Supervisable distributed confidential transaction system and method
A transaction method and distributed technology, applied in the direction of payment system, payment system structure, protocol authorization, etc., can solve the problems that the regulator cannot implement penetrating supervision, damage the security of the transaction system, and the usability is not ideal, so as to ensure timely effectiveness and effectiveness, improve user experience, and improve supervision efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0057] A regulated distributed confidential transaction method, executed from a supervisory party, comprising the following steps:
[0058] Generate public parameters using a non-interactive zero-knowledge proof system generation algorithm;
[0059] Using the integrated encryption signature method, a public-private key pair is generated, and the private key is used as the global supervision private key;
[0060] Receive the registration request of the participating parties, and obtain the public and private key pairs, encrypted balances and public account information of the participating parties;
[0061] Monitor the transactions of the participating parties, confirm whether the transaction amount and the account balance of the transaction originator are within a reasonable range, or receive confirmation results of whether the transaction amount and the account balance of the transaction originator are within a reasonable range;
[0062] If the confirmation result is passed, ...
Embodiment 2
[0069] A regulated distributed confidential transaction method, executed from participating parties, comprising the following steps:
[0070] Send a registration request, send your own public / private key pair, encrypted balance and account public information;
[0071] Receive public parameters, generate or receive transaction requests, and confirm whether the transaction amount and the balance of the transaction originator are within a reasonable range, or, receive the confirmation result of whether the transaction amount and the account balance of the transaction originator are within a reasonable range;
[0072] If the confirmation result is passed, the confidential transaction will be carried out, and the account status will be updated according to the confidential transaction record verified by the legitimacy, otherwise the confidential transaction will be abandoned.
Embodiment 3
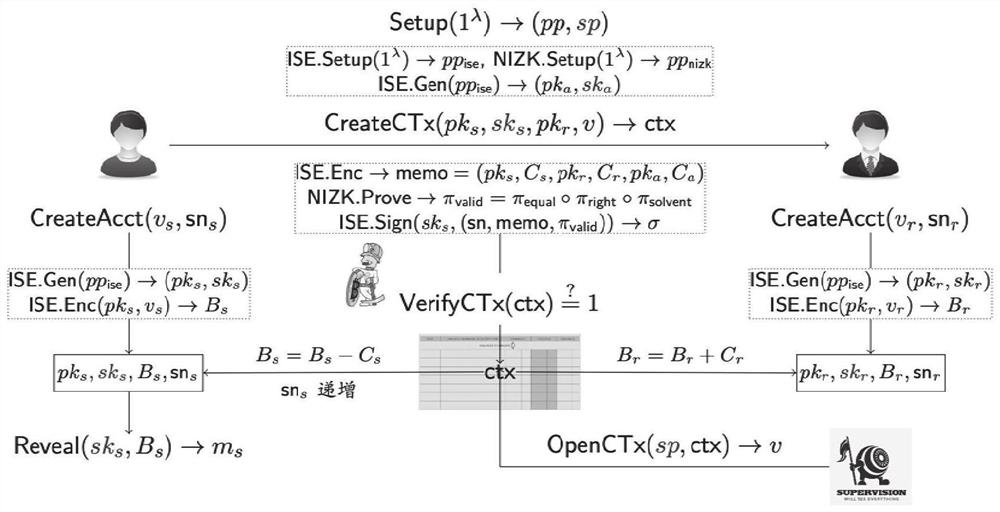
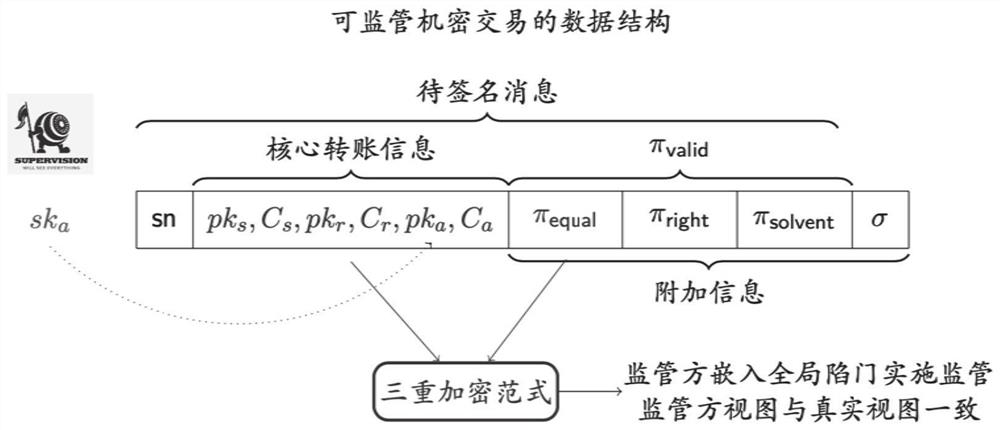
[0074] A regulated distributed confidential transaction method such as figure 1 shown, including the following steps:
[0075] (1) Perform system generation.
[0076] The system is designed based on an integrated cryptographic signature scheme (in which the cryptographic components support additive homomorphism) and a non-interactive zero-knowledge proof protocol.
[0077] Specifically, the supervisor performs the following operations:
[0078] (1-1) Run the system generation algorithm integrating the encrypted signature scheme and the non-interactive zero-knowledge proof respectively, and generate the corresponding public parameters pp_ise and pp_nizk;
[0079] (1-2) Run the key generation algorithm of the integrated encryption signature scheme to generate a public-private key pair (pk_a, sk_a);
[0080] (1-3) Publish pp=(pp_ise, pp_nizk, pk_a) as the public parameter of the system, and secretly hold sk_a as the global supervision private key.
[0081] (2) Account registr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com