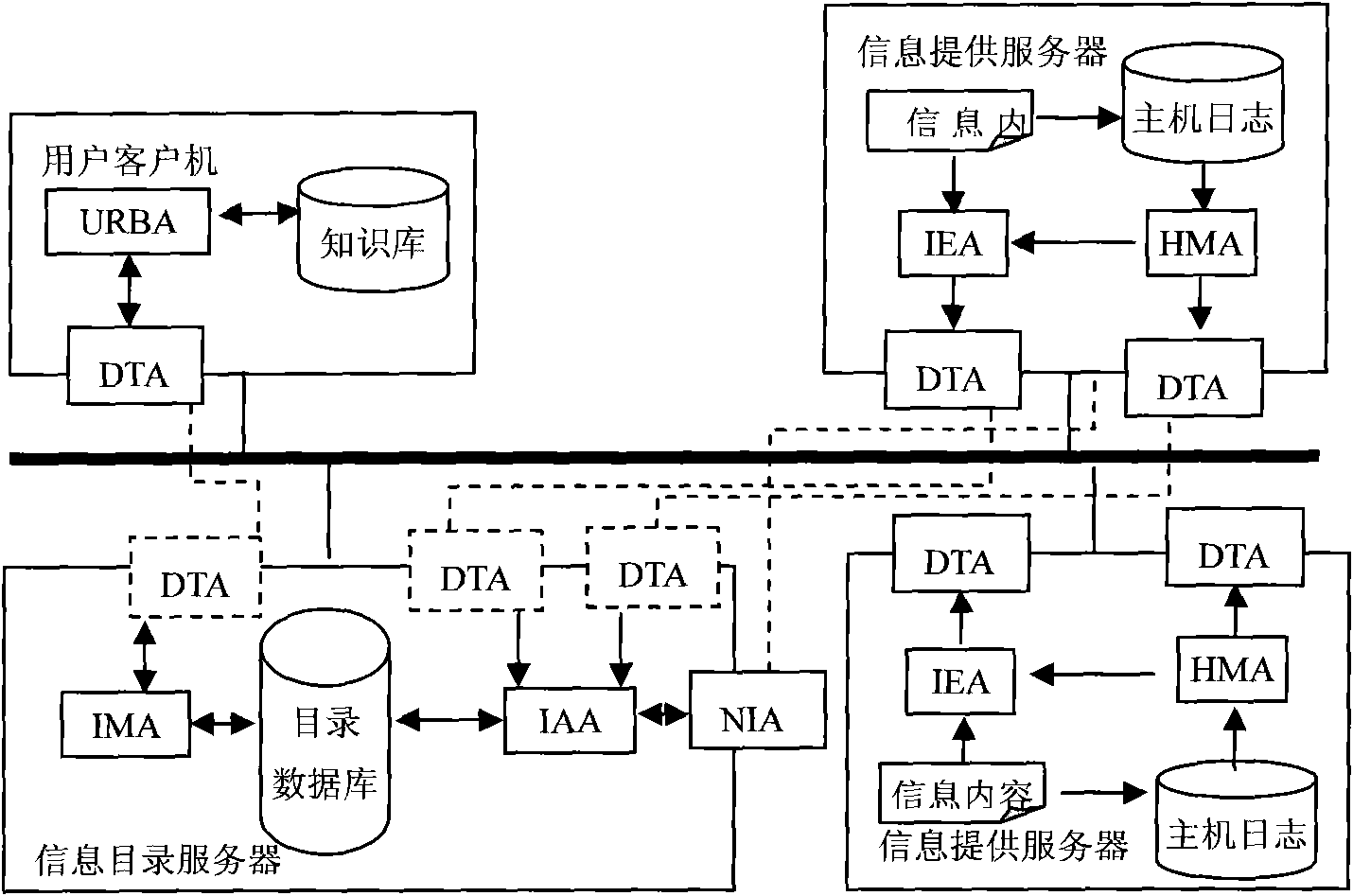
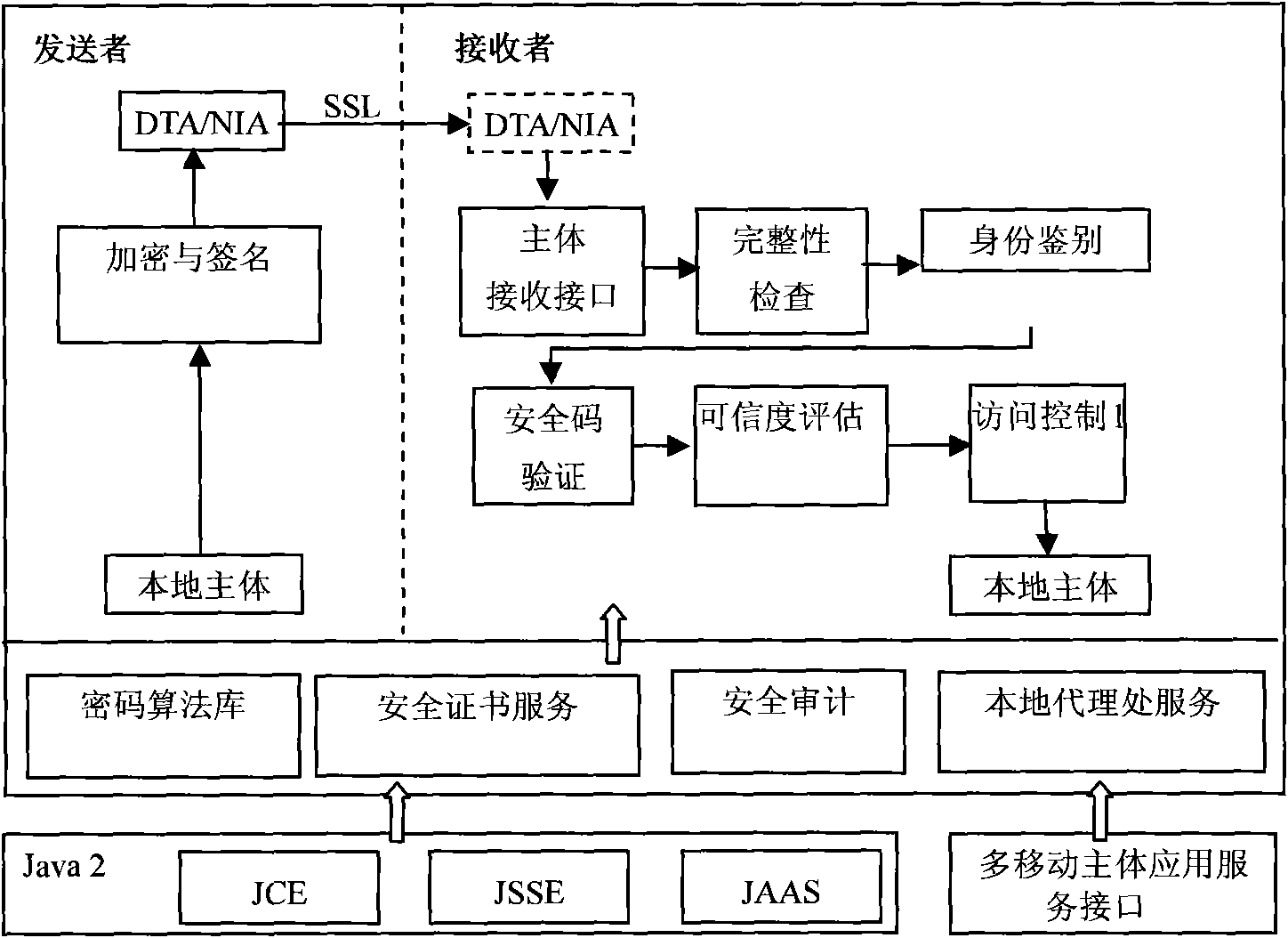
Multiple-mobile-agent credible interaction method for information acquisition system in open network
A technology of mobile subject and interaction method, applied in the field of trusted interaction, to achieve the effect of ensuring effectiveness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
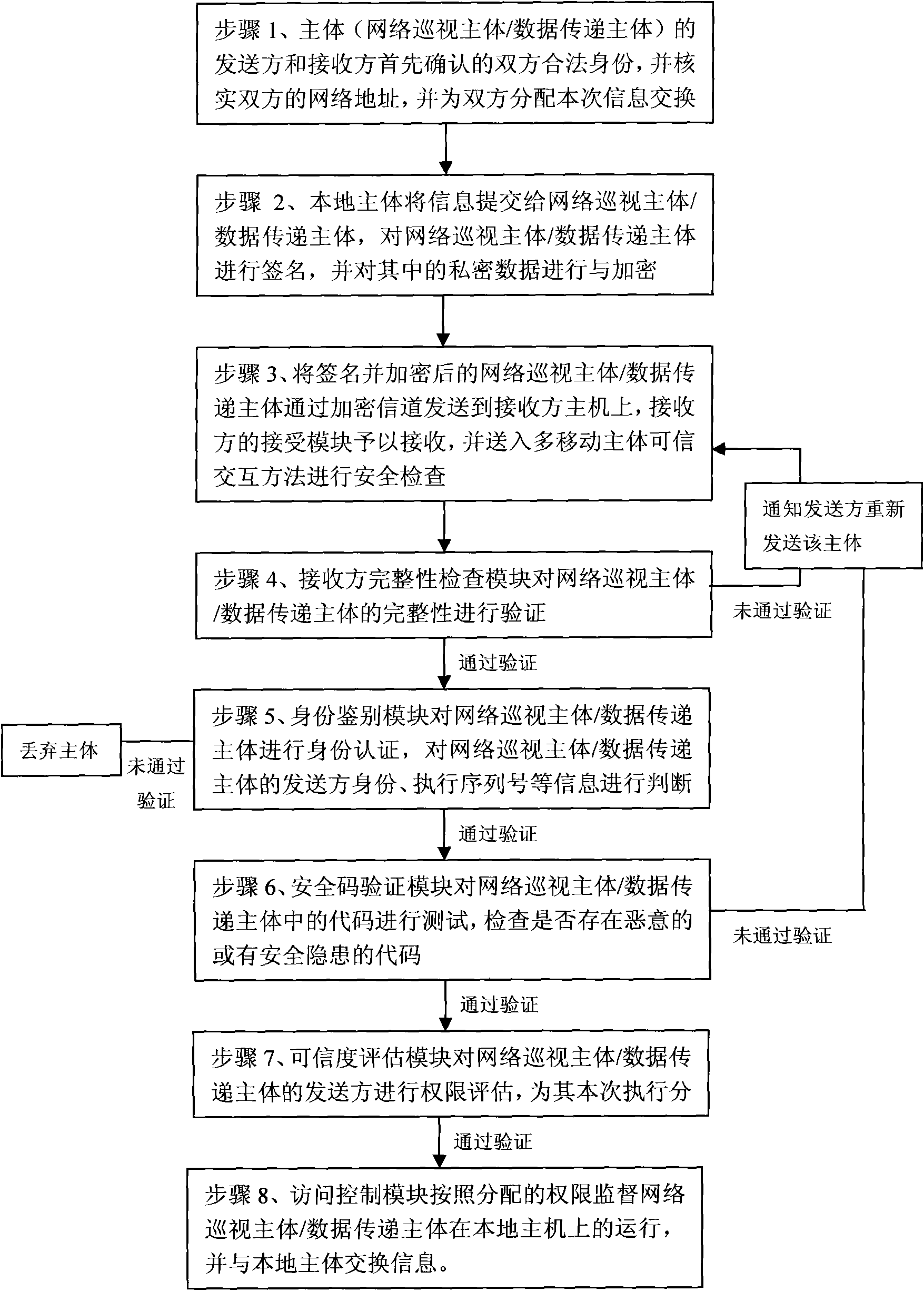
[0056] The flow of the multi-mobile subject trusted interaction method is as follows:
[0057] Step 1. The sender and receiver of the subject first confirm the legal identities of both parties, verify the network addresses of both parties, and assign the execution sequence number of this information exchange to both parties;
[0058] Step 2. The local subject submits the information to the network patrol subject / data transfer subject, signs the network patrol subject / data transfer subject, and encrypts the private data therein;
[0059] Step 3. Send the signed and encrypted network inspection subject / data transfer subject to the receiver host through an encrypted channel based on the secure socket layer, and the receiving module of the receiver receives it and sends it to the multi-mobile subject trusted interaction method for further processing. Security check;
[0060] Step 4. The receiver integrity checking module verifies the integrity of the network inspection subject / da...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com