Intelligent terminal isolation system and intelligent terminal isolation method both based on processor safety extension
A security expansion and smart terminal technology, applied in the field of smart terminal isolation system, can solve the problems that the operating environment of smart terminals cannot reach a sufficient security level, highly sensitive services lose security, and cannot provide an operating environment, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
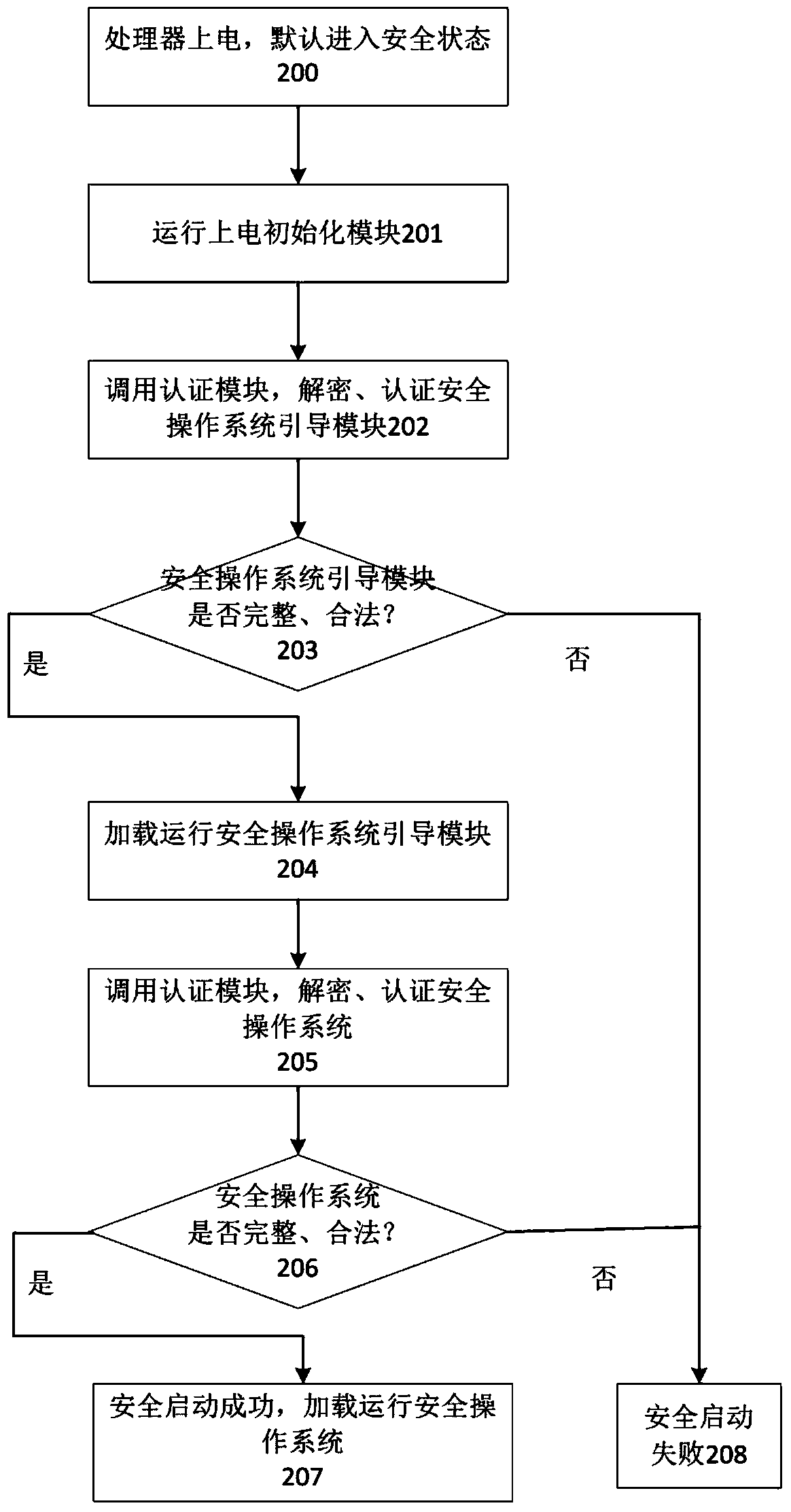
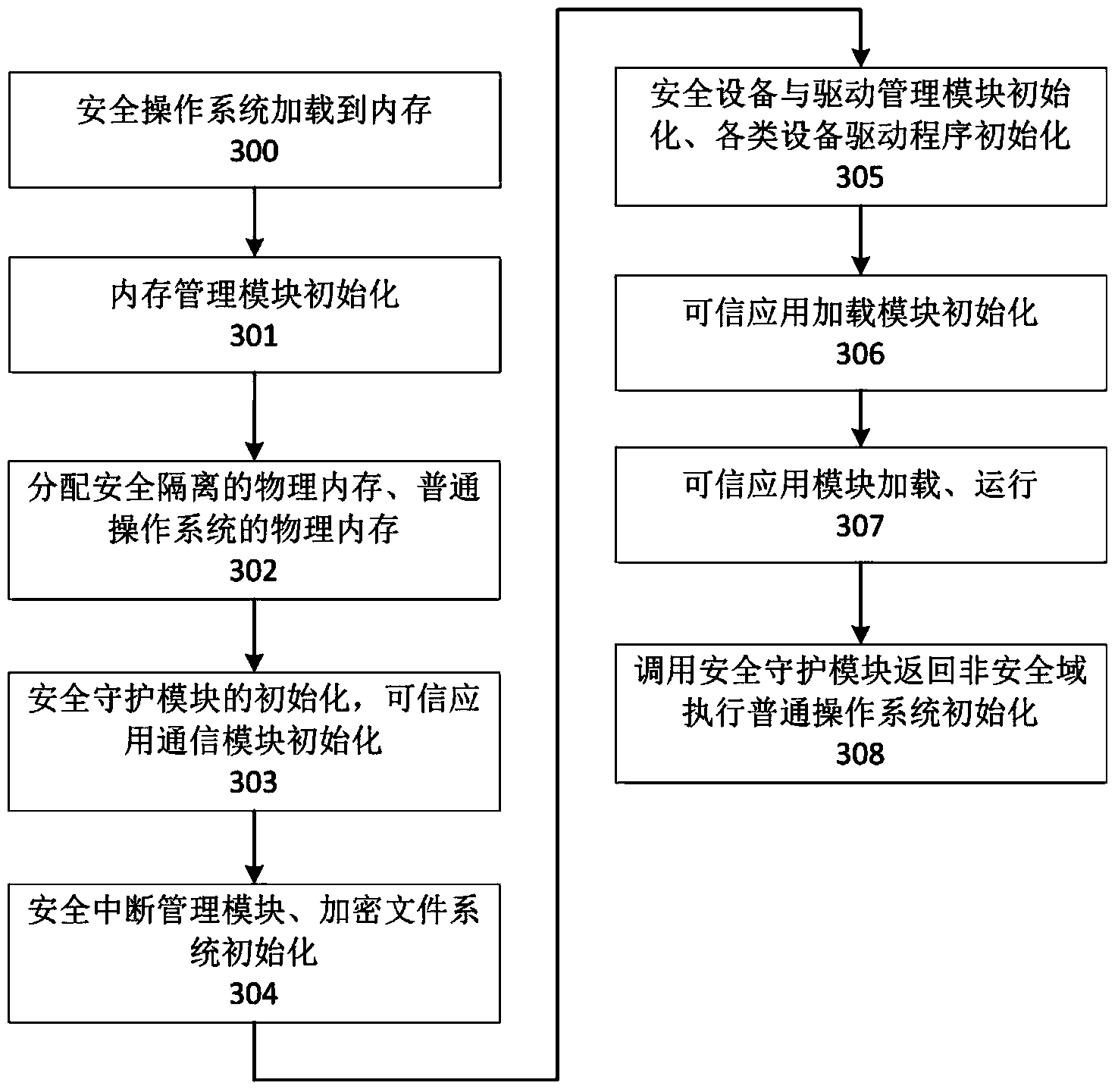
[0067] The present invention is further described and explained by the following examples.
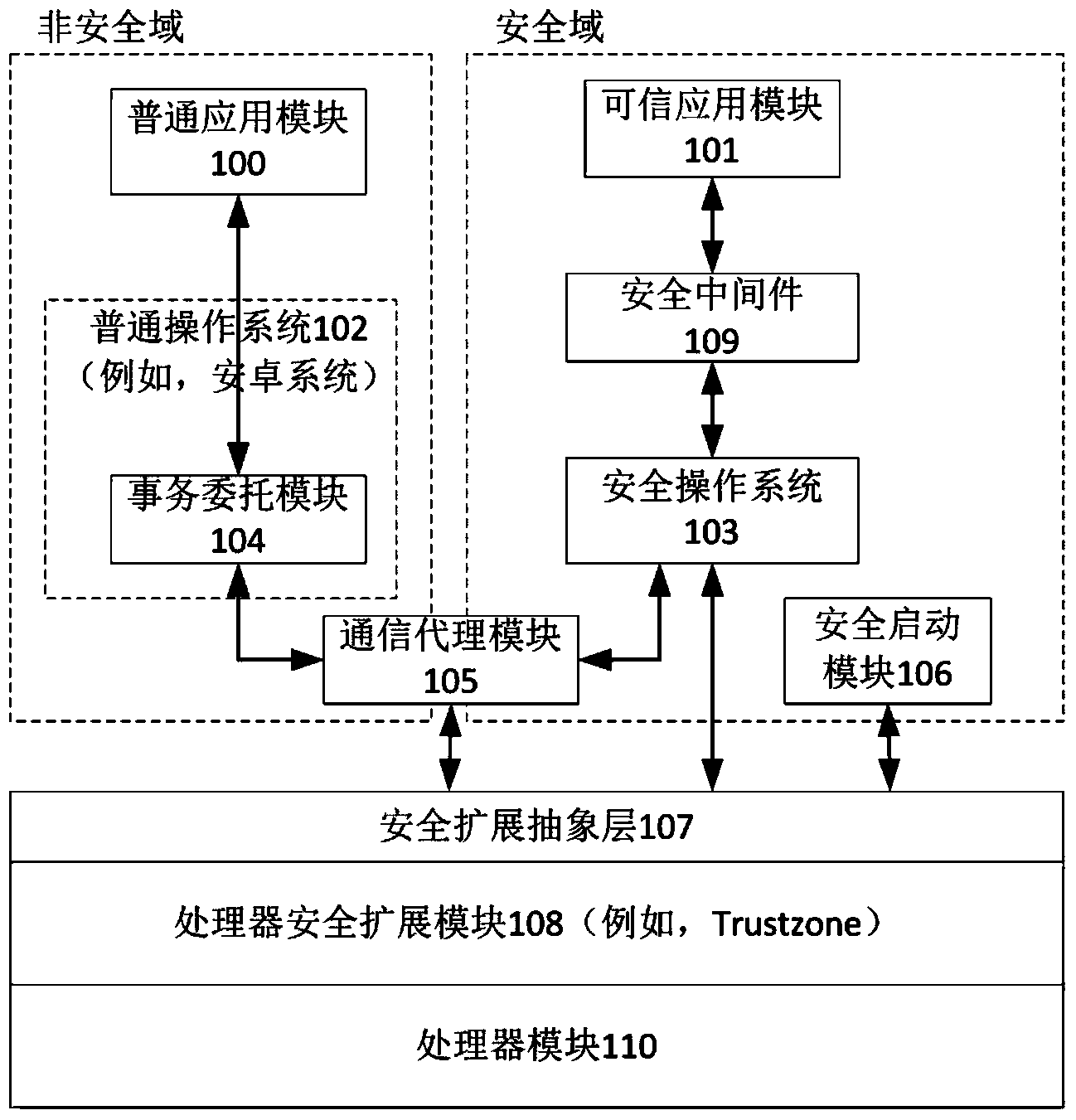
[0068] The present invention will use the Android system as the common operating system 102, combined with Trustzone technology as the processor security extension module 108, to describe the specific implementation on the smart phone. However, other implementations of the present invention can still be used on existing or future common operating systems or kernels, and other processor security extension technologies can also be used. In addition, the embodiments described in the following specific examples are implemented by smart phones, but the isolation system of the invention can be used in whole or in part on smart terminals such as flat panels, digital TV set-top boxes, and smart TVs.
[0069] see figure 1 , the figure shows the relationship between the various components of the present invention. Trustzone is an embodiment of the processor security extension module 108. The p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com