A virtual machine security migration system
A technology for migrating systems and virtual machines, applied in the field of virtual machine security migration systems, can solve problems such as active control attacks, less research on security issues, security threats, etc., and achieve the effect of ensuring atomicity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0041] Existing virtual machine migration systems do not have platform certification for virtual machine migration, and cannot guarantee that the state of the source platform and target platform of virtual machine migration is safe and credible. At the same time, it lacks data transmission protection and cannot handle threats such as man-in-the-middle attacks during virtual machine migration.
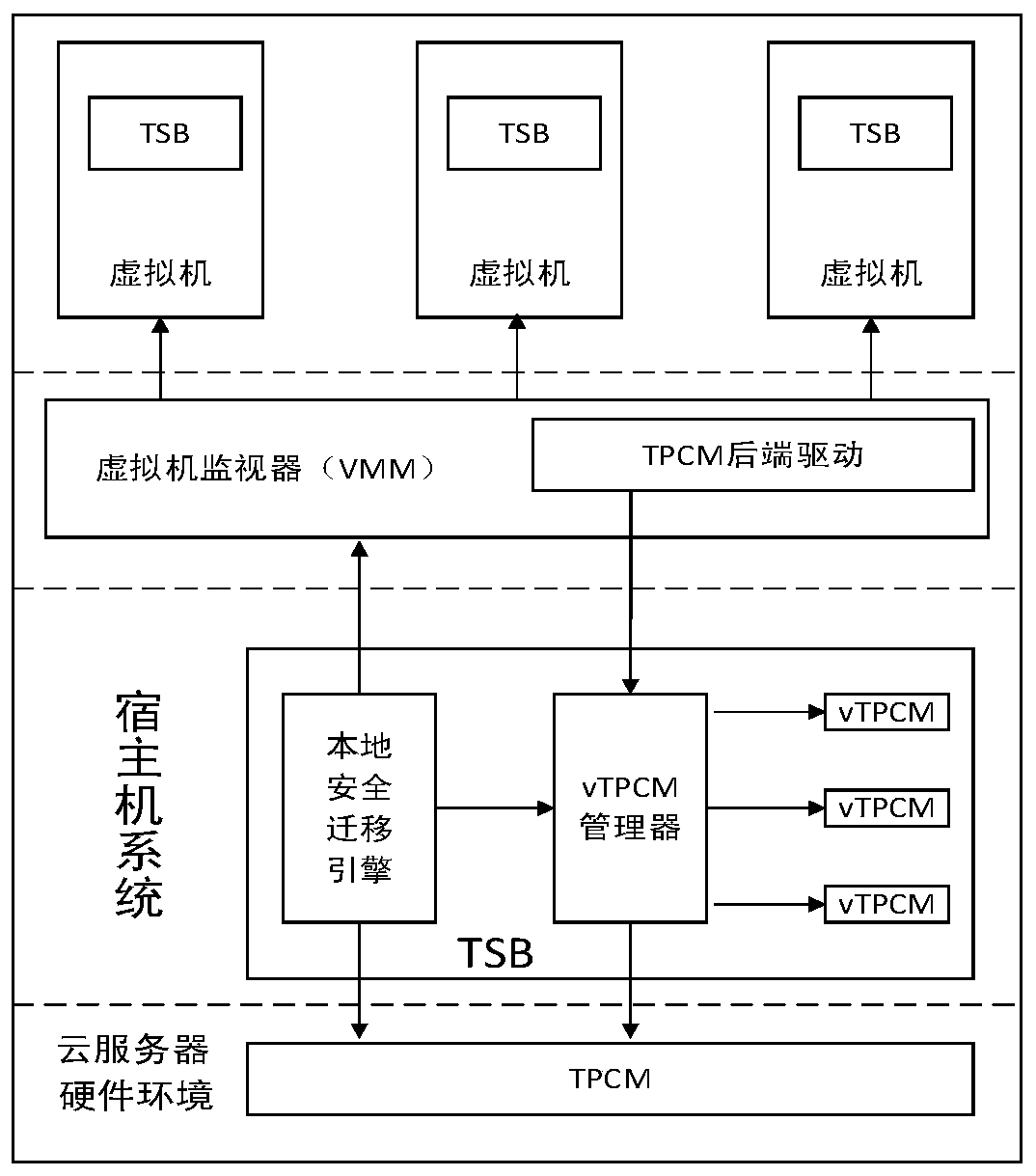
[0042] Aiming at the defects existing in the existing virtual machine migration system, this embodiment discloses a virtual machine security migration system, the system frame diagram is as follows figure 2 As shown, including the cloud server hardware environment, host system, virtual machine monitor and virtual machine instance:
[0043] Among them, the hardware TPCM chip in the underlying hardware environment provides the system with trusted computing cryptographic services, and the TPCM and the host system form a dual-system architecture proposed by Trust 3.0, which provides active...
Embodiment 2
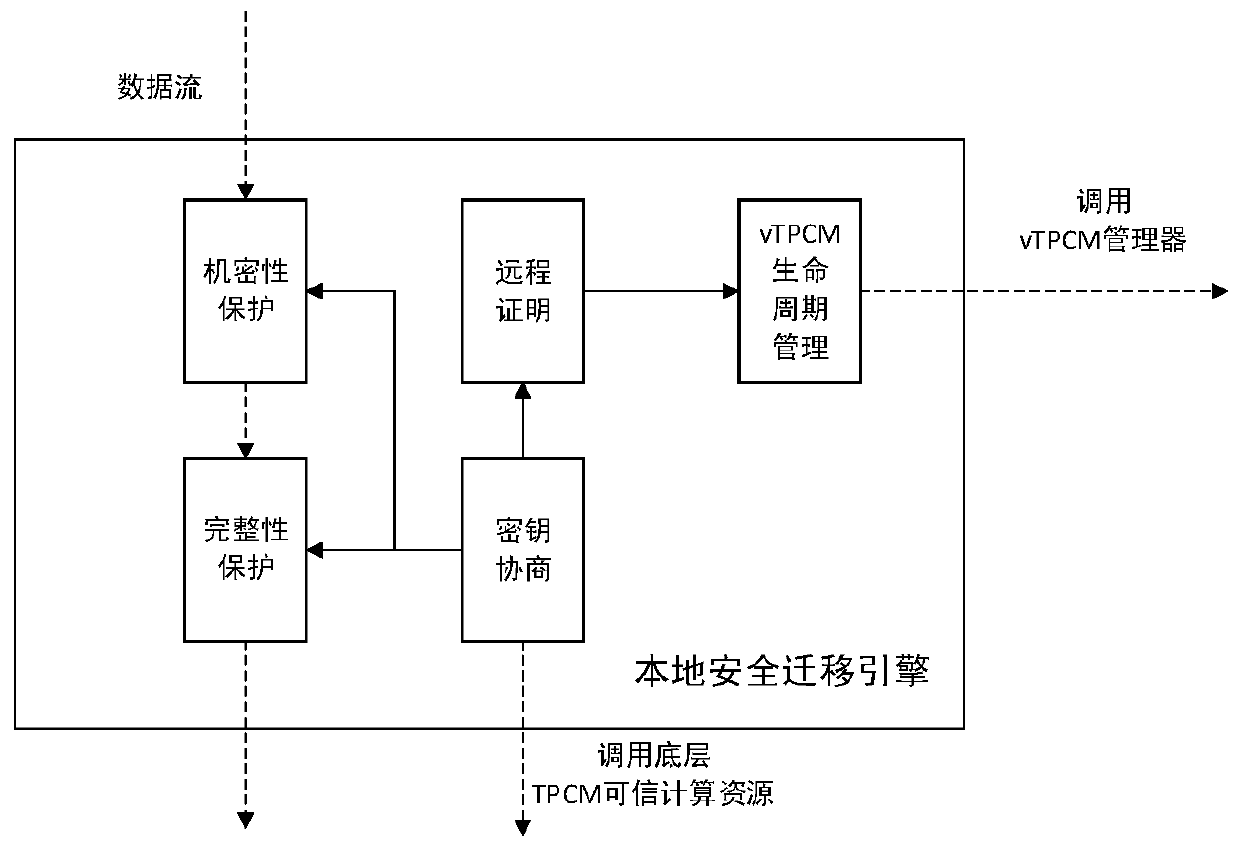
[0048] This embodiment will describe in detail the local security migration engine in the above-mentioned virtual machine security migration system, as image 3As shown, the secure migration engine includes five modules of key agreement, remote attestation, confidentiality protection, integrity protection and virtual TPCM lifecycle management, and the functions of each module are described in detail below:
[0049] (1) Key agreement module
[0050] The key agreement module is used for mutual identity authentication between the source platform and the target platform, and negotiates the key used to protect the confidentiality and integrity of the subsequent data exchange, that is, to provide the confidentiality protection module and the integrity protection module of the local migration engine key. The key agreement module generates two symmetric keys—Kenc and Kmac—through the TLS handshake protocol. These two keys are calculated by the source and target platforms using the ex...
Embodiment 3
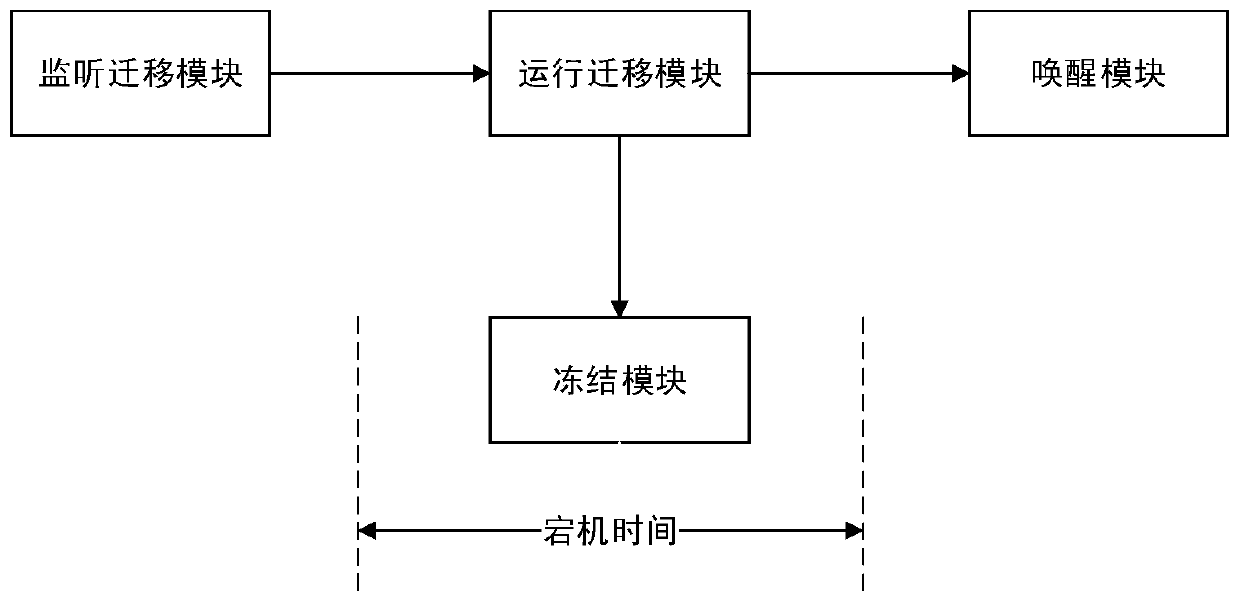
[0065] Based on the virtual machine security migration system in the above two embodiments, this embodiment proposes a virtual machine security migration method, such as Figure 4 As shown, the migration process is as follows:
[0066] (1) After the source platform receives the migration signal, it determines the address of the target platform. The source platform and the target platform use the TLS handshake protocol for key negotiation to obtain two symmetric keys——Kenc and Kmac.
[0067] (2) The source platform and the target platform verify the integrity of the target platform by using the session key obtained through key negotiation through the remote attestation module.
[0068] (3) The source platform virtual TPCM life cycle management module invokes the virtual TPCM manager to encapsulate the data of the virtual TPCM instance, and the virtual TPCM manager invokes the trusted computing resources of the underlying TPCM to complete the encapsulation of the virtual TPCM in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com