Method for security protection of video data of set top box for peer-to-peer computing
A technology for security protection and video data, which is applied in the direction of TV, color TV, color TV parts, etc., to achieve the effect of good security, improved concealment and high security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
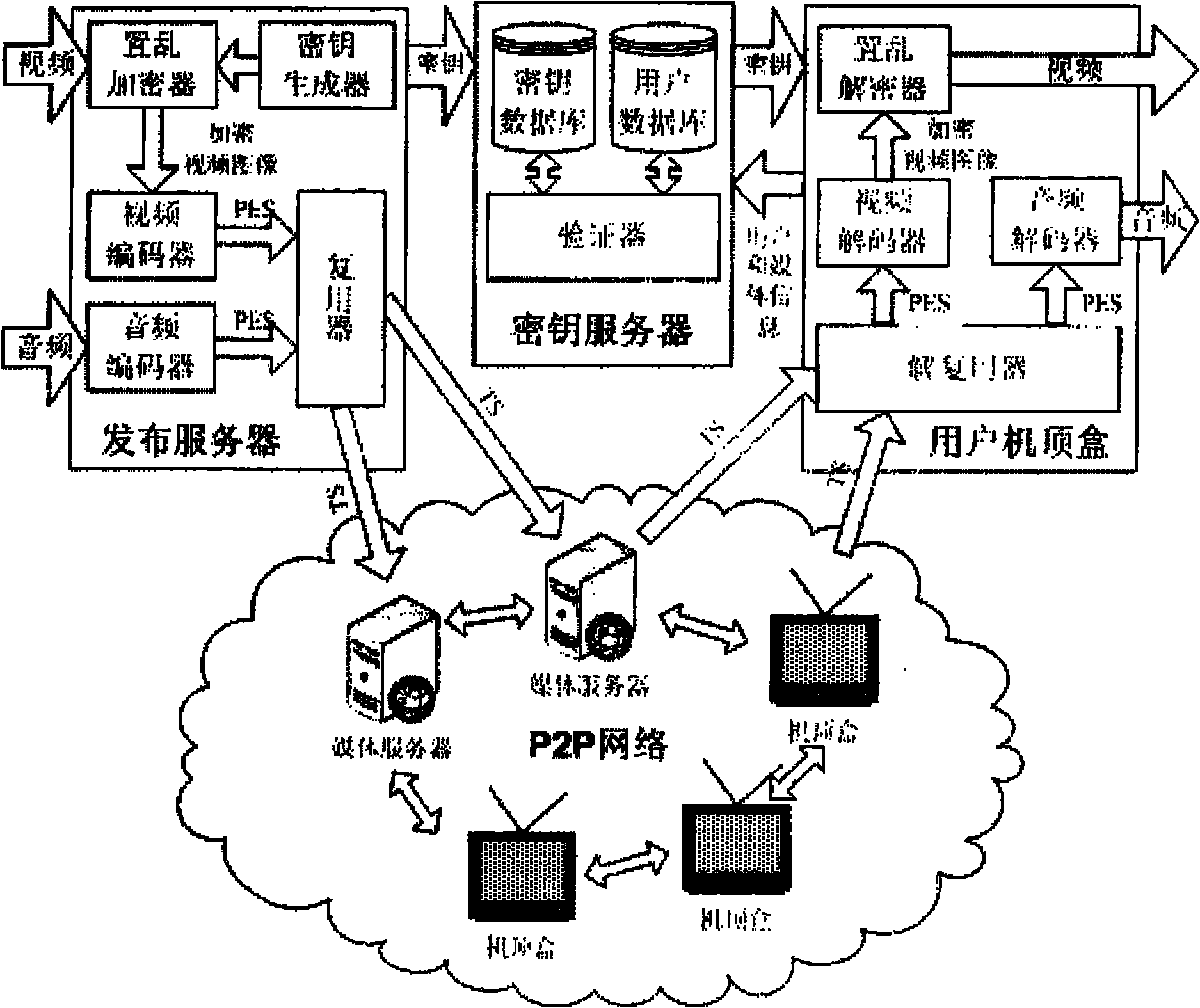
[0035] 1. Architecture
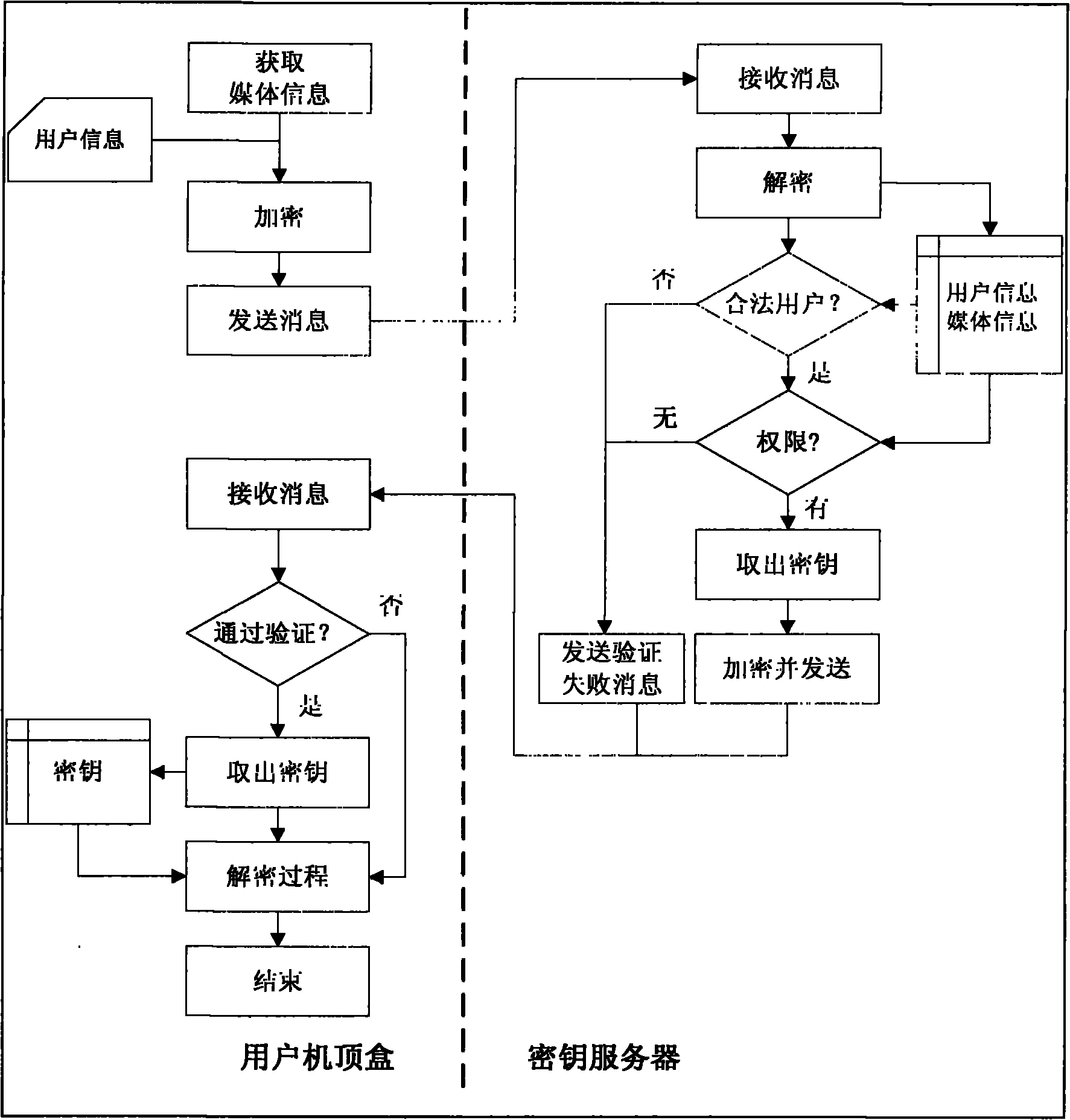
[0036] This solution is mainly divided into four parts: publishing server, media server, key server and user set-top box. The specific architecture is as follows: figure 1 .
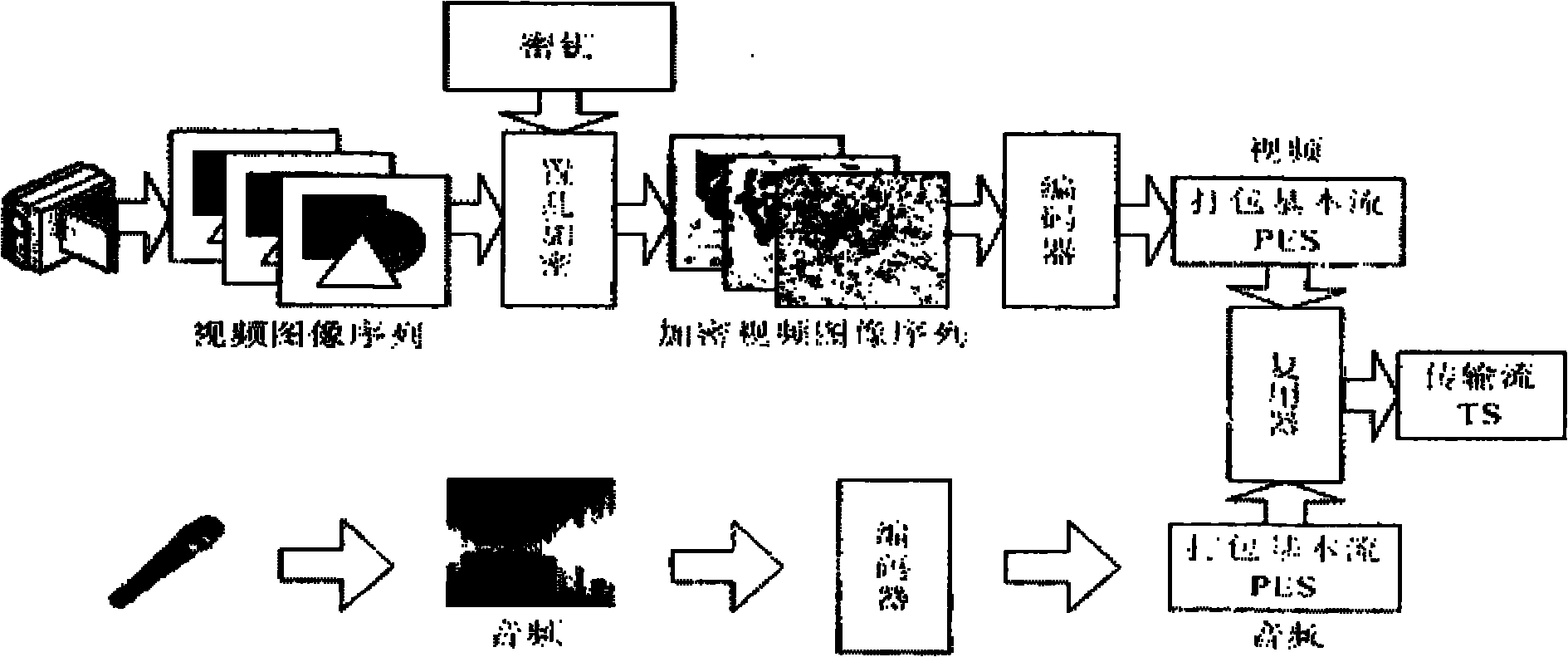
[0037] Publisher contains scrambler, key generator, video encoder, audio encoder and multiplexer. The original video can be regarded as an image sequence of 25 frames per second, that is, 25 images per second. The scrambling encryptor is an image encryptor that encrypts 25 images per second. A key generator generates keys for scrambling encryption and decryption. Since the encrypted video image is very large and cannot be transmitted on the network, a video encoder is used, which uses the great correlation and redundancy between video images to compress the video image, and forms a packaged basic image after compression. Stream (PES, Program Elementary Stream) file. The original audio data is also very large and is not suitable for transmission on the network. It must be com...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com