User identity secret-keeping method in communication system
A communication system and user identity technology, which is applied in the field of keeping user identity confidential, can solve problems such as security identity information leakage, security damage, etc., and achieve the effect of meeting security requirements and good confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] Specific embodiments of the present invention will be described in detail below, so as to fully understand the technical effects and solutions of the present invention.
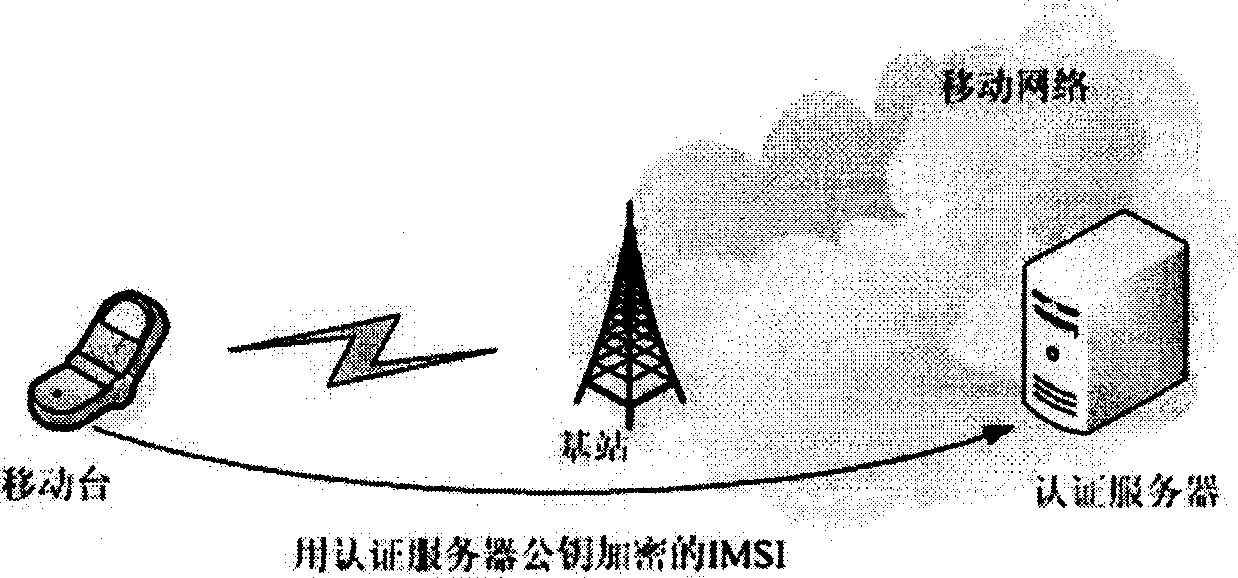
[0043] The main idea of the present invention is to adopt the asymmetric encryption technology in the cryptography in the identification process of the communication system. In cryptography, asymmetric cryptography is relative to symmetric cryptography. Symmetric cryptography uses the same key for encryption and decryption, while asymmetric cryptography uses different keys for encryption and decryption. The common asymmetric Cryptographic algorithms such as RSA, etc. Asymmetric cryptography uses a pair of corresponding keys—a public key and a private key. The public key is usually public and does not need to be kept secret; the private key needs to be kept carefully by the user, and only the user knows it. In common applications, the public key is used to keep data confidential to prevent malicious...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com