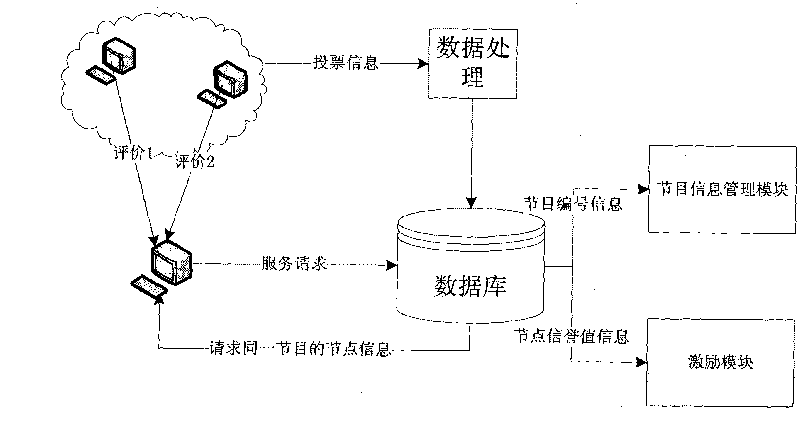
InactiveCN101335618AReduce direct interactionImprove securityPublic key for secure communicationUser identity/authority verificationAuthorization certificateTimestamp
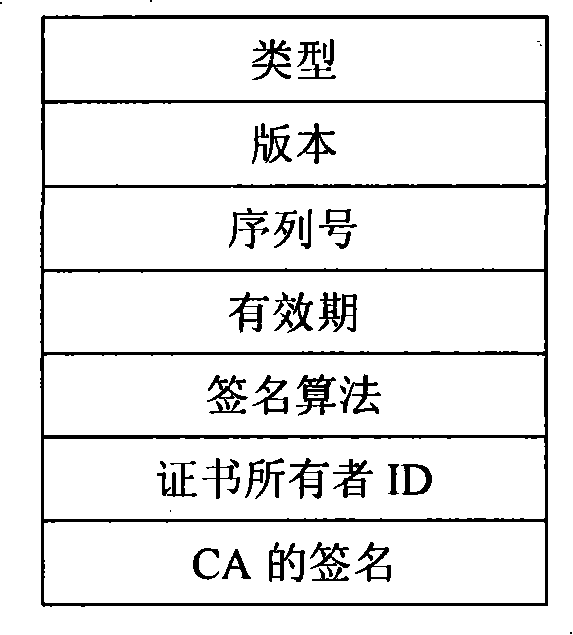
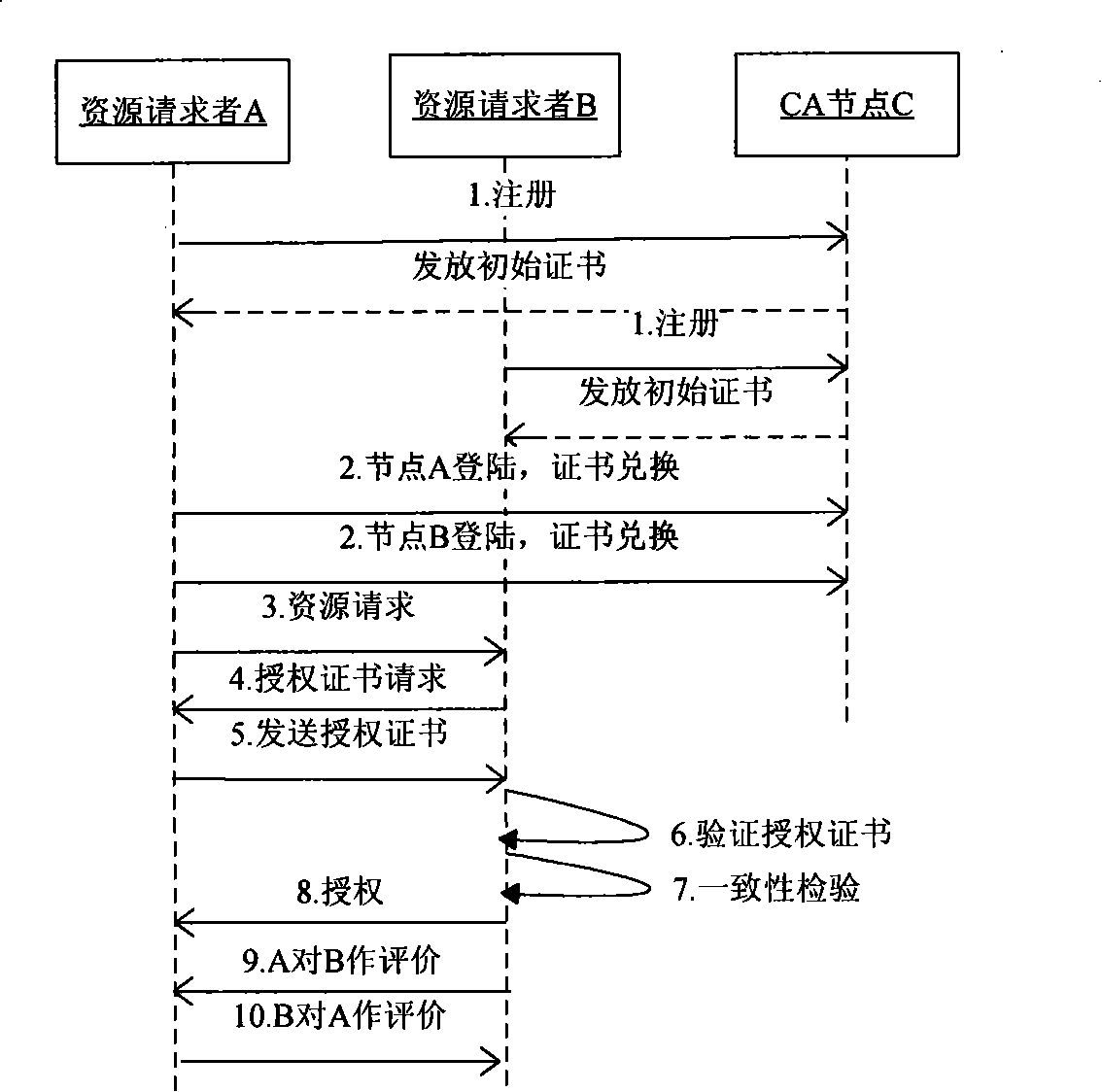
The invention discloses a method for carrying out evaluation and authorization to nodes in a peer-to-peer network by applying a certificate, which provides a safety-oriented authorization scheme in the peer-to-peer network, takes advantage of the features such as the strong dynamism of the peer-to-peer network and the strong independence of the nodes, etc., adopts the authorization scheme that associates evaluation with permission and essentially solves the problem of safe authorization in distributed computation. The method of the invention comprises the steps that: according to the levels of the authority certificate hold by the nodes and the levels of resources that are asked to be accessed by resource requesters, authorized decision-making is carried out by a resource provider; after transaction is finished, the resource providers and the resource requesters directly adopt the certificate to evaluate the performance of the other party; when a node logs in next time, the obtained evaluation certificate and the left authorization certificates are exchanged on a super node firstly so as to obtain the timestamp of a new certificate, continue the afterwards transaction, and improve evaluation rationality and authorization security carried out to node behavior in the peer-to-peer computing field. Compared with other evaluation and authorization schemes, the scheme of the invention is characterized by simplicity and safety, etc..
Owner:NANJING UNIV OF POSTS & TELECOMM
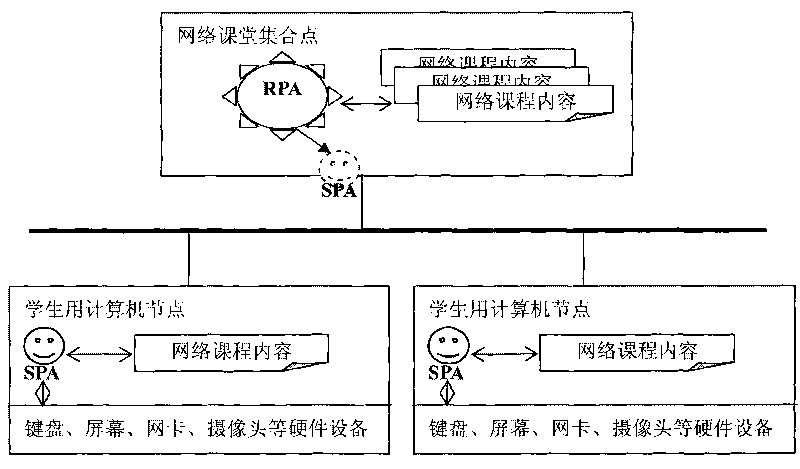
Method for supervising online class in real time or non real time based on peer-to-peer agents
InactiveCN101707011AReduce the burden onEffective monitoring of learningTransmissionElectrical appliancesNon real timePeer to peer computing
The invention relates to a method for supervising online class in real time or non real time, which is used in network computing environment based on Internet or Intranet, and realized by adopting peer-to-peer agents, and aims at solving the problems that classroom teaching in network environment can not ensure the quality and effect of teaching due to looseness, uncertainty and resistance to control, and the teaching result is not satisfactory. The method fuses agent technology and peer-to-peer computing technology together and applies the agent technology and the peer-to-peer computing technology to the real-time and non-real-time supervising system of an online class. The online class supervising system is divided into two parts: a computer for teachers and computers for students, wherein the computer for teachers is taken as an online class gathering point, and is resided with peer-to-peer agents of the gathering point for a long time so as to be in charge of establishing the peer-to-peer agents which are dispatched to the computers for students to supervise the situation of online class learning of students and interact with the peer-to-peer agents, thus realizing effective supervision on the situation of online class learning of students and leading the teacher to be capable of conveniently knowing the situation of online class learning of students at all places in real time and non real time.
Owner:NANJING UNIV OF POSTS & TELECOMM
Broadcasting a presentation or a file to an unlimited number of recipintes through peer-to-peer technology
InactiveUS20020120783A1Shorten the timeSave computing resourcesBroadcast information characterisationResource management arrangementsPeer to peer computingThe Internet
Broadcasting a presentation or sending files through the Internet to an unlimited number of recipients using a personal computer and peer-to-peer computing. An initiating computer contacts the members on a list, who in turn contact additional members from the list. The initial users screen image is captured and compressed into a file. The compressed file is then transferred to the users on the list using any electronic medium. Subsequent changes made to the initial user's screen are placed in a compressed file and sent to the users on the list. First file is viewed in conjunction with the files containing the changes, allowing the users on the list to view presentation.
Owner:EVGEY DAVID
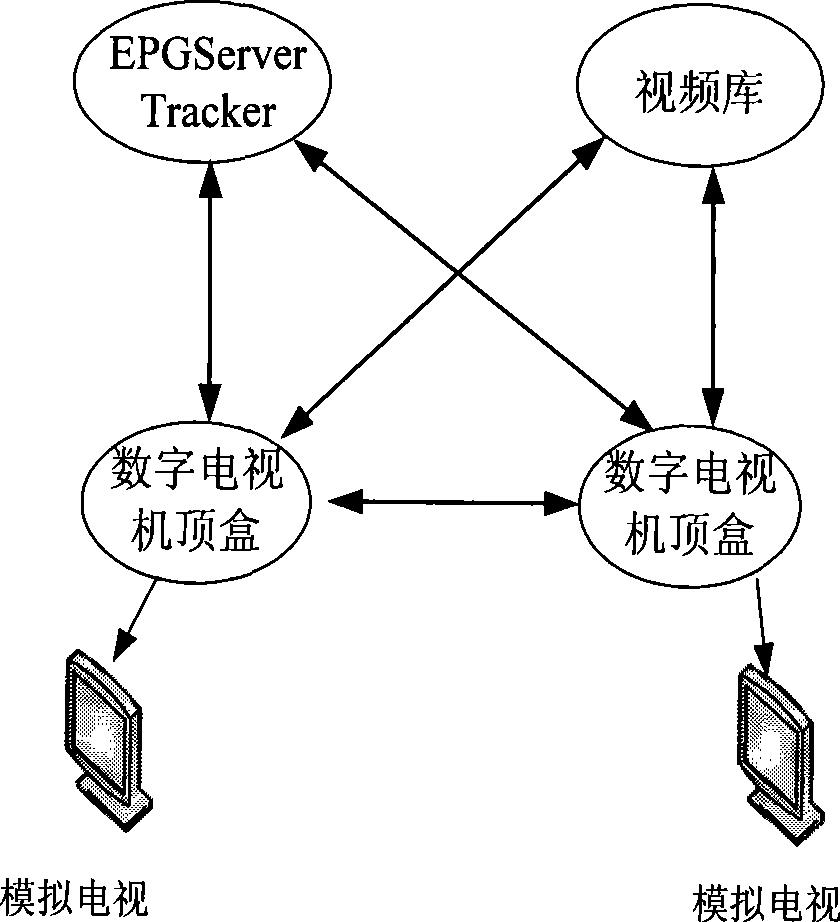
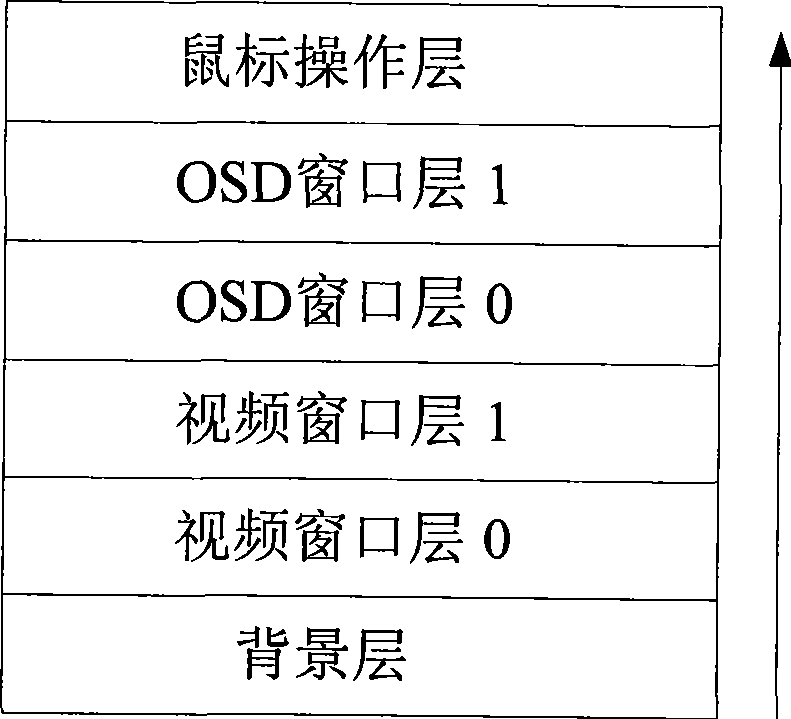
Set-top box on screen display system implementing method based on peer-to-peer computing technique
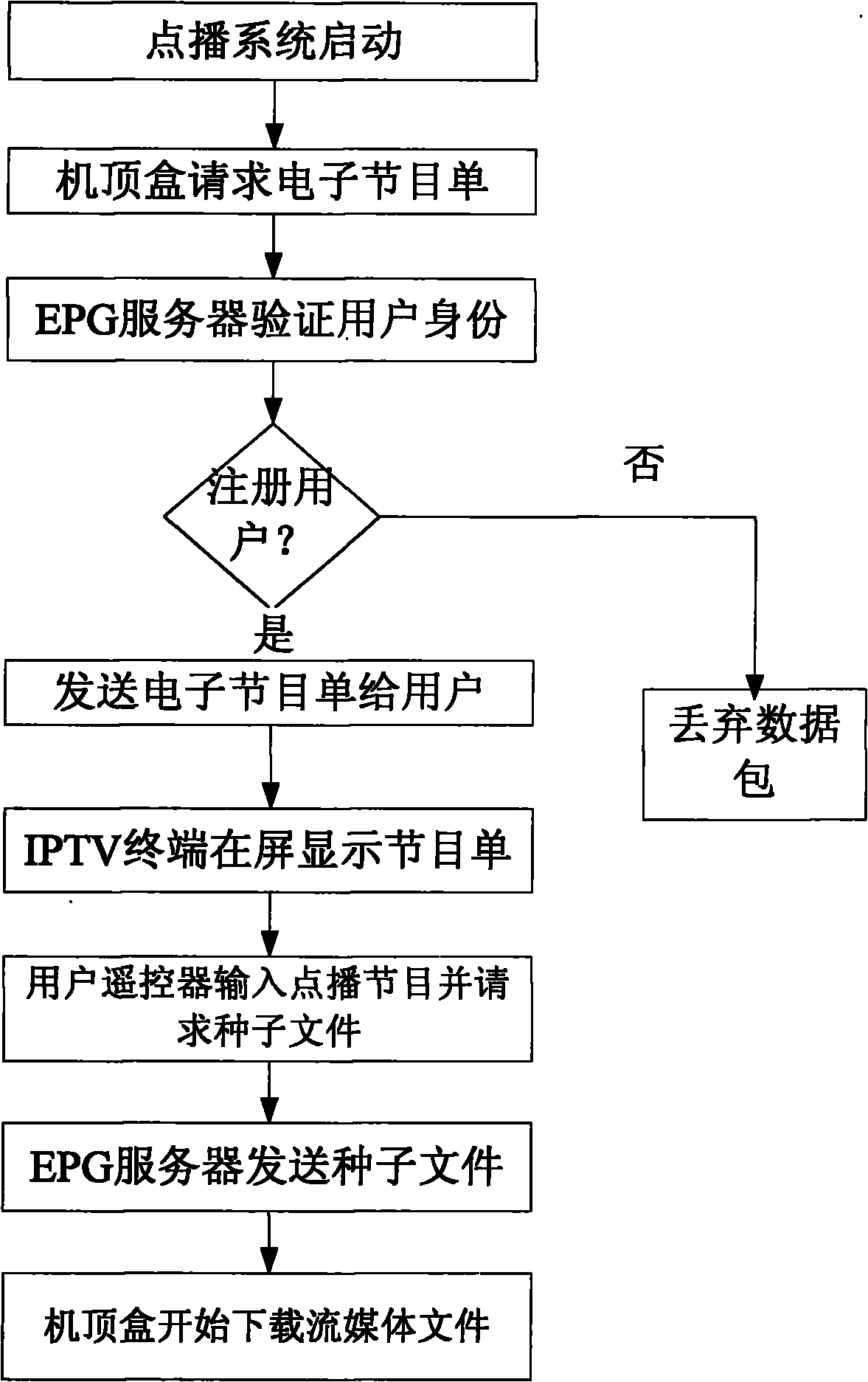
InactiveCN101365082AGood human-computer interfaceStrong scalabilityTelevision system detailsSpecific information broadcast systemsOperabilityXML
A realization method for a set-top box in a screen display system based on the peer-to-peer computing technology introduces a graphic layering technology, a bitmap storage technology, an encoding conversion technology, a SOAP technology which are used for meeting the requirements of GUI design, Chinese displaying, XML coding conversion, interaction with an EPG server, etc. that need to be processed in the development of an OSD system. Based on P2P protocol, a solution to the OSD system of an IPTV set-top box is provided on a DM6446 platform to solve the problems of GUI design, Chinese displaying, XML coding conversion, interaction with the EPG server, system integration, etc. Compared with the popular OSD systems for the set-top box in current market, the scheme has the advantages of novelty, flexibility, high expansibility, and high operability.
Owner:NANJING UNIV OF POSTS & TELECOMM
Video ordering transmission method based on peer-to-peer computing set-top box
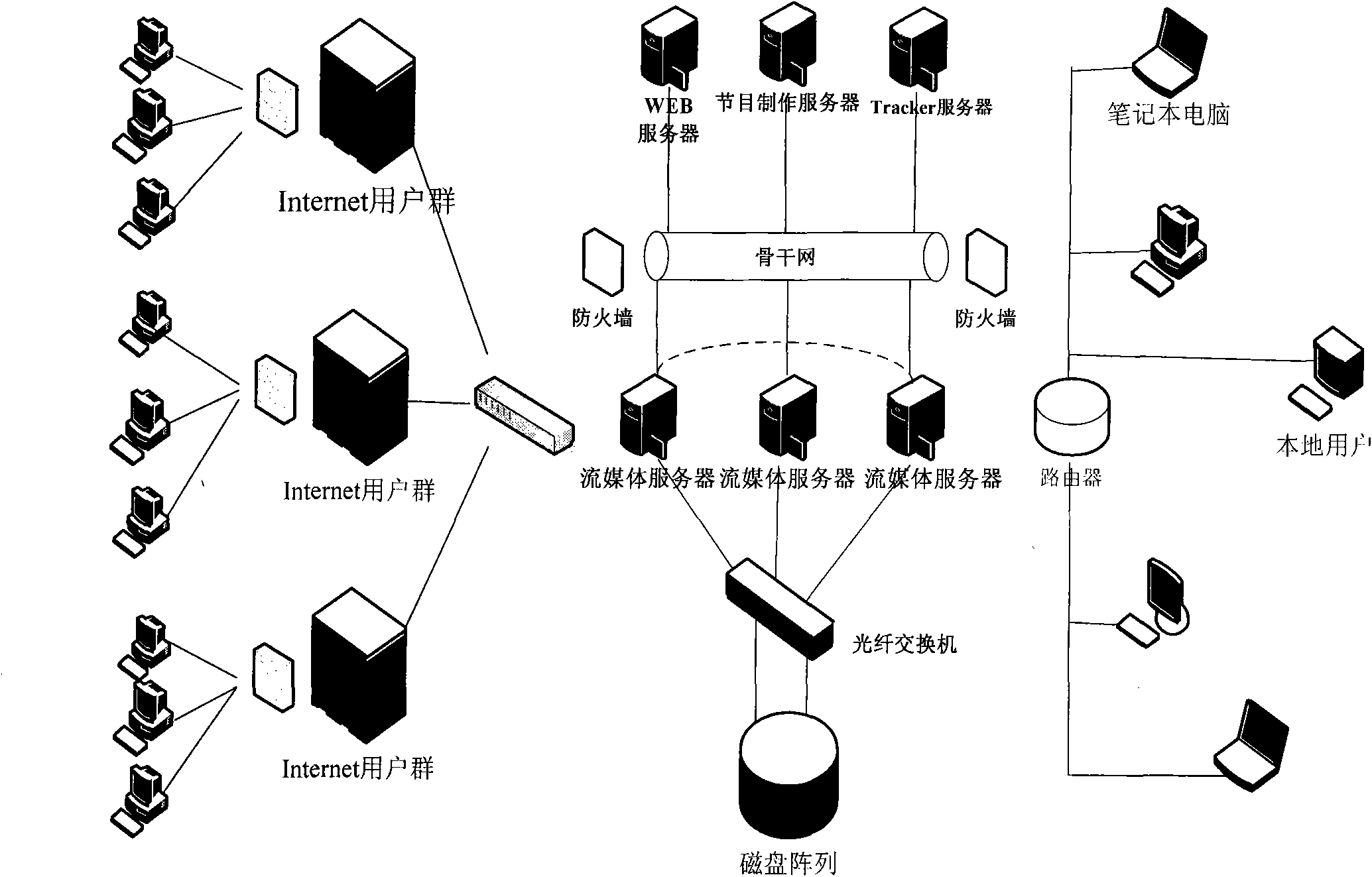
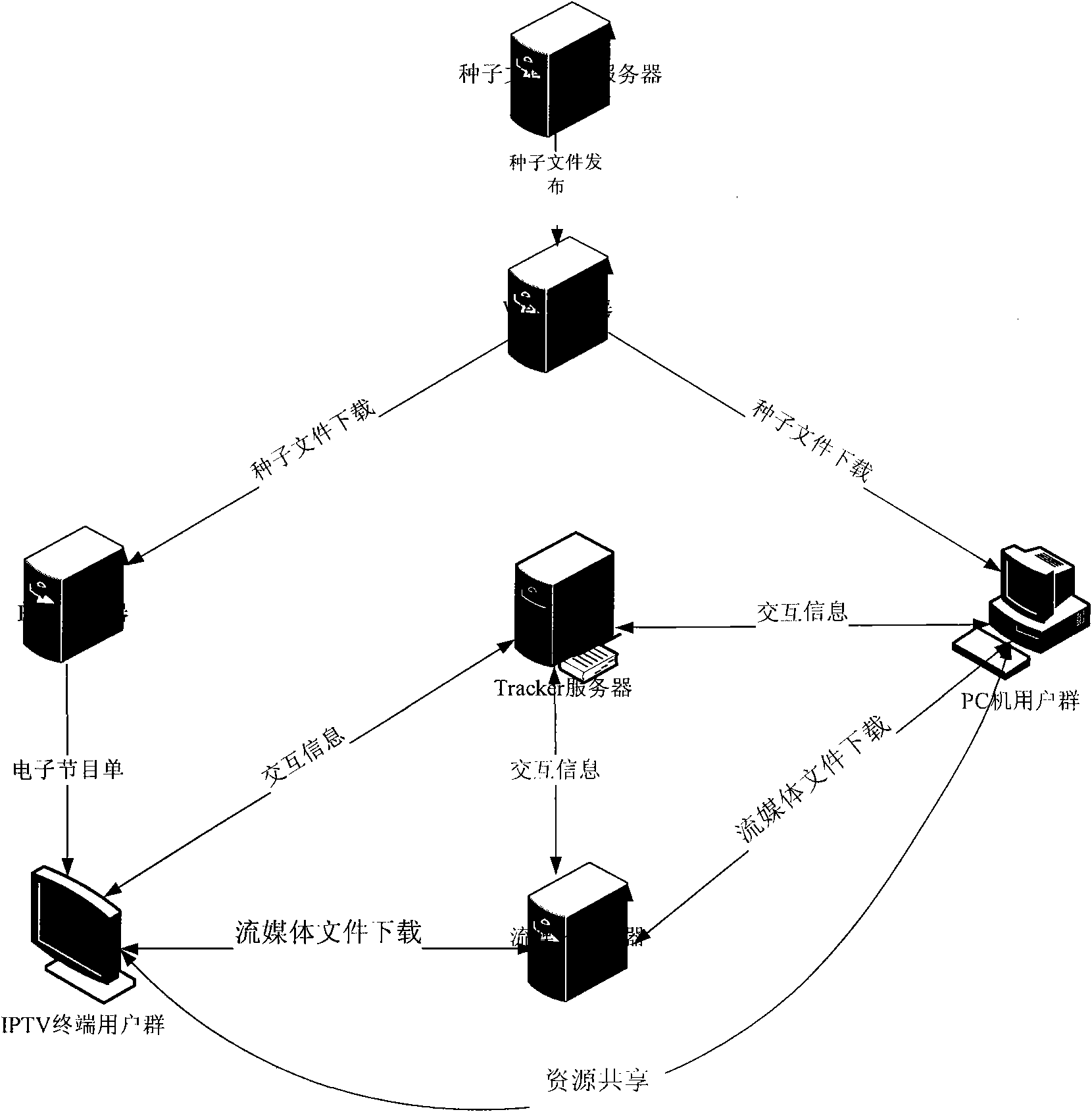
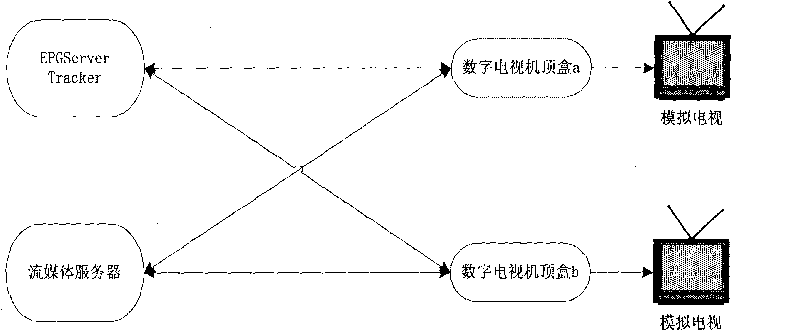
InactiveCN101867777AImprove transmission efficiencyMeet the requirements of on-demandPulse modulation television signal transmissionTwo-way working systemsBit torrentStructure of Management Information
The invention relates to a topological structure of a video ordering transmission method based on a peer-to-peer computing set-top box, which comprises a web television (IPTV) back stage service system, an IPTV terminal user group and an Internet user group, wherein the IPTV terminal user group consists of each user set-top box, the Internet user group consists of personal computer (PC) users, and the IPTV back stage service system mainly consists of an electronic program list server (EPG), an index server (Tracker), a seed manufacture server, a web page browsing server (WEB) and a stream media server. The invention improves the Bit Torrent protocol, introduces a slide window, adopts an integrated cataloged peer-to-peer (P2P) structure, solves the problems of server single-point failure and server connection bottleneck, lightens the pressure loaded at the server end, and realizes the application of the peer-to-peer computing to the set-top box.
Owner:NANJING UNIV OF POSTS & TELECOMM
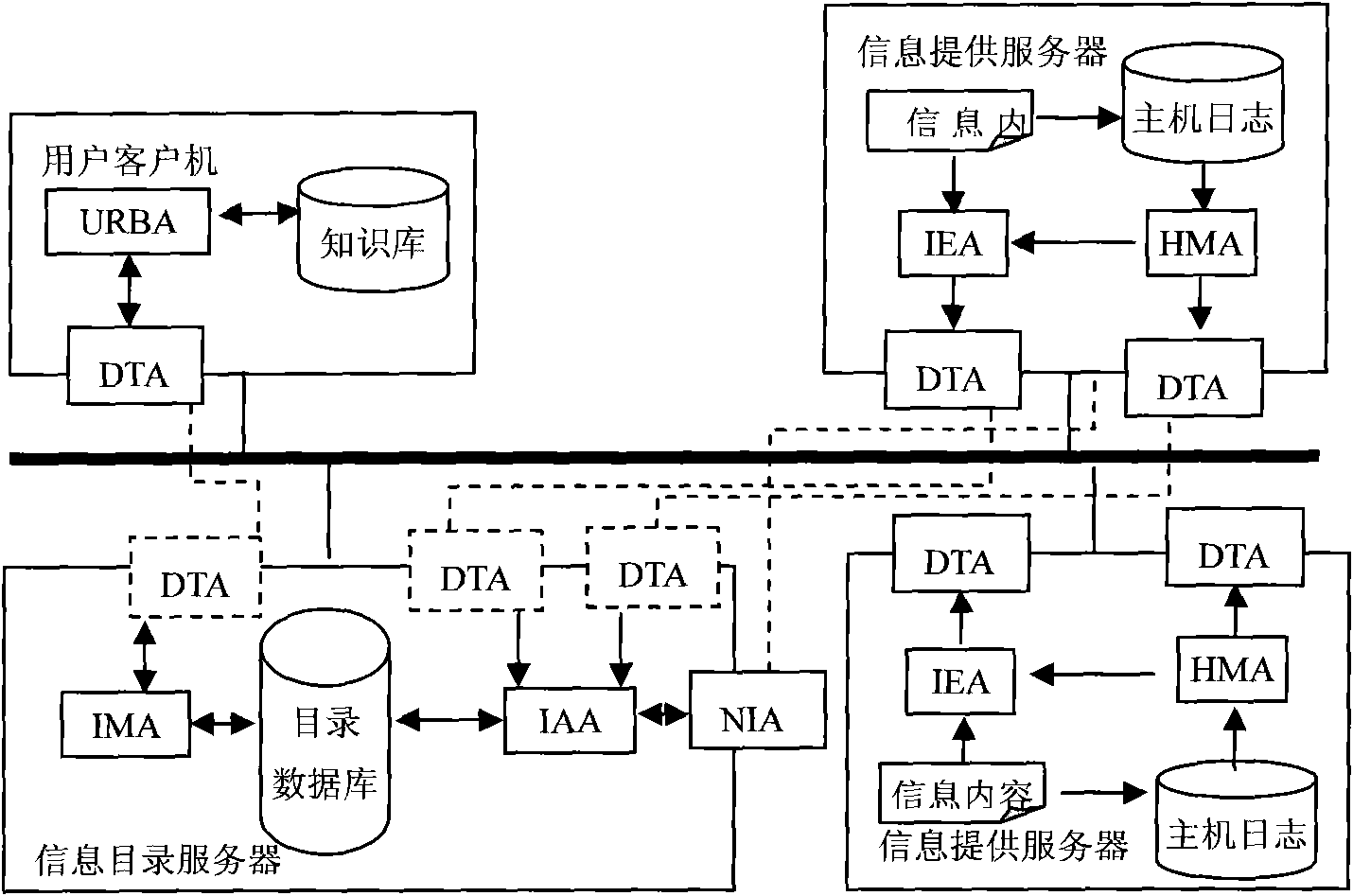
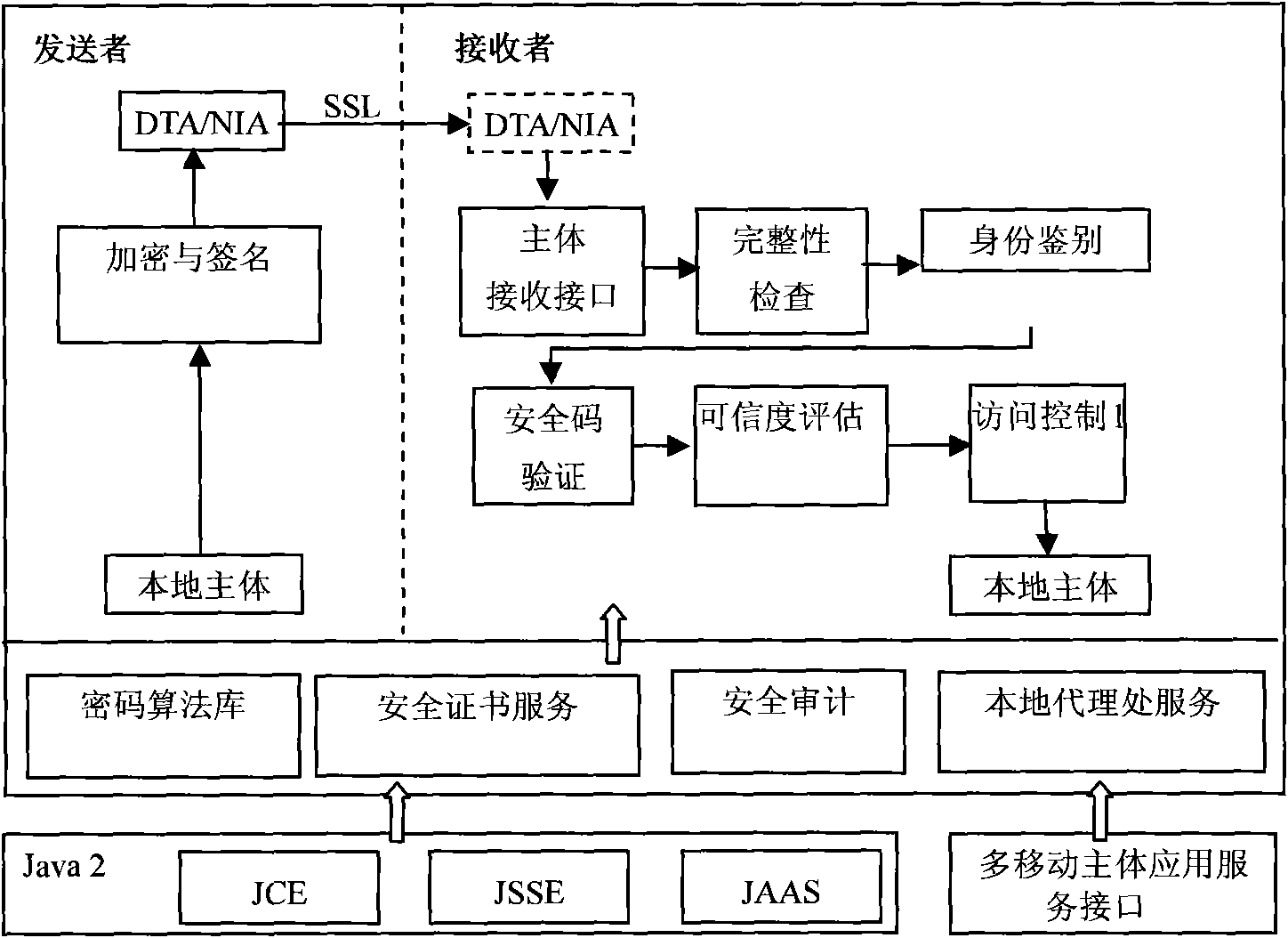
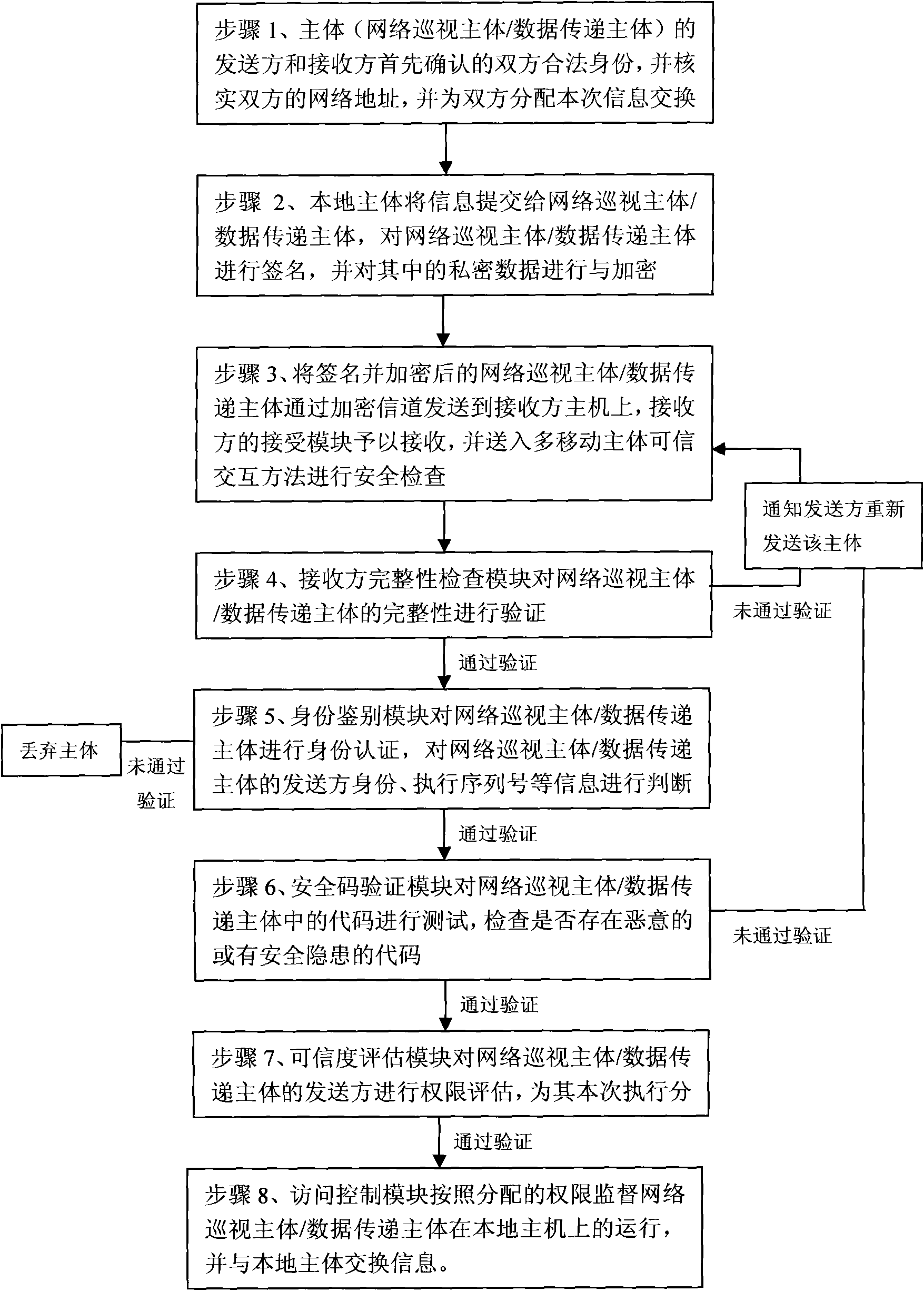
Multiple-mobile-agent credible interaction method for information acquisition system in open network
The invention relates to a credible interaction method used for ensuring the operational safe reliability of a system in an open network computing environment, such as grid computing, peer-to-peer computing, cloud computing and the like, when the multiple-mobile-agent technology is used for constructing corresponding network application systems, such as information acquisition systems and the like. From the angle of the application of the information acquisition in open networks, aiming at the safety problems in the information acquisition systems based on multiple mobile agents in an open network computing environment, the invention provides a credible interaction method as well as a solution. The specification firstly introduces the architecture and the working principle of the information acquisition system based on multiple mobile agents, deeply analyzes the safety problems of the system, designs the structure of the multiple-mobile-agent credible interaction method, and provides the specific working procedure of the multiple-mobile-agent credible interaction method. The multiple-mobile-agent credible interaction method solves the safety problems and has reference value for other application systems based on multiple mobile agents.
Owner:NANJING UNIV OF POSTS & TELECOMM
Autonomic peer-to-peer computer software installation
InactiveUS7890952B2Software testing/debuggingProgram loading/initiatingPeer to peer computingComputer software
Owner:INT BUSINESS MASCH CORP
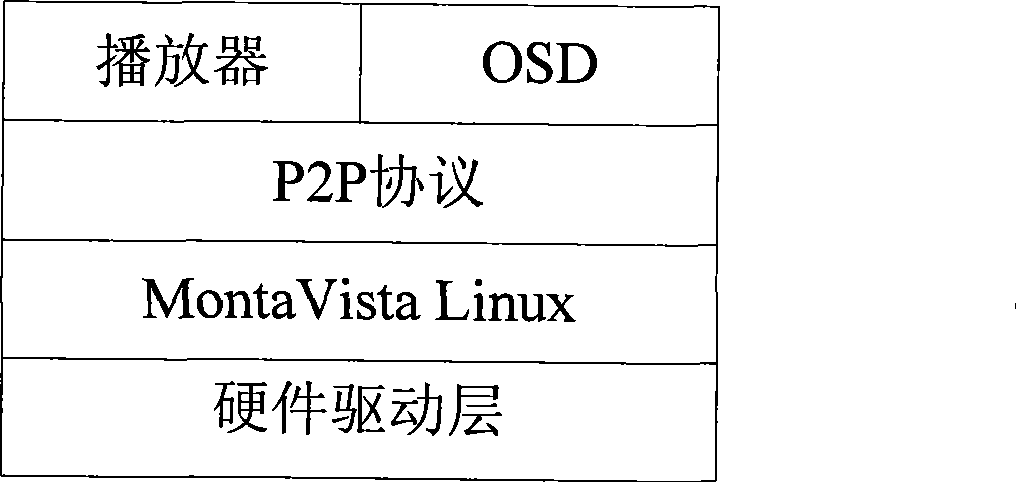
Implement method for mixing network TV stream media server of peer-to-peer computing network
InactiveCN101699860AGood human-computer interfaceVersatileTwo-way working systemsTransmissionMix networkPeer to peer computing
The invention discloses an implement method for mixing network TV stream media server of peer-to-peer computing network. The implement method is a solution of an IPTV set top box stream media server system on the basis of the P2P protocol by aiming at the DM6446 platform and solves the problems of designing GUI, building RTSP connection, interacting with an EPG (Electronic Program Guide) server, sending data, managing programs, stimulating the P2P digital set top box and the like. Compared with the popular stream media server system in the current market, the scheme of the invention has novelty, flexibility, easy expansibility and easy handleability, has pertinence to the P2P digital set top box and has favourable market prospect. The invention detailedly divides the function and the requirements of the IPTV top set box adopting the P2P technology, adopts the thought of modular design and humanity design as well as proposes and realizes the RTSP stream media server system according to the principle of owning favourable man-machine interaction interface.
Owner:NANJING UNIV OF POSTS & TELECOMM
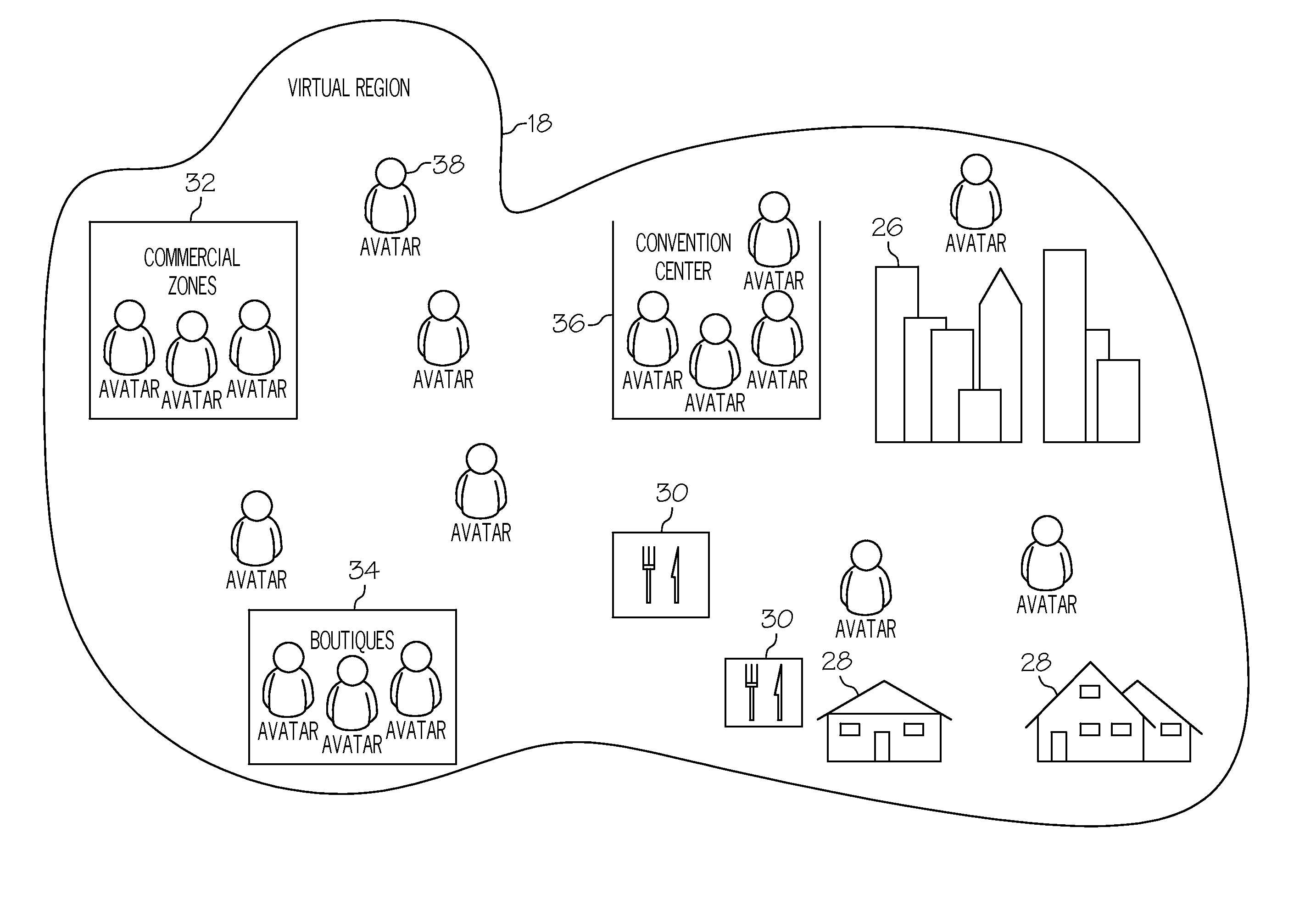
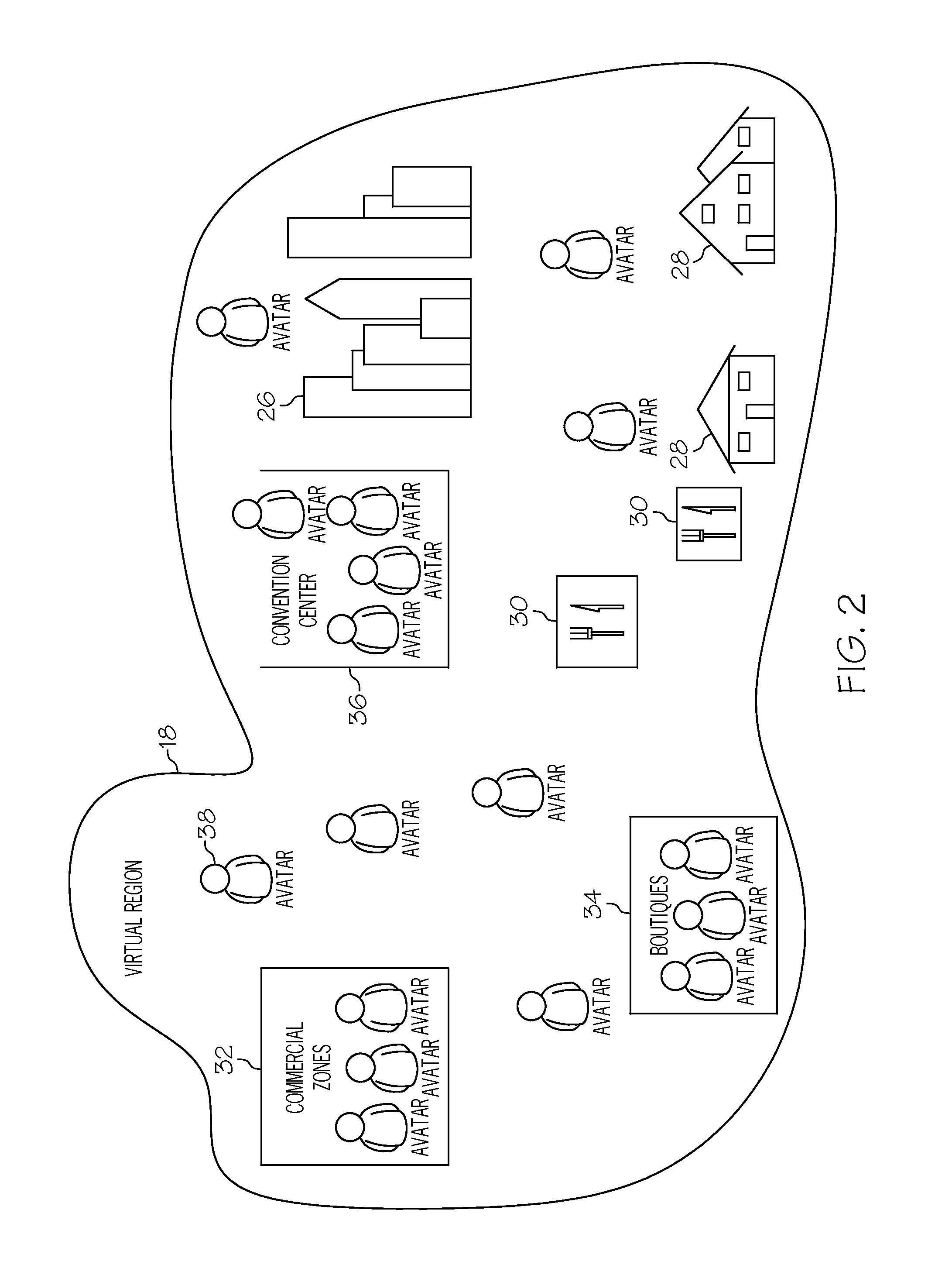
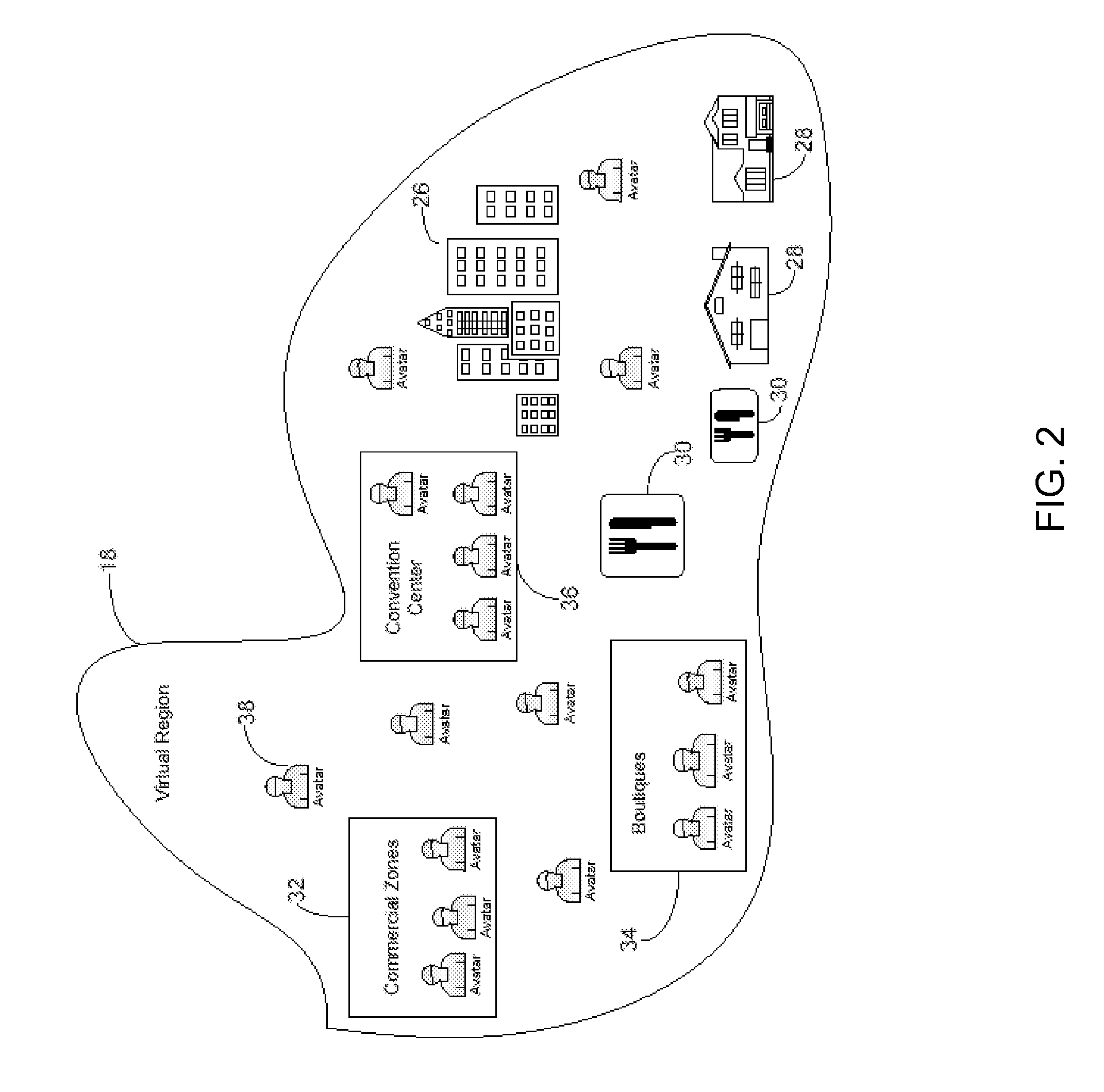
Peer-to-peer based content delivery in a virtual universe
ActiveUS8276084B2Multiple digital computer combinationsVideo gamesPeer to peer computingVirtual world
Owner:KYNDRYL INC
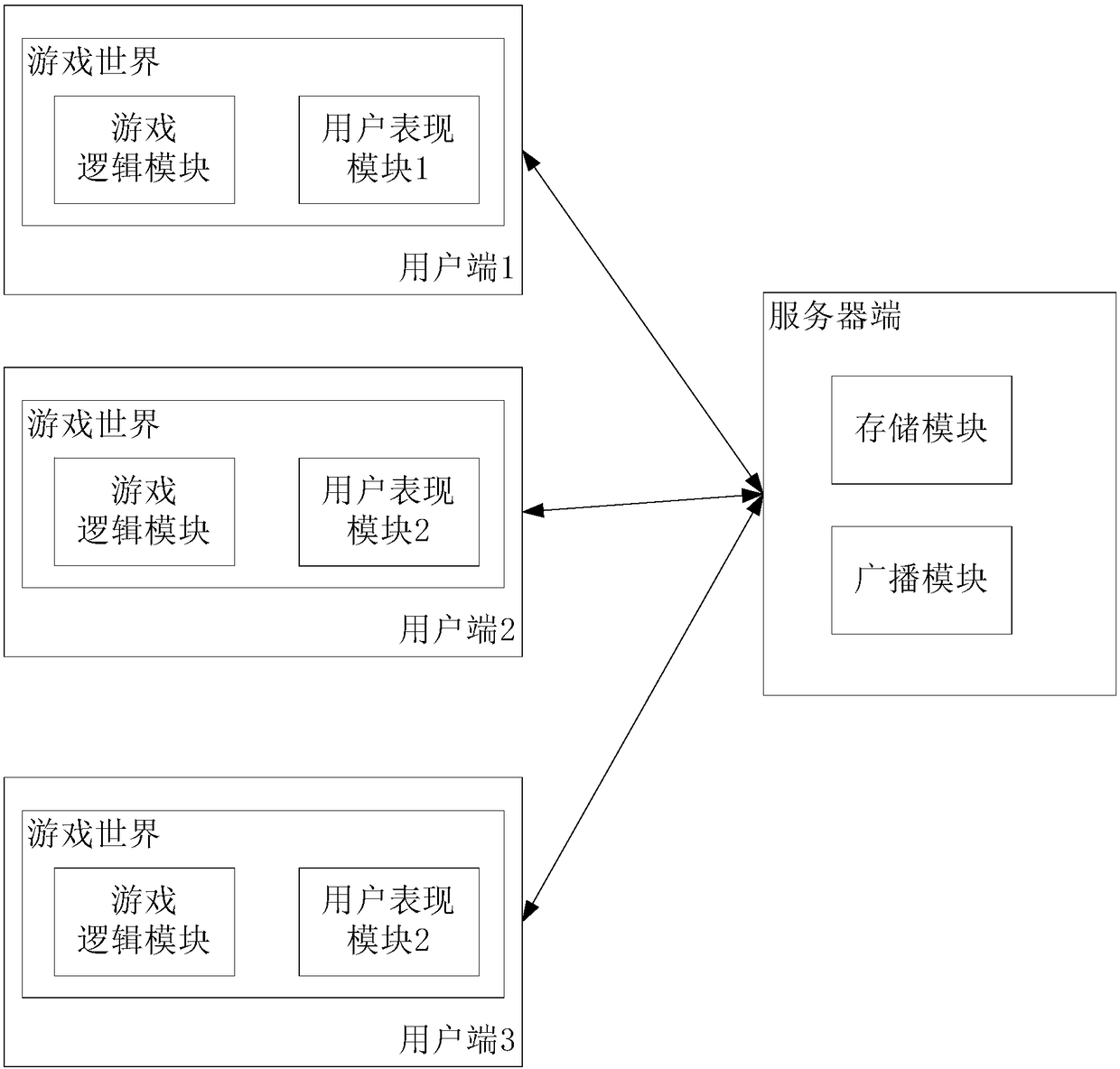
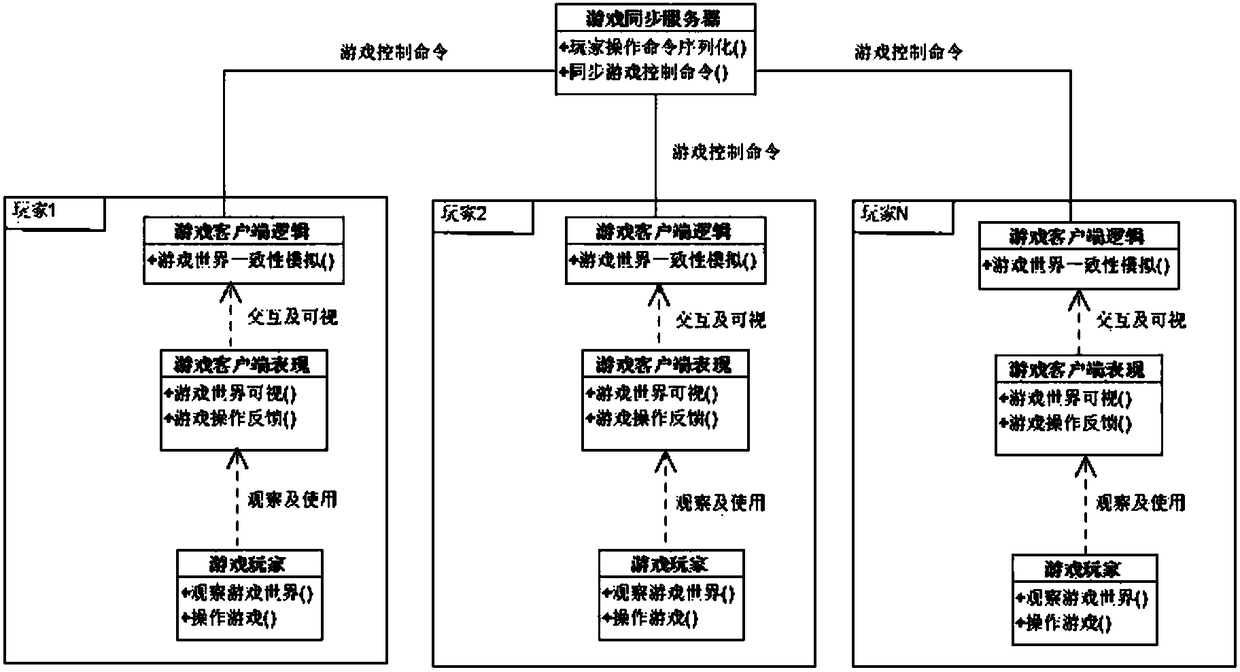
Peer-to-peer computing based game interactive method and system for multi-user scenario
InactiveCN108379833AGreatly load levelAchieve interactionVideo gamesPeer to peer computingHuman–computer interaction
The invention discloses a peer-to-peer computing based game interactive method and system for a multi-user scenario. The peer-to-peer computing based game interactive method comprises the following steps of: uploading a control instruction generated in a user operation process to a server, broadcasting the control instruction through the server, receiving the control instruction of the user whilereceiving data broadcasted by the server through each user side, independently and synchronously operating a complete game world according to the control instruction, thereby realizing interaction andsynchronization among the user sides. A server side of the peer-to-peer computing based game interactive device only store and broadcast game data, and therefore, a peer-to-peer computing technologyprovided by the invention does not bring higher requirements on network and cpu consumption under the multi-user scenario, and can greatly improve user bearing level. Moreover, user experience is realized by a relatively independent user presentation module in each user side. While improving user experience, the peer-to-peer computing based game interactive method reduces requirements on bearing ability of the server, so that cost at the game operation stage is reduced.
Owner:SNAIL GAMES
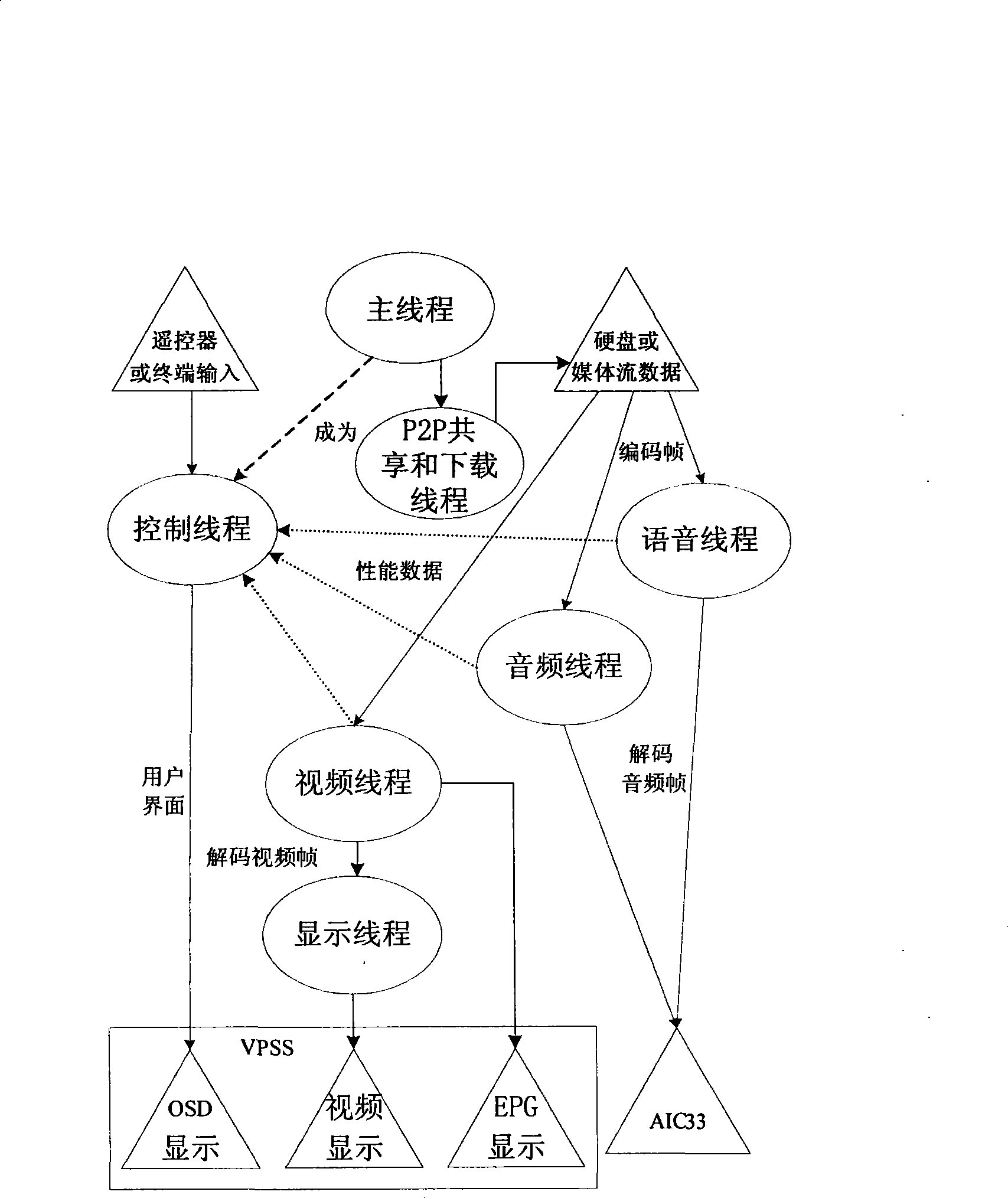
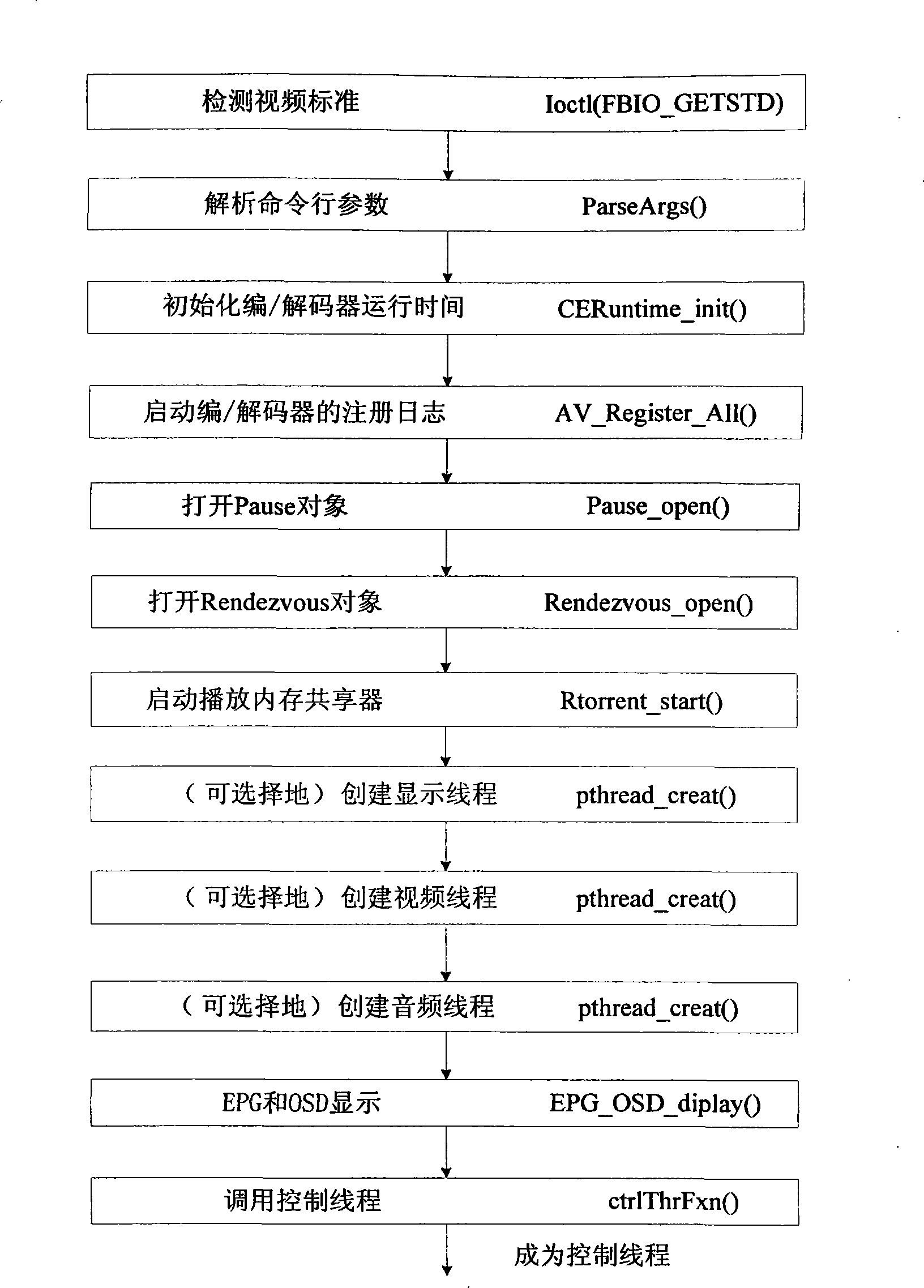
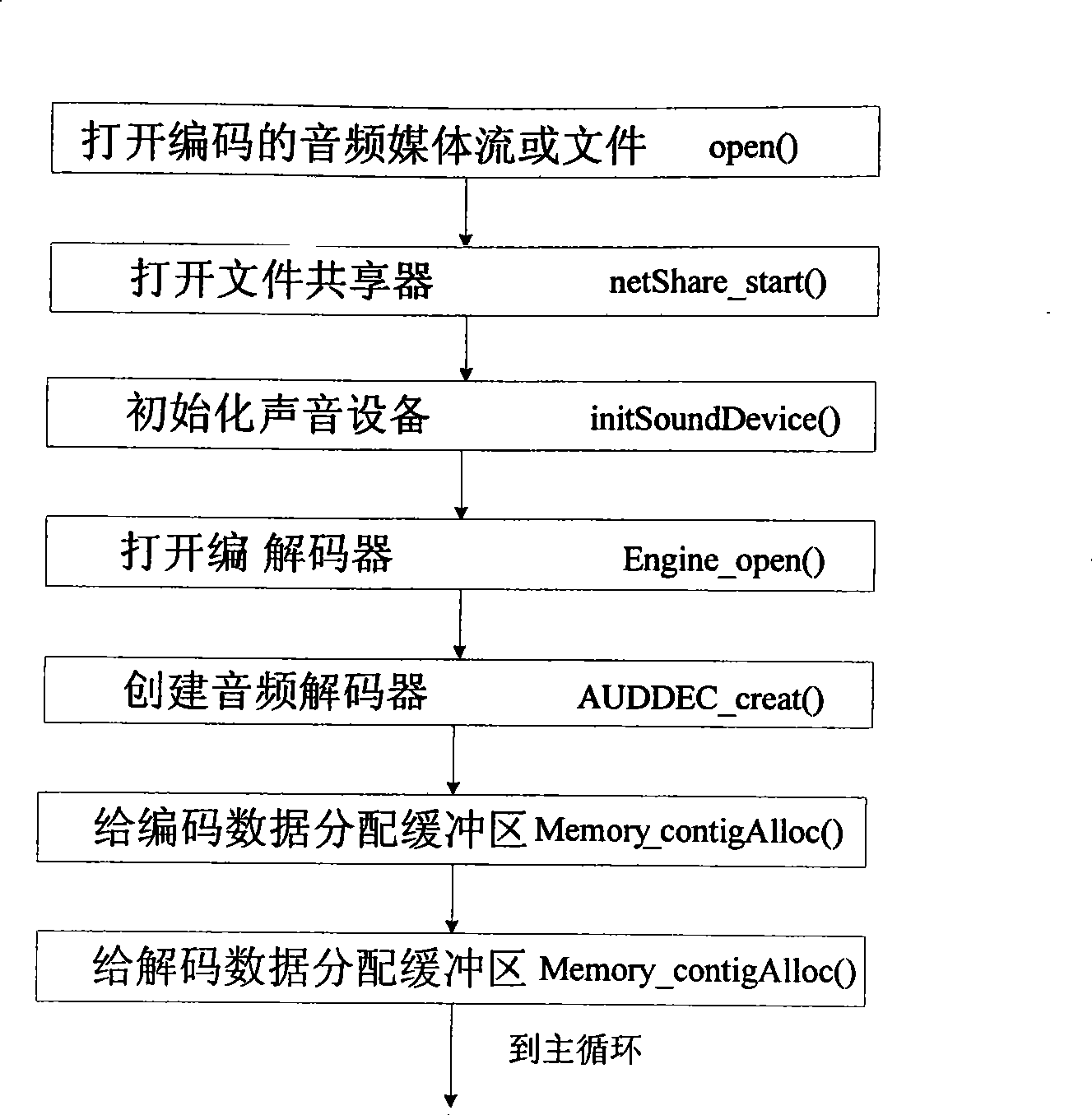
Control method for peer-to-peer calculation set-top box player
InactiveCN101442627AImprove healthImprove reliabilityTelevision system detailsColor television detailsPeer to peer computingRequirements analysis
The invention provides a controlling method used for a player of a peer-to-peer computing set top box, which is used for a player of a P2P (Peer-to-Peer) set top box to play a media file which is not completely downloaded in the P2P set top box, thereby solving the problem of downloading, playing while sharing of the P2P set top box. The realizing method of the player comprises: step 1) analyzing requirement; step 2) designing a module according to the analysis file of the step 1); step 3) designing and realizing a main thread and a control thread of the player according to the file of the step 2); step 4) designing and realizing decoding and playing of an audio file and a video file according to the file of the step 2); step 5) designing and realizing a file loading and sharing module according to the file of the step 2); and step 6) providing functions, namely play, pause, stop, position, fast forward and quick backward, for the player so as to ensure that the player can be automatically positioned to corresponding time to start playing after a user fills the time and presses the enter key.
Owner:NANJING UNIV OF POSTS & TELECOMM
Trust evaluation method in computing environment without central network
InactiveCN101674300AImprove stabilityIncrease success rateTransmissionPeer to peer computingThe Internet
The invention relates to a trust evaluation method used in grid computing, peer-to-peer computing, cloud computing, or other open computing environments which are oriented to China and based on the Internet and do not have central networks. The method is designed in order to promote the honest and reliable interaction of every node and has distinguishing Chinese characteristics. In view of the thinking model, the subjective desire and the way of action of Chinese people, the invention designs the trust evaluation method for network nodes so as to effectively enhance the system safety stabilityand the coordination success ratio in the computing environment without a central network in China. The trust evaluation model fully considers the identifications of the nodes, the relationship amongthe nodes, the direct interaction experiences and the objective comprehensive evaluation conditions, and also considers the dynamic changes of the node trust conditions. Due to strong pertinency, popularization capacity and feasibility, the scheme has favorable reference value and practical value.
Owner:NANJING UNIV OF POSTS & TELECOMM
Peer-to-peer computing system
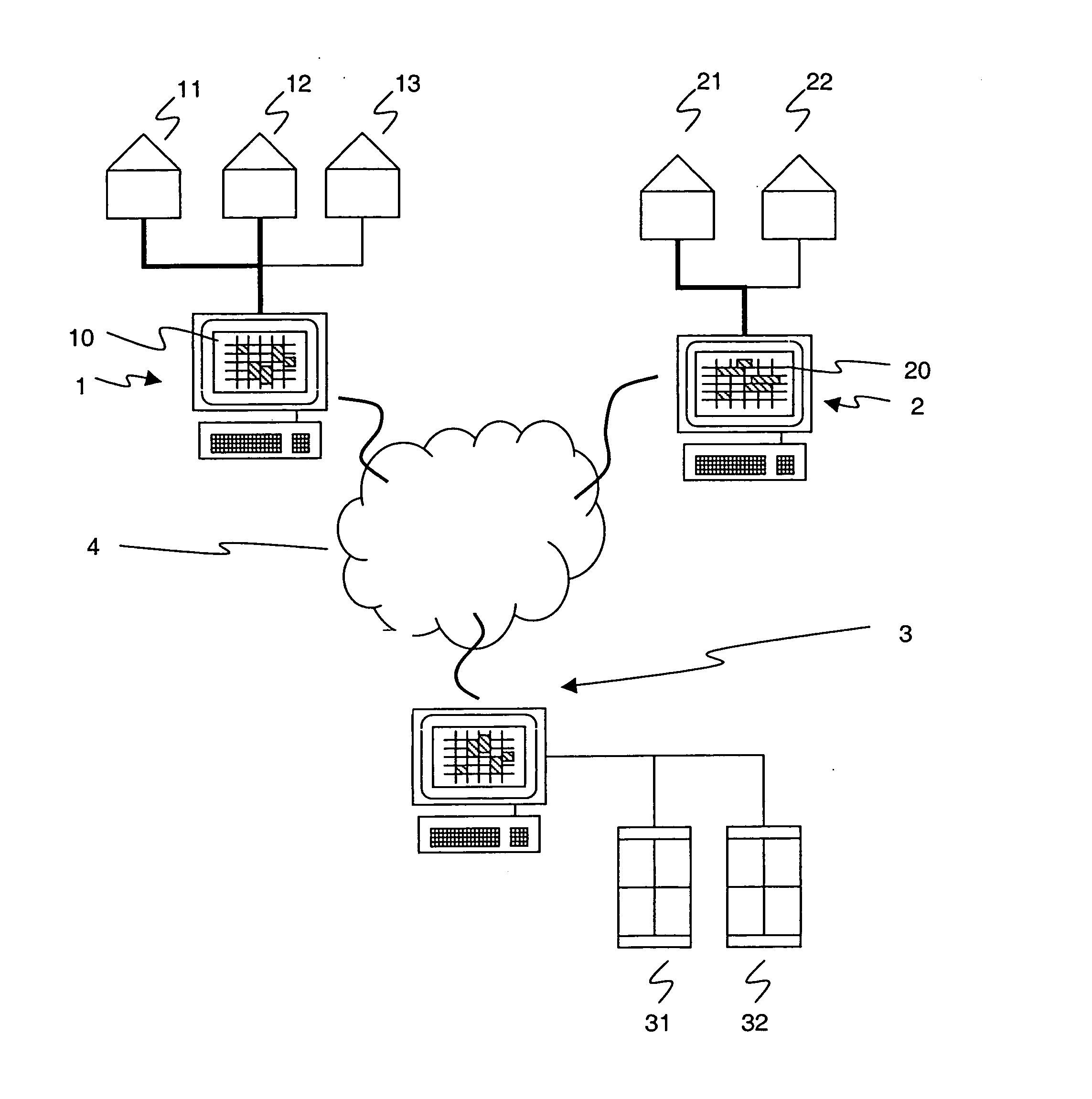
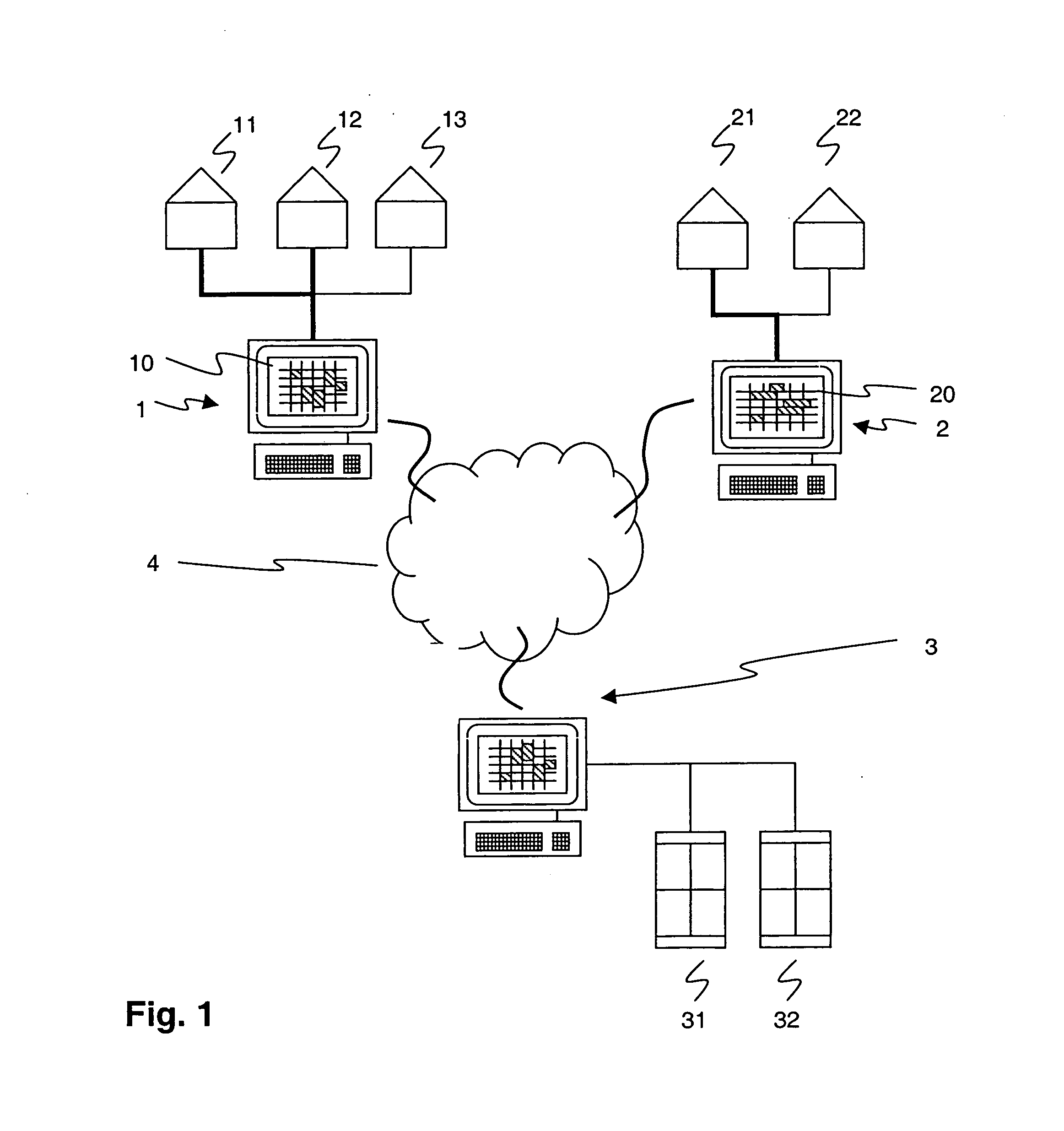
InactiveUS20050033640A1Reduce office spaceReduce spacingBuying/selling/leasing transactionsSpecial data processing applicationsOccupancy ratePeer to peer computing
The present invention is concerned with the utilisation of tangible assets (11), and in particular with an optimization of the occupancy rate of rooms dedicated to a single purpose such as conference rooms. In order to facilitate usage of the conference room during low periods by potential co-users, the peer-to-peer sharing approach known for digital or intangible assets is adapted. The tangible asset (11) is advertised over a peer-to-peer network, and peers (2) other than the peer (1) associated with the asset-owner are enabled to make a reservation for a forthcoming use of the tangible asset (11) via a reservation or booking facility (10).
Owner:ABB TECH FLB
Peer-to-peer based content delivery in a virtual universe
ActiveUS20100306675A1Input/output for user-computer interactionVideo gamesPeer to peer computingVirtual world
The present invention permits performance adjustment in a virtual universe. In particular, the invention proposes a mixed server-based / peer-to-peer approach, in which transmission responsibilities are shifted towards peer-to-peer computing as the number of avatars within a region increases. The invention may foster fluid business transactions (e.g., sales) during times of high avatar load.
Owner:KYNDRYL INC
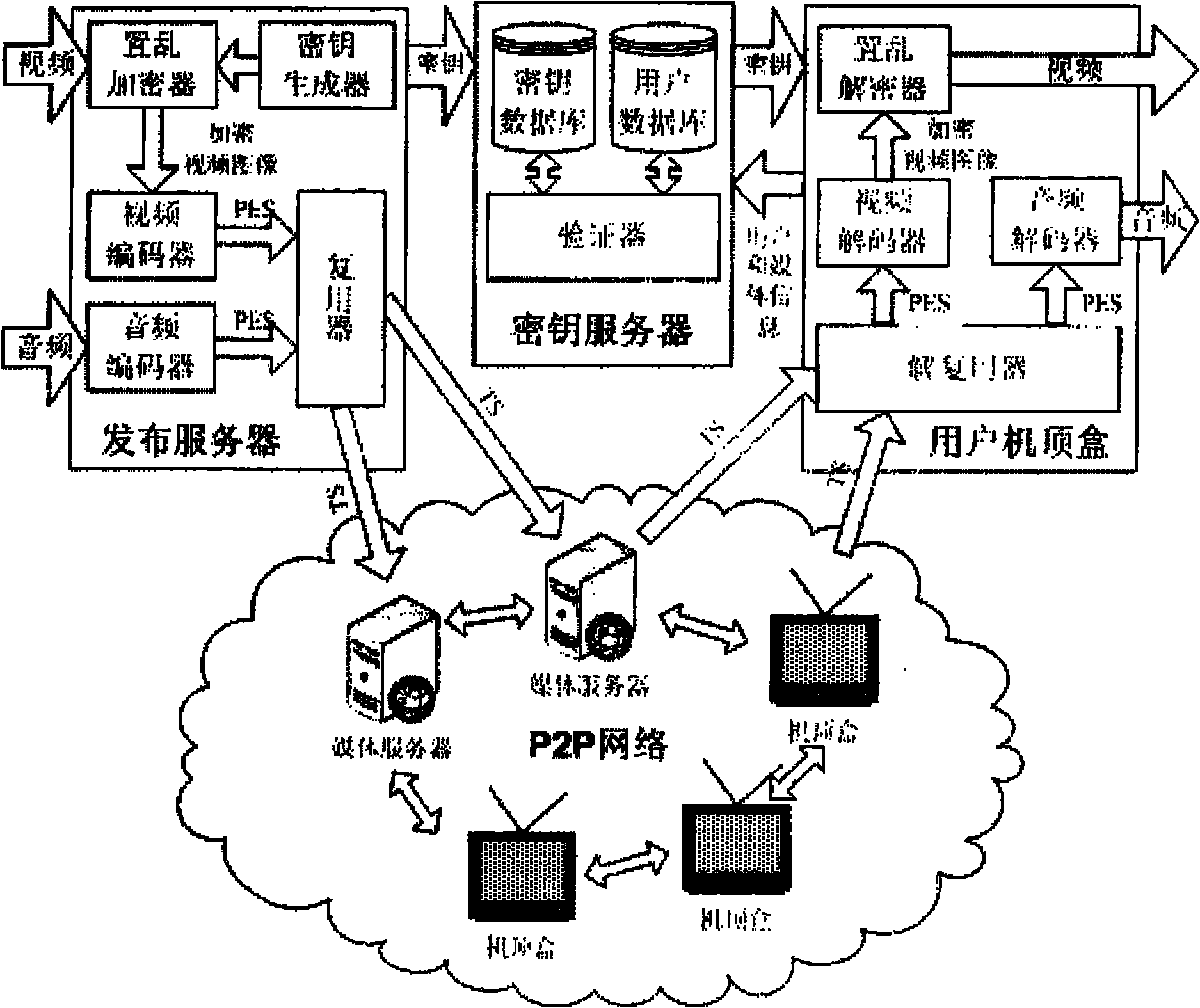
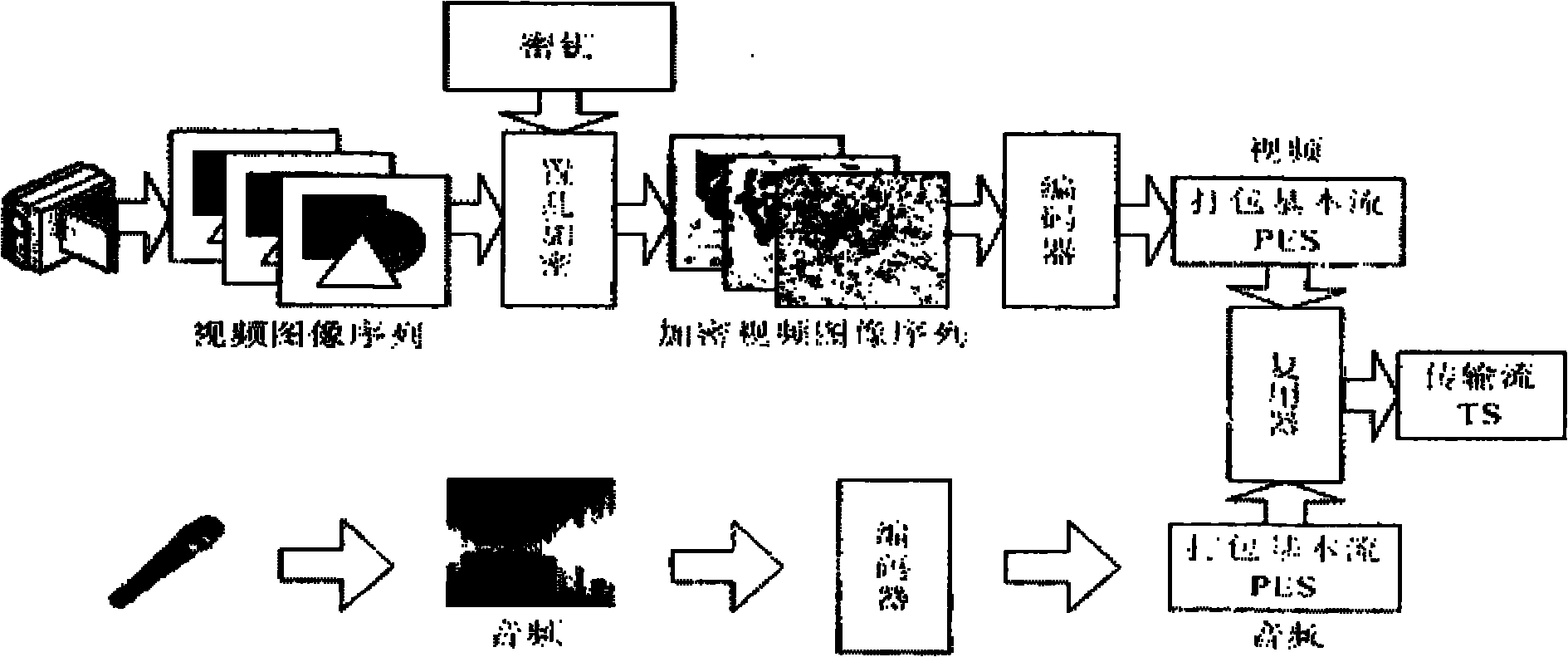
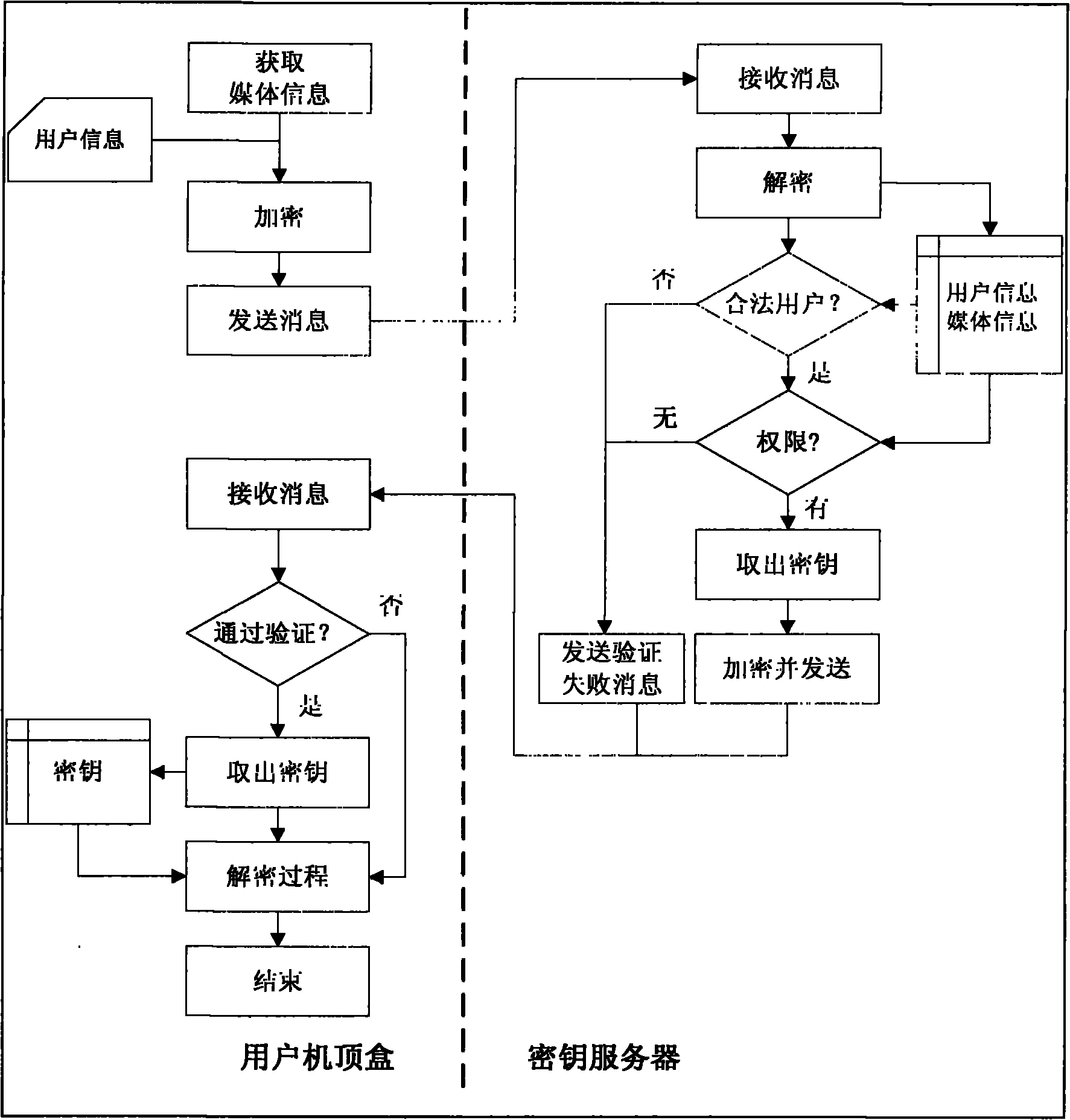
Method for security protection of video data of set top box for peer-to-peer computing
InactiveCN101783925AImprove adaptabilityStrong scalabilityTelevision system detailsAnalogue secracy/subscription systemsTelevision systemExtensibility
The invention relates to a method for security protection of video data of a set top box for peer-to-peer computing, which is a technical method for security protection of video data of a P2P IPTV system. On the basis of the P2P IPTV system, a digital image scrambling encryption technology is introduced, and a single key server is designed, thereby achieving the purpose of security protection of video data in the P2P IPTV system. The invention solves the security problem caused by that the P2P IPTV system uses a P2P network for transmitting video data. The method expands the P2P IPTV system on the basis that the original framework of the P2P IPTV system is not changed, designs an encryption algorithm and generation, management, transmission and use of keys, has the advantages of innovation, security, expandability and practicability, and has good application prospects and market value.
Owner:NANJING UNIV OF POSTS & TELECOMM
Method for evaluating and authorizing peer-to-peer network node by certificate
InactiveCN101335618BReduce direct interactionImprove securityPublic key for secure communicationUser identity/authority verificationAuthorization certificateTimestamp
Owner:NANJING UNIV OF POSTS & TELECOMM
Method and apparatus for segmented peer-to-peer computing
InactiveCN1526109AMultiple digital computer combinationsDigital data authenticationData processing systemPeer to peer computing
A method, apparatus, and computer implemented instructions for managing processing of data in data processing system within a peer-to-peer network data processing system. A request is received from a requester. Preferences are compared within the request to control information to form a comparison, in which the control information dictates responses by the data processing system. The request is selectively responded to based on comparison.
Owner:IBM CORP
Real-time video monitoring system implementing method based on network television set-top box
InactiveCN101505365BAdjustable definitionLower latencyClosed circuit television systemsSelective content distributionDual coreOperability
The invention relates to a method for achieving a real-time video monitoring system based on an internet protocol television top-set box, which is a method for achieving the function of real-time video monitoring on the internet protocol television (IPTV) top-set box. Based on an added-value extended function provided by an IPTV peer-to-peer computing top-set box developed on a dual-core development platform TMS320DM6446 (Vinci digital platform), the invention provides the method for achieving the real-time video monitoring system based on the internet protocol television top-set box for achieving a household real-time video monitoring system on the IPTV top-set box developed on the basis of the DM6446 platform so as to solve the problems of the read-write operations driven by a video capture device, the call of a DSP MPEG-4 coding interface, the transmission and the control of a RTP (Real-time Transport Protocol) data pack, the achievement of MPEG-4 decoding, and the multimedia interface display based on SDL. The proposal has the advantages of novelty, flexibility, easy expansibility, easy operability, low cost and the like.
Owner:NANJING UNIV OF POSTS & TELECOMM
Authentication system and method based on peer-to-peer computing network
InactiveCN101714996BSolve the problem of single point of failureImprove resource utilizationTransmissionResource utilizationPeer to peer computing
The invention discloses authentication system and method based on a peer-to-peer computing network. The authentication system comprises a super node, and the super node is used for receiving an authentication request of a user node and authenticating a user which corresponds to the user node according to locally stored authentication information. The invention achieves the effect of enhancing resource utilization rate.
Owner:ZTE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com