Identity based efficient anonymous batch authentication method in IOV (Internet of Vehicles) environment
An authentication method, a technology of the Internet of Vehicles, applied in user identity/authority verification, digital transmission systems, electrical components, etc., can solve the problems of low efficiency of the authentication process, high computational overhead, and no improvement in efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0053] The technical solutions of the present invention will be described in detail below, but the protection scope of the present invention is not limited to the embodiments.
[0054] The present invention is carried out under certain system hypothesis, and concrete system model and hypothesis are described as follows:
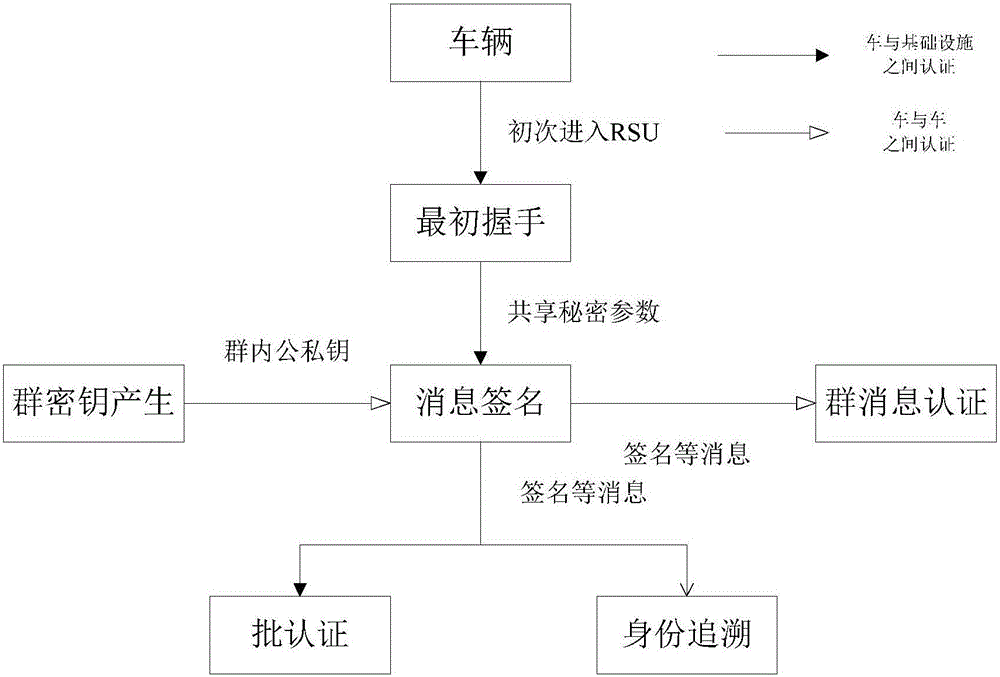
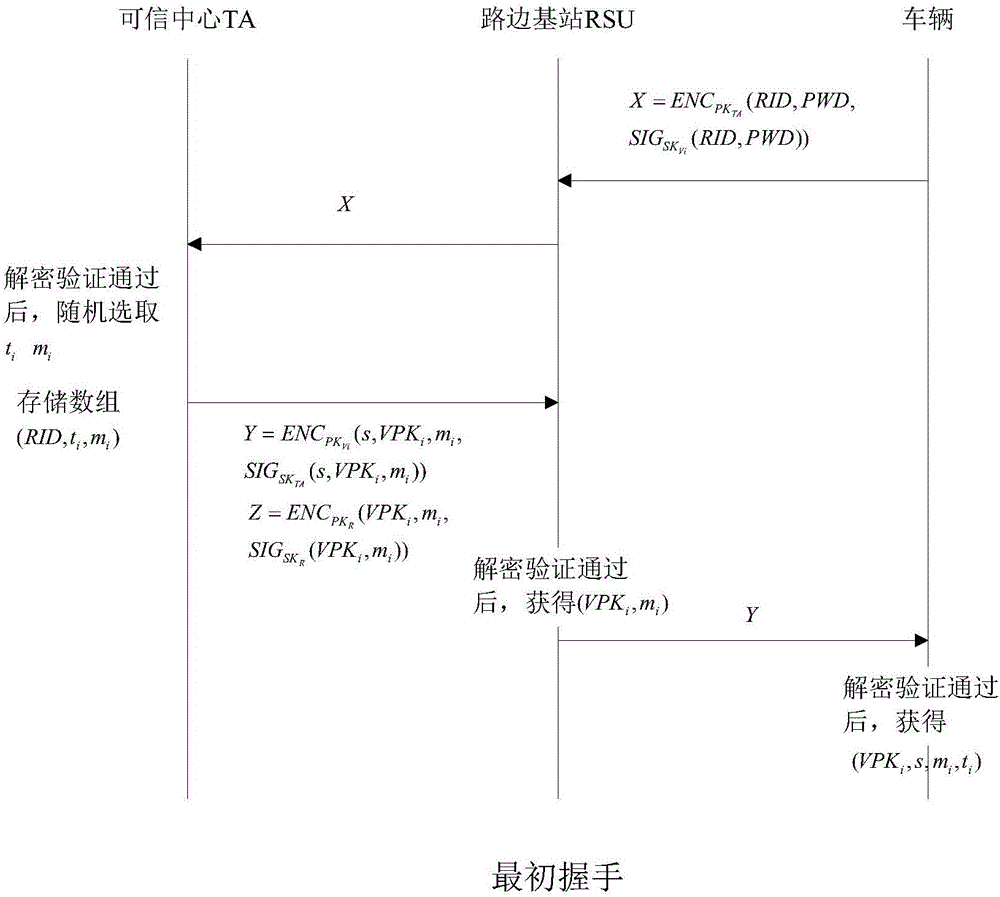
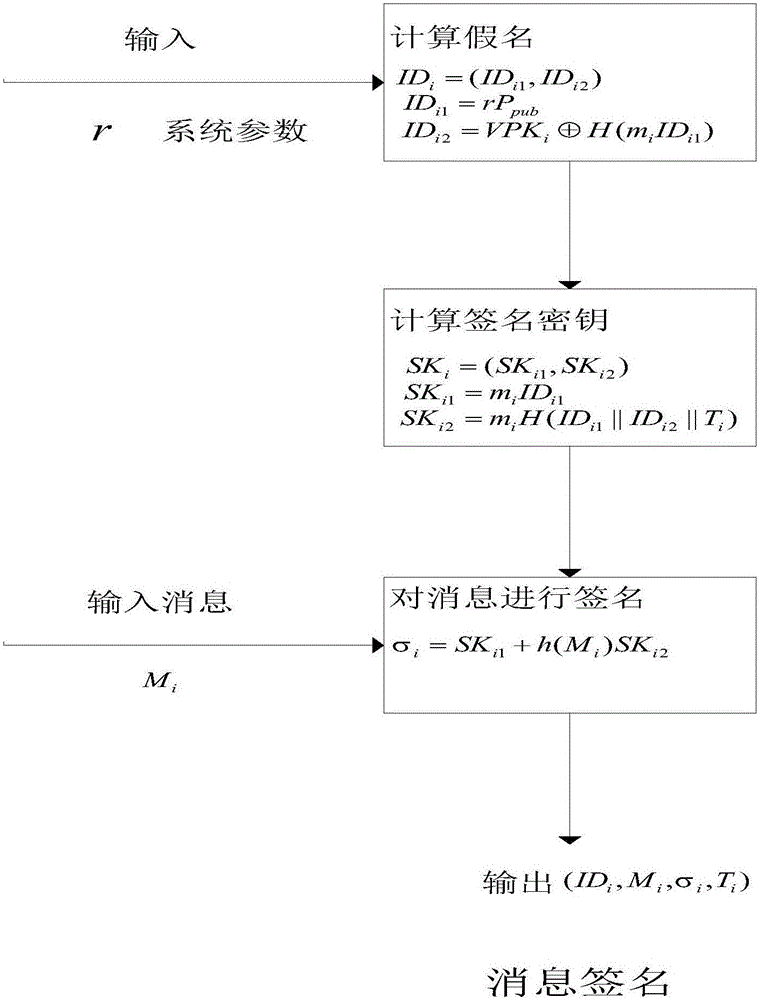
[0055] Introduce several important components in the Internet of Vehicles model. Trusted Hub (TA), Roadside Infrastructure (RSUs), On-board Communications Unit (OBU). RSUs are trusted and usually have strong computing power and high storage capacity.
[0056]1. Assume that TA is always online, trustworthy, and never compromises. Such an assumption is usually taken when defining it in the Internet of Vehicles. The communication between TA and RSUs is through a secure channel, usually through a secure wired connection. There are redundant TAs to avoid single point of failure and functional bottlenecks. TA is the issuing organization of the certificate, and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com