Data transmission method and data transmission system
A data transmission method and technology of transmission control protocol, which are applied in transmission systems, electrical components, public keys for secure communication, etc., can solve the problems of lack of security, high complexity, and insufficient data privacy protection in communication protocols. The effect of avoiding remote control flooding, enhancing security, and reducing complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
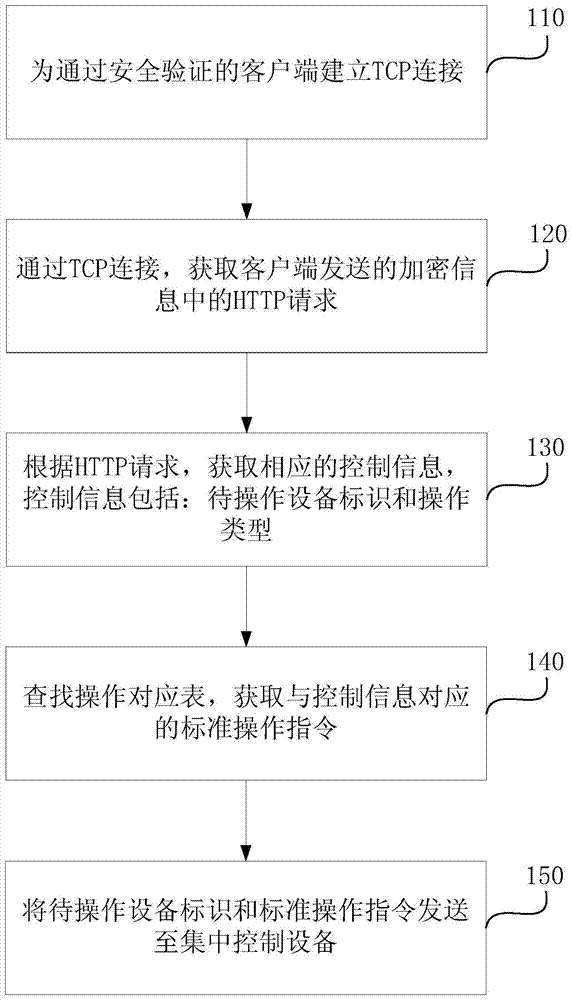
[0053] figure 1 It is a flow chart of a data transmission method in the first embodiment of the present invention. The method in this embodiment can be executed by a data transmission system. The system can include a server, a centralized control device, and at least two receiving devices, and is installed in a mobile Client interaction within the terminal. The method of this embodiment is specifically executed by the server, including the following steps:
[0054]Step 110, establishing a TCP (Transmission Control Protocol, Transmission Control Protocol) connection for the client that has passed the security verification.
[0055] In this embodiment, the user of the smart home system can use the client (for example: smart home control software) installed in the mobile terminal (for example: smart phone, tablet computer, etc.) Send corresponding control commands. When the server detects the client's access request, it will establish a TCP connection for the client that has p...
no. 2 example
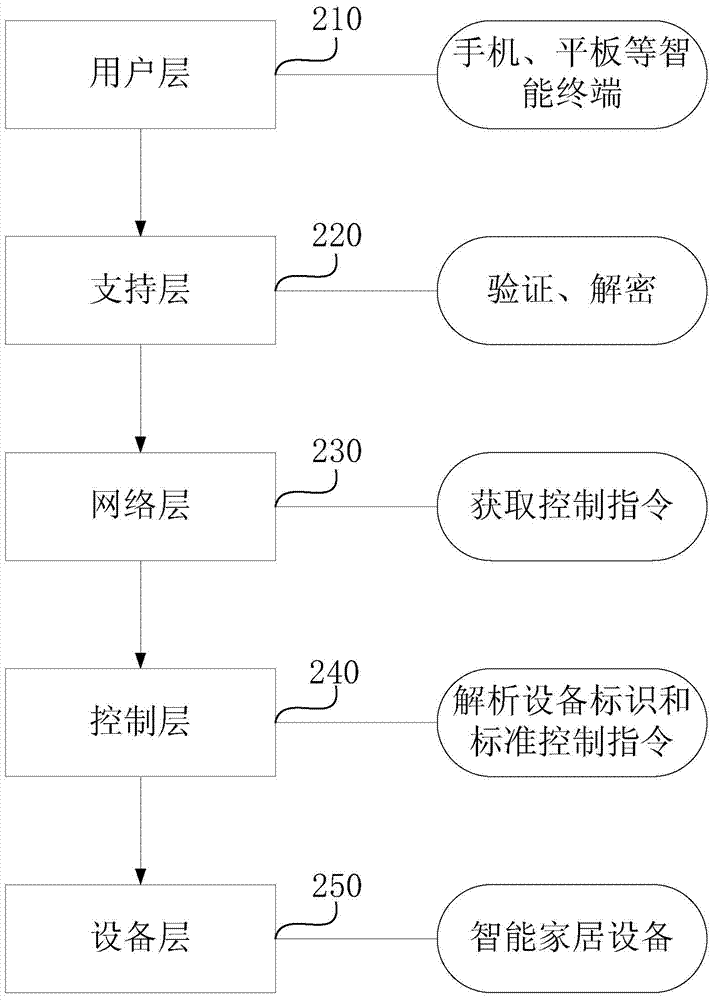
[0097] exist figure 2 shows a system architecture diagram of a data transmission process in the second embodiment of the present invention. This embodiment is based on the above-mentioned embodiments, and implements the data transmission methods in the above-mentioned embodiments in a logical layered manner. . Such as figure 2 As shown, the system includes: a user layer 210 , a support layer 220 , a network layer 230 , a control layer 240 and a device layer 250 . The user layer 210 is responsible for sending control instructions in the form of application layer HTTP requests, the support layer 220 is responsible for verifying the authority of the instructions, decrypting them, and submitting them to the network layer 230, and the network layer 230 is responsible for obtaining the device identification and standard operating instructions in the control instructions. It is submitted to the control layer 240, and finally the control layer 240 completes the direct control of t...
no. 3 example
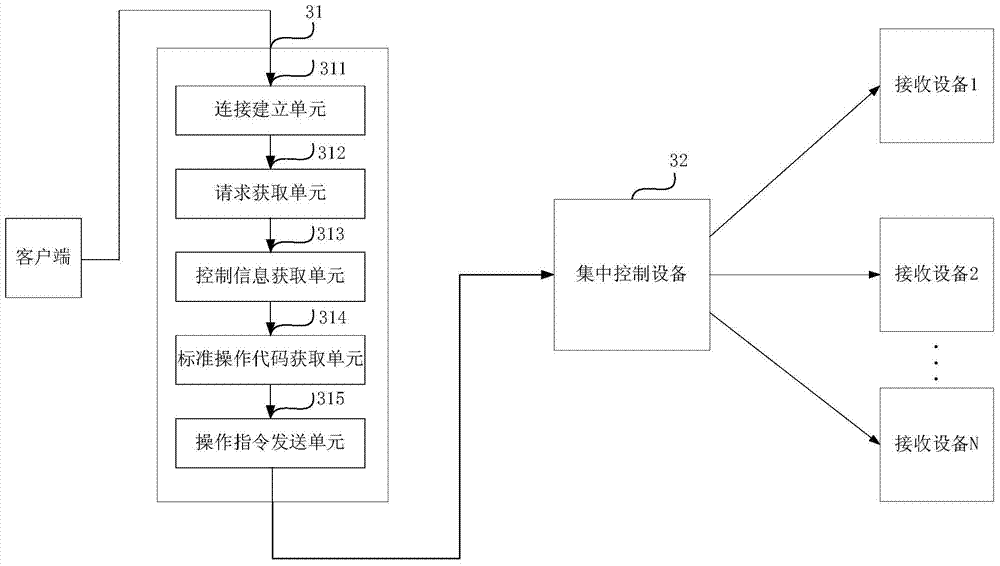
[0100] exist image 3 A structural diagram of a data transmission system according to the third embodiment of the present invention is shown in . Such as image 3 As shown, the system includes:
[0101] A server 31, a centralized control device 32 and at least two receiving devices, the server 31 is connected to the centralized control device 32, and the centralized control device is connected to at least two receiving devices respectively, wherein:
[0102] Server 31 includes:
[0103] A connection establishment unit 311, configured to establish a TCP connection for a client that has passed security verification;
[0104] A request obtaining unit 312, configured to obtain the HTTP request in the encrypted information sent by the client through the TCP connection;
[0105] A control information obtaining unit 313, configured to obtain corresponding control information according to the HTTP request, wherein the control information includes the identification of the device t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com