Safety on-demand supply method and system, and service type acquisition method
A business type and business technology, applied in the field of information security, can solve problems such as different security risks, different security strengths, staying in the theoretical stage, etc., and achieve the effect of improving user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
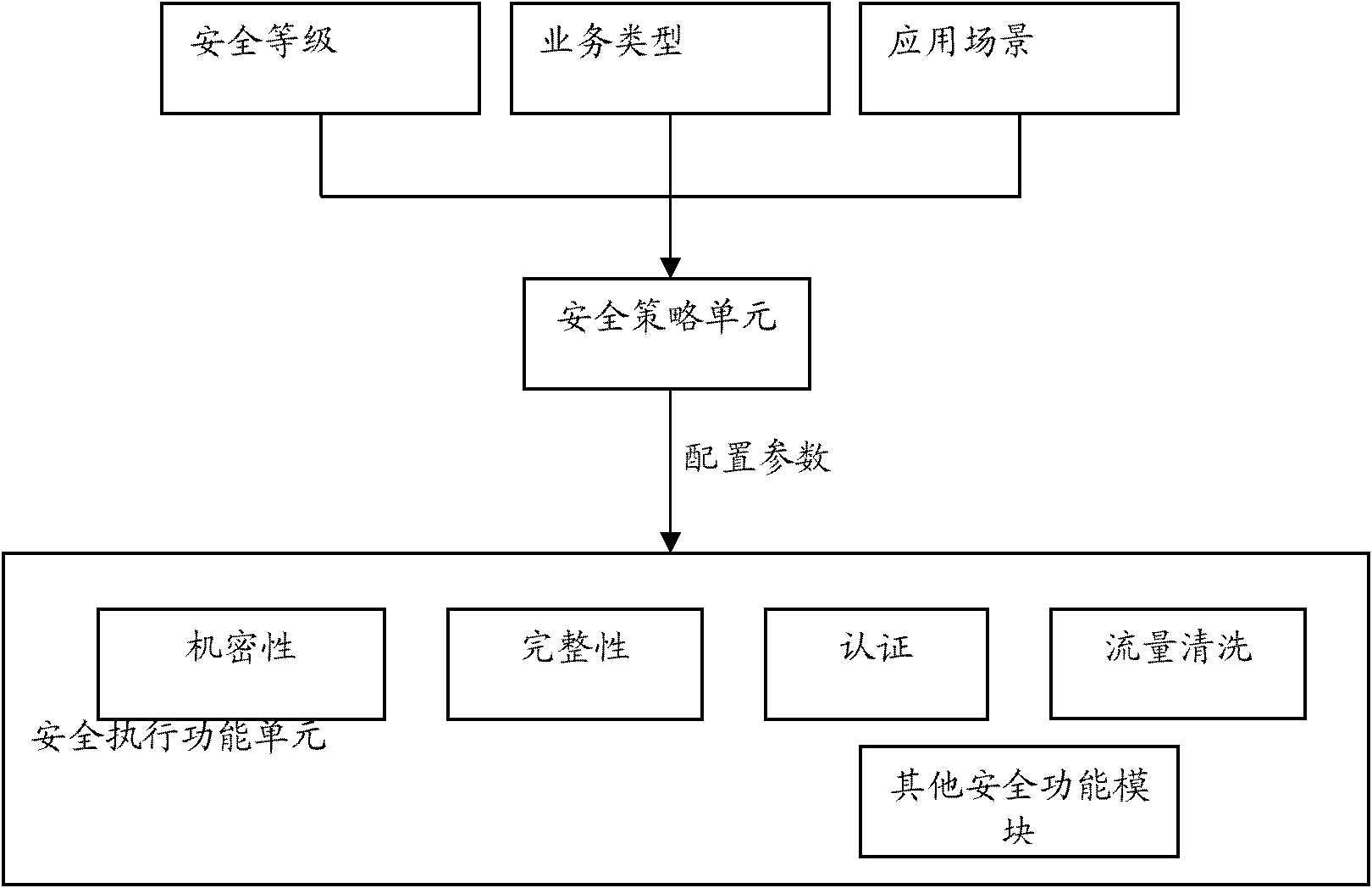
[0068] The basic idea of the present invention is: by extracting the service identifier from the service type, combined with the application scene, the user's setting of the security level, as the input parameter of the security policy, deriving the security parameter from the security policy, and acting on the security algorithm and protocol, thereby Provide on-demand security protection for business data.
[0069] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail by citing the following embodiments and referring to the accompanying drawings.
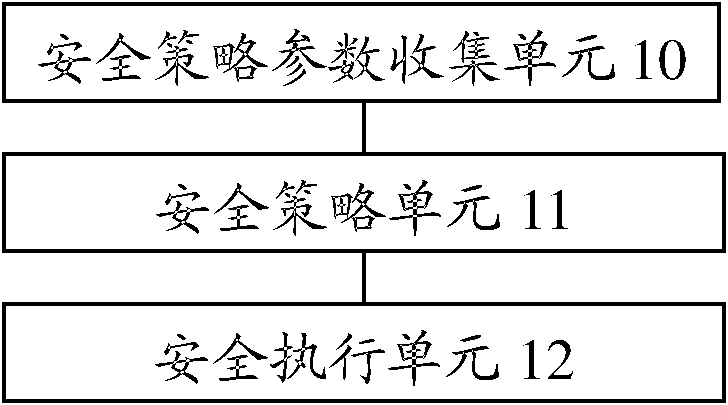
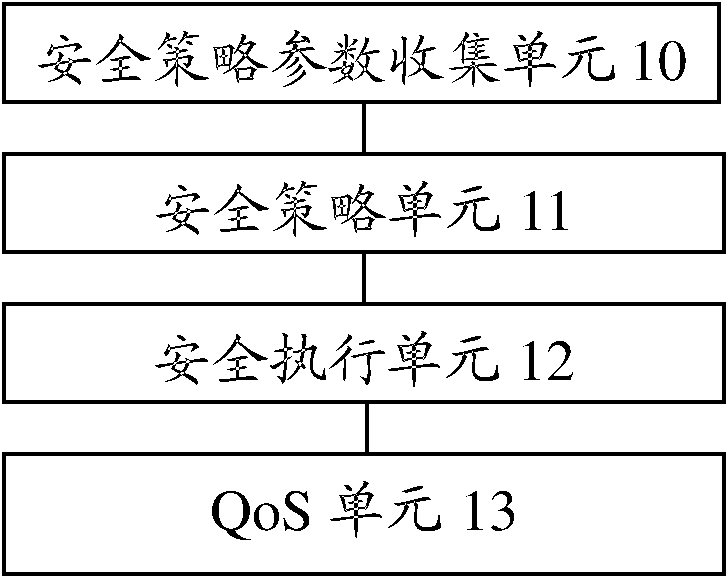
[0070] figure 1 It is a schematic diagram of the composition and structure of the secure on-demand provisioning system of the embodiment of the present invention, such as figure 1 As shown, the security on-demand system of the present invention includes a security policy parameter collection unit 10, a security policy unit 11 and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com