Method, system and equipment for authentication
An authentication method and equipment technology, applied in electrical components, wireless communication, safety devices, etc., can solve problems such as AP equipment authentication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0077] In order to realize authentication of an AP device by a UE and authentication of a UE by an AP device, an embodiment of the present invention provides an authentication method. In this method, a terminal and an AP device use an AKA algorithm to authenticate each other.
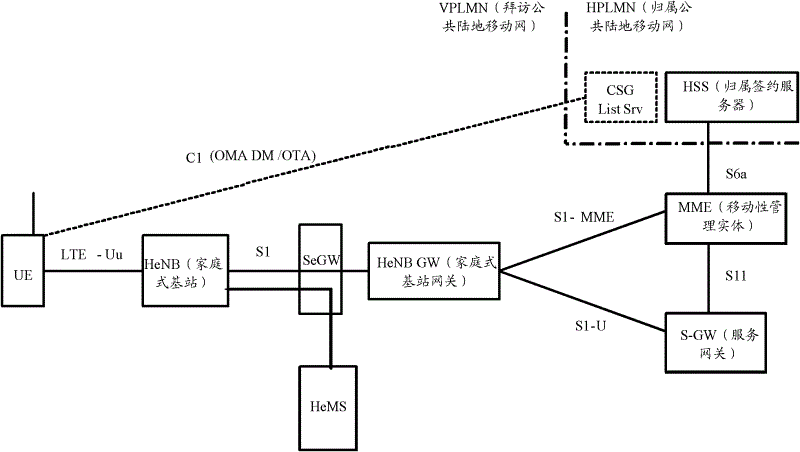
[0078] The embodiments of the present invention can be applied in the newly introduced long-term evolution local area network (Local Area Network, LTE-LAN) system, and can also be applied in other systems including UE, AP equipment, gateway equipment and HSS.
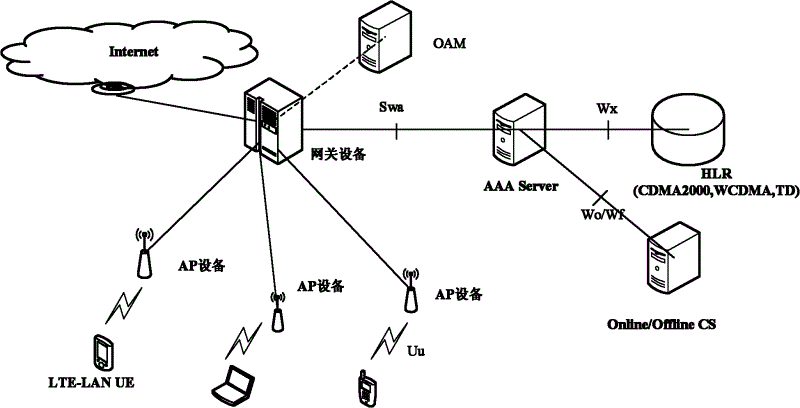
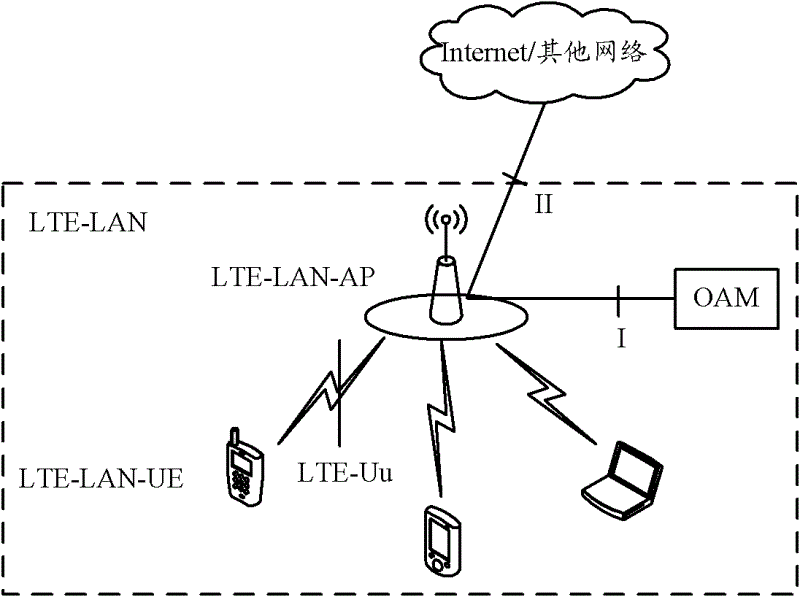
[0079] Such as Figure 2A As shown, in the LTE-LAN system, the AP device is a new access device. The existing LTE physical layer technology is used on the air interface. After the synchronization between the AP devices is completed, the gateway device accesses the Internet. The frequency band used by the AP device There is no overlap with the frequency band of the macro base station (eNB). In the LTE-LAN system, the UE completes the data ser...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com