Patents
Literature
99 results about "Prospective data" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Prospective Data Collection. Sometimes the data is just not available... Sometimes you need to collect patient care data that is not already available and cannot be obtained from existing records or through a survey. In this case, you need to create your own data collection form that can be used.
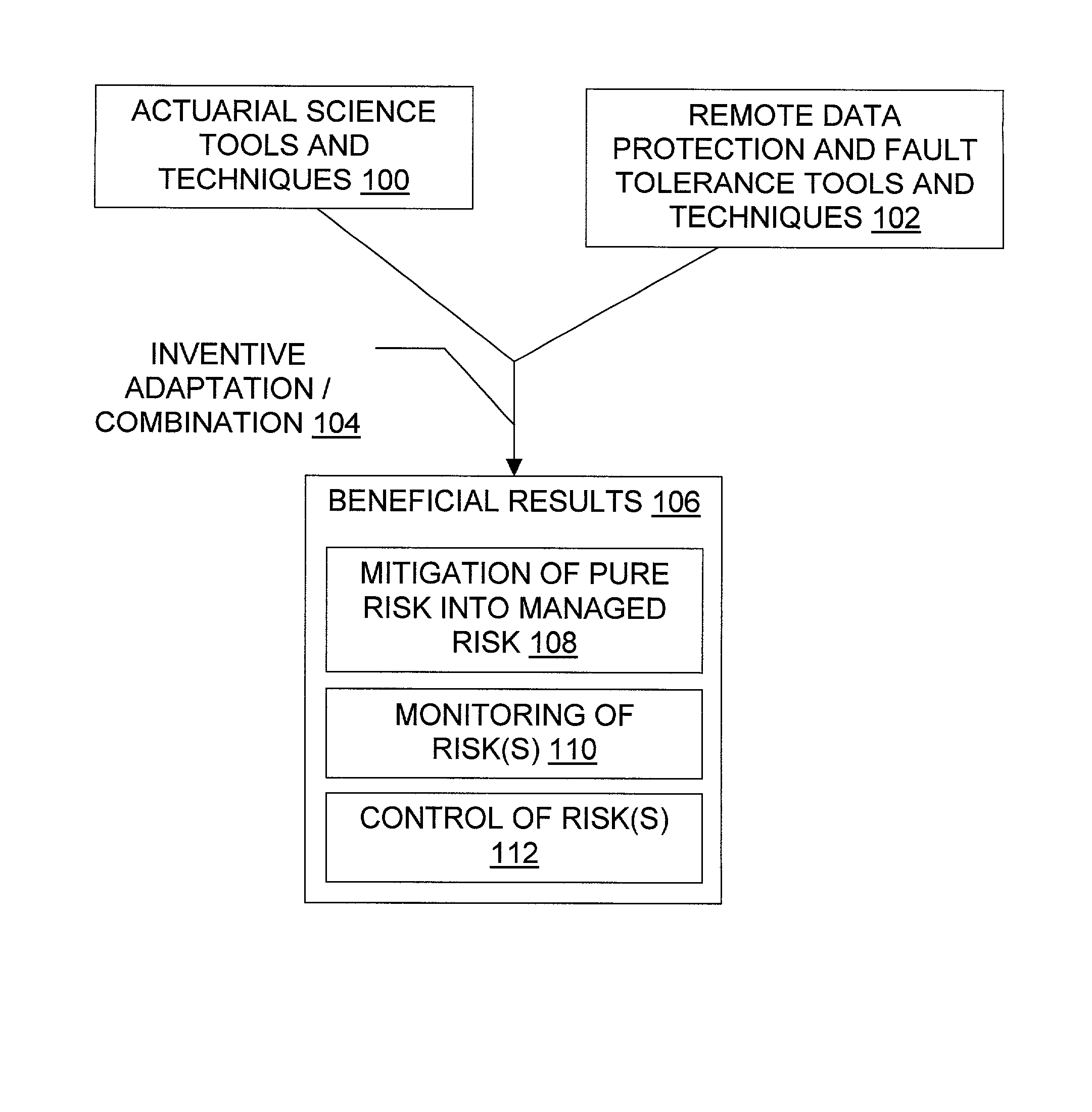
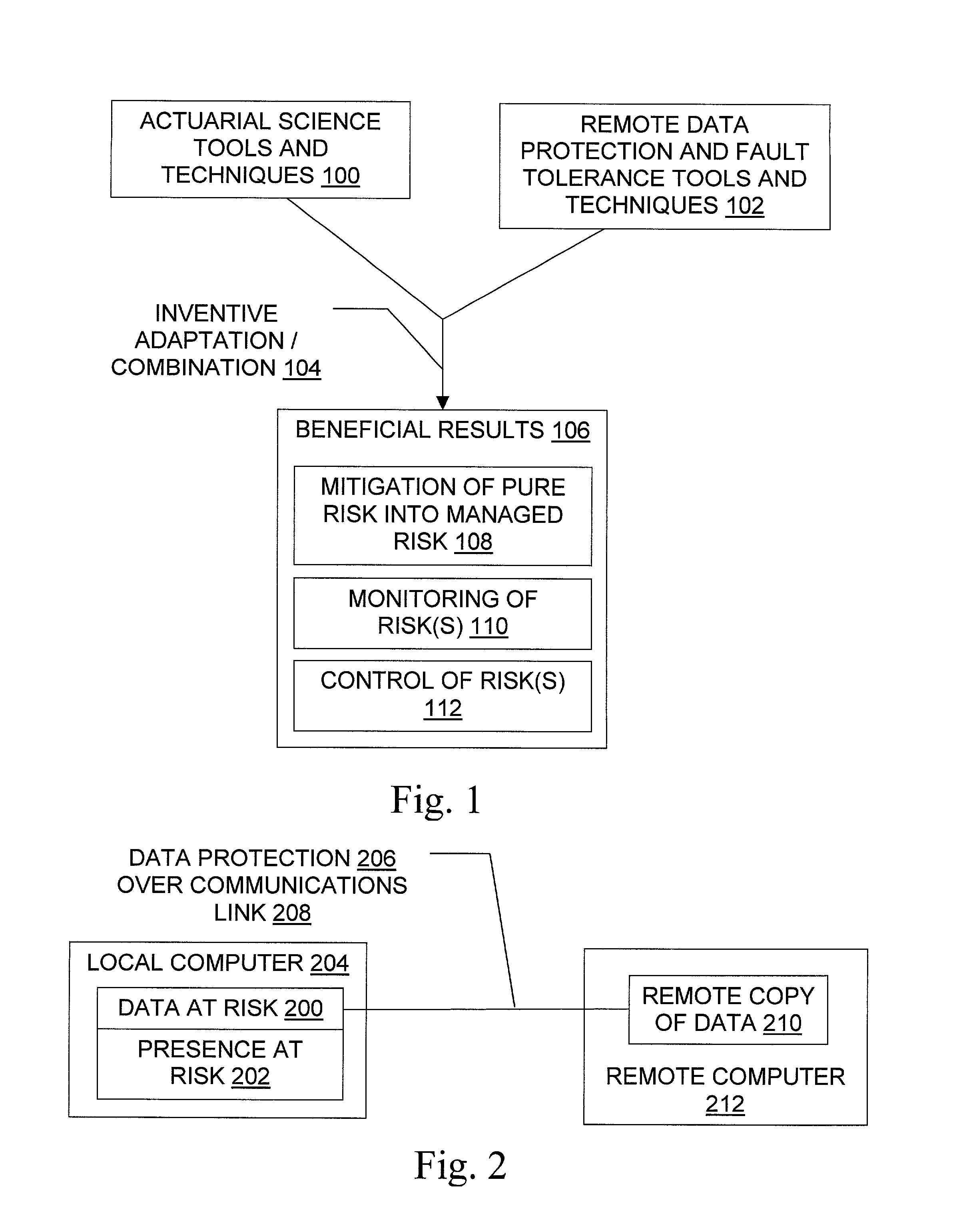
Data/presence insurance tools and techniques
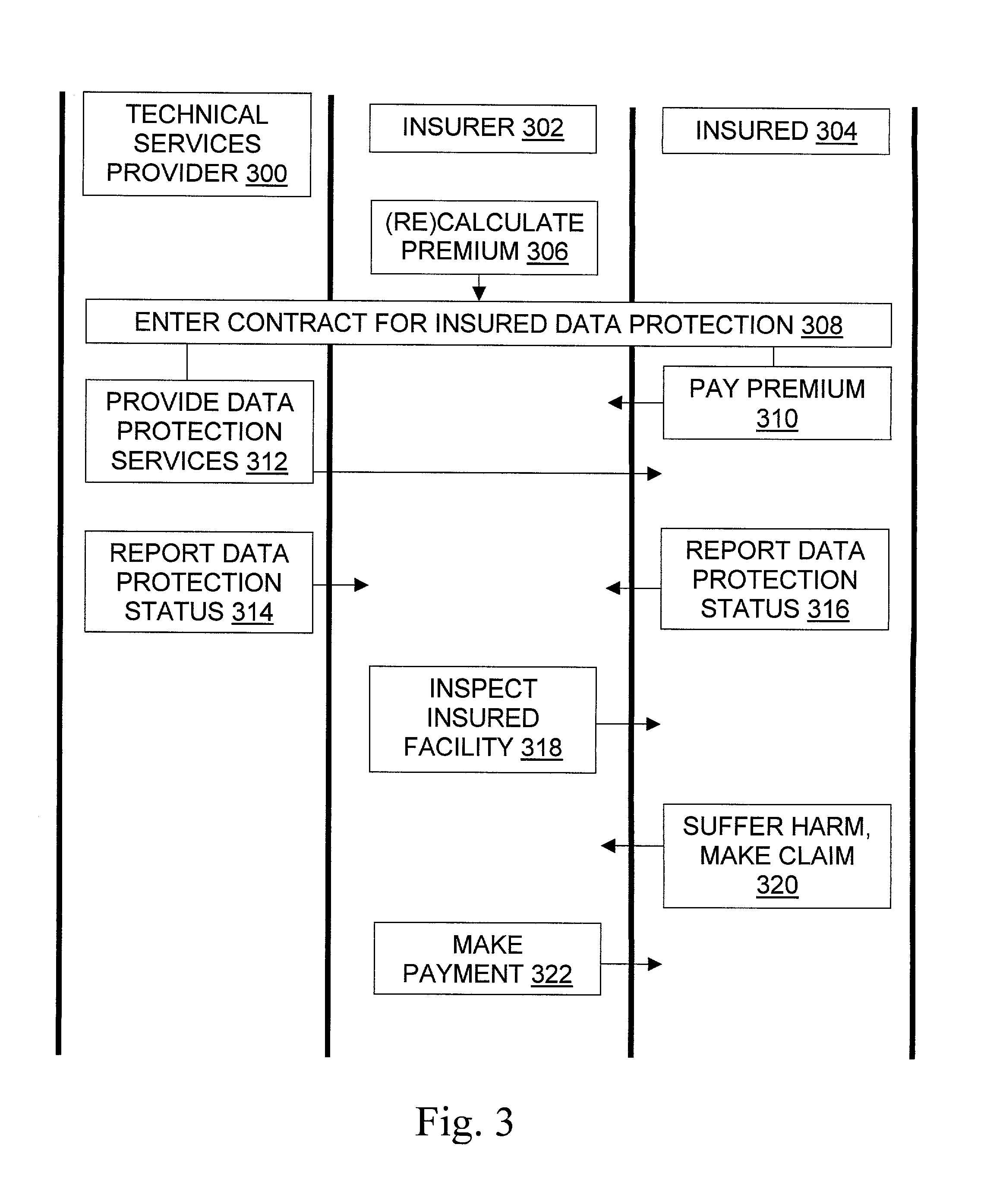
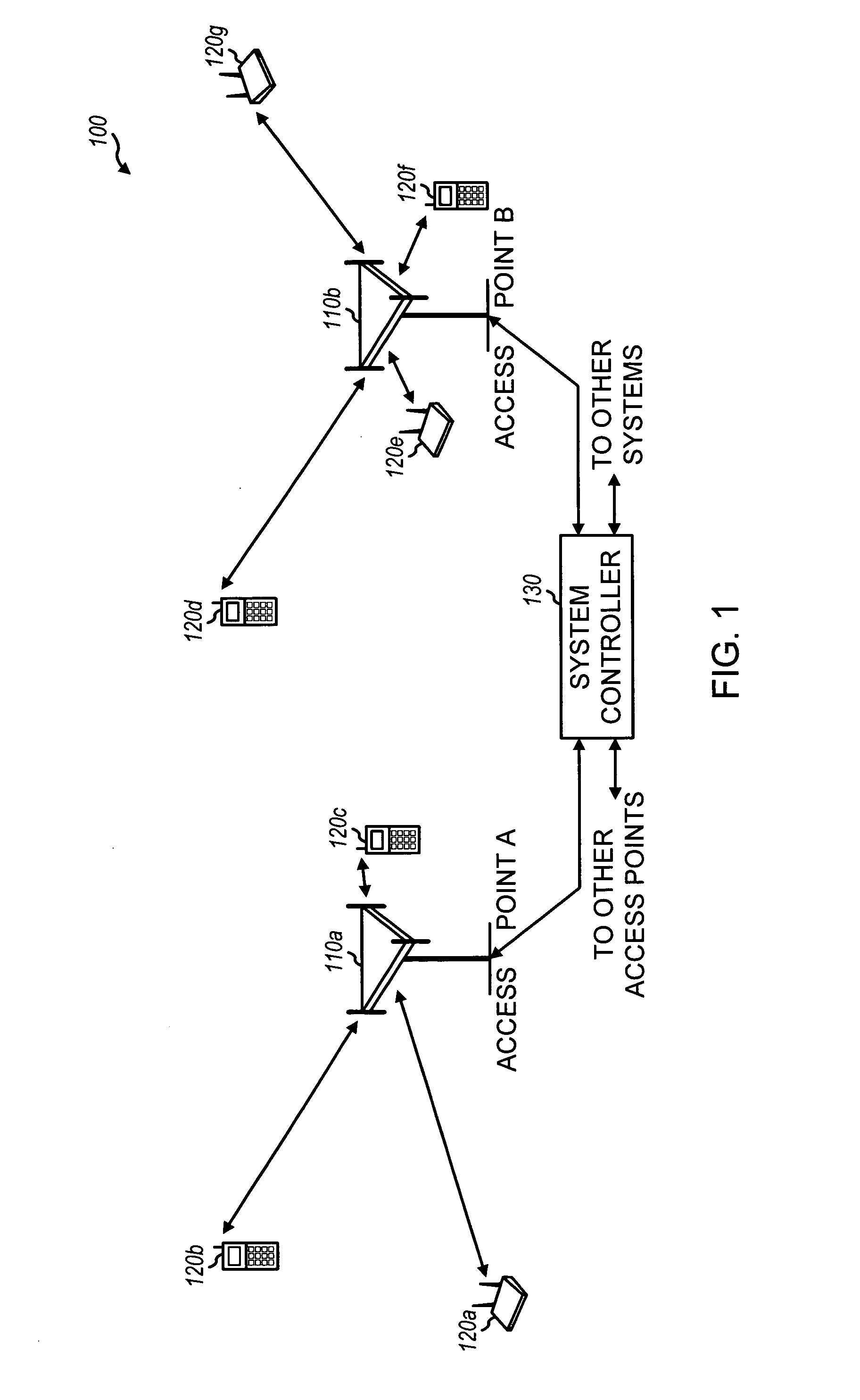
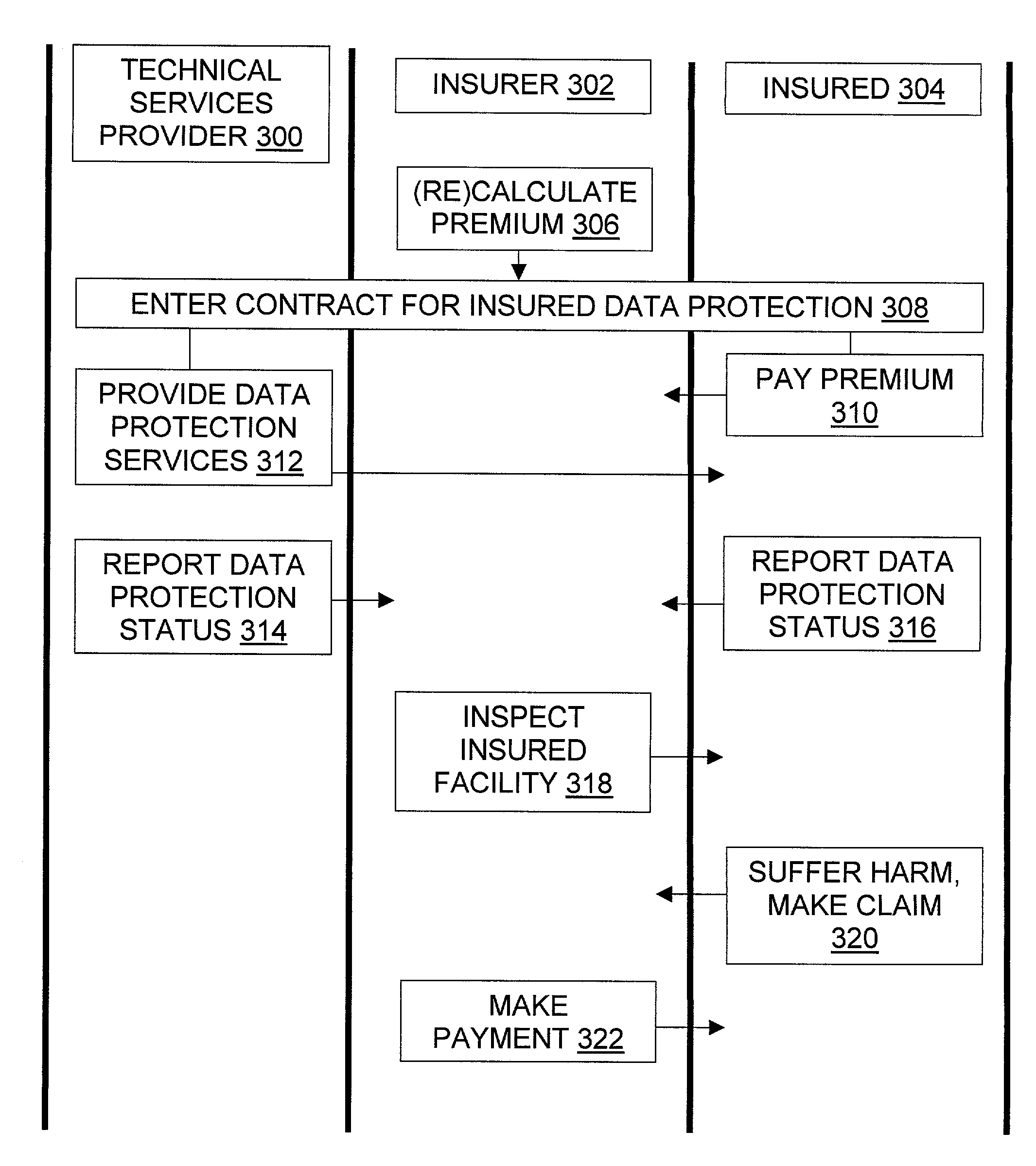
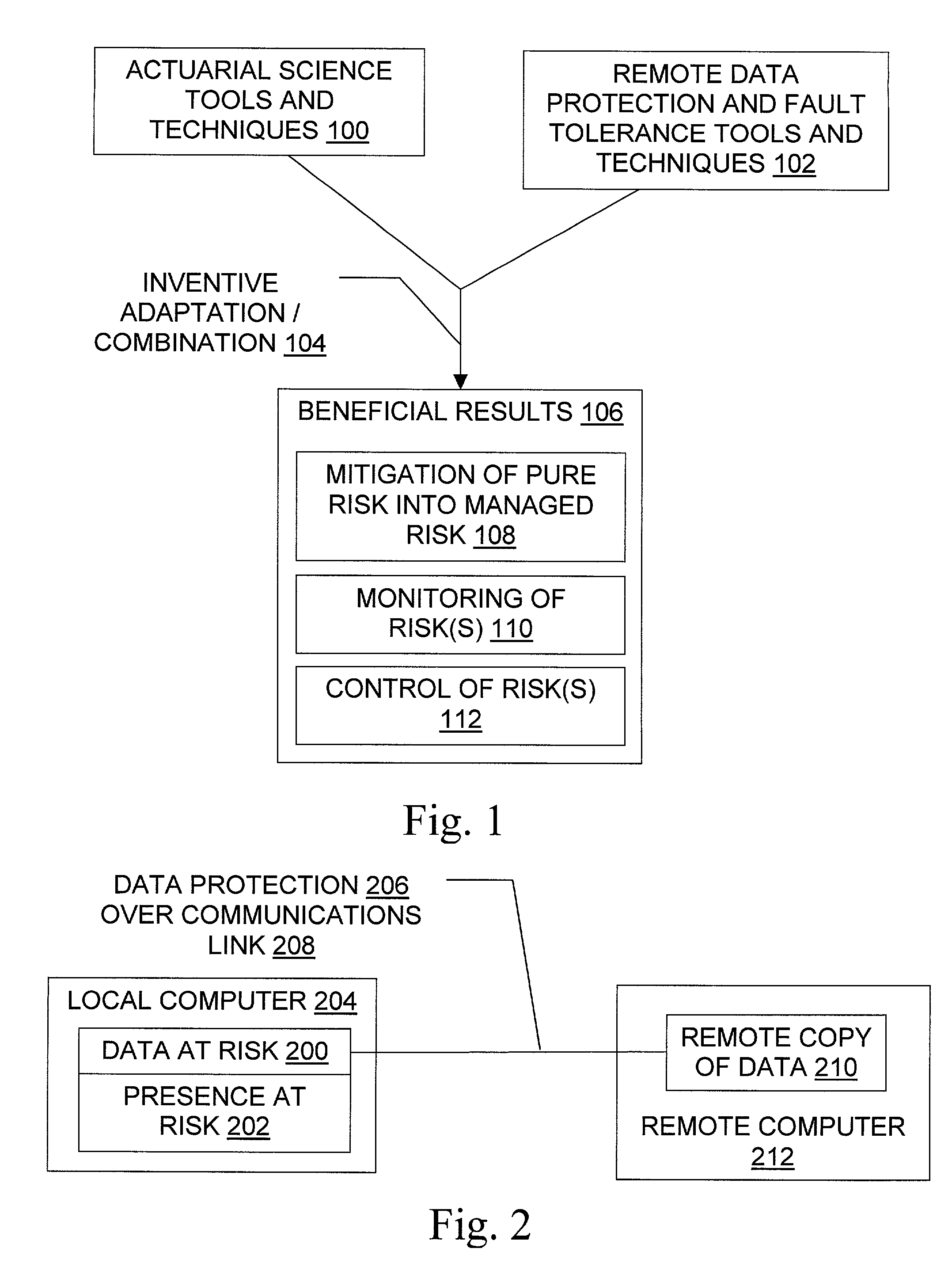
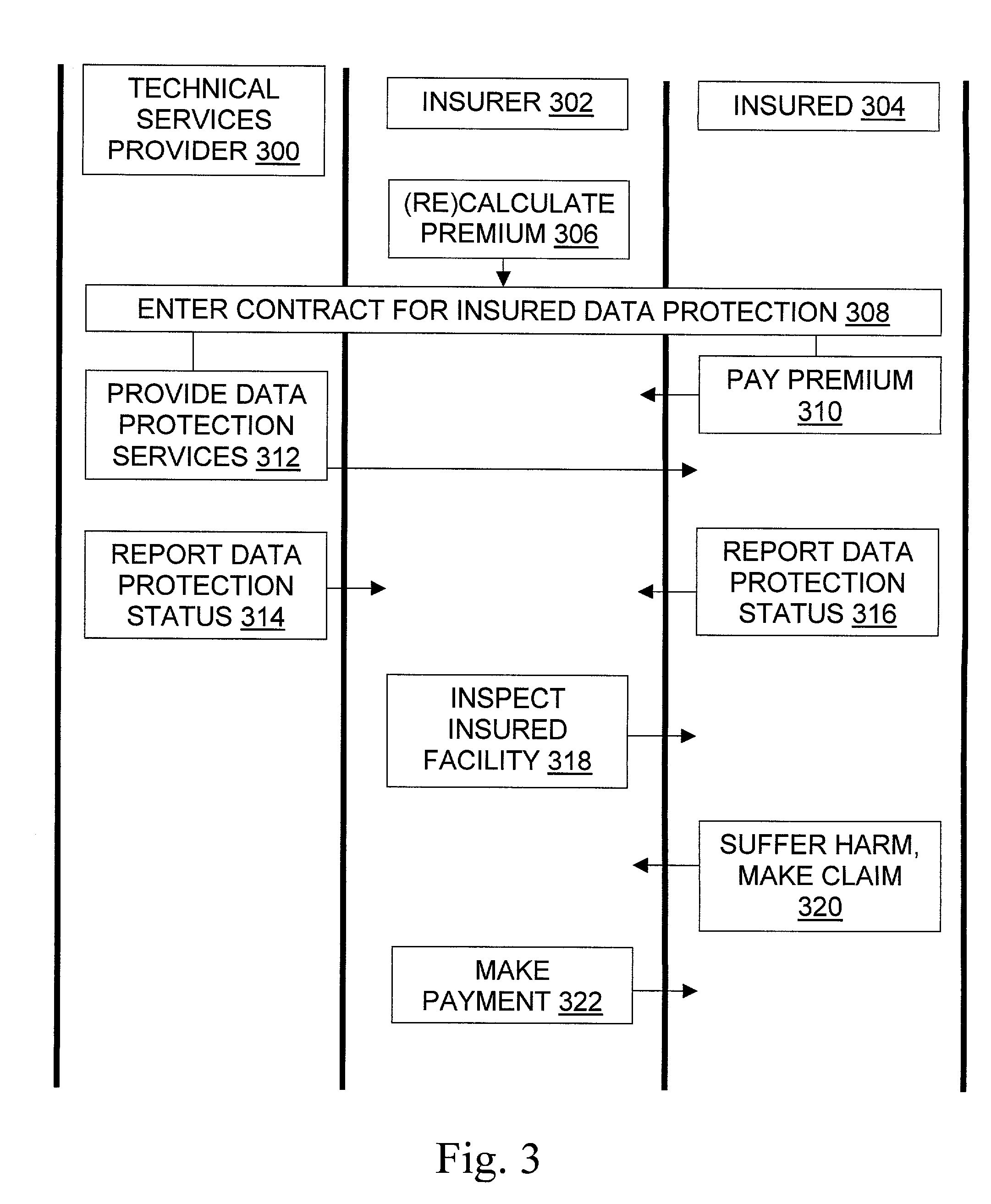
Methods for insurance of online presence (202) and / or data (200) are described. An insurer (302) contracts with an insured entity (304) in an agreement (308) under which a premium (310) is paid for insurance coverage. The premium is calculated (306) using a pure premium method (400) or a loss ratio premium method (402), in a manner that depends on factors such as expected virus scan results (404), expected data recovery time (406), expected geographic spread (408), use of multiple recovery methods (410), and other information regarding the insured entity's business and the technical protection services (206) to be used. In some embodiments, the technical protection services are provided under the agreement by a third party technical services provider (300). Systems, signals, and configured media are also described.
Owner:INTELLECTUAL VENTURES II
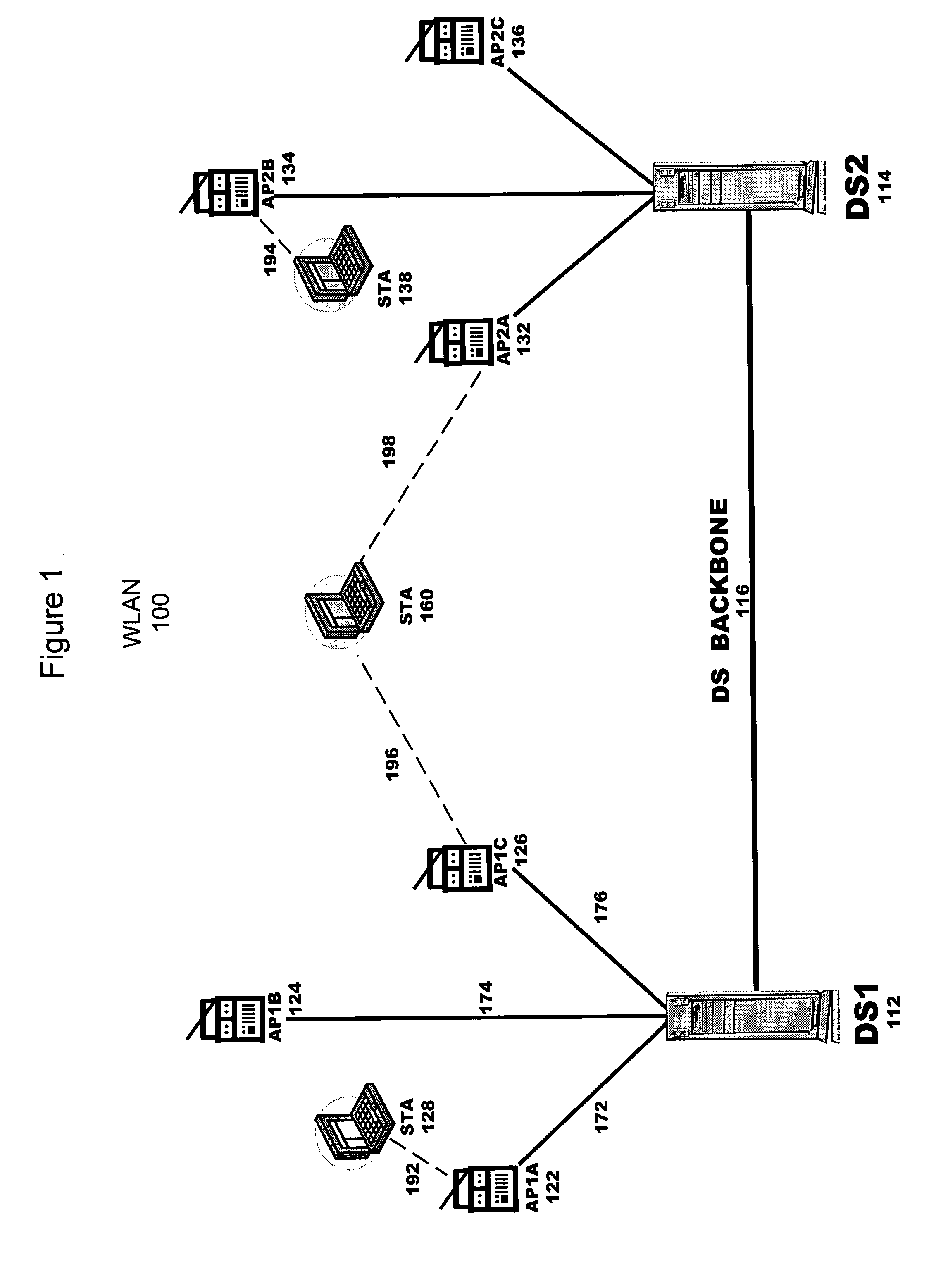
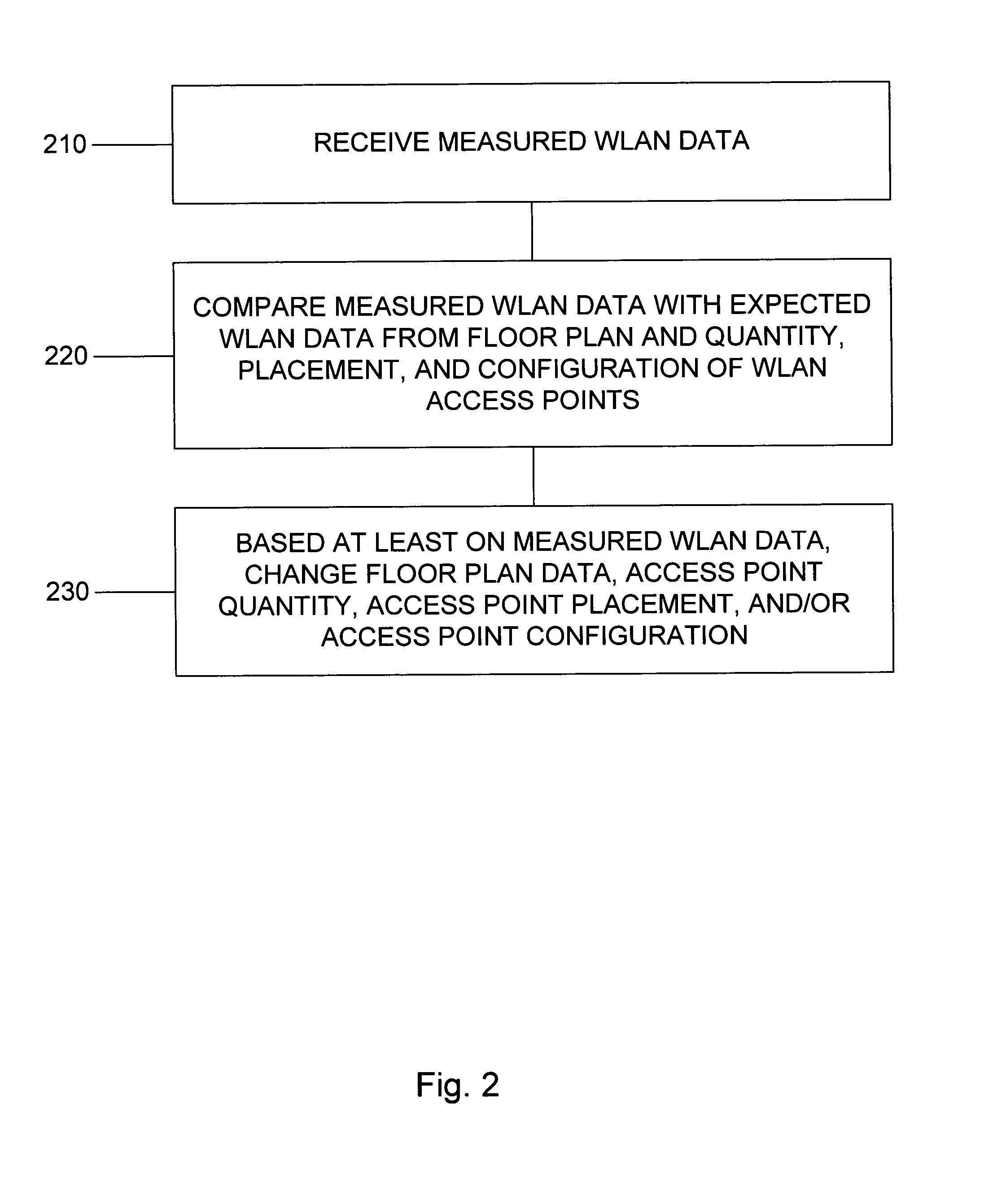
Wireless LAN measurement feedback
Measured data, such as WLAN data, are received. The measured data are compared with expected data, such as expected WLAN data. Expected WLAN data can be generated from various sources, for example floor plan data and access point data (e.g., quantity, placement, and / or configuration). Based on such measured data, WLAN features can be changed, such as floor plan and / or access point data (e.g., quantity, placement, and / or configuration).
Owner:TRAPEZE NETWORKS
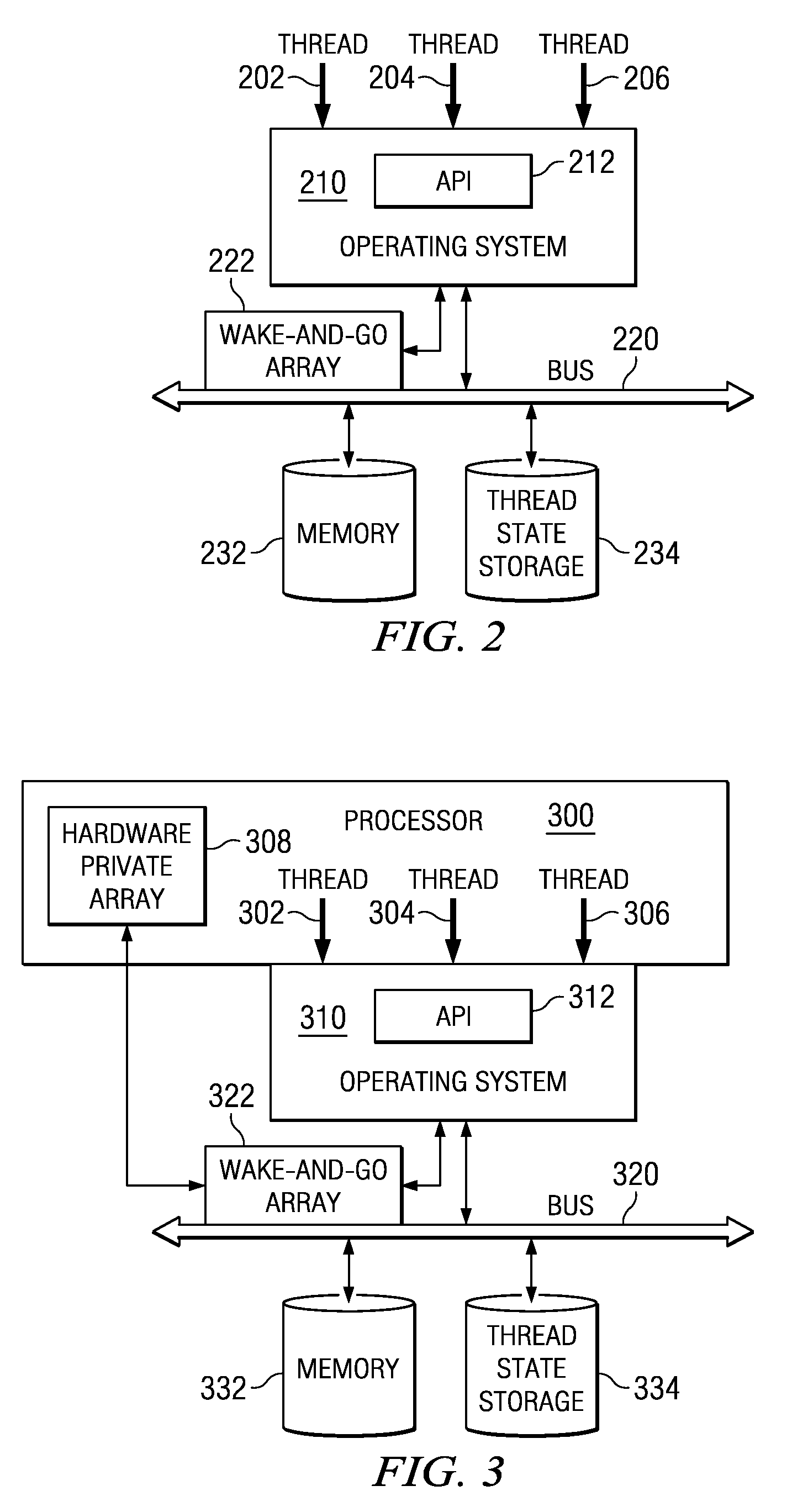
Wake-and-Go Mechanism with Data Monitoring
ActiveUS20090199029A1Energy efficient ICTVolume/mass flow measurementOperational systemArray data structure
A wake-and-go mechanism is provided for a data processing system. The wake-and-go mechanism recognizes a programming idiom, specialized instruction, operating system call, or application programming interface call that indicates that a thread is waiting for an event. The wake-and-go mechanism updates a wake-and-go array with a target address, expected data value, and comparison type associated with the event. The thread then goes to sleep until the event occurs. The wake-and-go array may be a content addressable memory (CAM). When a transaction appears on the symmetric multiprocessing (SMP) fabric that modifies the value at a target address in the CAM, logic associated with the CAM performs a comparison based on the data value being written, expected data value, and comparison type.
Owner:IBM CORP
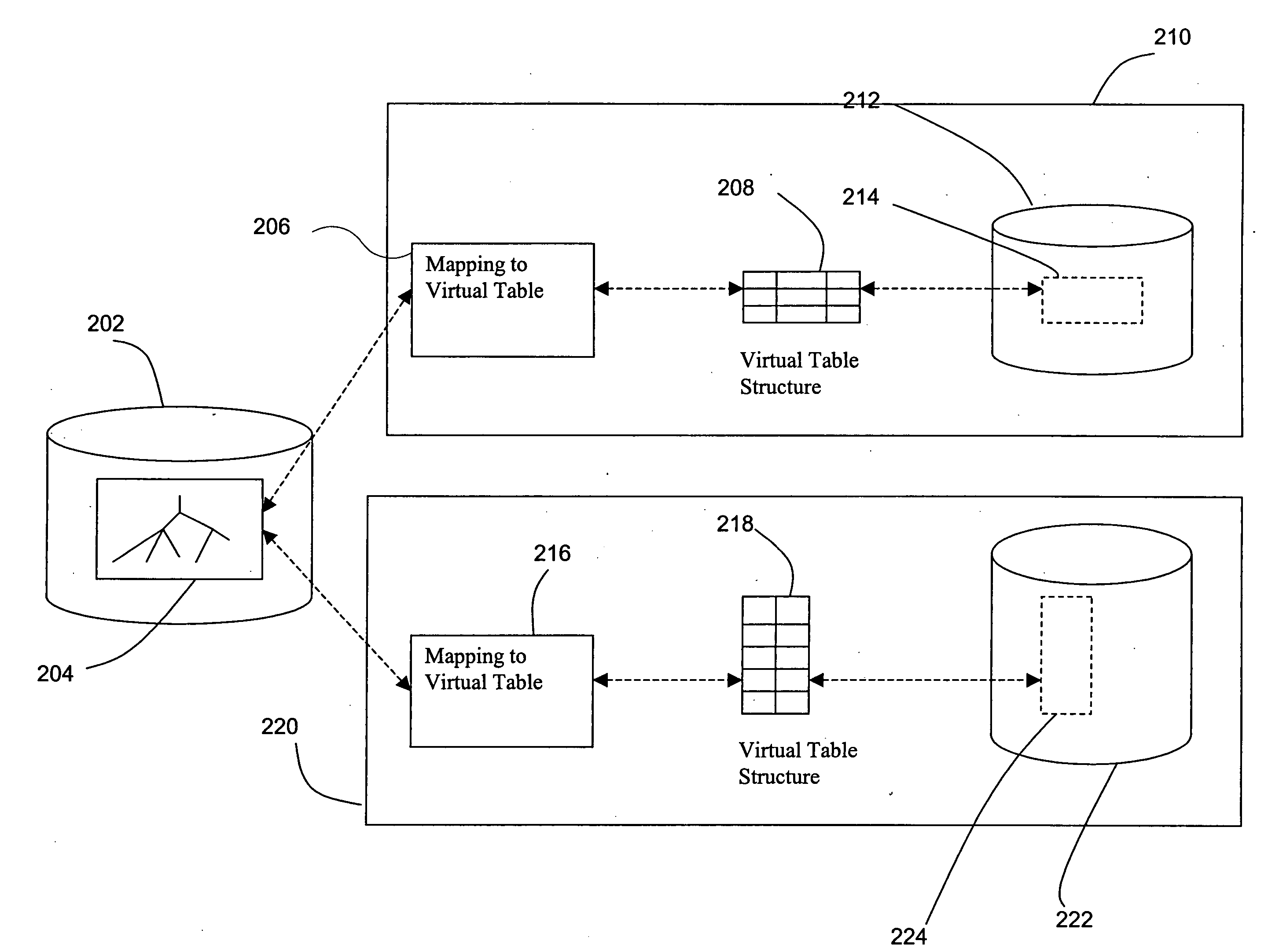
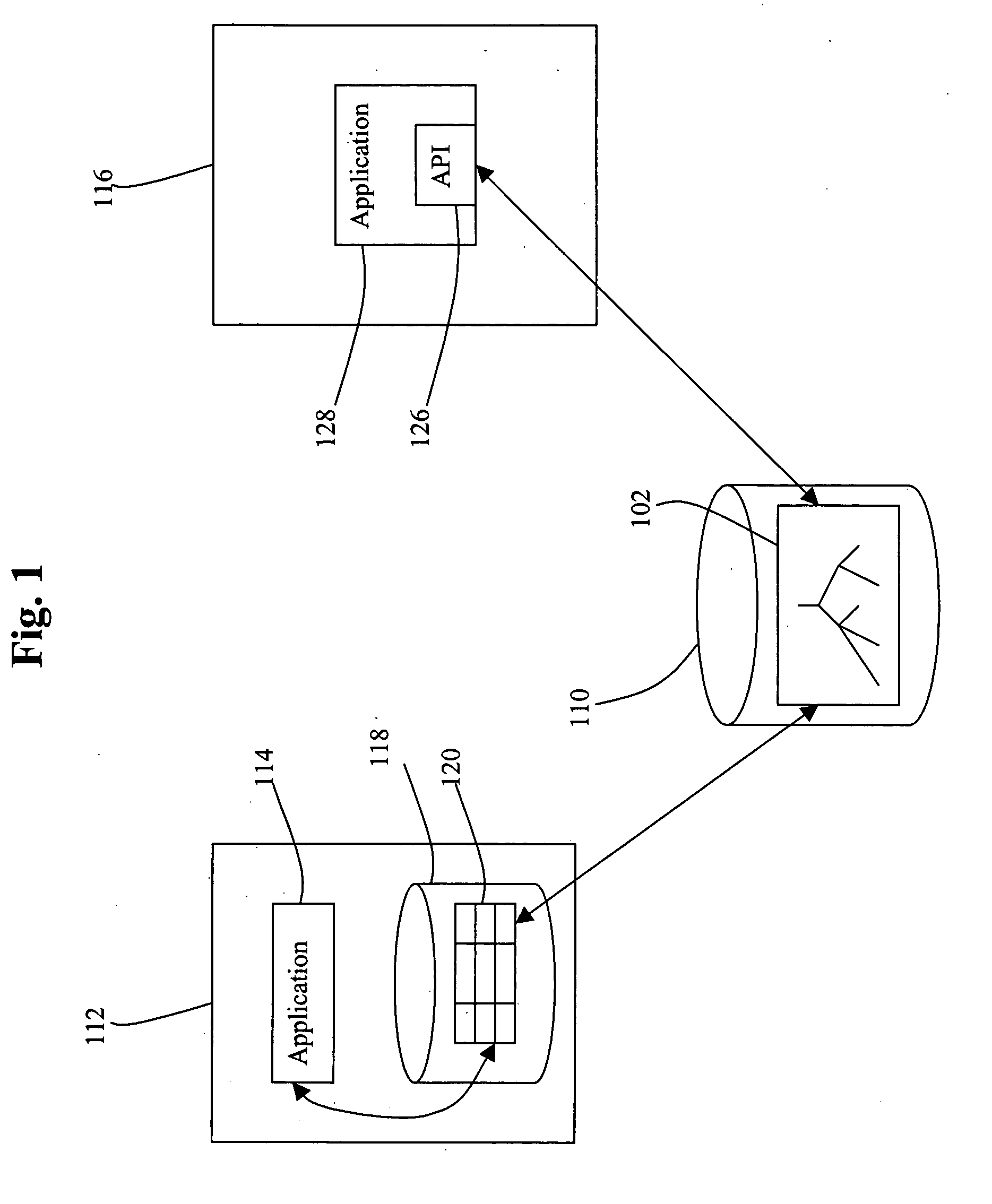
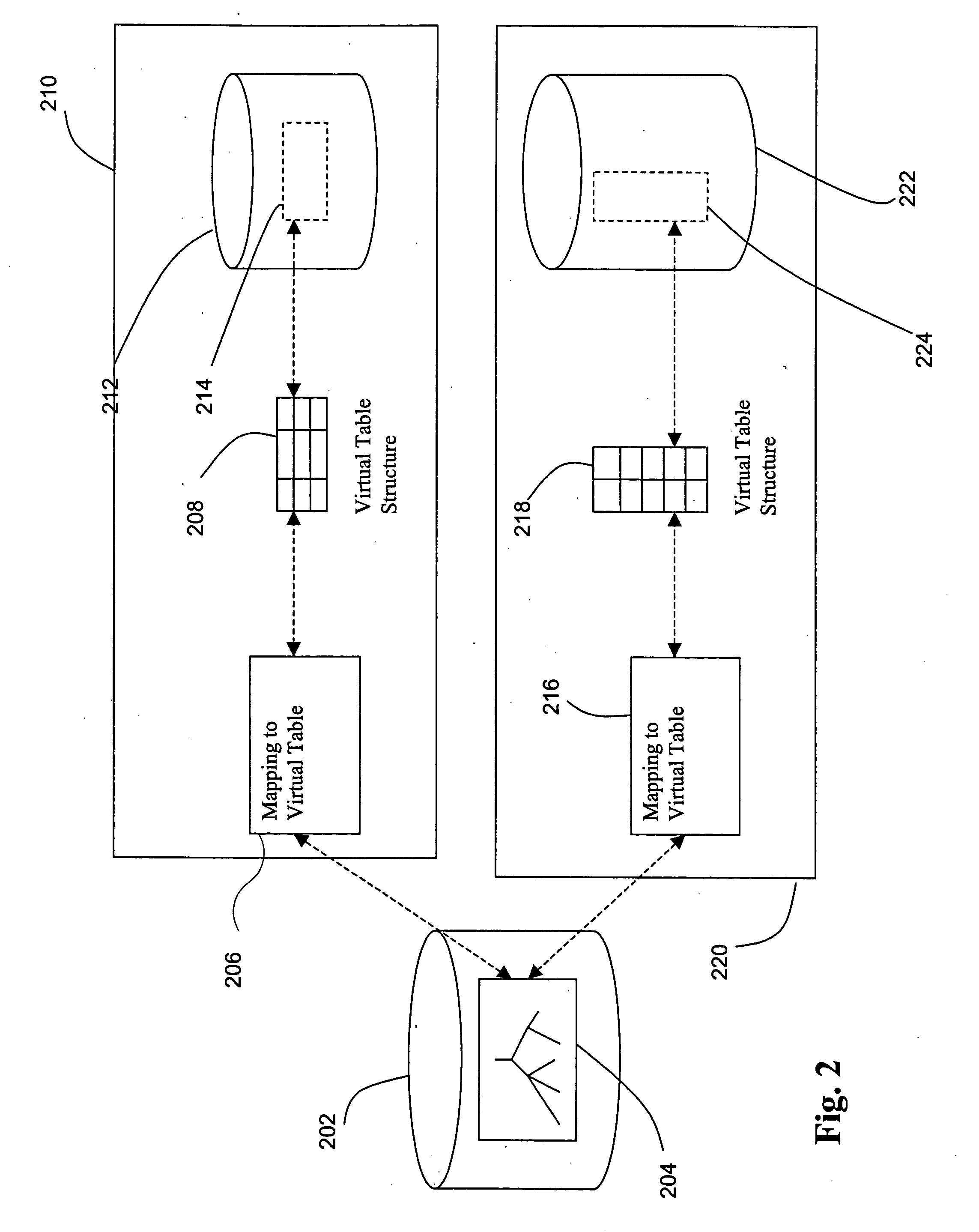
Method and system for implementing and accessing a virtual table on data from a central server
ActiveUS20050289174A1Providing transparencyEfficient use ofDigital data information retrievalSpecial data processing applicationsRelational databaseCentralized management
A method, mechanism, and computer program product for managing, referencing, and accessing centrally managed information are disclosed. Transparency is provided to the centrally managed data by introducing a mapping system between locally expected data and the central data repository. This allows, for example, local relational database systems to transparently access information from a central LDAP directory.
Owner:ORACLE INT CORP
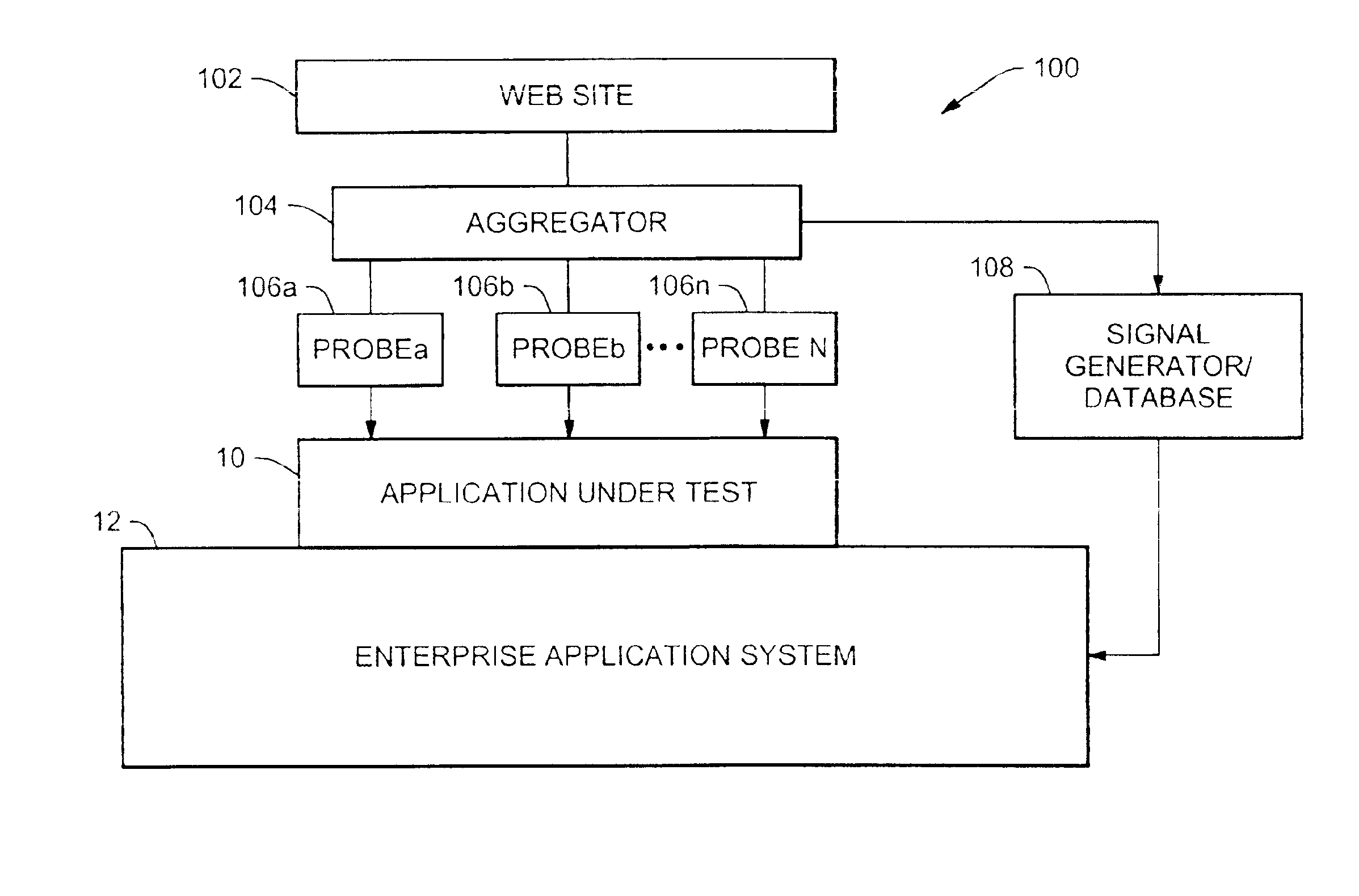
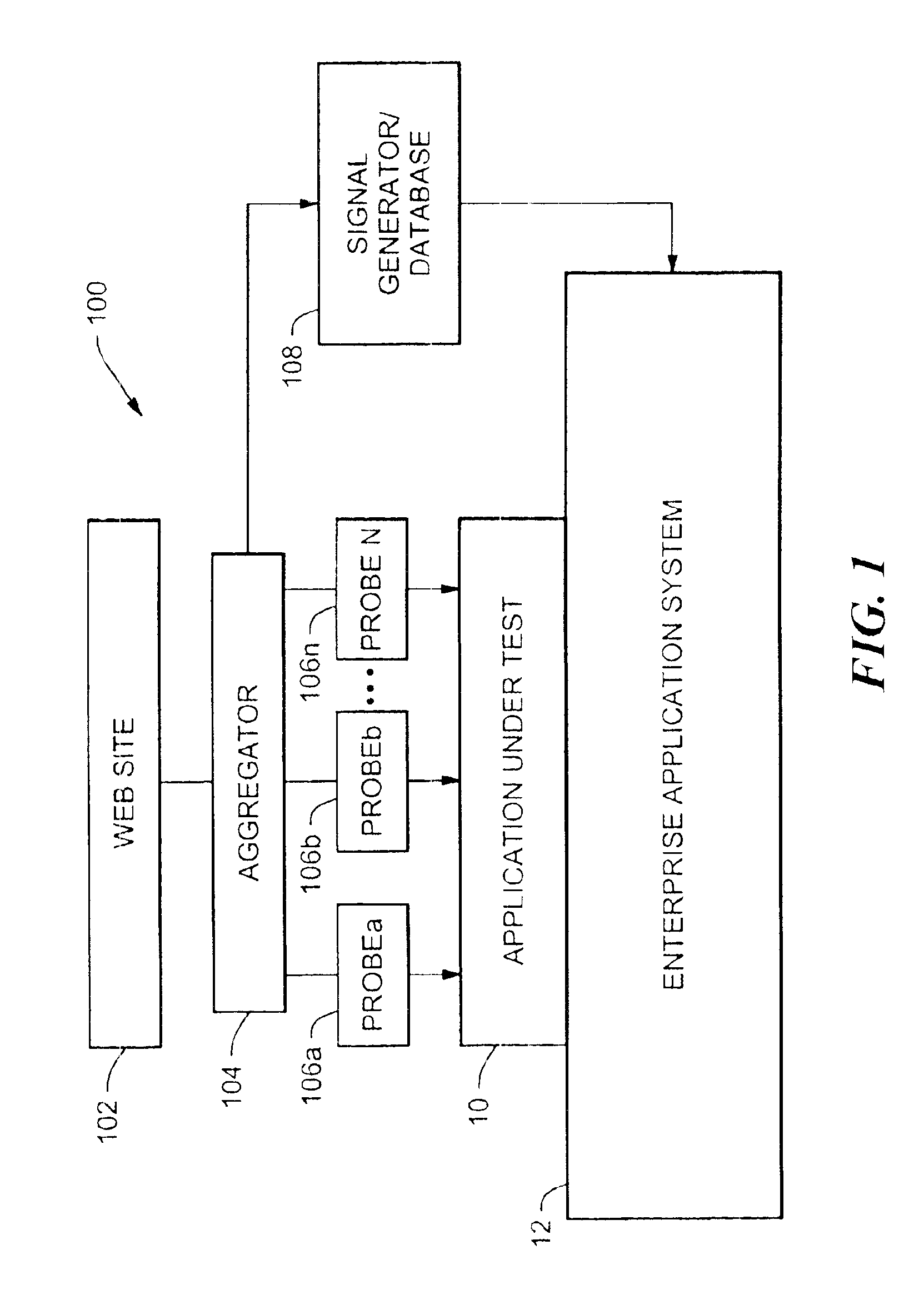
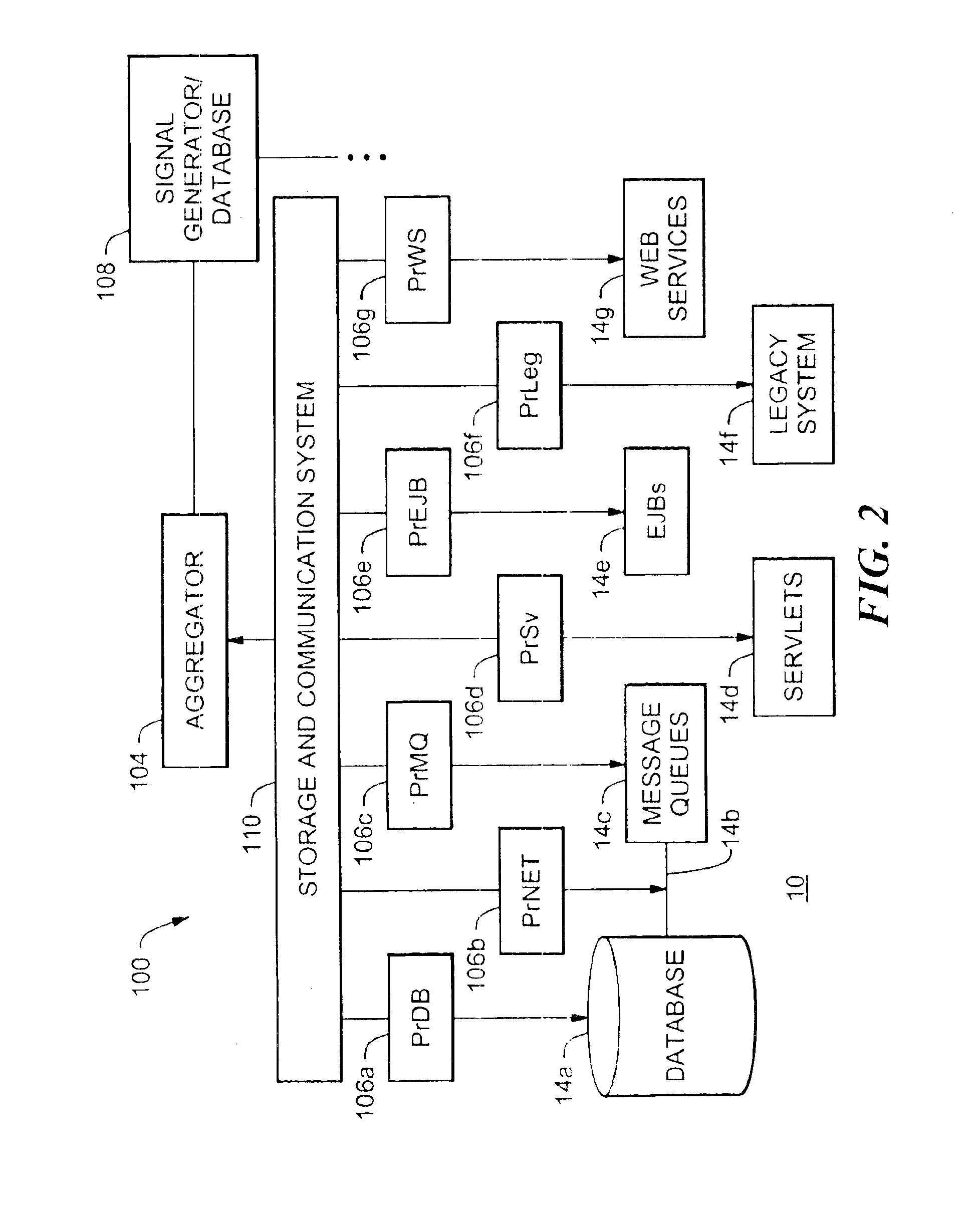
Enterprise test system having program flow recording and playback
InactiveUS6865692B2Software testing/debuggingSpecific program execution arrangementsTransaction dataEnterprise system
An enterprise test system includes a plurality of probes inserted at various locations in the enterprise system for recording data from system components during teach mode. During playback mode, the recorded data is used to exercise the system as probes collect actual data for comparison to expected data. In one embodiment, data from actual user transactions is recorded by the probes. The recorded data can be expanded to load test a component using recorded transaction data. In one embodiment, the recorded data can be used to load test a component under test without compiling test code.
Owner:ORACLE INT CORP
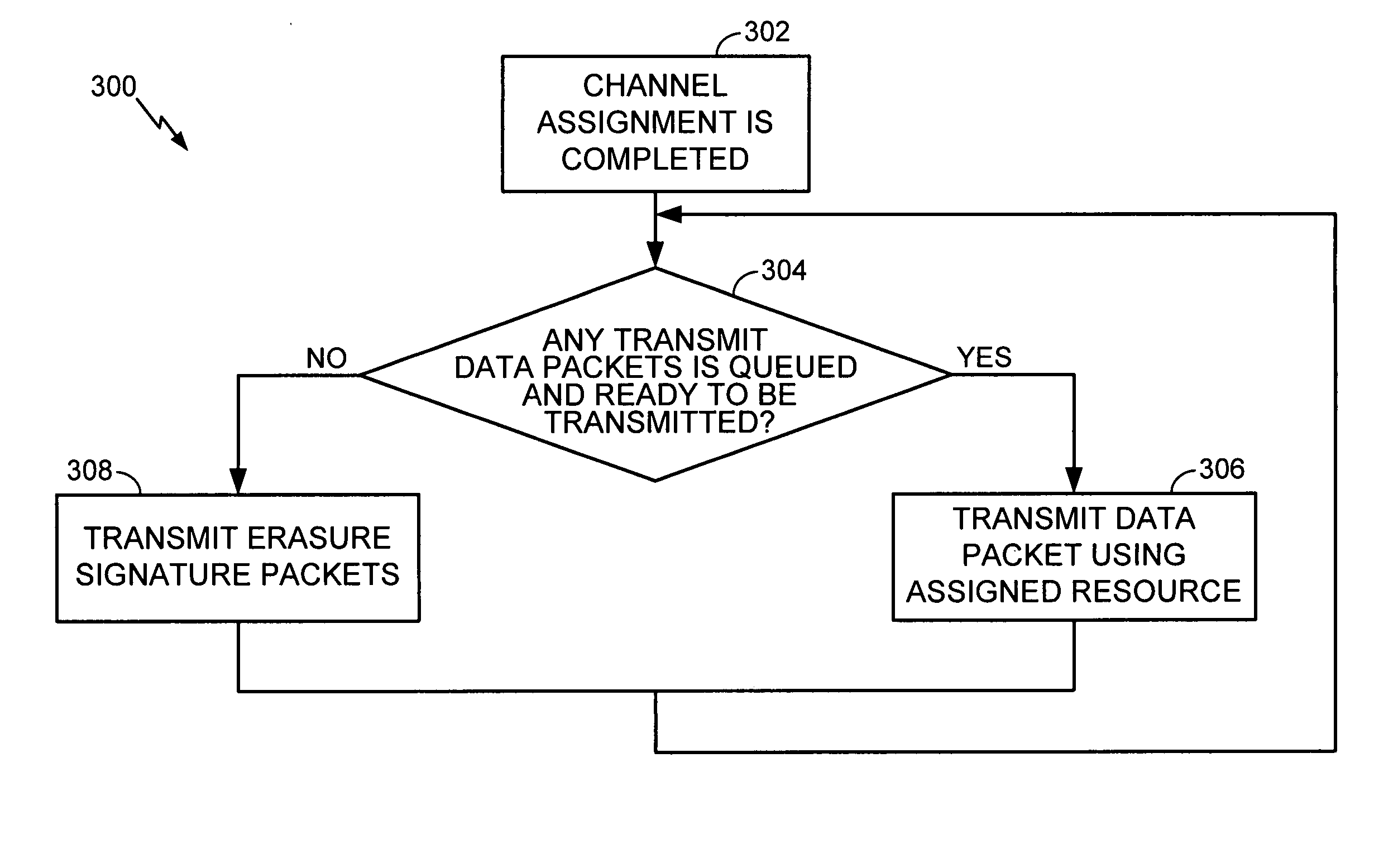
Method of providing a gap indication during a sticky assignment
ActiveUS20060164993A1Error preventionFrequency-division multiplex detailsData patternsReal-time computing
Owner:QUALCOMM INC
Data/presence insurance tools and techniques
Methods for insurance of online presence (202) and / or data (200) are described. An insurer (302) contracts with an insured entity (304) in an agreement (308) under which a premium (310) is paid for insurance coverage. The premium is calculated (306) using a pure premium method (400) or a loss ratio premium method (402), in a manner that depends on factors such as expected virus scan results (404), expected data recovery time (406), expected geographic spread (408), use of multiple recovery methods (410), and other information regarding the insured entity's business and the technical protection services (206) to be used. In some embodiments, the technical protection services are provided under the agreement by a third party technical services provider (300). Systems, signals, and configured media are also described.
Owner:INTELLECTUAL VENTURES II
Template filler, method, and computer program product
InactiveUS20070130505A1Improve time efficiencyReduce the possibility of errorNatural language data processingSpecial data processing applicationsComputer scienceDatabase
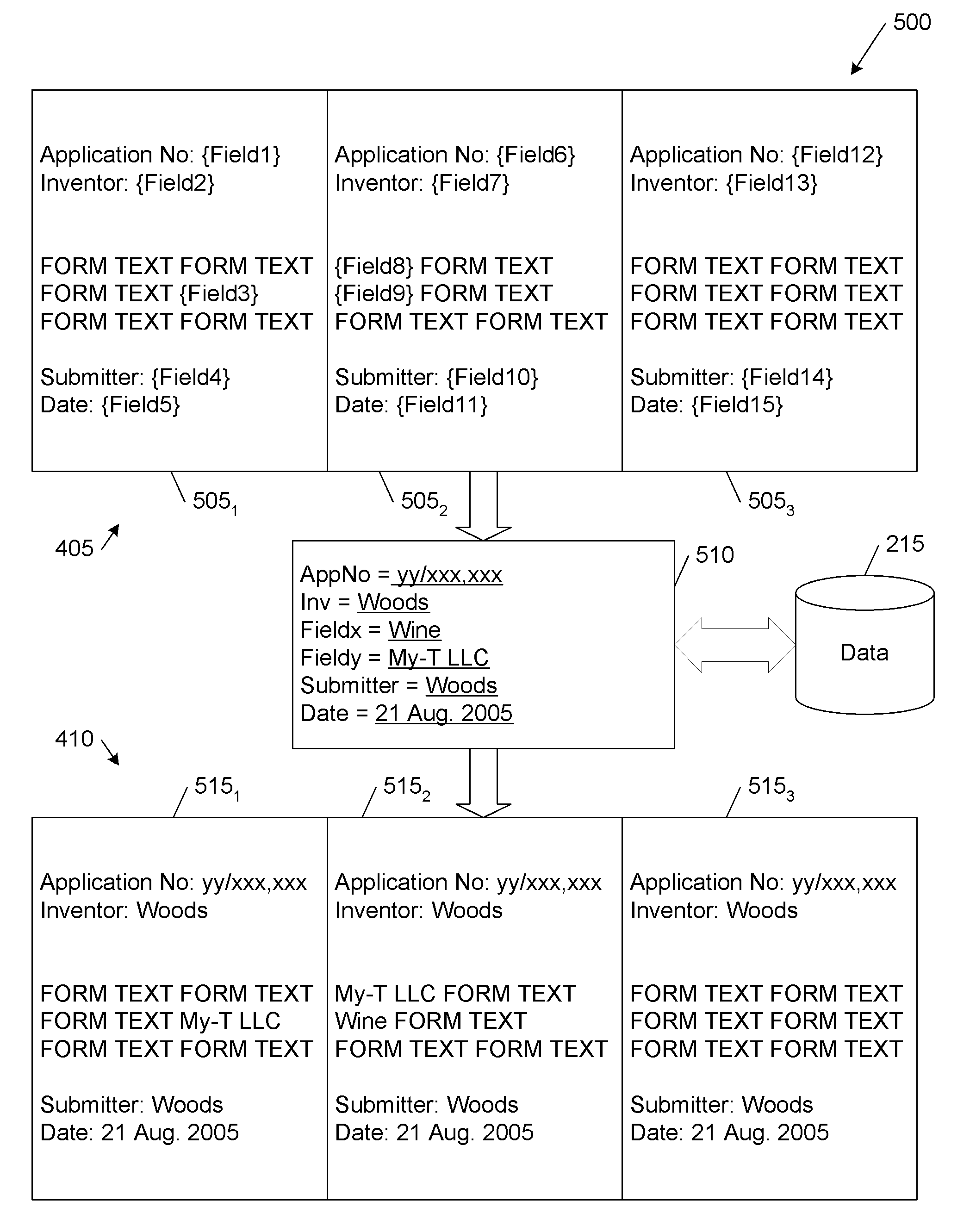
A system, method, computer program product and propagated signal for generating one or more forms in one operation using data identified in a dynamically generated user editable form that includes a list limited to the fillable fields of the form templates and prospective data to be substituted into those fields when the forms are generated from the selected form templates, particularly using forms in PDF that may be accessed using an API.
Owner:WOODS MICHAEL E
Method and system for onboard bit error rate (BER) estimation in a port bypass controller
InactiveUS7451362B2Error detection/prevention using signal quality detectorCorrect operation testingData streamEngineering
Certain aspects of the method may comprise receiving via a first port of the port bypass controller, a data stream comprising at least one known bit pattern. Upon locking onto at least a portion of the known bit pattern in the received data stream, a bit error rate may be generated based on a bit-by-bit comparison of at least a portion of the data stream received after locking occurs. At least a portion of the data stream may be compared with a corresponding portion of expected data. The bit error rate may be calculated based on results from comparing at least a portion of the data stream with a corresponding portion of the expected data. The known bit pattern may be internally generated within the port bypass controller or it may be externally generated by a host system.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Application-Aware Multiple Wireless Radio-Access Technology Coexistence Solution and Time Sharing Between Multiple Radio-Access Technologies for In-Device Coexistence
ActiveUS20160174280A1Improve throughputImprove performanceConnection managementWireless commuication servicesTelecommunications linkTime-sharing
A user equipment (UE) device may be configured to effectively manage coexistence of multiple radio access technologies (RATs) on the device. Respective controllers responsible for at least partially managing wireless communications according to corresponding respective RATs may communicate to each other expected data transfer patterns that take place over their respective communications links, including application-specific data transfer patterns and data-transfer-mechanism-specific data transfer patterns. The RAT controllers may manage their respective data transfers according to the expected data-transfer pattern information associated with the other RATs received from each in order to prevent data transmission by the device over one RAT link interfering with data transmission of the device over another RAT link. The expected data pattern information may be sent in messaging of a specific type with indexes determined based at least on a status of the data transfer mechanism and a connectivity status of the UE device.
Owner:APPLE INC
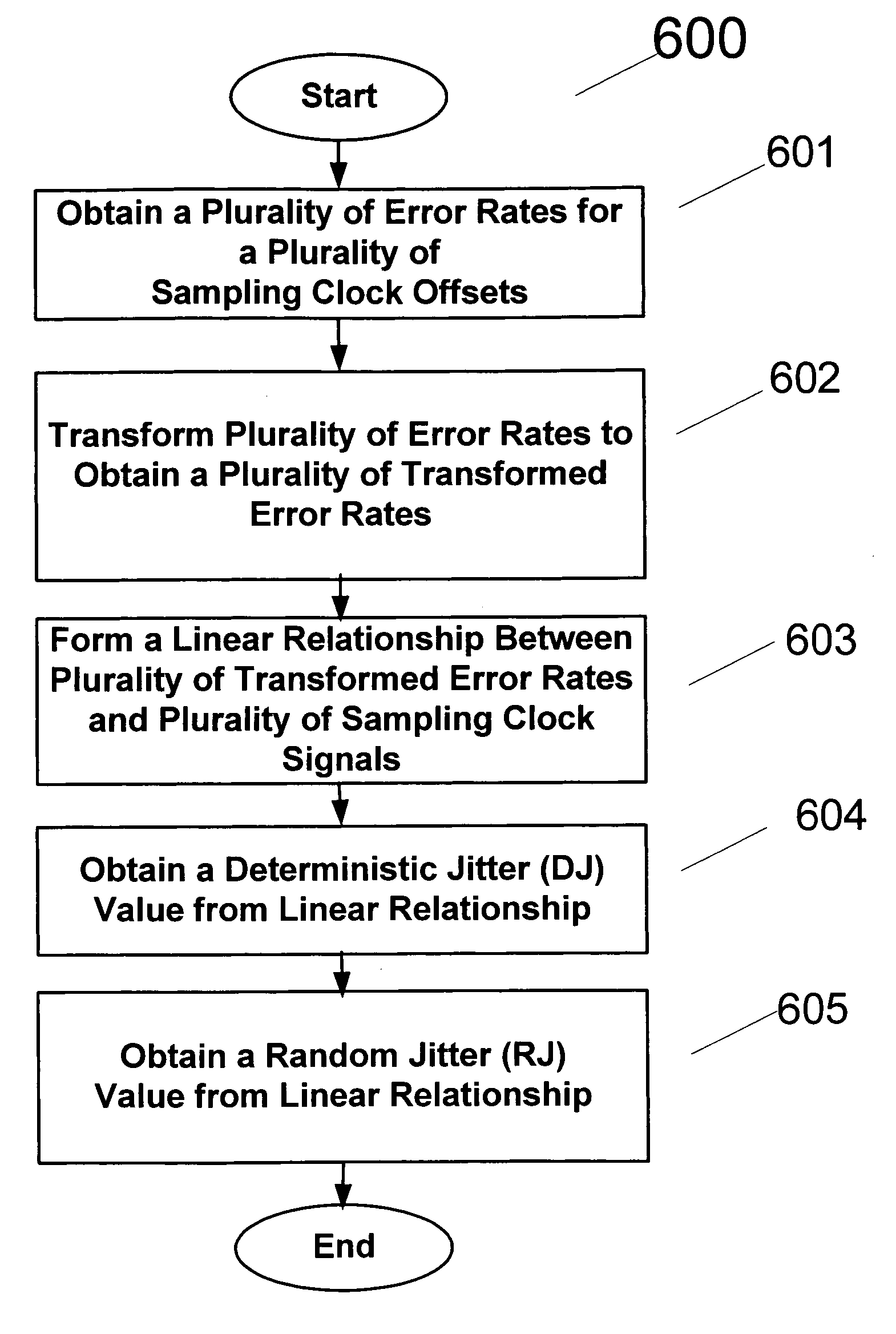
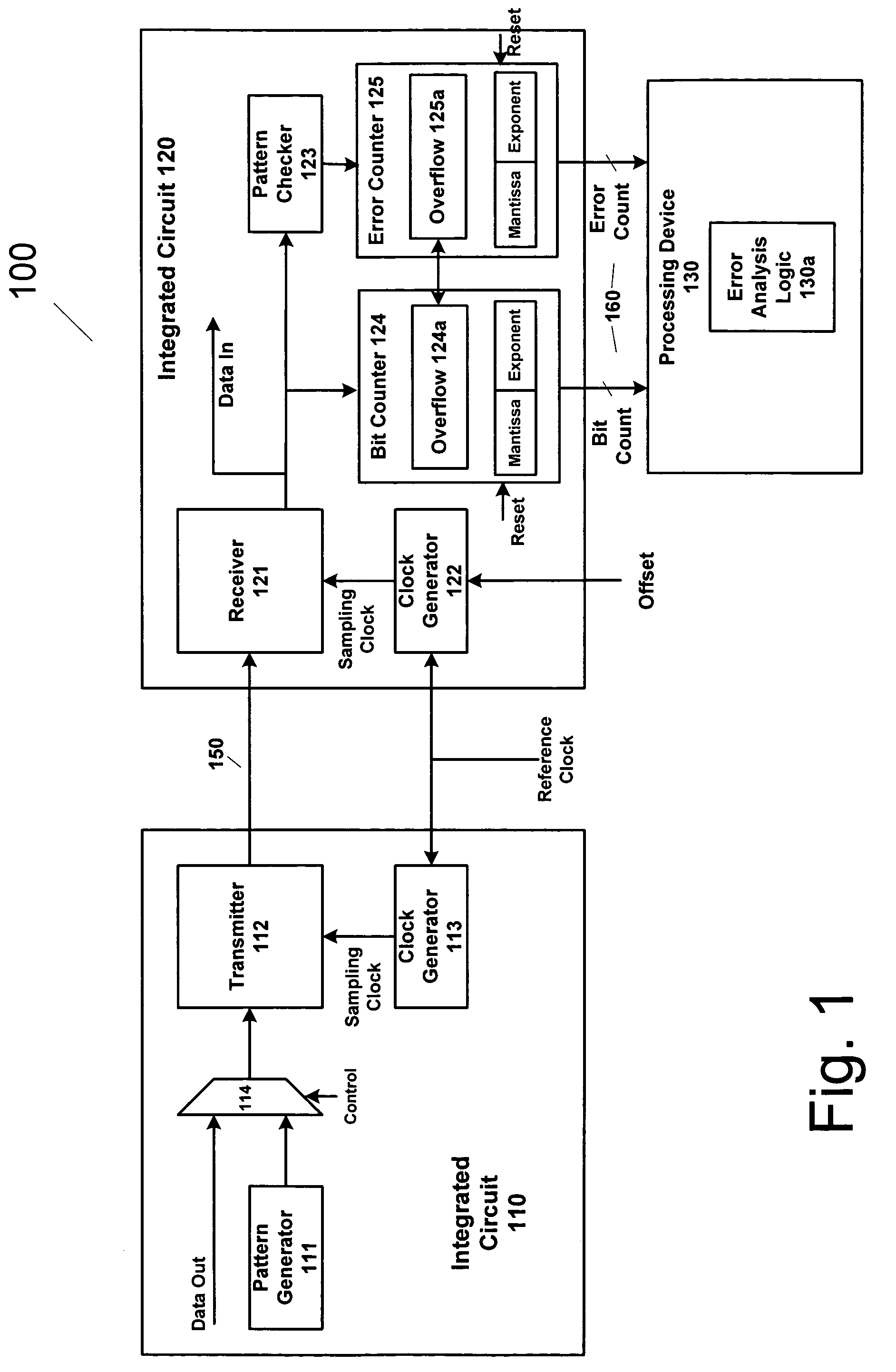
Method and apparatus for estimating random jitter (RJ) and deterministic jitter (DJ) from bit error rate (BER)
An apparatus and method provides prediction of BER for an interface between ICs, such as a processor and a memory device, without using special test equipment. A known data pattern or PRBS is transmitted to a receiver, which compares the received data values with expected data values to determine if a bit error has occurred in an embodiment of the present invention. A center of data eye and the edge of the data eye are sampled (over sampled) in order to determine if a bit error has occurred in an alternate embodiment of the present invention. A first counter is used to count the total number of bits sampled and the second counter is used to count the number of errors that occurred in the total number of bits sampled.
Owner:RAMBUS INC
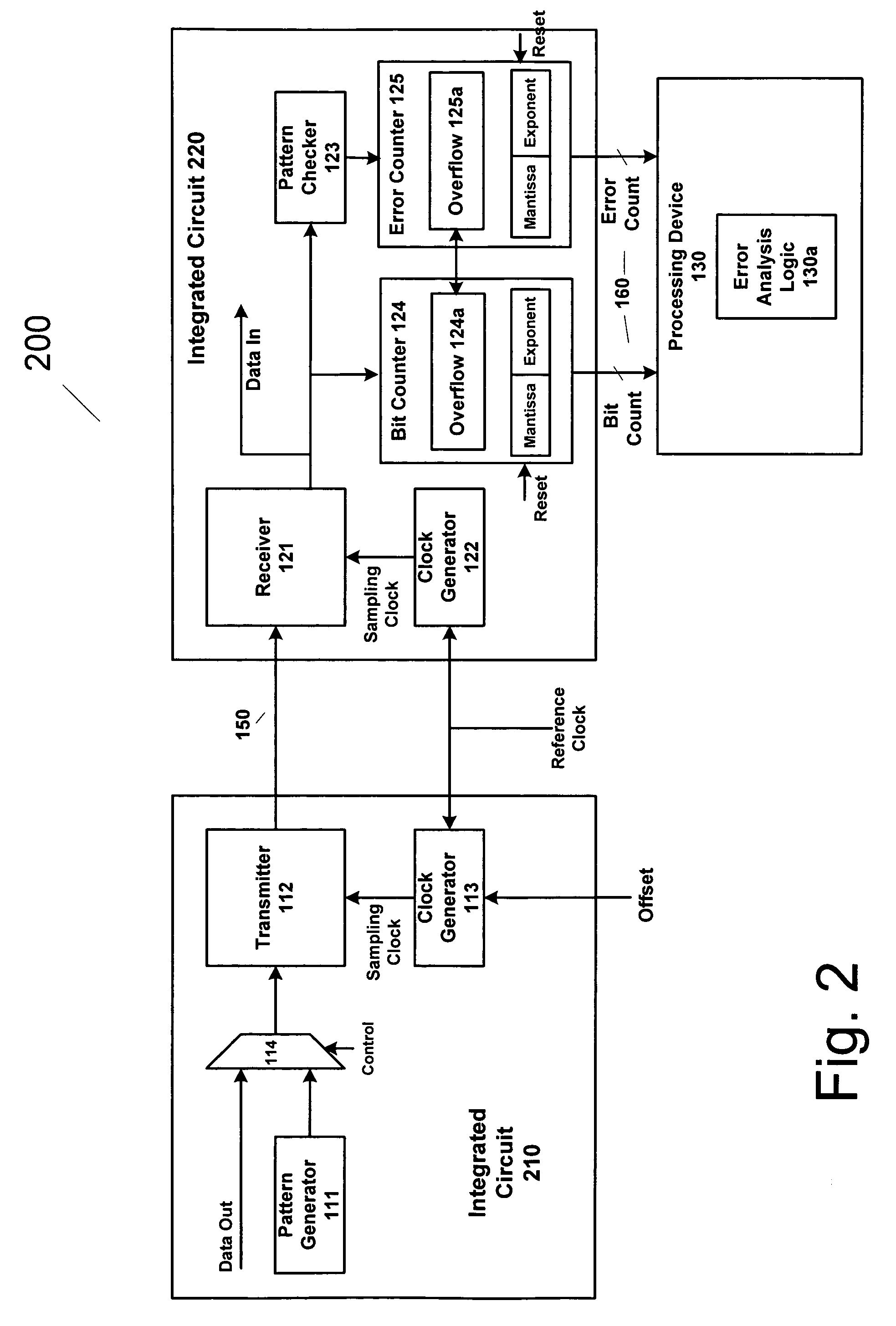
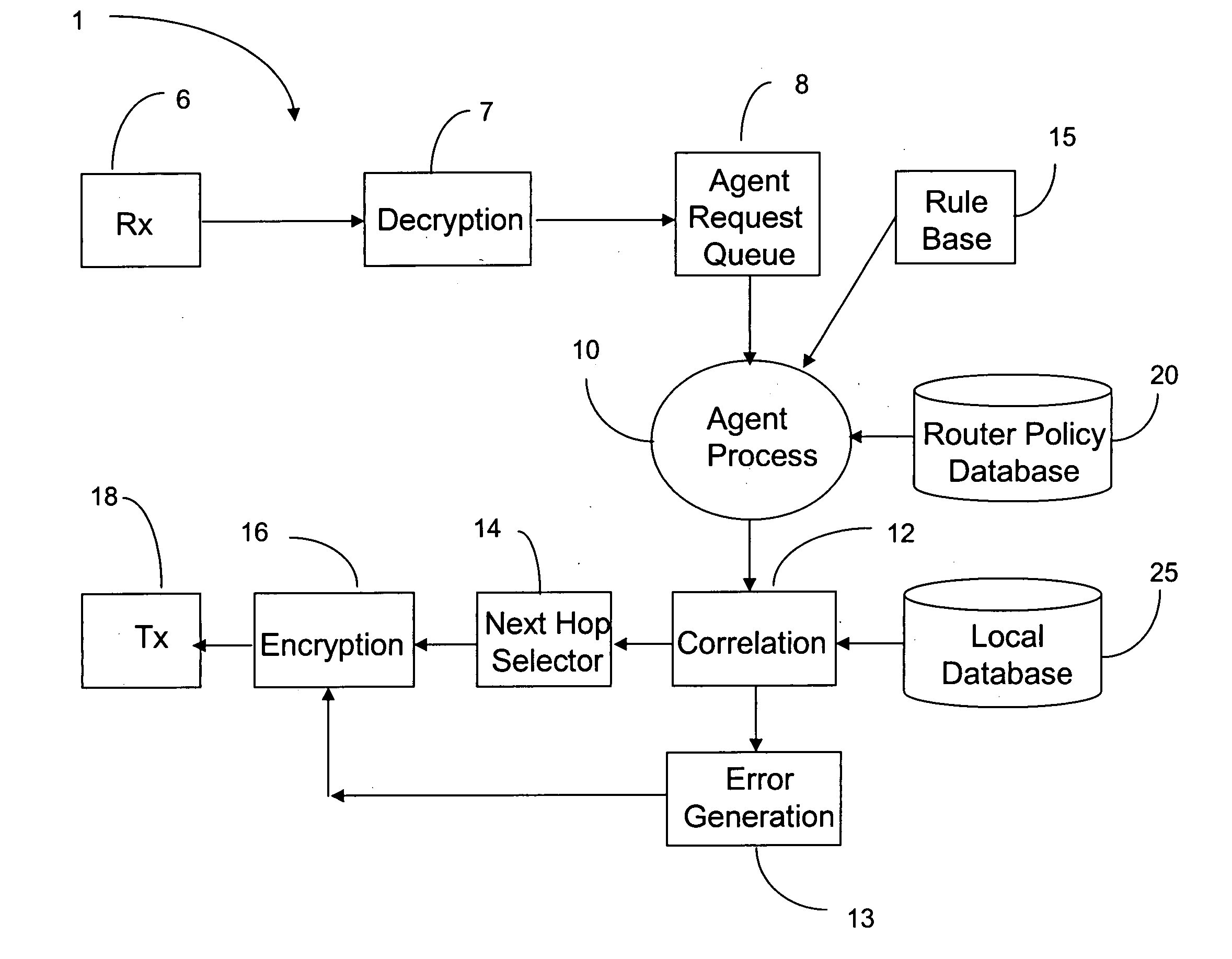
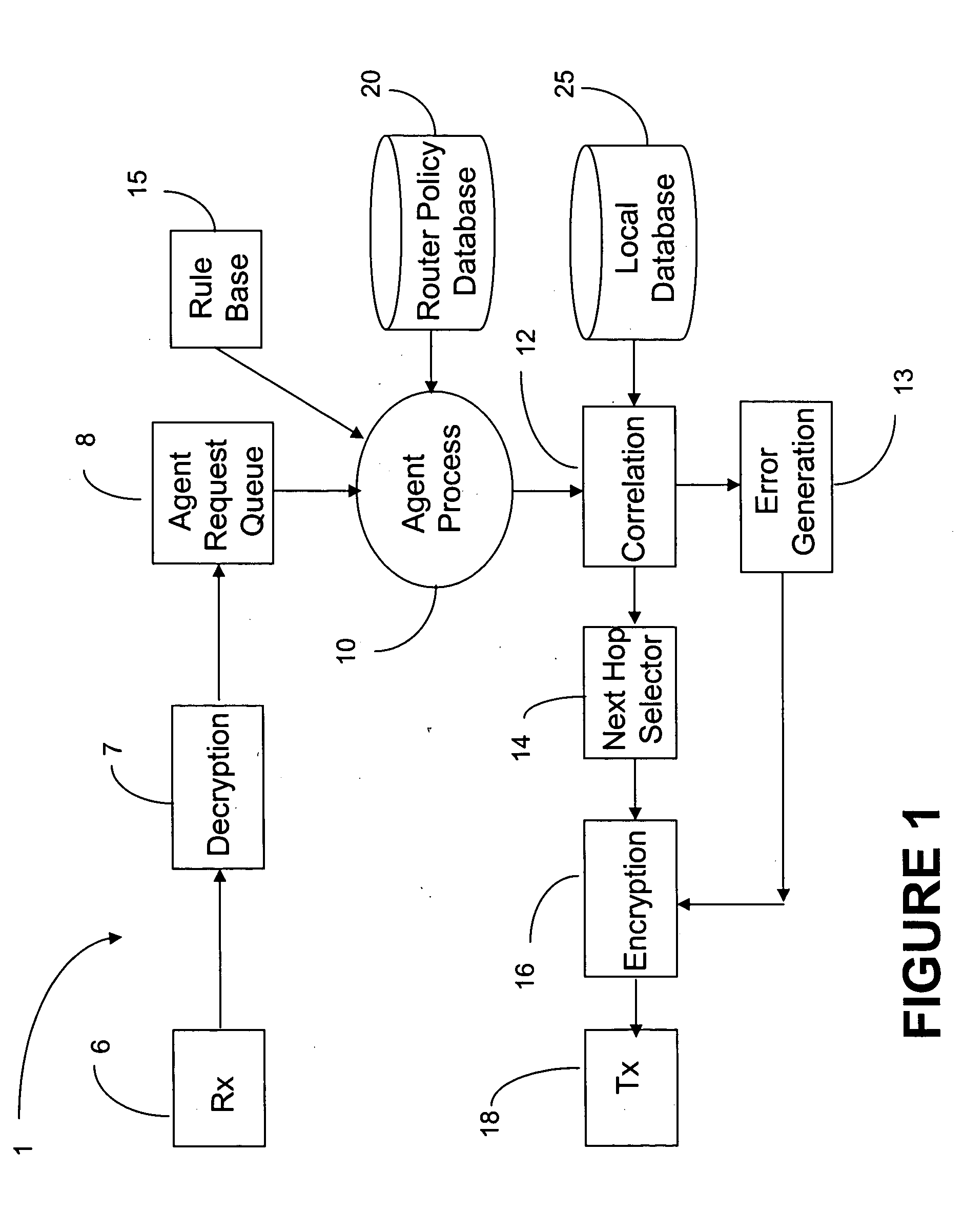
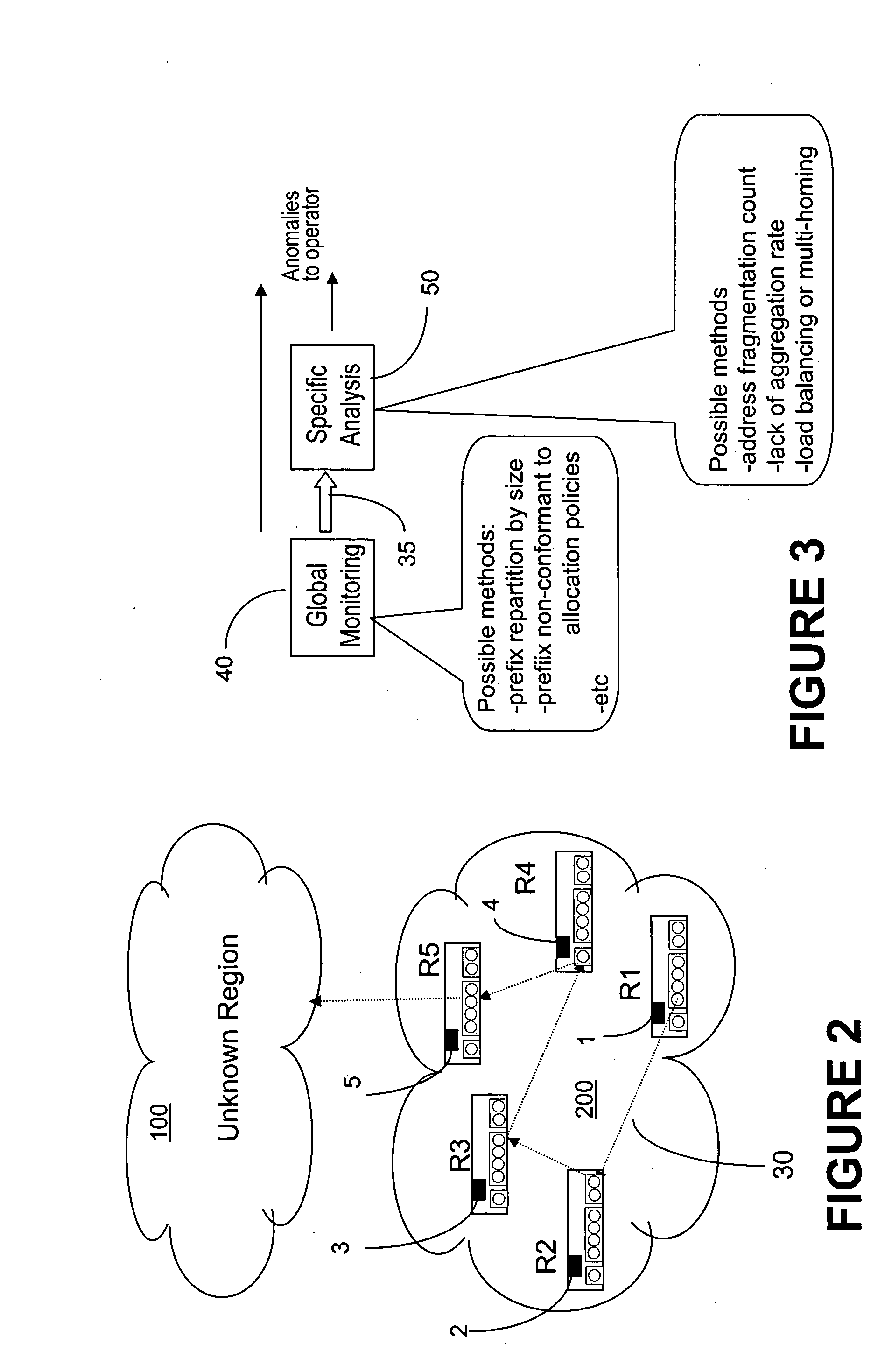
Agent based router monitoring, diagnostic and maintenance
ActiveUS20050240835A1Reduce overheadReduce traffic overheadError detection/correctionData switching networksDiagnostic dataDatabase analysis
A distributed, multistage agent for monitoring, diagnosis and maintenance of network devices comprises an input / output interface for receiving input monitoring and diagnostic data relevant to operation of a first neighboring agent and transmitting output monitoring and diagnostic data relevant to operation of the host network device to a second neighboring agent. An agent process analyzes the input data and generates processed data characterizing operation of the host network device, using a local database which stores expected performance data on operation of said network device. The processed data is correlated with the expected data any error is signaled to the network operator. The agents may be designed as a multiple stage process, the stages being triggered by the data output by an earlier stage only when needed.
Owner:RPX CORP
Receiving apparatus and method for digital multi-carrier transmission
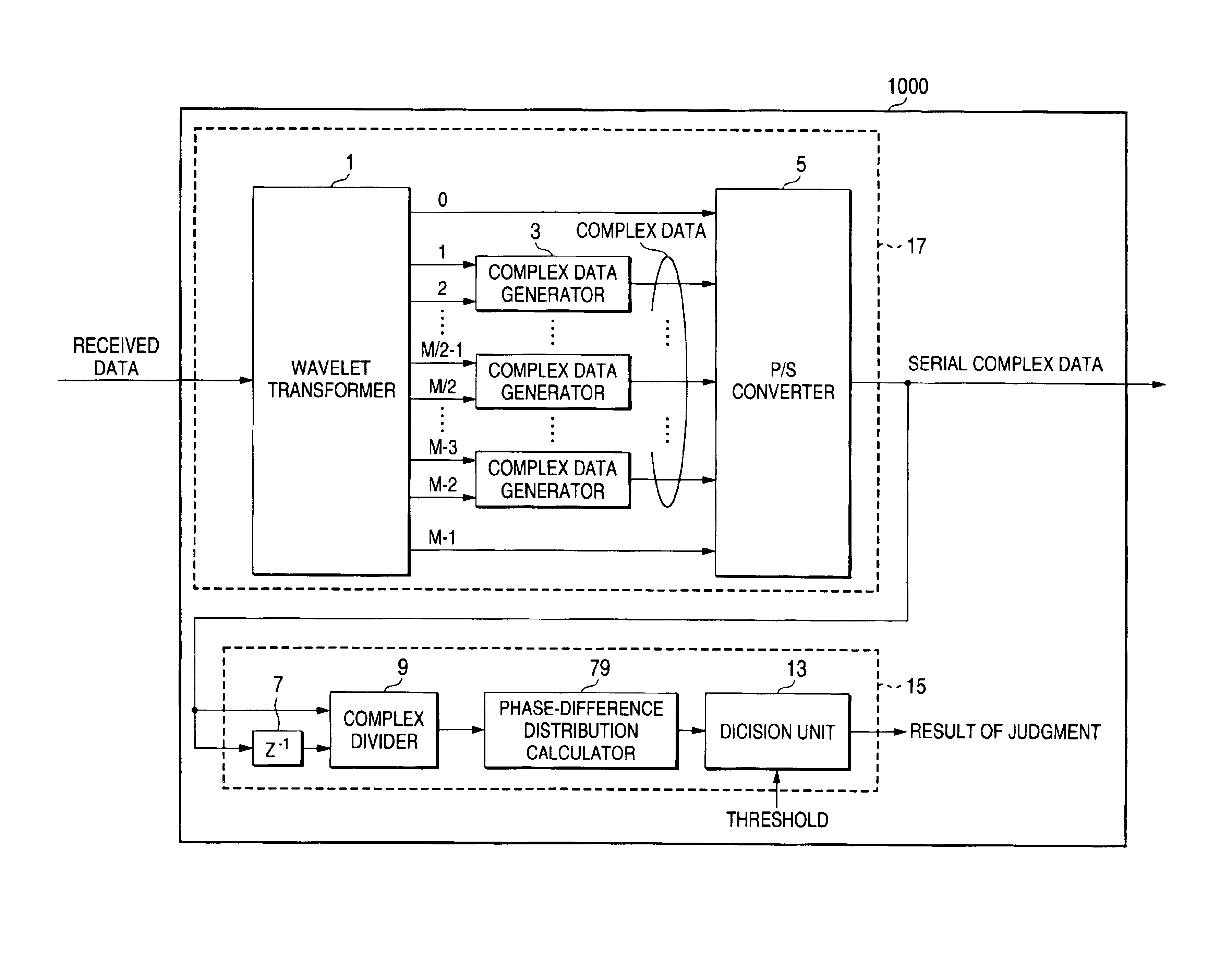
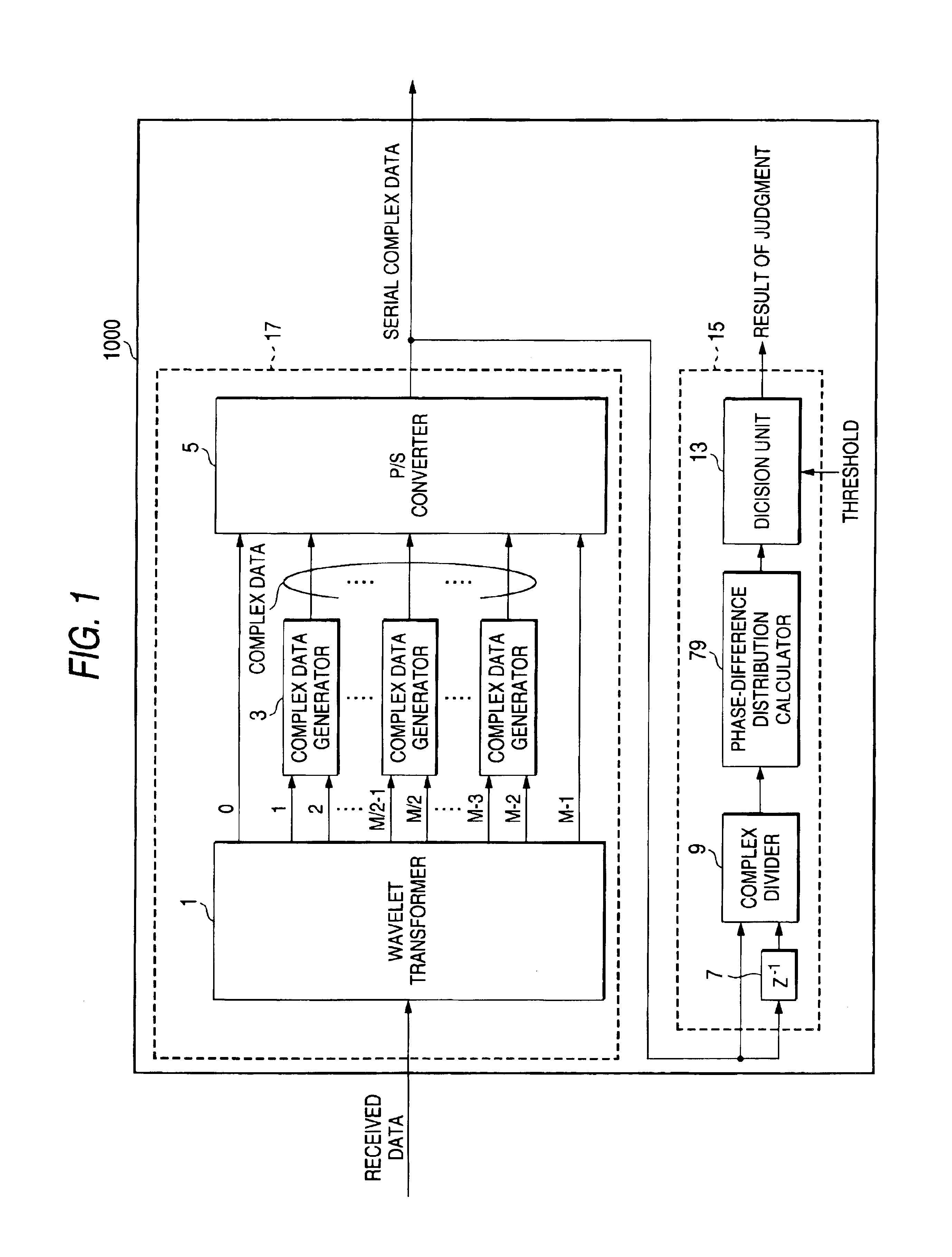
InactiveUS6944232B2Picture reproducers using cathode ray tubesPicture reproducers with optical-mechanical scanningOrthogonal coordinatesAlgorithm
A receiving apparatus and method for performing carrier detection in a frequency domain for a digital wavelet multi-carrier transmission. A wavelet transform of received data is performed to output complex data and then the complex data is delayed for one sampling period. Subsequently, the delayed complex data and delayed complex data are divided. A number of the divided complex data present within each of plural quadrants on orthogonal coordinates is calculated and a maximum number of data present within one of the quadrants is selected and compared with a threshold in order to decide whether the received data is intended data.
Owner:PANASONIC CORP
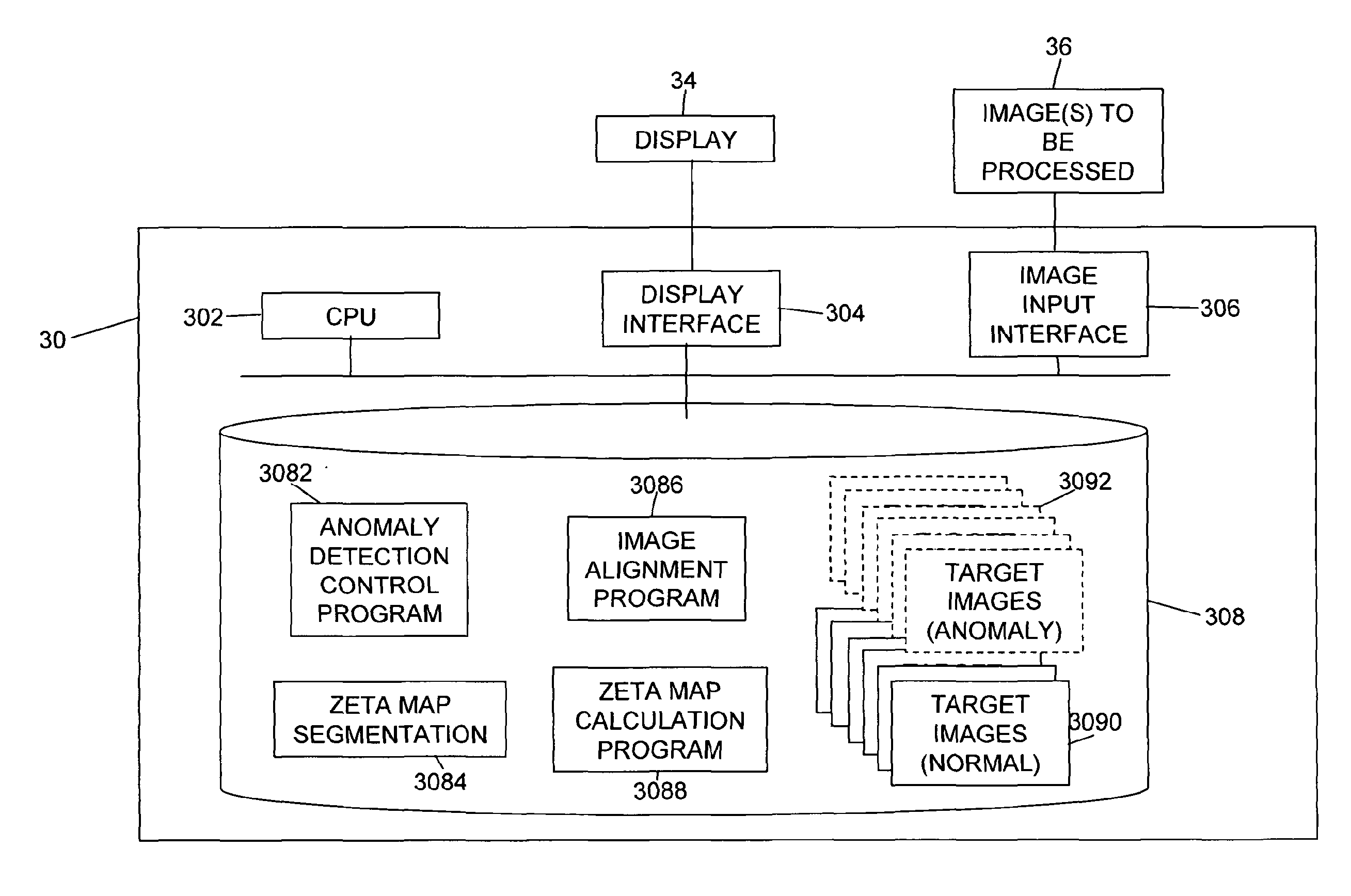
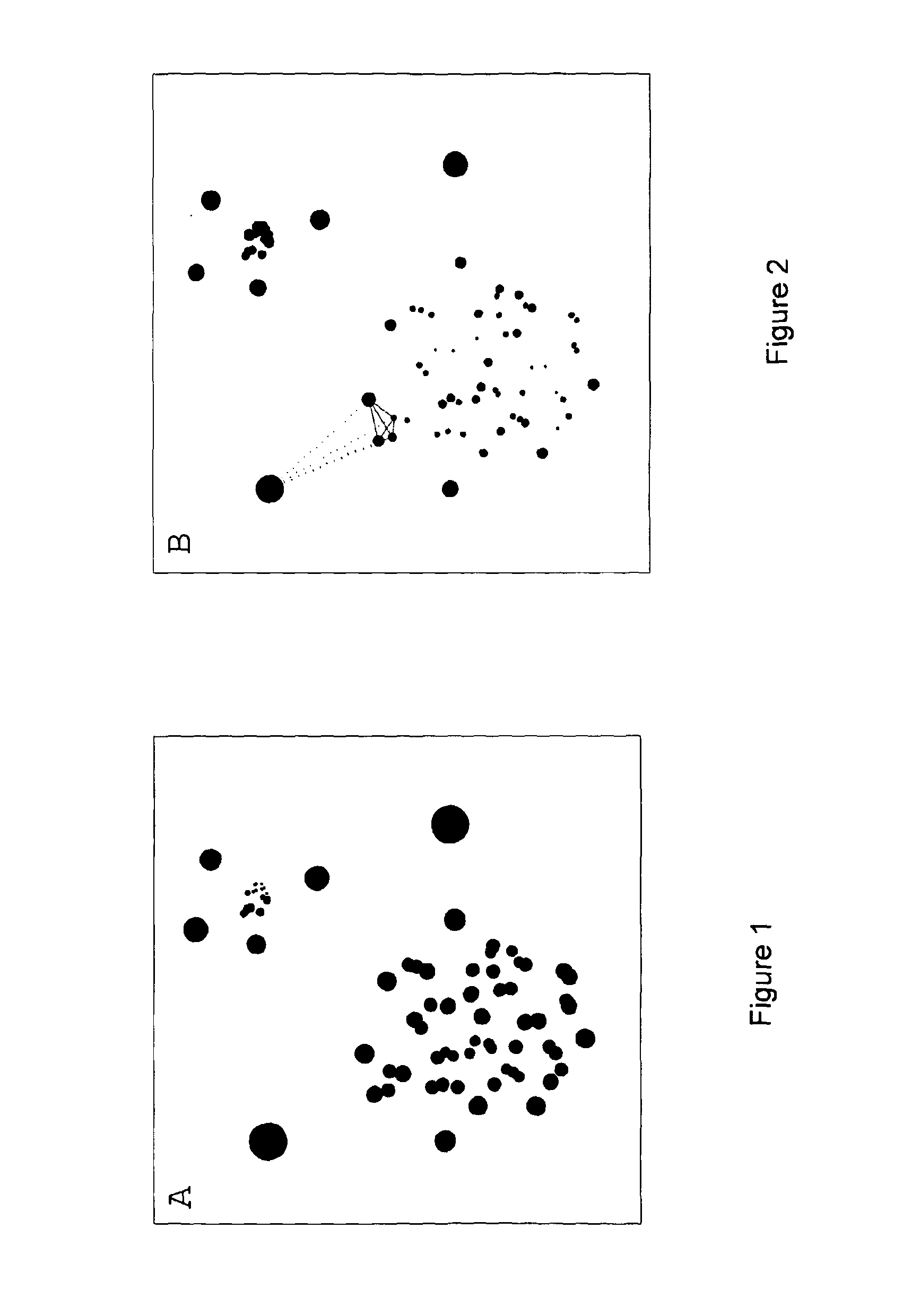
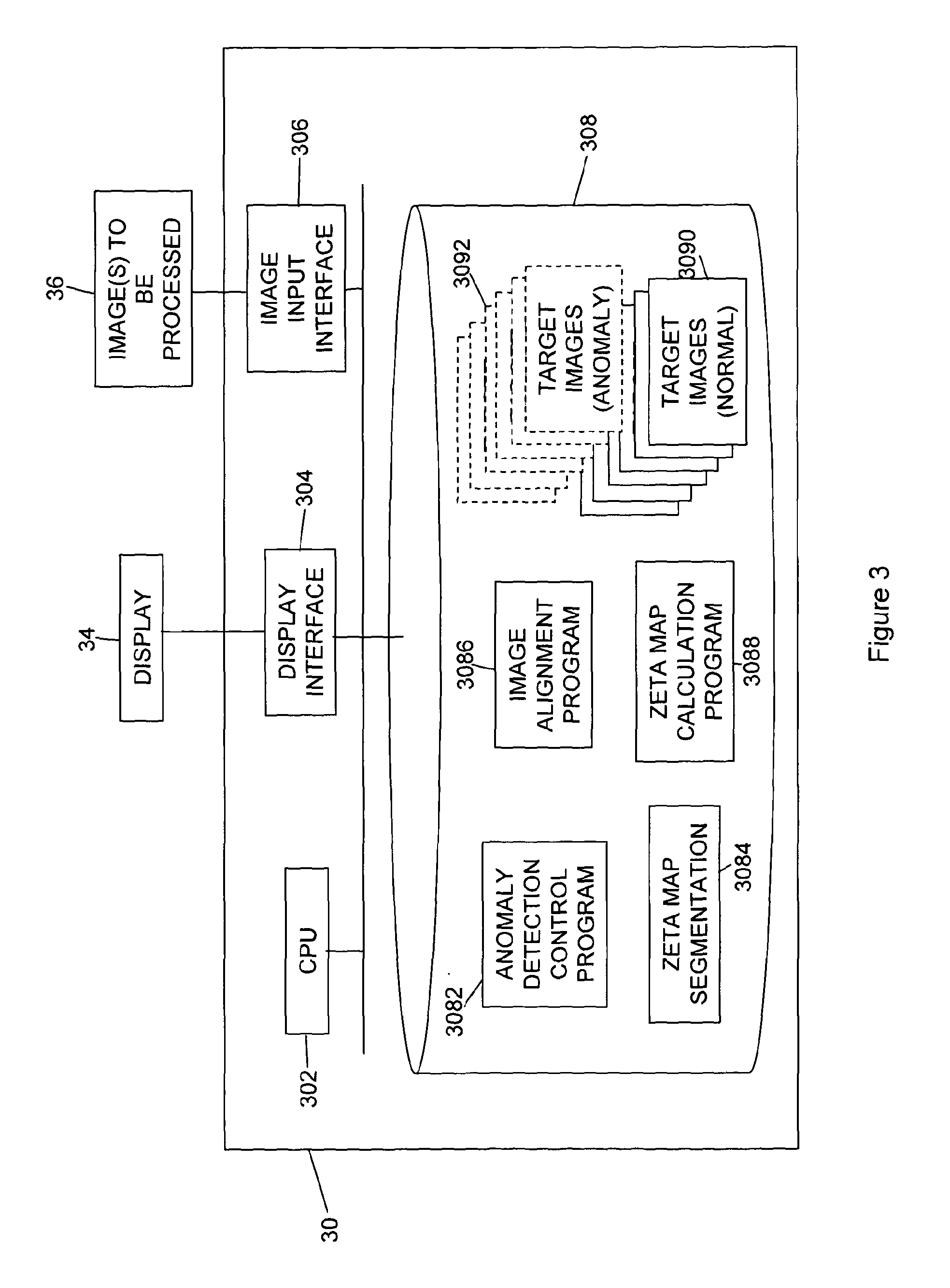
Method and system for anomaly detection in data sets
ActiveUS20130304710A1Easy to optimizeParameter is also alteredImage enhancementImage analysisData setAlgorithm
A method and apparatus for detecting and segmenting anomalous data in an input data set such as an image is described, which makes use of a normalised distance measure referred to as a zeta distance score. A test data point from an input test data set is compared with its corresponding nearest neighbouring standard data points in standard data sets representing variation in normal or expected data values, and the average distance from the test data point to the standard data points is found. An additional average distance measure representing the average distance between the different nearest neighbouring corresponding standard data points is also found, and a normalised distance measure obtained by finding the difference between the average distance from the test data point to the standard points and the average distance between the nearest neighbouring standard data points themselves. Where the input test data set is an image then a zeta distance score map can be found. By then thresholding the zeta distance scores obtained for the input data set using an appropriate threshold, anomalous data in the data set with a high zeta distance score can be identified, and segmented.
Owner:UCL BUSINESS PLC
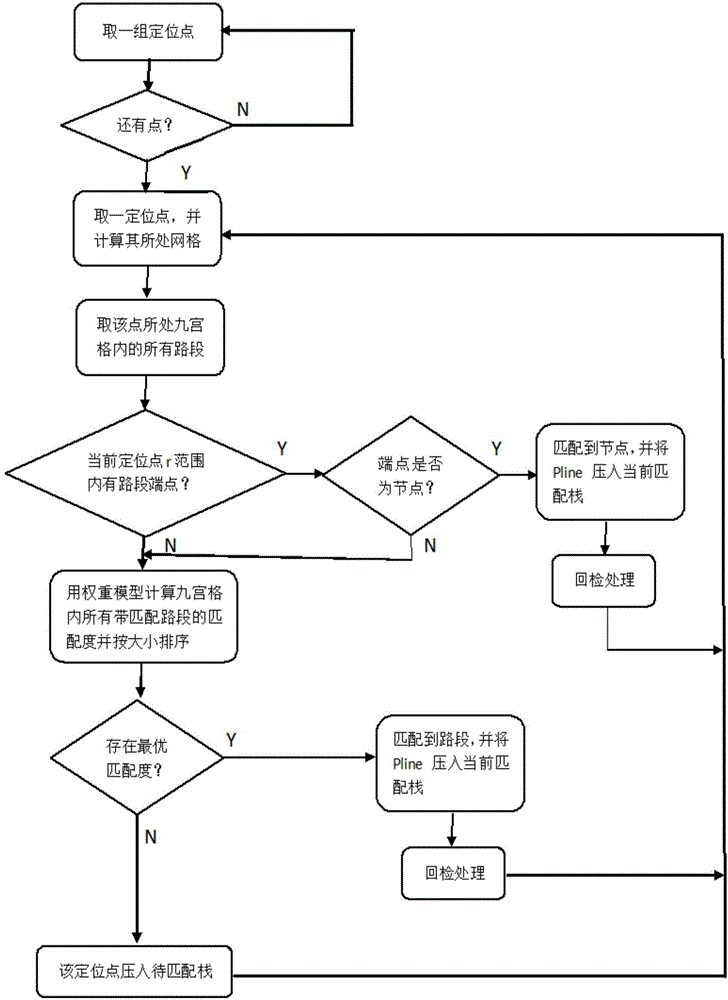
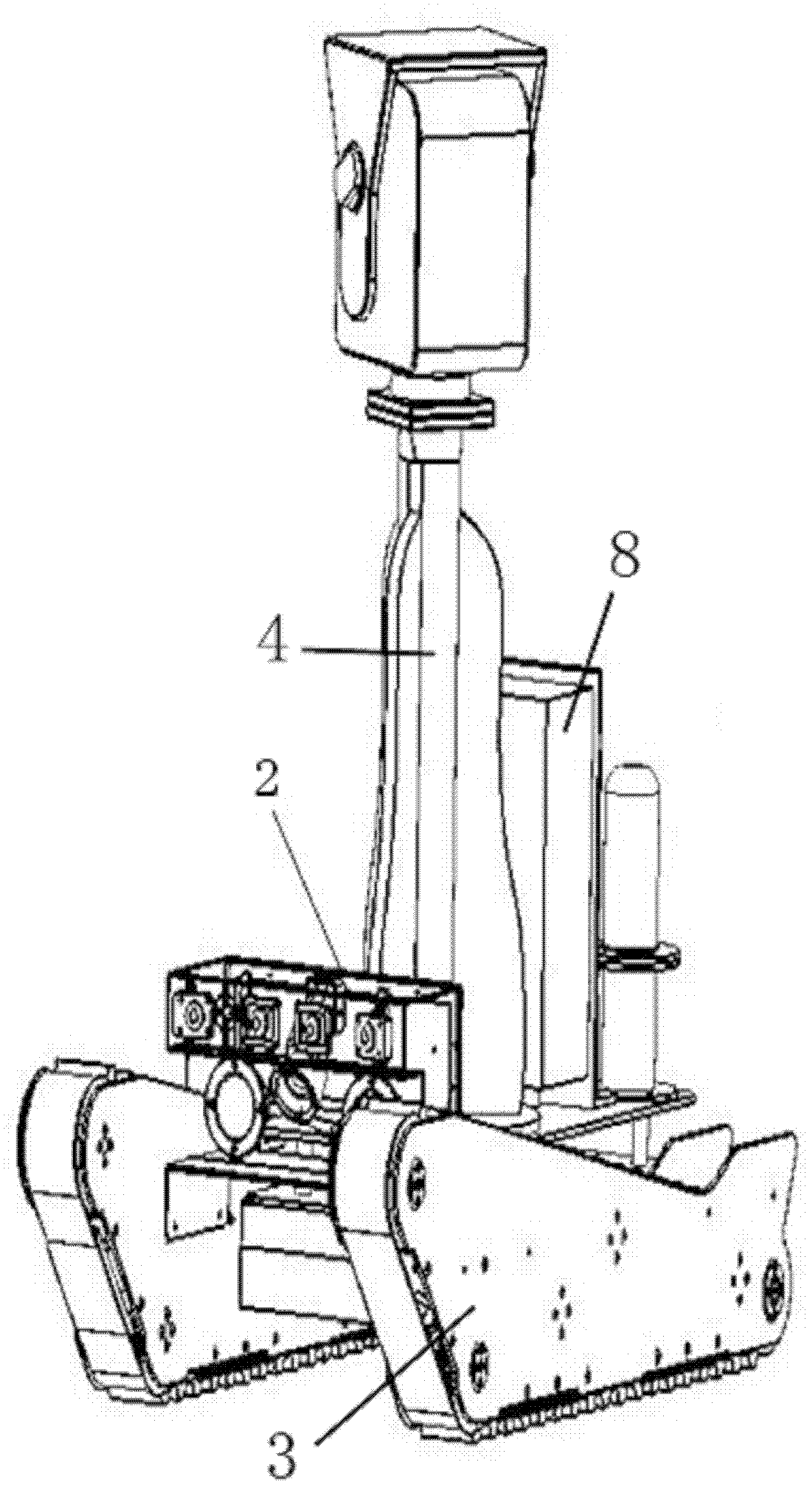
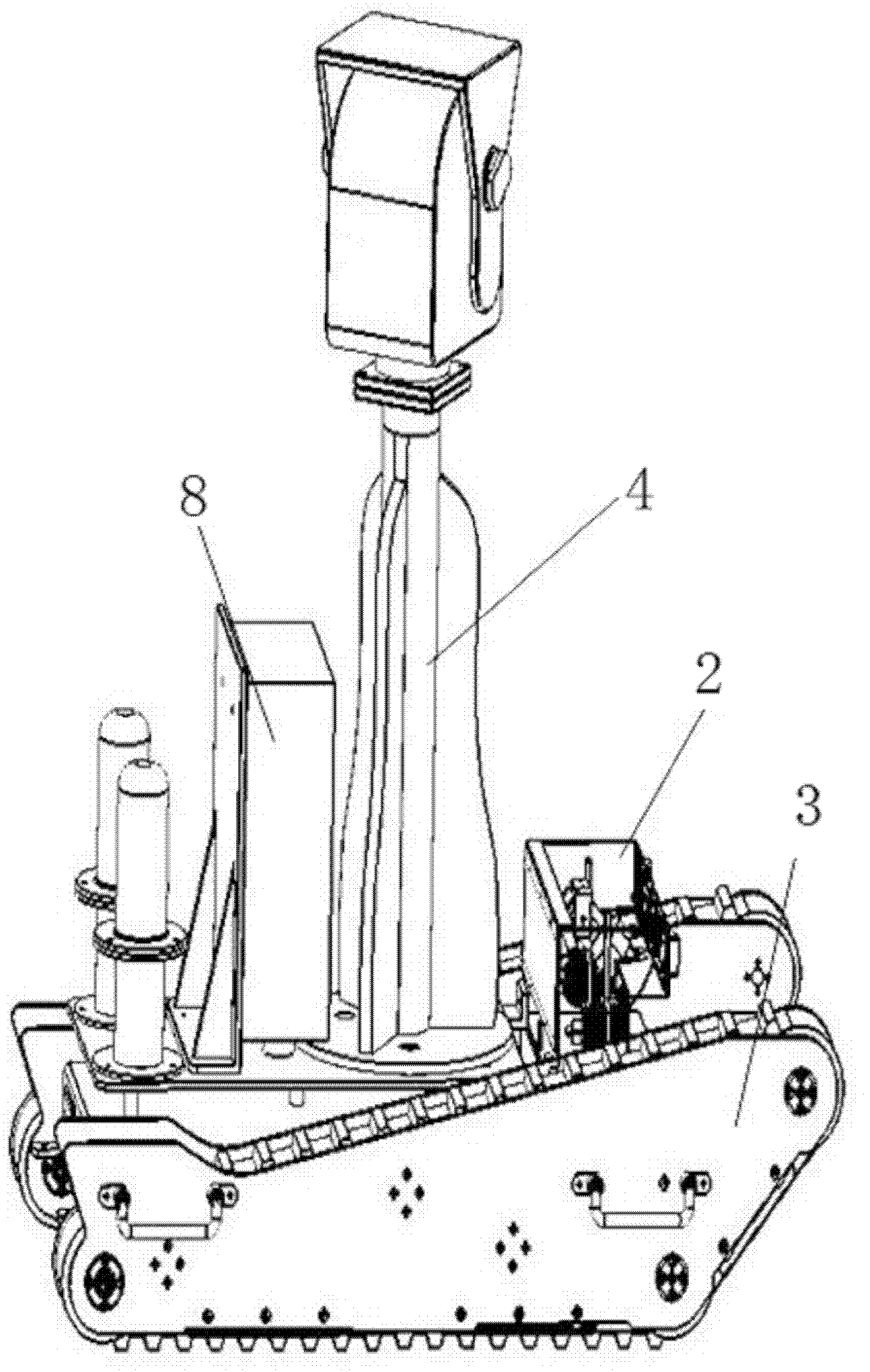
Road matching method based on fusion of probe vehicle movement track and electronic map
InactiveCN104634352AGood precisionReduce complexityInstruments for road network navigationDependabilityMatching methods
The invention relates to a road matching method based on the fusion of a probe vehicle movement track and an electronic map. The method is characterized in that an urban road network is divided by adopting a mesh division technology, so that the road section search complexity can be greatly reduced; a map matching method fusing a three-section matching concept of reference historical data and prospective data and an improved weight model concept is adopted for overcoming the weaknesses by acquiring strong points, the matching degree calculated by adopting the weight model is adopted as the evidence, and the three-section matching concept is used for making the decision, so that the reliability of the decision evidence and the reasonability of a result decision can be improved, and the relatively high matching precision can be achieved by virtue of the minimum complexity.
Owner:JILIN UNIV
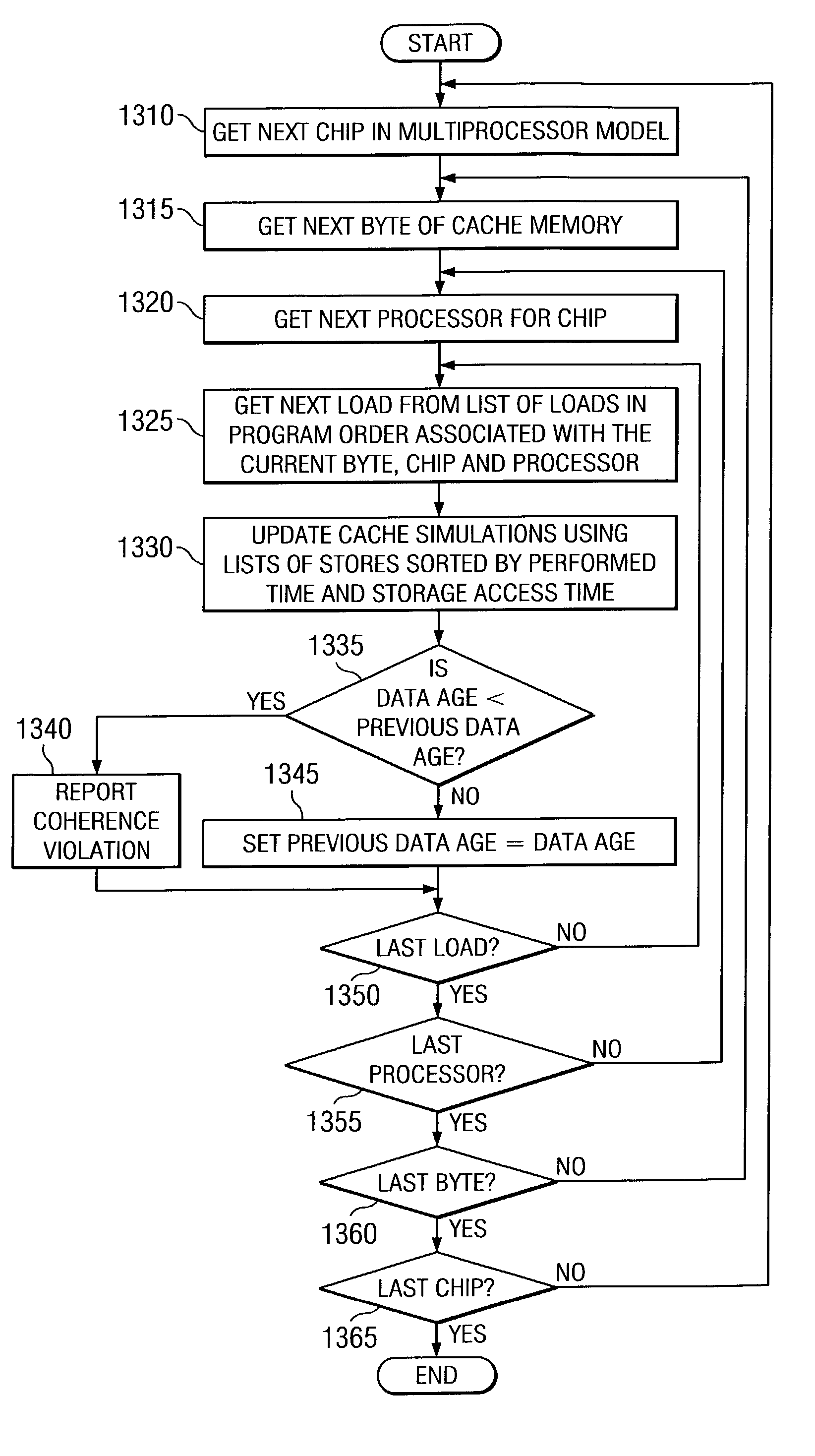
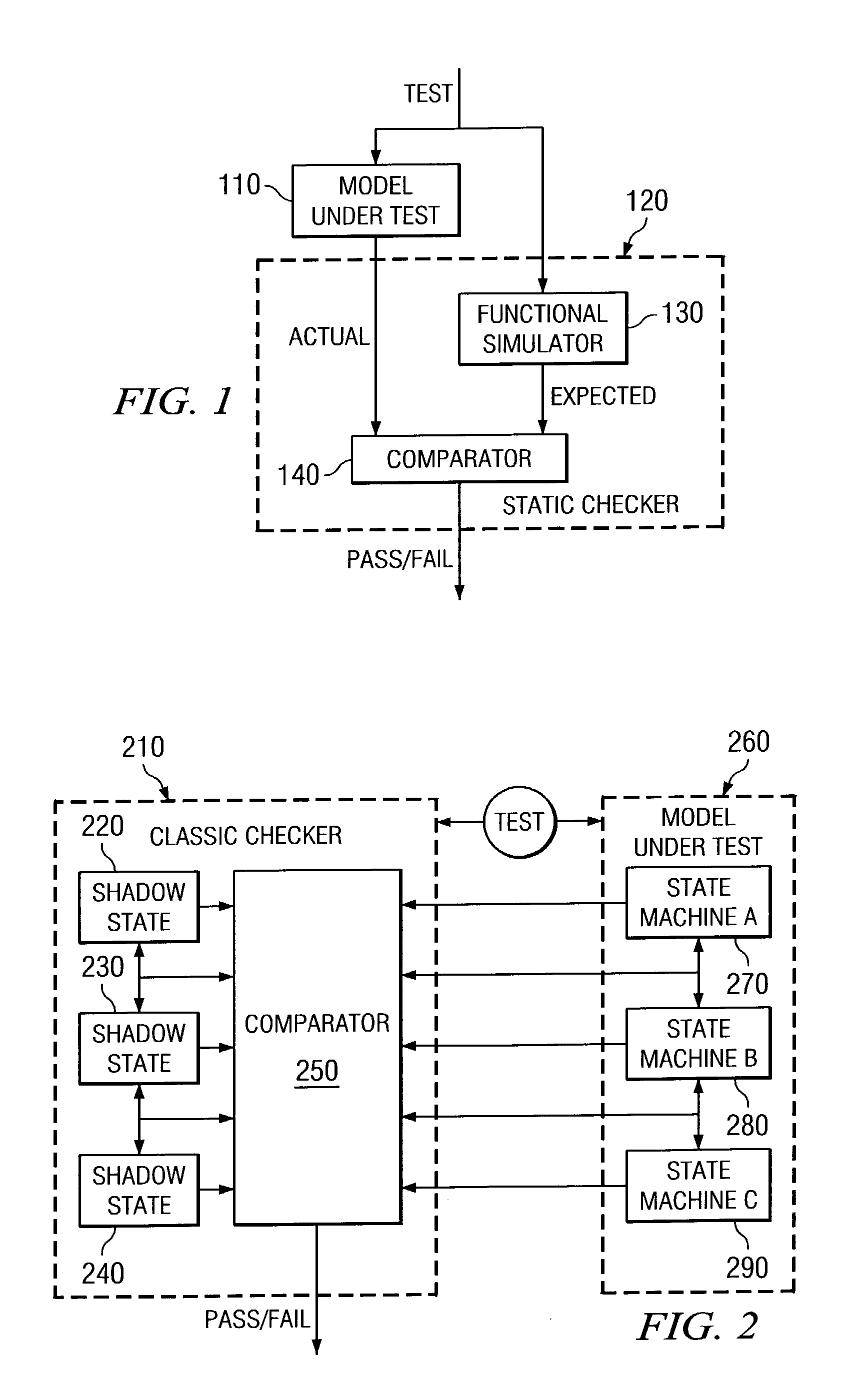
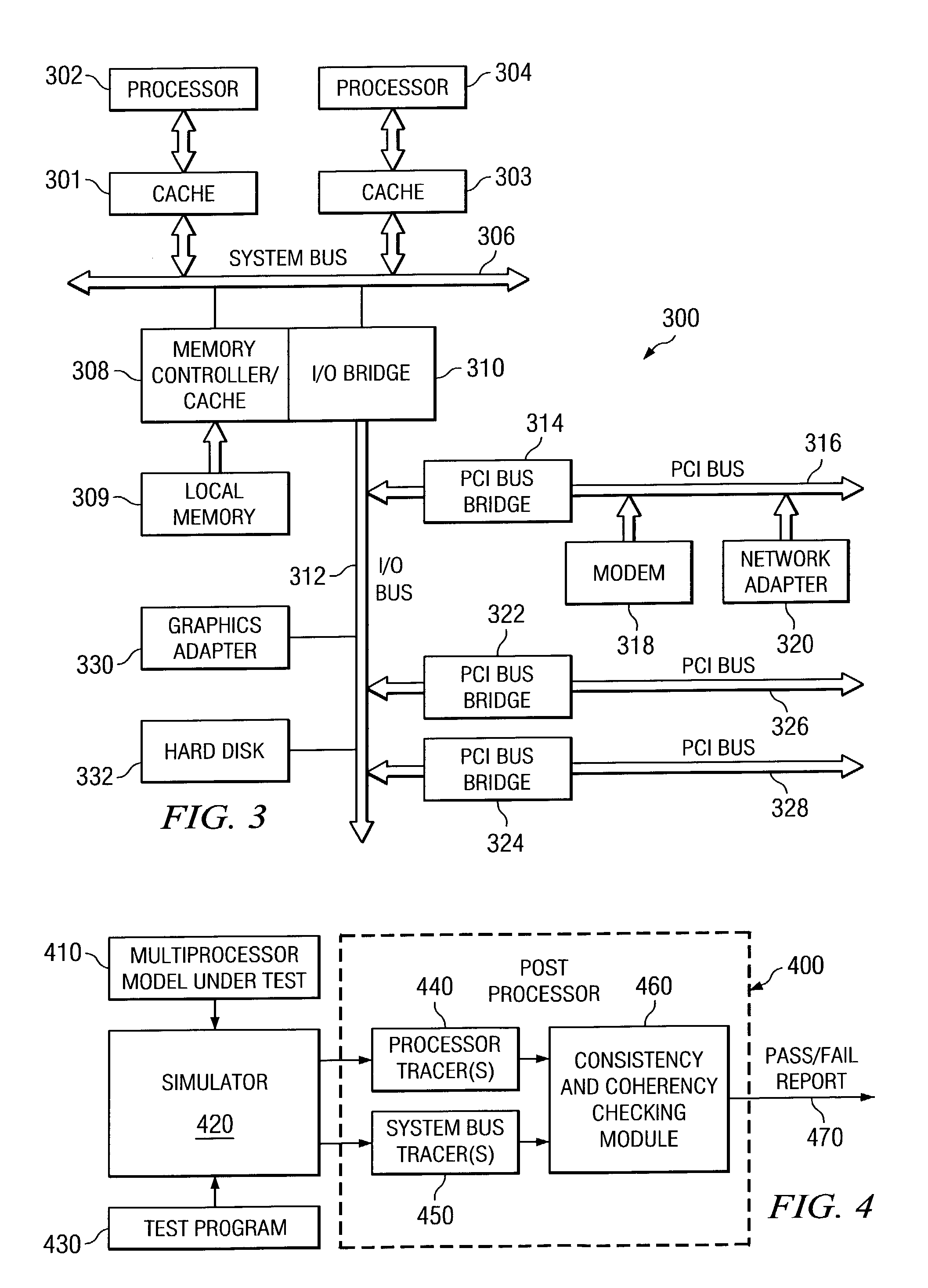
Method and apparatus for verification of coherence for shared cache components in a system verification environment
InactiveUS7000079B2Memory architecture accessing/allocationError detection/correctionSystem verificationParallel computing
A method and apparatus for verification of coherence for shared cache components in a system verification environment are provided. With the method and apparatus, stores to the cache are applied to a cache functional simulator in the order that they occur in the trace information from the canonical tracers. However, rather than updating the cache simulator with the actual data stored, the performed time of the store event is applied to the simulator as data. The cache simulator stores the latest performed time for each byte of each cache line in the simulated cache, in an associated data structure. For each load event that is encountered in the trace information for a byte, a comparison is made between a global expected data age of the data in the cache and the performed time associated with the byte. If the data age in the simulated cache for the byte is less than the global expected data age, i.e. a latest previously encountered data age, then a cache coherence violation has occurred.
Owner:IBM CORP
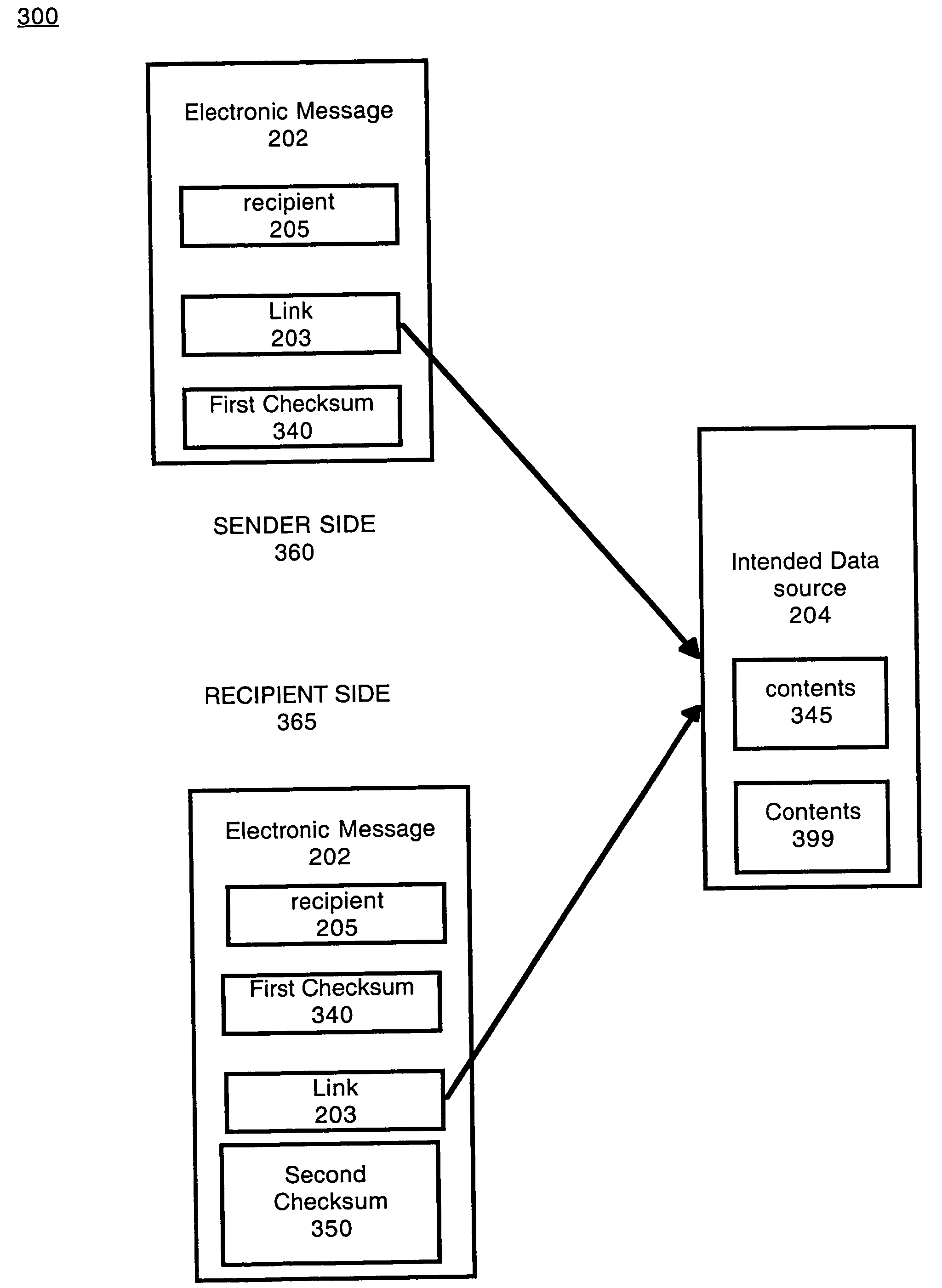
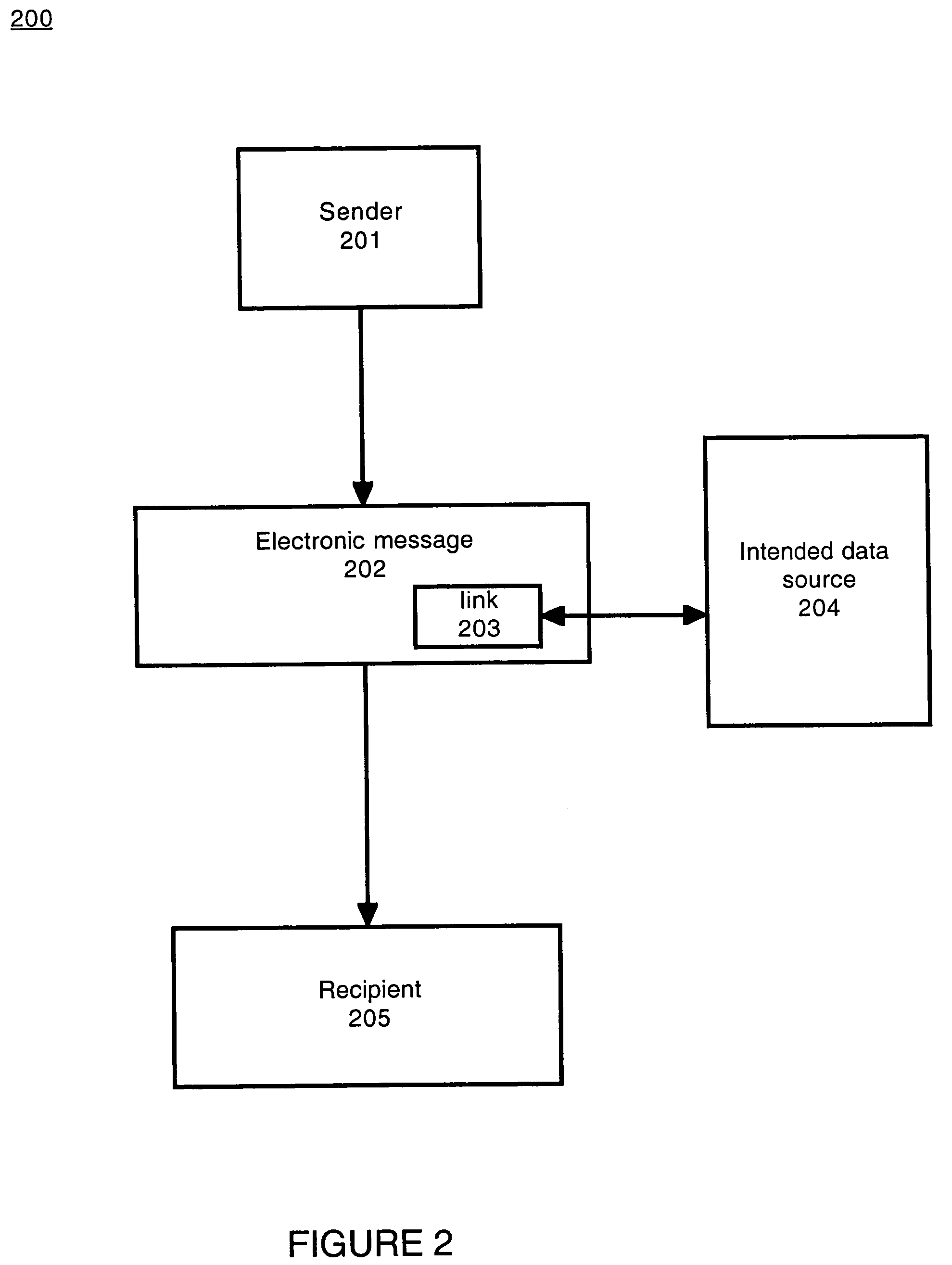
System and method for verifying intended contents of an electronic message
ActiveUS8452880B2Digital data processing detailsMultiple digital computer combinationsData sourceRecipient side
Embodiments of the present invention include a method and system for verifying intended contents of an electronic message comprising: accessing an electronic message destined for a recipient comprising a link to an intended data source. The method further includes accessing the intended data source and computing a first message digest value associated with the intended data source. Additionally, the method includes sending the electronic message and the first message digest value to the recipient. The recipient side may check the message digest value against a recently generated value and alert the recipient of any digest mismatch that represents a recent change in the intended data source.
Owner:ORACLE INT CORP
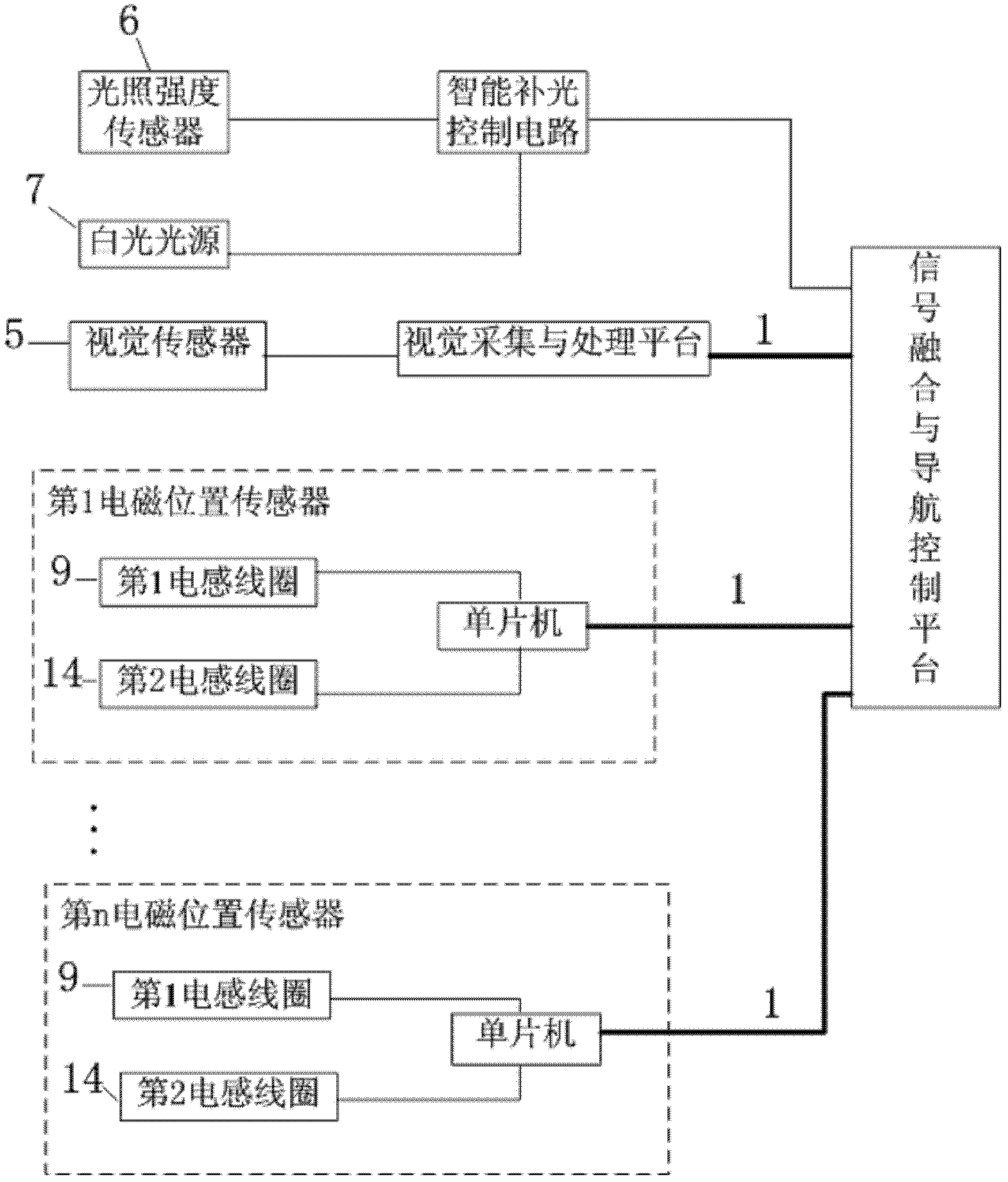
Vision and electromagnet based fusion inspecting navigation control system
InactiveCN102621985AForward-lookingHigh speedPosition/course control in two dimensionsVision basedRoad surface
The invention discloses a vision and electromagnet based fusion inspecting navigation control system, which belongs to the technical field of automatic detection and control. The vision and electromagnet based fusion inspecting navigation control system is structurally characterized in that an intelligent light filling control circuit is connected with a illumination intensity sensor, a white light source and a signal fusion and navigation control platform respectively, a vision acquisition and processing platform is connected with a vision sensor and is connected with the signal fusion and navigation control platform through a RS485 bus, yellow navigation lines are laid on road surfaces, induced navigation lines are laid under the road surfaces, and two ends of the induced navigation lines are connected with electromagnetic signal generators to form a loop. The vision and electromagnet based fusion inspecting navigation control system has the advantages that (1), speed can be optimized and increased by the aid of prospective data, the system can be adaptable to all whether including rainy and snowy days all year round; (2) the vision sensor and electromagnetic position sensors can be used independently or integrally; (3) fusion can be achieved dynamically according to requirements by the aid of an intelligent software self-adaptive data fusion unit designed and developed; and (4) cost and power consumption are low.
Owner:CHINA AGRI UNIV
Database modeling and analysis
ActiveCN105556515ADesign optimisation/simulationSpecial data processing applicationsData miningProspective data
A method of modeling a prospective database migration between database systems may include collecting performance data associated with a plurality databases in a first database system. The method may also include receiving a selection of a set of databases in the plurality of databases to migrate to a second database system. The method may additionally include computing, using at least some of the performance data, combined performance data that estimates how the set of databases will perform on the second database system. The method may further include providing one or more indications as to whether the set of databases should be migrated to the second database system. In some embodiments, the one or more indications may be based on the combined performance data.
Owner:ORACLE INT CORP
Managing supplied data
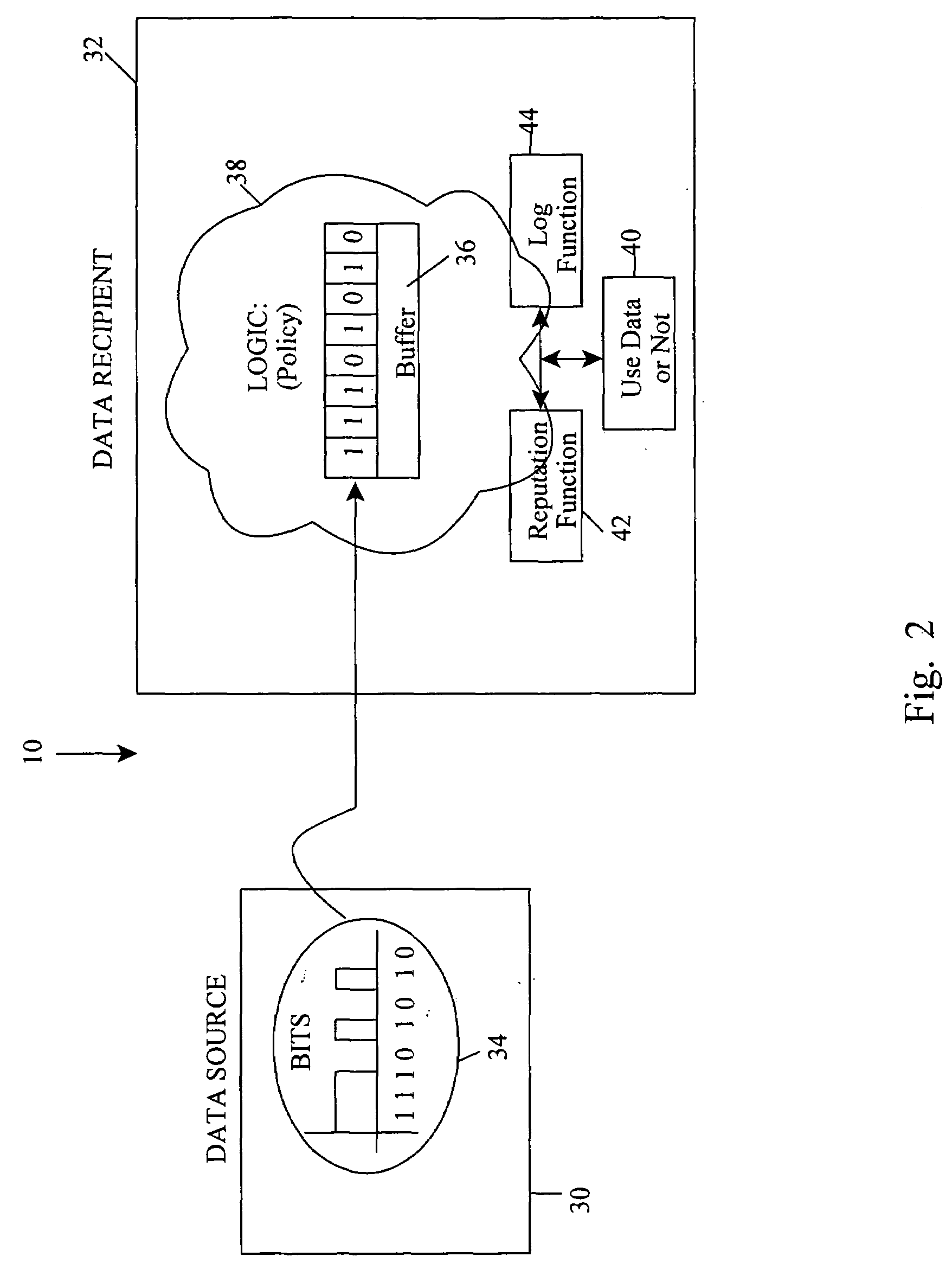
In a computing system environment, a data recipient manages entropy data supplied from an external data source despite not knowing or being certain about their trustworthiness or if such varies over time. Features relate to scoring the data and determining whether it meets or exceeds a predetermined policy score. One or more initial or updated reputation values of the data source are contemplated and used for scoring. Logging of the scoring, reputation values or other matters is provided for historical purposes and to identify possible future corrective actions. Other embodiments contemplate enhancing the score of the entropy data. In some instances, use of less than all the data by the recipient occurs to increase attack-resistance. Whether such occurs or how much occurs remains substantially unbeknownst to all parties other than the data recipient. Still other embodiments contemplate computer-readable media.
Owner:APPLE INC
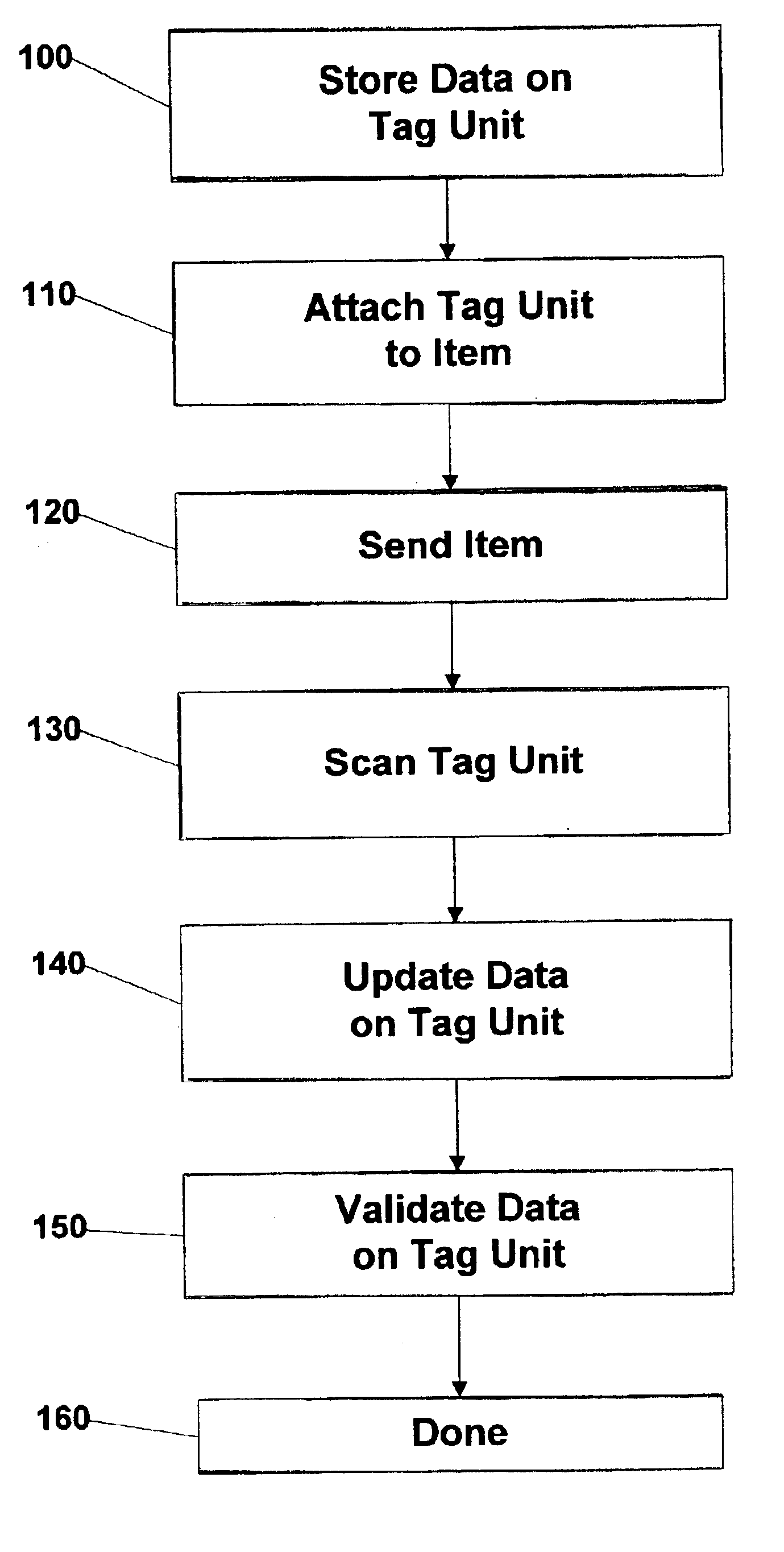
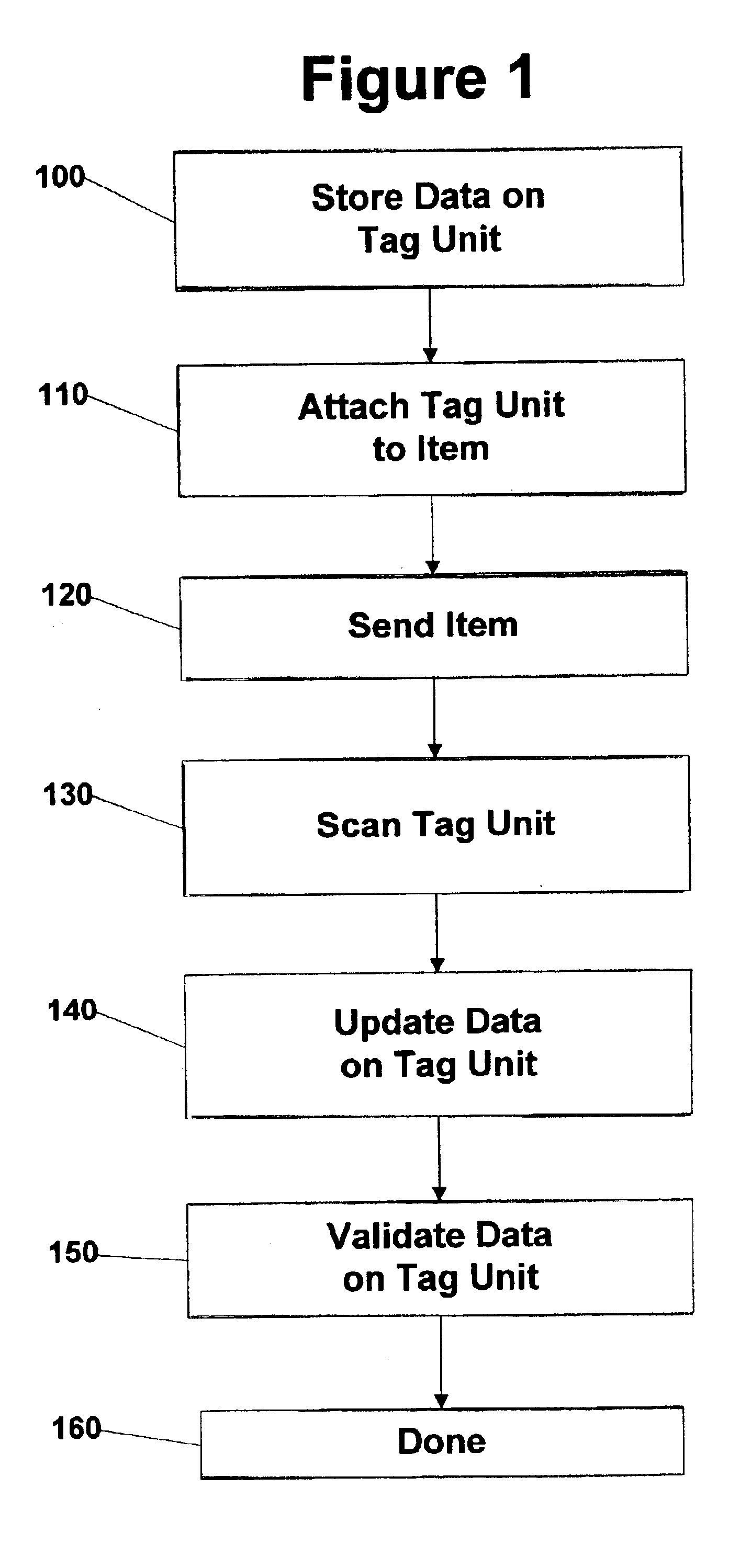
Method and system for collaborative and fail-tolerant deployment of automatic identification and data collection (AIDC) devices
InactiveUS6919807B2Memory record carrier reading problemsCo-operative working arrangementsComputer hardwareData store
Data is stored on a tag unit. The tag unit provides for alert monitoring capabilities and monitoring of events, these capabilities allow for supply chain plans to be restructured and for events to be rescheduled. The tag unit is attached to an item for tracking purposes. The tag unit monitors and stores a status of the item. Then the item is sent to a destination. The tag unit is scanned when the item has been sent to a destination. The data on the tag unit is updated as a function of scanning. The data is updated when the tag unit is scanned at a destination. Then the data on the tag unit is validated. The data is validated for security purposes. The data on the tag unit is scanned to identify conditions to trigger actions. The system recovers from failure to read data on the tag unit by reconstructing the expected data from a history of the tag unit. Failure may be a result of identified or unidentified tempering of tag units, failure of the tag unit mechanism, or violation of the tag unit access limitations.
Owner:TRACKX INC
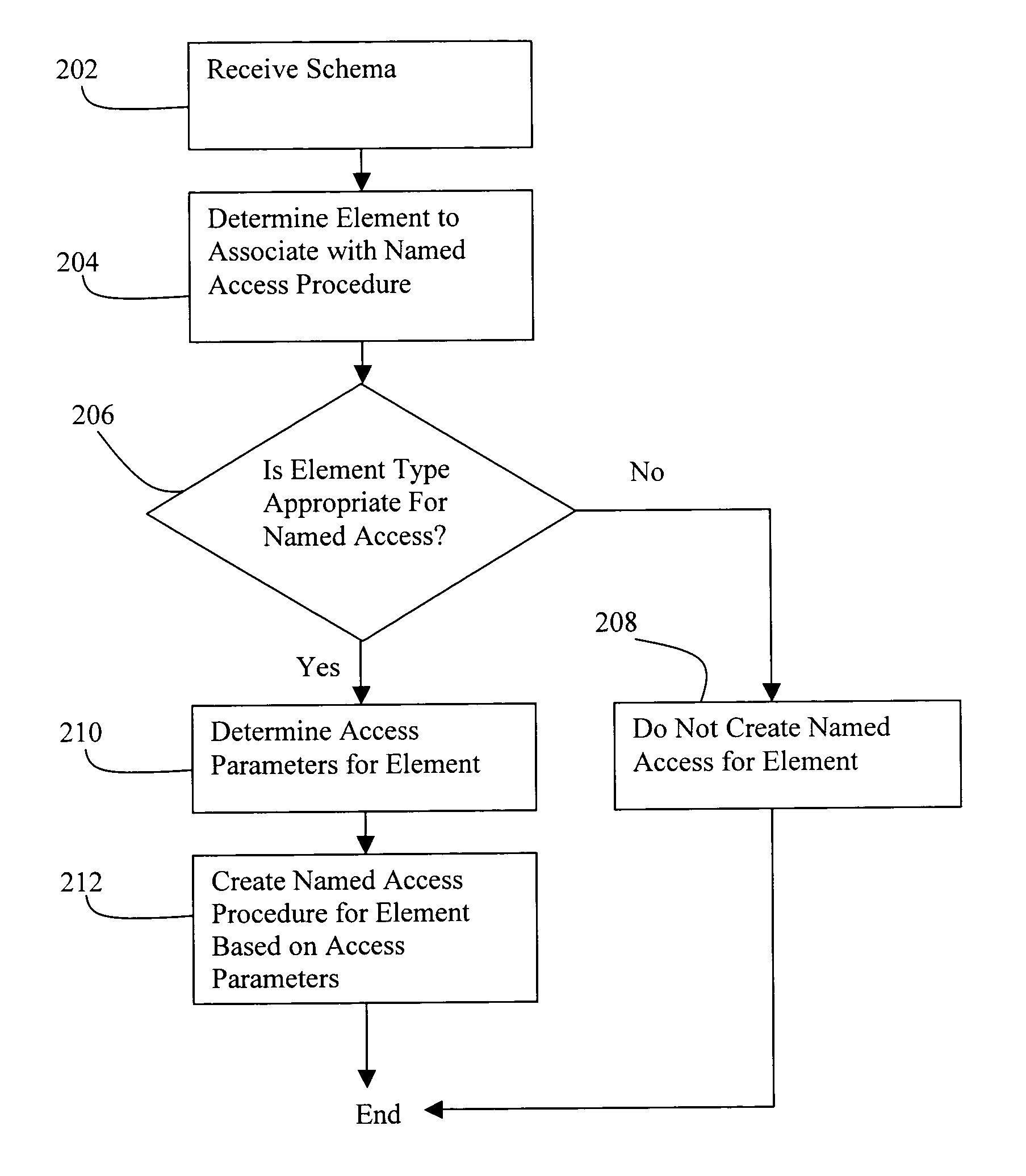
Method and mechanism for efficient access to nodes in XML data
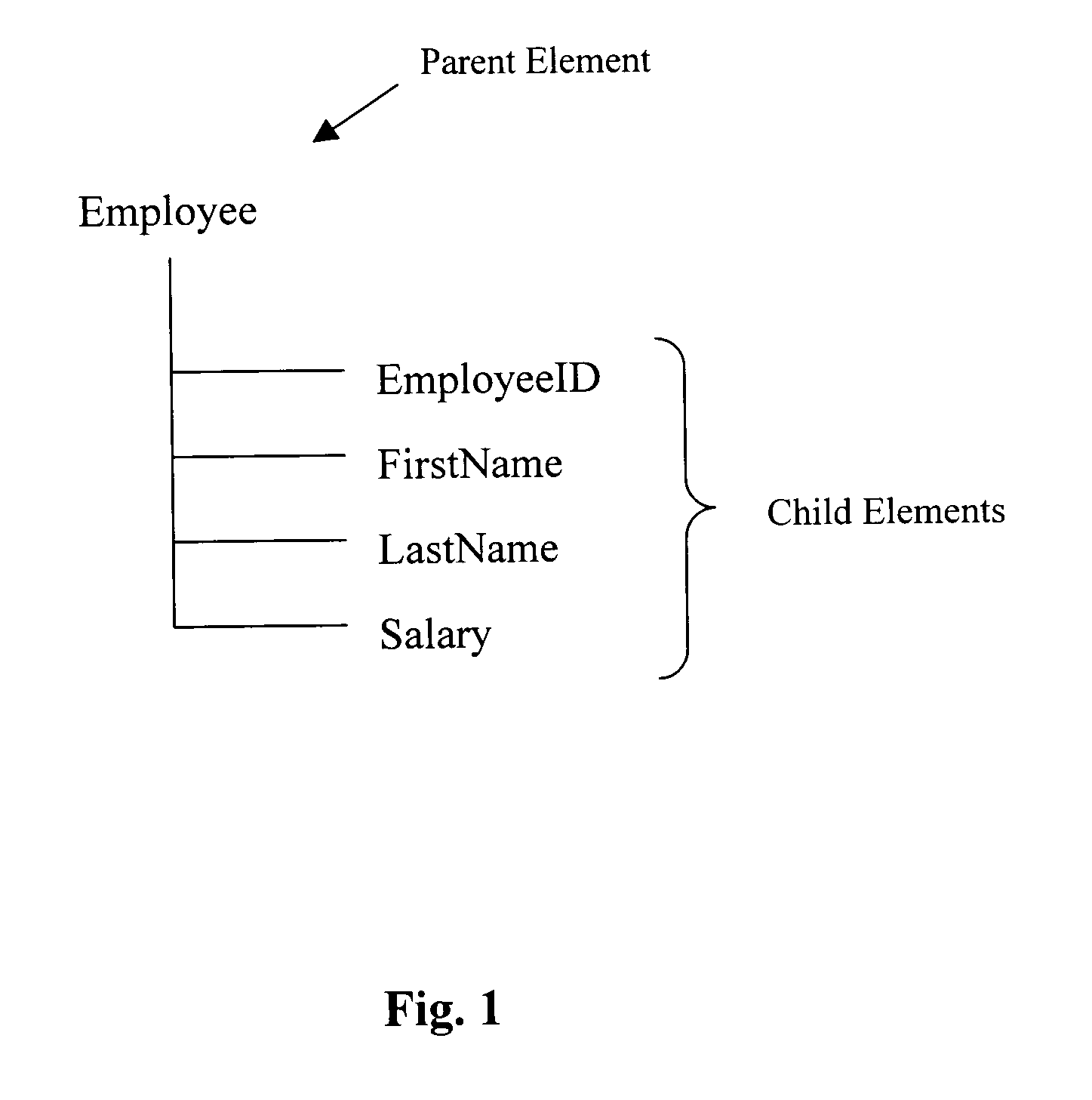
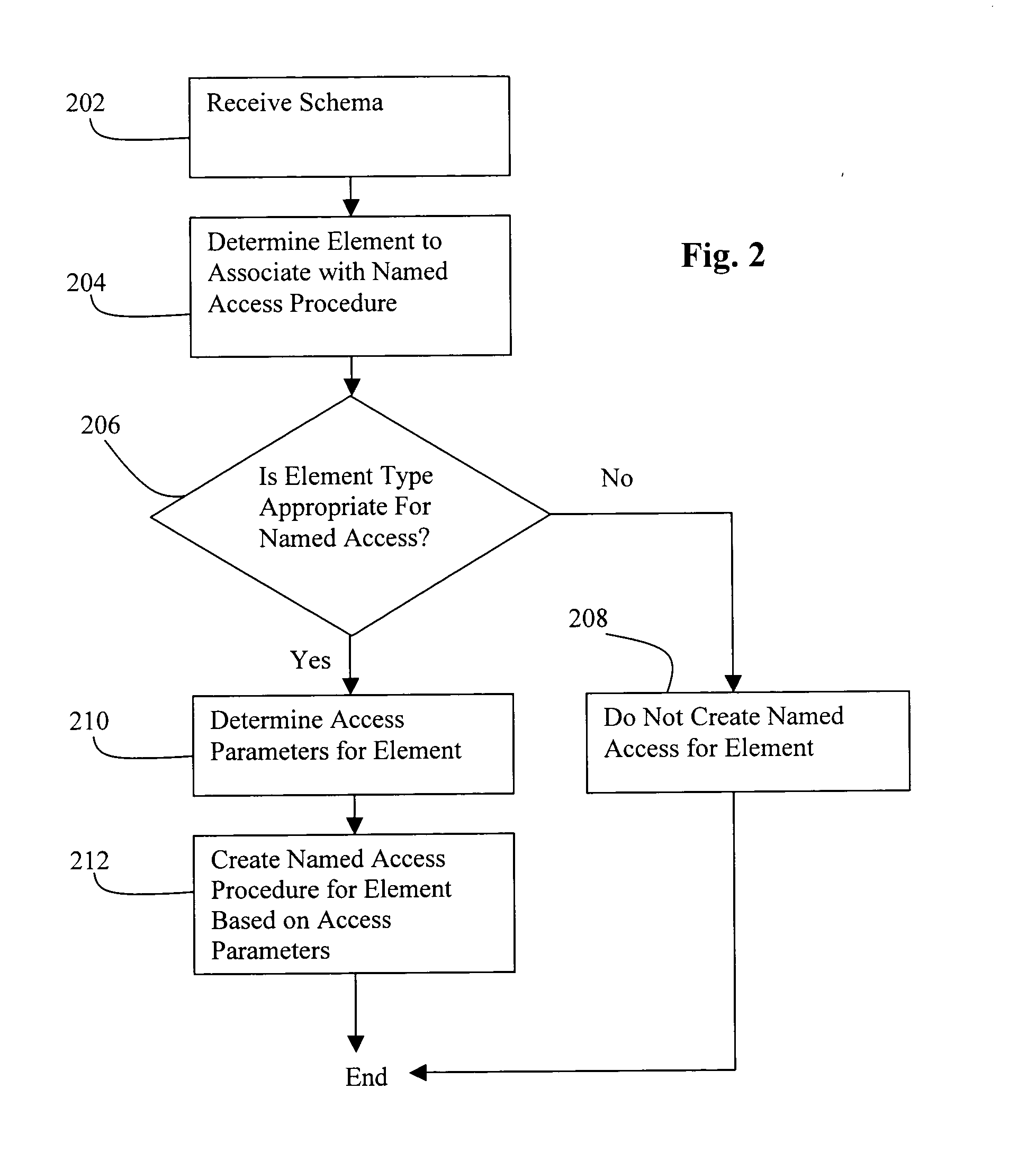
InactiveUS20050055629A1Lazy manifestationRetrieve data moreSemi-structured data mapping/conversionSpecial data processing applicationsDocumentationDatabase
Disclosed is a method and mechanism for accessing XML data. In one approach, in the case of a schema based document, the structure of the XML document is known apriori and this information can be exploited to store and retrieve the data more efficiently. A Named Access interface or procedure can be defined and associated with elements of the schema. The need for datatype conversions can be eliminated by allowing direct mapping to the intended datatype or the closest matching datatype in the system to which the invention is directed. The storage information can be exploited to provide “direct” access to data based on offset in lieu of a linear traversal. Another aspect is that only the relevant portions need to be even loaded into memory.
Owner:ORACLE INT CORP
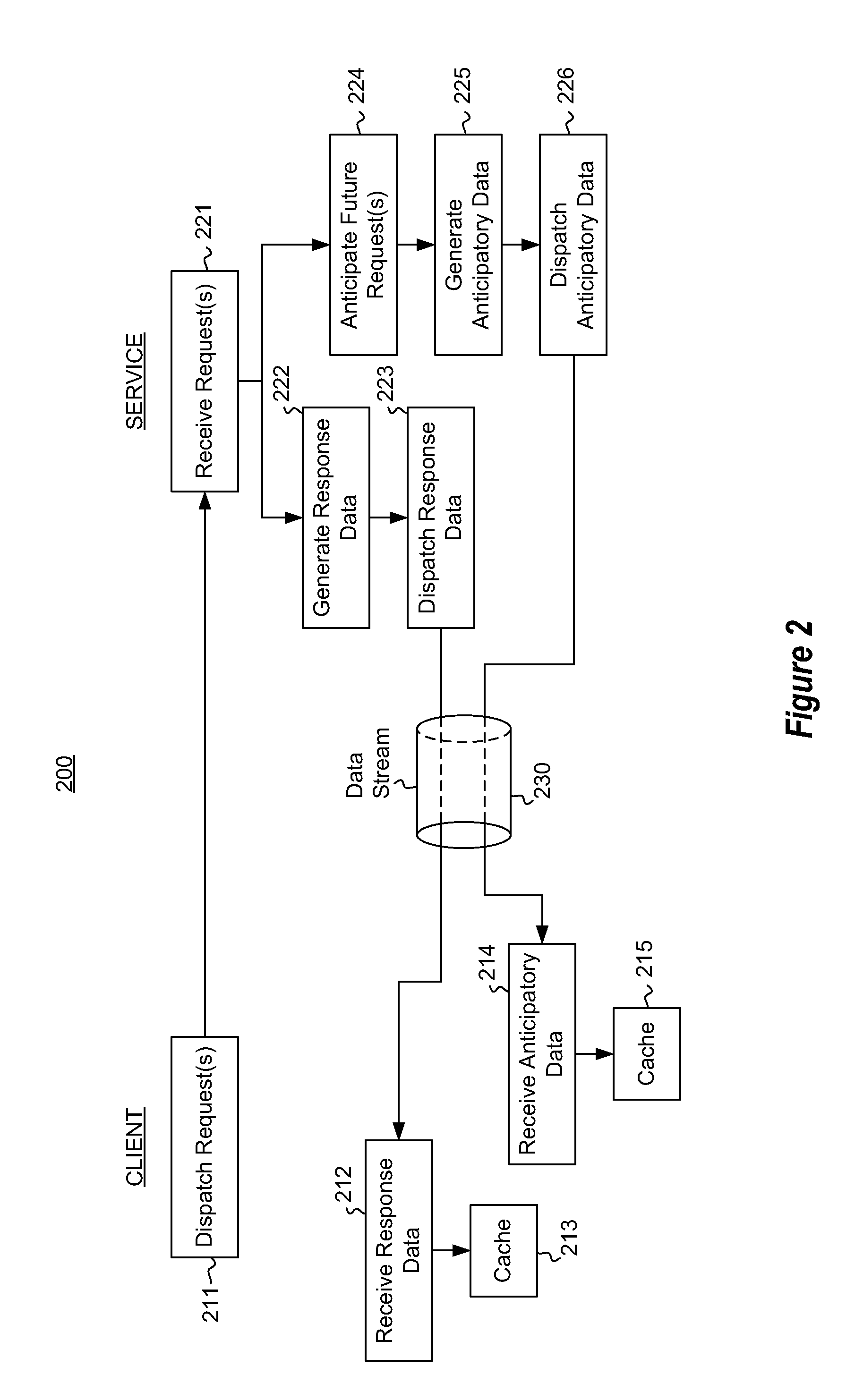
Anticipatory response pre-caching
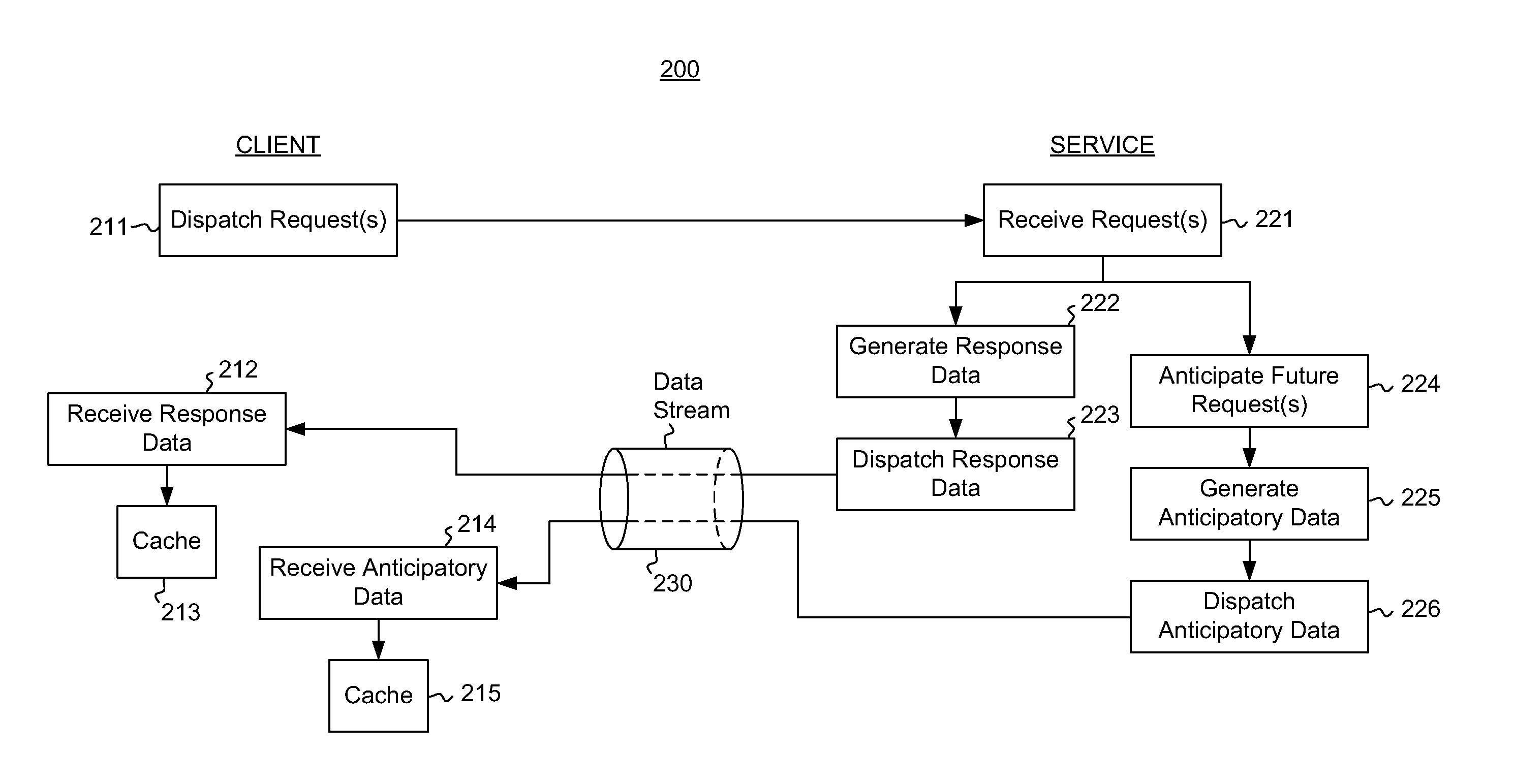
ActiveUS20110238921A1Lower latencyMemory adressing/allocation/relocationMultiple digital computer combinationsData streamClient-side
Interaction between a client and a service in which the service responds to requests from the client. In addition to responding to specific client requests, the service also anticipates or speculates about what the client may request in the future. Rather than await the client request (that may or may not ultimately be made), the service provides the unrequested anticipatory data to the client in the same data stream as the response data that actual responds to the specific client requests. The client may then use the anticipatory data to fully or partially respond to future requests from the client, if the client does make the request anticipated by the service. Thus, in some cases, latency may be reduced when responding to requests in which anticipatory data has already been provided. The service may give priority to the actual requested data, and gives secondary priority to the anticipatory data.
Owner:MICROSOFT TECH LICENSING LLC
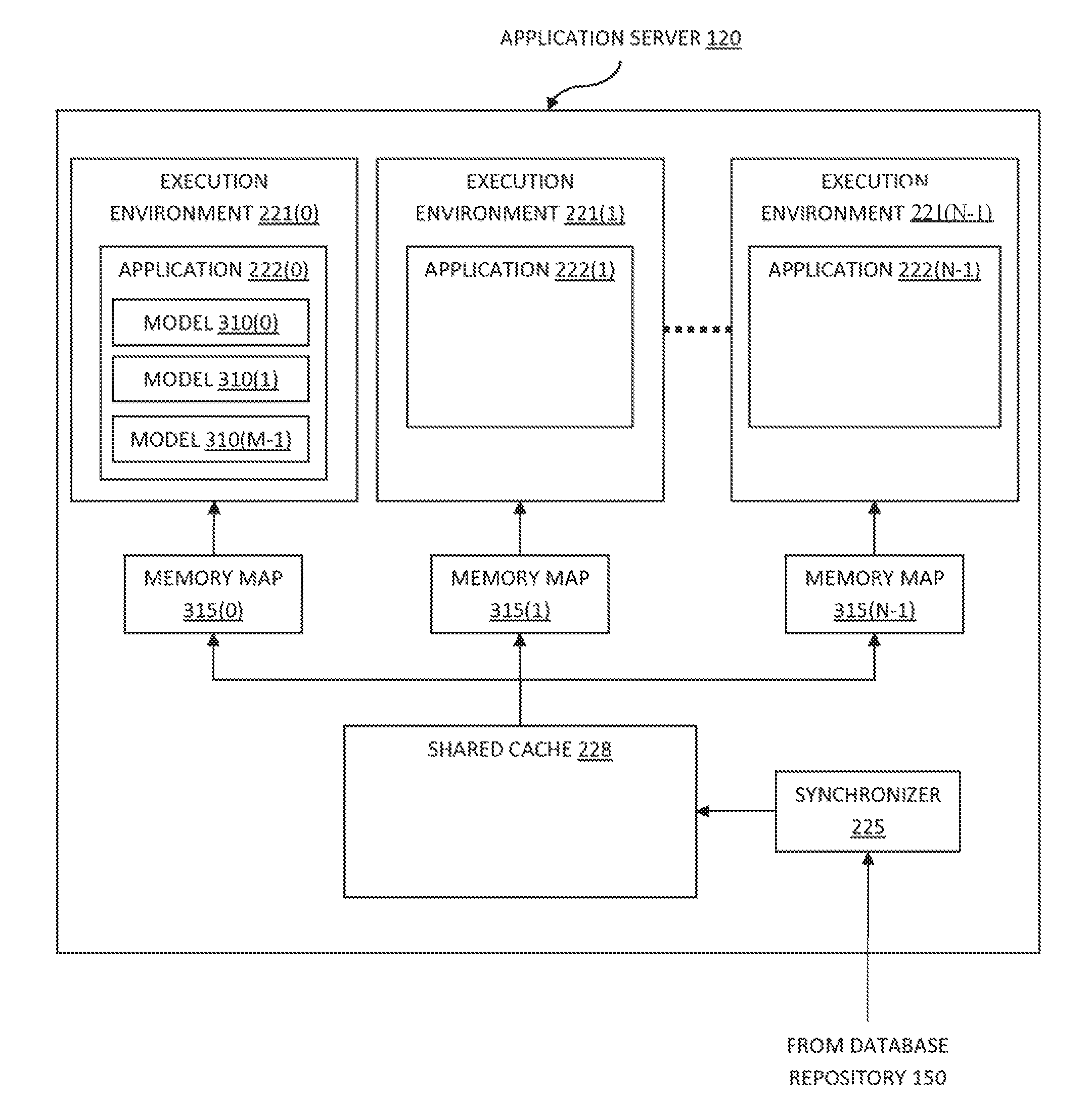
System and method utilizing a shared cache to provide zero copy memory mapped database
ActiveUS9367463B2Facilitates aggregating subsetEfficient analysisMemory architecture accessing/allocationDigital data information retrievalMemory addressData set
Methods and systems for providing a plurality of applications with concurrent access to data are disclosed. One such method includes identifying attributes of an expected data set to be accessed concurrently by the applications, initializing a shared cache with a column data store configured to store the expected data set in columns and creating a memory map for accessing a physical memory location in the shared cache. The method may also include mapping the applications' data access requests to the shared cache with the memory map. Only one instance of the expected data set is stored in memory, so each application is not required to create additional instances of the expected data set in the application's memory address space. Therefore, larger expected data sets may be entirely stored in memory without limiting the number of applications running concurrently.
Owner:PALANTIR TECHNOLOGIES
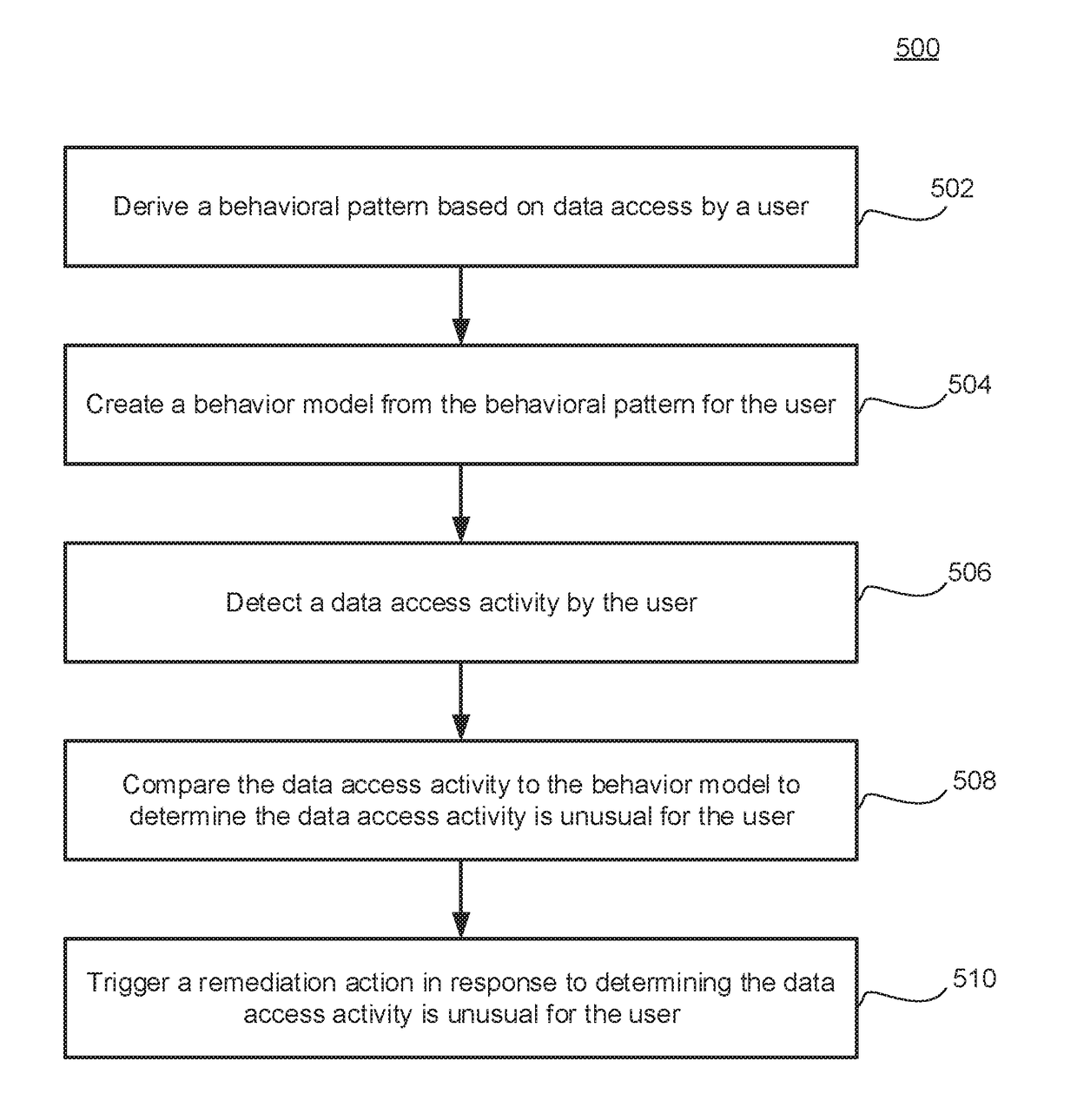
Systems and methods for modeling and monitoring data access behavior
InactiveUS20180191759A1Computer security arrangementsDesign optimisation/simulationInternet privacyData access
A system for monitoring data-access behavior is provided. The system may derive a behavioral pattern based on at least one of historic data access by a user or expected data access by the user. The system may also generate a behavioral model for the user based on the behavioral pattern for the user. In response to detecting a data access activity by the user, the system may compare the data access activity to the behavioral model to determine the data access activity is unusual for the user. The system may further trigger a remediation action in response to determining the data access activity is unusual for the user.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
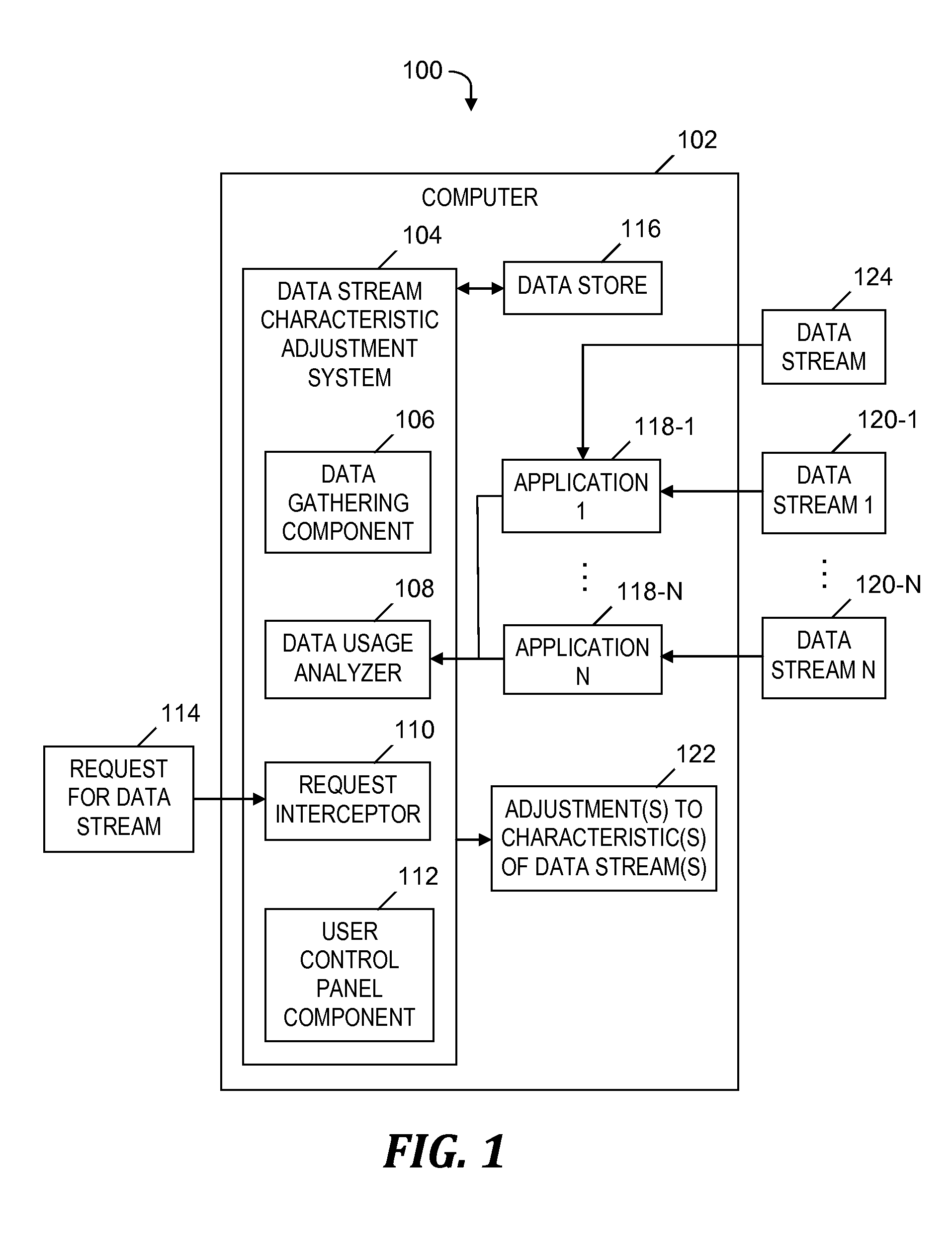
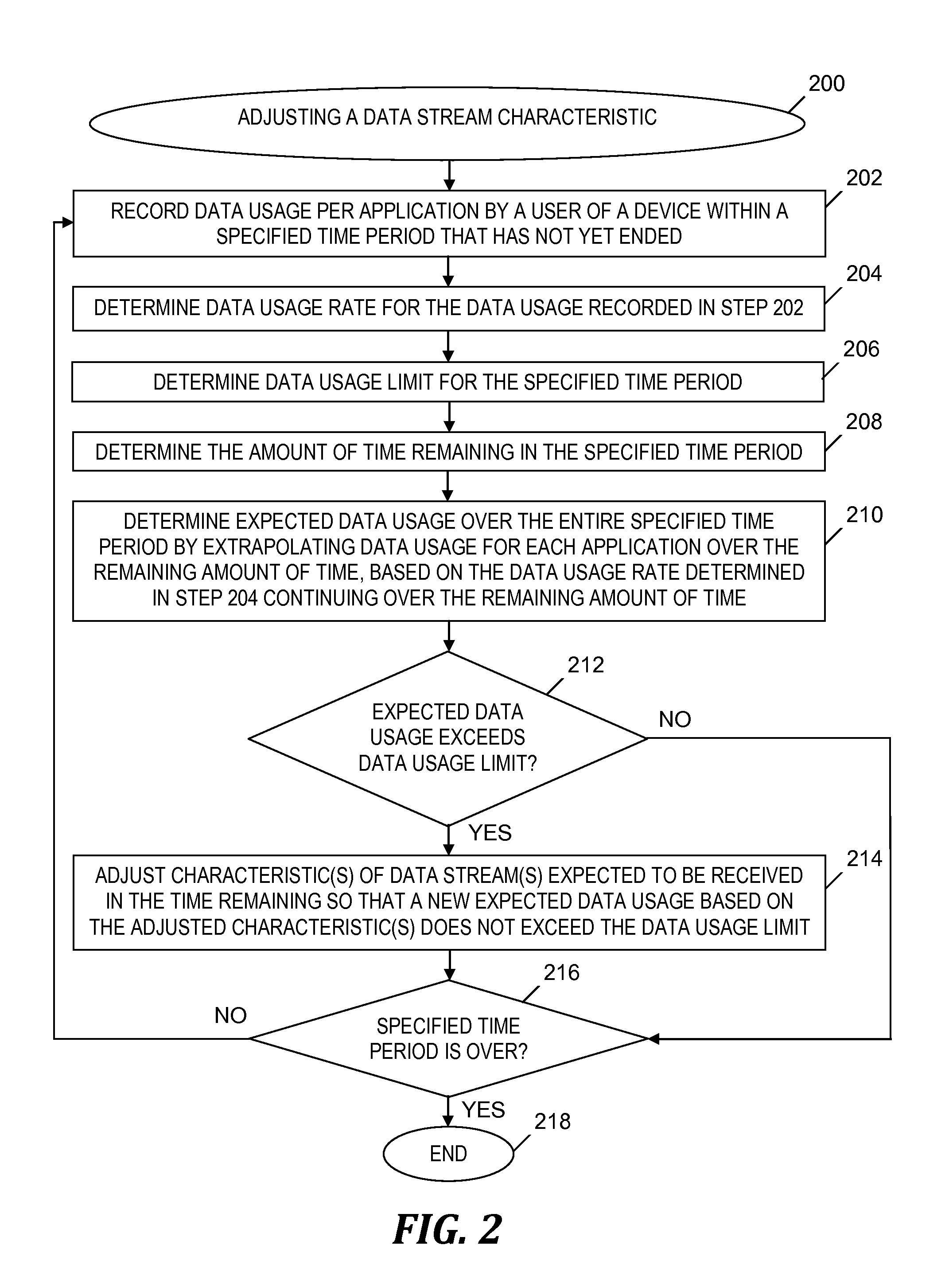
Changing a data stream characteristic based on a data usage rate
InactiveUS20150350956A1Avoid feesAvoiding other penaltyAccounting/billing servicesNetwork traffic/resource managementData streamData mining
An approach is provided for adjusting a characteristic of a data stream. A rate of data usage provided by one or more data streams within a time period that has not ended is determined. An amount of time remaining in the time period is determined. Based at least in part on the amount of time remaining in the time period and the rate of data usage, an expected amount of data usage within the entire time period is determined. Whether the expected amount of data usage exceeds a limit on data usage within the entire time period is determined. If the expected amount of data usage exceeds the limit, the characteristic of the data stream is adjusted so that actual data usage within the entire time period does not exceed the limit. The actual data usage is based in part on the adjusted characteristic.
Owner:IBM CORP
Shared cache used to provide zero copy memory mapped database
ActiveUS20140281115A1Efficient Data AnalysisFacilitates aggregating subsetMemory architecture accessing/allocationDigital data information retrievalMemory addressData set
A technique for concurrently accessing a data set includes initializing a shared cache with a column data store configured to store an expected data set in columns and creating a memory map for accessing the physical memory location in the shared cache. Other operations include mapping the applications' data access requests to the shared cache with the memory map. One advantage of the disclosed technique is that only one instance of the expected data set is stored in memory, so each application is not required to create additional instances of the expected data set in the applications memory address space. Therefore, larger expected data sets may be entirely stored in memory without limiting the number of applications running concurrently.
Owner:PALANTIR TECHNOLOGIES
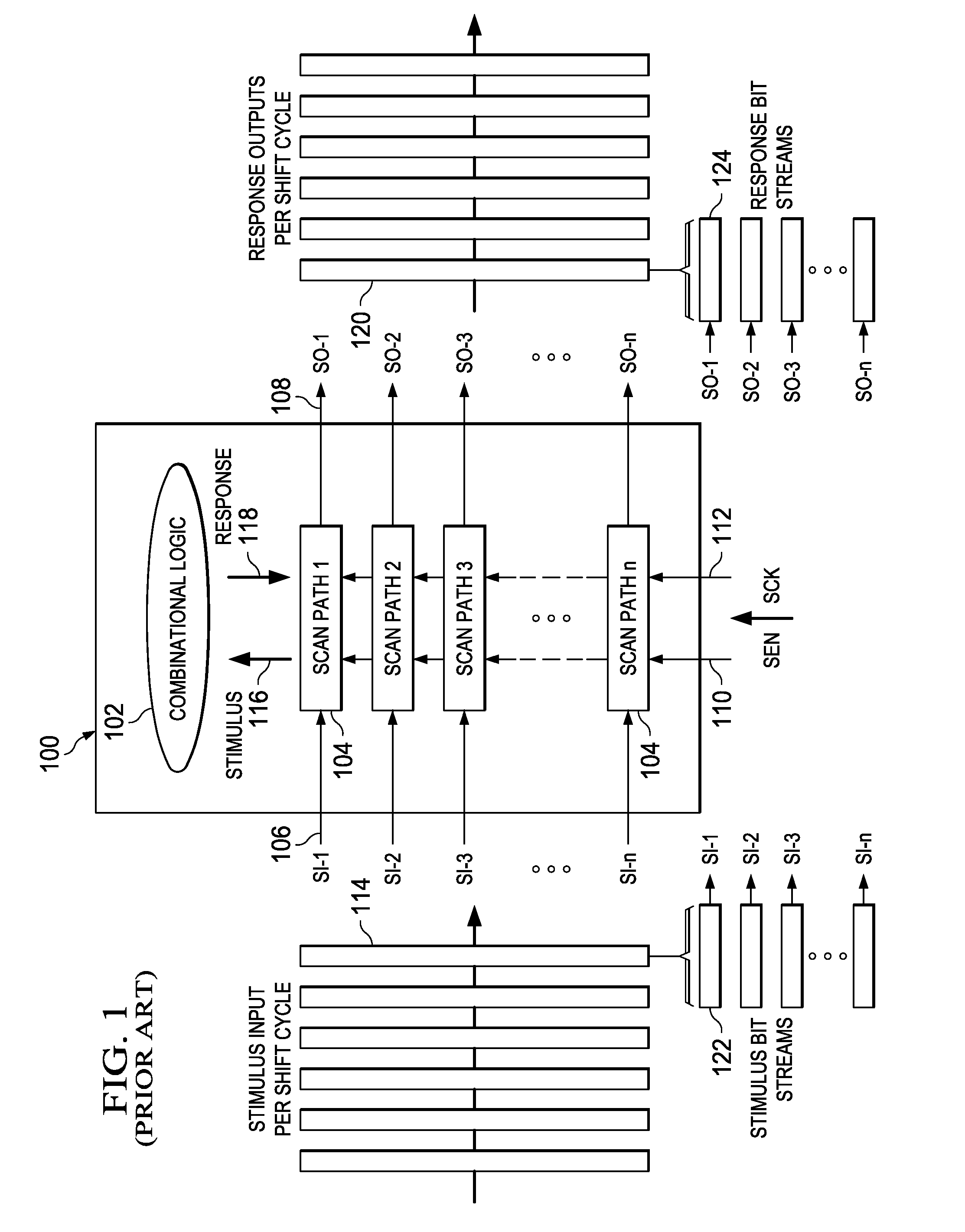
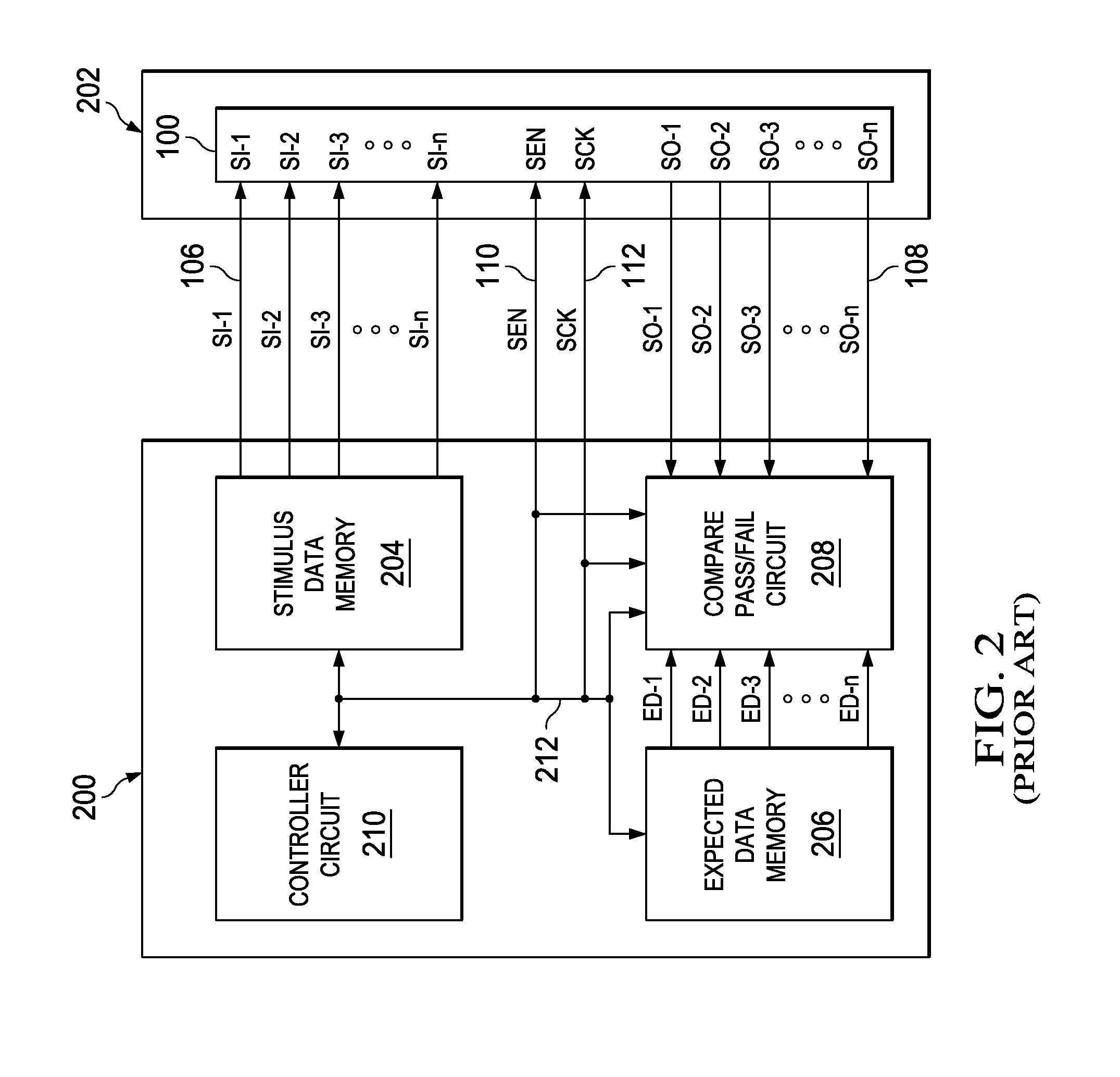
Formatter selectively outputting scan stimulus data from scan response data
Owner:TEXAS INSTR INC
Data leakage prevention over application programming interface
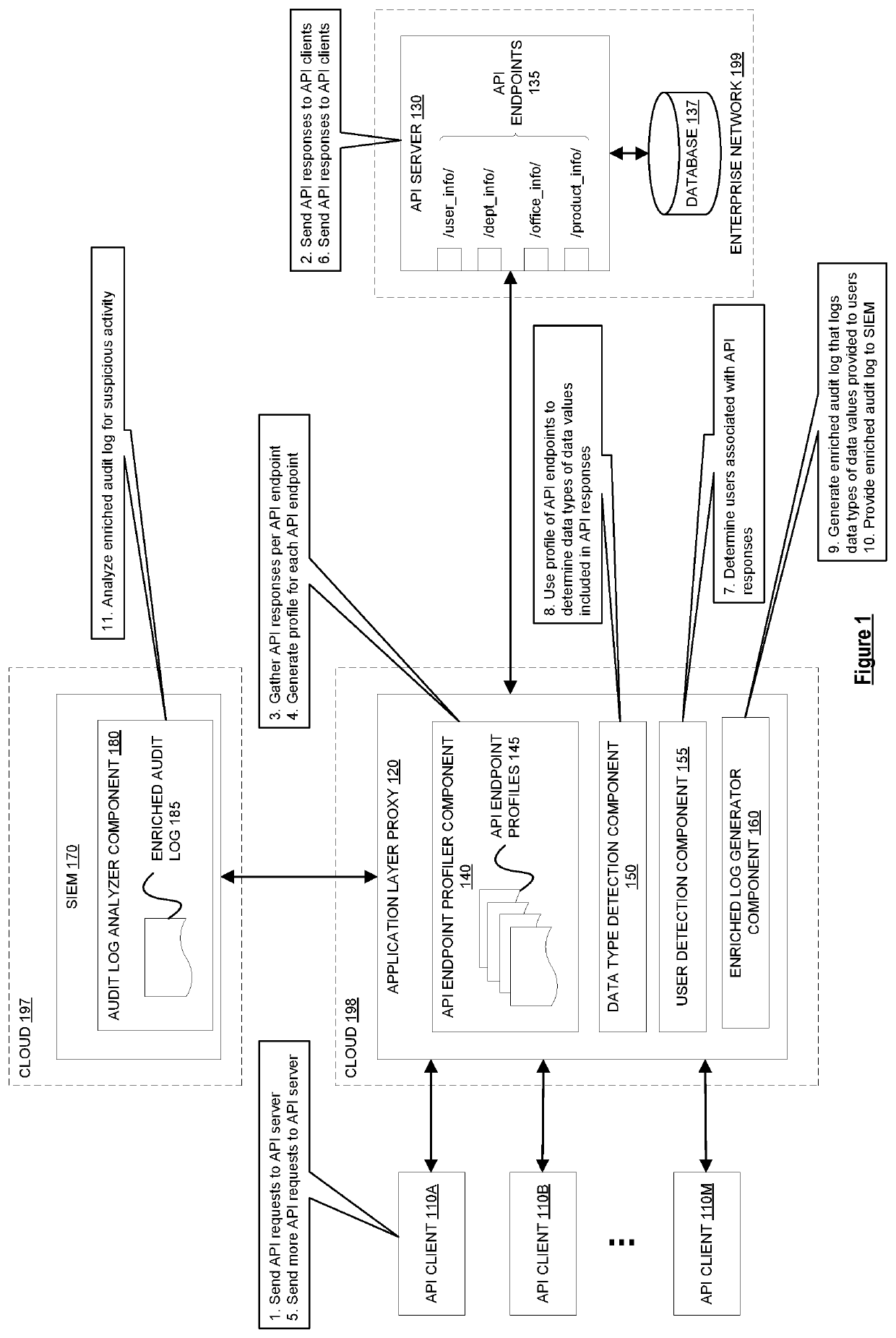
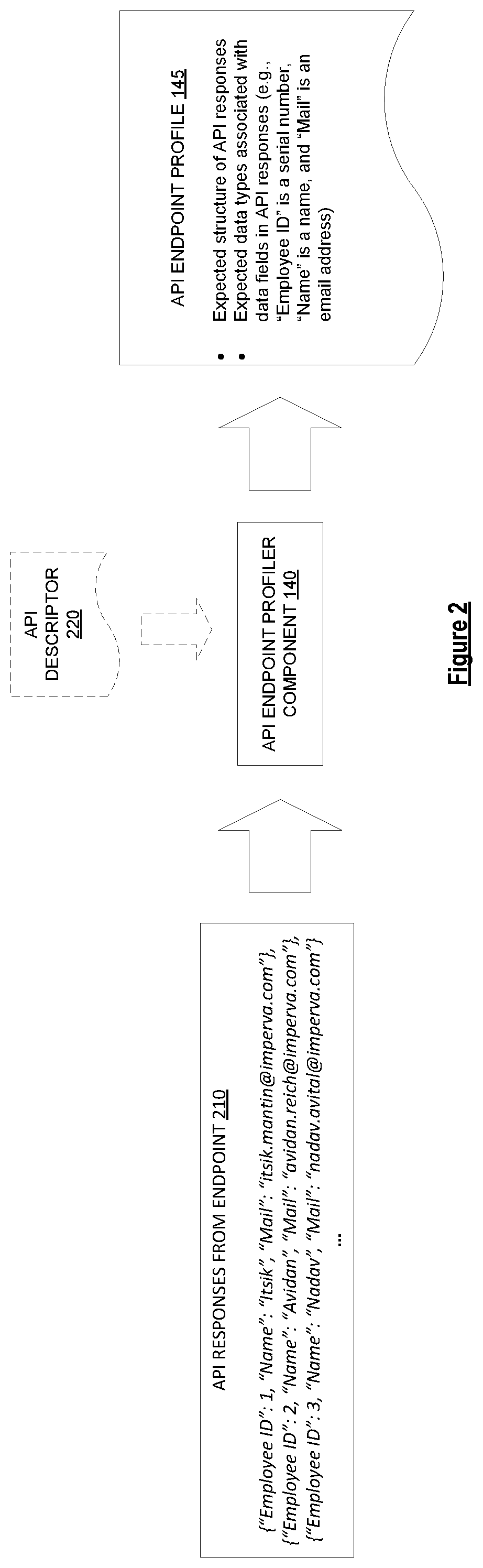
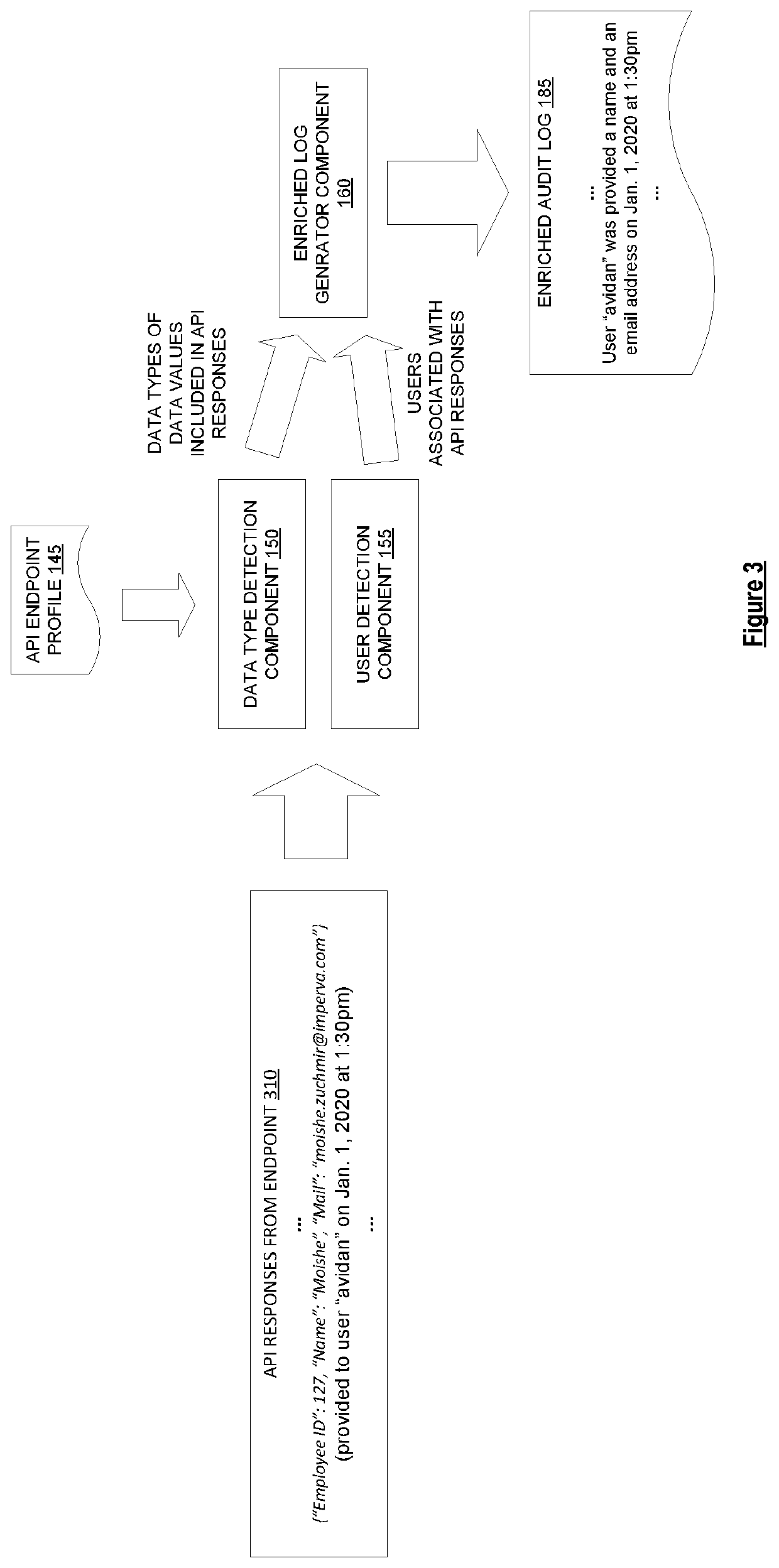
A method by a network device for generating audit logs. The method includes obtaining a first set of application programming interface (API) responses from an endpoint of an API, generating a profile for the endpoint of the API based on analyzing the first set of API responses, where the profile of the endpoint indicates an expected structure of API responses and expected data types associated with data fields included in API responses, obtaining a second set of API responses, using the API profile to determine, for each API response in the second set of API responses, data types of data values included in that API response, and generating an audit log that logs information regarding the data types of the data values included in the second set of API responses.
Owner:IMPERVA
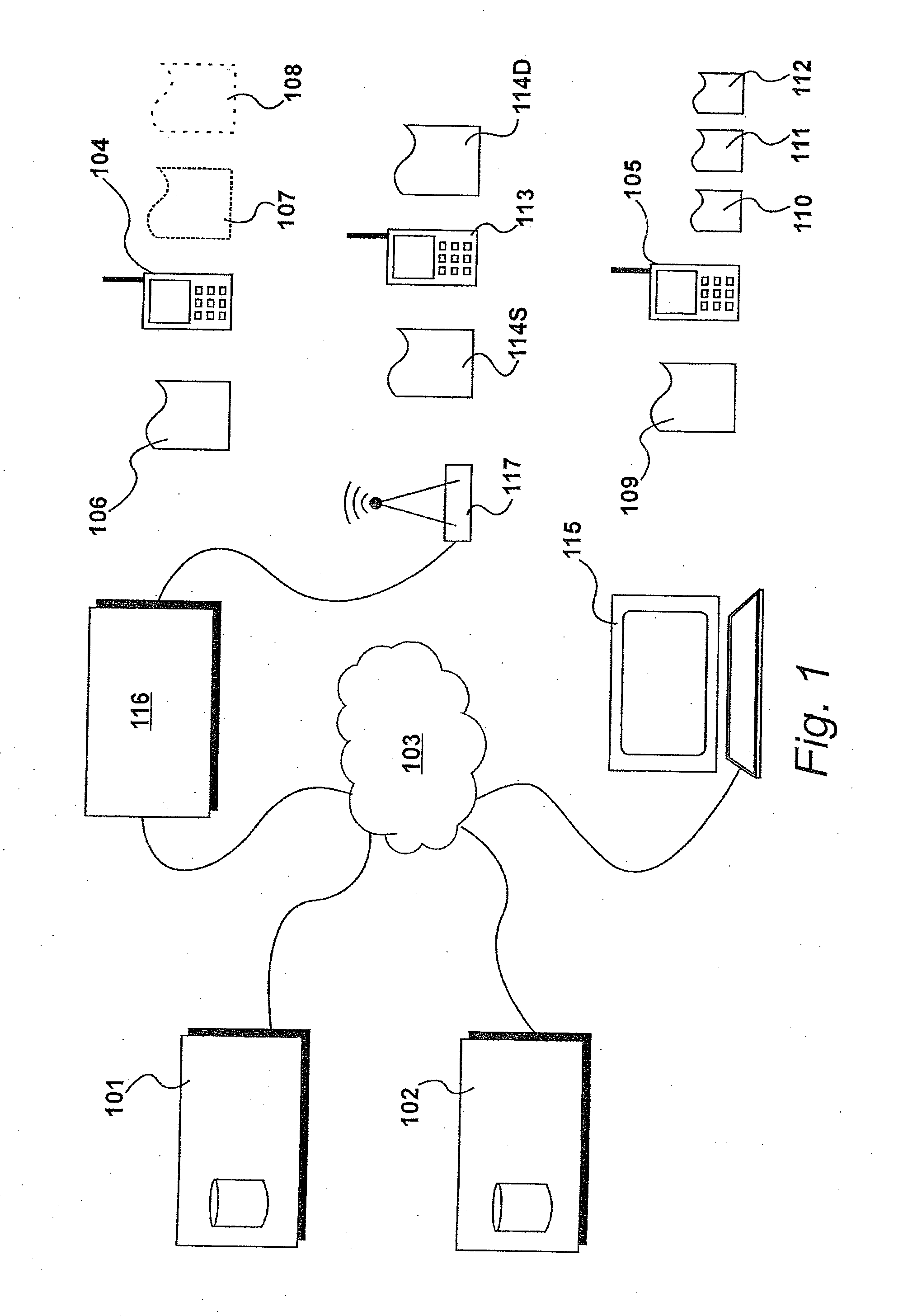
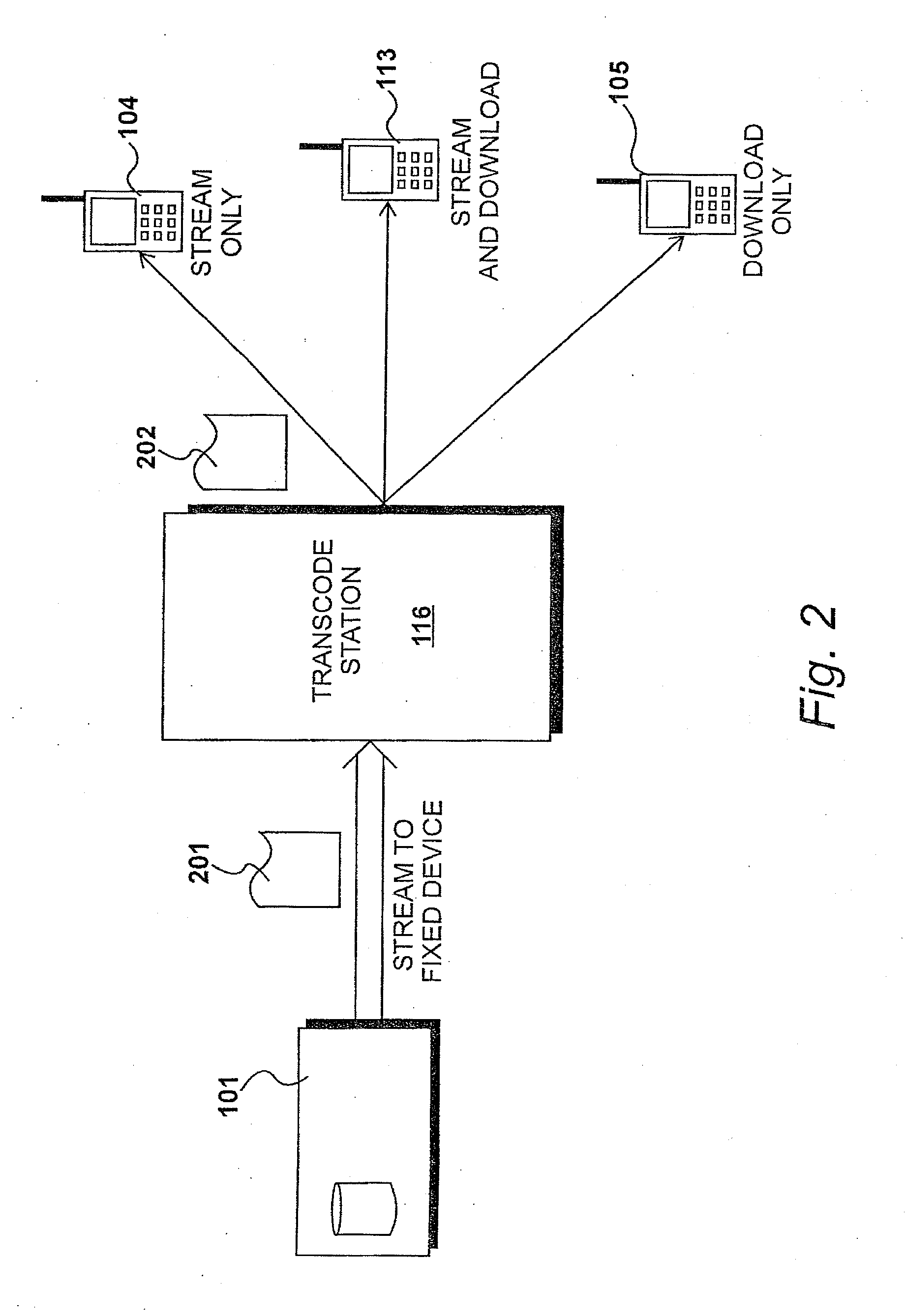
Transcoding Video Data
InactiveUS20100266009A1Picture reproducers using cathode ray tubesPicture reproducers with optical-mechanical scanningComputer hardwareTranscoding
Video data is transcoded on the fly to produce a progressive download viewed while the data is being received while streaming and / or may be downloaded and played later. An analyser analyses a portion of an input video data file to determine coded characteristics of encoded input video and determines an expected data volume. A generator generates a file header for output video data that includes an indication of the expected volume thereof. A transcoder transcodes the input video data to produce encoded output video data. The output interface supplies the encoded output video data with the file header as a stream to a receiving device. In a first embodiment, the expected volume of data in the header is overestimated and blank video chunks added. In an alternative embodiment, the expected data of volume is underestimated and compression parameters are modified during the transcoding process.
Owner:SAFFRON DIGITAL
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com