Patents
Literature
142 results about "Phishing attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
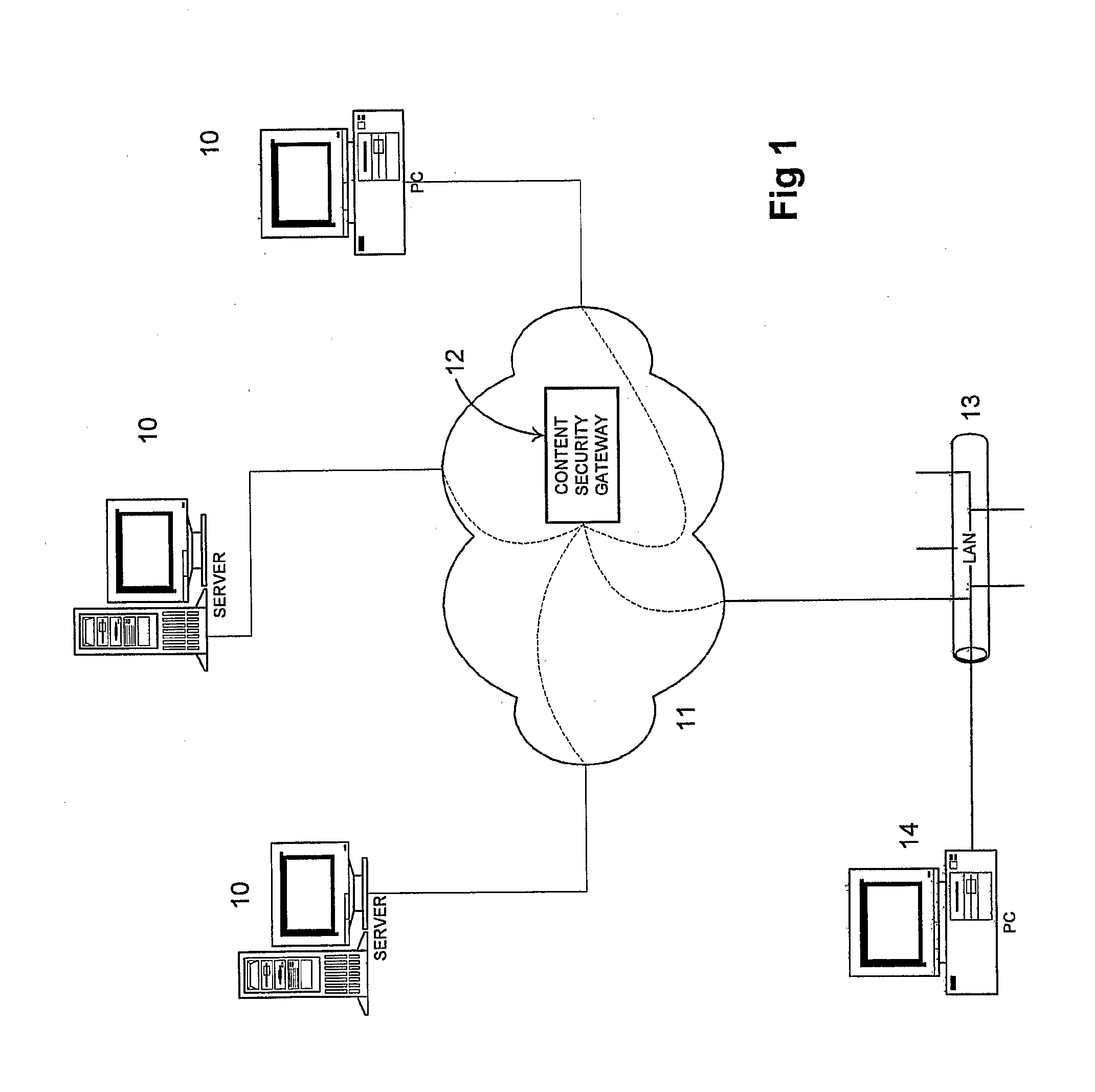
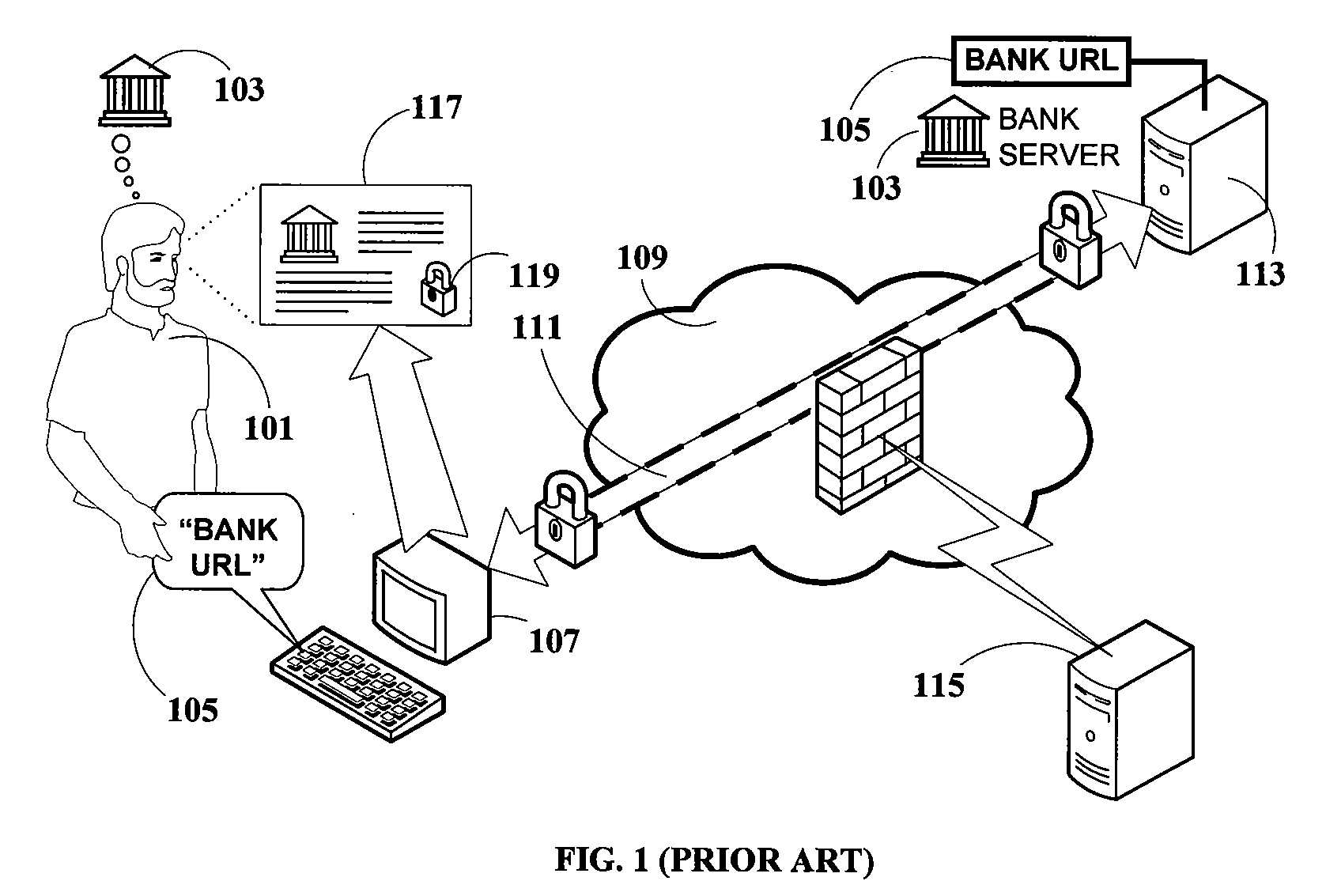
Phishing is a type of security attack that attempts to trick or coerce targets into divulging sensitive/valuable information. Sometimes referred to as a “phishing scam,” attackers target users’ login credentials, financial information (such as credit cards or bank accounts), company data, and anything that could potentially be of value.
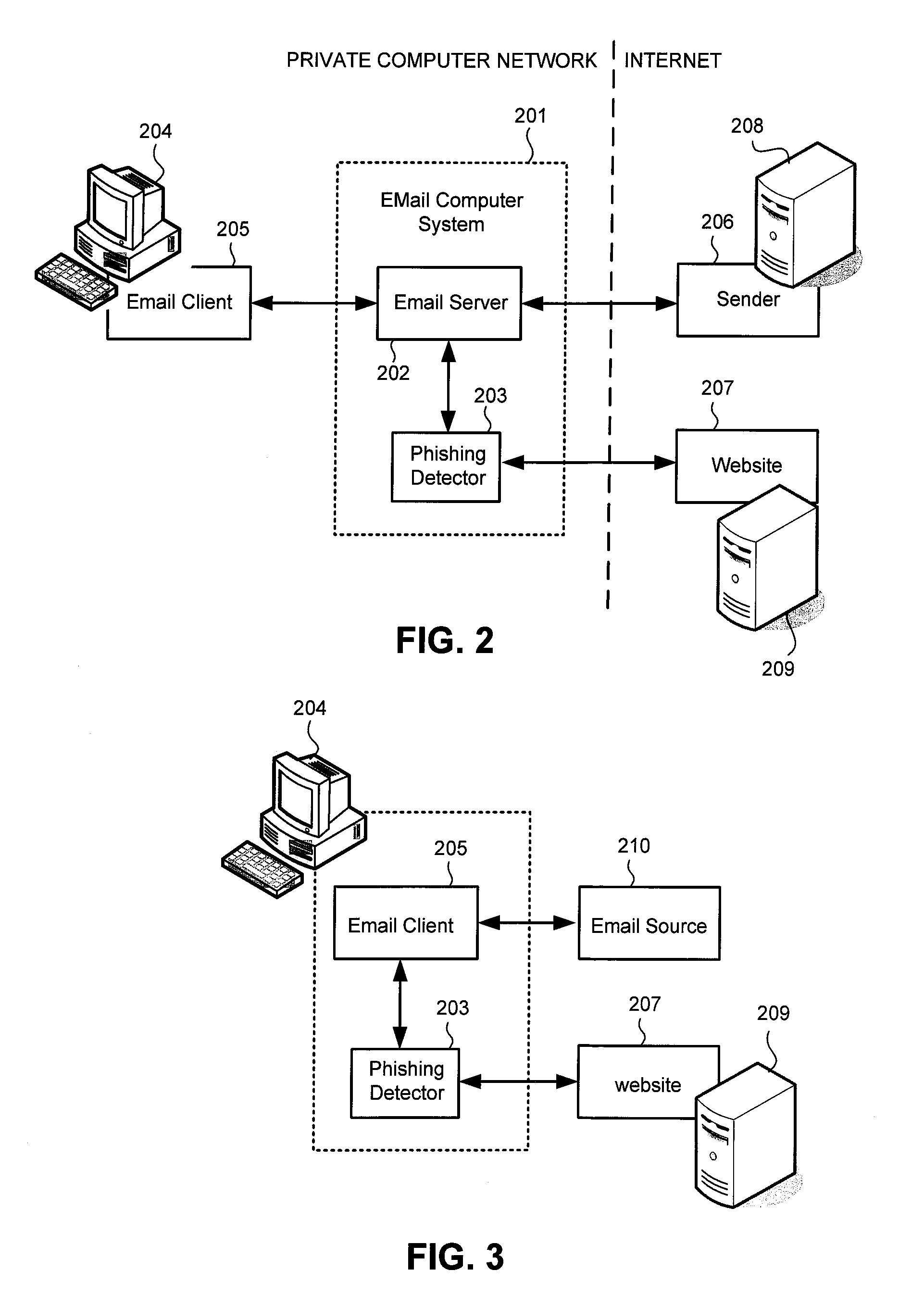
Methods and systems for phishing detection and notification
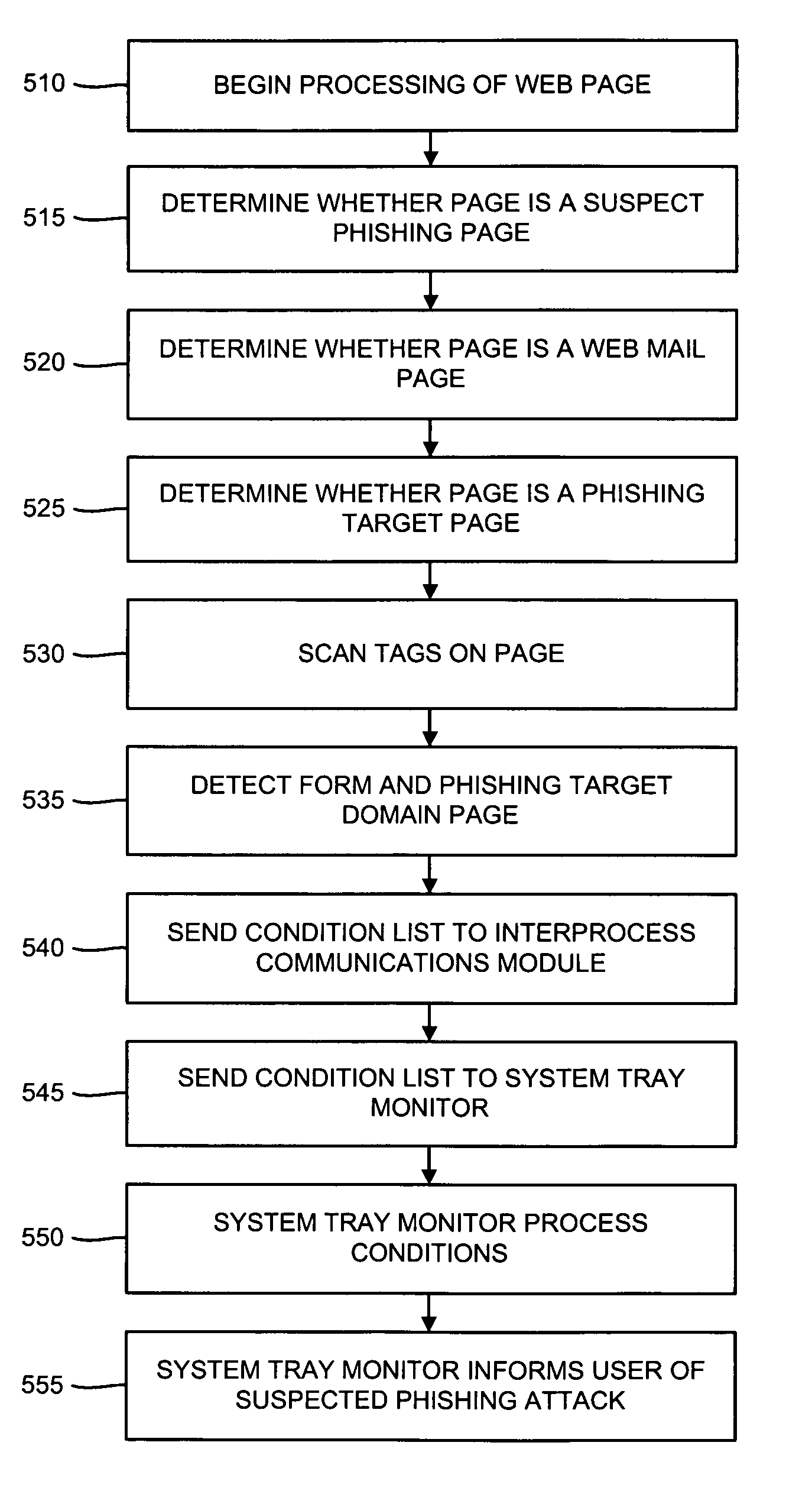
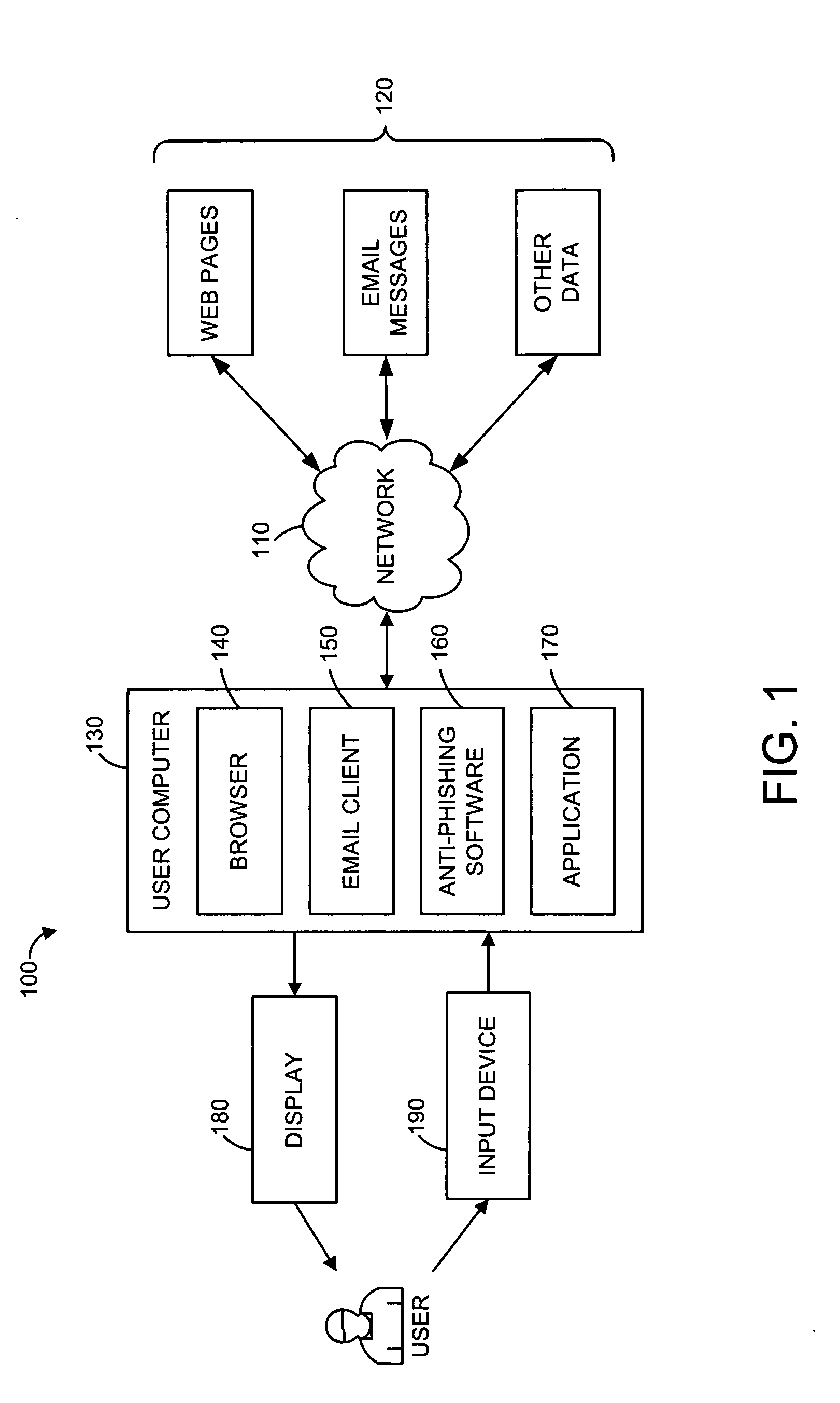
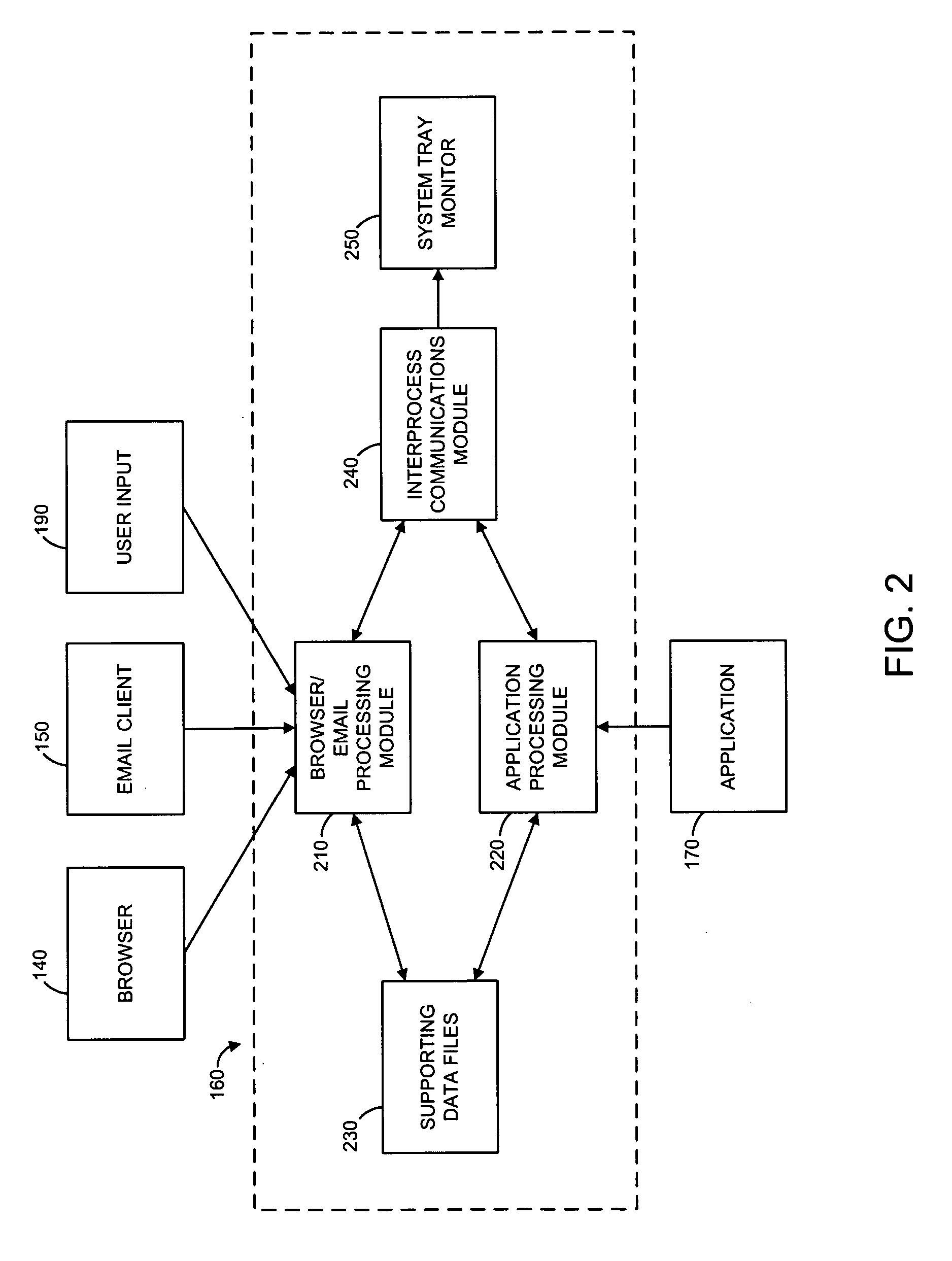
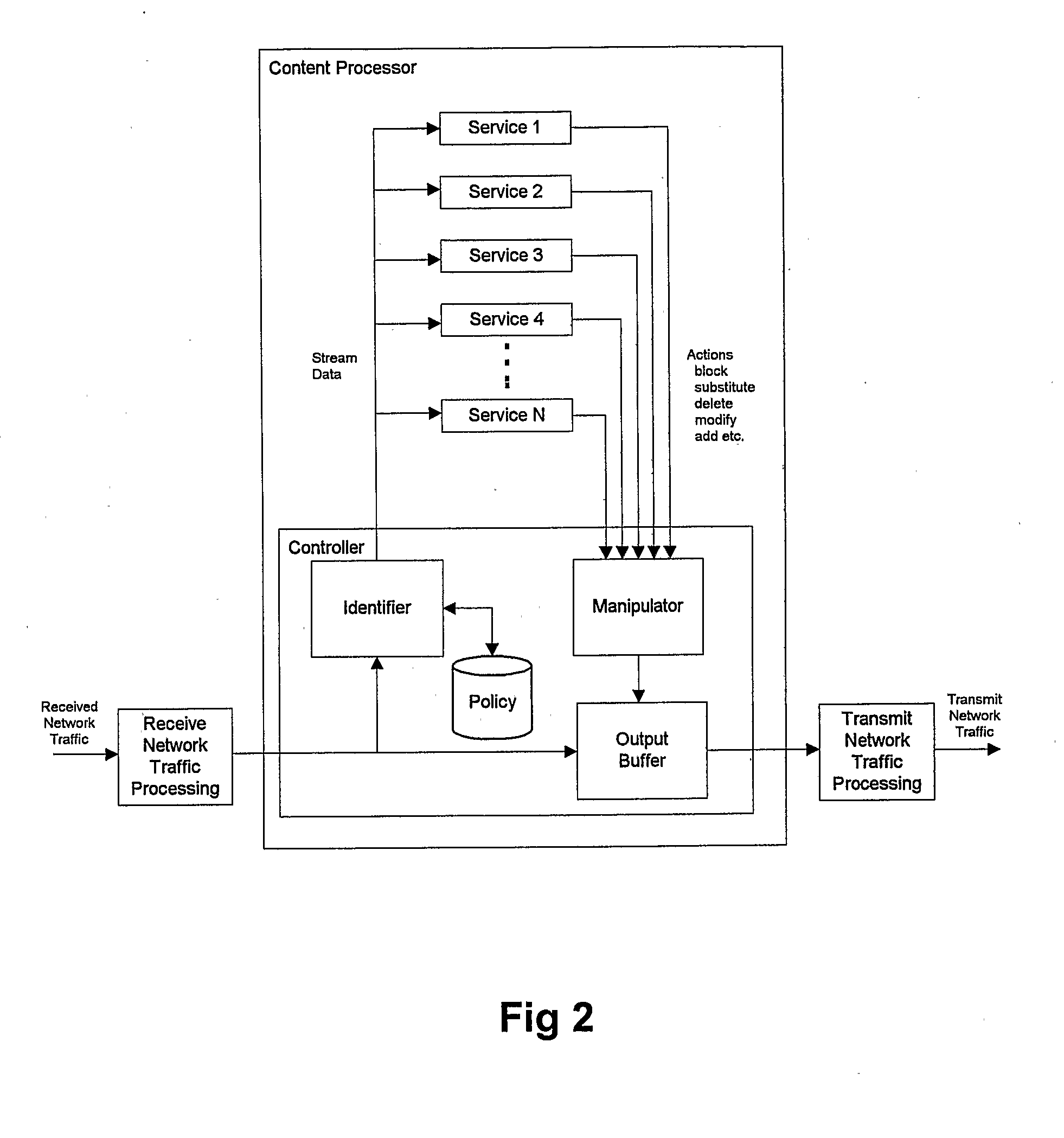
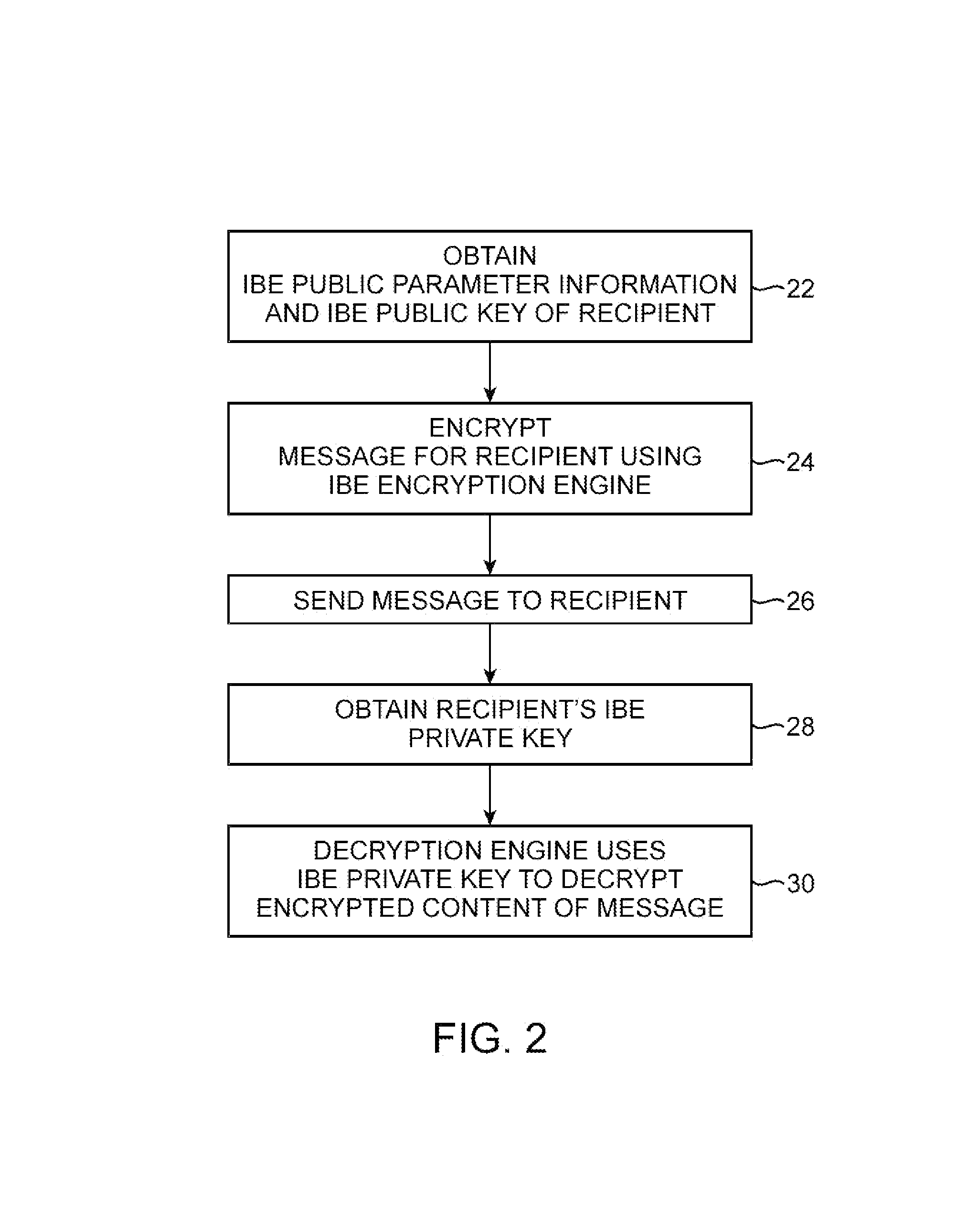
Various techniques are provided for detecting phishing attacks and notifying users of such attacks. In one example, a machine-implemented method can be provided for detecting a phishing attack over a computer network. A web page can be accessed and information associated with the web page can be processed. One or more conditions can be set in response to the processing. The conditions can be compared to a set of conditions indicative of a phishing attack. A user can then be informed of a potential phishing attack corresponding to the conditions through the display of an alert window and / or an icon. Such actions can also be performed in response to a user's selection of a link appearing in an email message. Appropriate systems and / or computer readable media incorporating these features can also be provided.
Owner:SEARCH INITIATIVES LLC
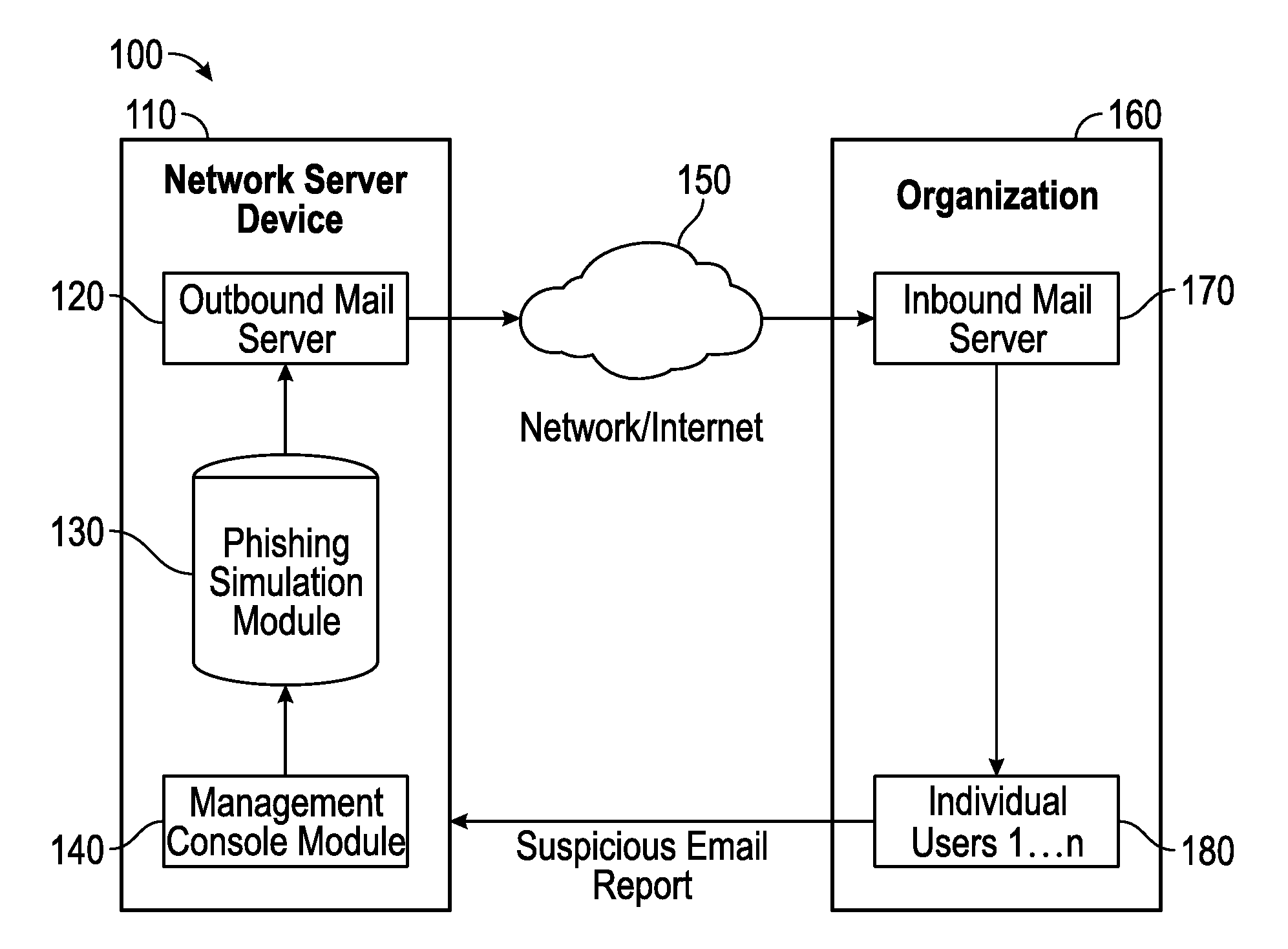
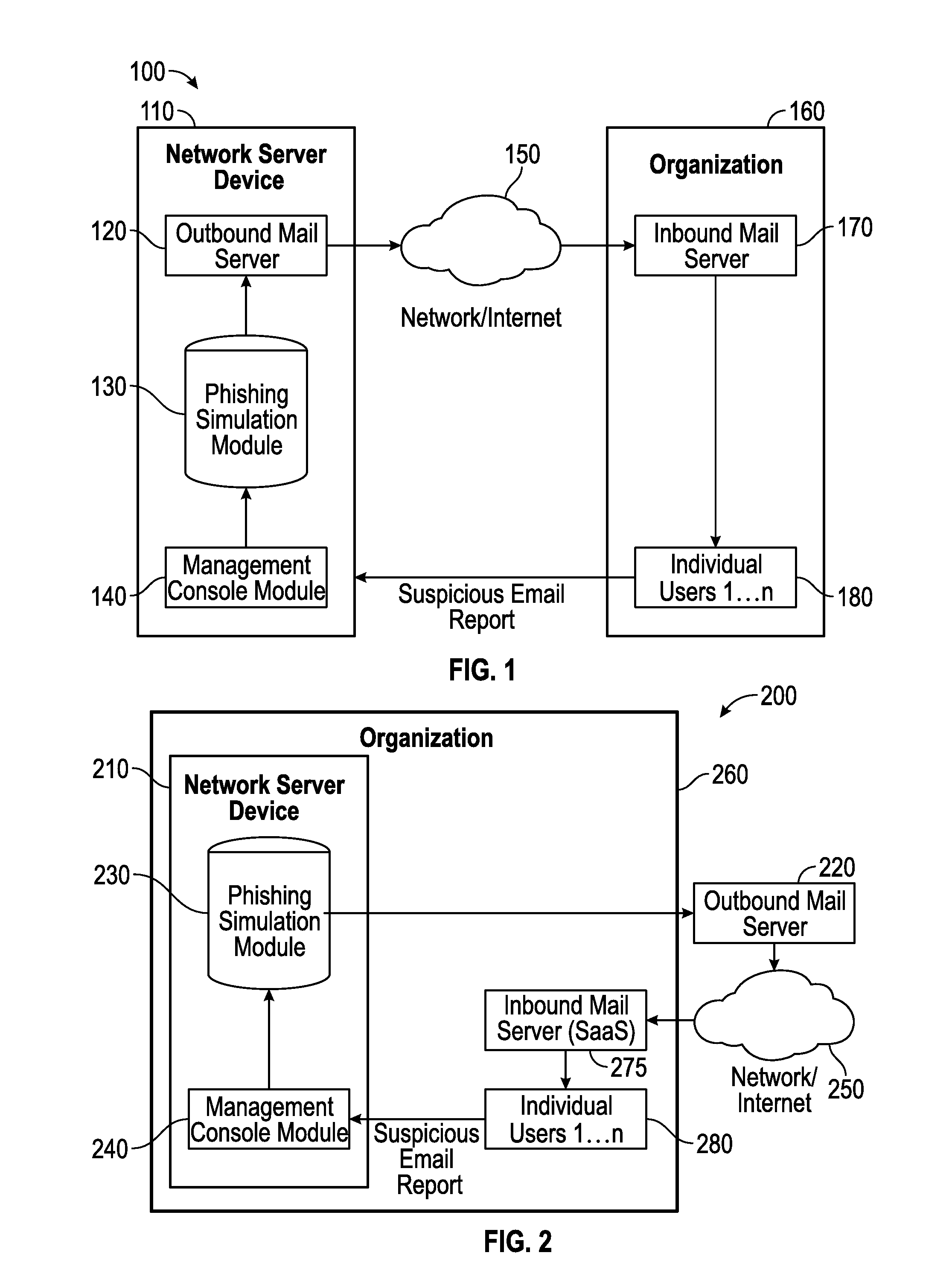
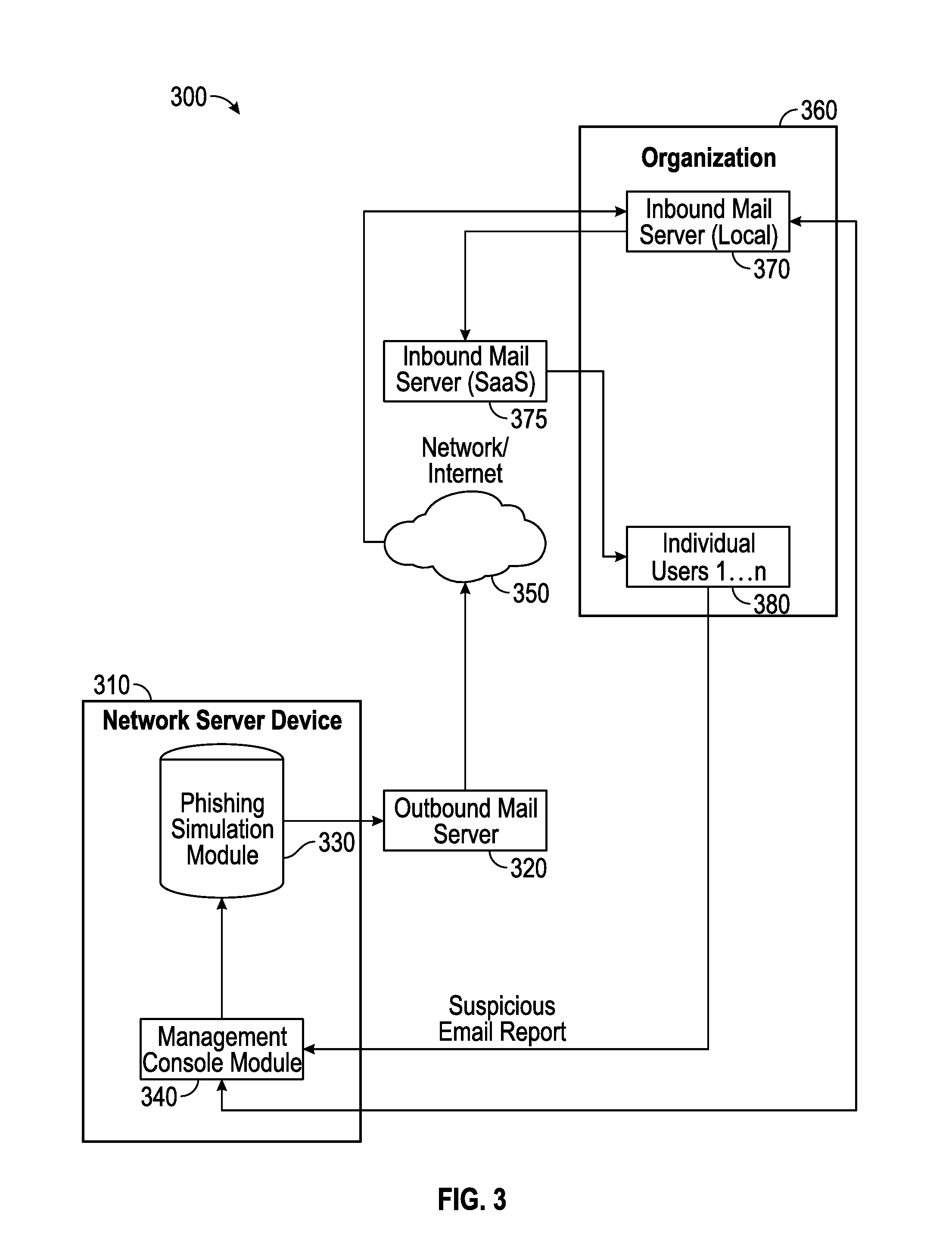
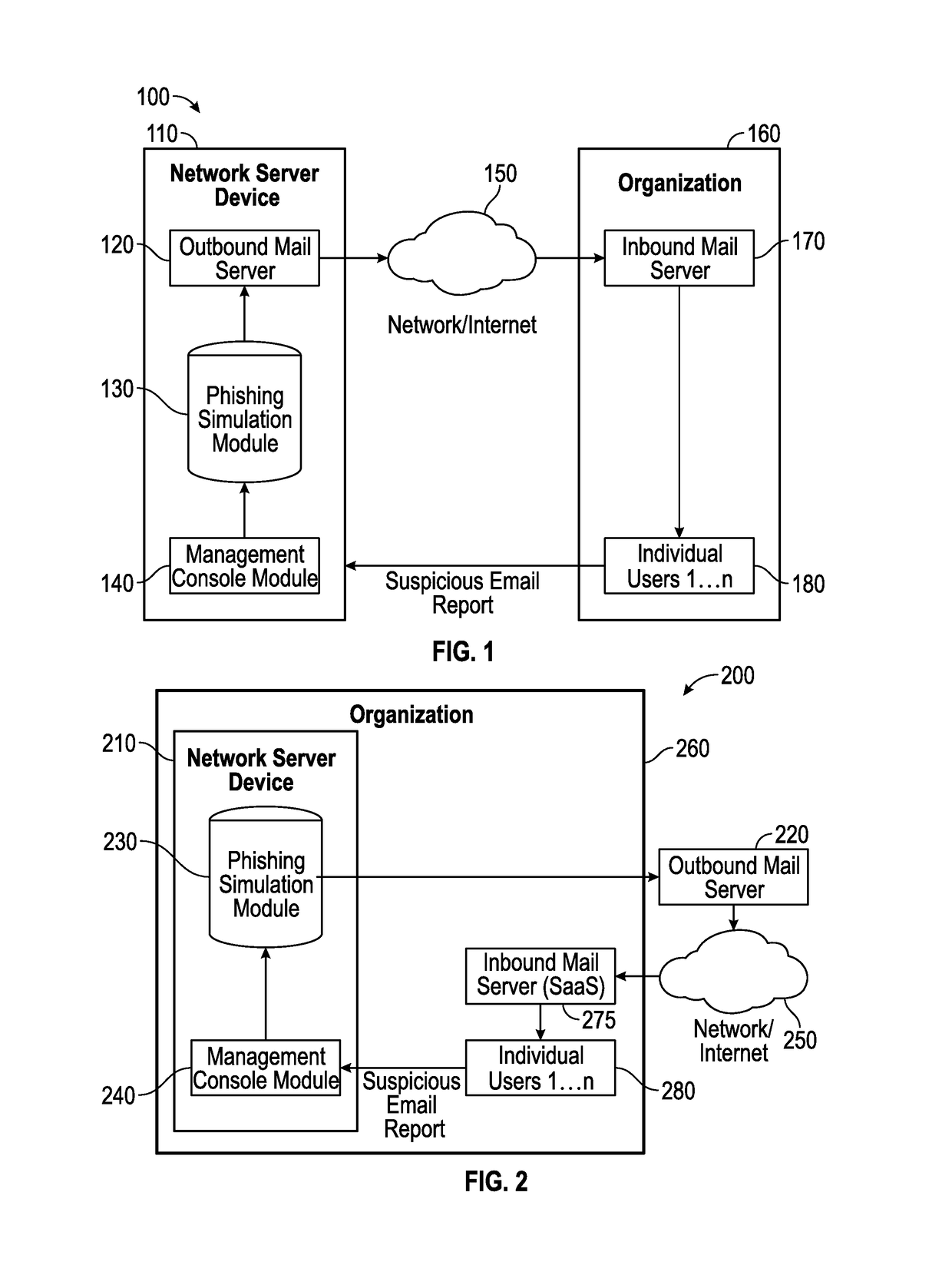
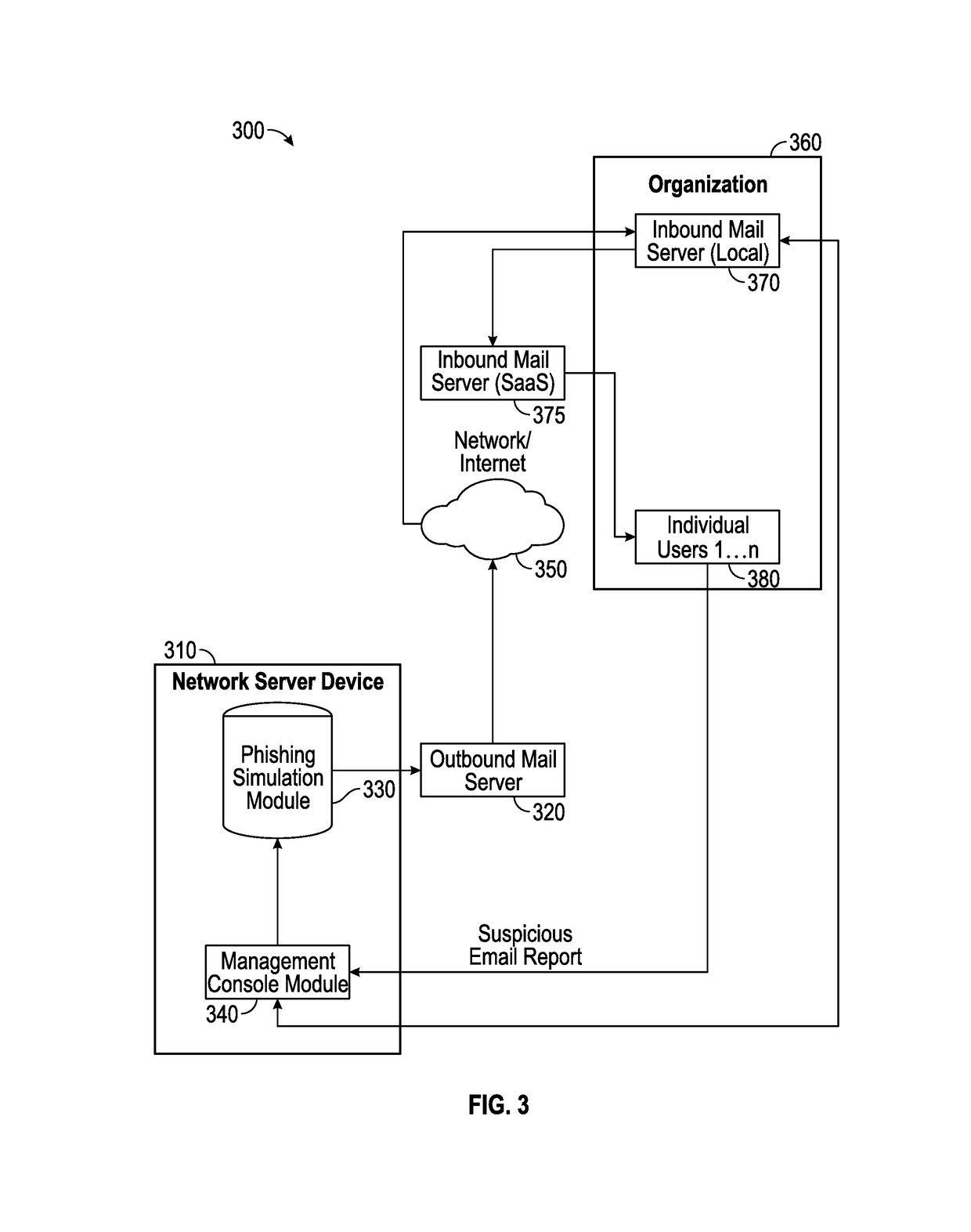
Collaborative phishing attack detection
ActiveUS8719940B1Reduce the possibilityMemory loss protectionError detection/correctionComputer networkRanking
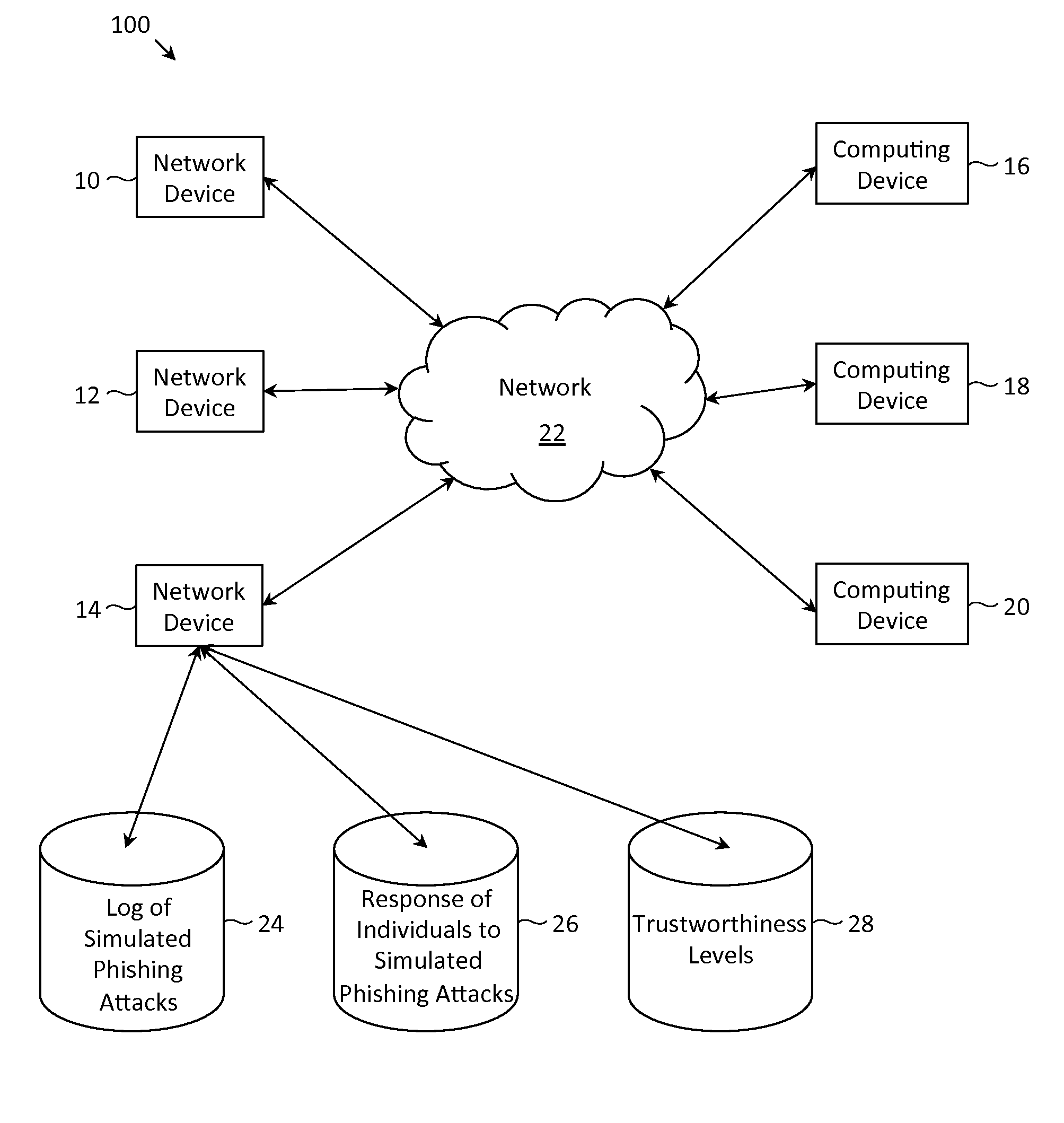
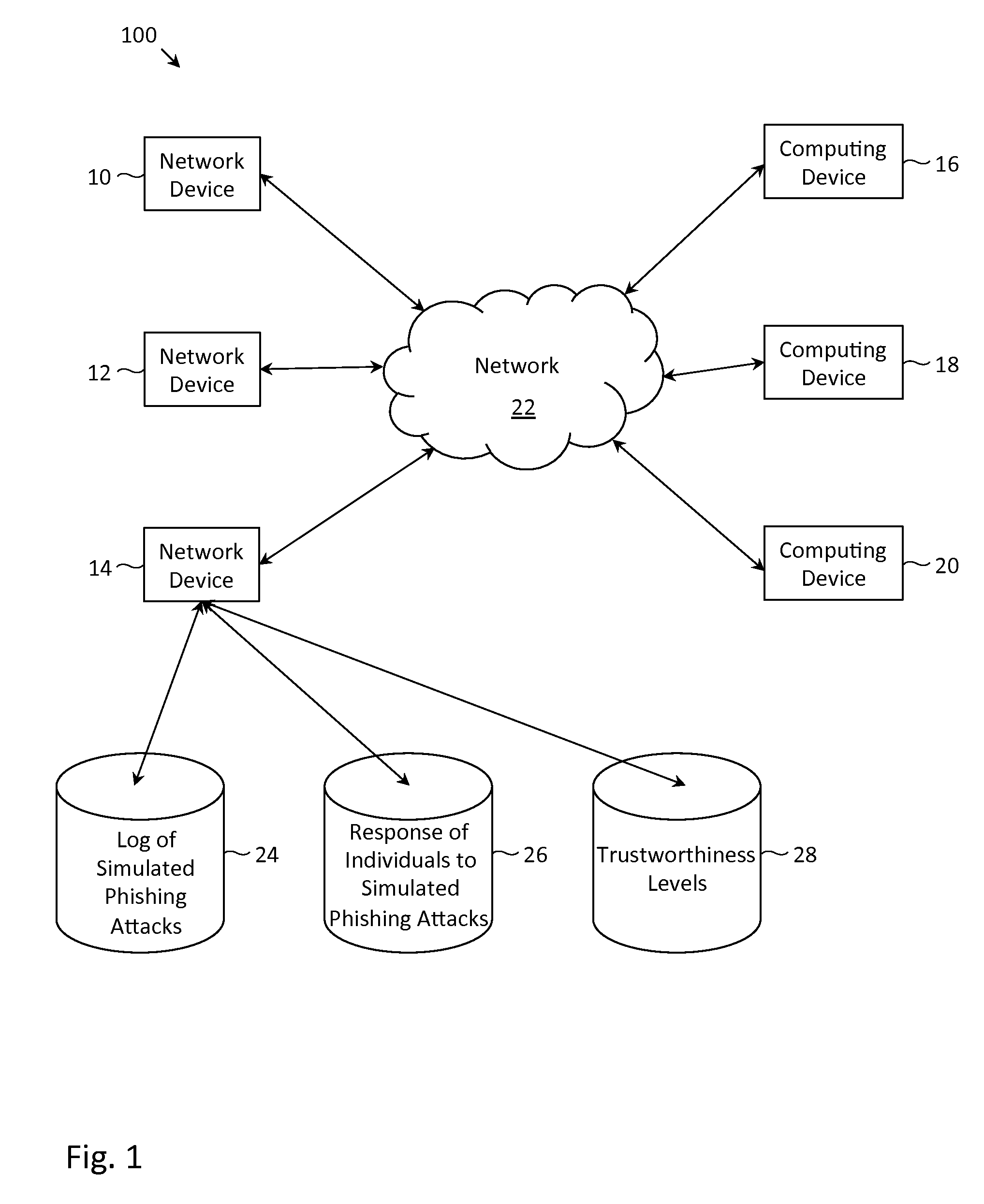
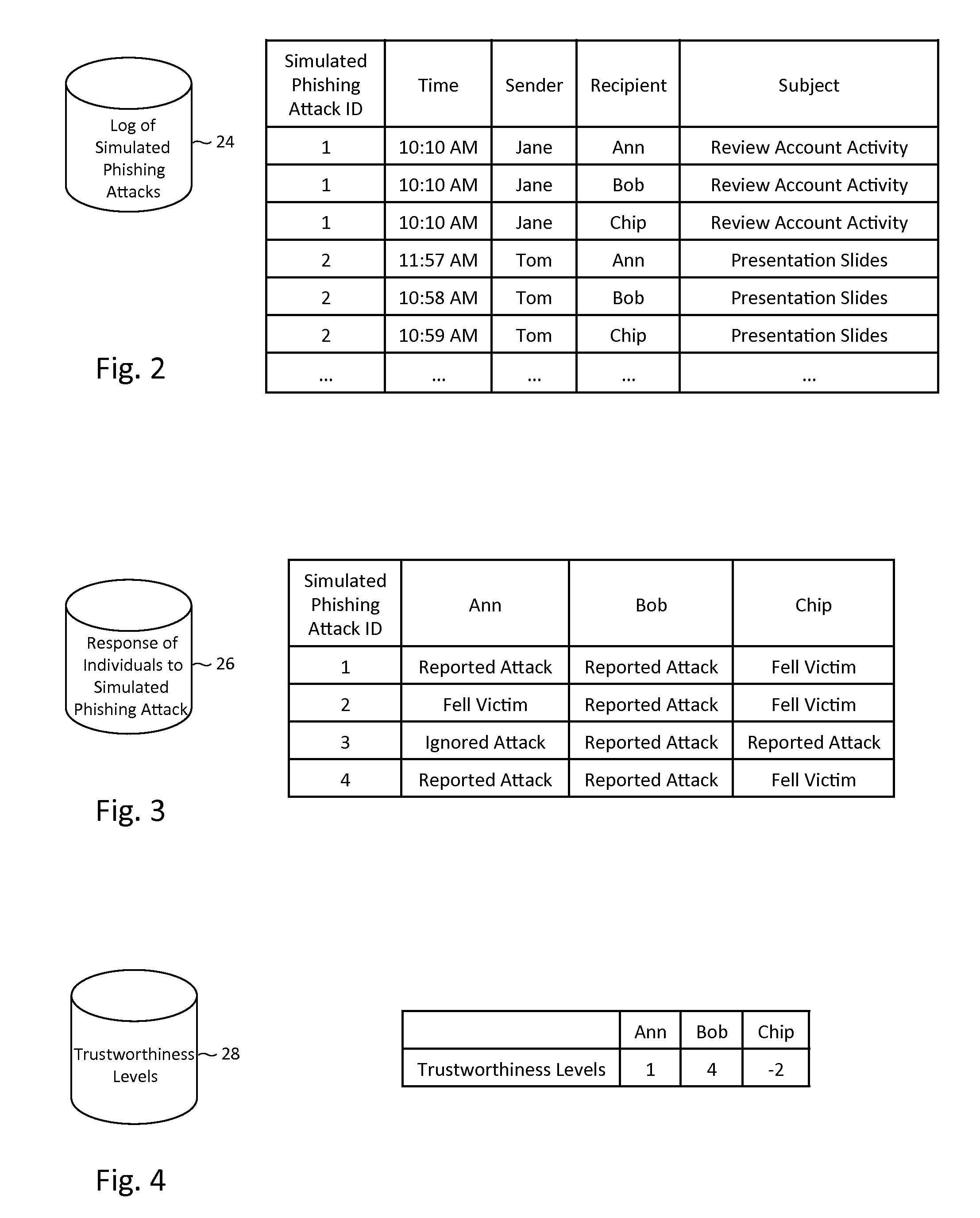
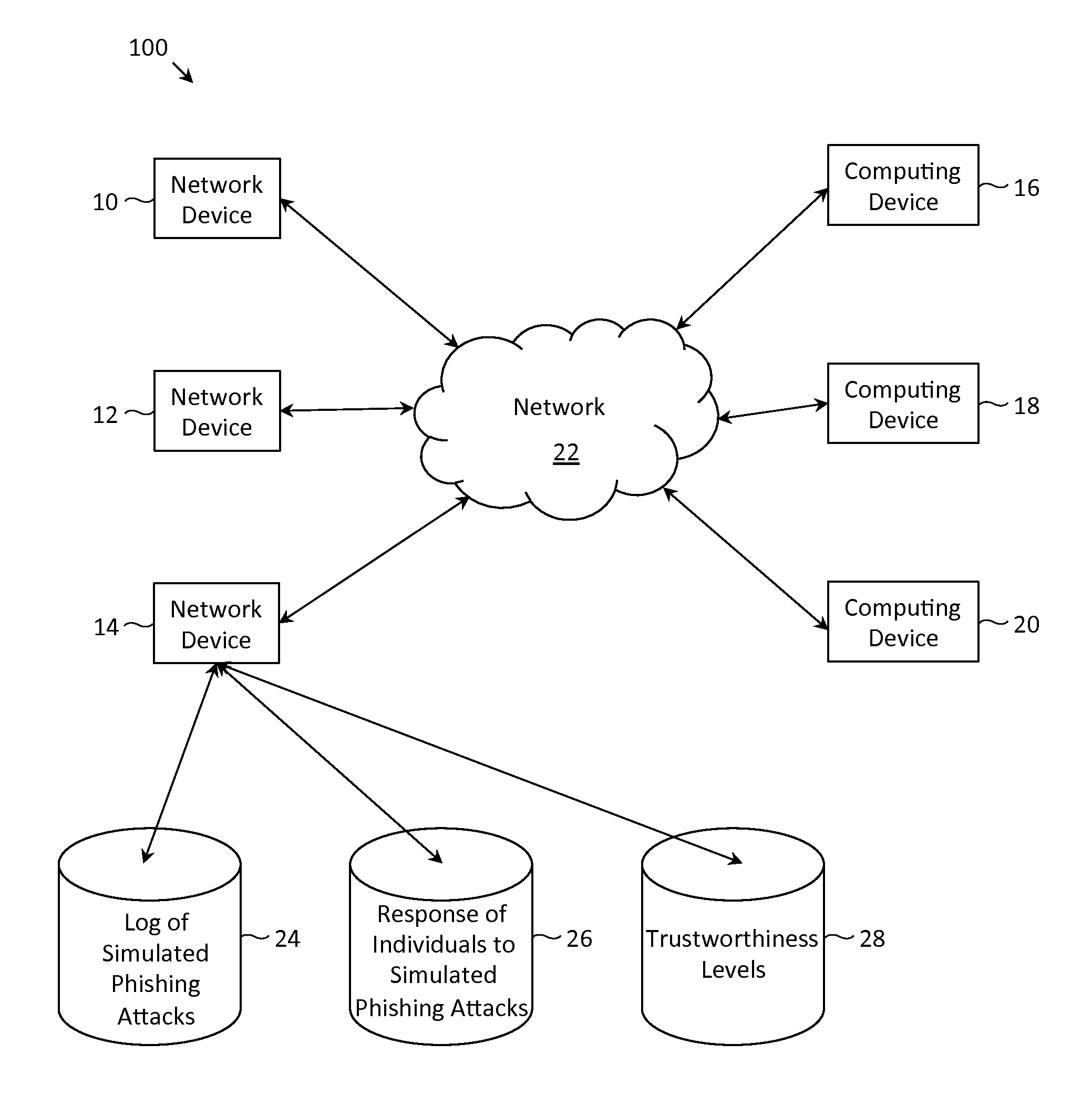
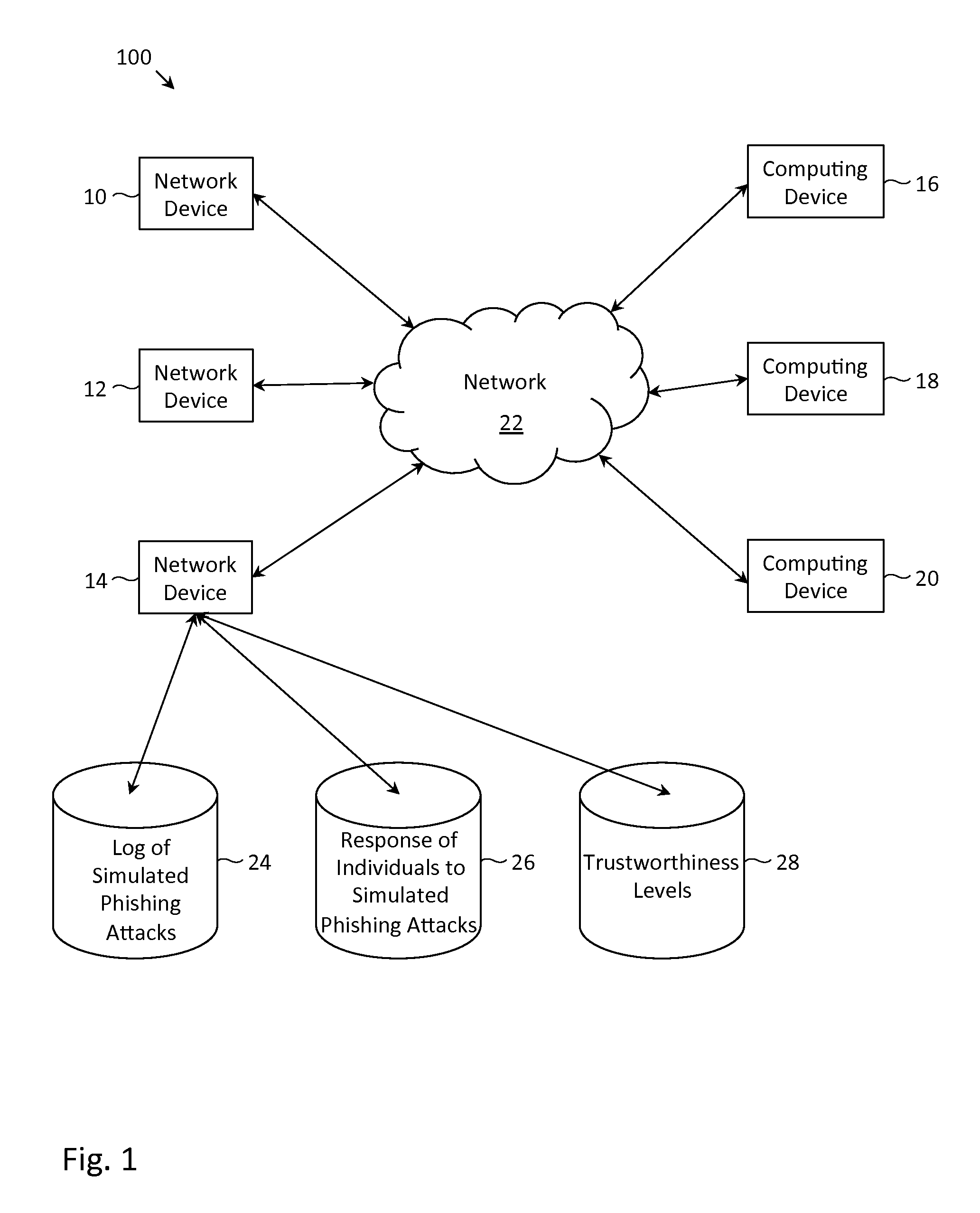
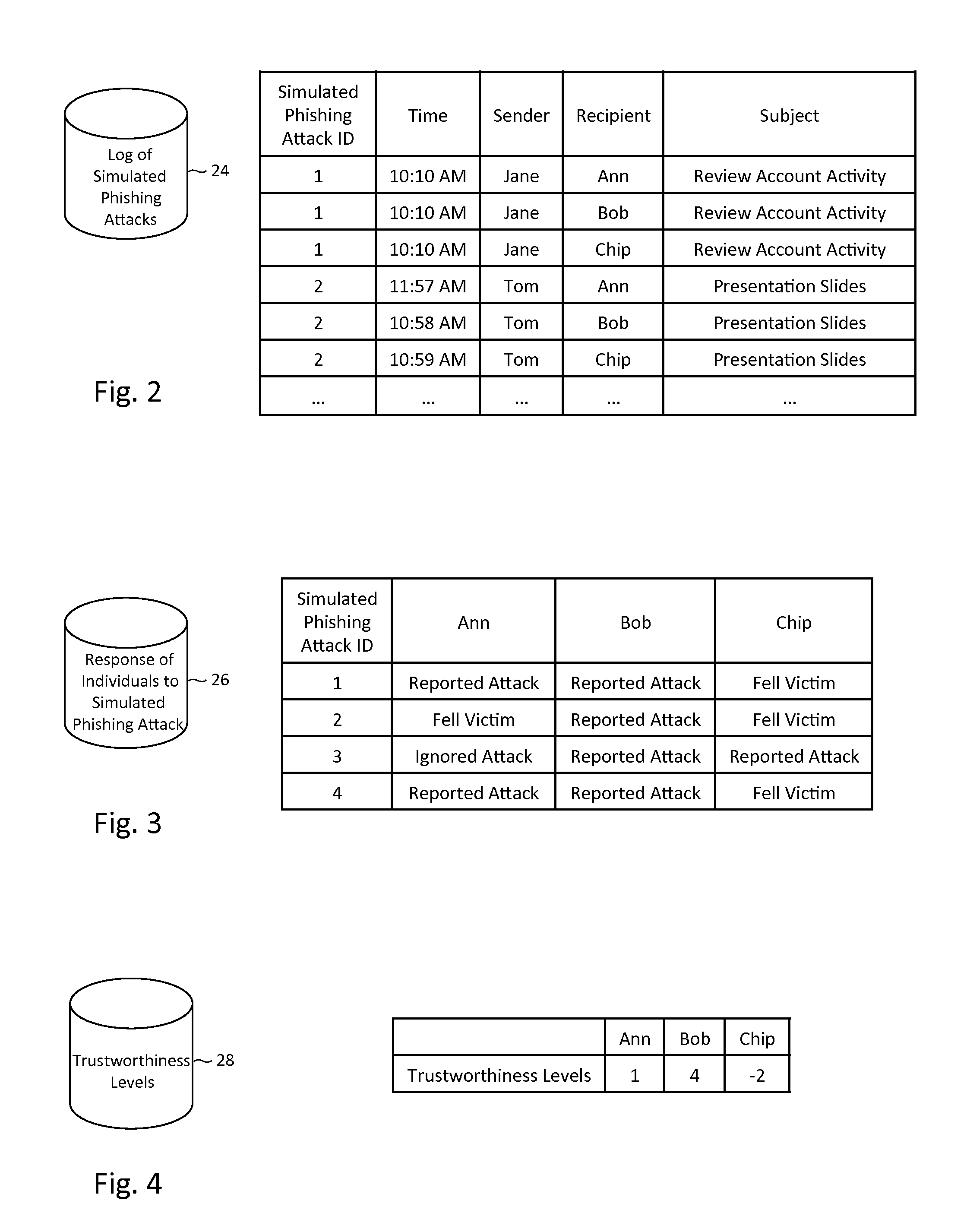
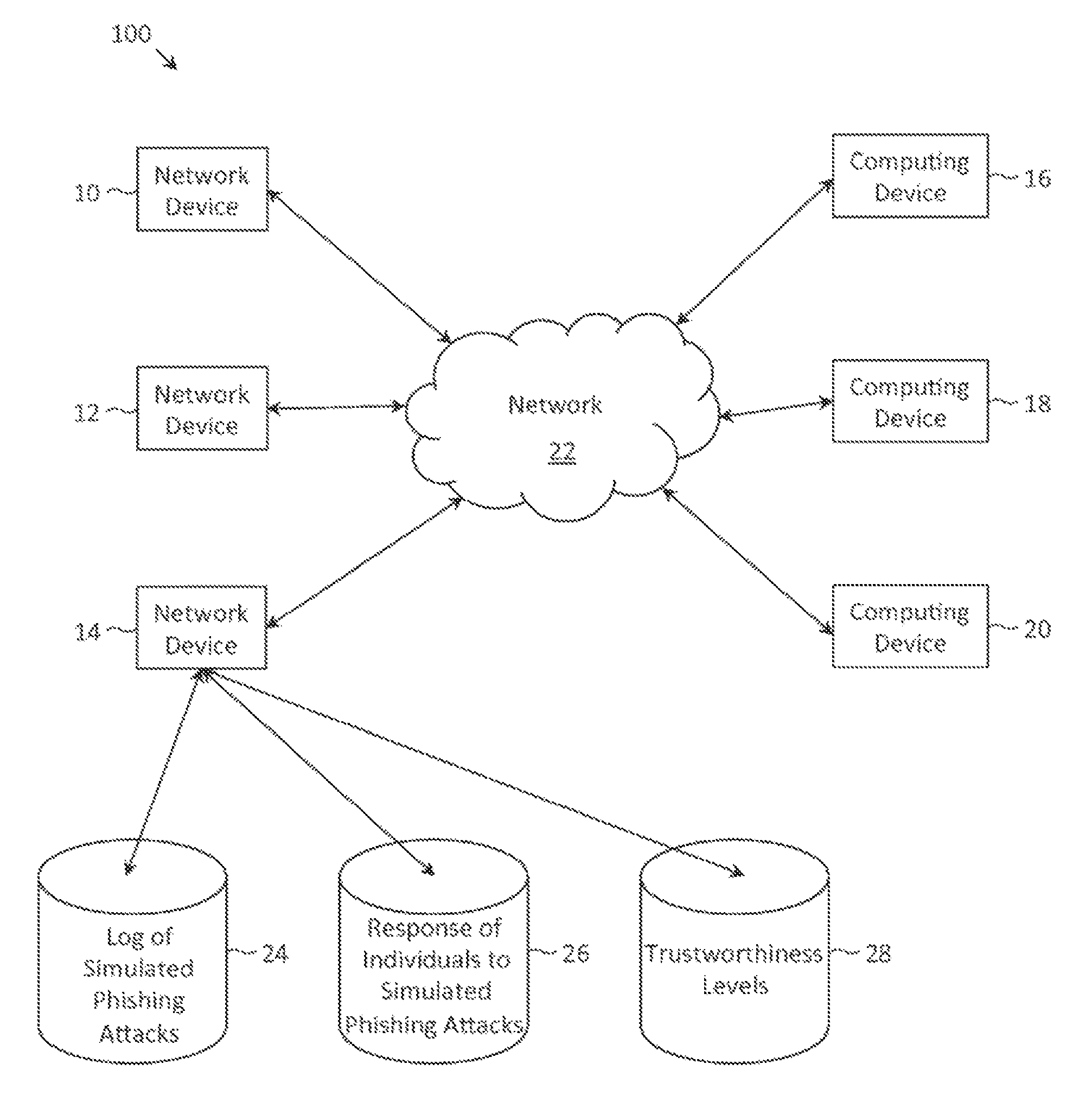
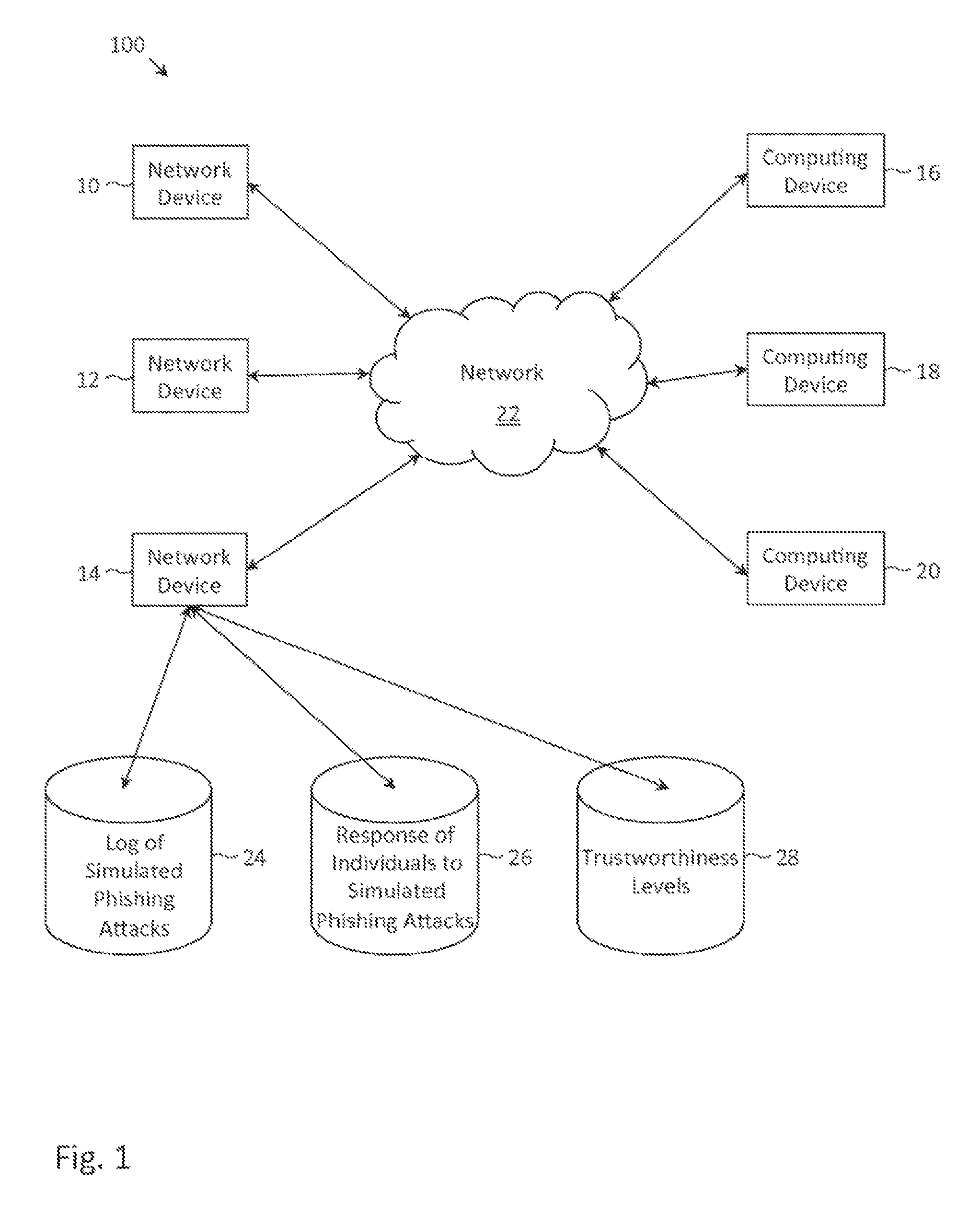
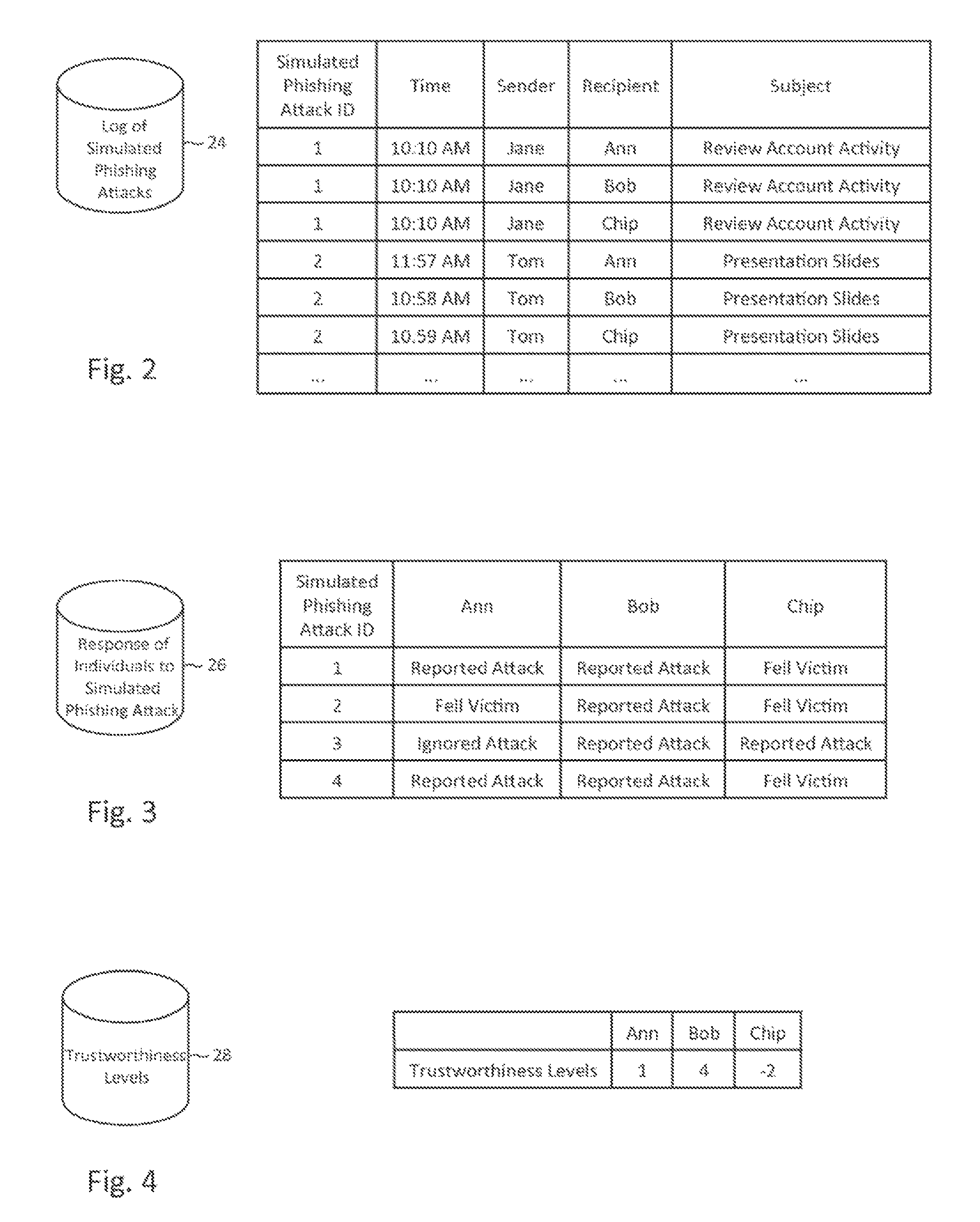
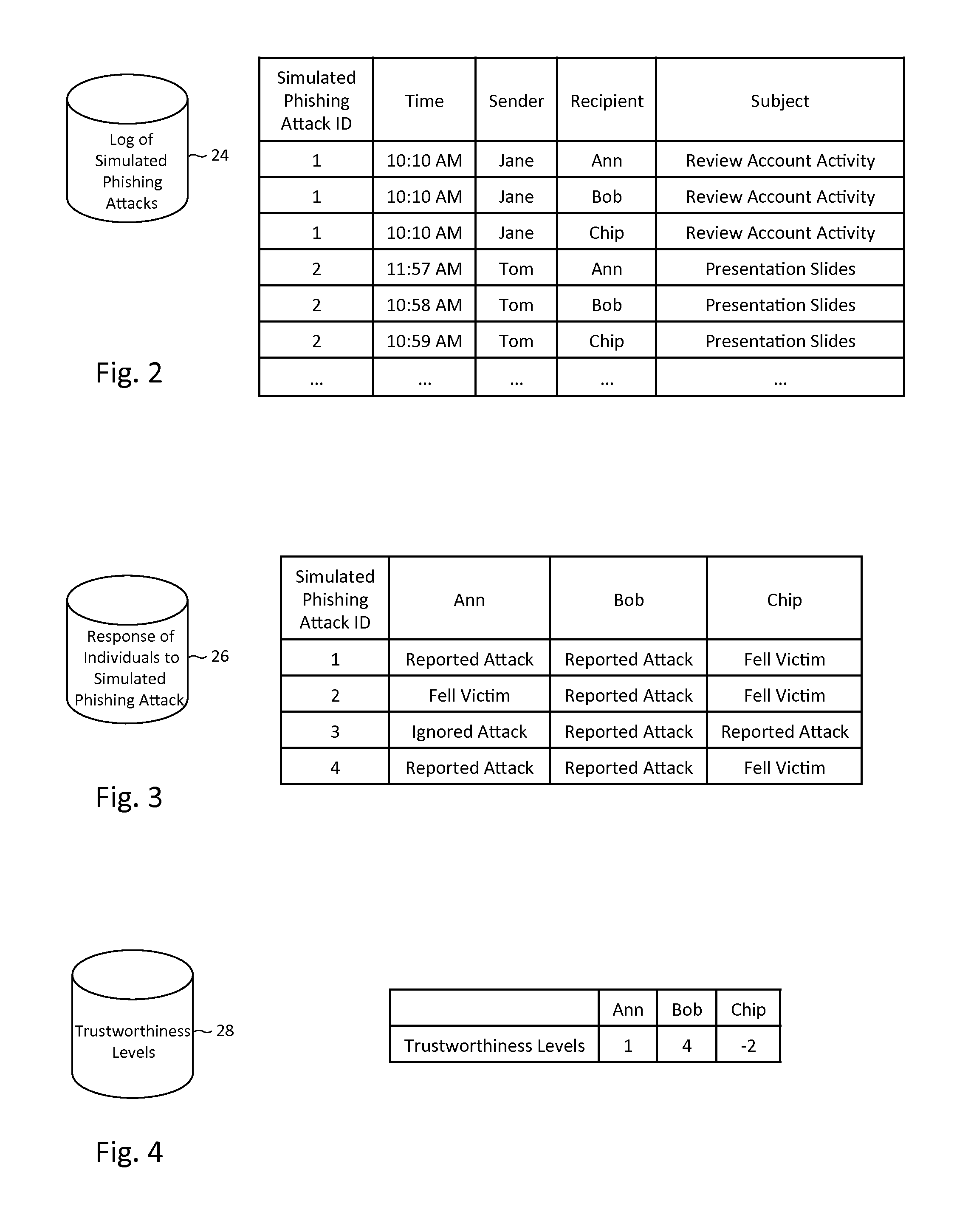
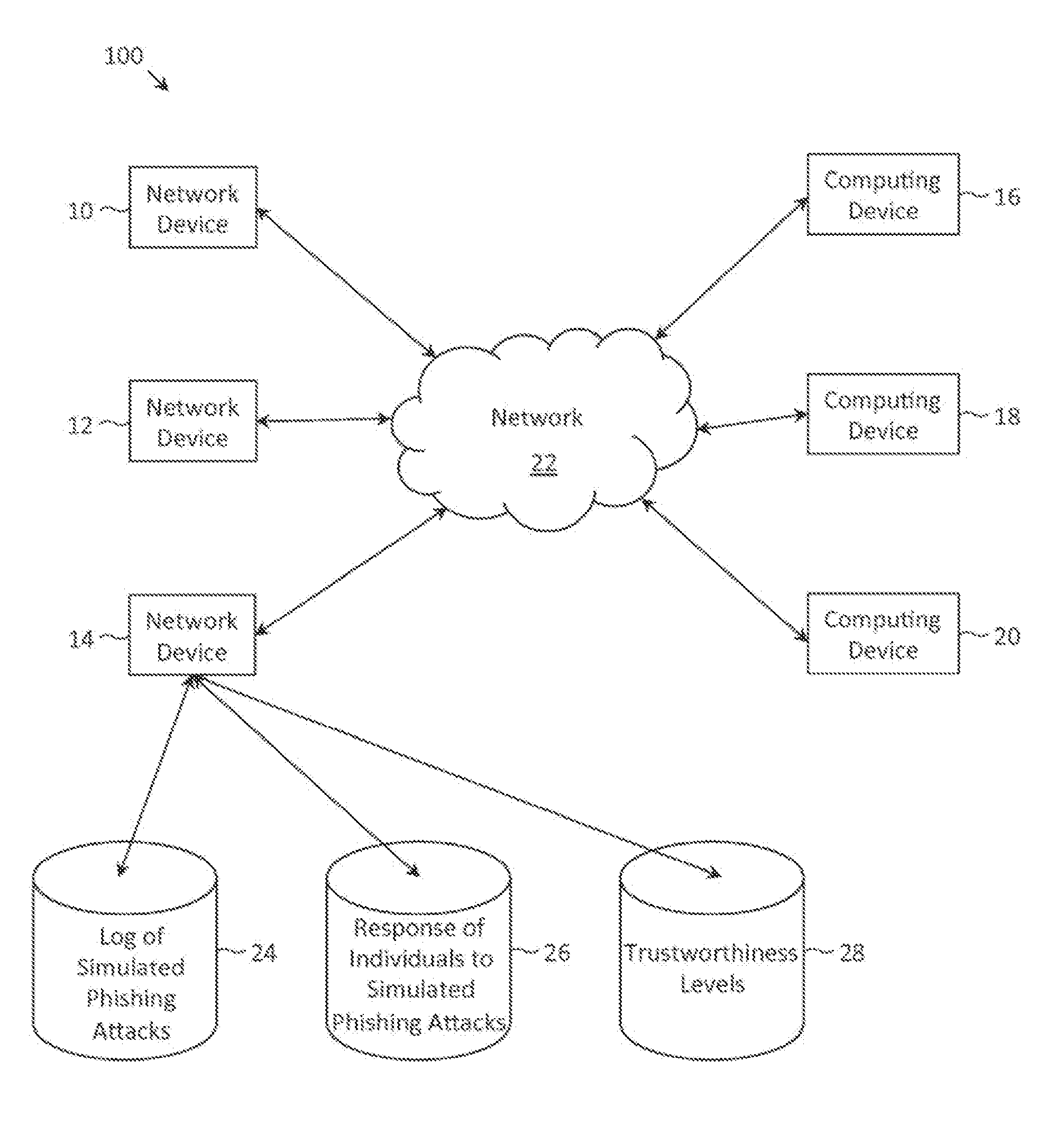
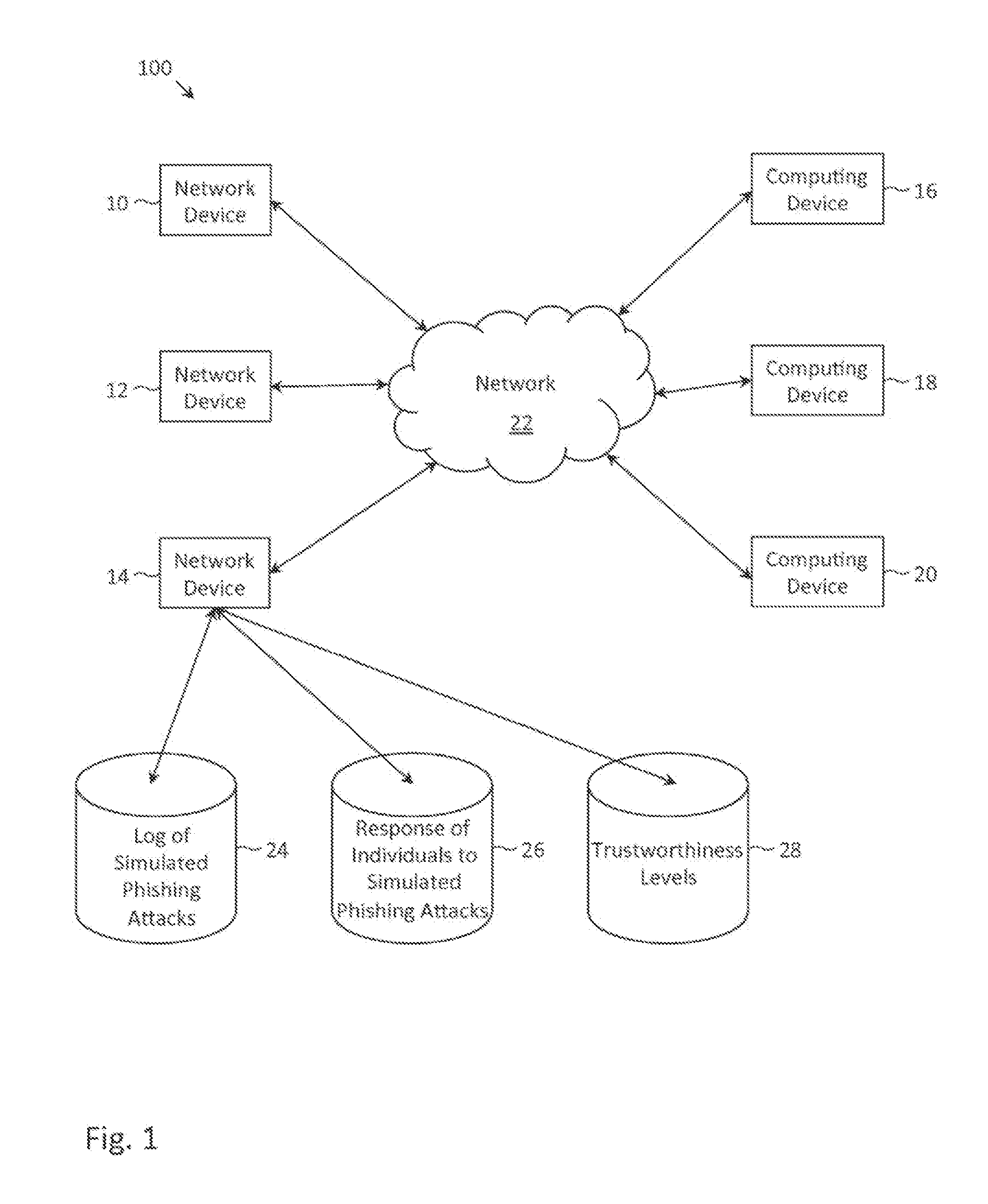
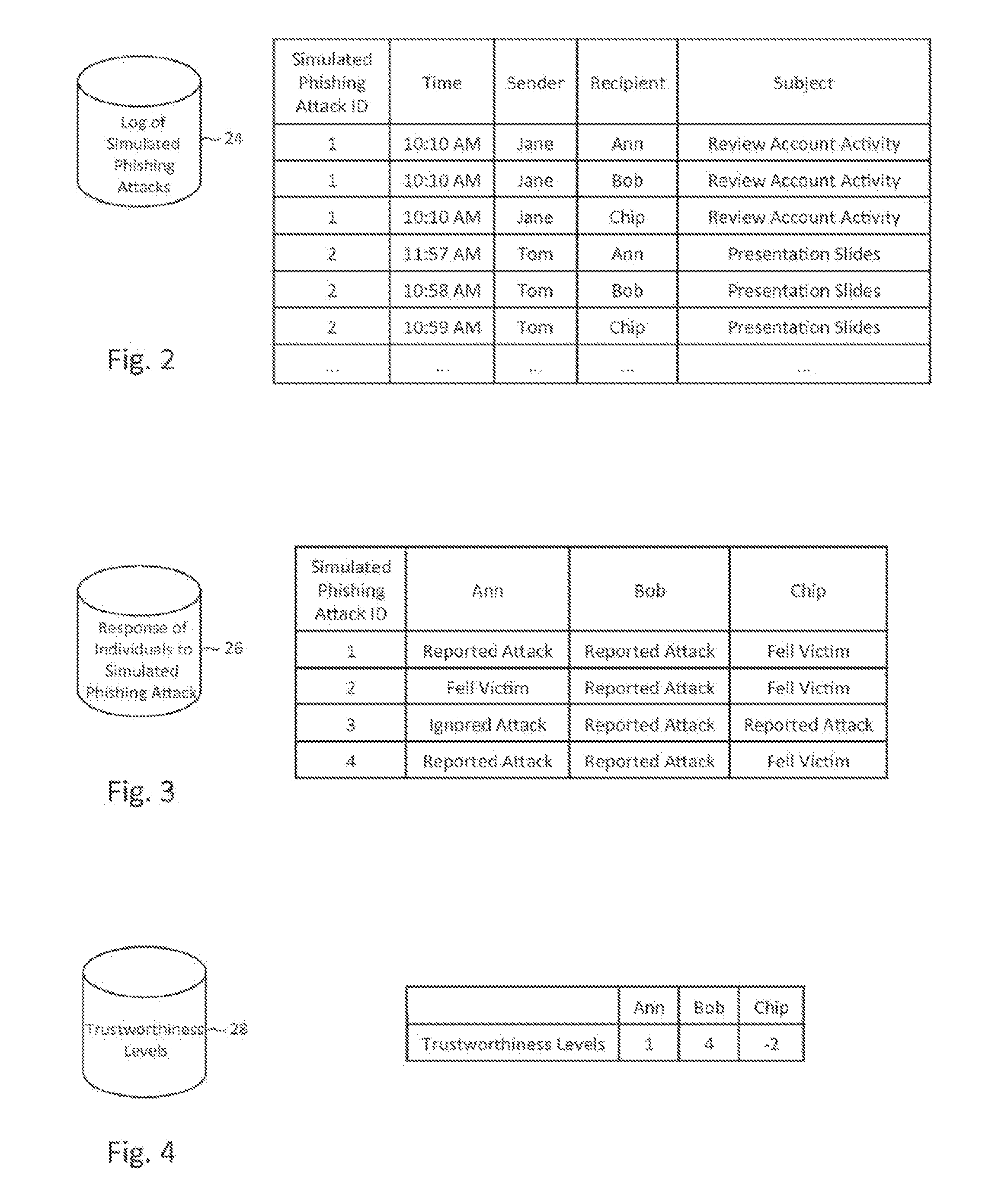
Described herein are methods, network devices and machine-readable storage media for detecting whether a message is a phishing attack based on the collective responses from one or more individuals who have received that message. The individuals may flag the message as a possible phishing attack, and / or may provide a numerical ranking indicating the likelihood that the message is a possible phishing attack. As responses from different individuals may have a different degree of reliability, each response from an individual may be weighted with a corresponding trustworthiness level of that individual, in an overall determination as to whether a message is a phishing attack. A trustworthiness level of an individual may indicate a degree to which the response of that individual can be trusted and / or relied upon, and may be determined by how well that individual recognized simulated phishing attacks.
Owner:COFENSE INC
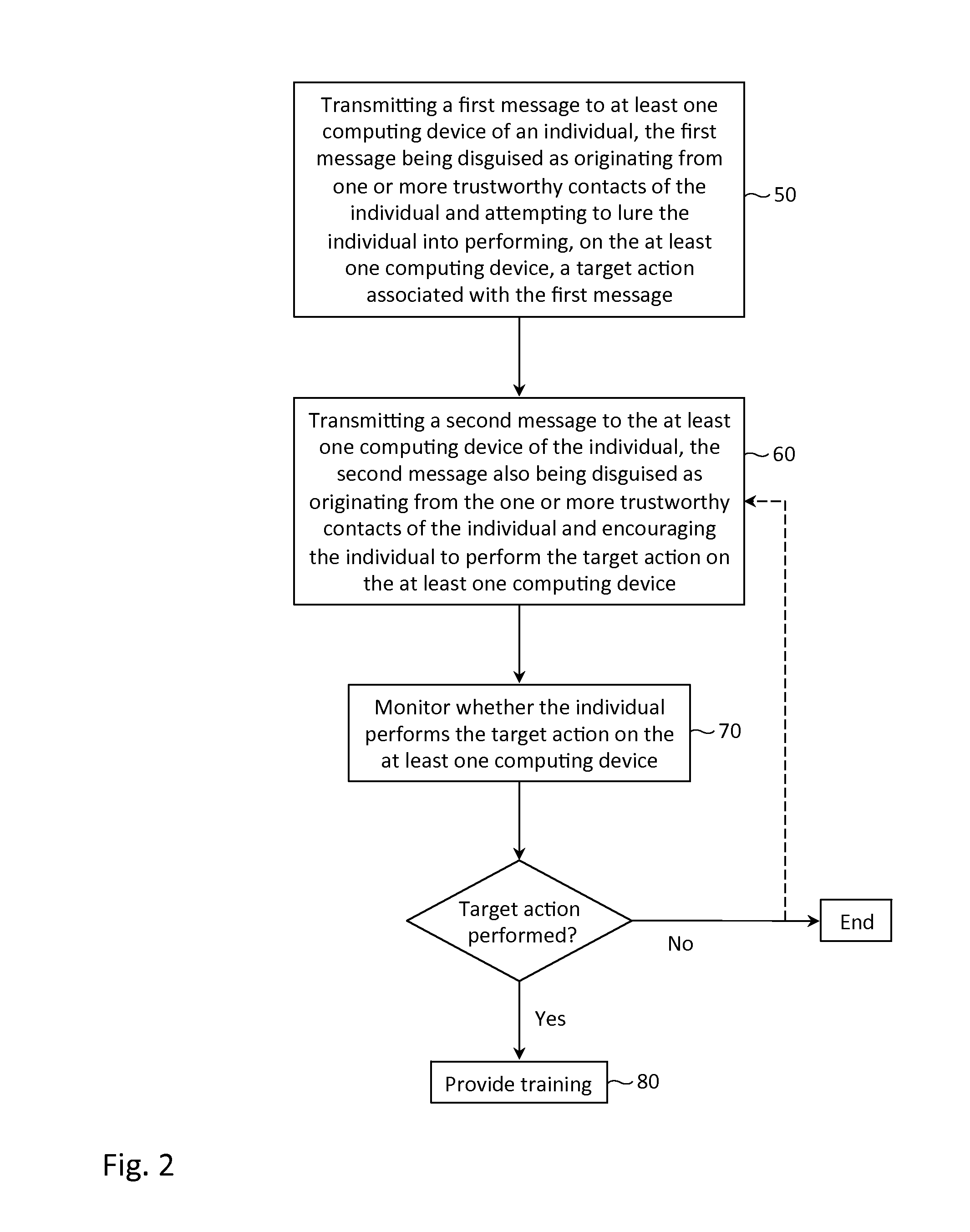
Simulated phishing attack with sequential messages
InactiveUS8615807B1Reduce the possibilityMemory loss protectionError detection/correctionTarget–actionComputer science
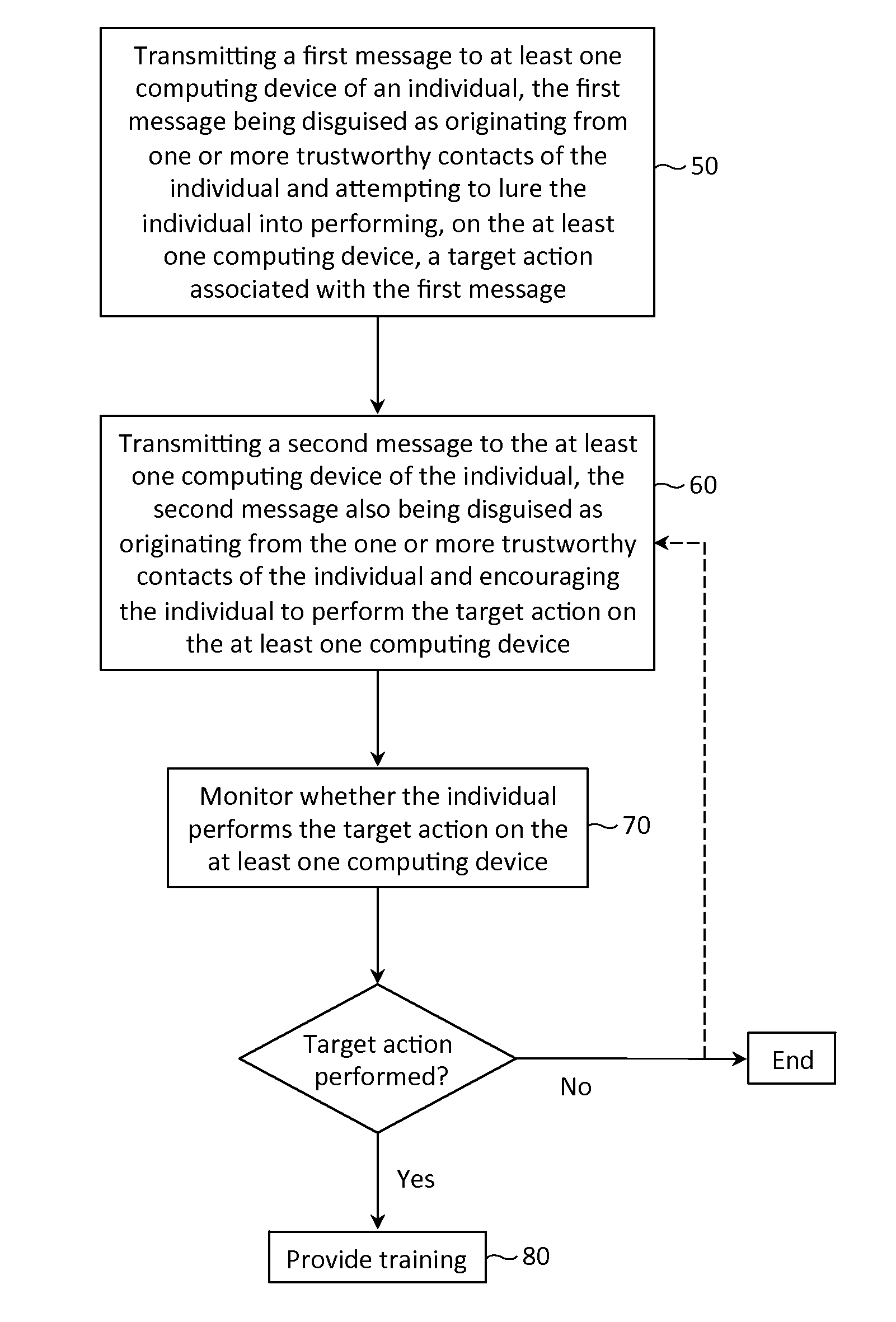
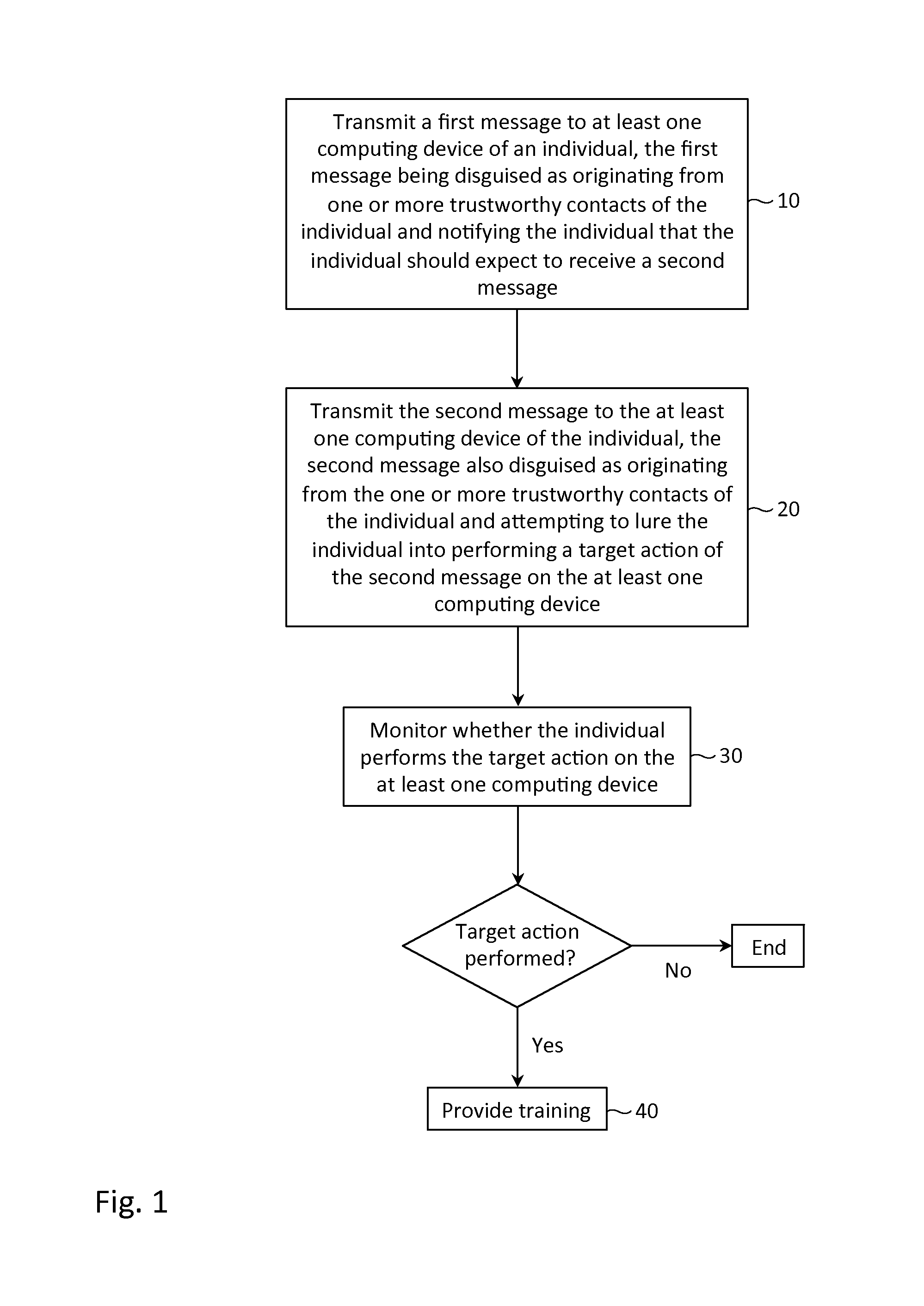
Described herein are methods, network devices and machine-readable storage media for conducting simulated phishing attacks on an individual so as to educate the individual about the various ways in which phishing attacks may be disguised. Specifically described is a simulated phishing attack involving a sequence of messages. At least one of the messages has an associated target action that would ordinary, if the attack were an actual phishing attack, result in the individual's personal information and / or computing device becoming compromised. In the simulated phishing attack, no malicious action is actually performed. At least one of the other messages is designed to draw attention to the message with the target action.
Owner:COFENSE INC
Suspicious message processing and incident response
ActiveUS20160301705A1Improve scoreReduce the overall heightData switching networksSpecial data processing applicationsMessage processingComputer science
The present invention relates to methods, network devices, and machine-readable media for an integrated environment for automated processing of reports of suspicious messages, and furthermore, to a network for distributing information about detected phishing attacks.
Owner:COFENSE INC
Collaborative phishing attack detection
ActiveUS9398038B2Reduce the possibilityUser identity/authority verificationComputer security arrangementsComputer networkInternet privacy
Owner:COFENSE INC
Methods and systems for preventing malicious use of phishing simulation records
ActiveUS8910287B1Effective attackMemory loss protectionError detection/correctionElectronic mailVulnerability
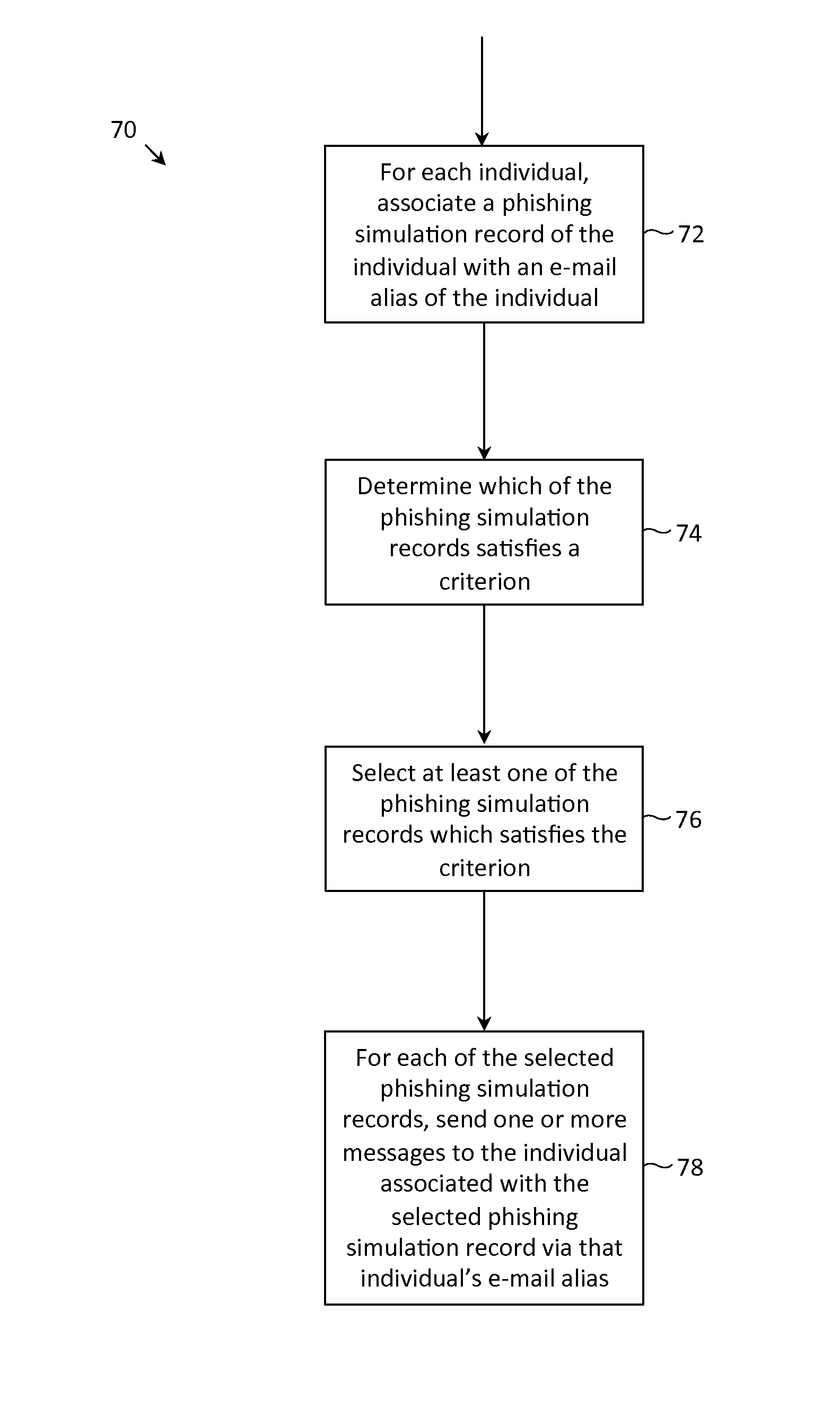
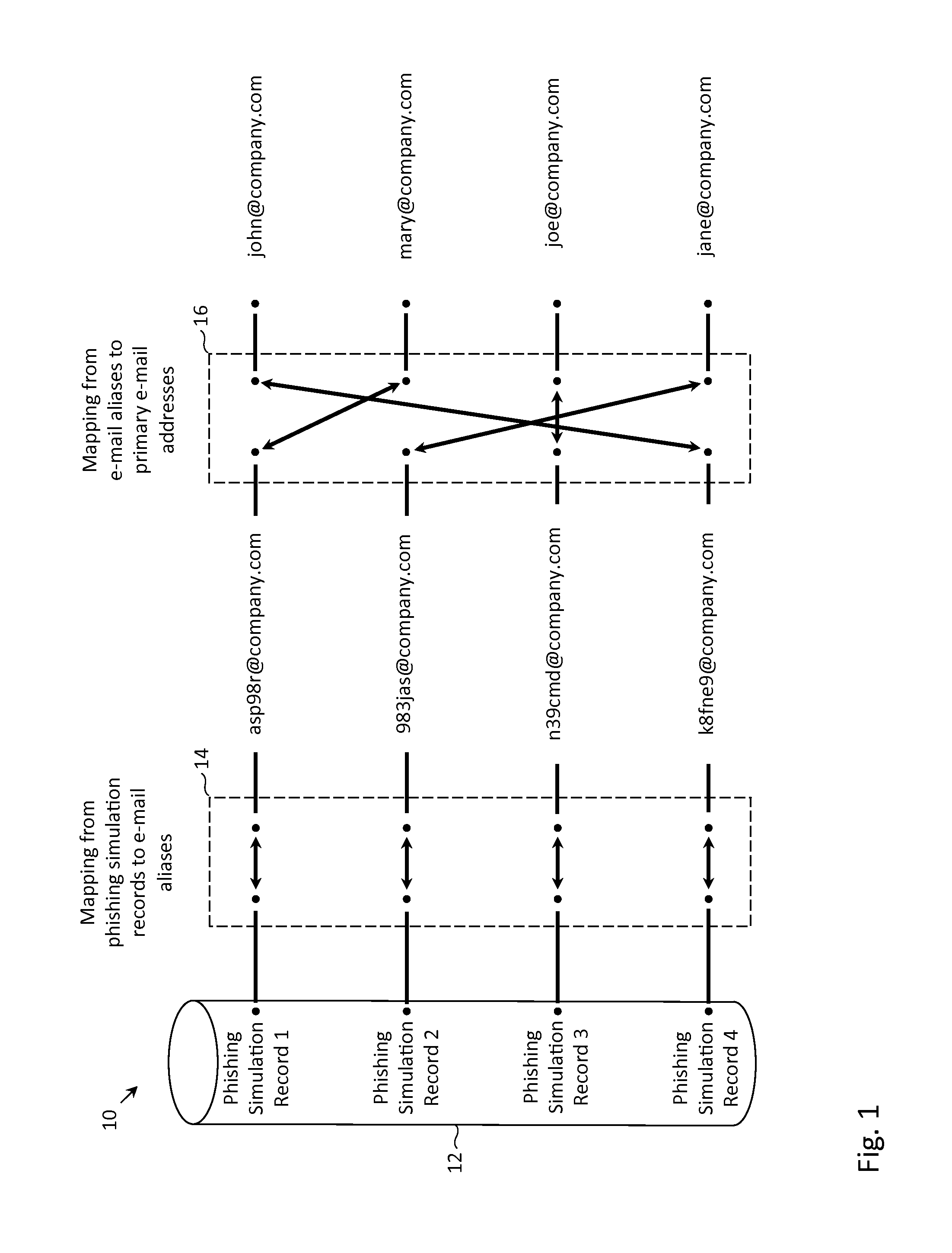
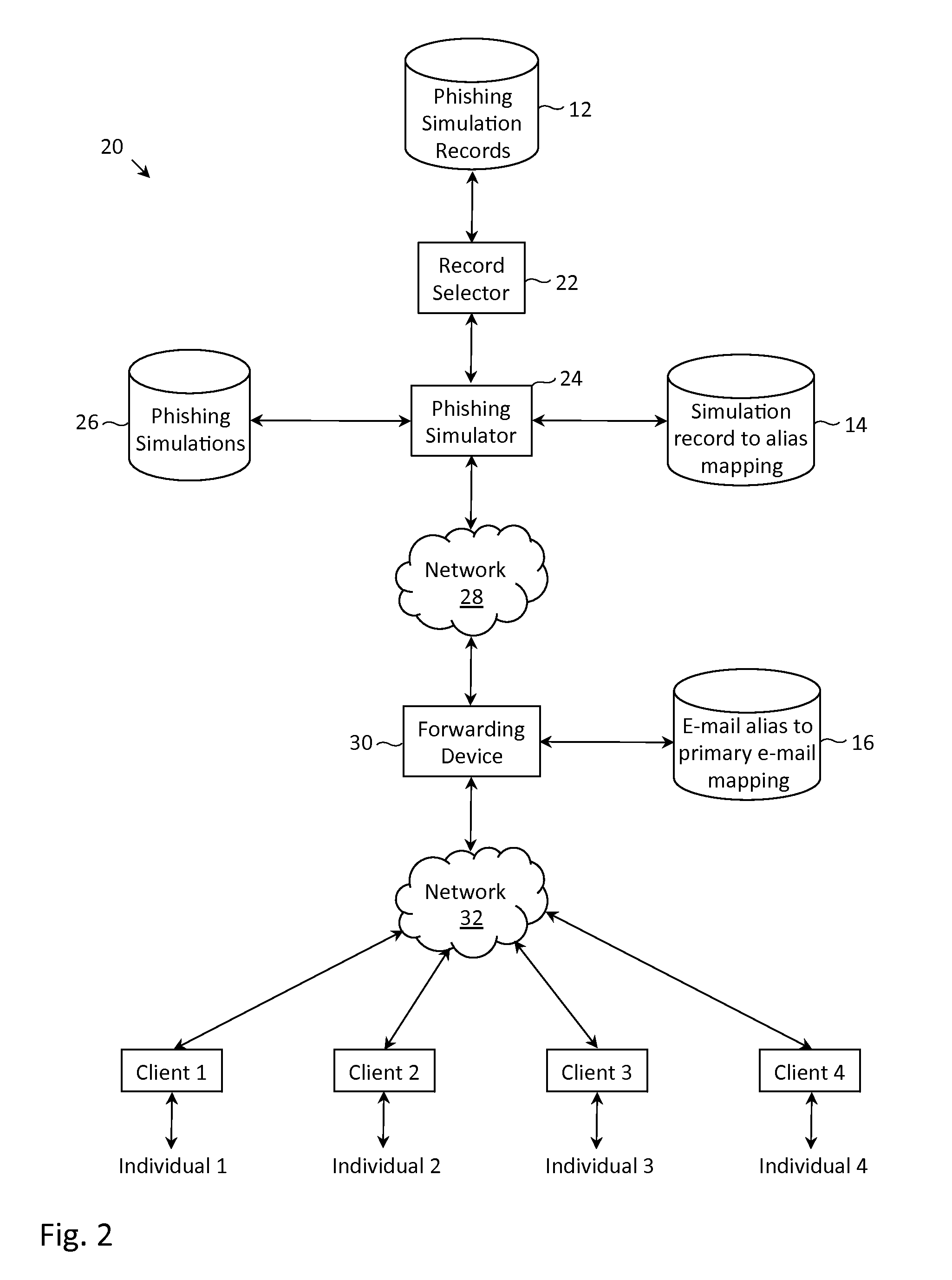
Described herein are methods, network devices and machine-readable media for preventing the malicious use of phishing simulation records. Phishing simulation records often times can reveal which individuals are most susceptible to phishing attacks. In the event that an attacker gains access to these records, the attacker can exploit such information to send phishing attacks to those individuals who are the most susceptible. To address such vulnerabilities, a phishing simulation record of an individual is only associated with an e-mail alias of the individual. Further, such e-mail alias may be deactivated after phishing simulations have been completed. Therefore, even if an attacker were able to identify individuals most susceptible to phishing attacks, the attacker will be unable to send any phishing attacks to those individuals since their e-mail aliases will have been deactivated.
Owner:COFENSE INC
Collaborative phishing attack detection
ActiveUS9325730B2Reduce the possibilityTransmissionInput/output processes for data processingComputer networkRanking
Described herein are methods, network devices and machine-readable storage media for detecting whether a message is a phishing attack based on the collective responses from one or more individuals who have received that message. The individuals may flag the message as a possible phishing attack, and / or may provide a numerical ranking indicating the likelihood that the message is a possible phishing attack. As responses from different individuals may have a different degree of reliability, each response from an individual may be weighted with a corresponding trustworthiness level of that individual, in an overall determination as to whether a message is a phishing attack. A trustworthiness level of an individual may indicate a degree to which the response of that individual can be trusted and / or relied upon, and may be determined by how well that individual recognized simulated phishing attacks.
Owner:COFENSE INC
Collaborative phishing attack detection
ActiveUS20140230061A1Reduce the possibilityMemory loss protectionError detection/correctionComputer networkRanking
Described herein are methods, network devices and machine-readable storage media for detecting whether a message is a phishing attack based on the collective responses from one or more individuals who have received that message. The individuals may flag the message as a possible phishing attack, and / or may provide a numerical ranking indicating the likelihood that the message is a possible phishing attack. As responses from different individuals may have a different degree of reliability, each response from an individual may be weighted with a corresponding trustworthiness level of that individual, in an overall determination as to whether a message is a phishing attack. A trustworthiness level of an individual may indicate a degree to which the response of that individual can be trusted and / or relied upon, and may be determined by how well that individual recognized simulated phishing attacks.
Owner:COFENSE INC
Suspicious message processing and incident response
ActiveUS20170237776A1Improve acuityShorten the timeTransmissionSpecial data processing applicationsMessage processingPhishing attack
Owner:COFENSE INC
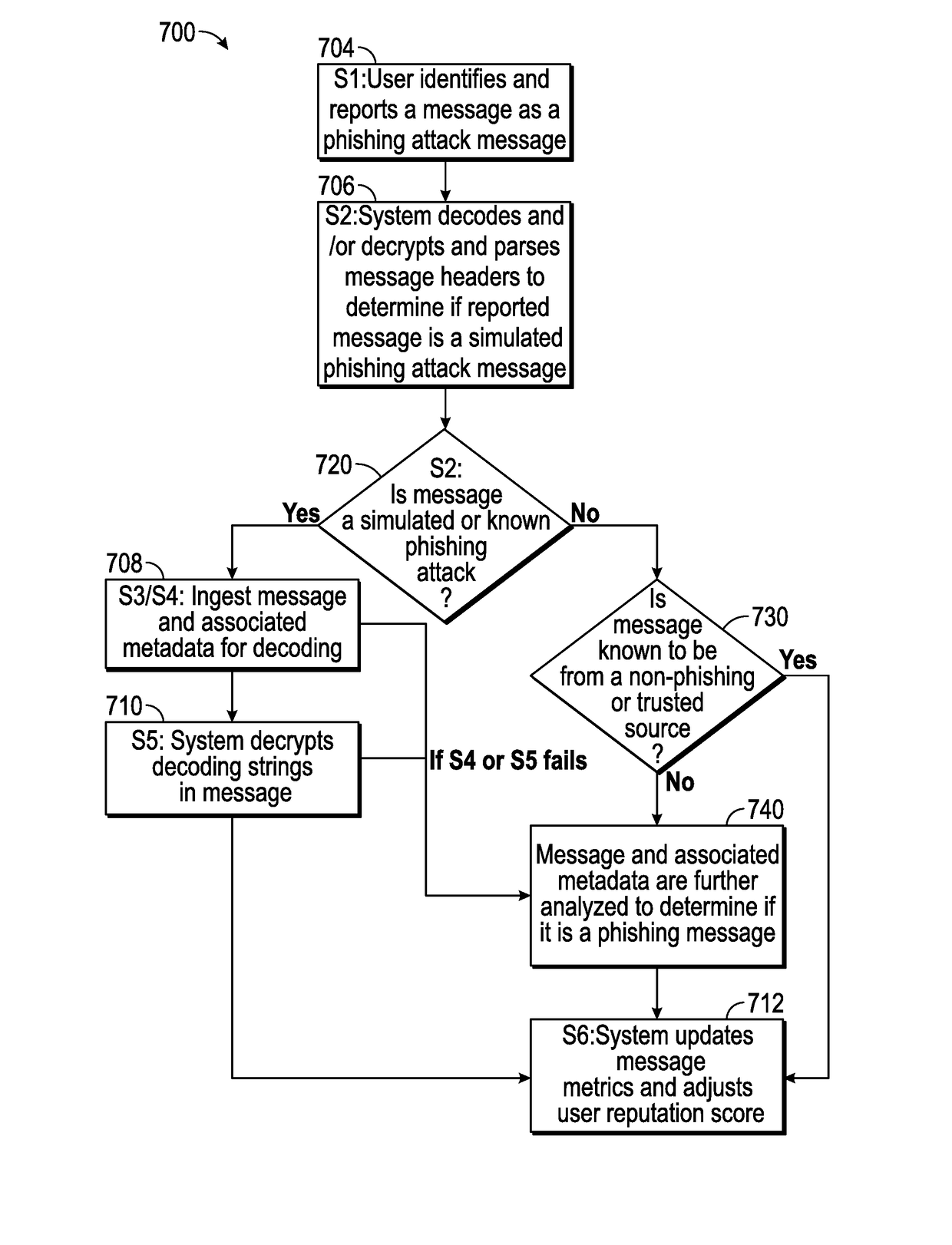
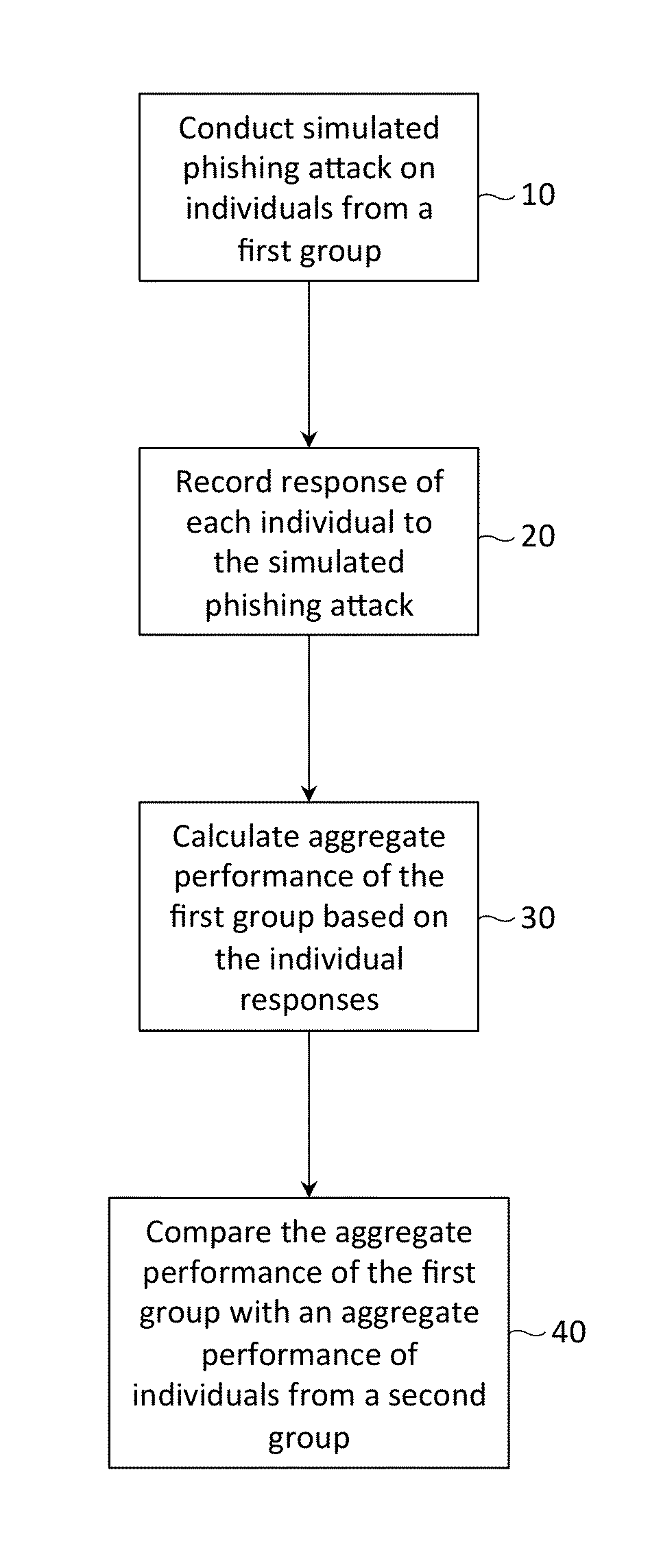
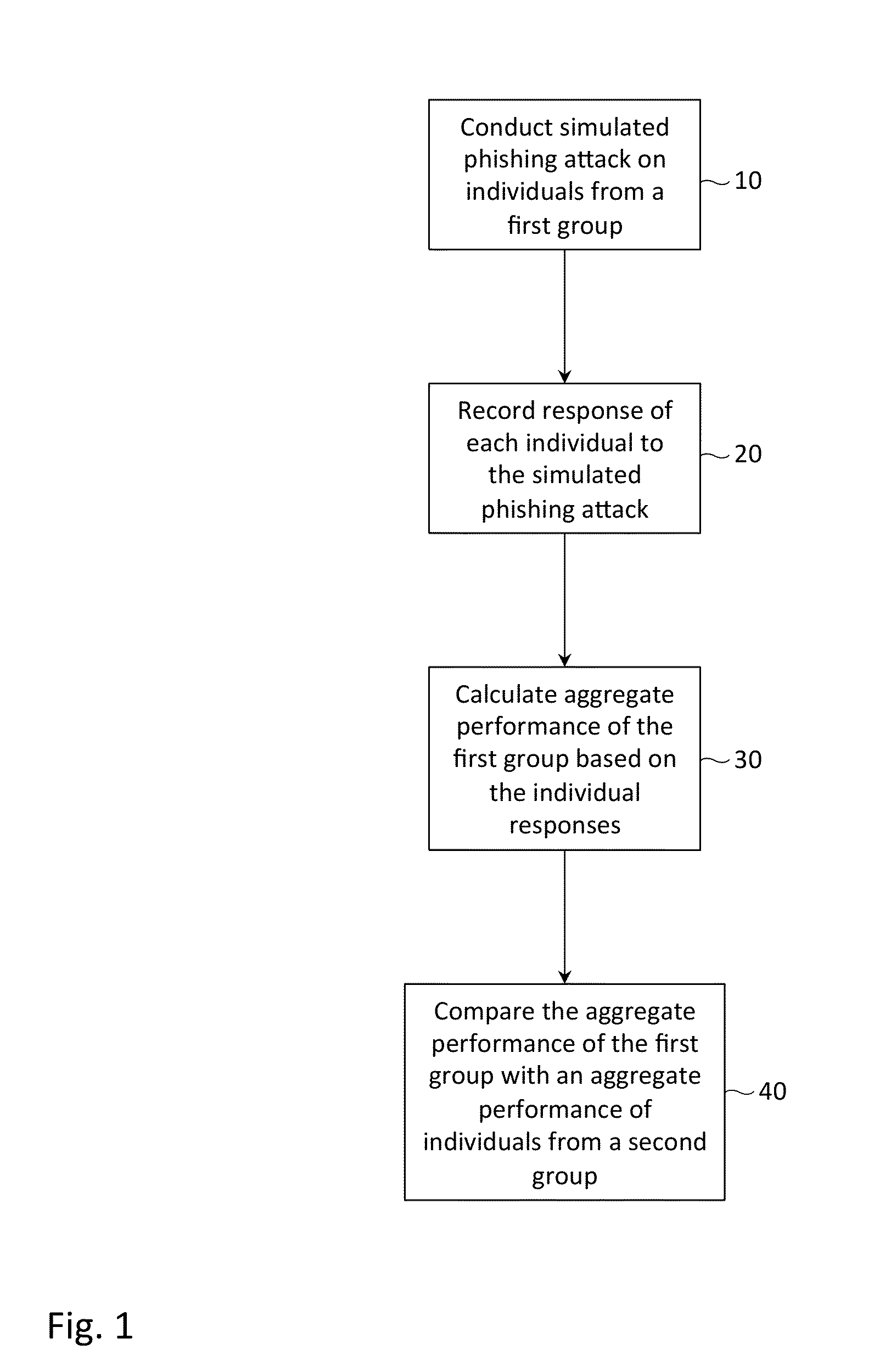
Performance benchmarking for simulated phishing attacks
ActiveUS20140230065A1Reduce the possibilityMemory loss protectionError detection/correctionComputer scienceStandardization
Described herein are methods, network devices and machine-readable media for conducting a simulated phishing attack on a first group of individuals, and performing an analysis of the group's performance to the simulated attack. In the analysis, an aggregate performance of the first group is compared with an aggregate performance of individuals from a second group. Standardizing the simulated phishing attacks for individuals from both the first and second groups is necessary in order for the performance of the first group to be fairly or meaningfully compared to the performance of the second group. To ensure uniformity in the simulated phishing attacks, messages thereof may be constructed from template messages, the template messages having placeholders for individual-specific and company-specific information.
Owner:COFENSE INC
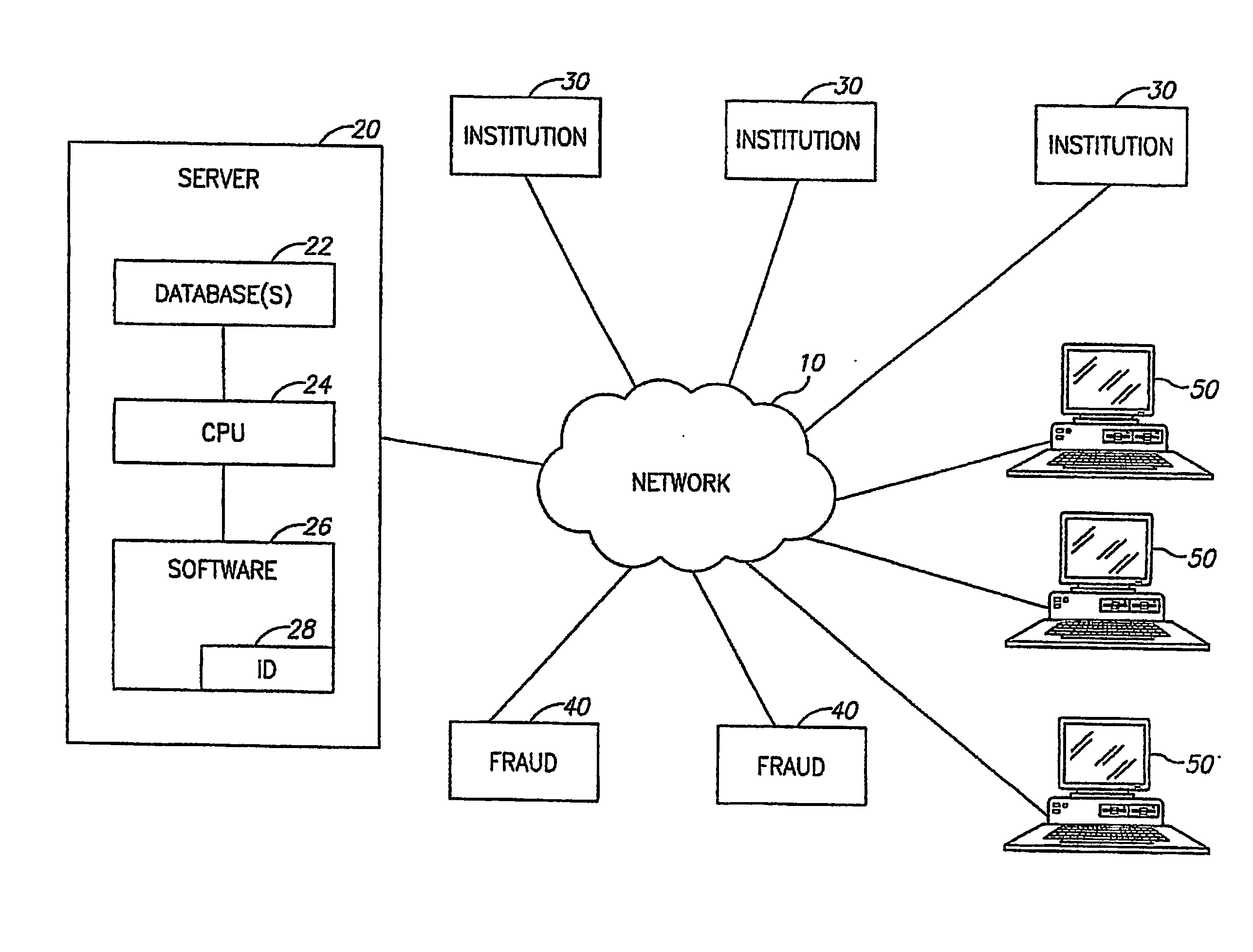
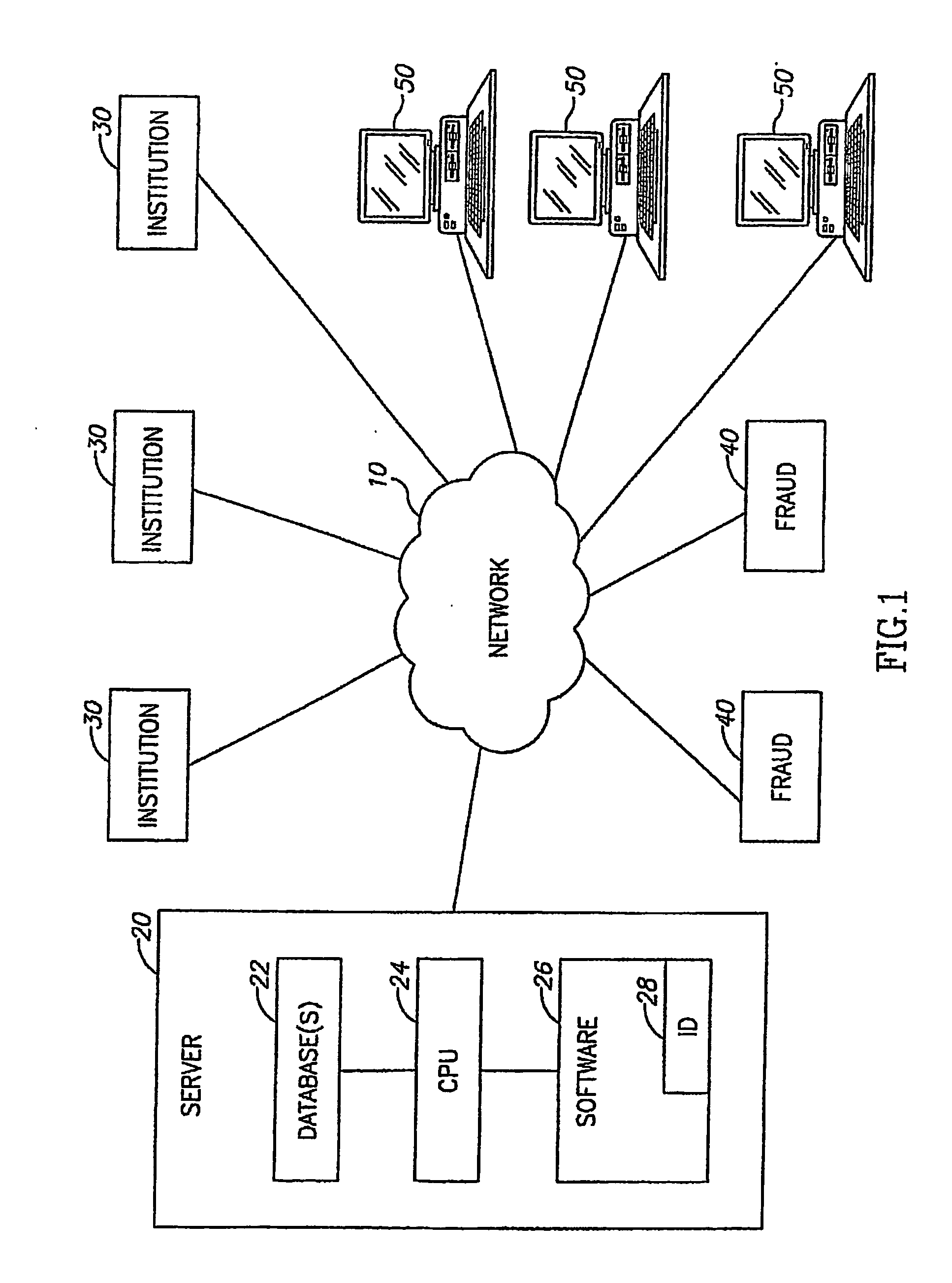
System and Method of Addressing Email and Electronic Communication Fraud
ActiveUS20080052359A1Raise the possibilityReducing negative consequenceMultiple digital computer combinationsTransmissionInternet privacyElectronic communication
A system and method may respond to a fraudulent attack, such as a Phishing attack. The system and method may send a number of responses to party committing fraud, the responses designed to mimic the responses to a Phishing attack. The responses may include codes or marked information designed to entrap or detect the party committing fraud.
Owner:EMC IP HLDG CO LLC
Systems and methods for performing or creating simulated phishing attacks and phishing attack campaigns
ActiveUS20170251009A1Risk minimizationMalicious action is preventedTransmissionElectronic mailData library
A method for establishing a campaign for a simulated phishing attack includes receiving, via a campaign manager, specification of a plurality of parameters for a campaign including at least an identifier of a campaign and identification of users to which to send the campaign, establishing, via the campaign manager, a type of exploit for the campaign and one or more types of data to collect via the type of exploit, storing, by the campaign manager, the campaign comprising the plurality of parameters, and identifying, by a simulation server, the campaign stored in the database to create a simulated phishing email, to be sent to email accounts of the users, using the plurality of parameters of the campaign, wherein the simulated phishing email is to be created to have a link to a landing page comprising the type of exploit and configured to collect the one or more types of data.
Owner:KNOWBE4 INC
Anti-Phishing System
InactiveUS20080141342A1Digital data processing detailsComputer security arrangementsNetwork addressingThe Internet
The present invention provides both method and apparatus for enhancing a user's network security. For example, it may be used to prevent phishing attacks being effected via the internet. A number of legitimate network addresses along with associated data are stored. Subsequently, analysis is carried out on any data transmitted between the user and a remote site to determine if the transmitted data is related to the stored data. If it is found that the data is related, user access to the remote site is denied unless the remote site's address is one of the stored network addresses. This provides more security than was previously available since it protects the user against attacks from sites that were not previously known to pose a threat.
Owner:BAE SYSTEMS PLC
Collaborative phishing attack detection
ActiveUS20150180896A1Reduce the possibilityMemory loss protectionError detection/correctionComputer networkRanking
Described herein are methods, network devices and machine-readable storage media for detecting whether a message is a phishing attack based on the collective responses from one or more individuals who have received that message. The individuals may flag the message as a possible phishing attack, and / or may provide a numerical ranking indicating the likelihood that the message is a possible phishing attack. As responses from different individuals may have a different degree of reliability, each response from an individual may be weighted with a corresponding trustworthiness level of that individual, in an overall determination as to whether a message is a phishing attack. A trustworthiness level of an individual may indicate a degree to which the response of that individual can be trusted and / or relied upon, and may be determined by how well that individual recognized simulated phishing attacks.
Owner:COFENSE INC
Systems and methods for creating and running heterogeneous phishing attack campaigns
ActiveUS20170251010A1Risk minimizationMalicious action is preventedTransmissionEngineeringHeterogeneous network
A method for creating a plurality of campaigns for simulated phishing attacks includes creating, by a campaign manager, a plurality of campaigns for simulated phishing attacks having a plurality of parameters including at least a time schedule, each of the plurality of campaigns having at least one parameter different than other campaigns of the plurality of campaigns, and identifying, by a simulation server from the database, a first campaign and a second campaign from the plurality of campaigns from which to create a first simulated phishing email to send on a first time schedule to email accounts of users of the first campaign, and a second simulated phishing email to send on a second time schedule, different than the first time schedule, to email accounts of users of the second campaign.
Owner:KNOWBE4 INC
Anti-phishing filter
ActiveUS20080276315A1Memory loss protectionUnauthorized memory use protectionInternet privacyElectronic communication
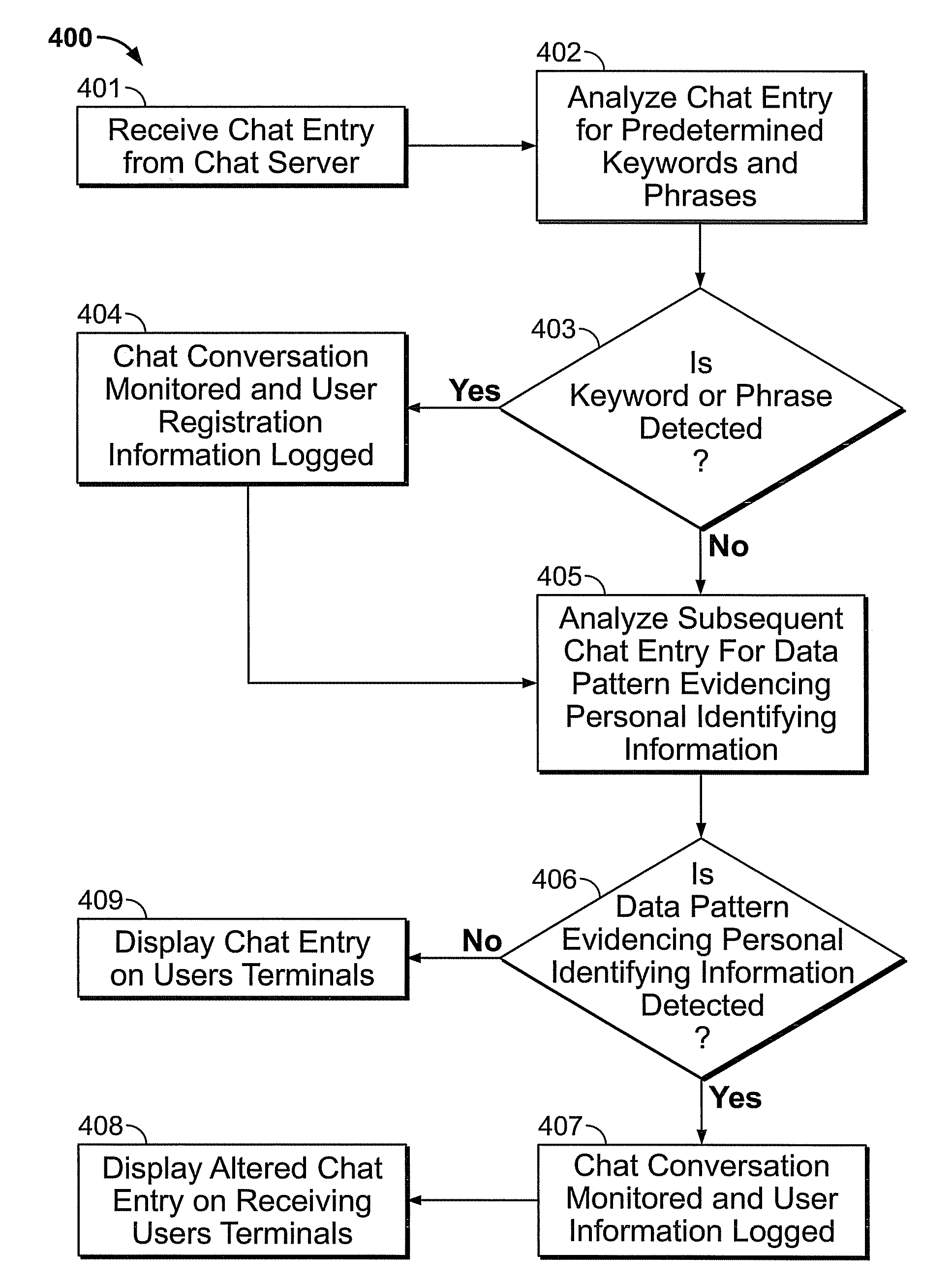
A method operates to detect personal identifying or account information exchanged in a real-time electronic communication occurring between computer network users, such as electronic chat. A detected personal identifier may be recognized as an attempt on the part of one user to engage in a phishing attack upon another user or to otherwise steal the other user's sensitive personal information. Upon recognizing the communication as an unwarranted attempt to collect such information, the electronic communication may be monitored, and communication of the personal information may be prevented.
Owner:SHUSTER GARY STEPHEN
Systems and methods for performing or creating simulated phishing attacks and phishing attack campaigns
ActiveUS9894092B2Expose a lack of vigilance and/or know-howRisk minimizationTransmissionElectronic mailData library
A method for establishing a campaign for a simulated phishing attack includes receiving, via a campaign manager, specification of a plurality of parameters for a campaign including at least an identifier of a campaign and identification of users to which to send the campaign, establishing, via the campaign manager, a type of exploit for the campaign and one or more types of data to collect via the type of exploit, storing, by the campaign manager, the campaign comprising the plurality of parameters, and identifying, by a simulation server, the campaign stored in the database to create a simulated phishing email, to be sent to email accounts of the users, using the plurality of parameters of the campaign, wherein the simulated phishing email is to be created to have a link to a landing page comprising the type of exploit and configured to collect the one or more types of data.
Owner:KNOWBE4 INC
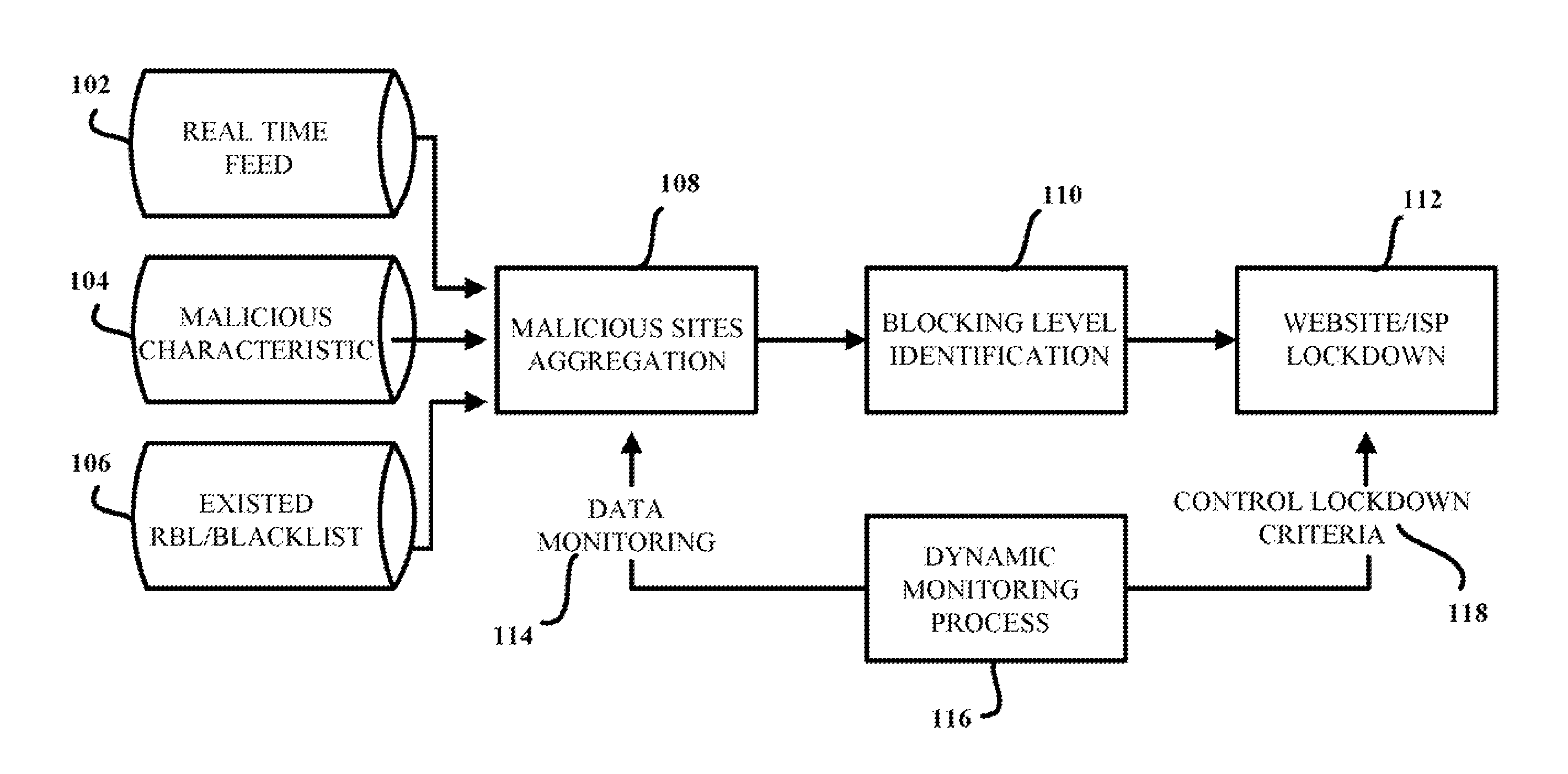
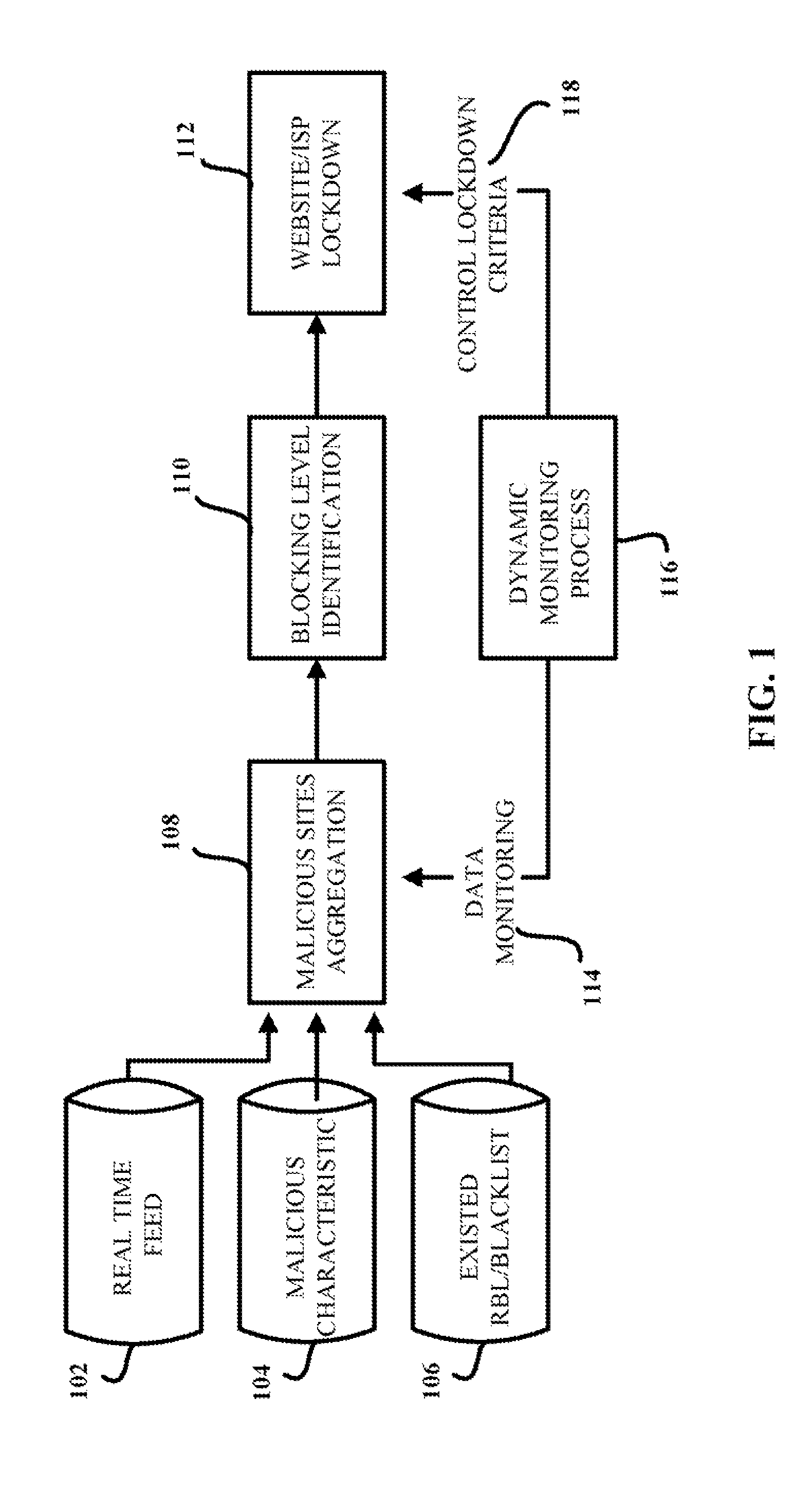
Aggregation-based phishing site detection
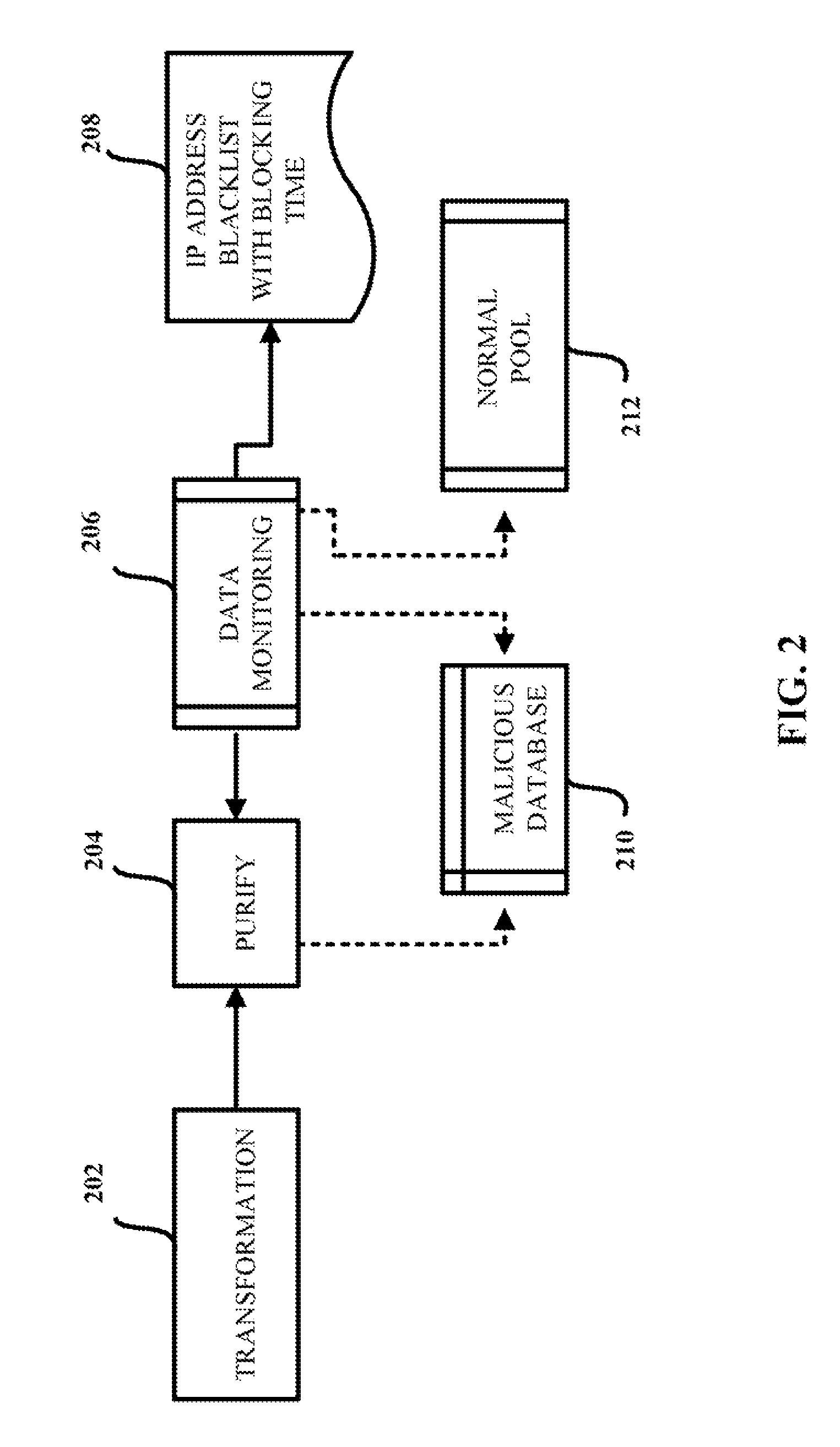
InactiveUS7854001B1Reduce in quantityReduce attackMemory loss protectionError detection/correctionWeb siteBlack list
A computer-implemented method for reducing phishing attacks that employ malicious websites is provided. The computer-implemented method includes gathering information about potentially malicious websites from a plurality of sources. The computer-implemented method also includes reducing the number of potentially malicious websites gathered; thereby creating a malicious website database that tracks at least a subset of the potentially malicious websites. In addition, the computer-implemented method includes generating a malicious website blacklist from the malicious website database, each website in the malicious website blacklist satisfying inclusion criteria, wherein the malicious website blacklist is employed to decide whether an access request to a given website is permitted.
Owner:TREND MICRO INC
Multiple factor user authentication system
InactiveUS20090063850A1Avoid attackUser identity/authority verificationDigital data authenticationUser authenticationUser identifier
The present invention describes a method and a system for multi-level authentication of a user and a server. The user registration process in the invention enables user to personalize the web page of the server. Further, the user authentication takes place in a multi-step process including entering credentials such as user ID, subset of user's password, subset of shared secret and a One Time Password (OTP). The system of the present invention provides various means of entering the said credentials which prevents phishing attacks.
Owner:JORAM SHARWAN KUMAR +3
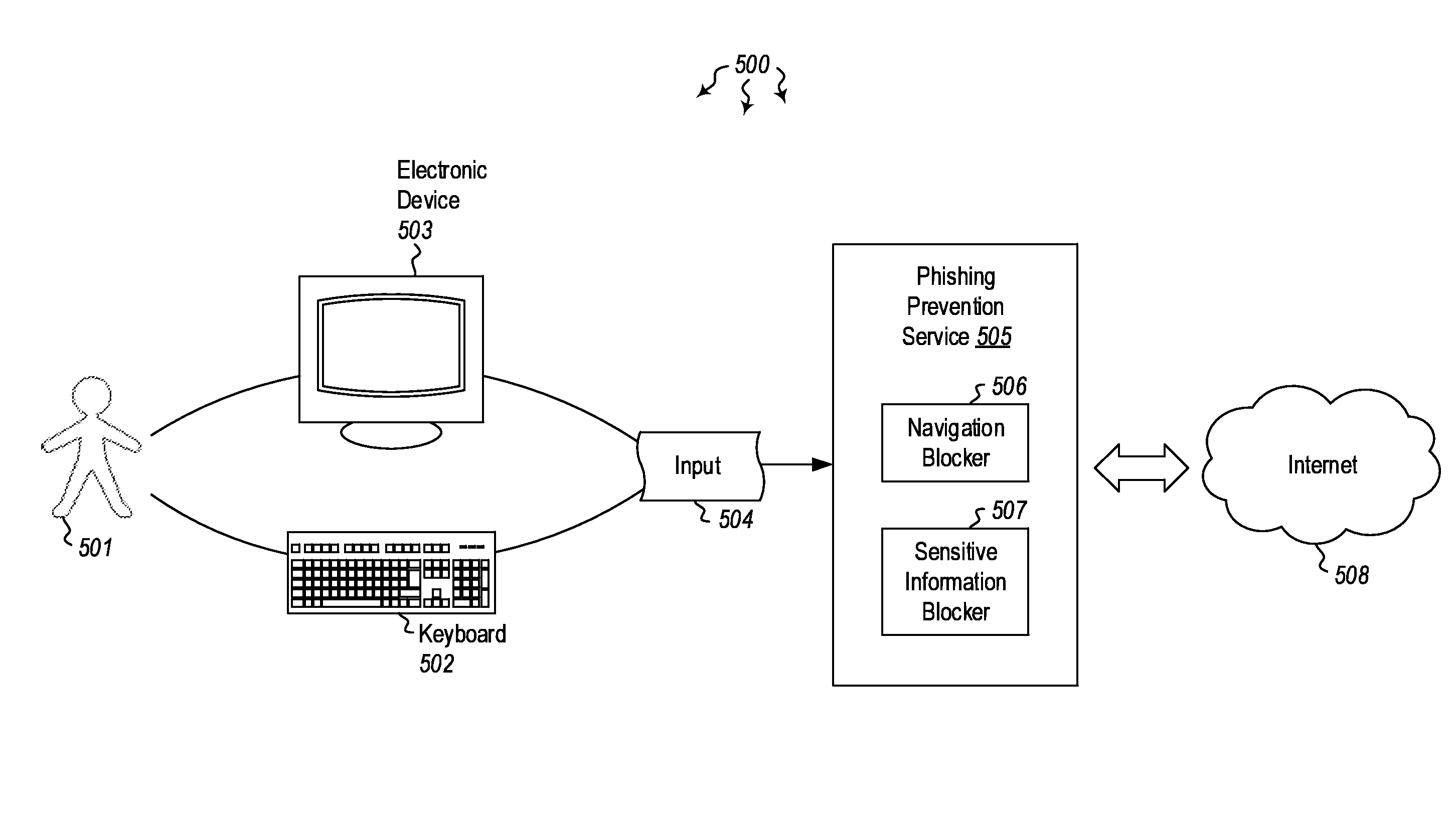
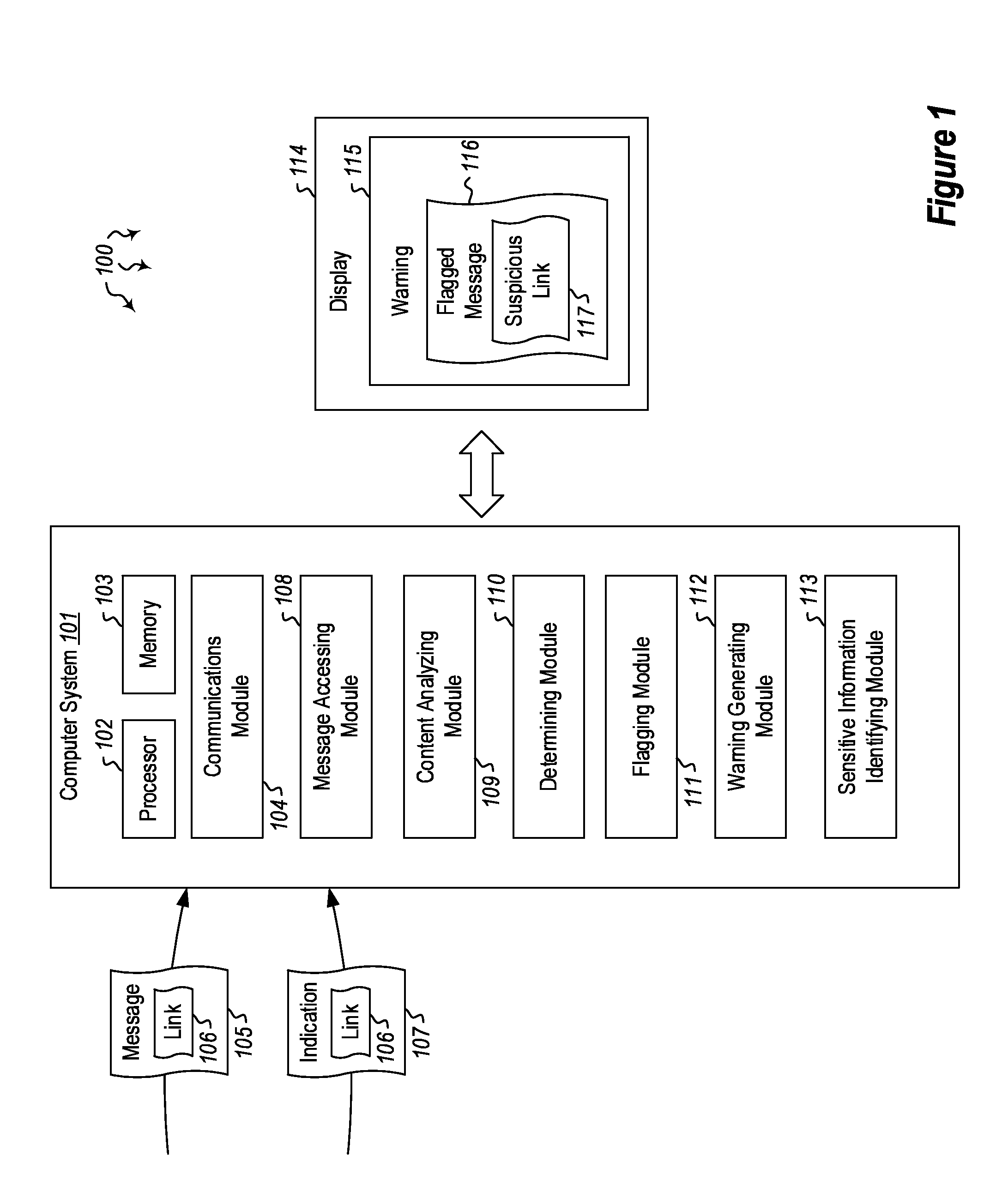
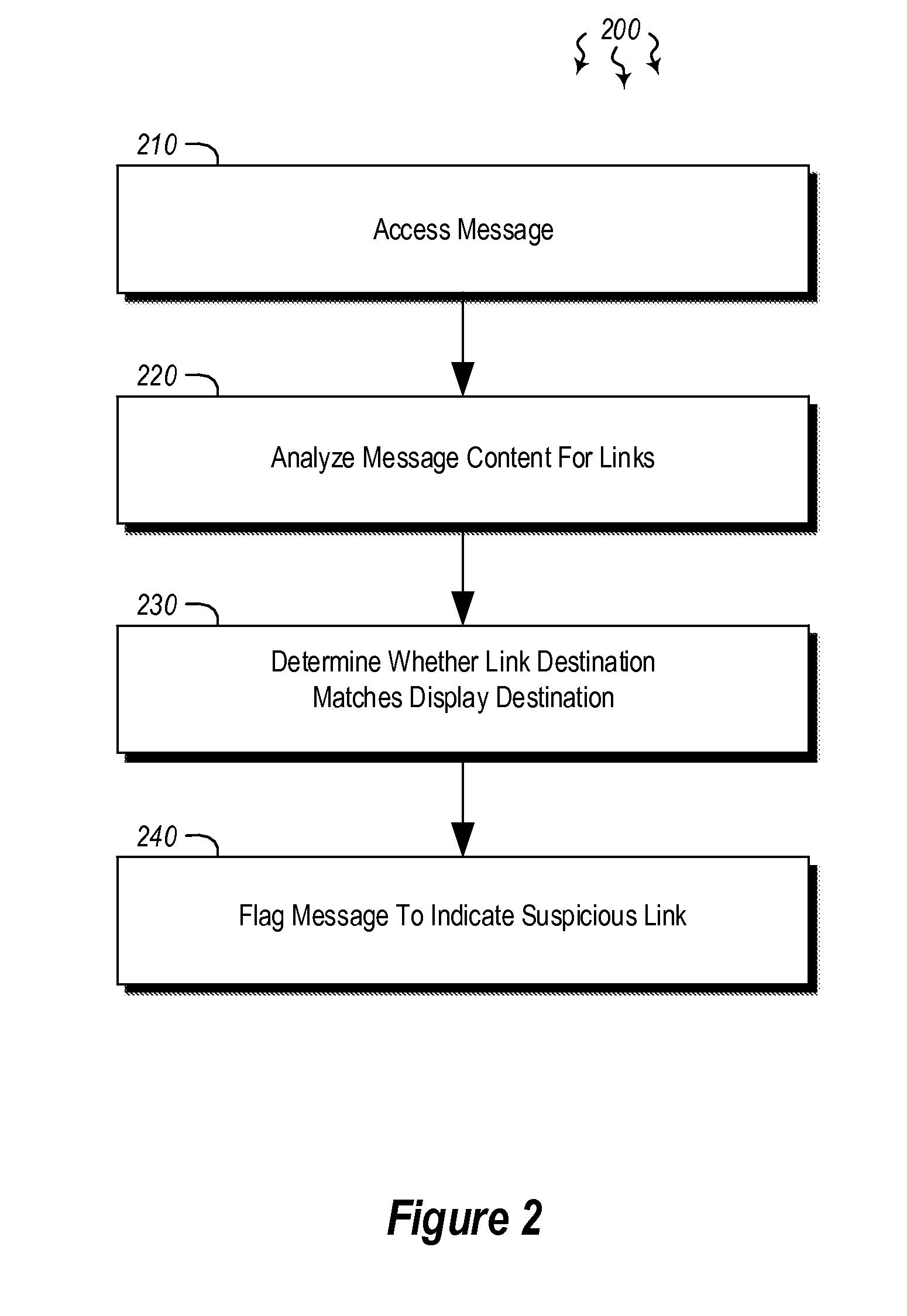
Detecting and preventing phishing attacks
InactiveUS20160006760A1Memory loss protectionError detection/correctionComputerized systemPhishing attack
Embodiments are directed to detecting and preventing phishing attacks. In one scenario, a computer system accesses a message and analyzes content in the message to determine whether a link is present. The link has a link destination and at least some text that is designated for display in association with the link (i.e. the anchor), where the text designated for display indicates a specified destination. Then, upon determining that a link is present in the message, the computer system determines whether the link destination matches the destination specified by the text designated for display and, if it determines that the destination specified by the text designated for display does not match the link destination, the computer system flags the message to indicate that the message includes at least one suspicious link.
Owner:MICROSOFT TECH LICENSING LLC
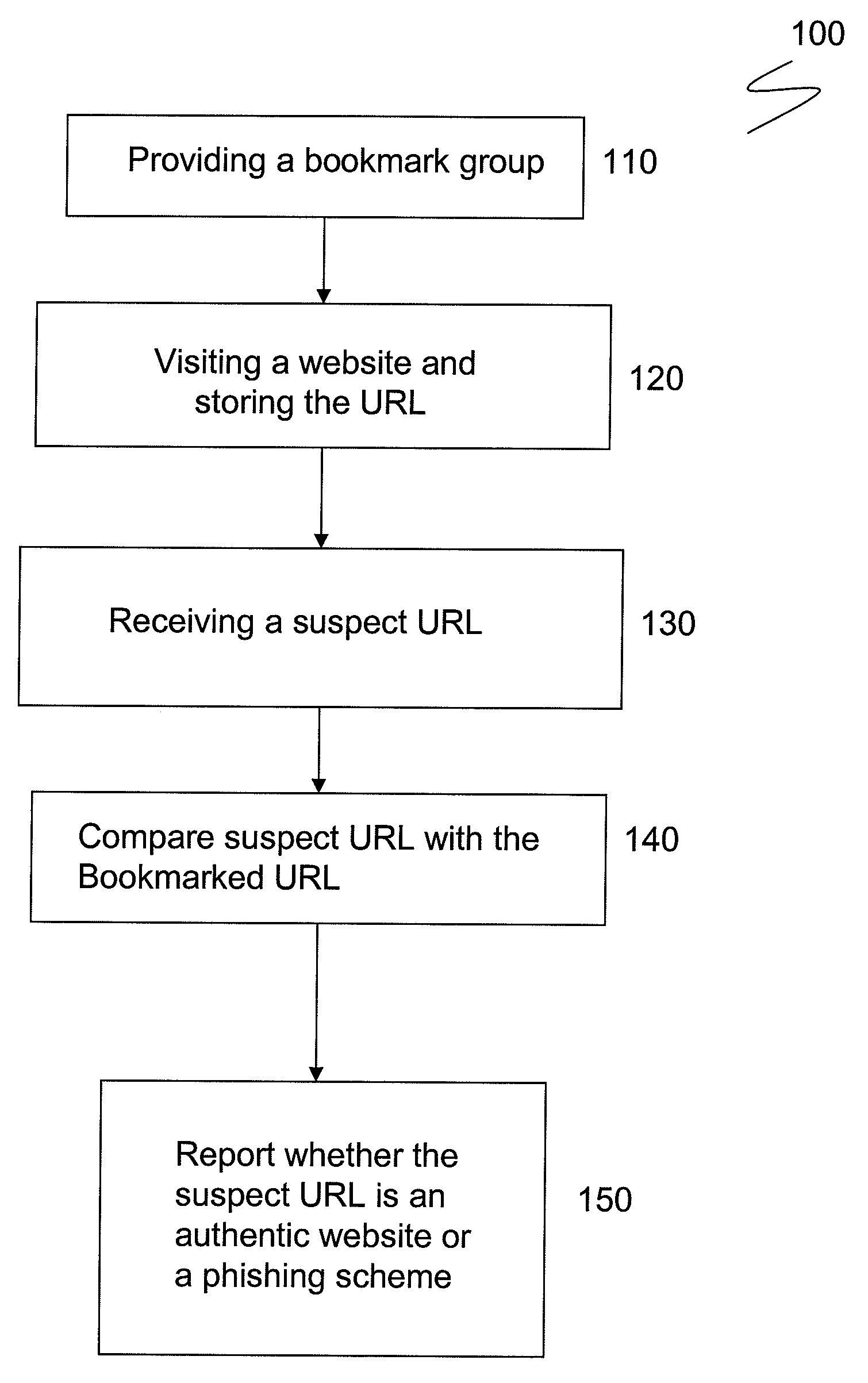
Method and apparatus for preventing phishing attacks
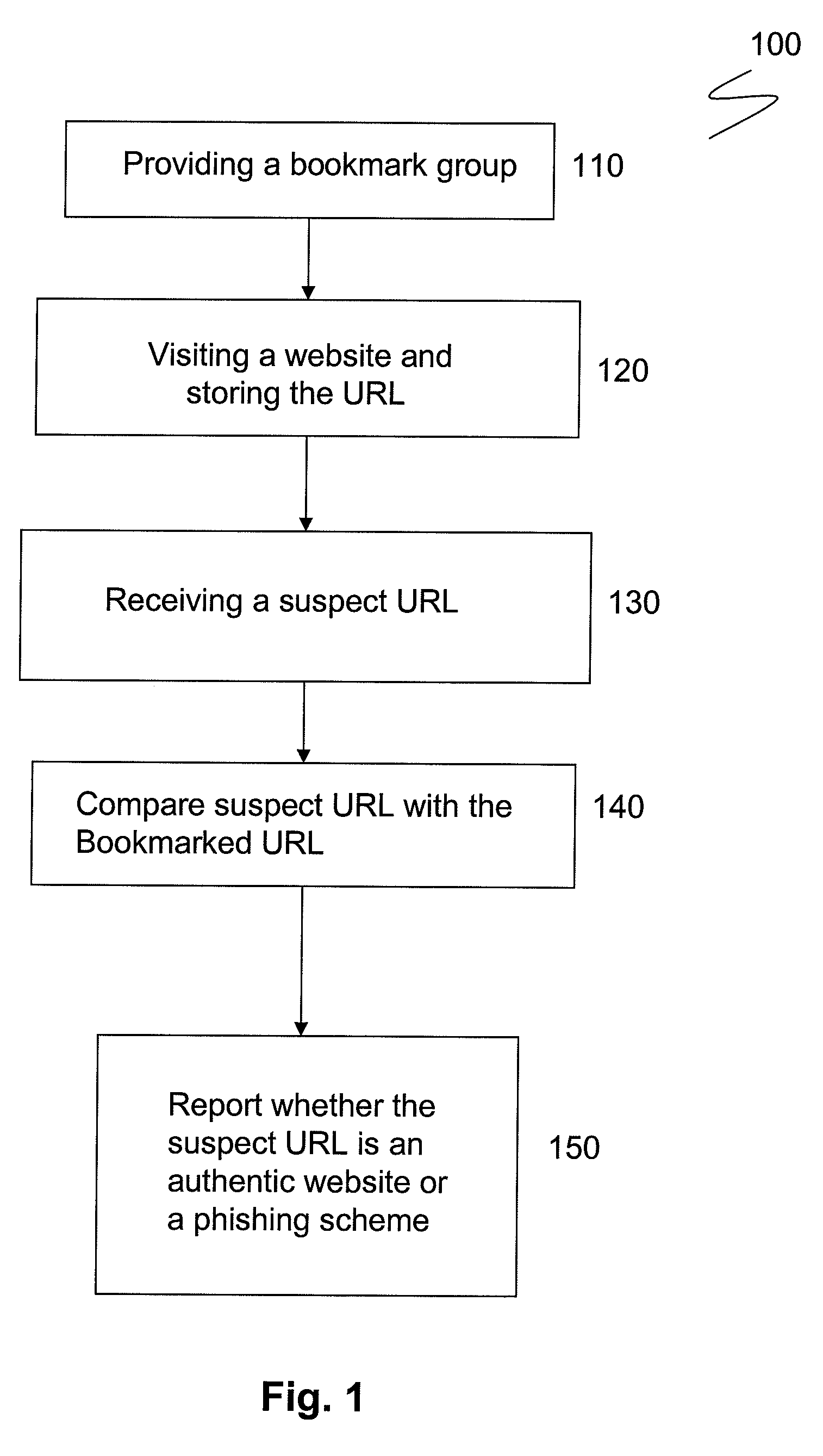
InactiveUS20090328208A1Preventing phishing attackMemory loss protectionError detection/correctionWeb browserIp address
The disclosure generally relates to a method for preventing phishing attacks on a computer browser. The method includes the steps of: providing a web browser having a bookmark group; directing the browser to a first Uniform Resource Locator (“URL”) having a first URL address, the first URL address having a plurality of alpha-numeric characters pointing to a first IP address; saving the first URL address in the bookmark group as a first bookmark; receiving an email communication containing a second URL address, the second URL address having a plurality of alpha-numeric characters similar to the first URL address and purporting to point to the first IP address; comparing the first URL address with the second URL address; and determining whether the first URL address and the second URL address share an identical IP addresses.
Owner:IBM CORP
Methods and systems for detecting email phishing attacks
Detection of email phishing attacks is initiated when an email is received in a computer system. The email is parsed for features indicative of an email phishing attack, such as a link to an external website. The link to the website is followed to connect to and access the website. Fictitious information, such as fake user credentials or fake credit card information, is provided to the website. The response of the website to the fictitious information is evaluated to determine if the website is a phishing site. The website is deemed to be a phishing site when the website accepts the fictitious information as valid. The email is blocked to prevent its addressee from opening the email when the email is deemed part of a phishing attack, such as when it links to a phishing site.
Owner:TREND MICRO INC
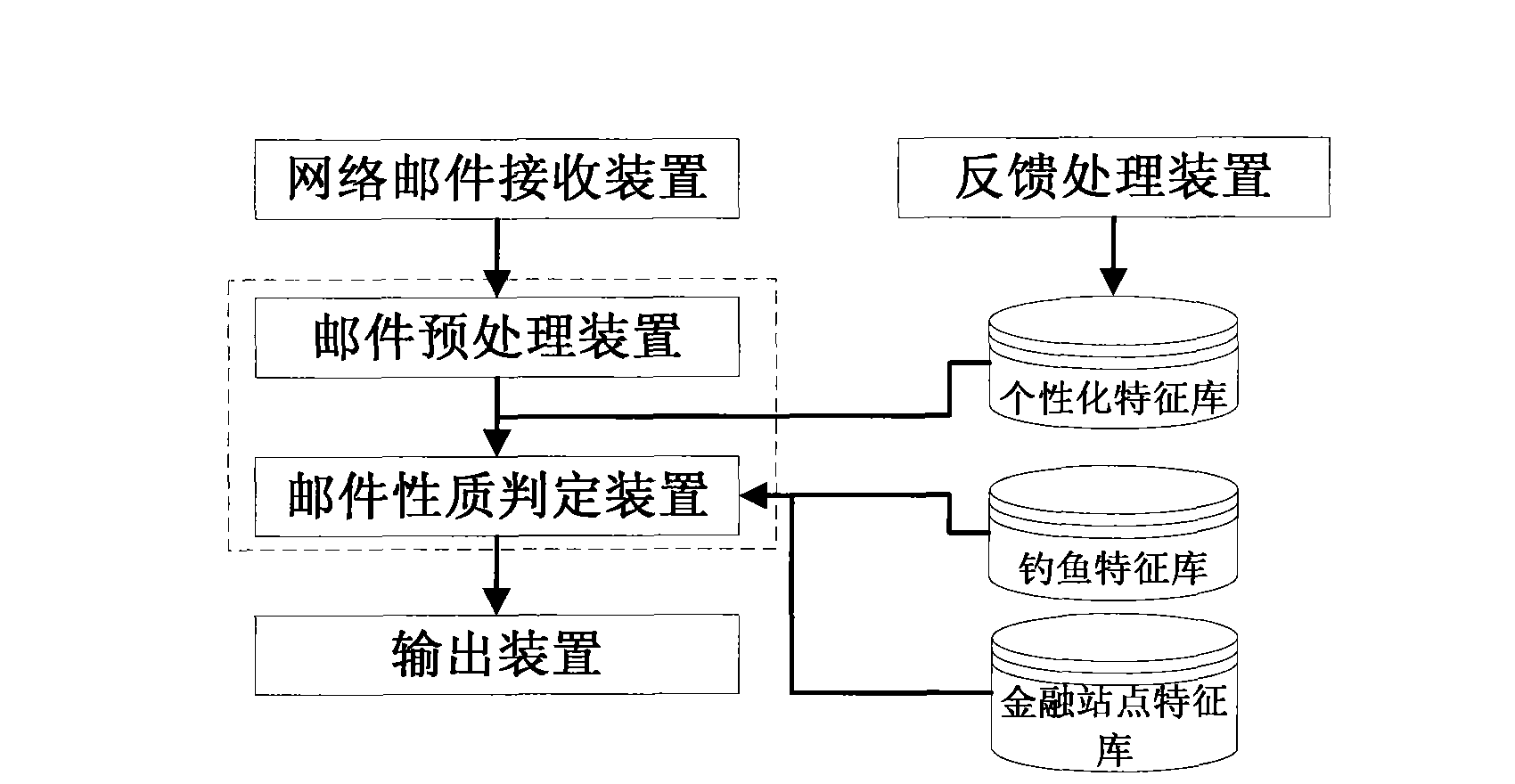
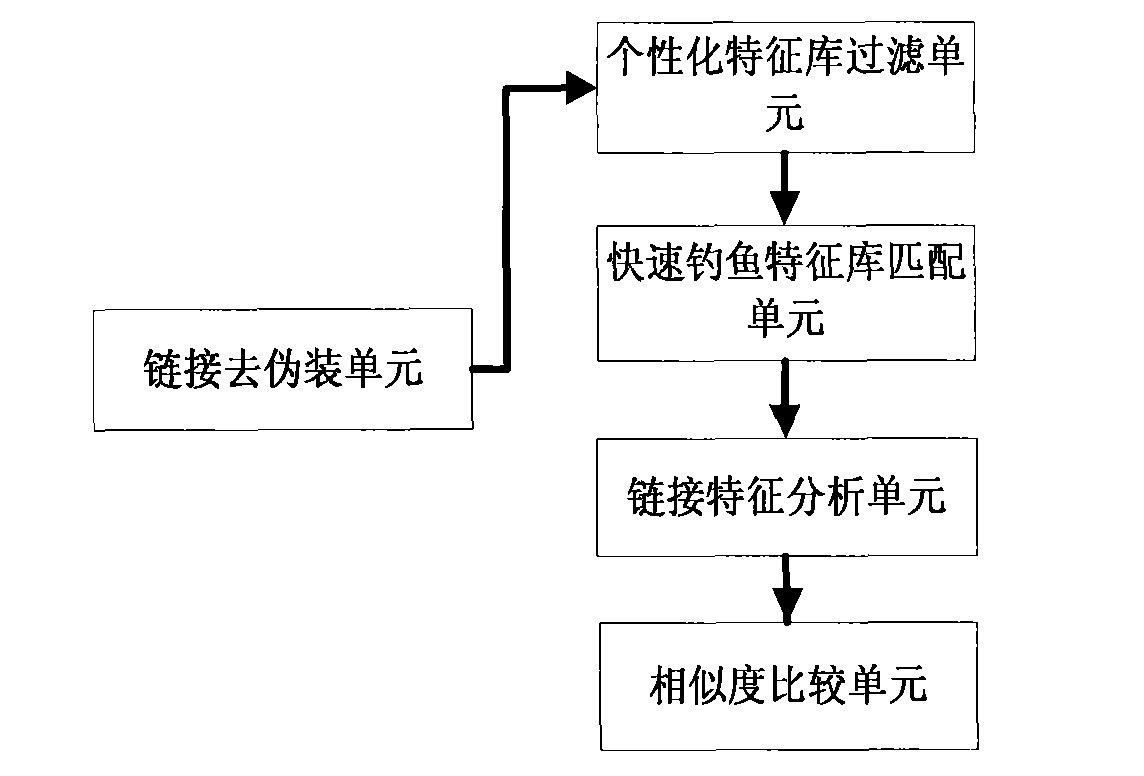
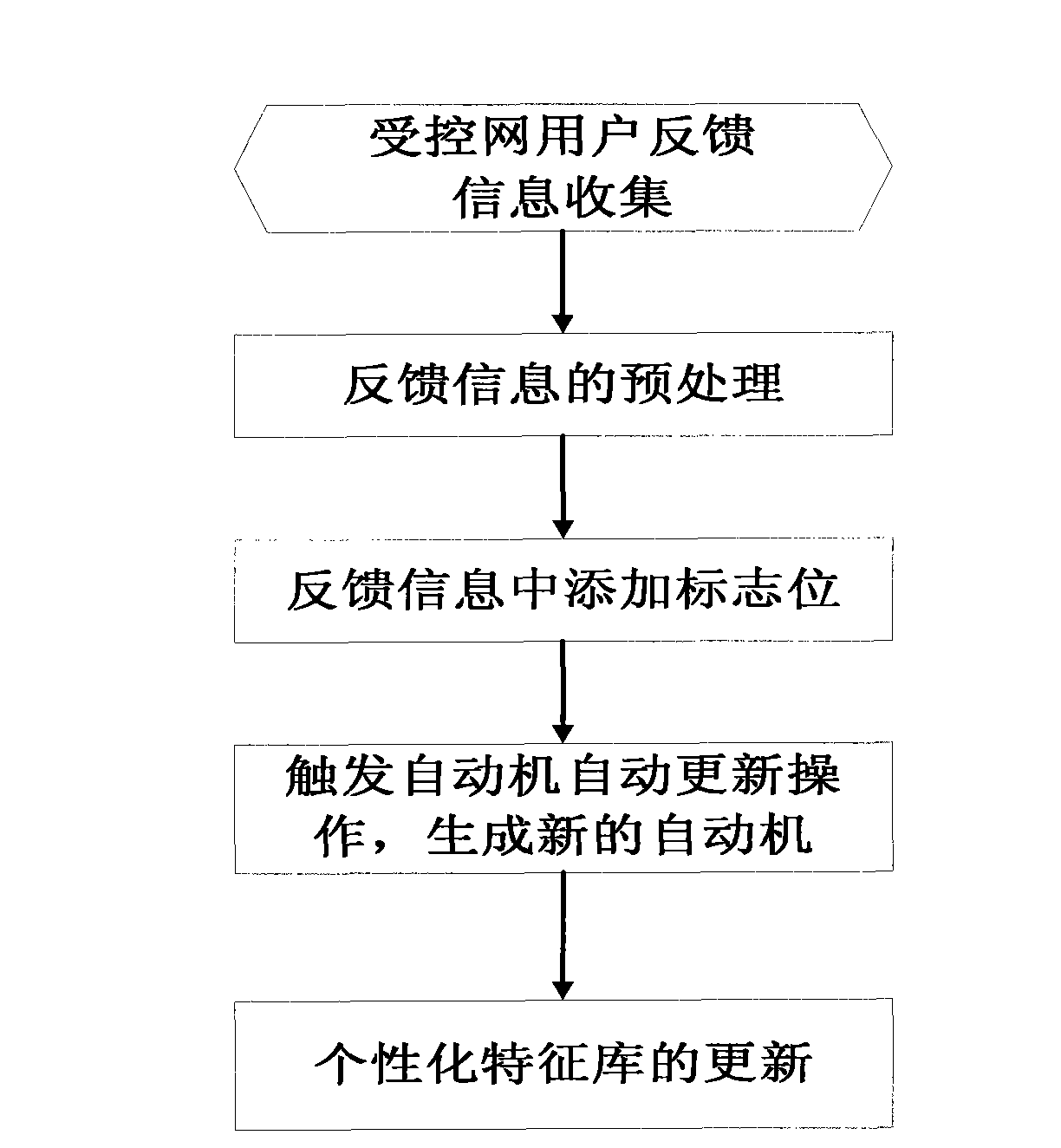
System and method for anti-phishing emails based on link domain name and user feedback
The invention provides a system and a method for anti-phishing emails based on link domain name and user feedback. The system comprises an email receiving device, an email pre-processing device, an email property judging device, an outputting device and a feedback processing device. The method comprises the following steps: analyzing characteristics of the link domain name in the email, combiningwith a controlled network user feedback strategy, and identifying phishing emails and doubtful phishing emails. The invention has advantages of high identification efficiency, low resource consumptionand no error rate. The invention can be configured to email servers, gateway servers and the like that require high real-time performance, protect the controlled network user against cheating by thephishing emails, resist the interference from the spiteful user in the controlled network, and can be widely applied to the application fields of network email filtering management, anti-phishing attack and the like.
Owner:杨辉
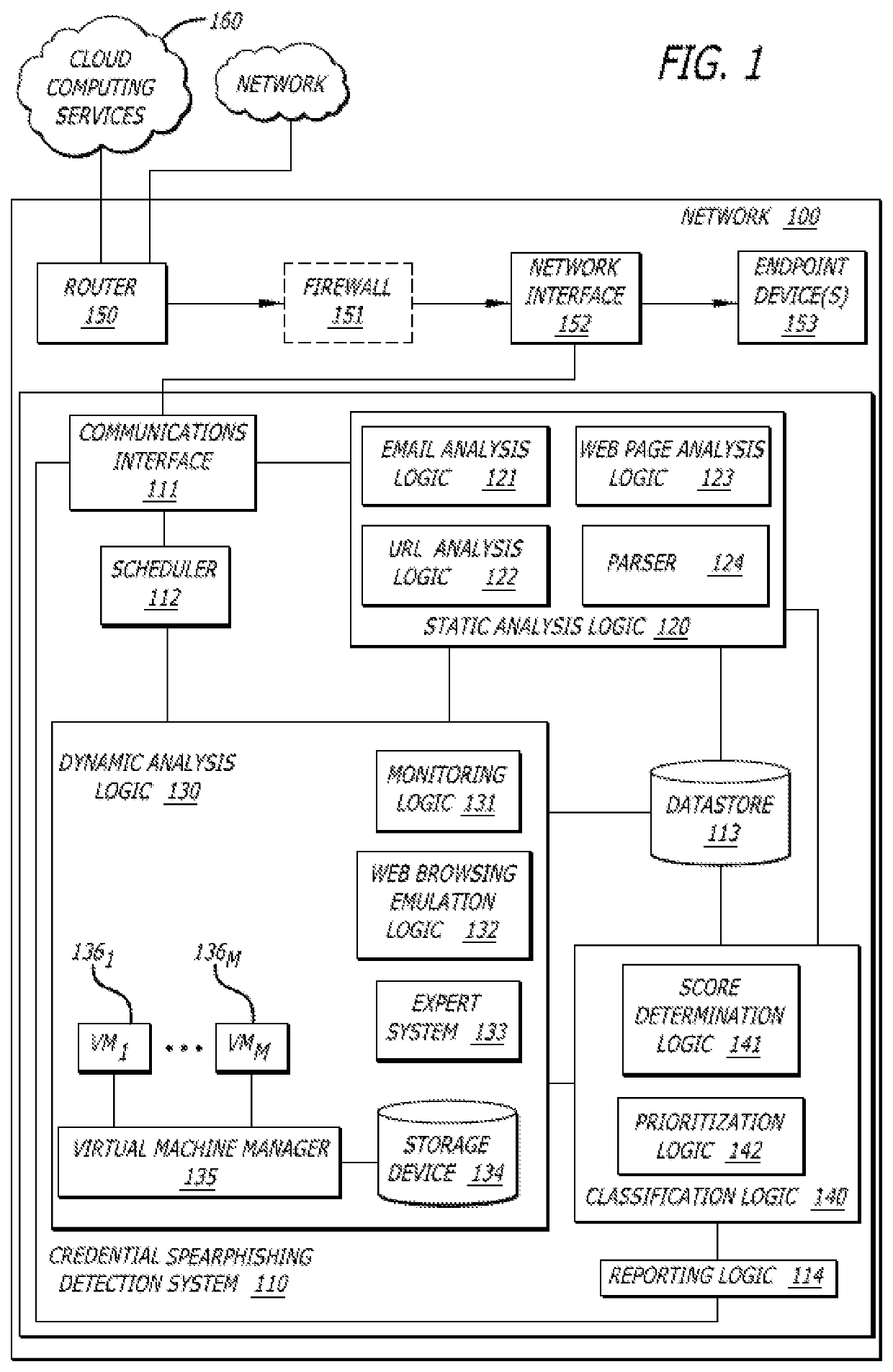
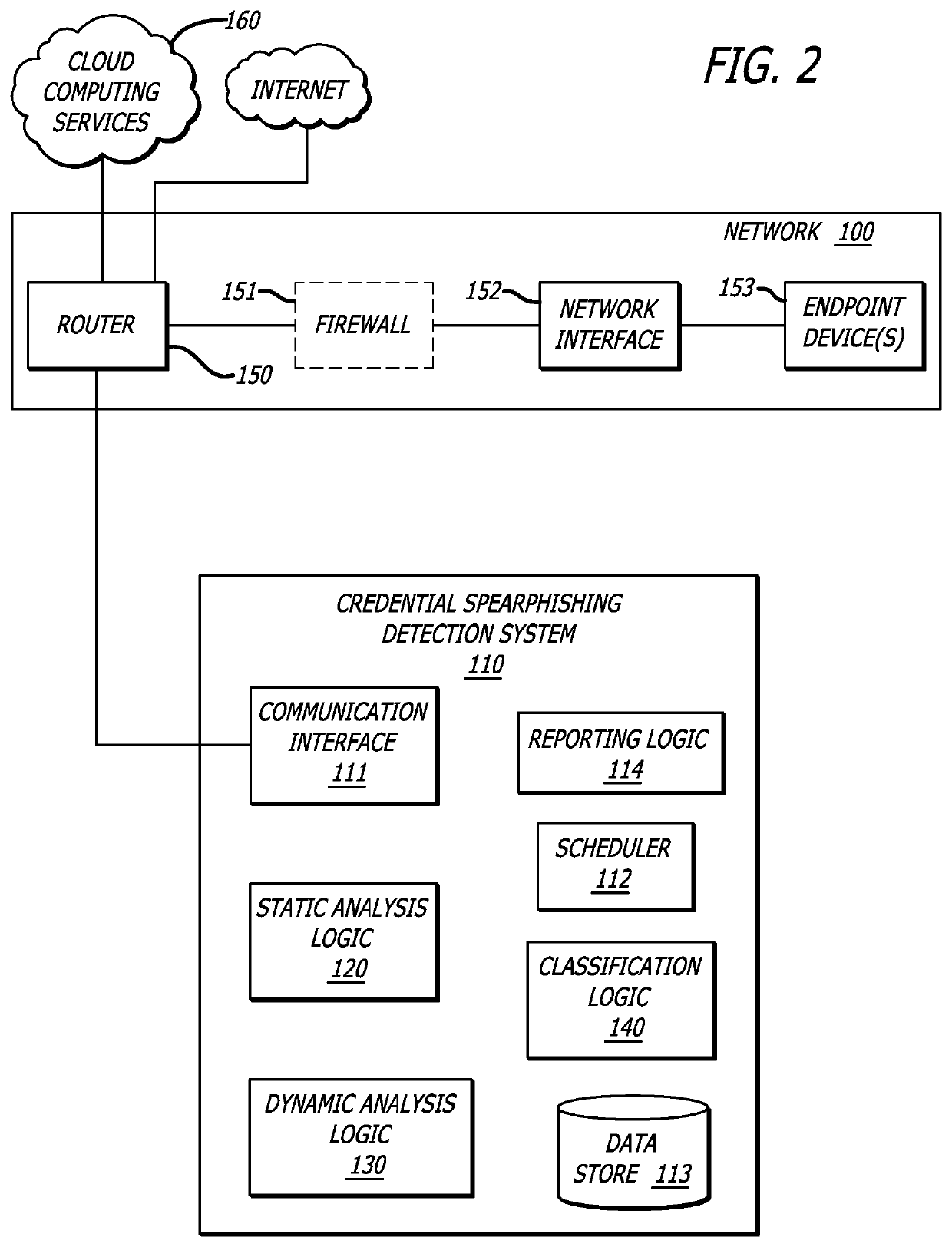
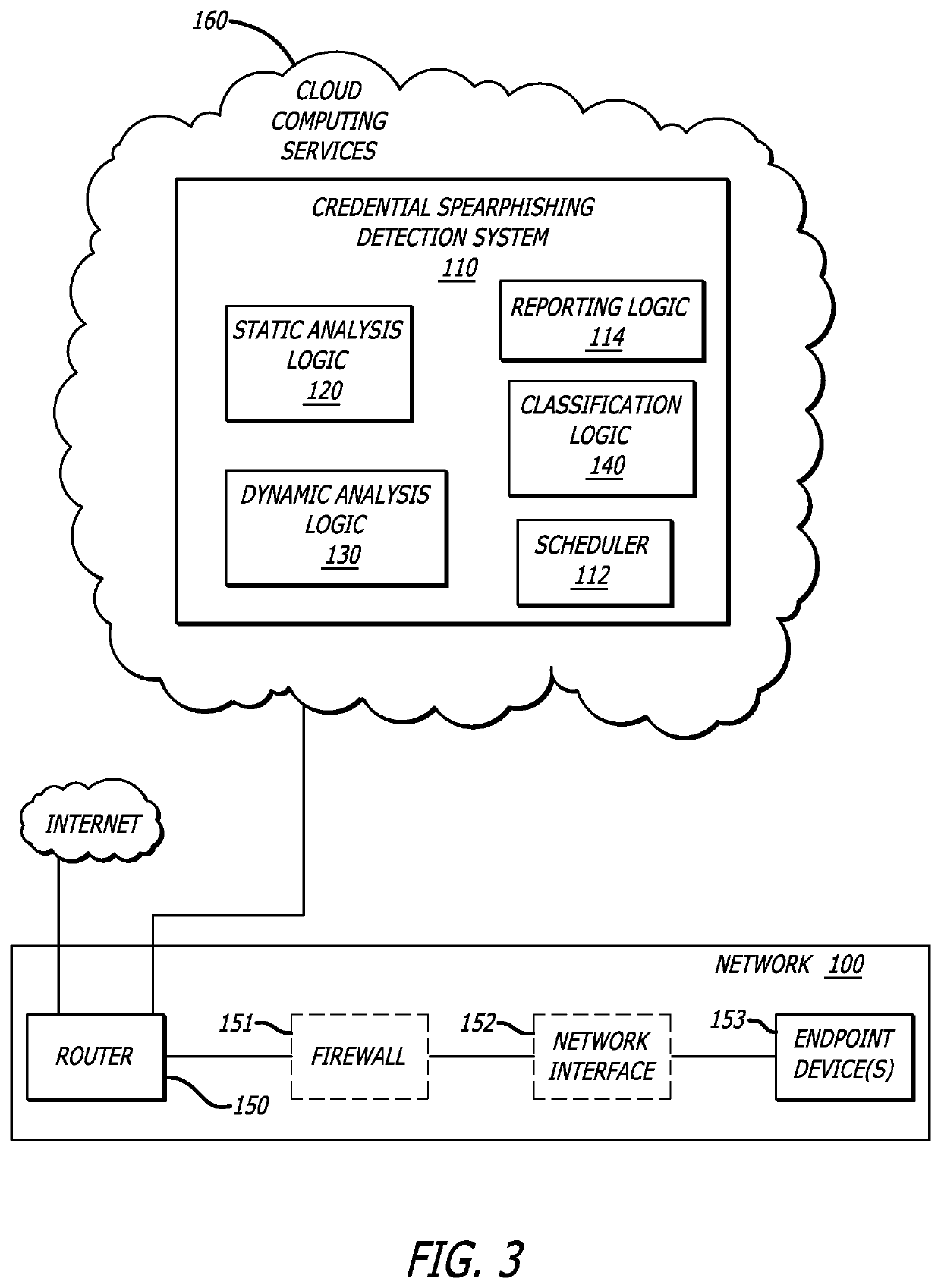
Detection of credential spearphishing attacks using email analysis
ActiveUS10601865B1Data switching networksSpecial data processing applicationsUniform resource locatorWeb page
A non-transitory computer readable storage medium having stored thereon instructions when executable by a processor perform operations including responsive to receiving an email including a URL, conducting an analysis of the email including: (i) analyzing a header and a body, and (ii) analyzing the URL; analyzing contents of a web page directed to by the URL; generating a score indicating a level of confidence the email is associated with a phishing attack based on at least one of the analysis of the email or the analysis of the contents of the web page; and responsive to the score being below a threshold, virtually processing the web page to determine whether the web page is associated with the phishing attack is shown.
Owner:FIREEYE SECURITY HLDG US LLC
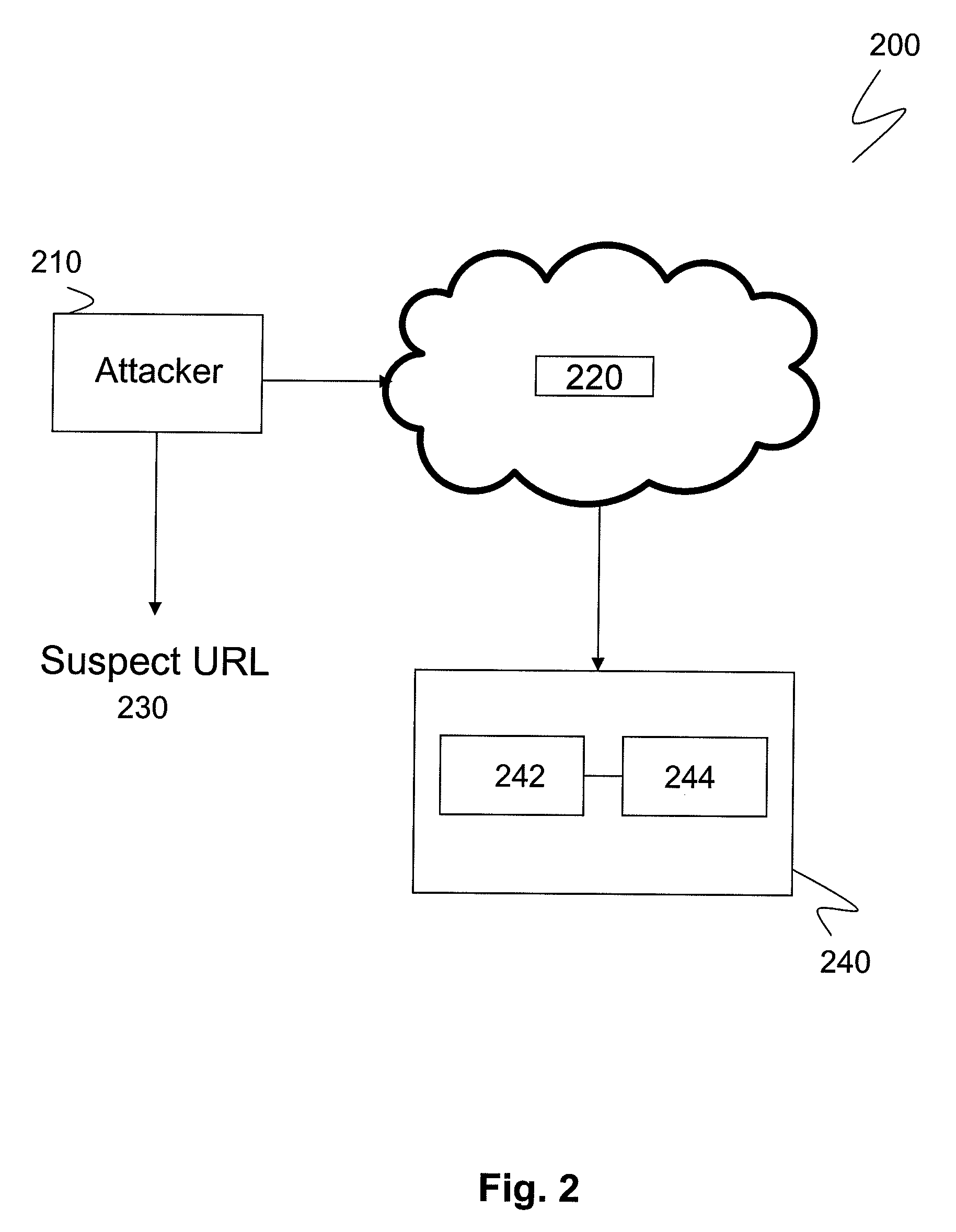
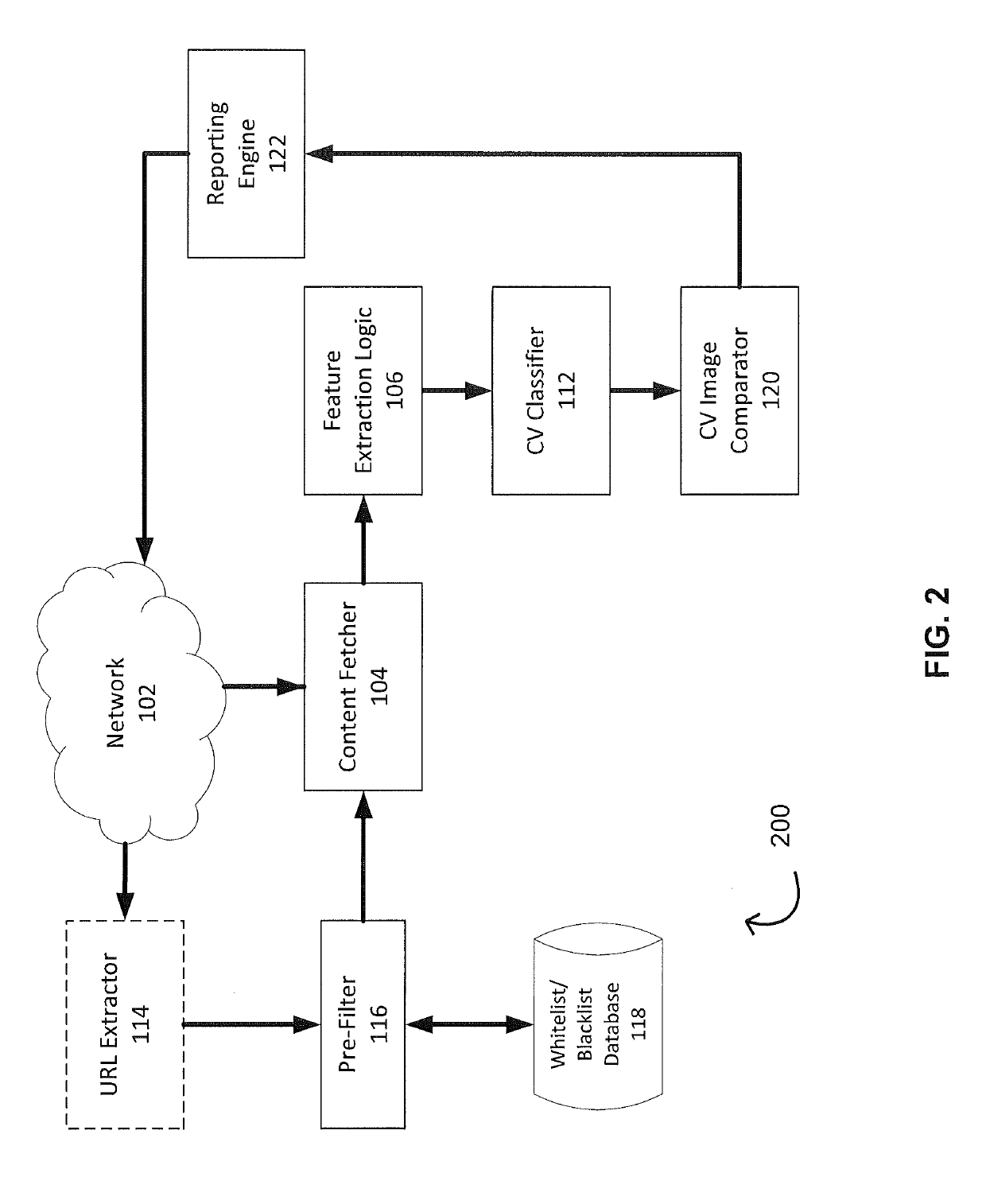
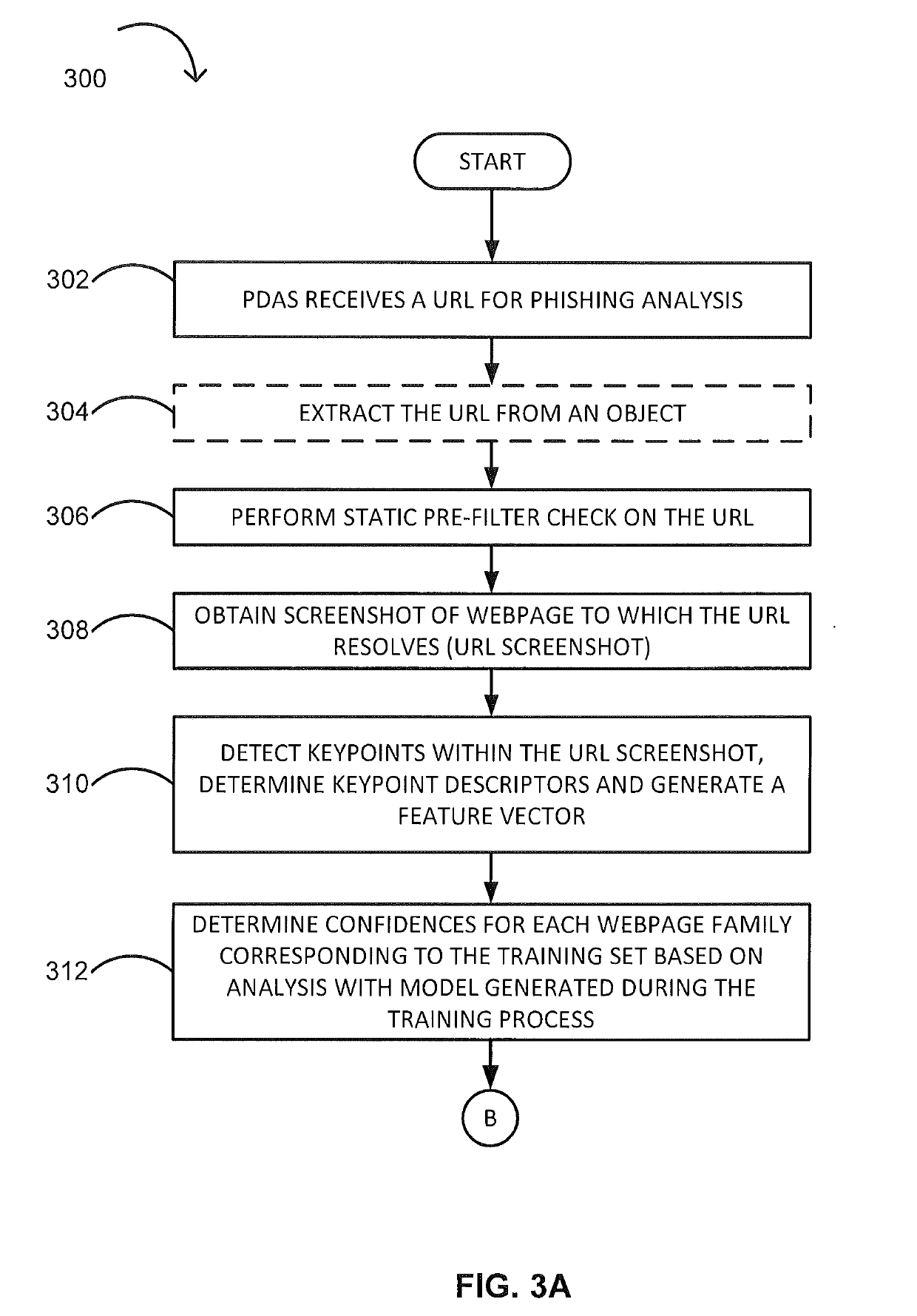
Phishing attack detection
A computerized method for analyzing a subject URL to determine whether the subject URL is associated with a phishing attack is disclosed. The method includes steps of detecting keypoints within a screenshot of a webpage corresponding to the subject URL and determining a set of confidences based on an analysis of the detected keypoints with a model. Each confidence within the set of confidences is assigned to feature vector within a set of training feature vectors representing a training set of URLs used in generating the model. The method comprises performing an image comparison between the screenshot and a screenshot corresponding to a feature vector within the set of training feature vectors, the feature vector being assigned a highest confidence. Responsive to determining the image comparison result exceeds a predefined threshold, transmitting an alert indicating that the subject URL is associated with the phishing attack.
Owner:FIREEYE SECURITY HLDG US LLC
Secure messaging system with personalization information
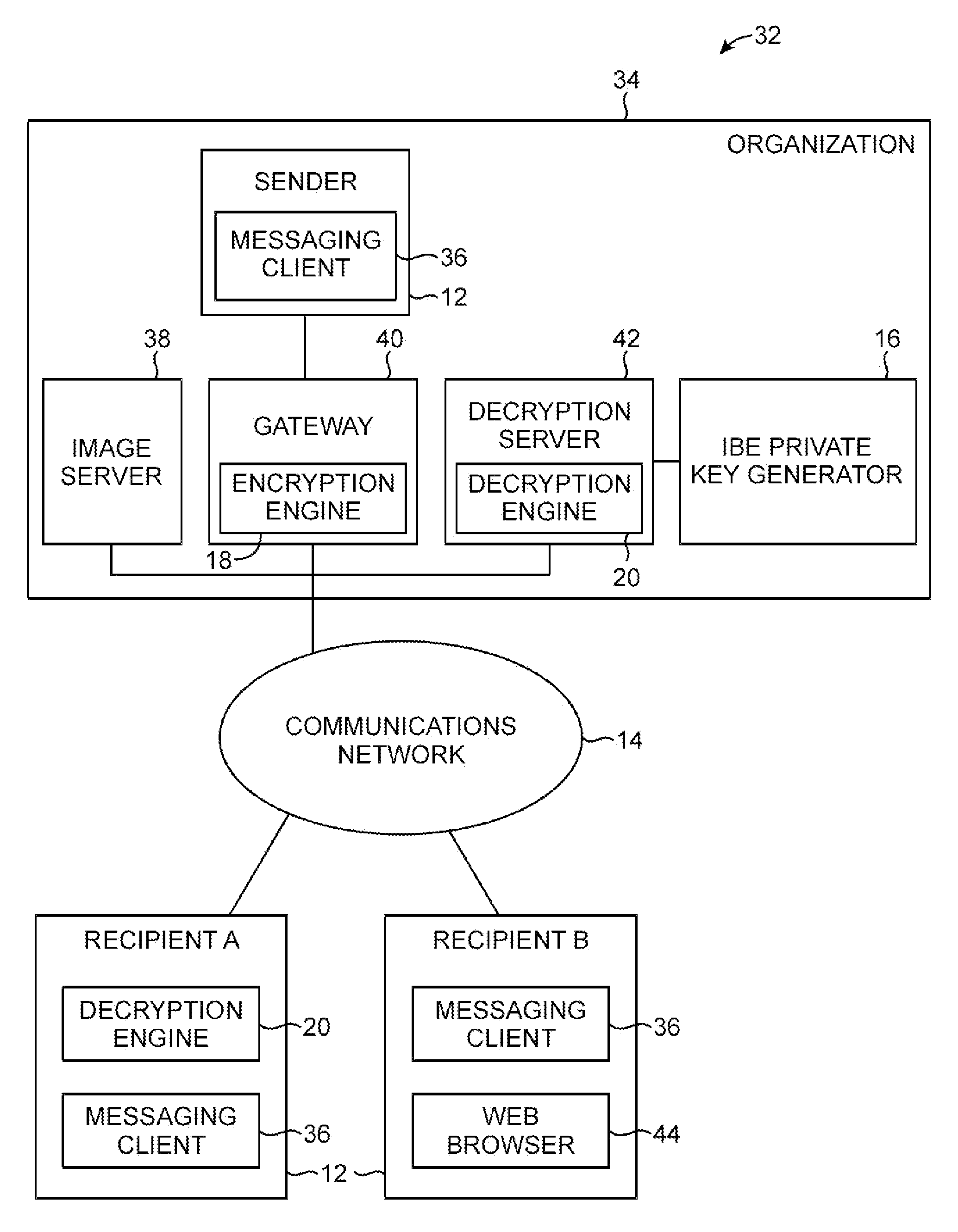
ActiveUS8145718B1Digital data processing detailsUser identity/authority verificationPersonalizationImage reference
Personalization images are included in email messages to combat phishing attacks in which an attacker attempts to trick a user into divulging sensitive information over the Internet. When a recipient of an email message receives a message, the recipient can visually inspect the personalization image in the message. If the personalization image is missing or if the personalization image is not valid, the email recipient is alerted to the possibility of a phishing attack. Email message content may be encrypted. A gateway associated with an email message sender may be used to perform encryption operations on the message content. The gateway may create an html version of the email by placing the encrypted message content in an html wrapper. An image reference corresponding to the personalization image may be embedded in the html version of the message.
Owner:MICRO FOCUS LLC
Methods and apparatus for detecting phishing attacks
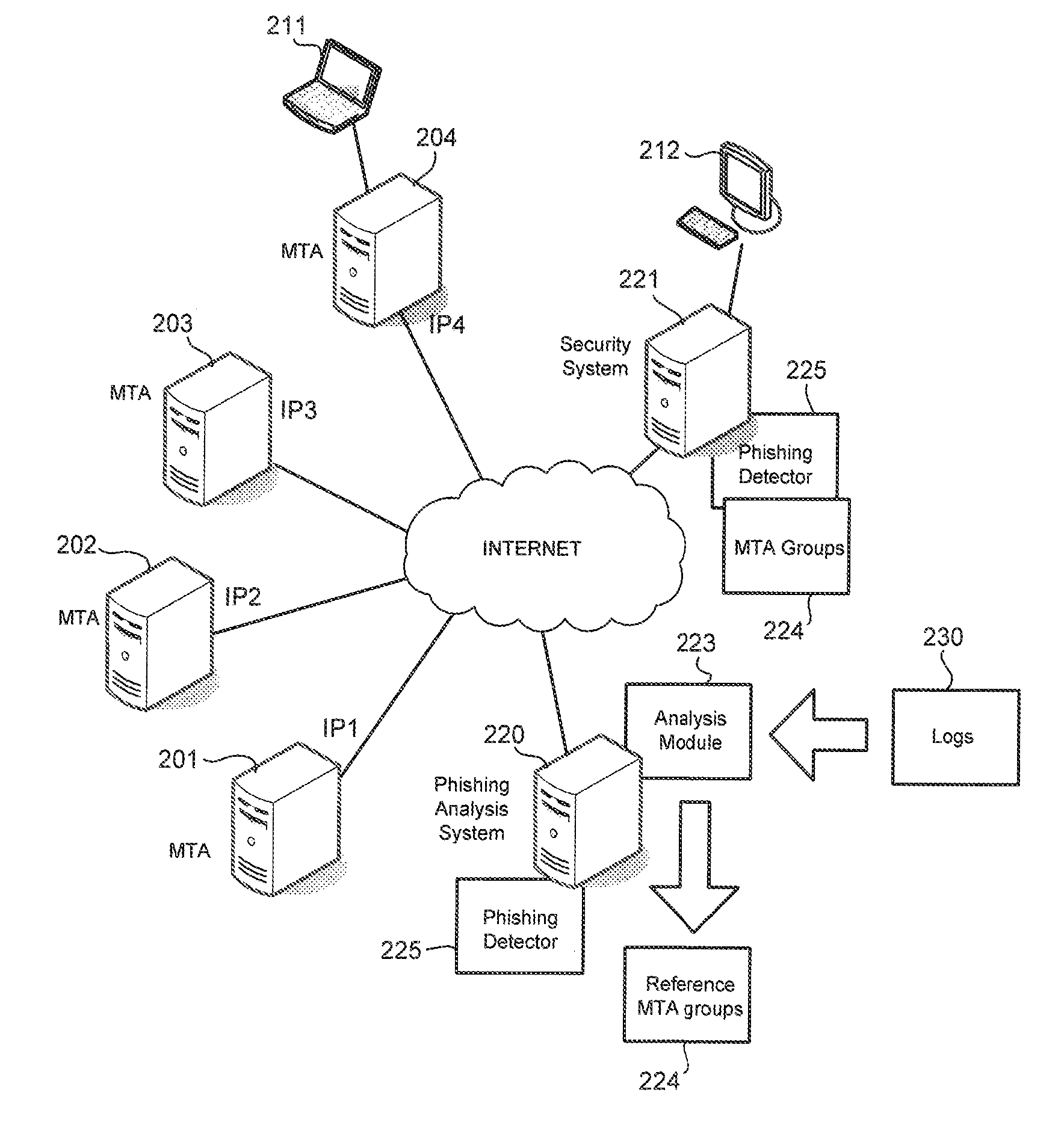
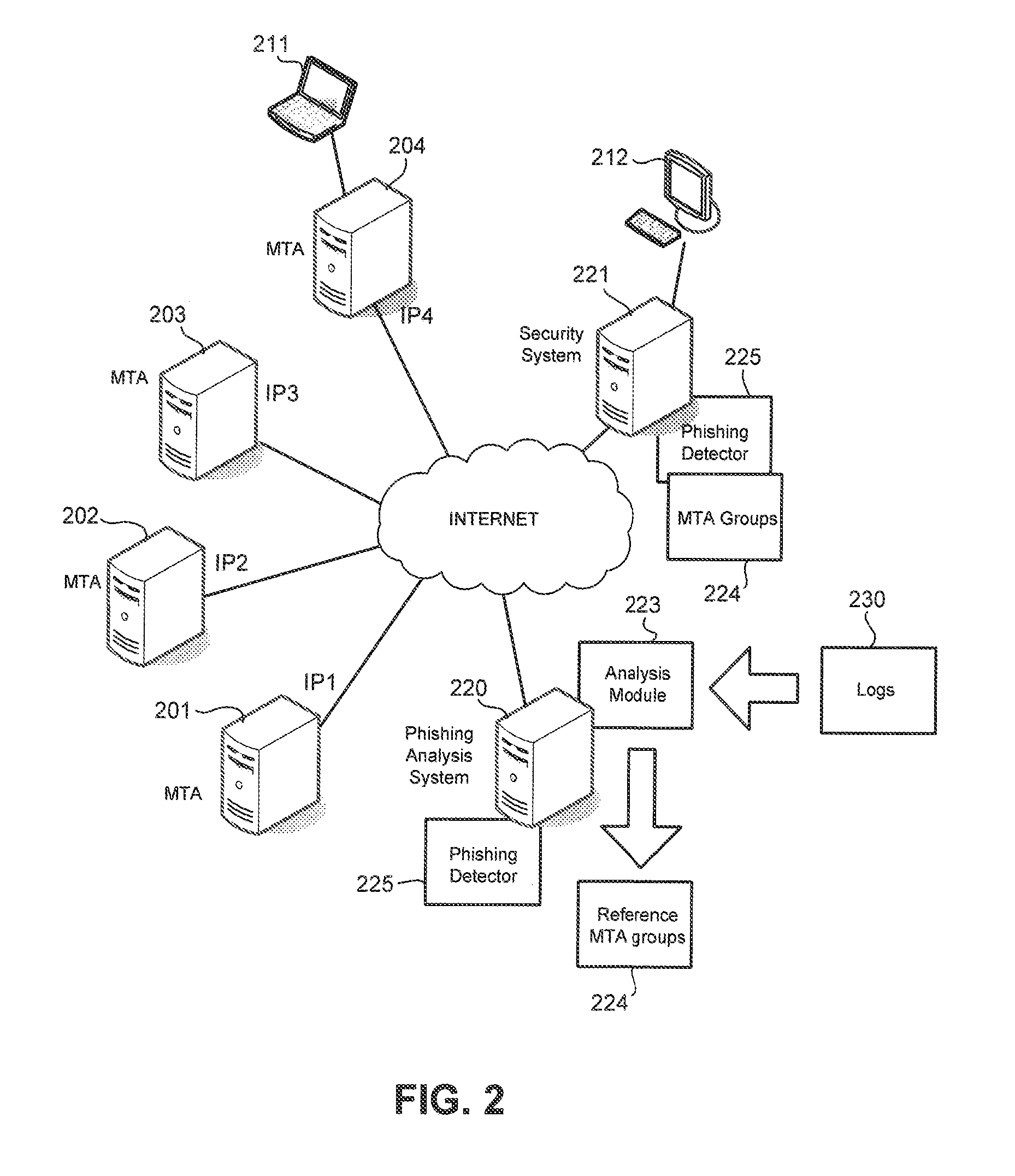
Phishing is detected by creating a message transfer agent (MTA) map, with each point on the MTA map referencing an MTA. Points on the MTA map are connected based on a number of emails with same signature sent by MTAs represented on the MTA map. Reference MTA groups are identified from the map. Phishing is detected when an MTA sent an email with the same signature as that of emails sent by MTAs belonging to a reference MTA group but the MTA is not a member of the reference MTA group.
Owner:TREND MICRO INC
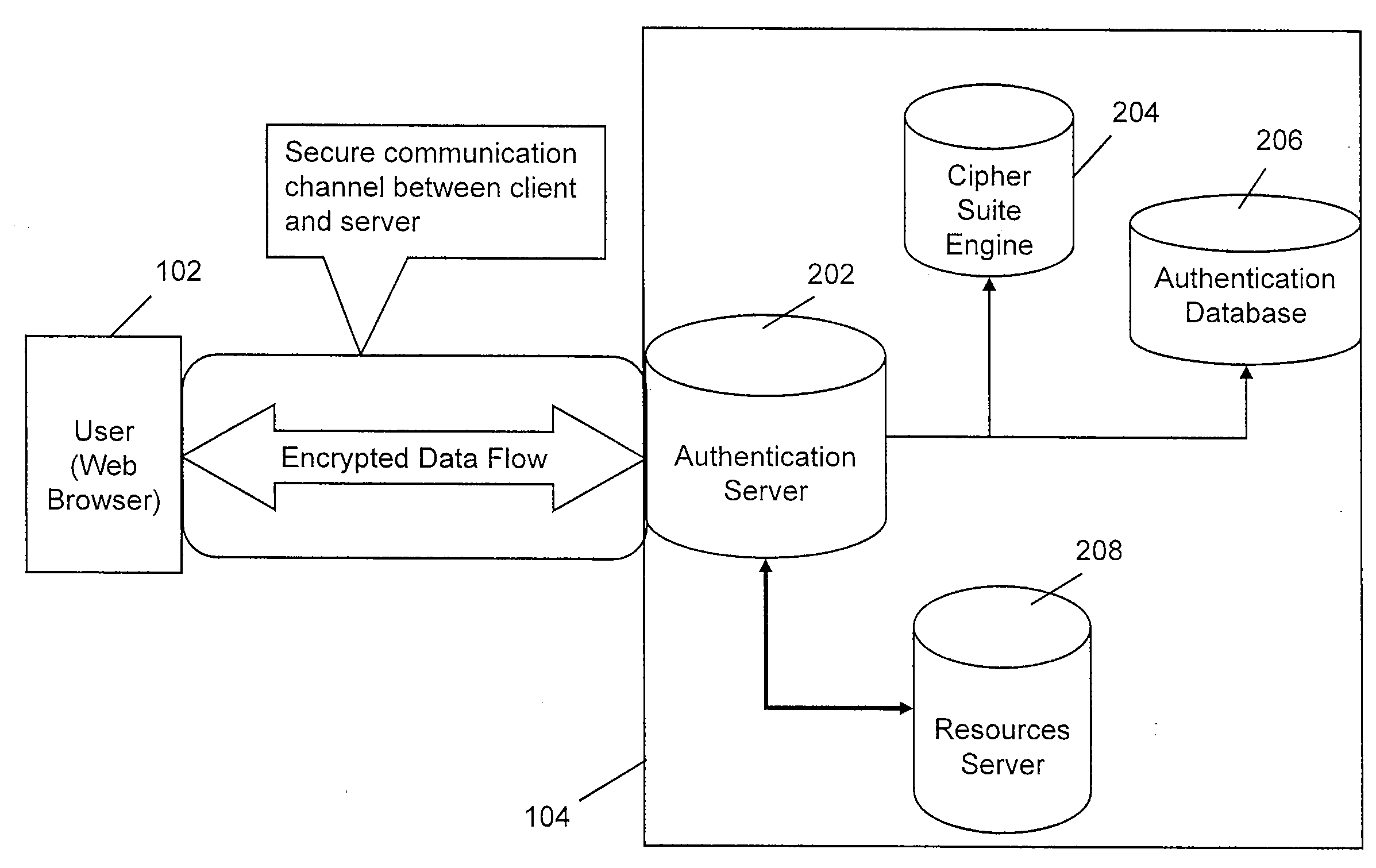
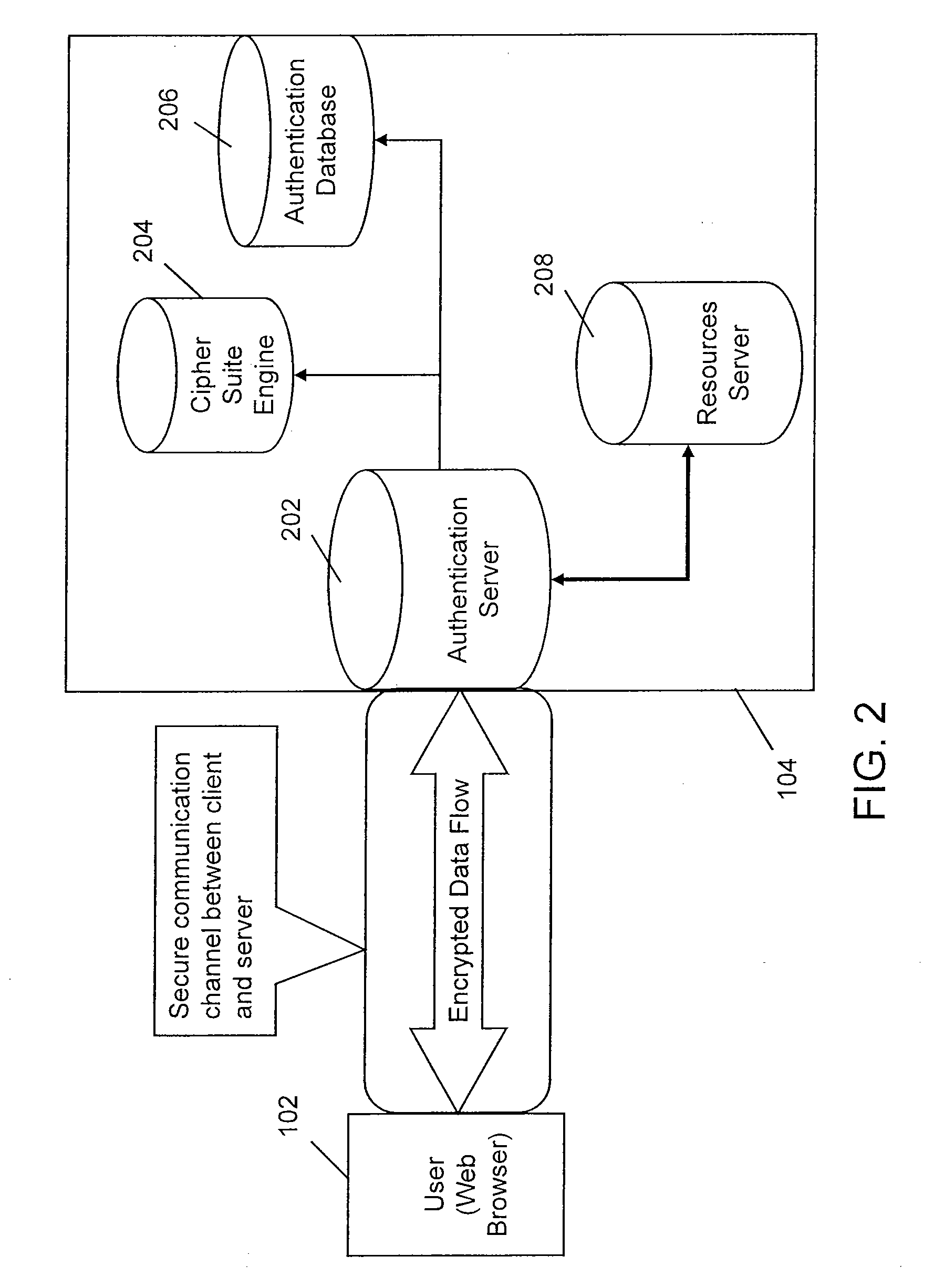
Method and apparatus for preventing phishing attacks
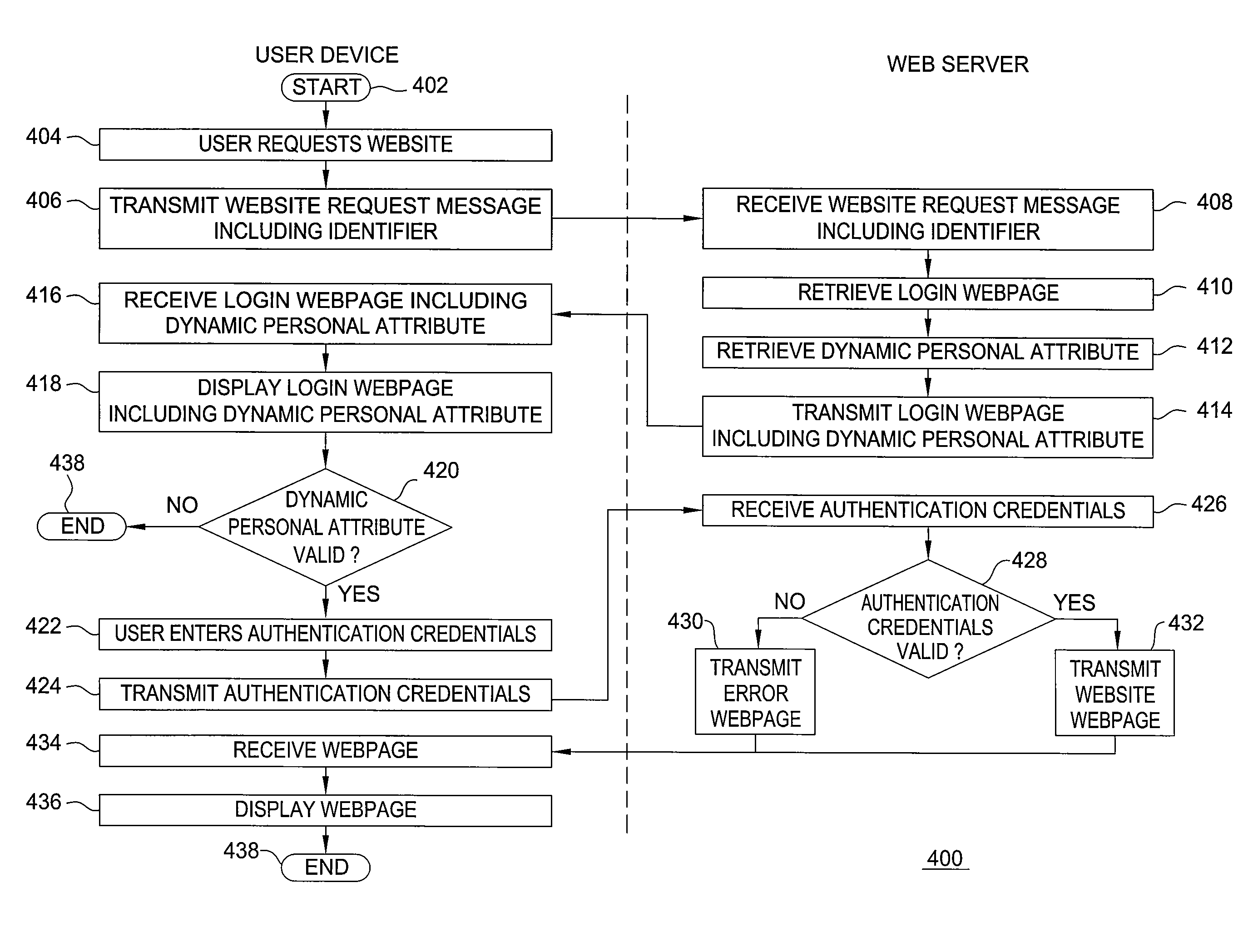
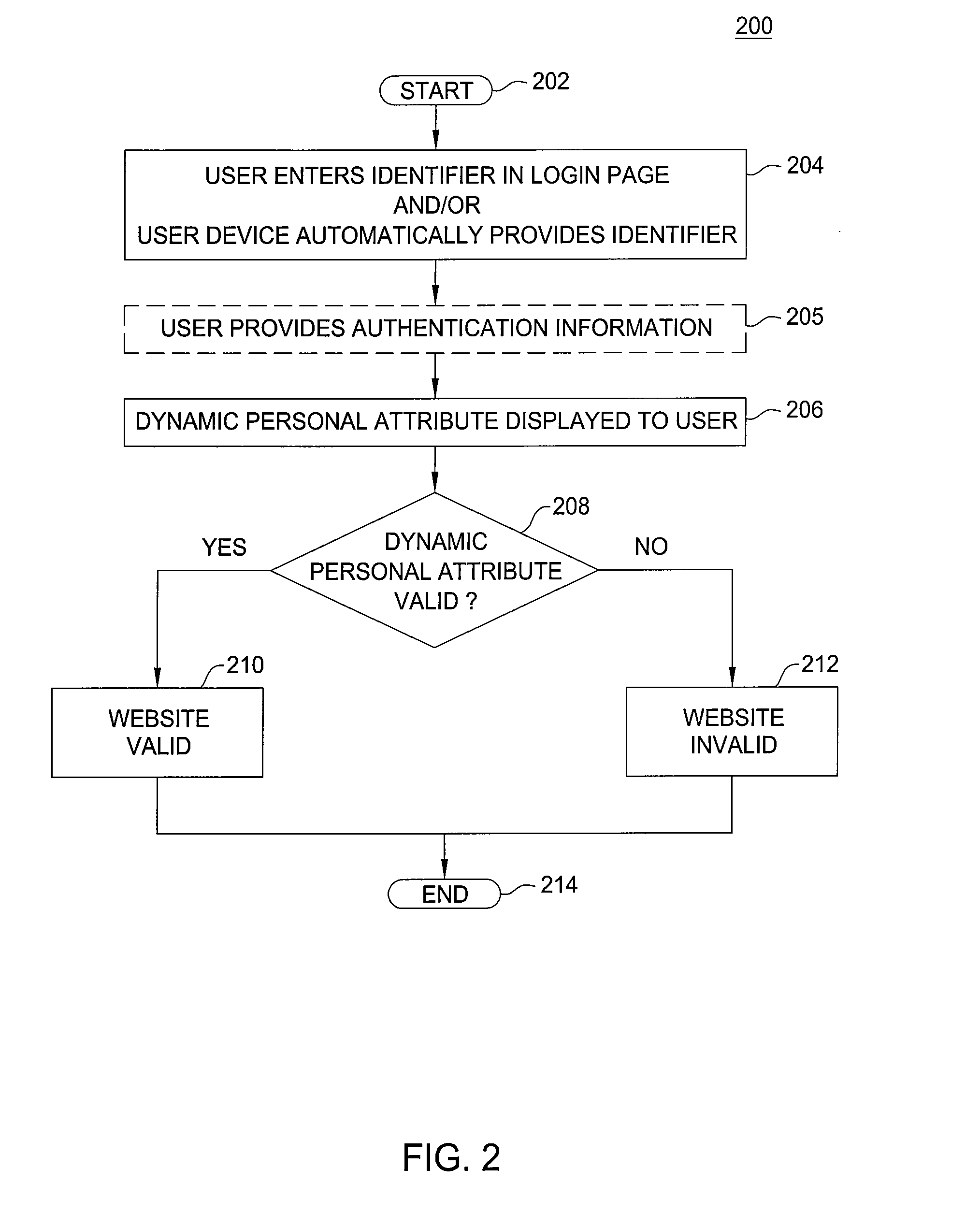
ActiveUS20090077637A1Preventing phishing attackFinanceDigital data processing detailsWeb serviceAuthentication server
The invention includes a method and apparatus for preventing phishing attacks. A first method, for informing a user that a remote server is valid, includes receiving a request for information available from the remote server where the request includes an identifier, obtaining a dynamic personal attribute associated with the user using the identifier, and propagating the dynamic personal attribute toward the user, wherein the dynamic personal attribute is adapted for use by the user in validating the remote server. The remote server may be a web server, an authentication server, or any other remote device with which the user may desire to authenticate. A second method, for informing a user that a received message is associated with a valid website, includes obtaining a dynamic personal attribute associated with a user, generating a message for the user where the message is adapted to enable the user to request a website and includes the dynamic personal attribute associated with the user, and propagating the message toward the user. The received message may be any type of message, such as an email message, an instant message, a text message, and the like.
Owner:ALCATEL LUCENT SAS
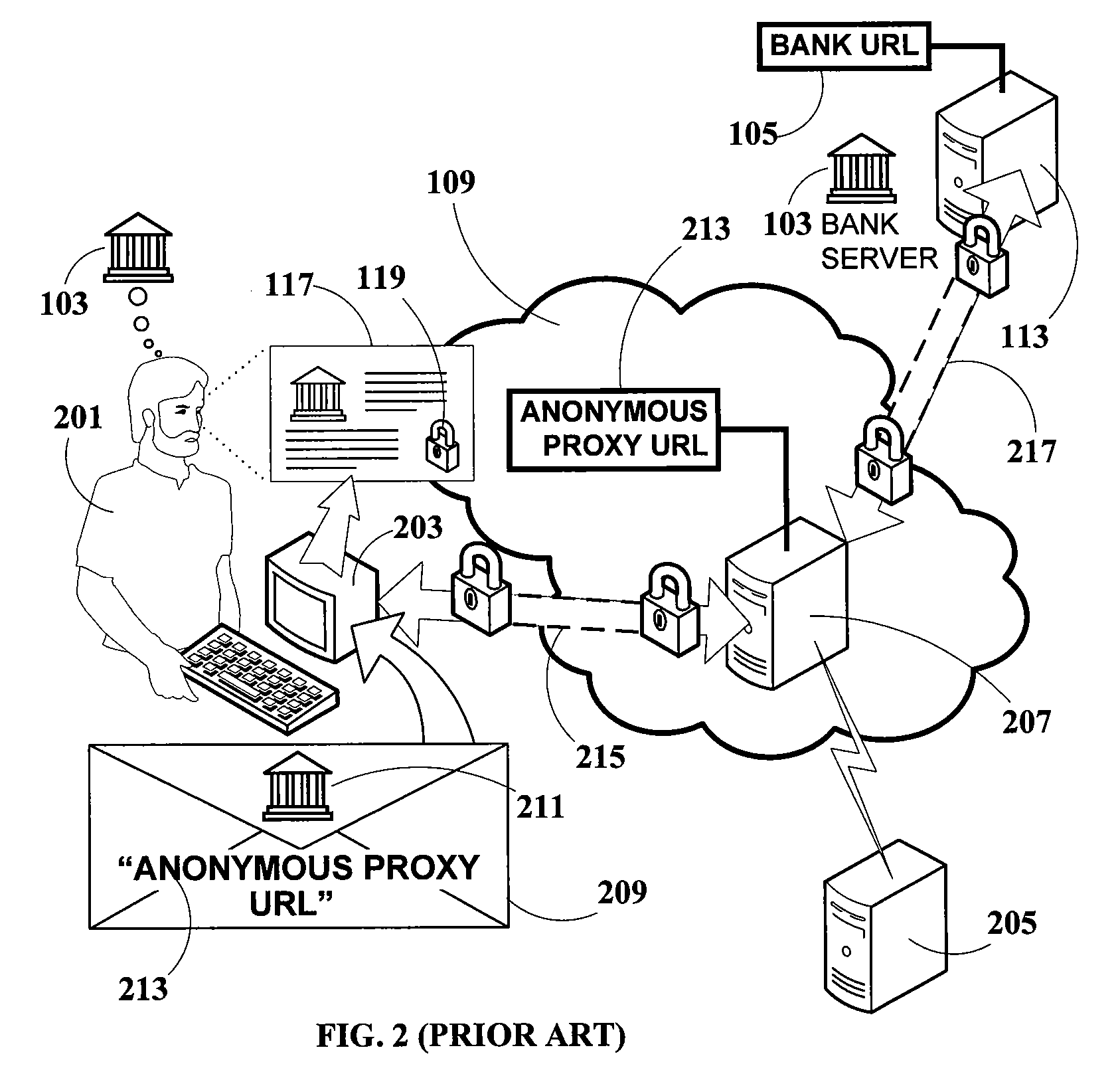
Method and system for detecting, blocking and circumventing man-in-the-middle attacks executed via proxy servers
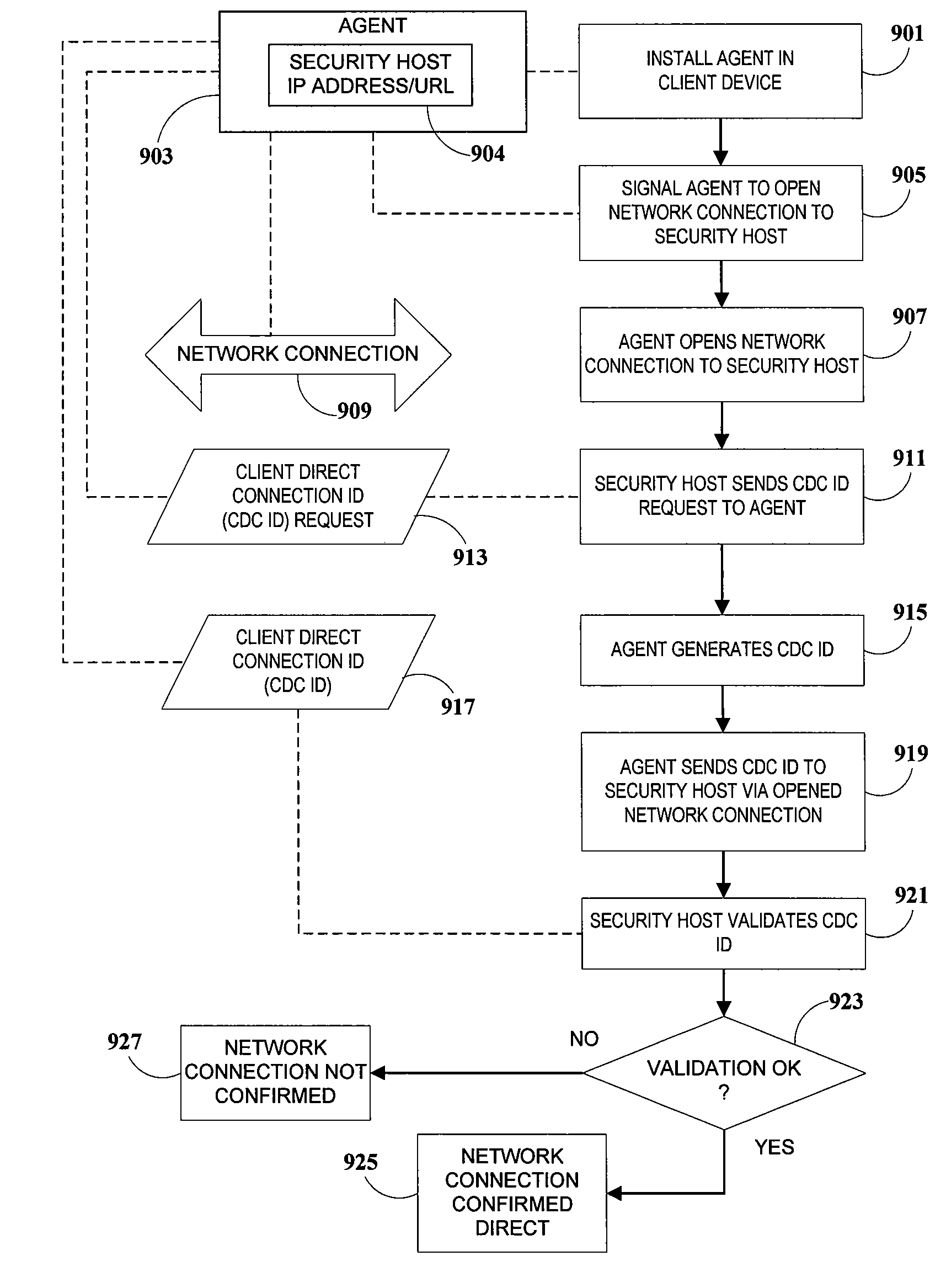
InactiveUS20100088766A1Avoids user distressAvoids concernMemory loss protectionError detection/correctionThird partyMan-in-the-middle attack
A method for detecting and blocking a Man-in-the-Middle phishing attack carried out on a client connection which has been fraudulently routed through an anonymous proxy server. An agent downloaded to the client device opens a client direct connection to the security host protecting against the attack and sends a client direct connection ID to the security host for validation. By comparing IP addresses correlated via the validated client direct connection ID, the security host determines whether the original connection is direct (secure) or indirect (attack via phishing proxy). The detection and blocking can be performed by the service provider's server or by a third-party validation server handling all security without additional requirements on the service provider server. In addition to detecting and blocking such attacks, methods for client direct connection ID, as well as automatic transparent and seamless attack circumvention and preemptive circumvention are disclosed.
Owner:SAFENET DATA SECURITY ISRAEL
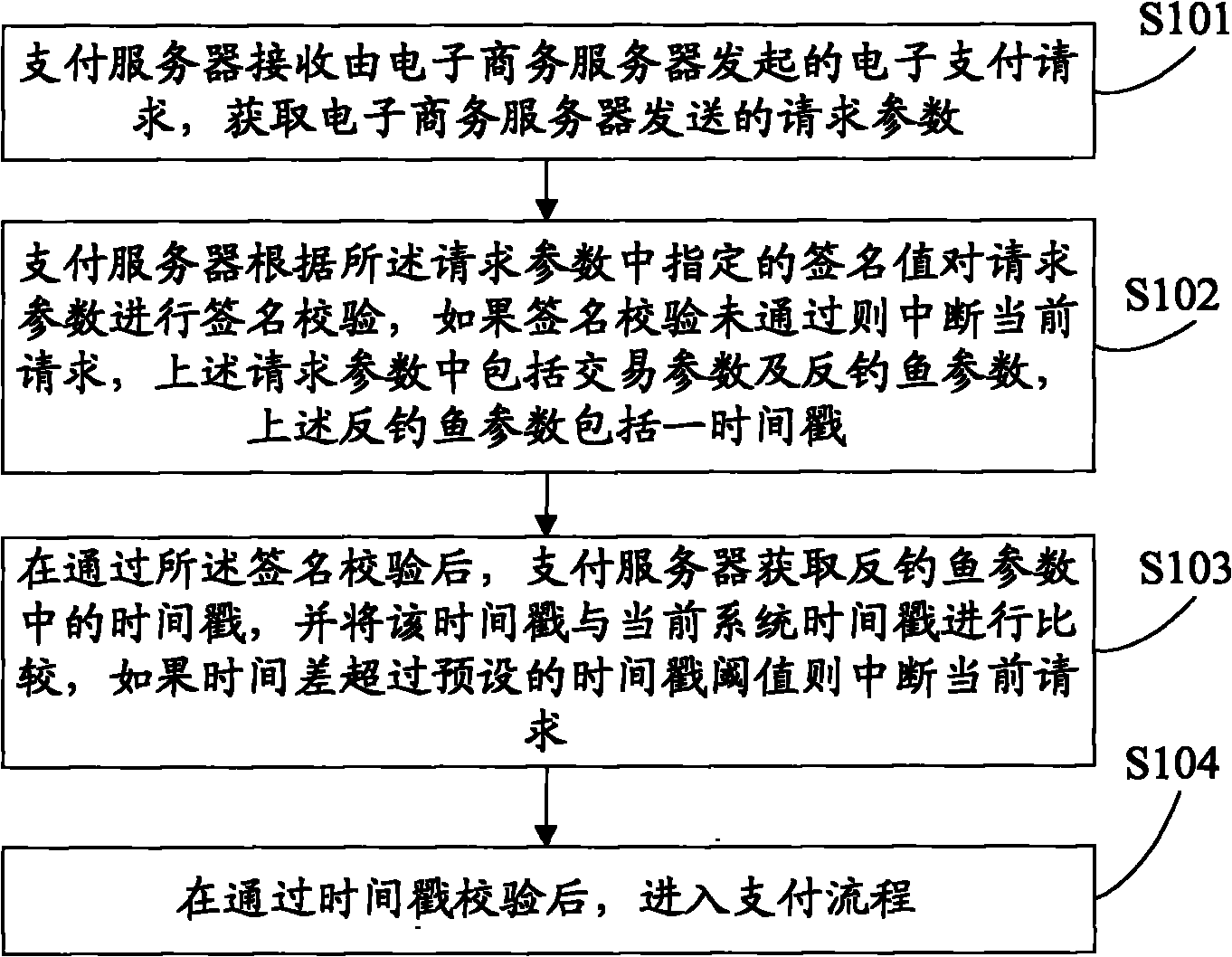
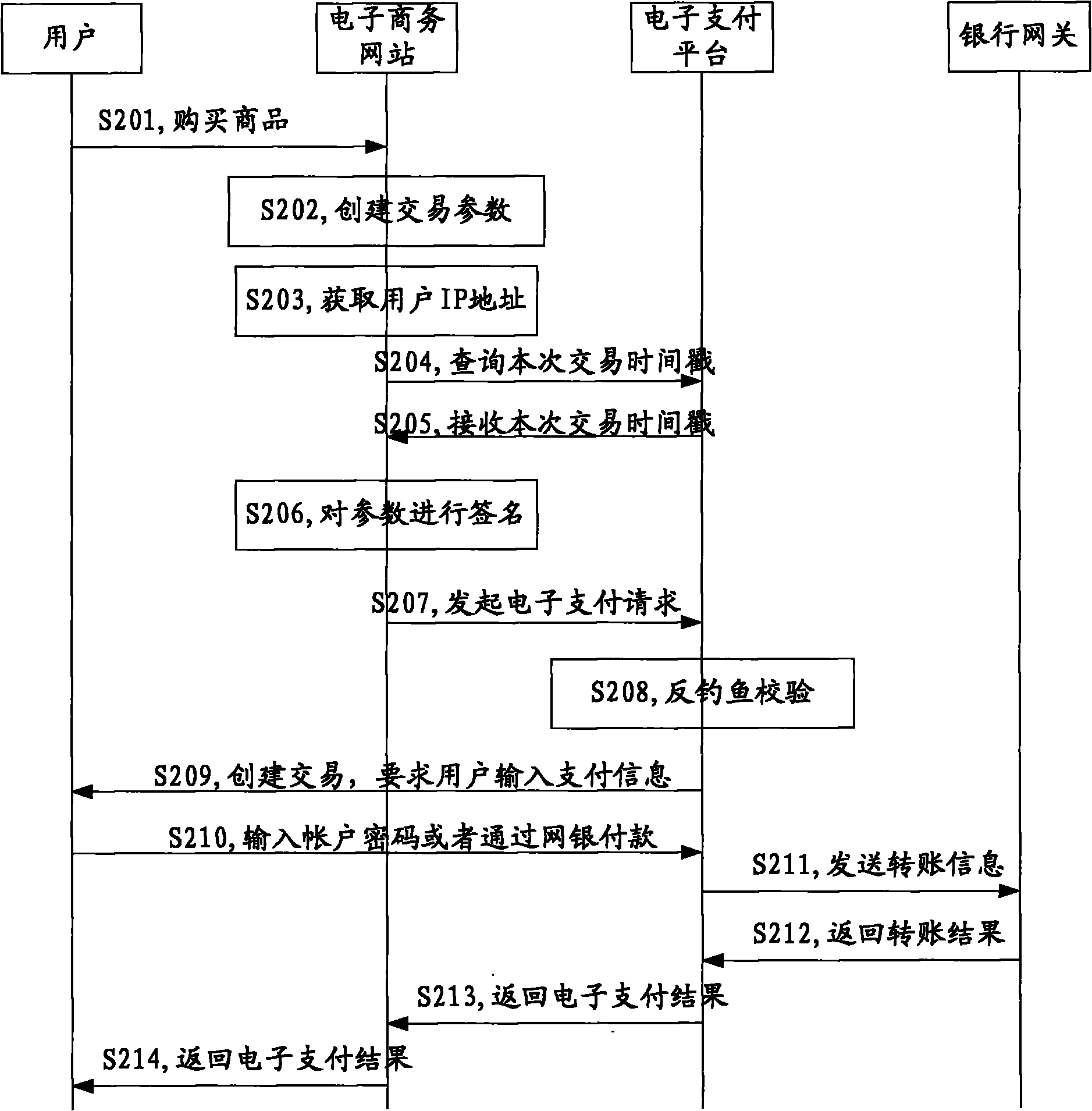
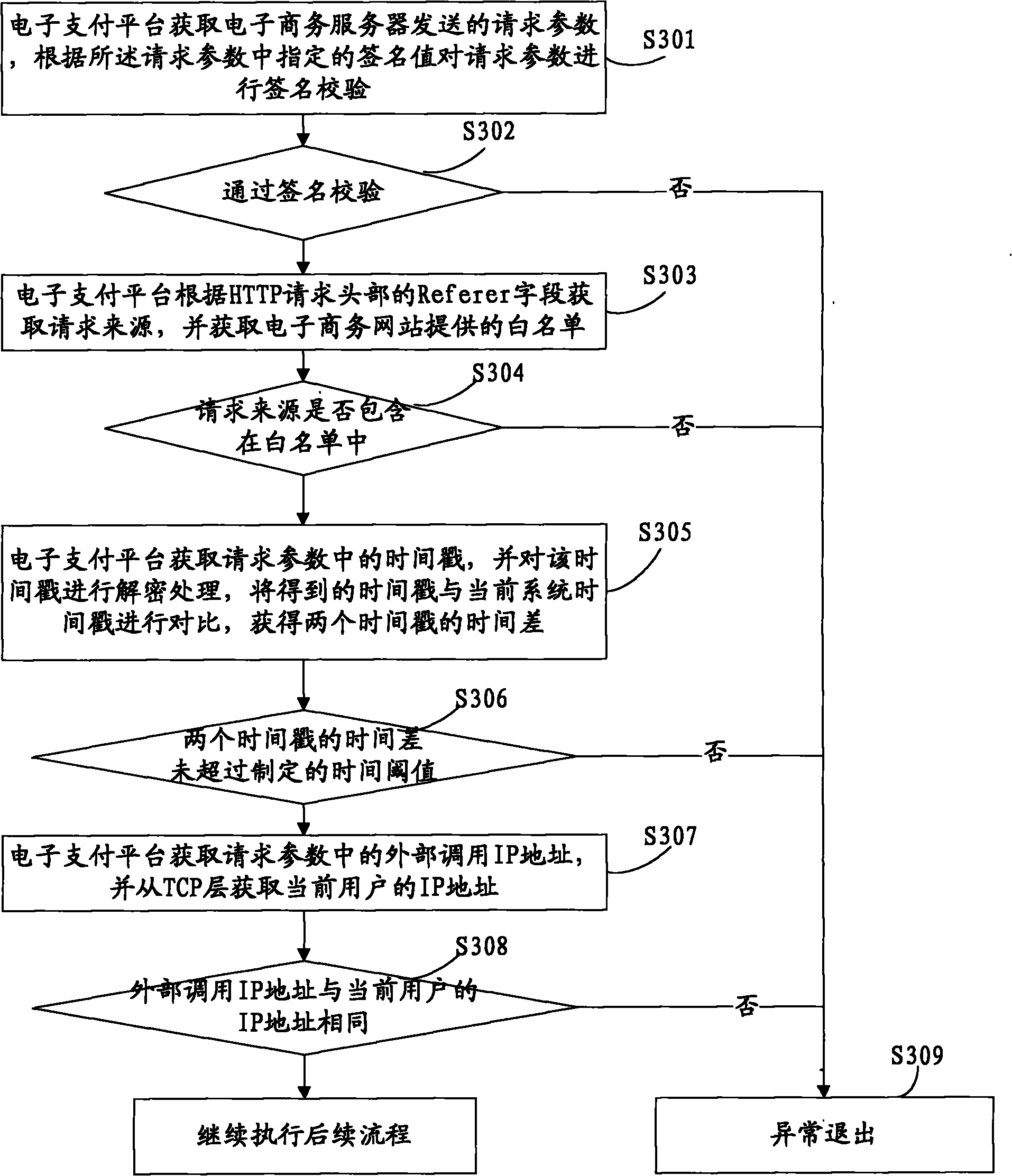
On-line payment method and system
An embodiment of the present invention discloses an on-line payment method and system. The scheme provided by the embodiment of the invention comprises the steps of: when receiving an electronic payment request, preventing service parameters from being reused and initiating a phishing attack through various specific anti-phishing verifications, for example, increasing the timeliness of the service parameters by timestamps of anti-phishing parameters; verifying the request source, i.e., determining whether the request source for this request is one in a white list or not through the request source white list, thereby completely eradicating the possibility of being embezzled by a phishing website from the request source; and determining whether a creater of an external business and a payer of an internal business are the same user by comparing an IP address of an external call with an IP address obtained by the local, so as to prevent someone paying for a business created by the phishing website itself. These verification methods monitor the business parameters from various aspects and realize protection and control of the behavior of anti-phishing.
Owner:ALIBABA GRP HLDG LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com