Forced access control method and apparatus in virtual environment
A technology of mandatory access control and virtualized environment, applied in program control devices, software simulation/interpretation/simulation, etc., can solve the problem of uncontrolled communication and resource sharing type, large granularity of communication and resource sharing control, and inapplicable multi-level security. environmental issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0059] The embodiments of the present invention are described in detail below in conjunction with the accompanying drawings: this embodiment is implemented on the premise of the technical solution of the present invention, and detailed implementation methods and specific operating procedures are provided, but the protection scope of the present invention is not limited to the following the described embodiment.
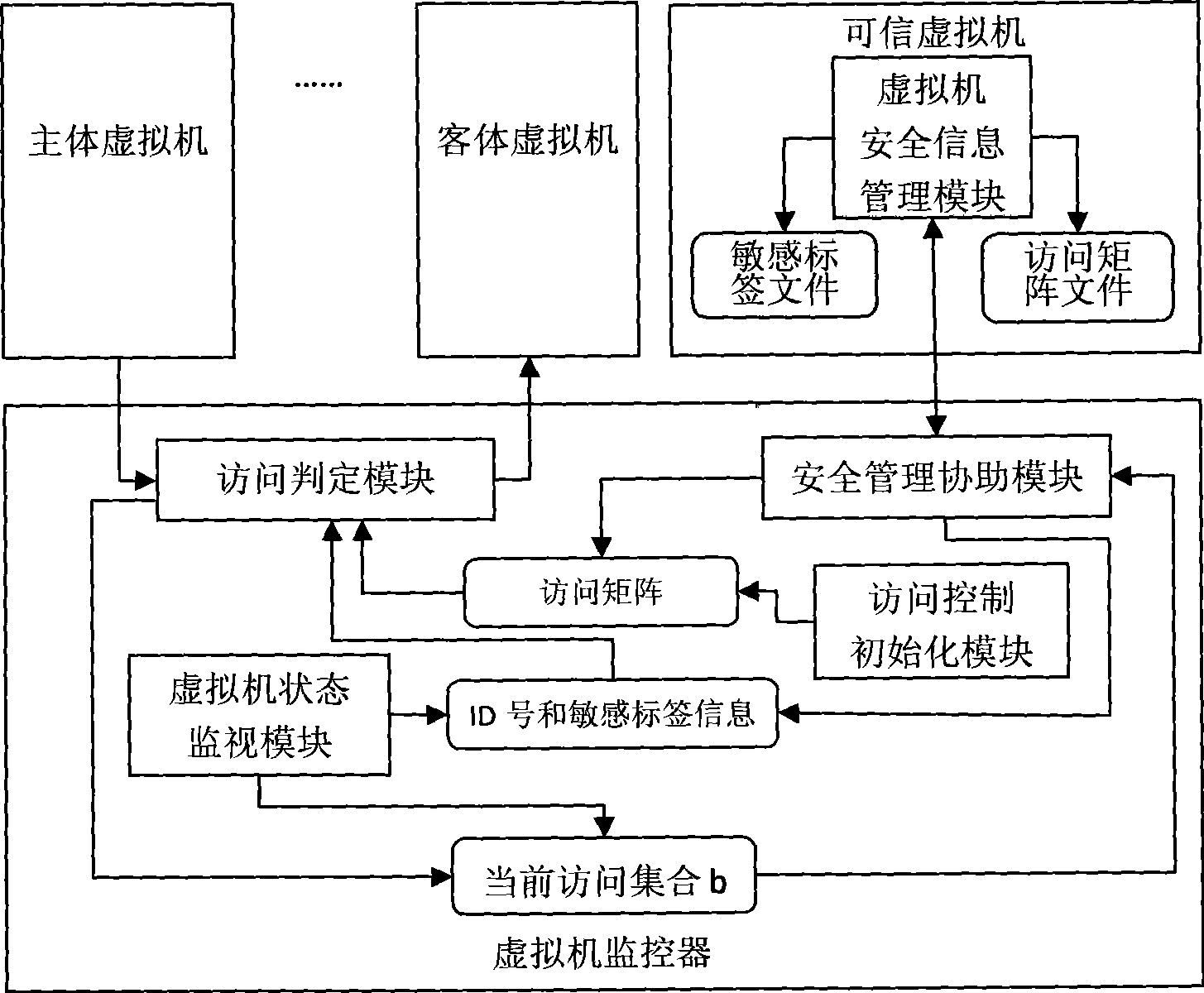
[0060] like figure 1 Shown is the virtual machine hierarchical relationship in this embodiment, the trusted virtual machine is on the root node of the hierarchical relationship, and other virtual machines are the child nodes of the root node.
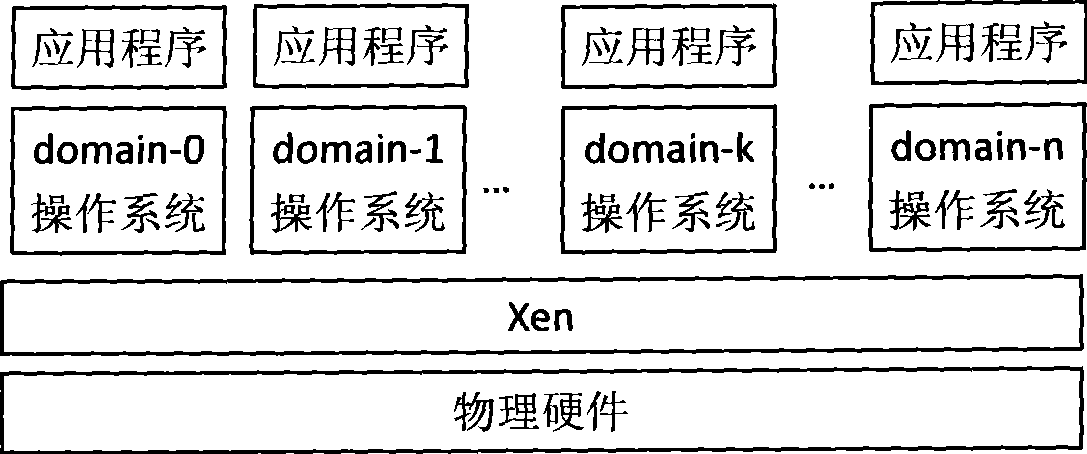
[0061] This embodiment is implemented on the virtual machine monitor Xen. like figure 2 As shown, the Xen virtual machine monitor is an open source virtual machine monitor project developed by the computer laboratory of Cambridge University. The relationship between the Xen virtual machine monitor and physical hardware, virt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com