A hardware-based embedded system confidentiality protection method
An embedded system, confidentiality technology, applied in memory systems, instruments, electrical digital data processing and other directions, can solve the problems of multiple on-chip hardware resources, system performance loss, system resource waste, etc., to achieve low implementation cost and performance loss, Reduce the impact of system performance and avoid leakage effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] The present invention will be described in detail below in conjunction with the accompanying drawings, but it is not intended to limit the present invention.
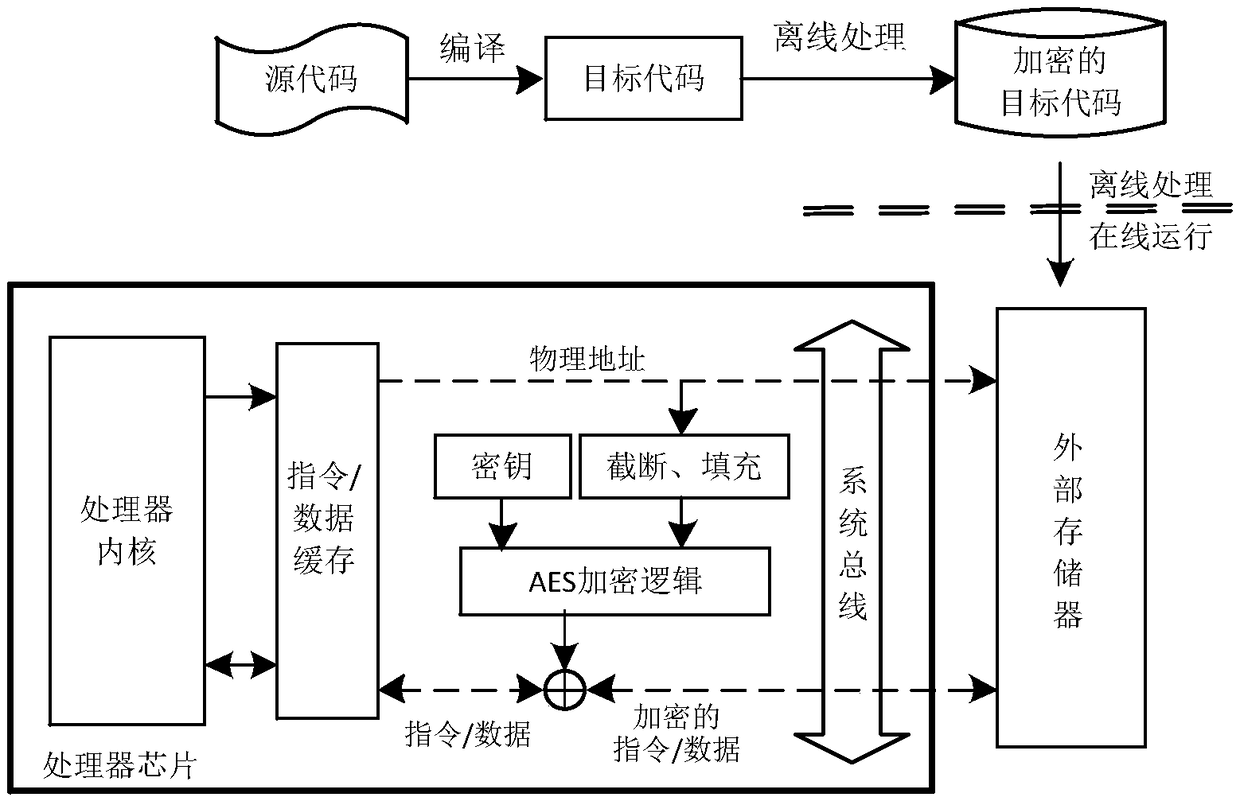
[0040] figure 1 It is an operation flowchart of a hardware-based embedded system confidentiality protection method of the present invention.
[0041] A kind of hardware-based embedded system confidentiality protection method of the present invention, such as figure 1 As shown, the method includes specific implementation steps as follows:
[0042] Step 1, according to the selected embedded processor, select the corresponding compiling and linking tool chain, and compile and link the user source program to generate the embedded system target code;
[0043] Step 2, preprocessing the target code on the host computer, encrypting the target code, and downloading the encrypted target code to the non-volatile memory of the embedded system. The method used here is to align the code segment and data segment in the targe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com