Method for evaluating and authorizing peer-to-peer network node by certificate
A network node and certificate technology, applied in the direction of user identity/authority verification, public key of secure communication, electrical components, etc., can solve the problems of complex evaluation algorithm, affecting authorization security, incomplete acquisition of historical interaction experience, etc. The effect of improving security and reducing storage space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
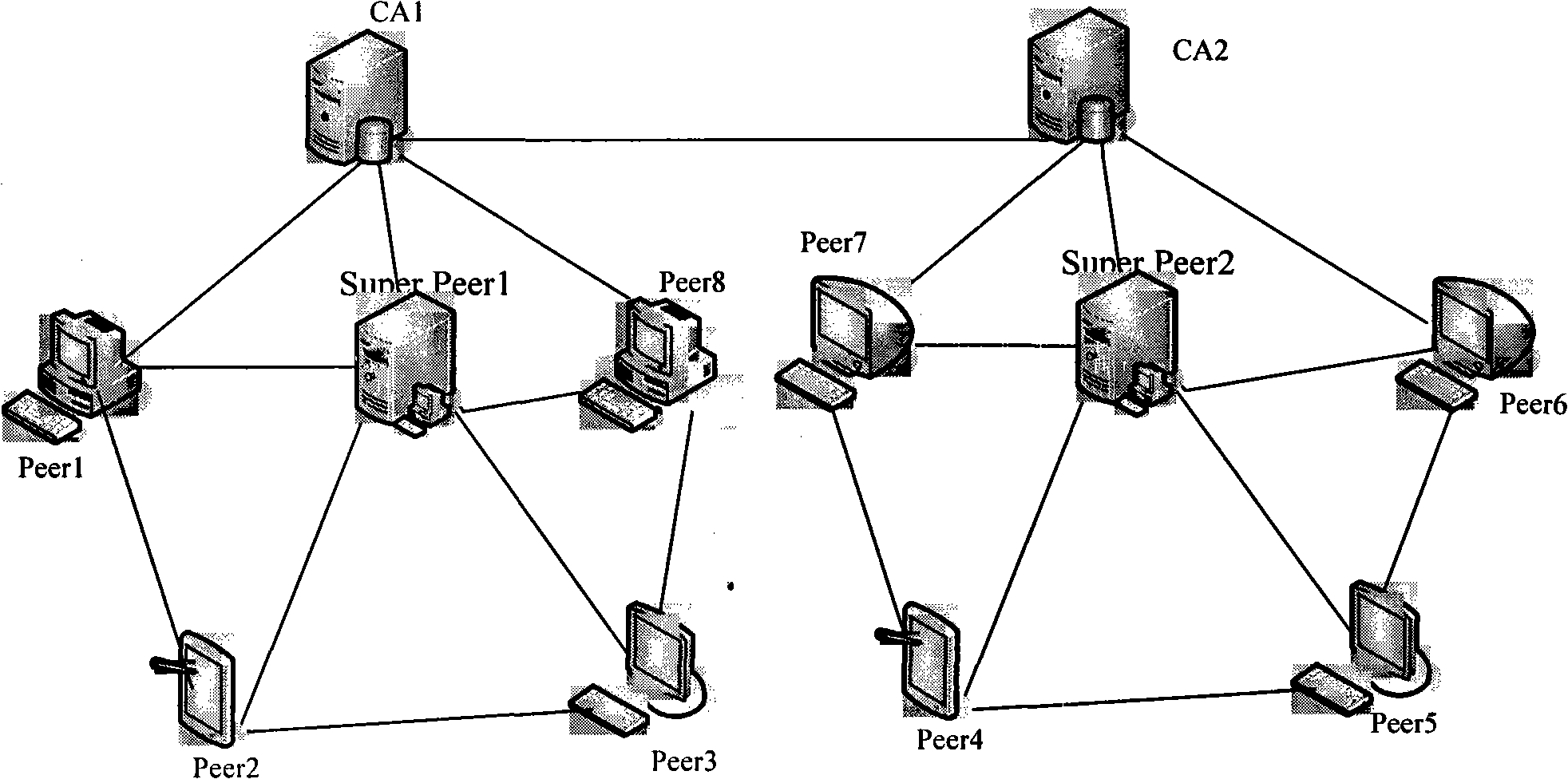
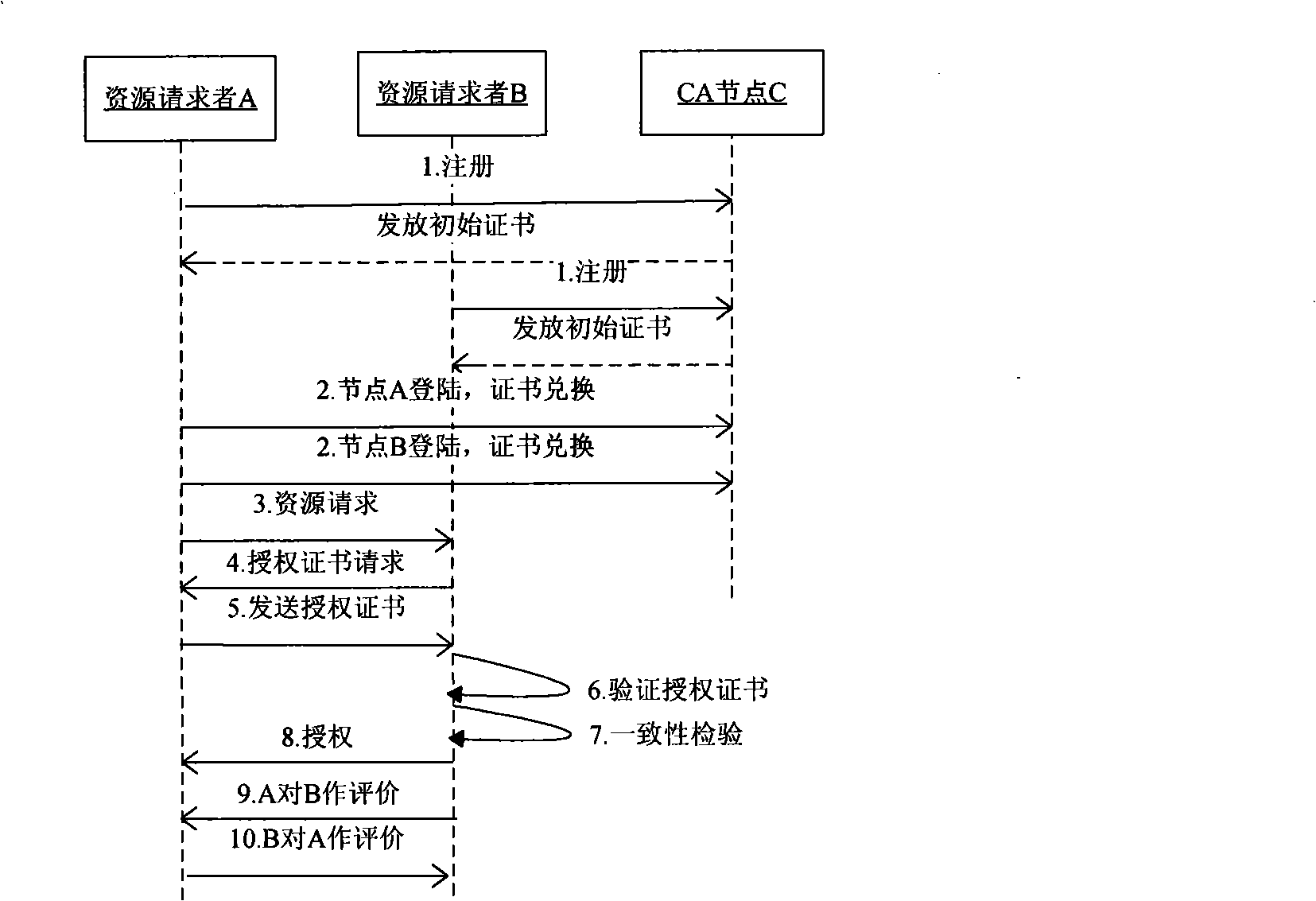
[0037] The method of using certificates to evaluate and authorize peer-to-peer network nodes is that resource providers make authorization decisions based on the level of authorization certificates held by nodes and the level of resources requested by resource requesters; After the end, directly use the evaluation certificate to evaluate the performance of the other party; when the node logs in next time, first exchange the obtained evaluation certificate and the remaining authorization certificate to the super node where it is located, and obtain a new certificate time stamp. transactions; details are as follows:
[0038] Step 1. Node registration, obtain initial evaluation certificate and authority certificate
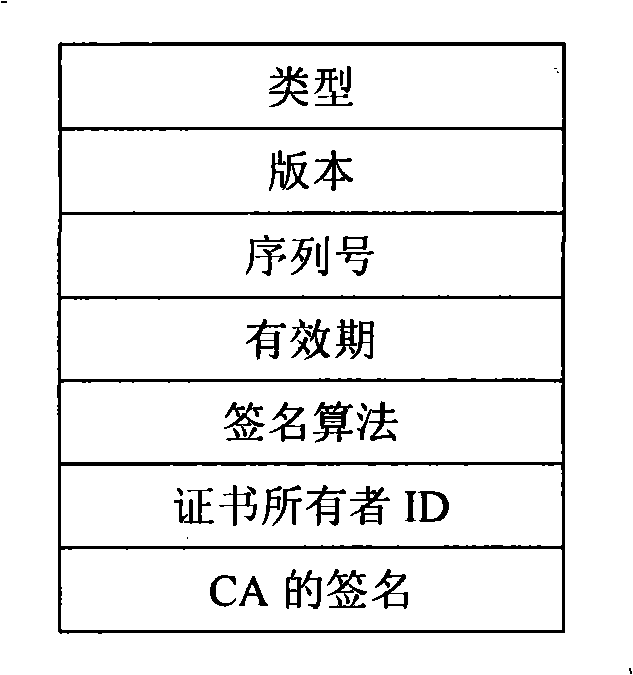
[0039] Nodes A and B select CA to send a registration request, and the CA node judges whether node A and node B have passed the registration according to the joining requirements of the system. For registered nodes, assign node IDs and assign initial authority certi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com