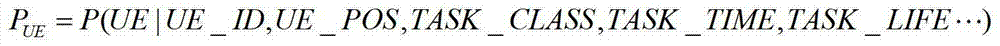Patents
Literature
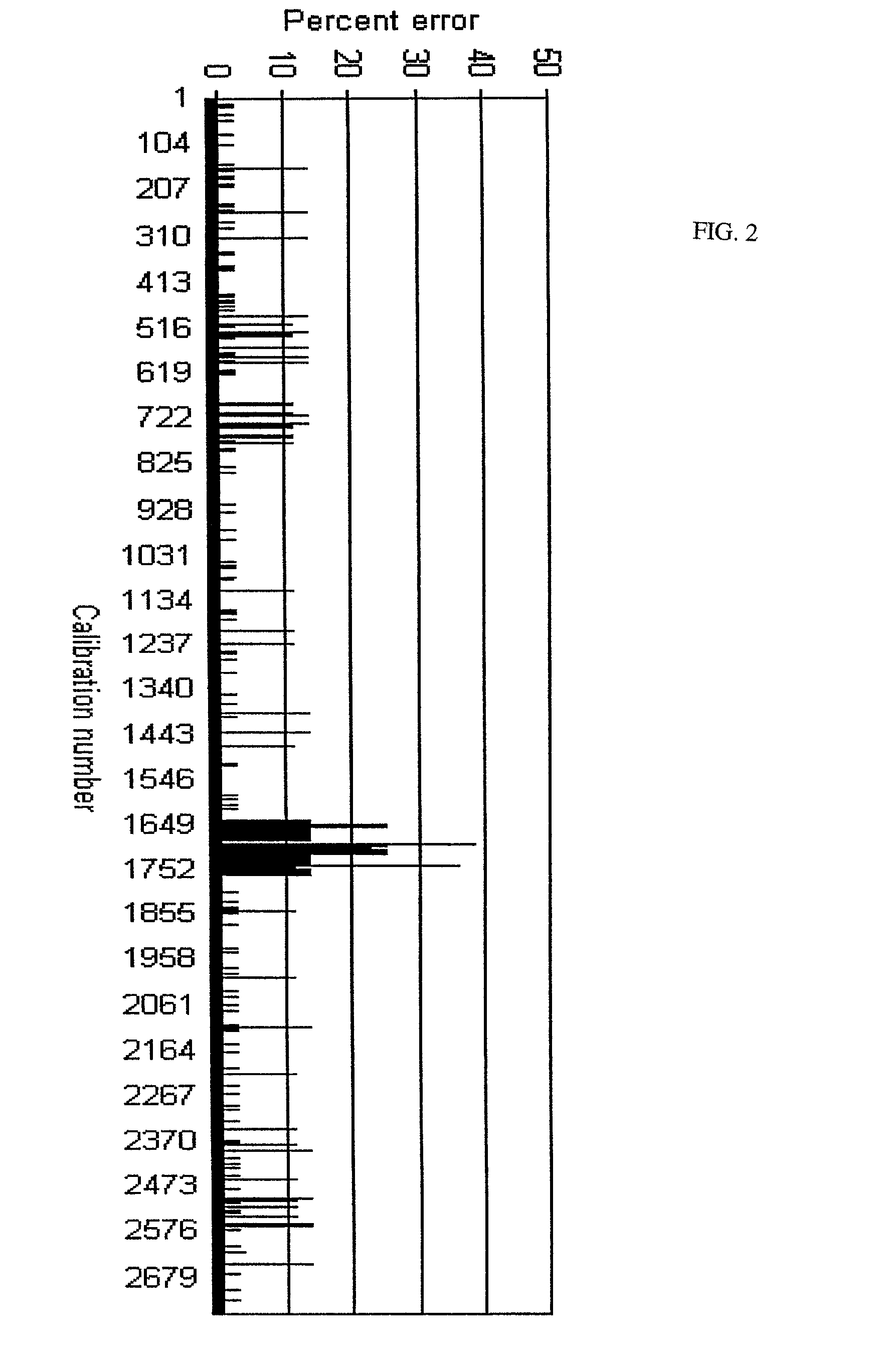
149 results about "Internet use" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
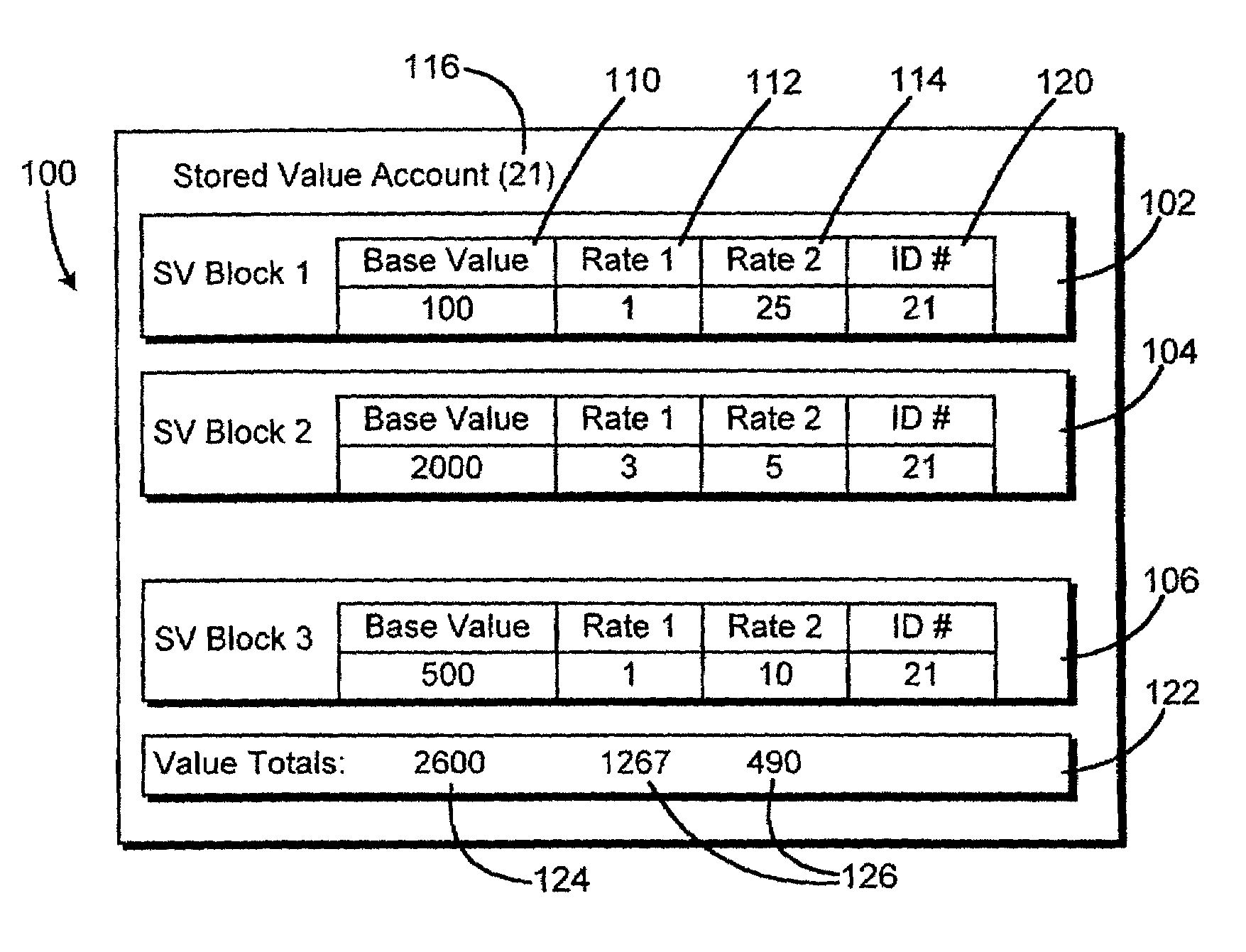
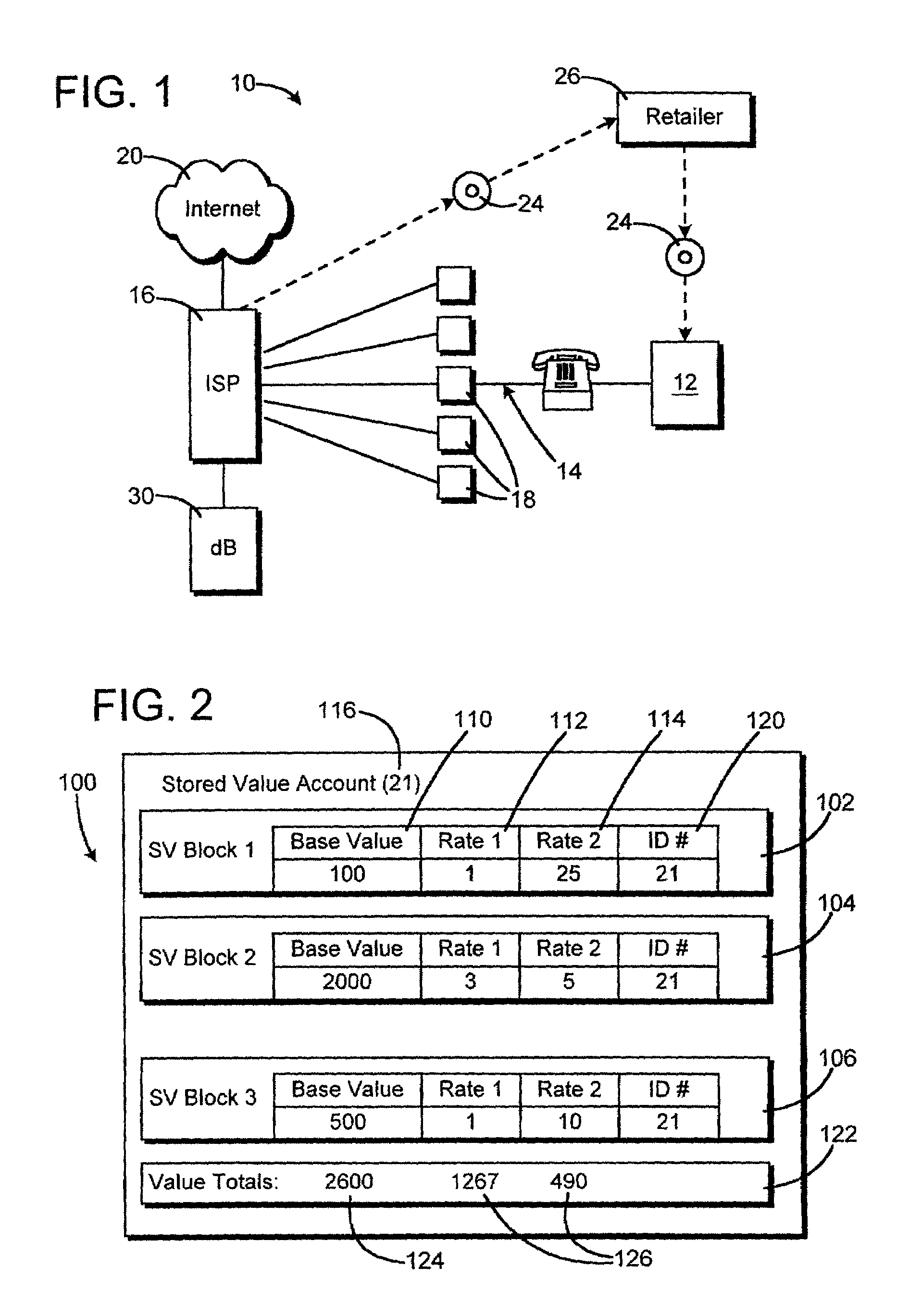
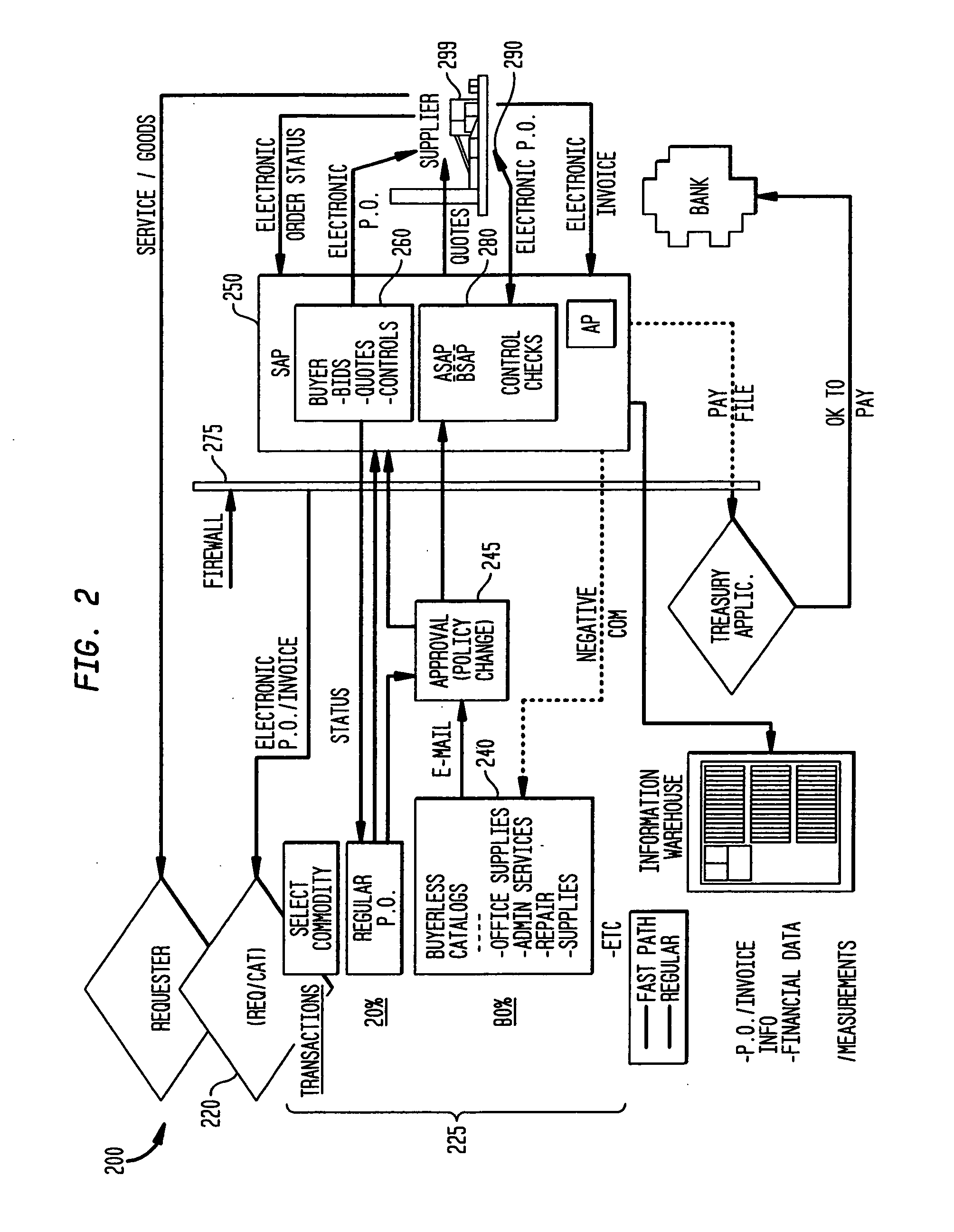
Method of accounting prepaid online internet service credit values
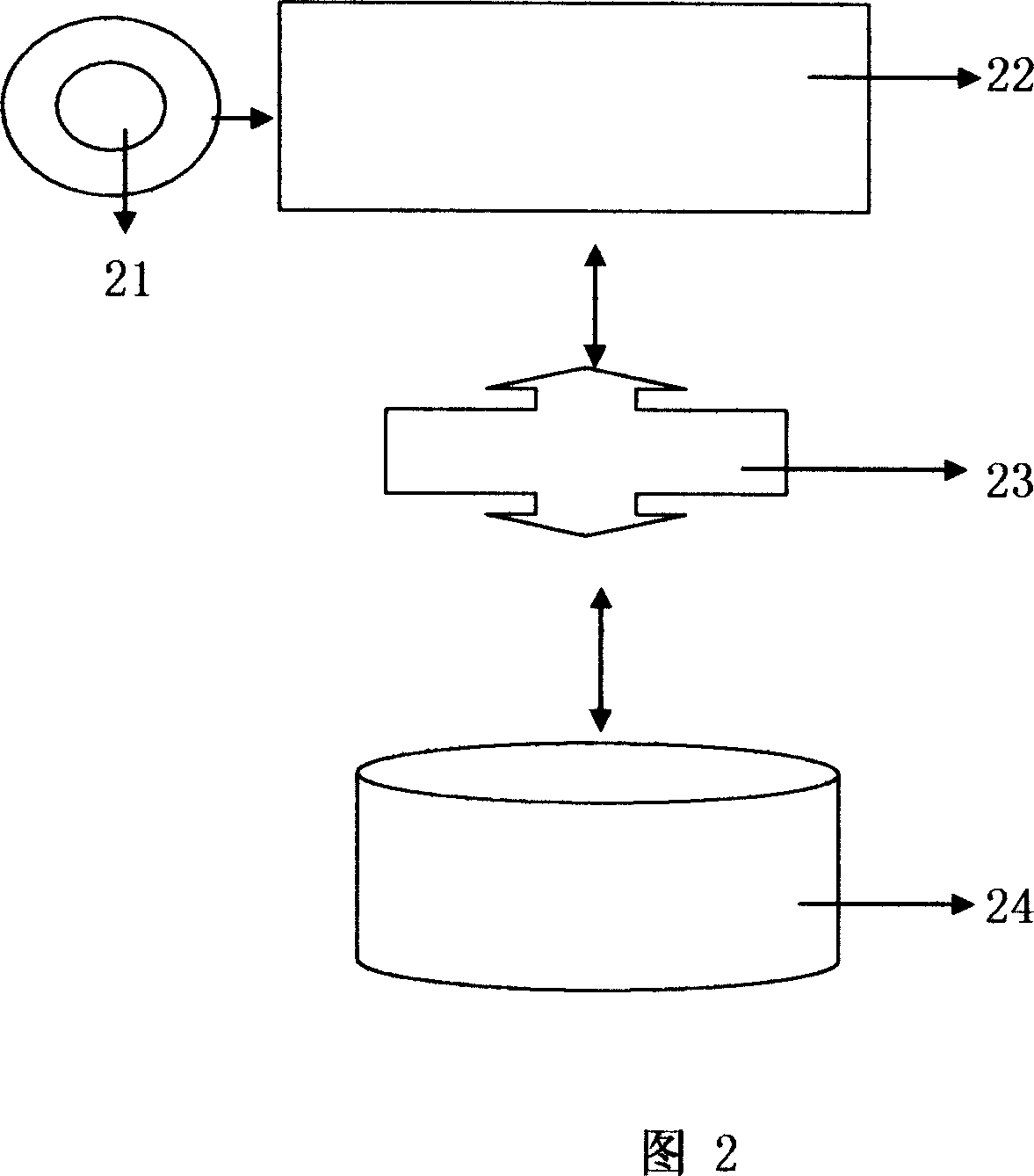
A method of accounting for online Internet usage credit includes establishing an account identifier in a database for a selected user. A number of credit value block records are associated in the database with the account identifier. Each credit value block has a stored credit value amount, and at least a second stored property indicator. In response to a measured amount of consumption of services by the user, at least one of the credit value blocks is debited by a debit amount based on the measured amount and the second stored property indicator. The stored property indicator may be a rate multiplier, or other factor indicating a different cost mode of online service, connection or usage.
Owner:QUALCOMM INC
System and method for processing and presenting internet usage information to facilitate user communications
A method for facilitating a chat session between a first user and second users visiting a first web site comprising receiving, from the first user, a first user ID; receiving, from the second user, a second user ID; providing, to the first user, at least an indication of the second user ID; receiving, from the first user, a request to open one of a public chat session, a semi-public chat session and a private chat session with the second user; transmitting, to the second user, an indication that the first user has requested a chat session; and receiving, from the second user, an acceptance to enter the chat session designated by the first user. The method also comprises receiving from the first user a query regarding other users in a co-branded community visiting the first web site and searching a database to determine a response to the query.
Owner:COMVERSE
Method and apparatus for conducting financial transactions
Method and apparatus for conducting financial transactions that allows traders, market makers, dealers, and liquidity providers to negotiate with multiple customers simultaneously, and receive and respond to transaction solicitations and amendment requests in real time. The invention, which may be accessed over an interconnected data communications network, such as the Internet, using a standard Web browser, automatically provides traders with up-to-date market rates as solicitations are received, and provides a graphical user interface with sorting and filtering capabilities to organize displays to show pending and completed transactions according to user preferences. Counterparty customers engaged in transactions with the traders and dealers using the system benefit by being able to negotiate with multiple providers simultaneously, and by receiving real-time, context-sensitive transaction status messages and notifications as the negotiations take place. An optional transaction status database records transaction events in real-time and provides transaction archiving and auditing capabilities superior to conventional manual transaction systems.
Owner:FX ALLIANCE
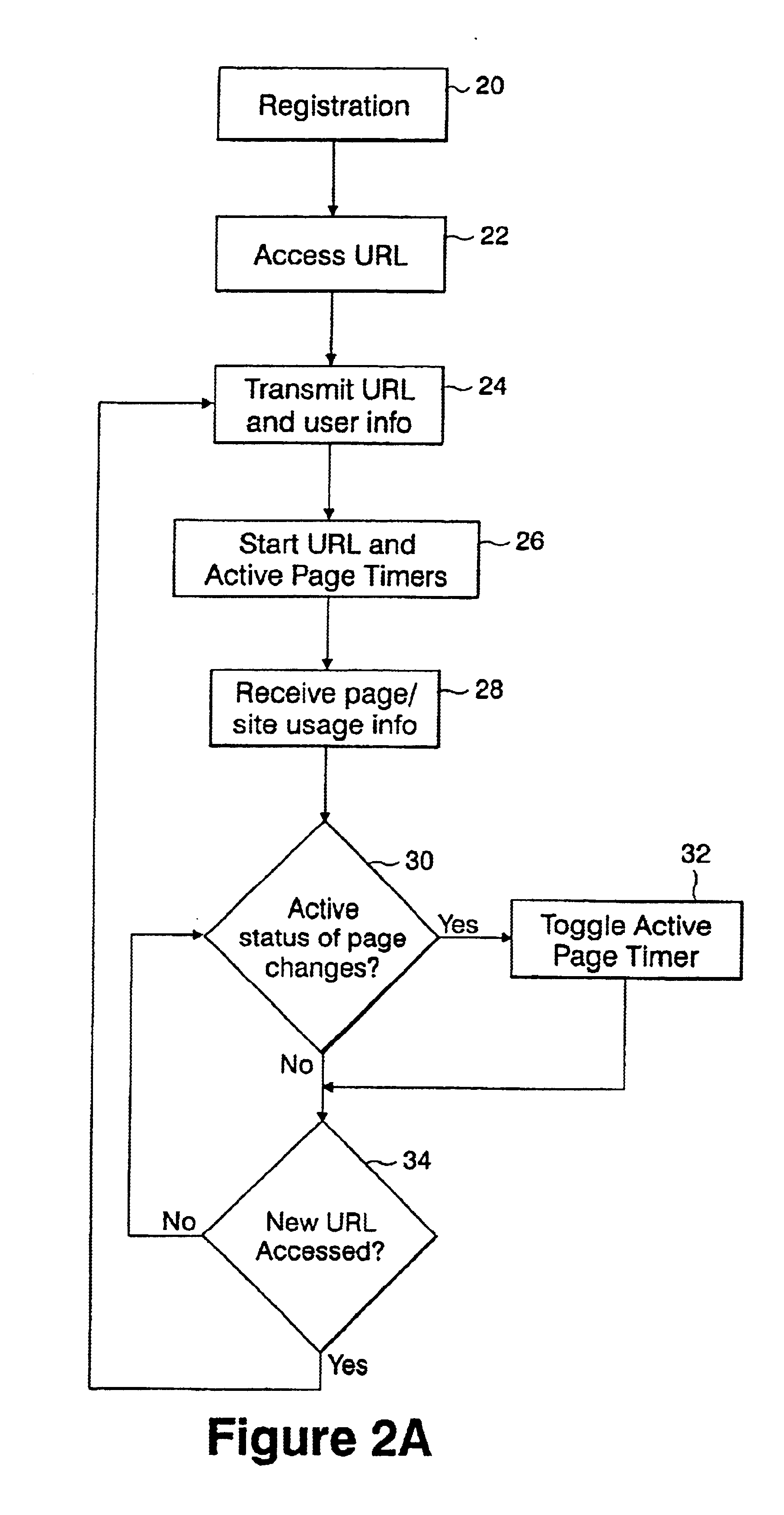
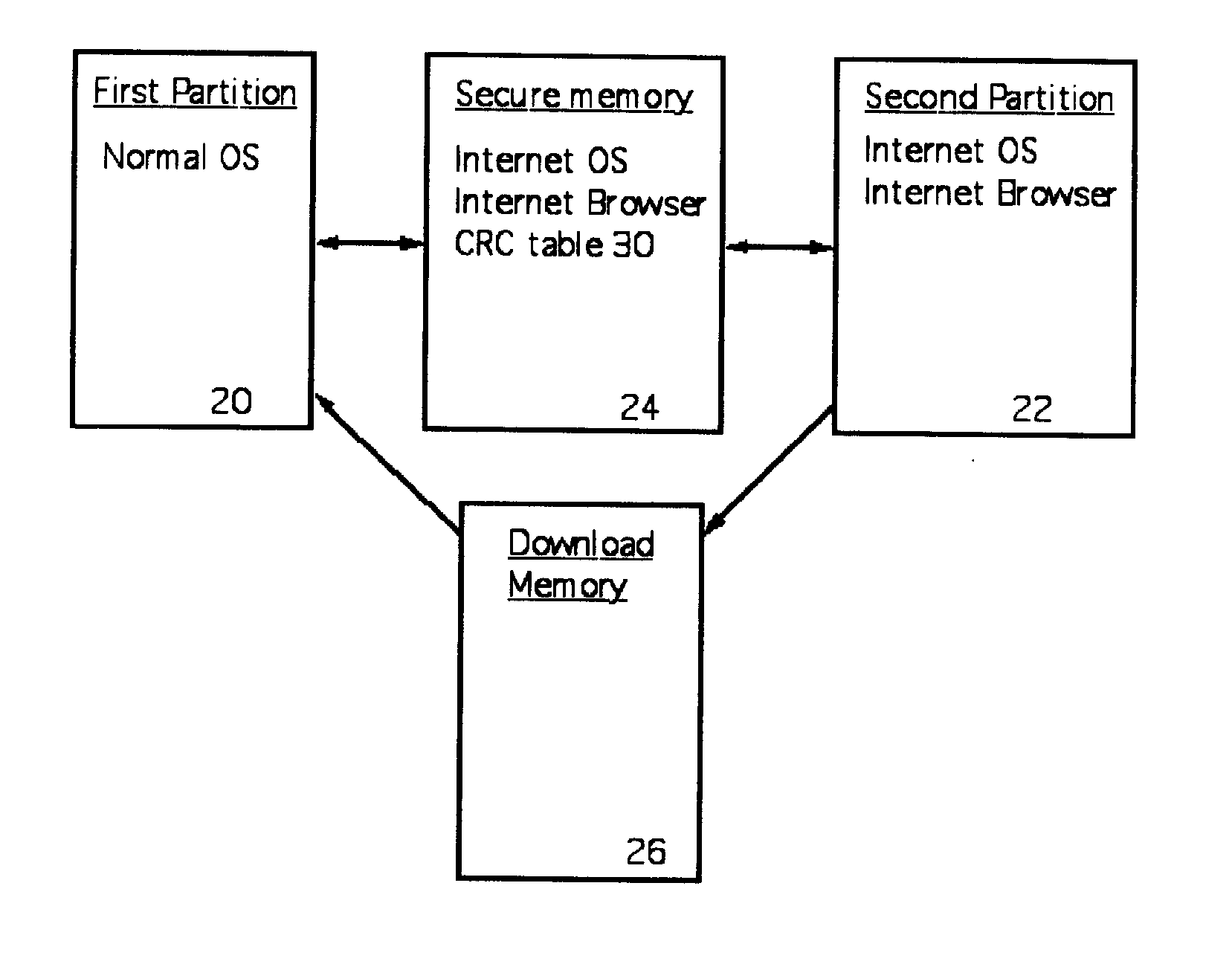
Method for preventing malicious software installation on an internet-connected computer
ActiveUS20070192854A1Prevents gaining accessAvoid accessMemory loss protectionDigital data processing detailsOperational systemTerm memory
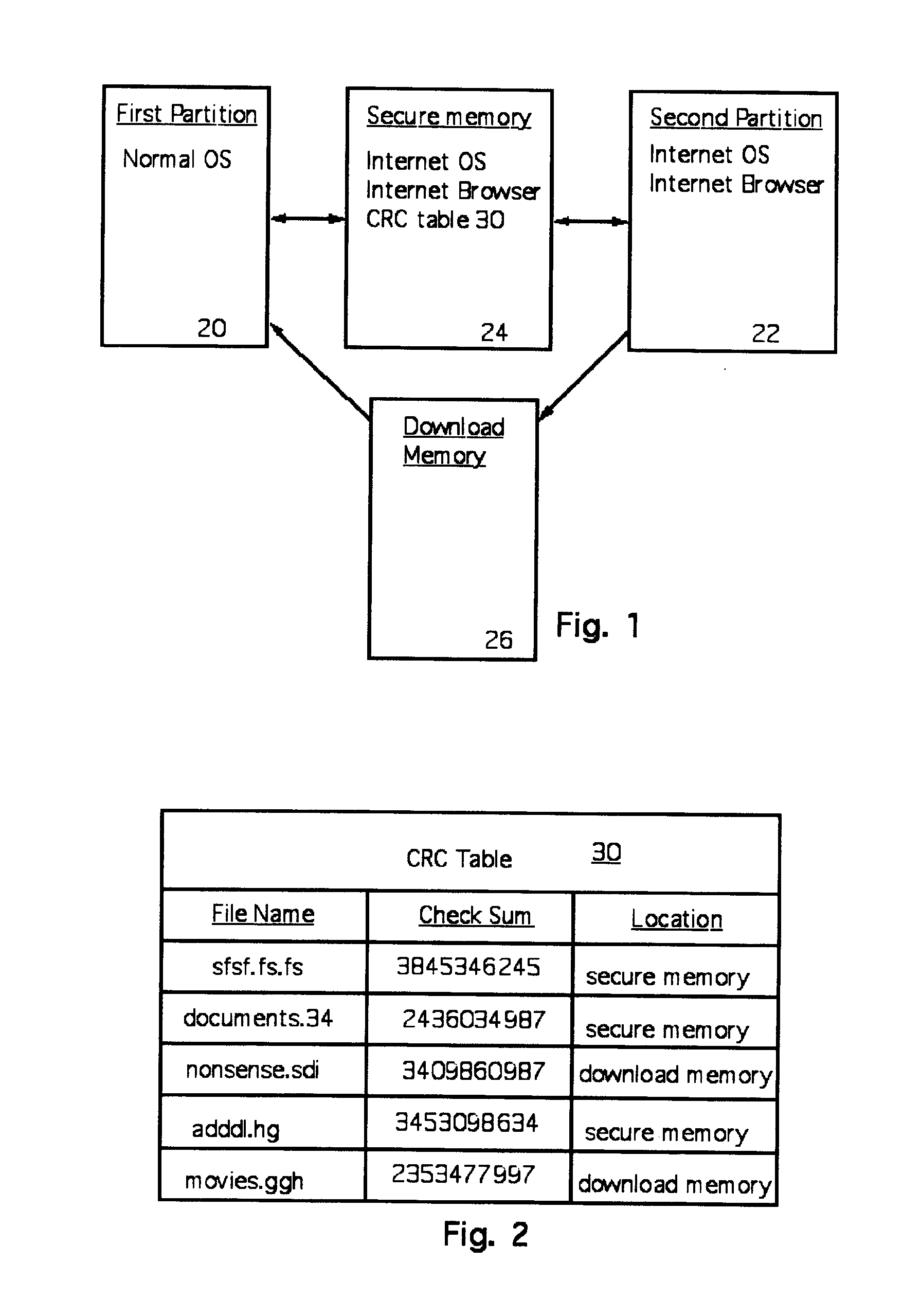
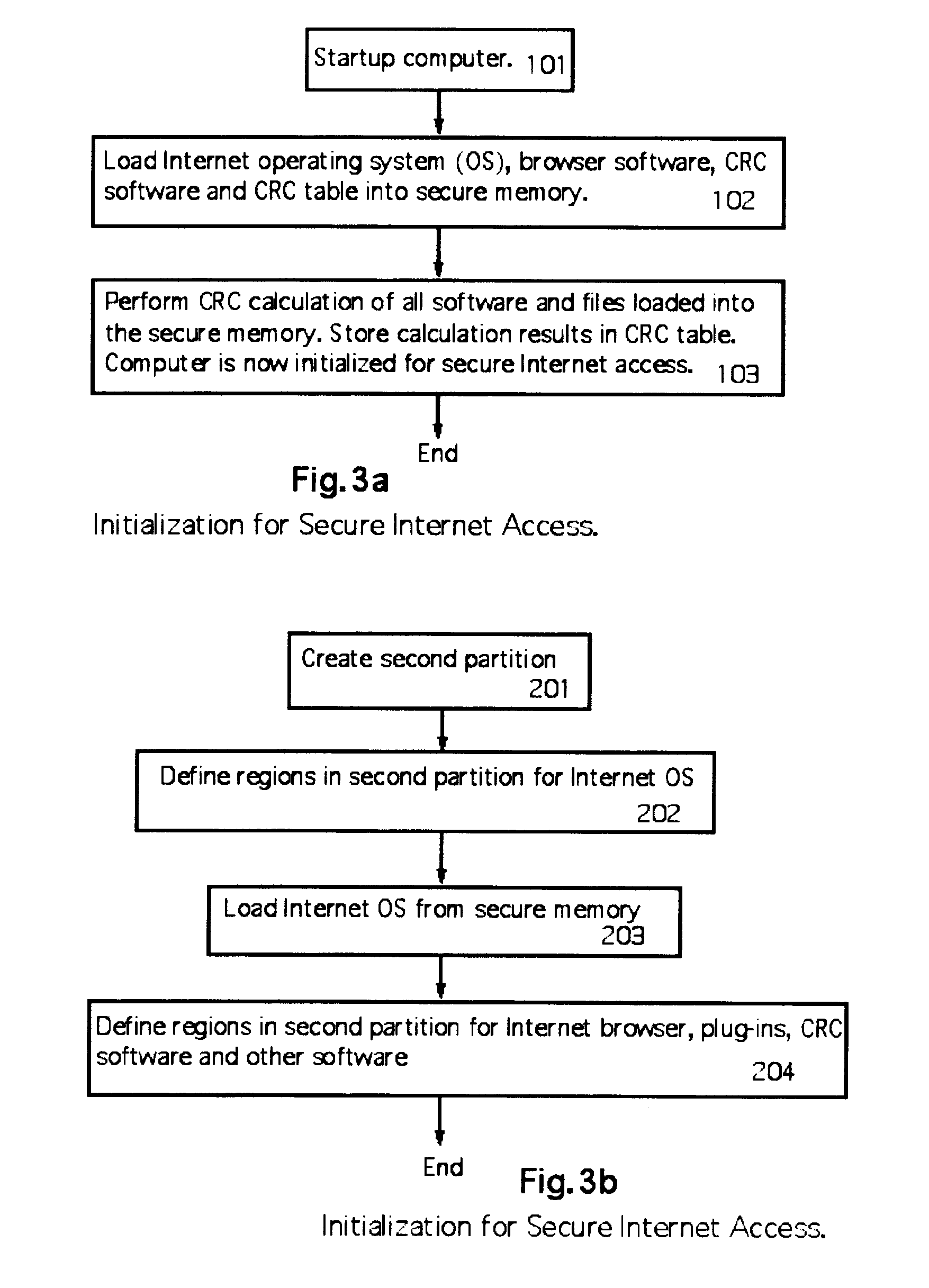
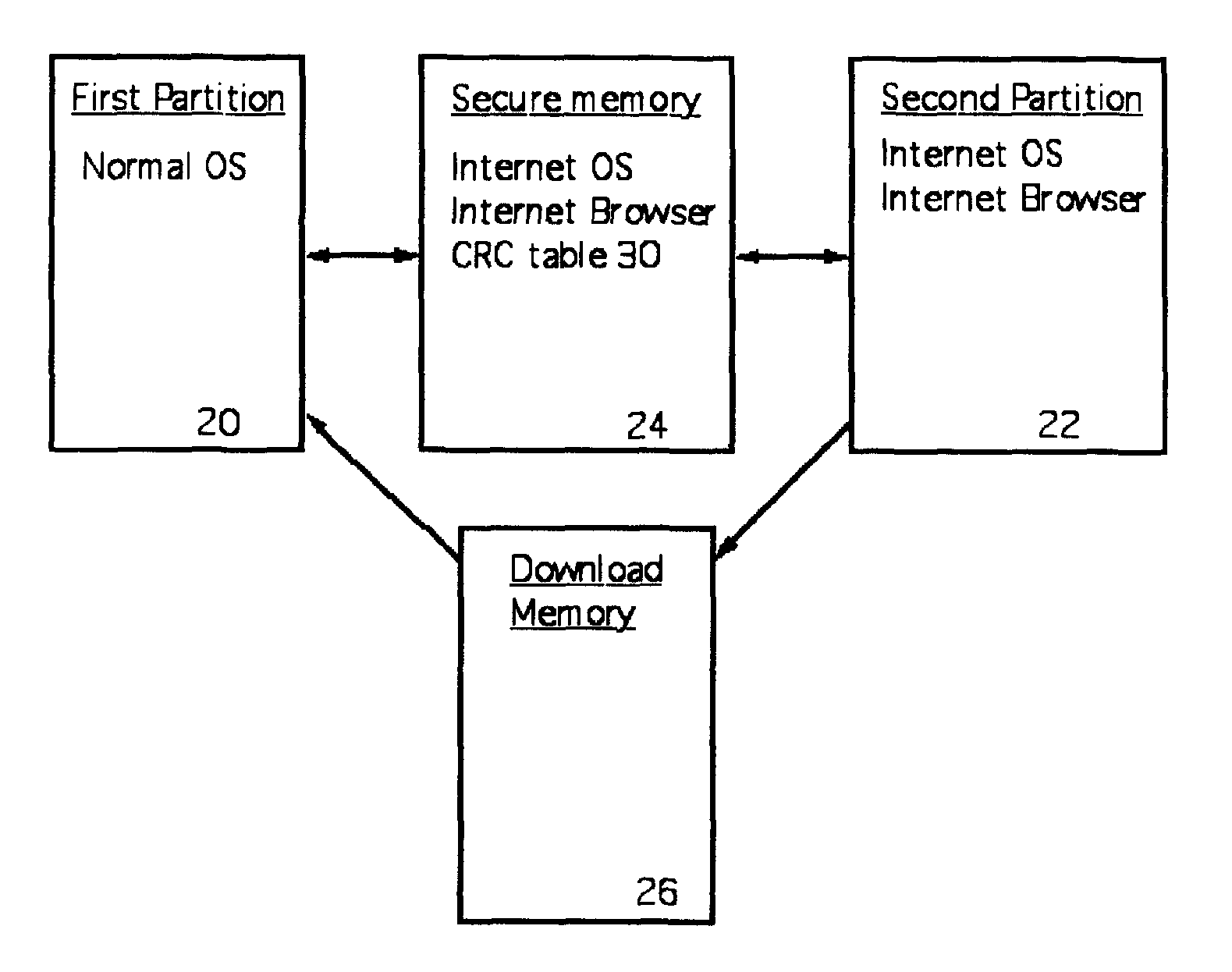
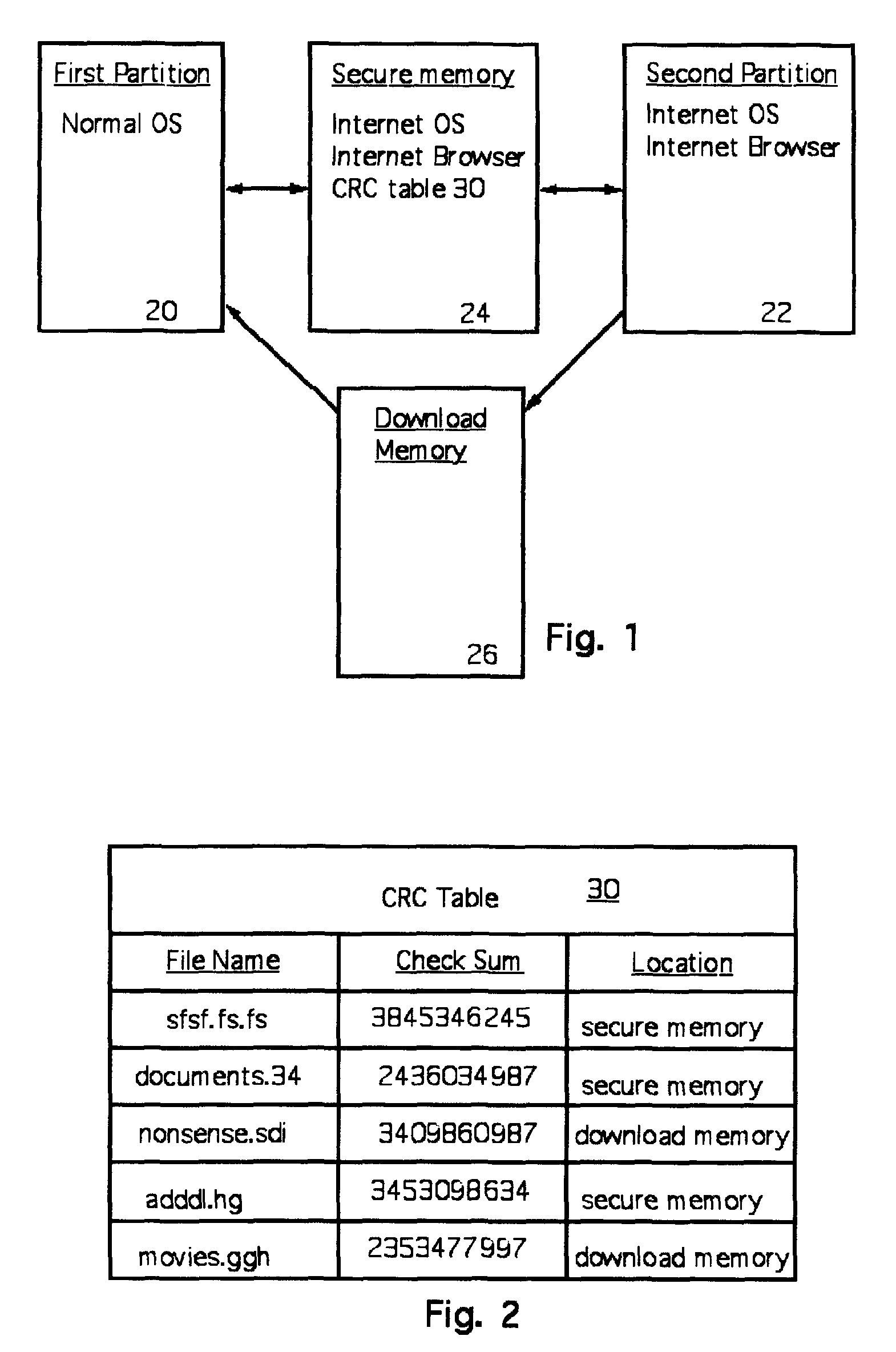
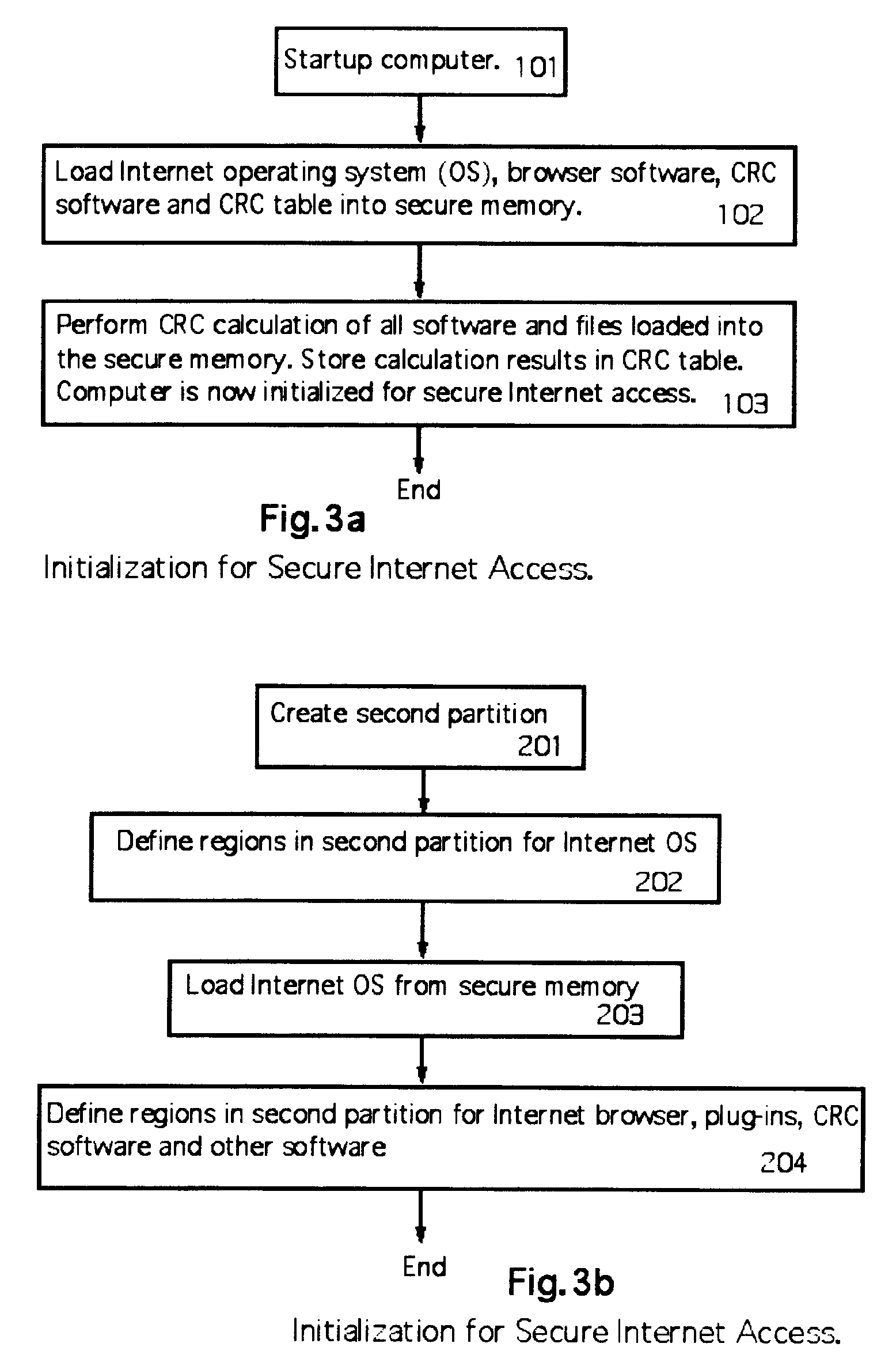
A computer random access memory is divided into first and second partitions. Each partition has its own operating system (OS). The first partition has a conventional OS and is designated for non-Internet use. The second partition is designated for secure Internet access, and has an OS specific for Internet usage. Software in the second partition cannot write or copy files in the second partition. The size of the second partition is fixed and unchangeable while said second partition is open. Each software application in the second partition is allocated a memory region that cannot be changed, thereby preventing memory overflow attacks. A secure memory is designated for temporary storage of software used in the second partition. Cyclic redundancy check (CRC) values are calculated for all files in the secure memory. To detect unauthorized file changes, CRC values are calculated for all files used in the second partition, and checked against values stored in the secure memory. The second partition can write only to a secure memory using a security arrangement such as password protection or a download memory separate from the first partition to allow files stored in the download memory to be examined by scanning and testing from the first partition prior to being stored elsewhere in the computer.
Owner:KYNDRYL INC
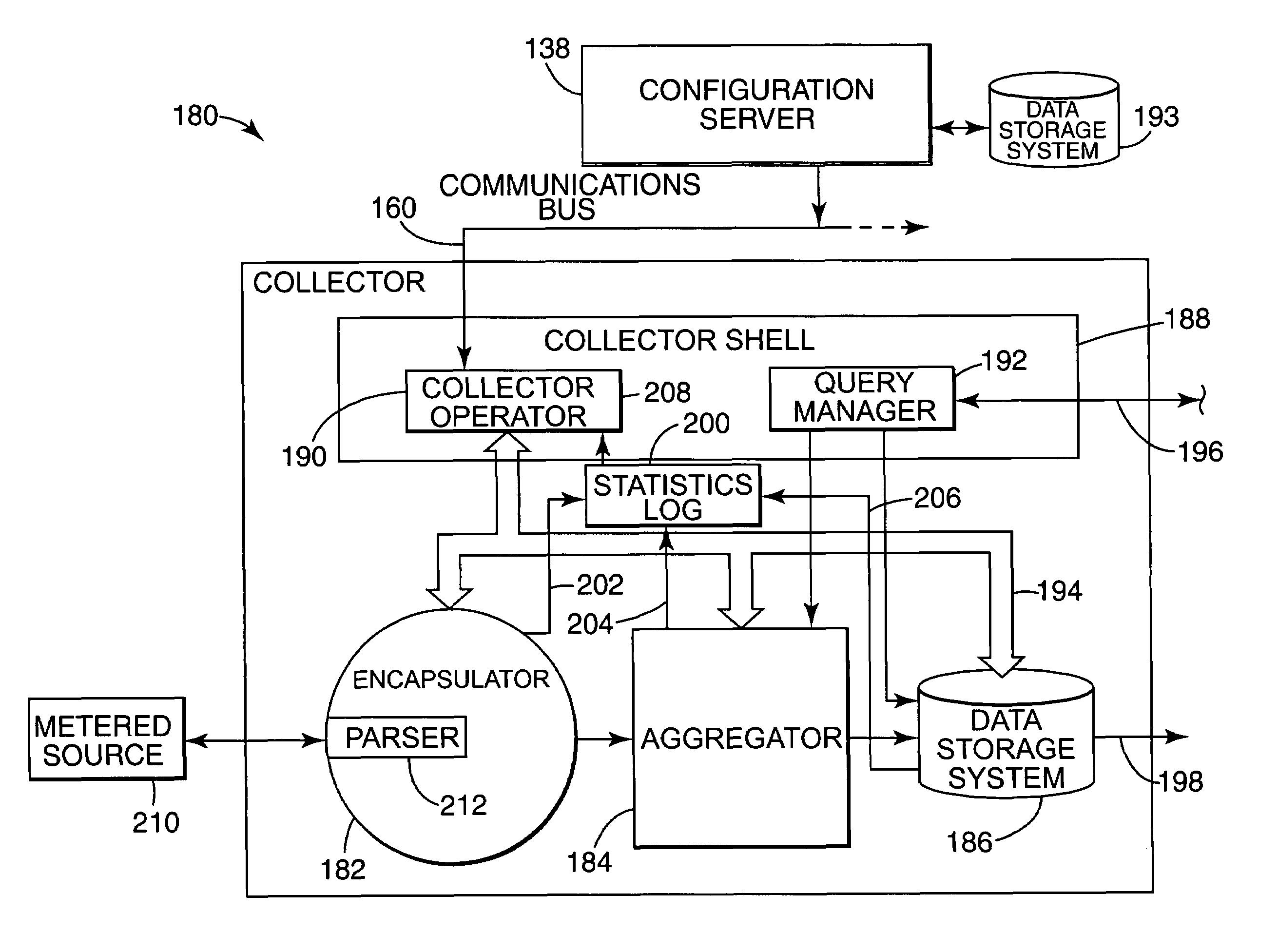
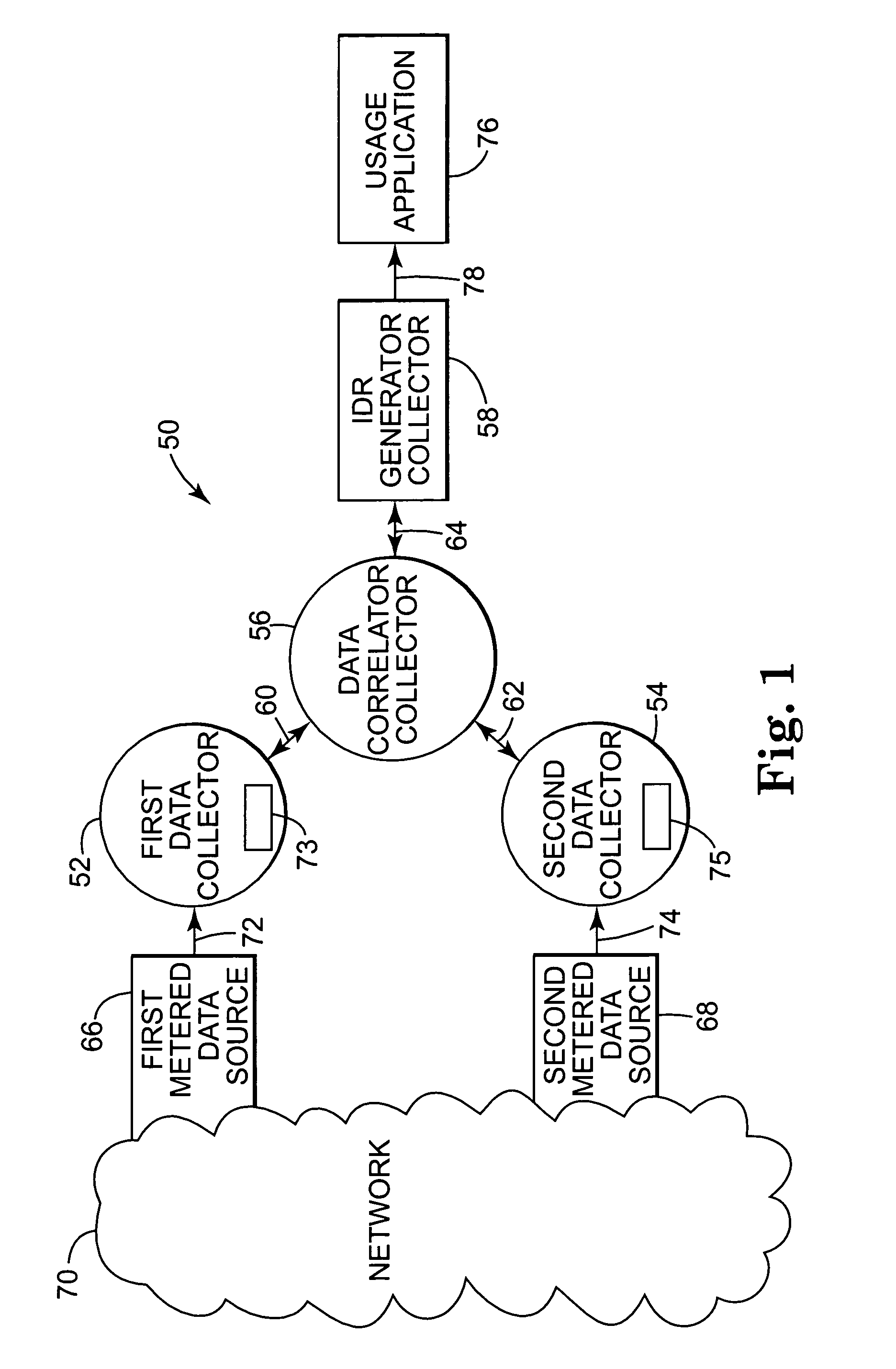
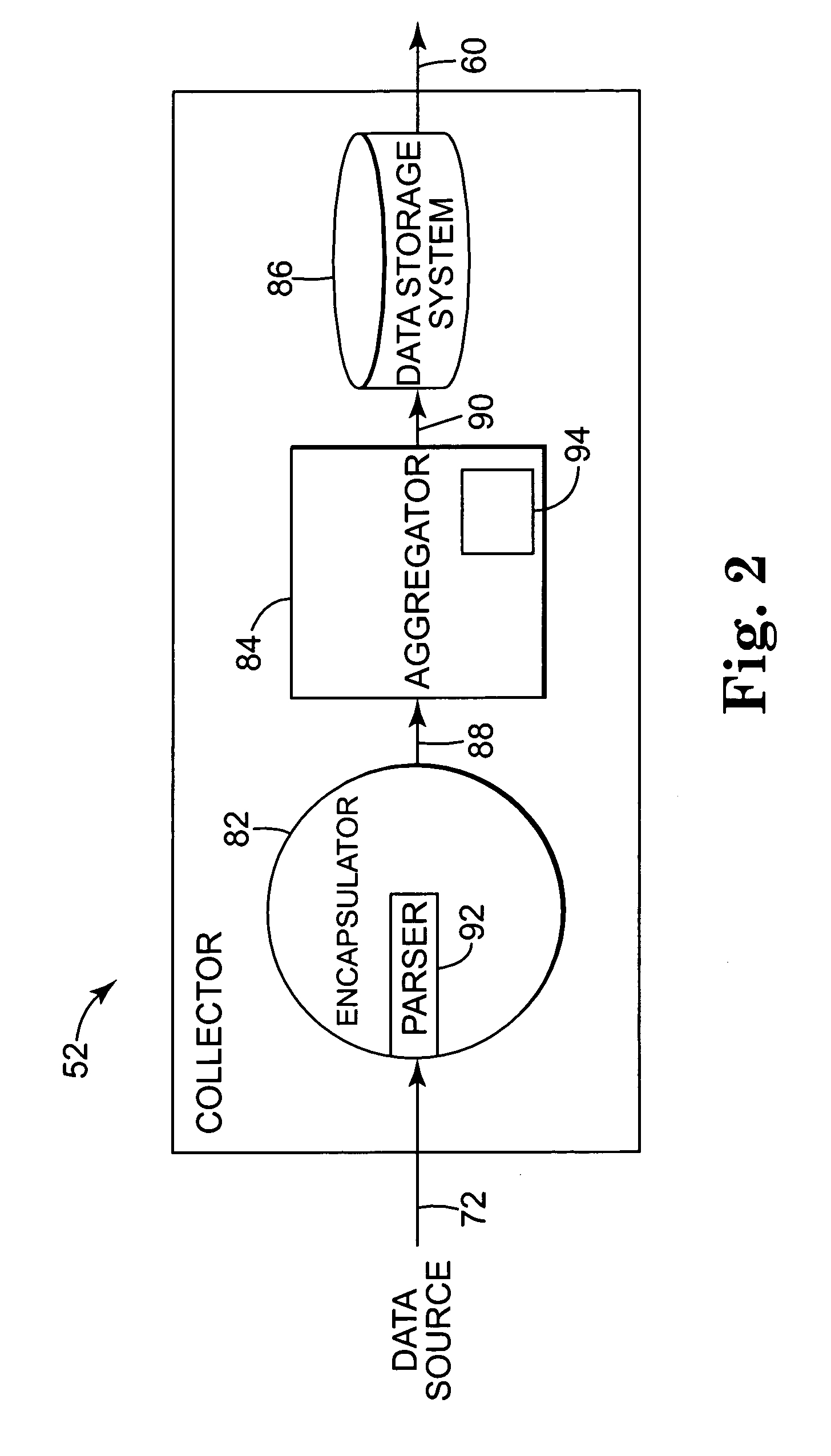
Internet usage data recording system and method with configurable data collector system
InactiveUS7024468B1Avoid data trafficAvoid less flexibilityDigital computer detailsTransmissionData recordingData store
An internet usage data recording system and method is described. In one embodiment, the present invention provides a network usage recording system. The network usage recording system includes a configurable collector. The collector includes an encapsulator for reading a plurality of network data records from a network data source and converting the network data records to a plurality of normalized metered events. An aggregator is provided for processing the normalized metered events to create aggregated normalized metered events. A data storage system is provided, wherein the aggregator periodically stores the aggregated normalized metered events in the data storage system.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
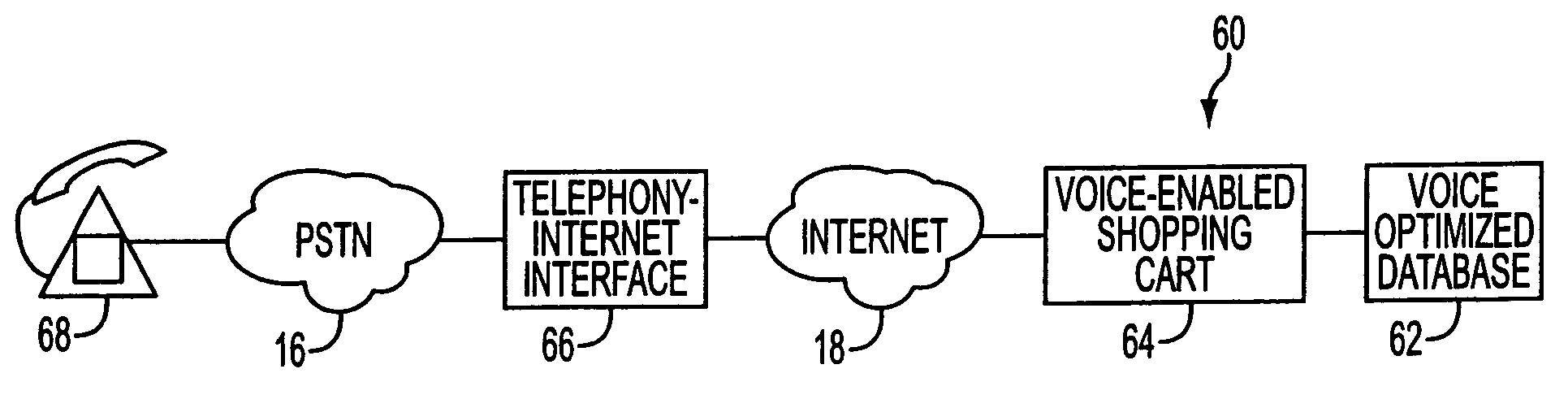
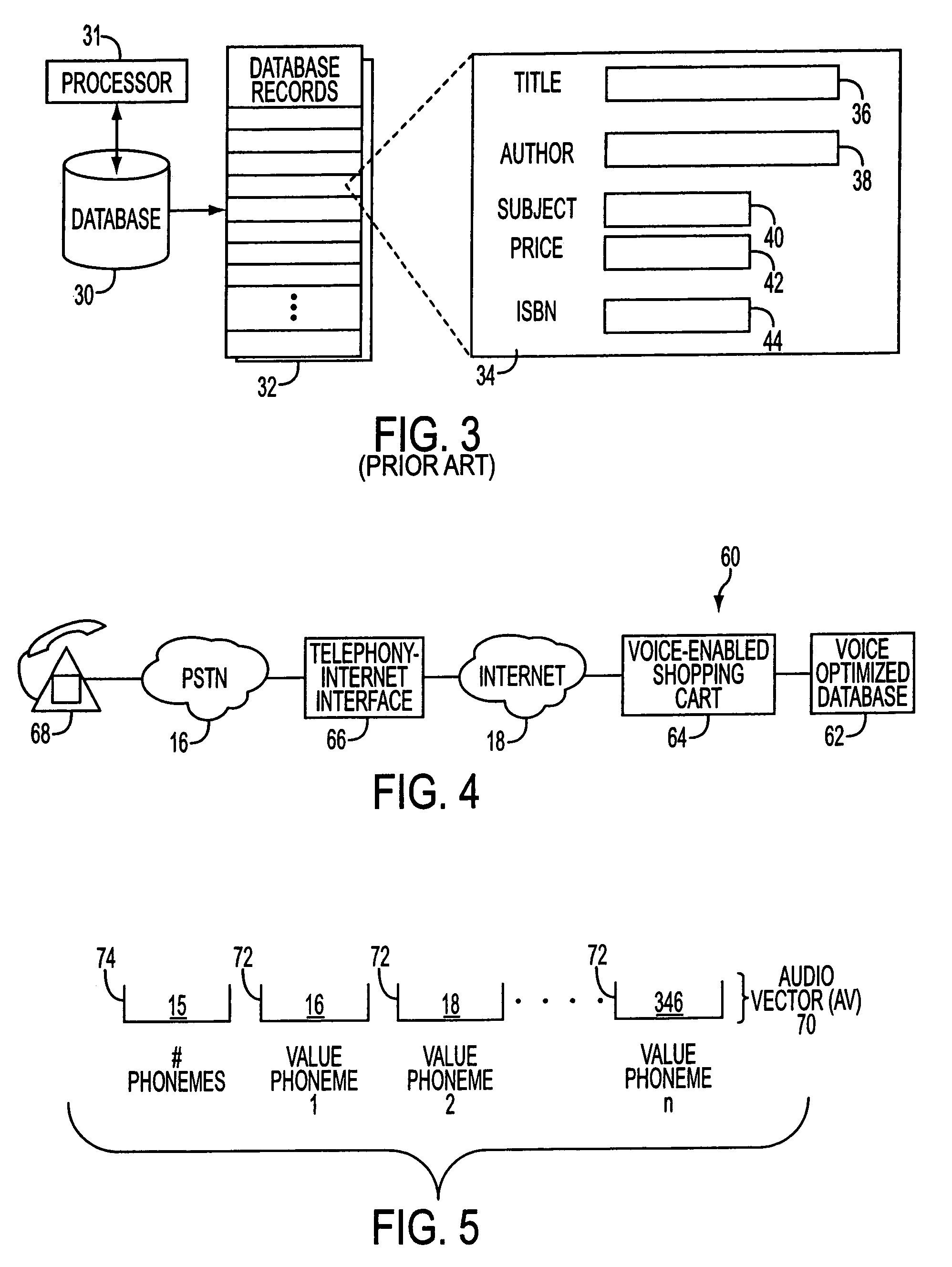
Telephony-data application interface apparatus and method for multi-modal access to data applications
InactiveUS6941273B1Overcome deficienciesTelephonic communicationBuying/selling/leasing transactionsCredit cardTTEthernet
A voice-enabled system for online shopping provides a voice and telephony interface, as well a text and graphic interface, for shopping over the Internet using a browser or a telephone. The system allows customers to access an online shop, search for desired database items, select items, and finally pay for selected items using a credit card, over a phone line or the Internet. A telephony-Internet interface converts spoken queries into electronic commands for transmission to an online shop or database. Markup language-type pages transmitted to callers from the online-shop or database are parsed to extract selected information. The selected information is then reported to the callers via audio messaging.
Owner:LOGIC TREE
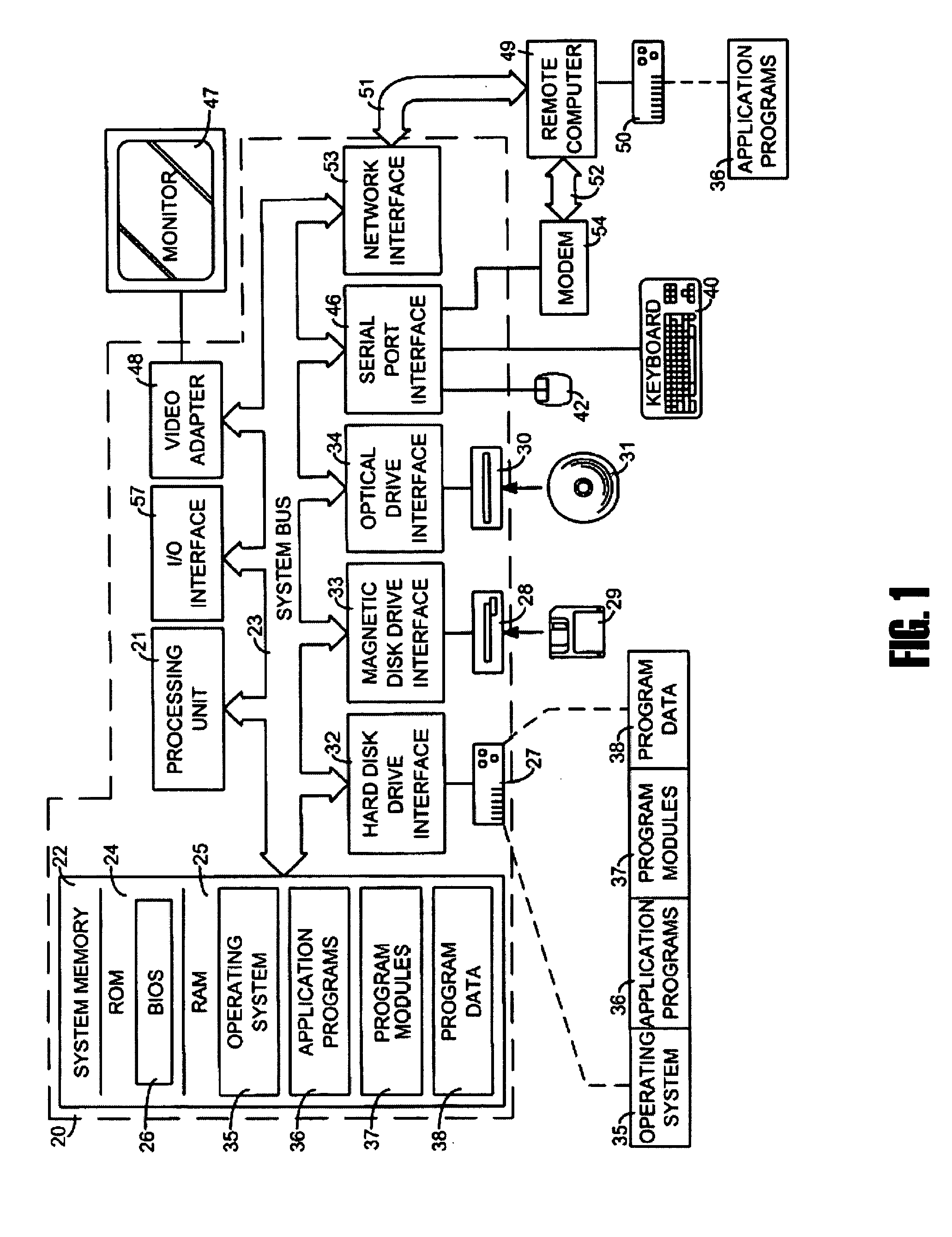
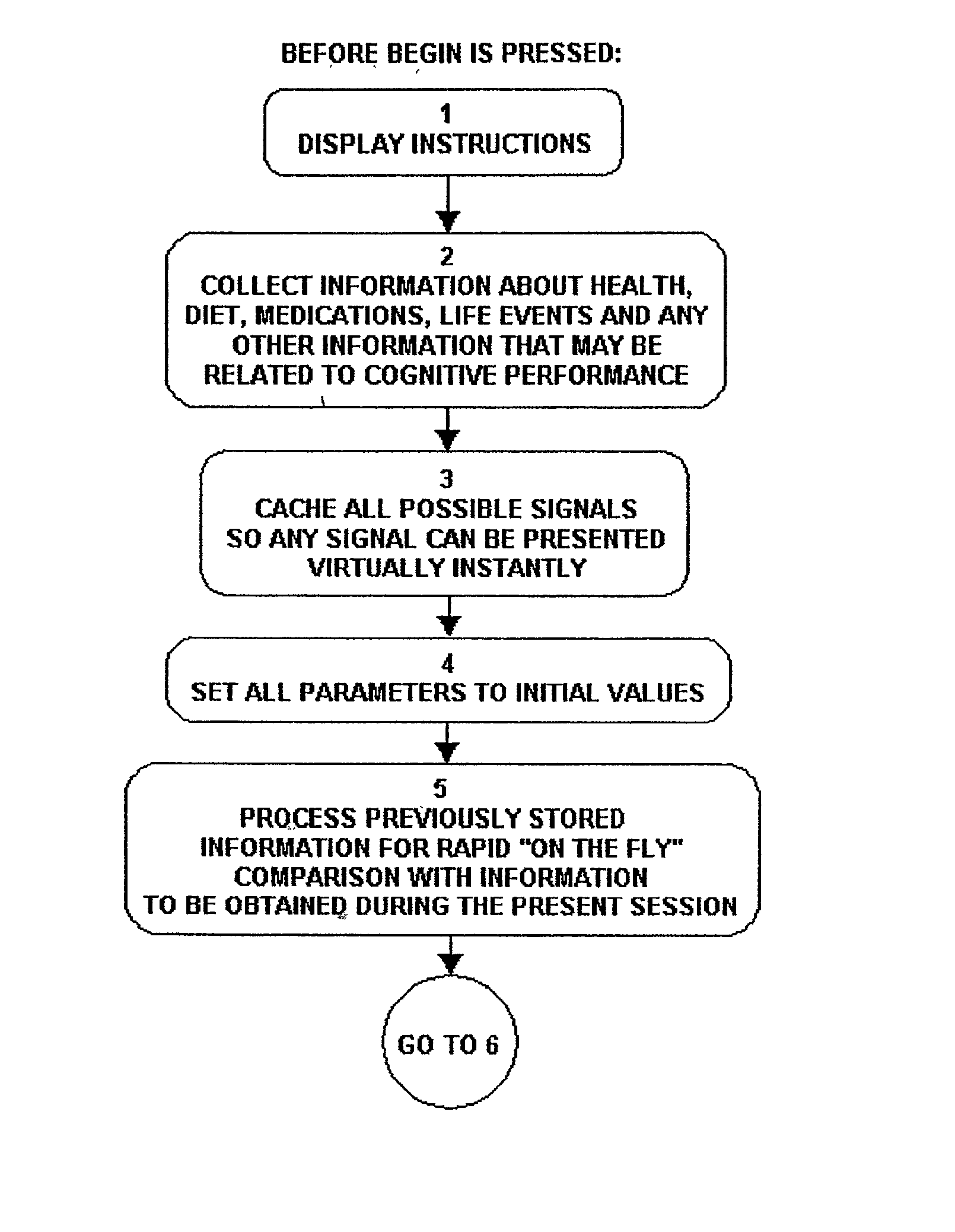
High-precision cognitive performance test battery suitable for internet and non-internet use
InactiveUS6712615B2Performance data is accurateGood for healthEducational modelsElectrical appliancesComputer networkTest battery
A system and method for internet-based cognitive performance measurement is provided. Furthermore, a method is provided whereby improvements in statistical accuracy is obtained.
Owner:MARTIN ROLF JOHN
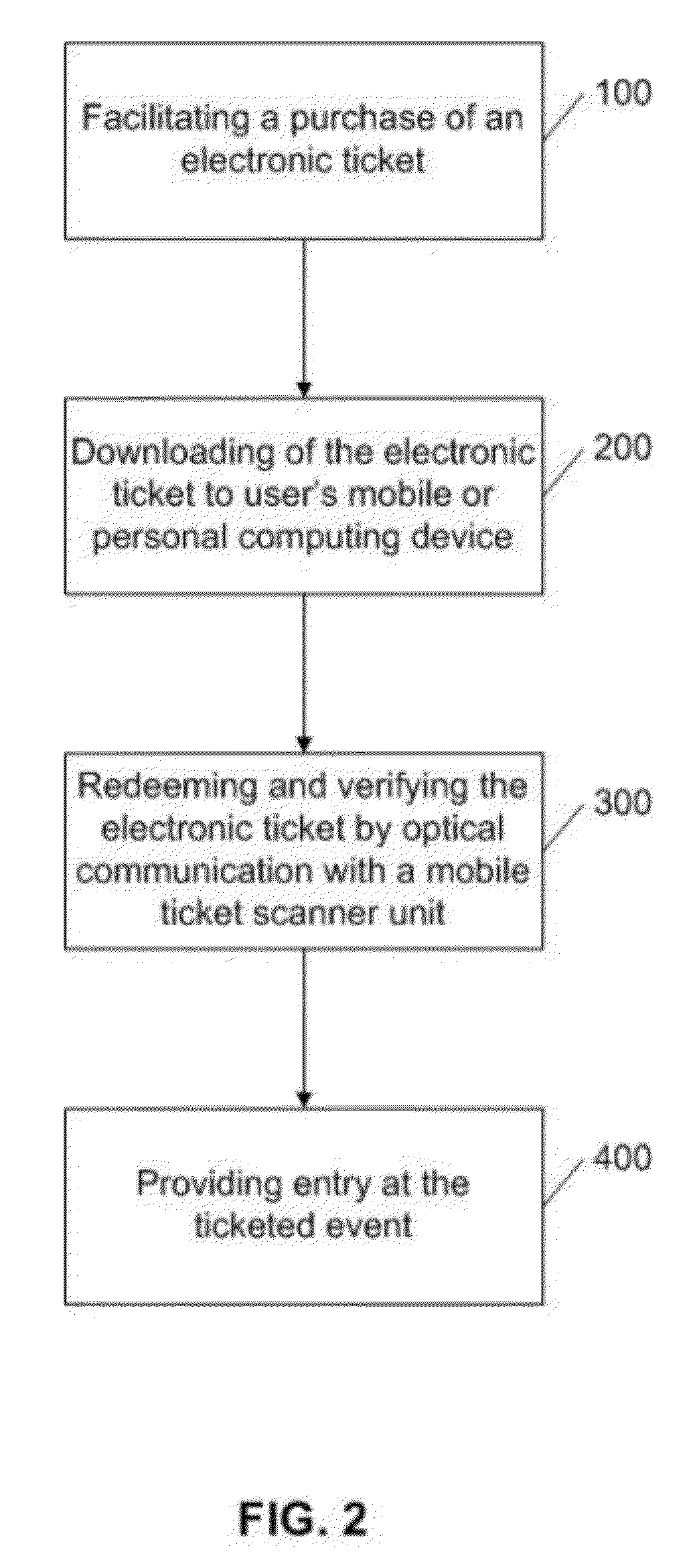
Secure Electronic Ticketing using Mobile Communication Devices over the Internet
InactiveUS20120221474A1Improve of creationImprove securityComputer security arrangementsBuying/selling/leasing transactionsInternet communicationDisplay device
The invention consists of a method and system for secure mobile ticketing through the use of a mobile device with display output and data input capabilities. The system utilizes a cryptographic security string appended to a URL and embedded in a 2D barcode to securely create an electronic ticket which is displayed on the mobile device display for redemption, redeem the displayed electronic ticket by means of optical scanning, and optionally register and authenticate a ticket scanning unit. The system utilizes real-time internet communication with a remote server for ticket distribution, redemption and ticket scanning unit registration and authentication to restrict unauthorized creation or redemption of electronic tickets and to reduce queuing.
Owner:SKYCORE
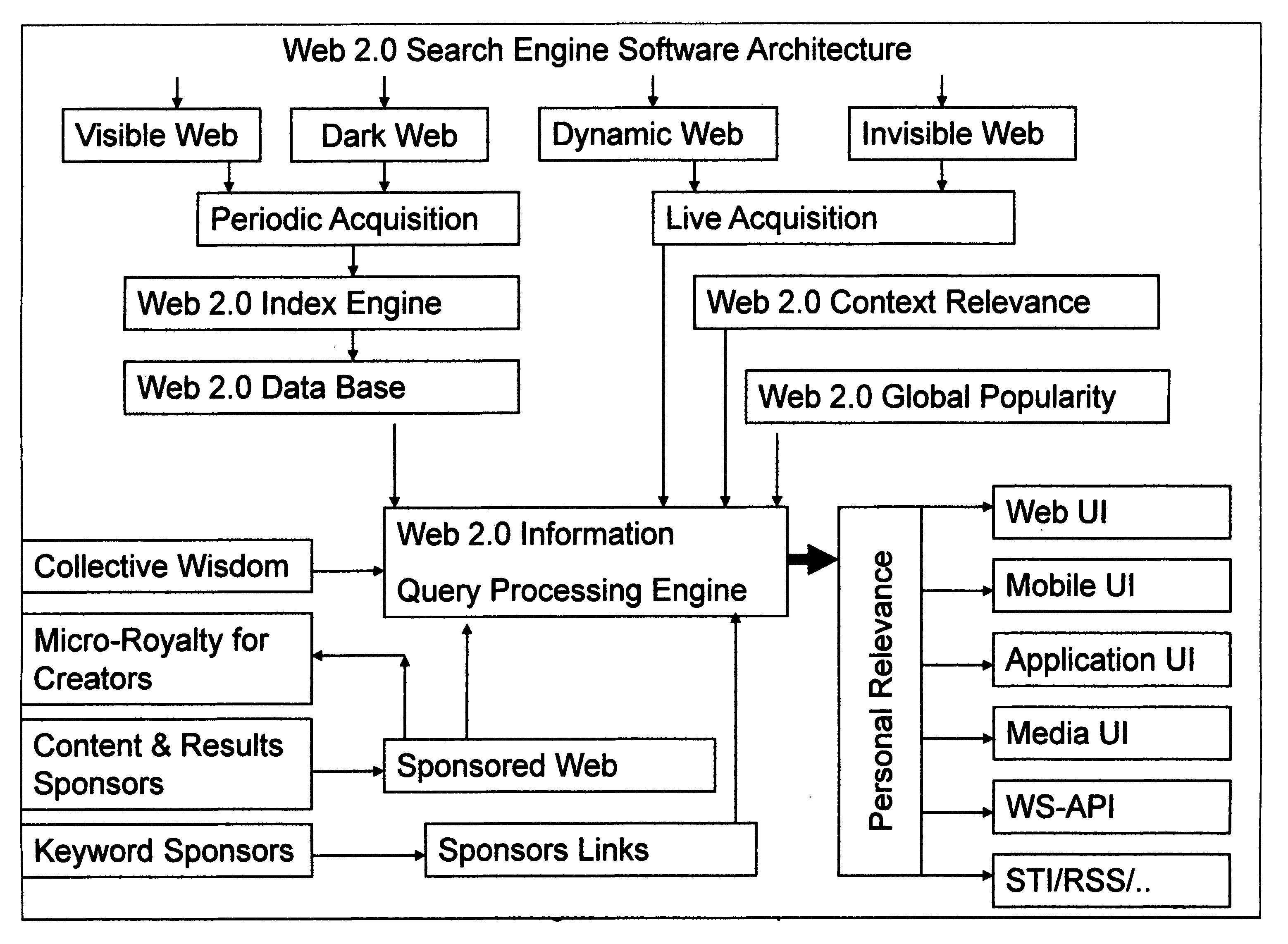
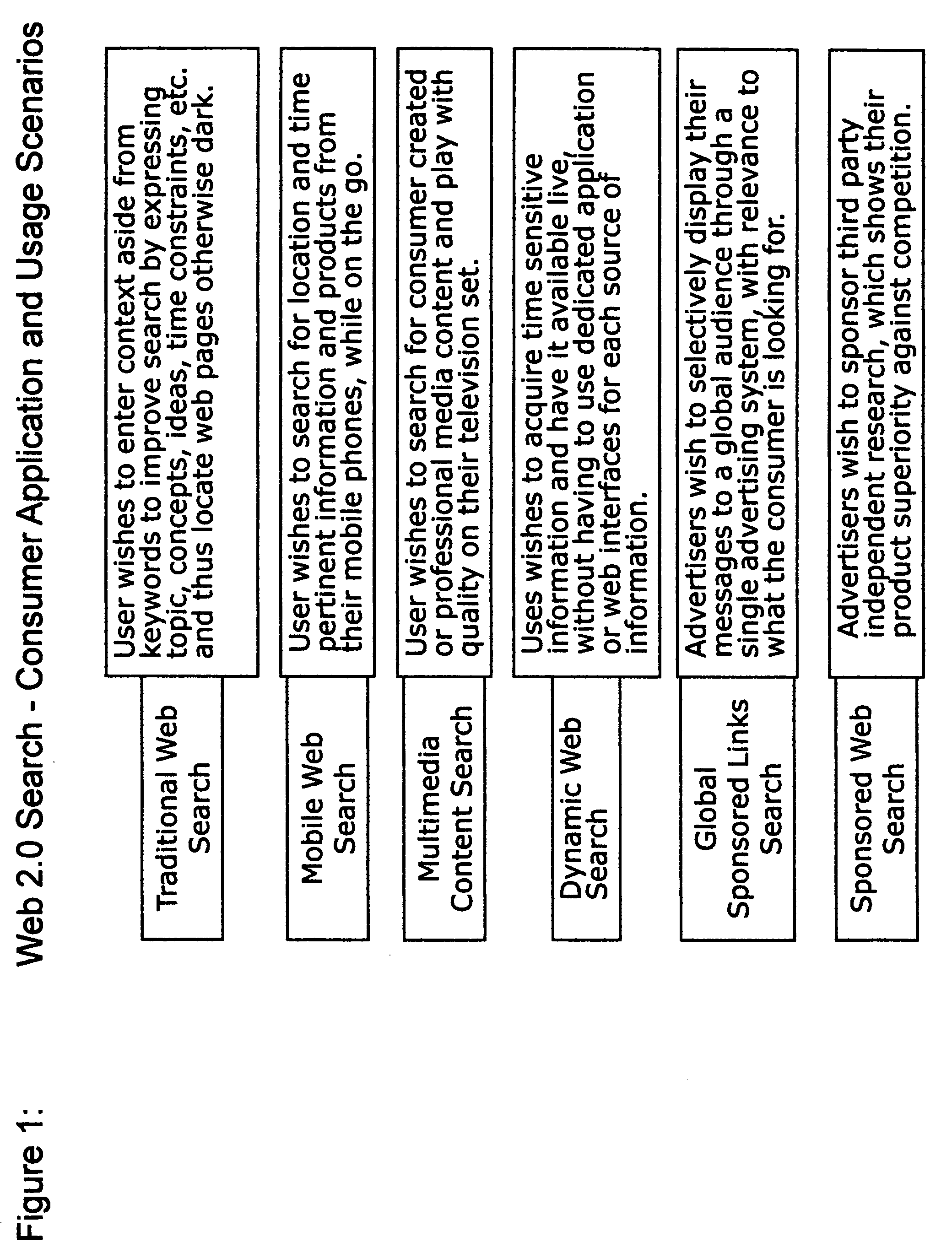
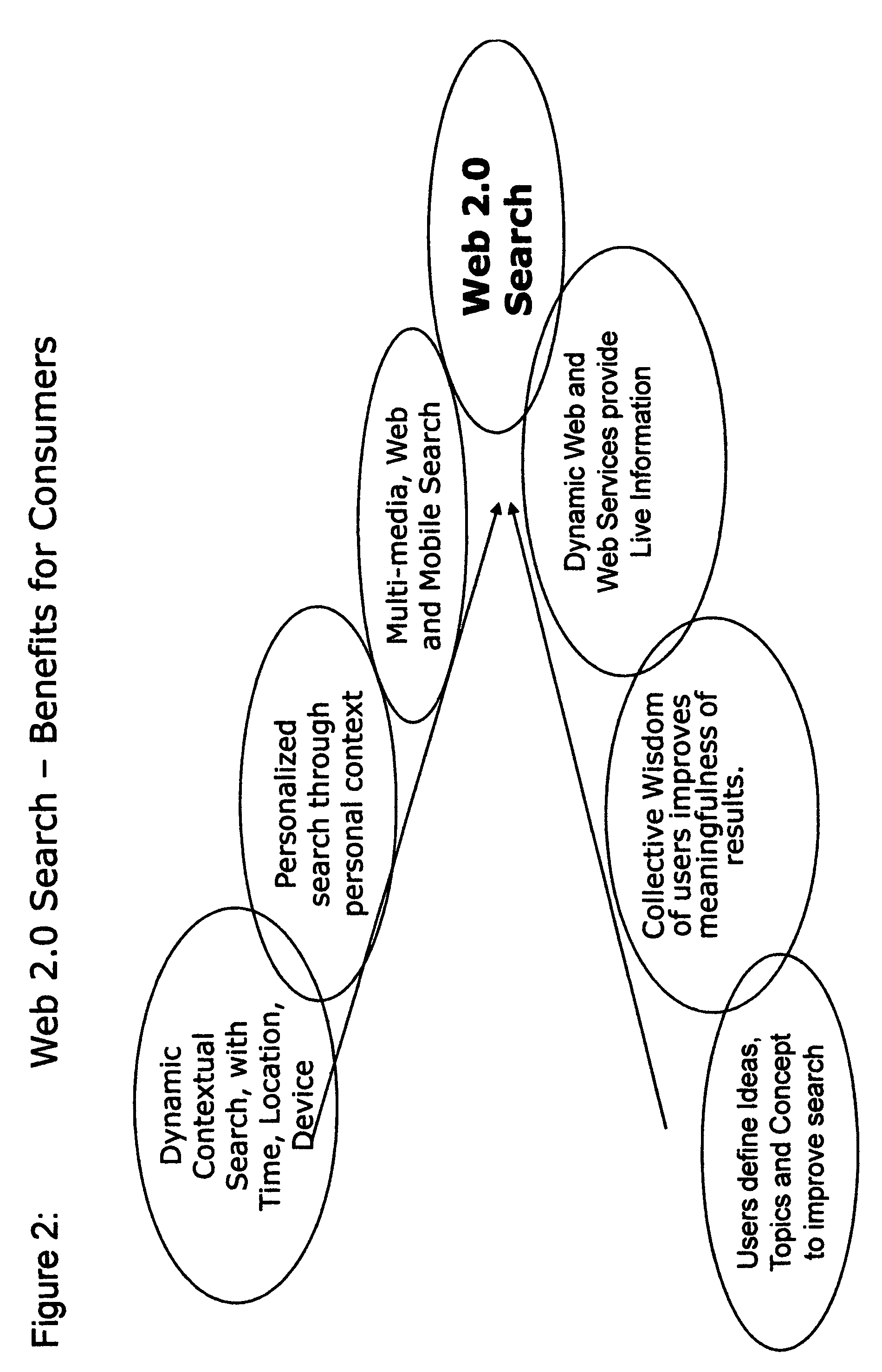
"Web 2.0 information search and presentation" with "consumer == author" and "dynamic Information relevance" models delivered to "mobile and web consumers".
InactiveUS20080281794A1Increase valueOffice automationWebsite content managementWeb serviceMobile content
Moving forward from current generation of search engines, originally designed for web 1.0, an entirely new comprehensive information search system is presented for searching and presenting of information in the Web 2.0, and other emerging new models of the global Internet using new and emerging sources of static and dynamic information, including but not limited to professionally created web pages, consumer created content, increasingly dynamic yet invisible web or web services based web, unconnected yet relevant dark web, mobile content web, social networked web and other emerging models of content publication, with access using mobile and fixed wireless and wire-line networked computing, communication and entertainment devices, user agents and application agents, and corresponding new business and delivery models for consumer and business users worldwide through sponsored web business model, content advertising business models, keyword advertising models, multi-media advertising models or pay per search, pre-paid and service business models.
Owner:MATHUR ANUP K
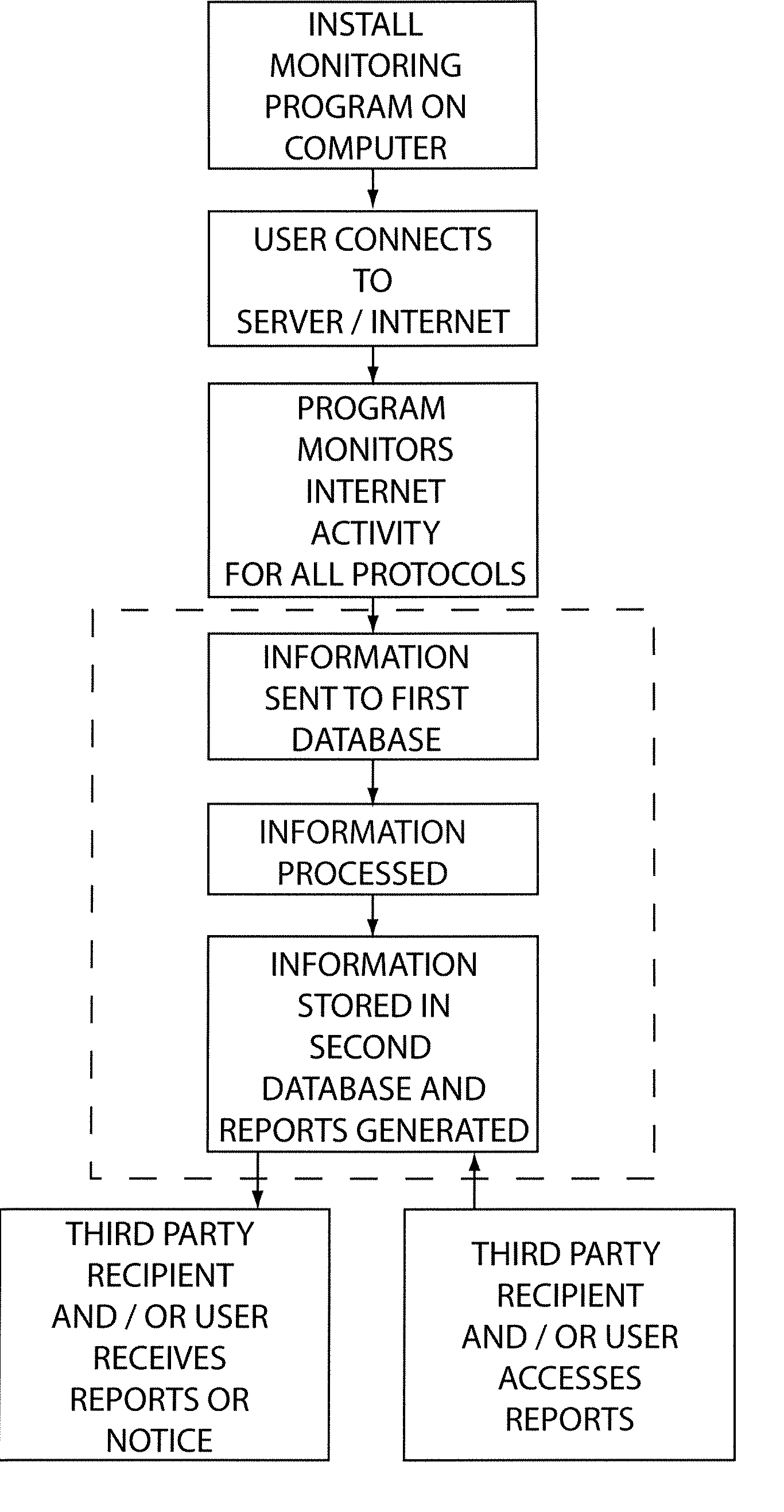
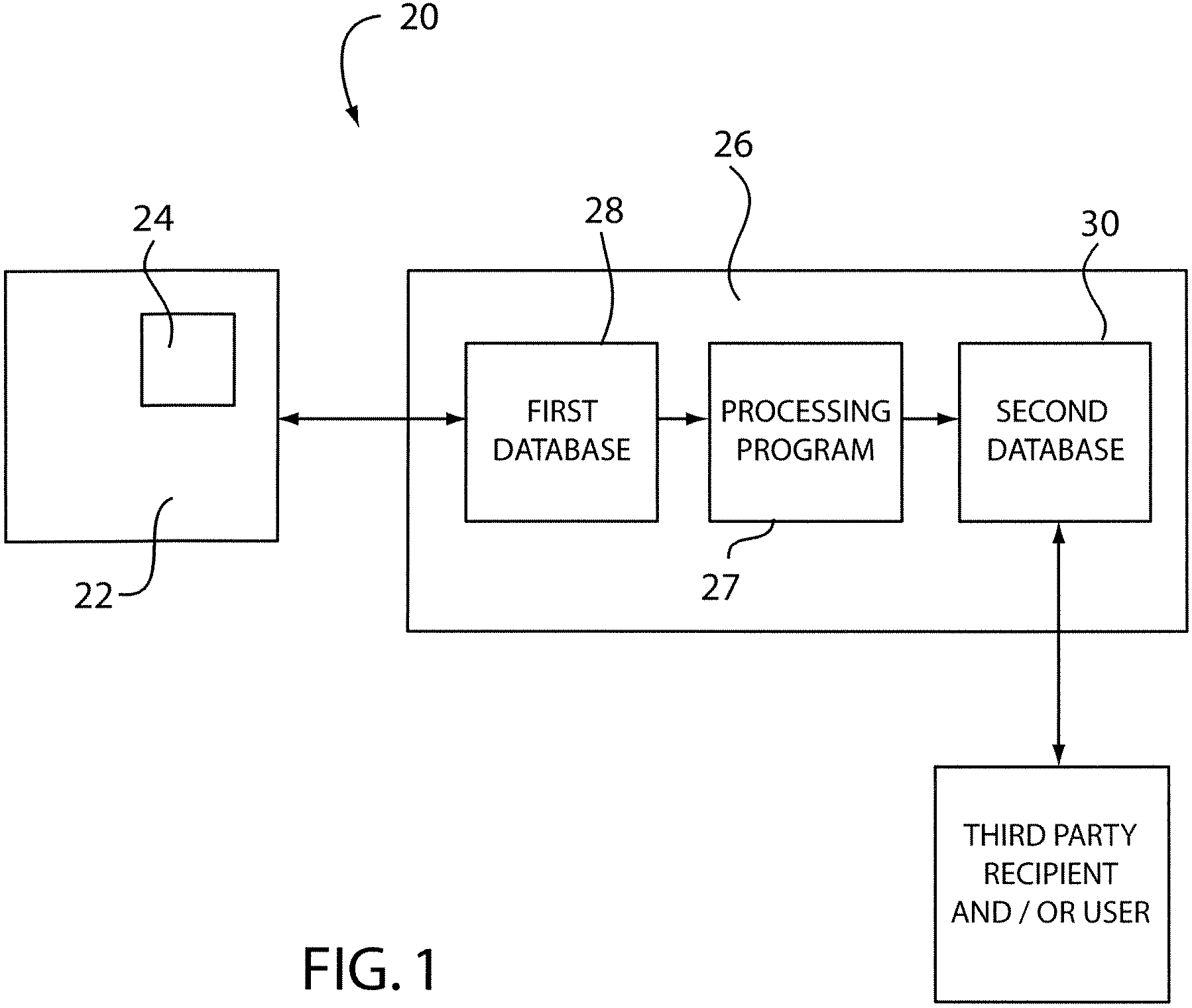
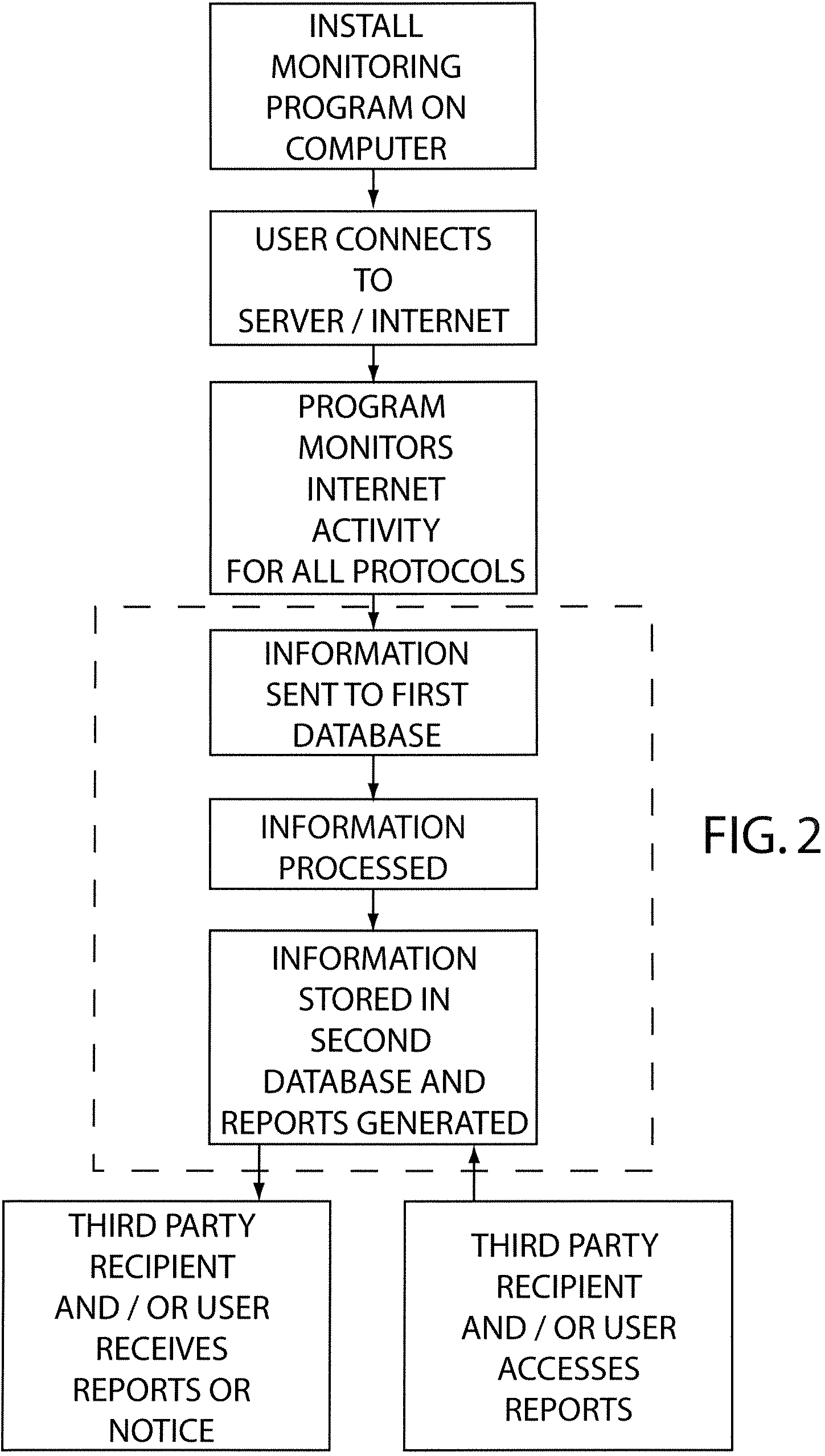
Internet use monitoring system and method
A system for monitoring Internet use of a selected computer user includes a remote server and a computer having a monitoring program voluntarily installed thereon by the user communicatively connected to the remote server. The monitoring program is configured to monitor various Internet access activity of the computer user and record the Internet access activity on the remote server. The Internet access activity includes access of at least one Internet protocol from the group consisting of newsgroups, file sharing programs, file transfer programs, chat rooms, peer to peer chats, and electronic mail activity. A method of using a monitoring system includes the steps of a computer user voluntarily installing a monitoring program on a selected computer, recording the Internet access activity, and providing the recorded information to a third party recipient. A report may be provided that includes a variety of information and may include a plurality of portions.
Owner:COVENANT EYES
Protective system
InactiveCN1925397AUser identity/authority verificationCharacter and pattern recognitionInternet useEngineering
This invention relates to protection system in the user identification and filter technique, wherein, current network user can download each kind of materials with most not suitable for children; and we can adopts biological collection technique to judge age of biology but the current device has not the control, limitation or degree on internet for children.
Owner:SHANGHAI ZHONGCE IND & TRADING +1
Method and apparatus for controlling child's internet use
InactiveUS20050240960A1Digital data information retrievalDigital data processing detailsRemote controlComputer usage
A method and apparatus for inducing children to select appropriate programming over the Internet comprises providing a parent or other supervisor with equipment and software for monitoring Internet usage by the child's computer on a remote television set and providing the supervisor with a remote control device for disconnecting the child's computer from the Internet or disabling the child's computer completely if undesirable content is detected. The child's computer usage can be recorded and stored for later viewing. A controller can be set to permit time periods during which Internet usage is permitted.
Owner:NAGTZAAM MARTINUS
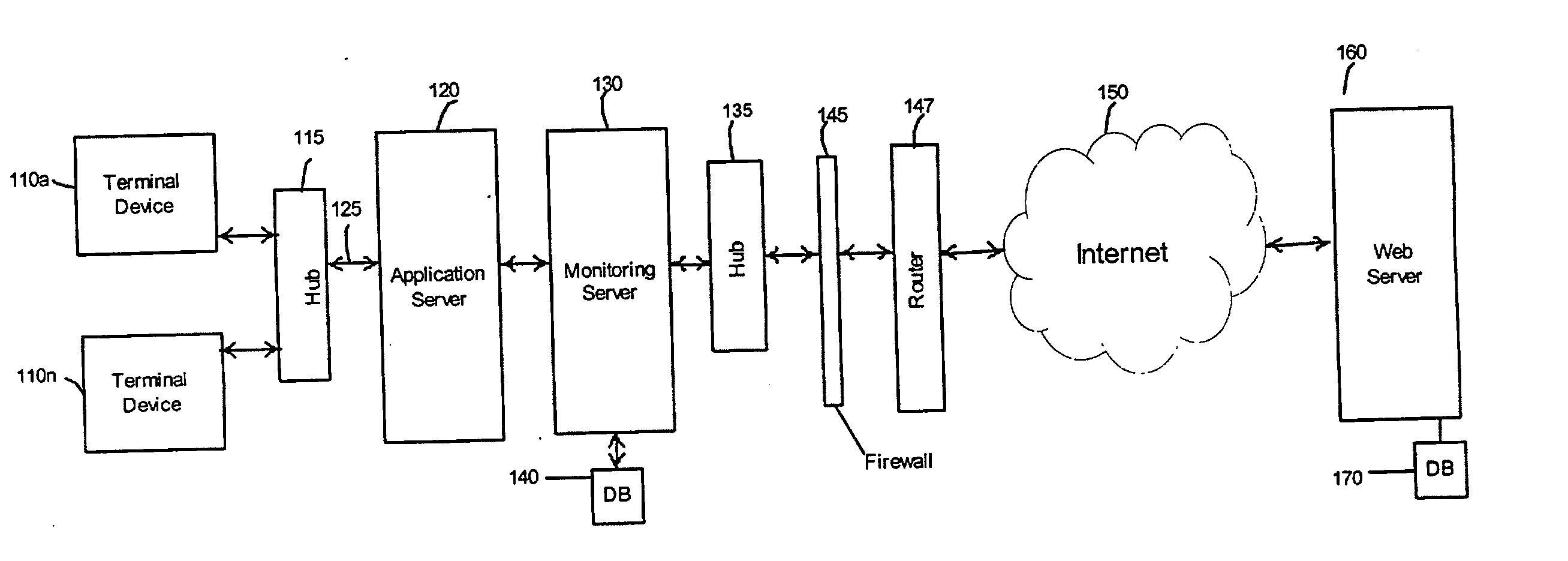
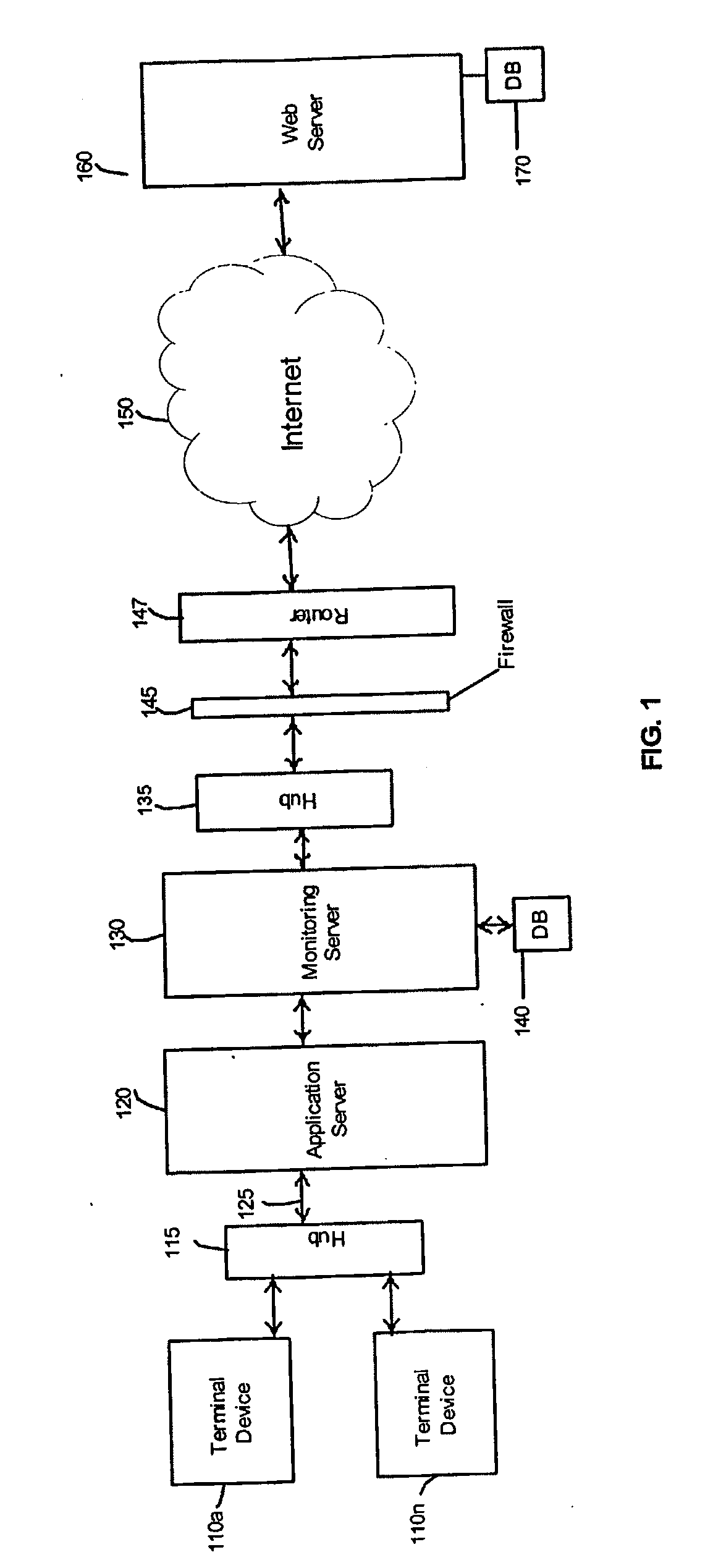
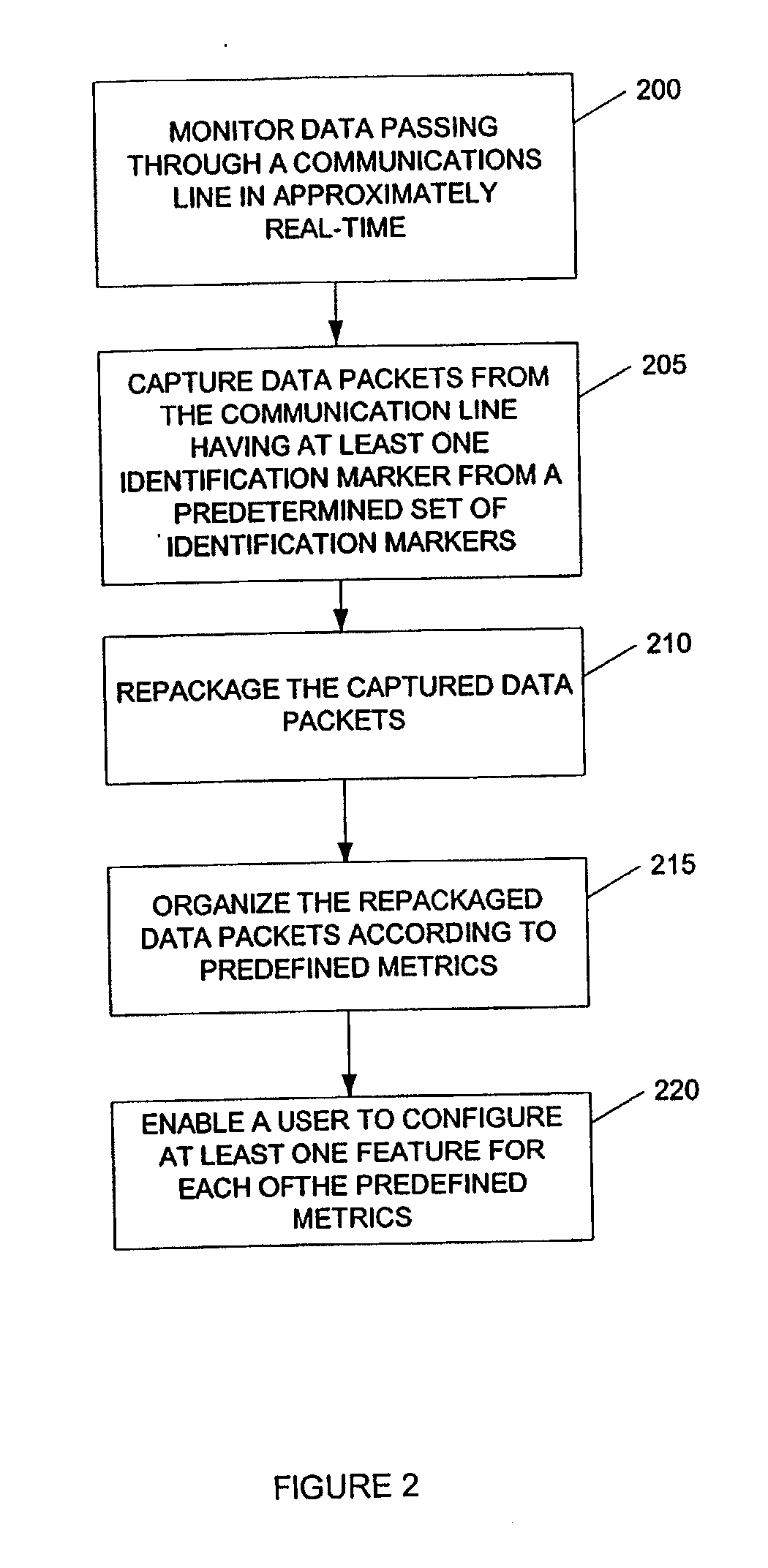
Method and system for monitoring network communications in real-time
InactiveUS20070061451A1Interprogram communicationDigital computer detailsInternet useNetwork communication
A system and method are provided for monitoring network communications in approximately real-time by capturing data that passes through a computer network and searching the data for at least one identification marker from a pre-determined set of identification markers. The information associated with the captured data is repackaged, viewed, and stored in a database. An authorized party may be provided with real-time alerts when predefined criteria are satisfied and the information may also be presented in reports that are organized and easy to read. As a result, the invention enables an authorized party to view pre-selected transactions in order to enforce Internet use policies.
Owner:VILLADO MICHAEL +1
Systems, methods, and computer program products for tracking and controlling Internet use and recovering costs associated therewith
InactiveUS20050120024A1Accurate monitoringBill back research timeMetering/charging/biilling arrangementsDigital data processing detailsWeb siteInternet use
Systems, methods and computer program products enable the recovery of costs associated with Internet browsing by requiring the users to enter validation information such as a client and matter number before accessing administrator-identified web sites. Administrators may also control Internet browsing using executable scripts that operate when administrator-specified filters are satisfied. These scripts may log all or select Internet activity, prevent a browser from accessing a URL, redirect a browser, save HTML or web page content, and generally control all Internet browser use for web browsing.
Owner:THARPE JIM
High-precision cognitive performance test battery suitable for internet and non-internet use
InactiveUS20030186201A1Performance data is accurateGood for healthEducational modelsElectrical appliancesTest batteryComputer network
A system and method for internet-based cognitive performance measurement is provided. Furthermore, a method is provided whereby improvements in statistical accuracy is obtained.
Owner:MARTIN ROLF JOHN
Richard and Preston super network, "The Super Net"
InactiveUS20050114484A1Multiple digital computer combinationsOffice automationWeb siteInternet users
We have invented extensions to the current Domain Name System which include top level domains that create more available domain names. Some of the newly introduced top level domains provide information on a web sites location of operation. This will enable search engines to categorize search results based on location. Also the domain name systems we introduce, provide a long term method of expanding the current domain name system. They also offer domain names which include words internet users are familiar with. Some of the new top level domains address growing internet related areas in which domain name usage will be pertinent. Areas such as communications and internet capable devices will benefit from the top level domains created specifically for them. Another area addressed by the new top level domains is countries with large internet usage. Countries like Japan United States and China can use multiple top level domains created specifically for them because of their large number of internet users and high tech businesses. The need for personal web sites is also increasing. Internet profiles are means for people to allow others to view information about them. A new extension for personal websites will allow more people to have a web address to post information about them. The domain name systems and top level domains we have invented will coexist with the current domain name system.
Owner:WILSON RICHARD PHILLIP +1
Uni-directional cross-domain identity verification based on low correlation of private cipher key and application thereof
InactiveCN101478396AImprove privacyReduce correlationUser identity/authority verificationMobile Telephone NumberPrimary station
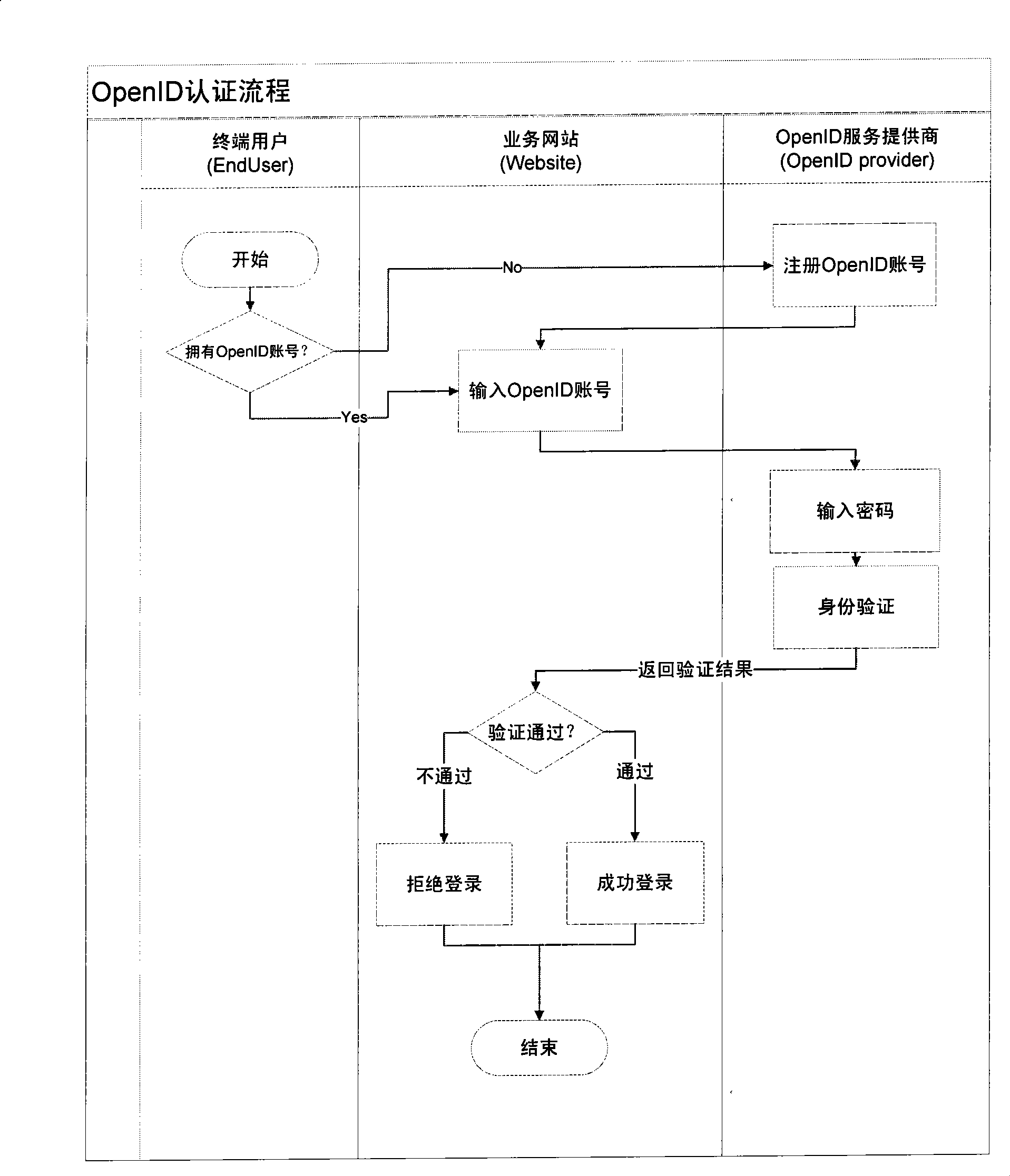
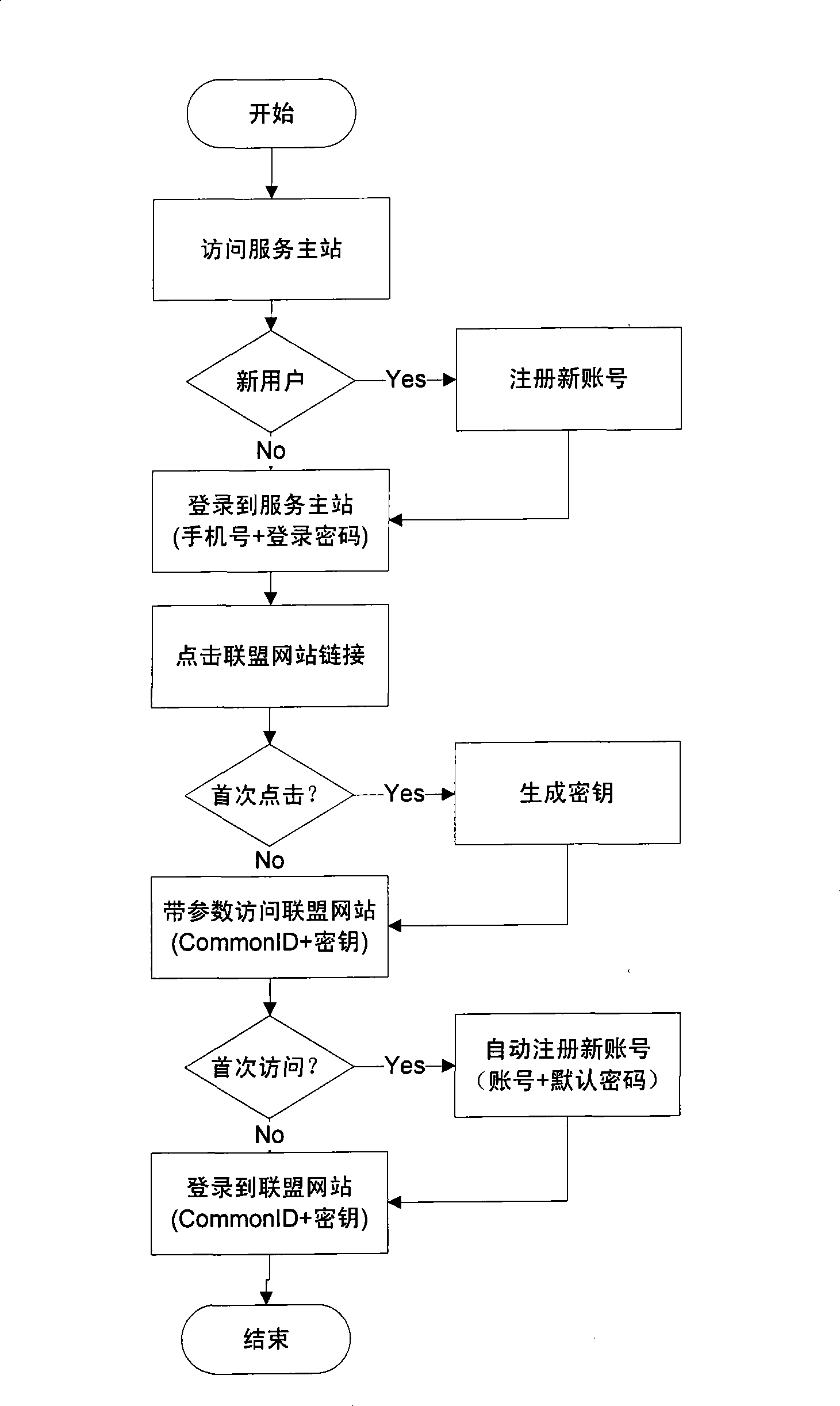
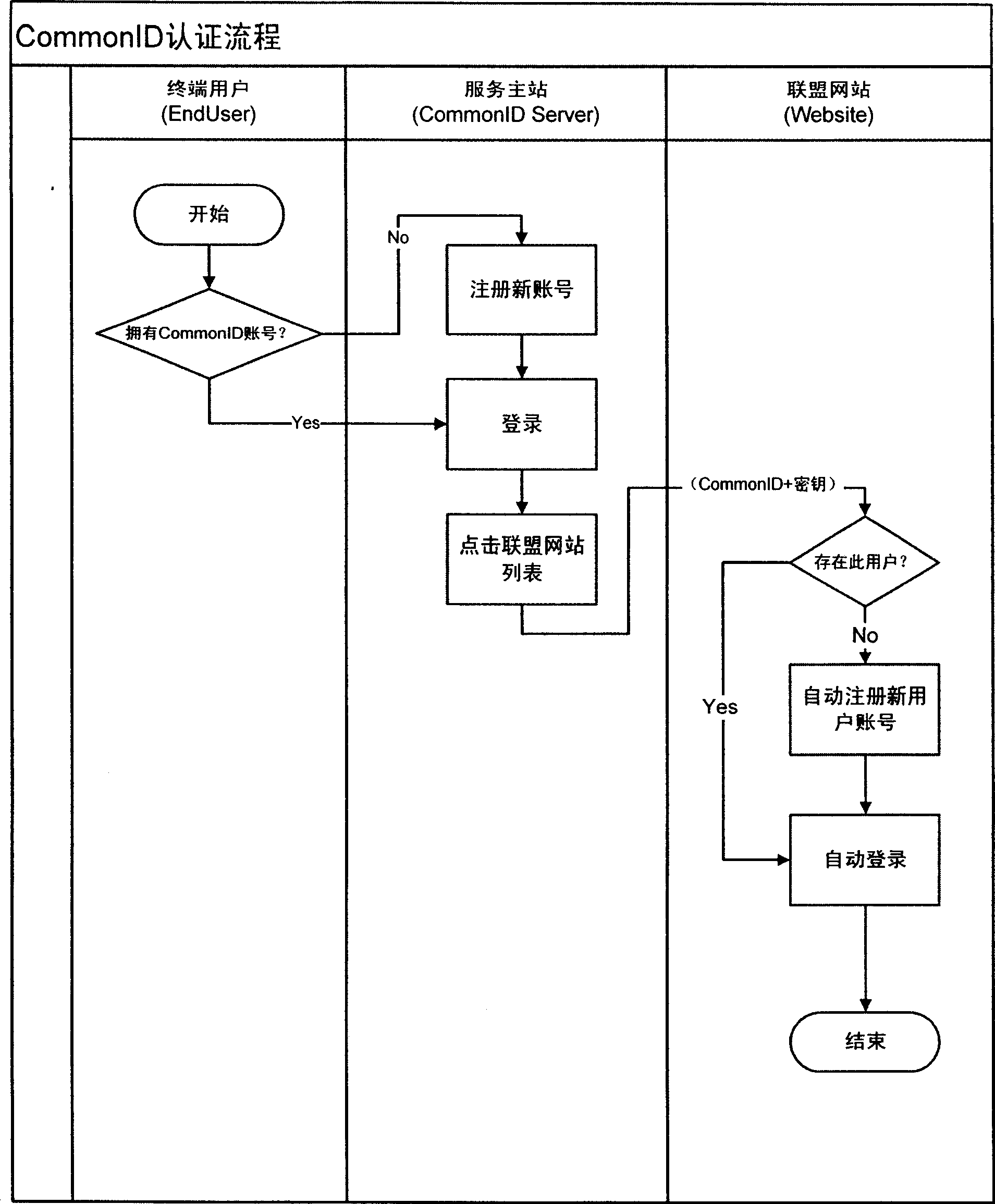
The invention provides a method for low-correlation one-way cross-domain identity authentication based on private key. The method comprises the following steps: a user registers a user name in a common ID server and the system allocates a common ID to the user if the registration is successful; the user logins to the common ID server to acquire the authenticated ID; the user clicks the link of a Website in the common ID server and the common ID server transfers the common ID of the user and a relevant key to the Website; the Website receives the parameters transferred from the common ID server, if determining the first visit, allocates the user name to the user by use of the acquired two parameters (i.e. common ID and key) and calls a log-in module to succeed in the identity authentication; and if determining the second visit, the Website calls the log-in module to succeed in the identity authentication by use of the acquired two parameters (i.e. common ID and key). The method is applied to the log-in procedure bound to the mobile telephone number of the user and the multiple internet application names of the user in the mobile internet, and has the advantages of good privacy property, easy use, convenience for network management and strong applicability.
Owner:黄希 +1
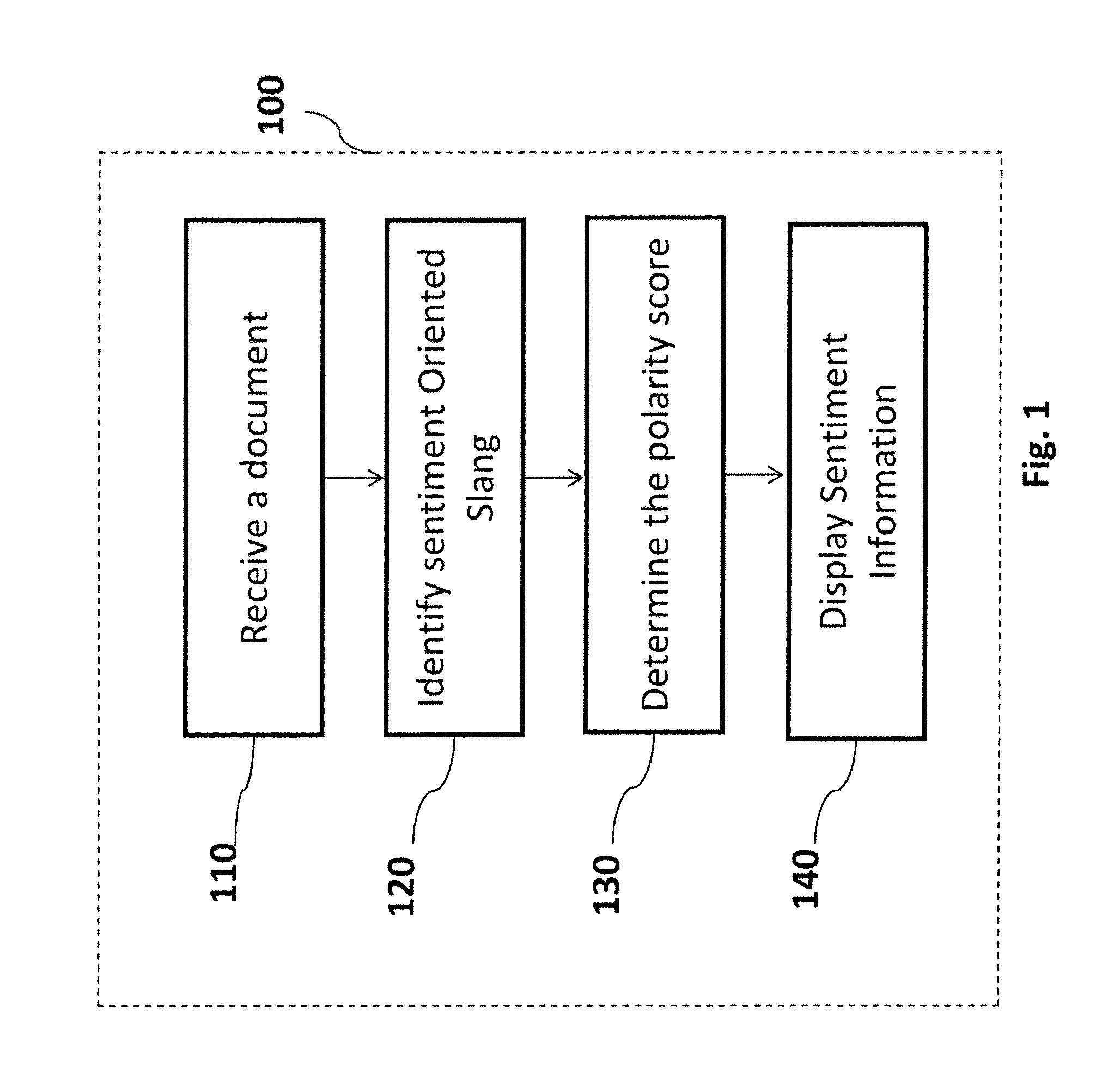
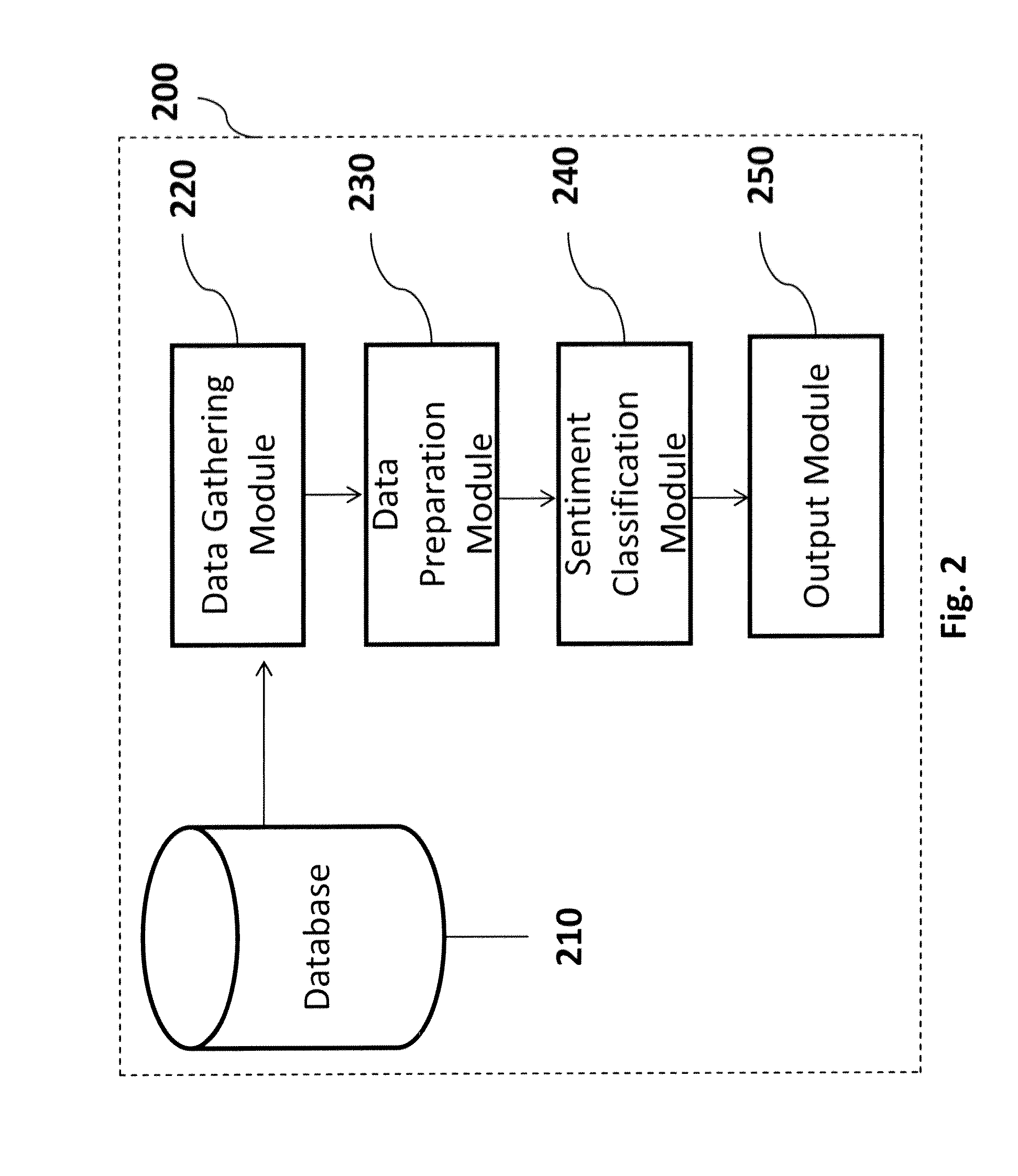
System and method for slang sentiment classification for opinion mining
ActiveUS20120259617A1Accurate sentiment scoreMore precisionNatural language translationSemantic analysisInternet useOutput device
The present disclosure describes a method of sentiment oriented slang for opinion mining. With increasing use of internet, many users can submit their review comments directly to the companies which can be automatically processed and summarized with critical issues from time to time and help the company get real time feedback from its customers. The method comprises, receiving at least one document comprising a plurality of sentiment oriented slang. The next step of the method comprises identifying the plurality of sentiment oriented slang in the at least one document. Further, a polarity score of each of a slang word identified is determined and sentiment information is displayed on an output device as an output.
Owner:INFOSYS TECH LTD (IN)
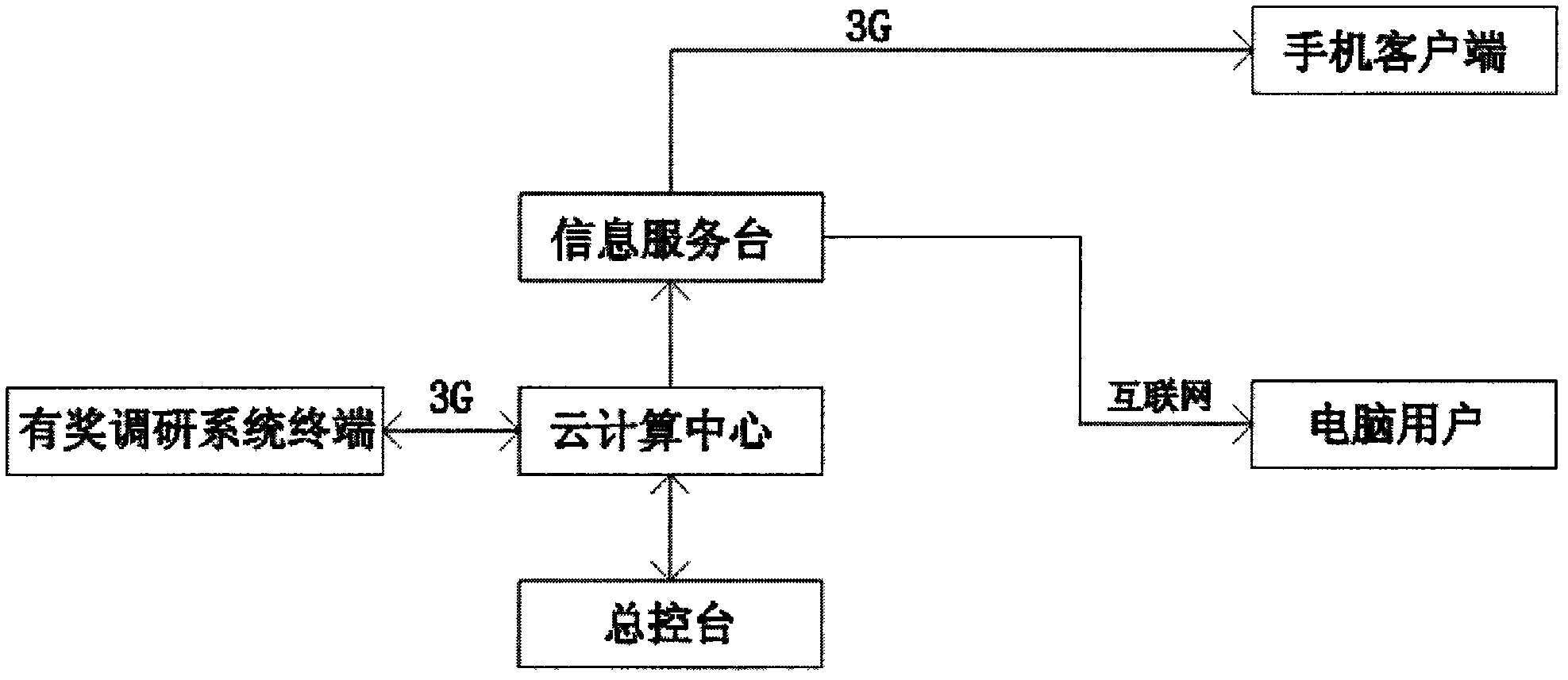
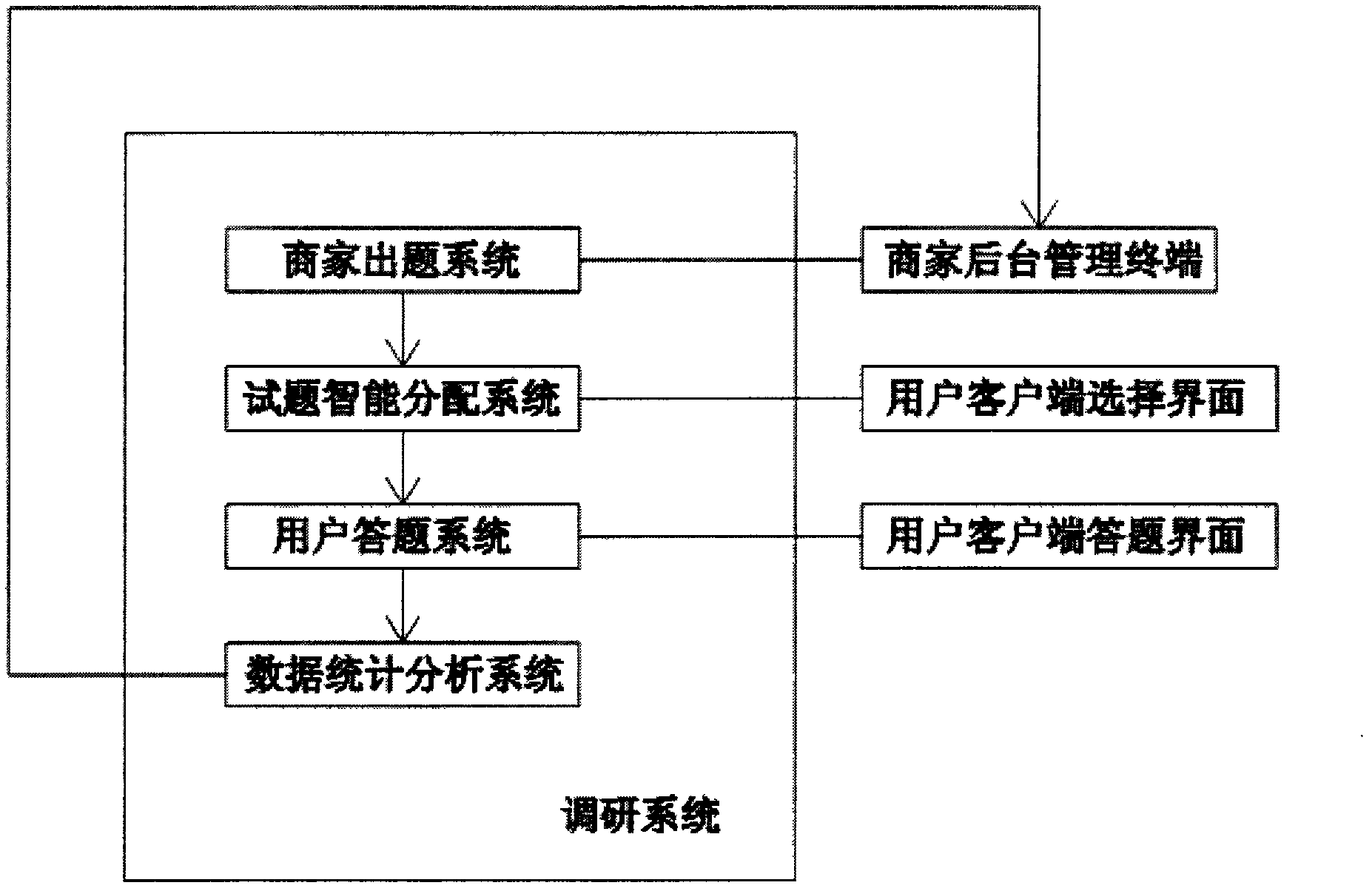
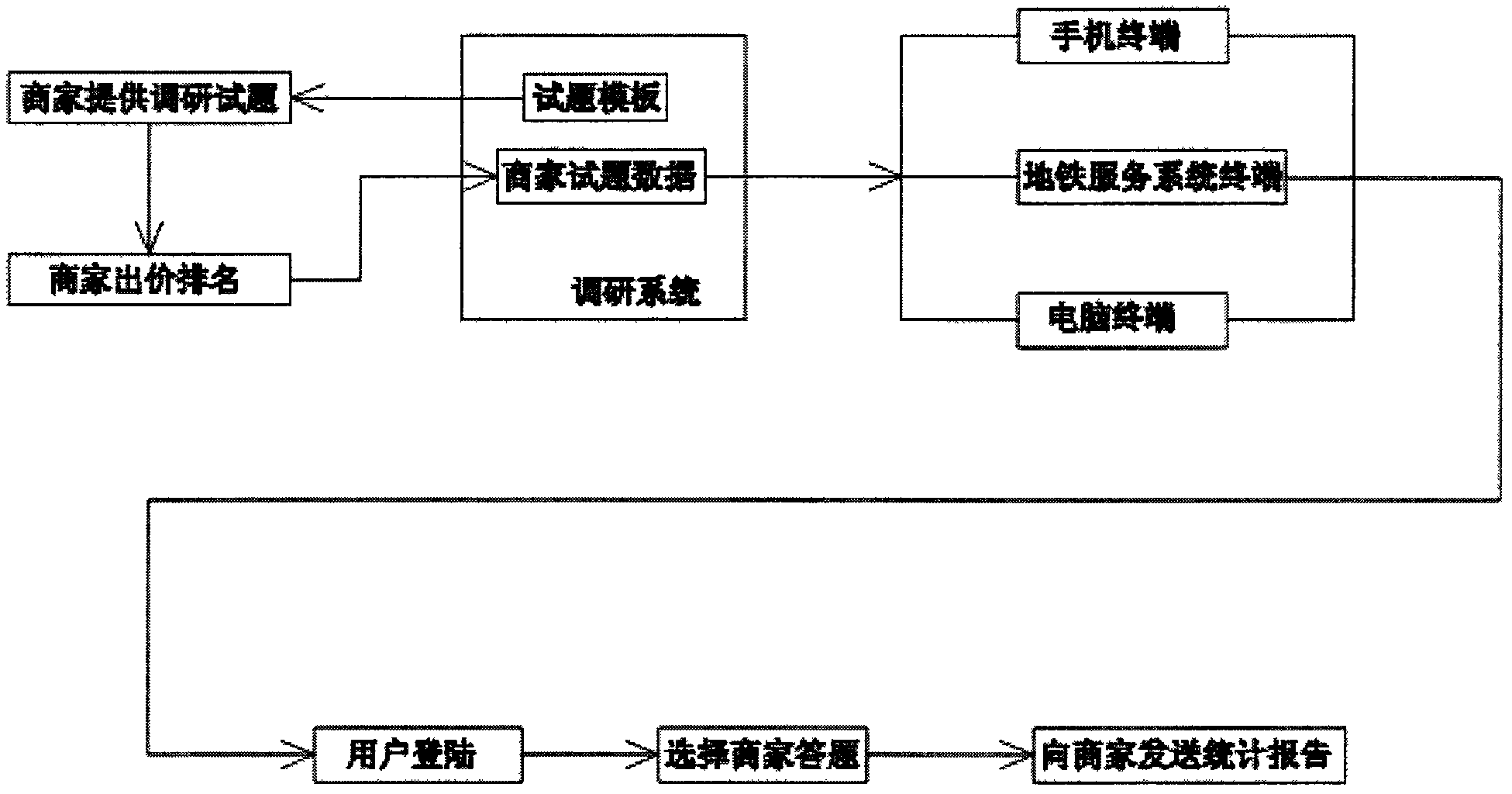
Premium investigation system with accurate advertisement dissemination effect
The invention discloses a premium investigation system with an accurate advertisement dissemination effect, which is based on a premium investigation system terminal and an information service model of a website. The investigation system comprises a businessman question make-out system, a user answering system, an intelligent question allocation system and a data statistics analysis system. The investigation system provided by the invention can be landed with the aid of special ID information through Internet, the businessman can make out questions according to a question template; users can answer the questionnaire, obtain compensation, and participate in a campaign of drawing a lottery; and a statistics report can be sent to the businessman through the system. Through the system provided by the invention, a traditional model that the advertising information is passively received by audiences is changed, and the billing is performed according to the watching and right comprehension of audiences, so the historic breakthrough from the price to the value of the advertisement is realized, the real-time dynamic monitoring is achieved, the accurate advertisement effect can be measured, and the audiences can gain the advertising information and a certain remuneration during entertainment, and accordingly, the user experience value is promoted, and the interactive watching becomes the mainstream and trend.
Owner:深圳市英尔科技有限公司
Method for preventing malicious software installation on an internet-connected computer
ActiveUS7845005B2Avoid accessMemory loss protectionDigital data processing detailsOperational systemRandom access memory
A computer random access memory is divided into first and second partitions. Each partition has its own operating system (OS). The first partition has a conventional OS and is designated for non-Internet use. The second partition is designated for secure Internet access, and has an OS specific for Internet usage. Software in the second partition cannot write or copy files in the second partition. The size of the second partition is fixed and unchangeable while said second partition is open. Each software application in the second partition is allocated a memory region that cannot be changed, thereby preventing memory overflow attacks. A secure memory is designated for temporary storage of software used in the second partition. Cyclic redundancy check (CRC) values are calculated for all files in the secure memory. To detect unauthorized file changes, CRC values are calculated for all files used in the second partition, and checked against values stored in the secure memory. The second partition can write only to a secure memory using a security arrangement such as password protection or a download memory separate from the first partition to allow files stored in the download memory to be examined by scanning and testing from the first partition prior to being stored elsewhere in the computer.
Owner:KYNDRYL INC
Metered Internet usage
ActiveUS7089304B2Accurate usage trackingRaise the possibilityMultiple digital computer combinationsData switching networksIdle timeNetwork packet
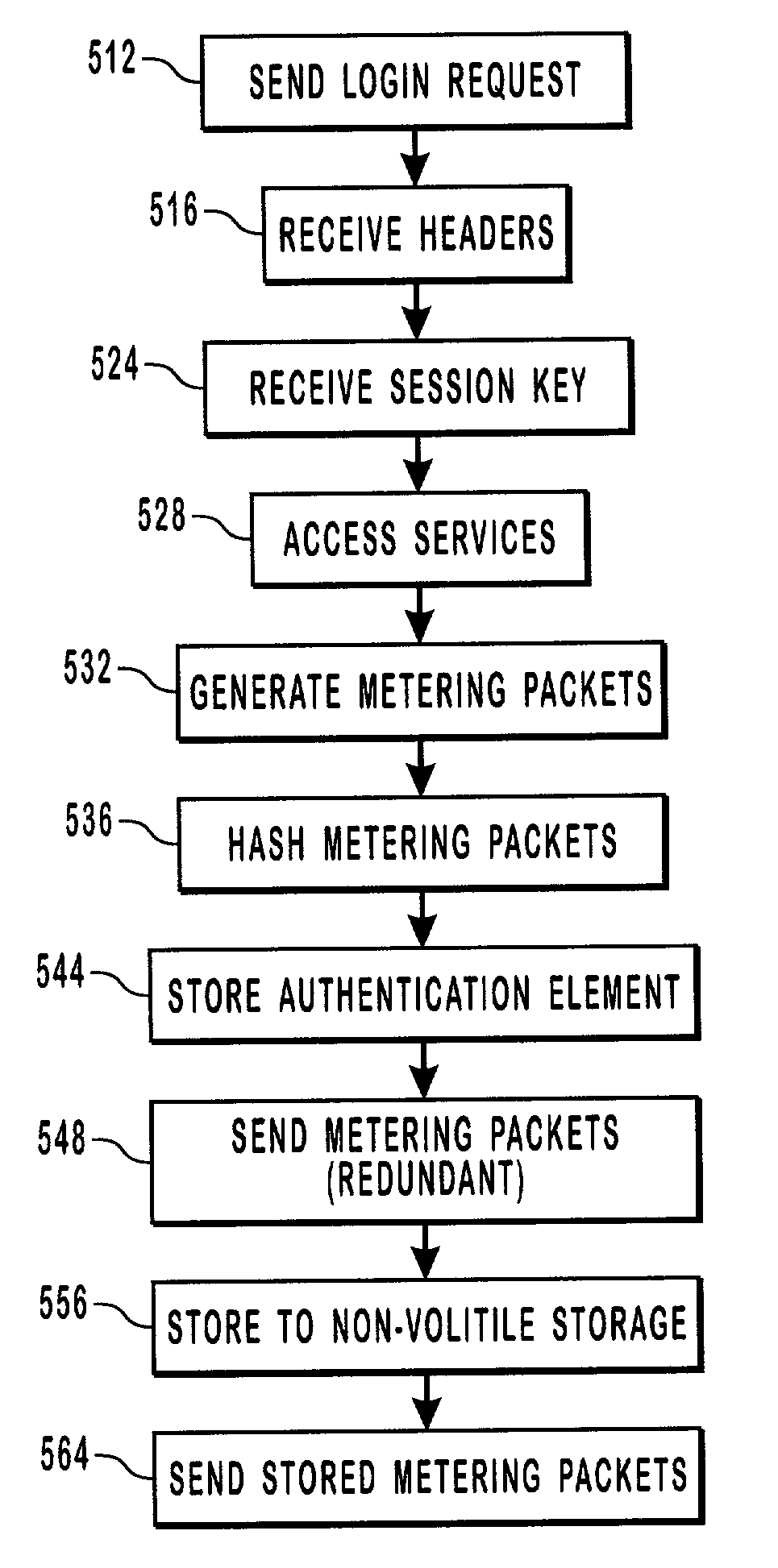
Methods, systems and computer program products for tracking a client's usage of one or more services provided by one or more servers. A client generates and sends one or more metering packets to a census service. Each metering packet includes a time element indicating the client's usage of the one or more services. The time element may include a charged time portion and a free time portion. An authentication element may be included with each metering packet so that the census service can determine whether or not a given metering packet is genuine. A login service communicates to the client whether or not usage should be tracked and indicates a time interval to expire between subsequent metering packets. A session identifier in each metering packet allows multiple sessions to be tracked simultaneously. Upon receiving metering packets, the census service discards redundant metering packets and updates a usage database accordingly.
Owner:ZHIGU HLDG
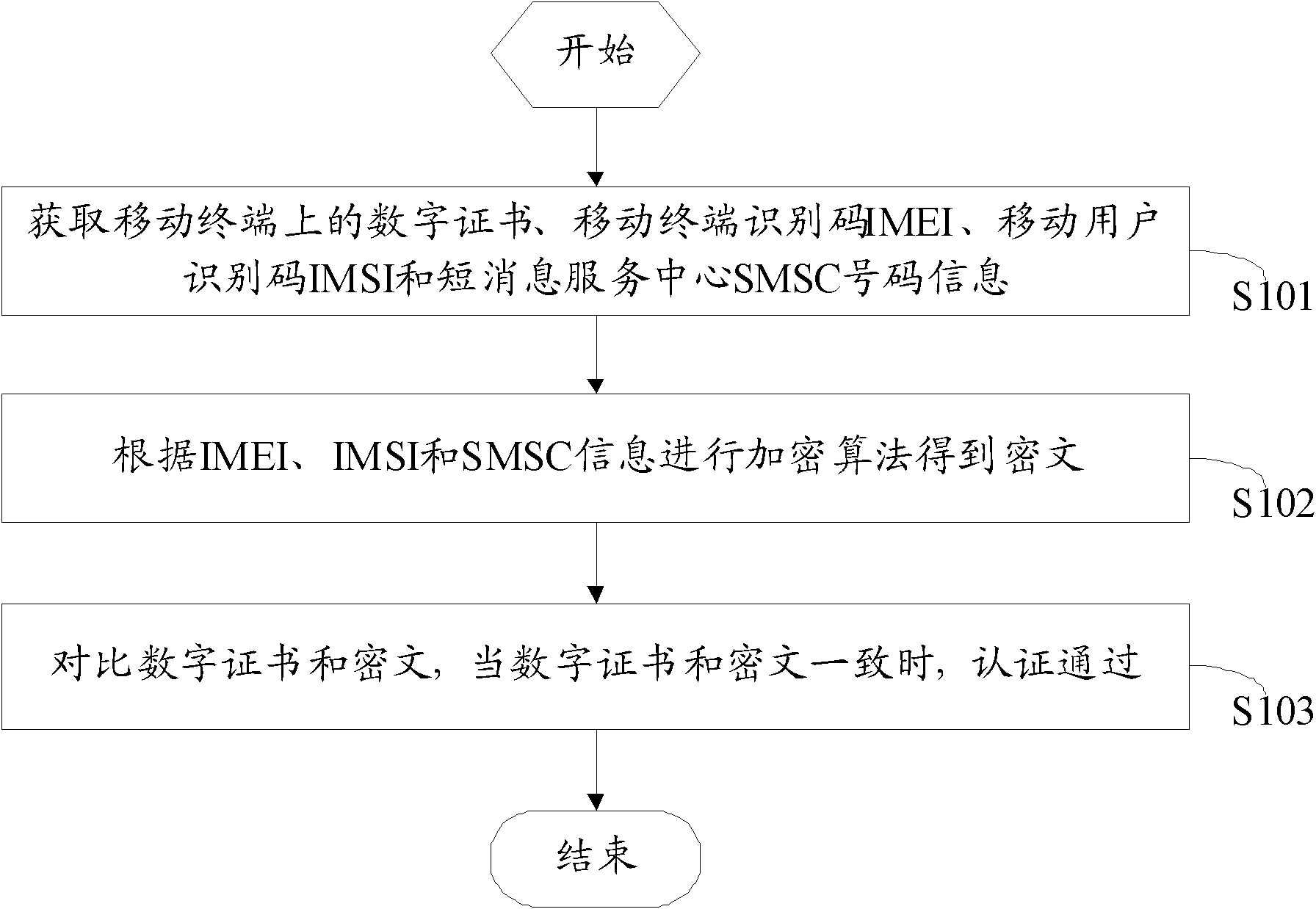
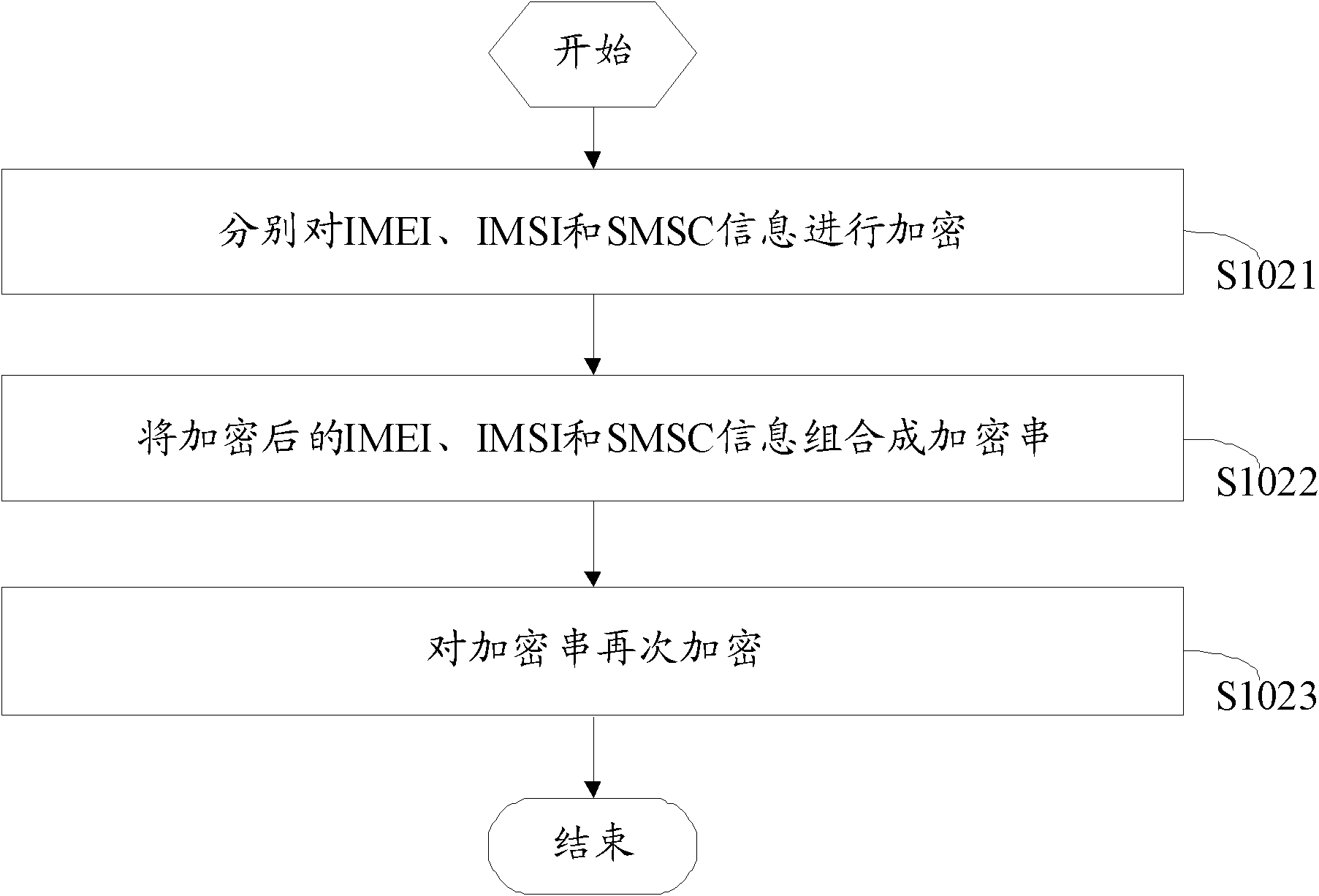
Method and device for authenticating mobile terminal
The invention discloses a method for authenticating a mobile terminal, comprising the following steps of: acquiring a digital certificate, an international mobile equipment identity number (IMEI), an international mobile subscriber identification number (IMSI) and short message service center (SMSC) number information on the mobile terminal; carrying out the encryption algorithm according to the IMEI, the IMSI and the SMSC number information to obtain a ciphertext; comparing the digital certificate with the ciphertext; and when the digital certificate is consistent with the ciphertext, passing the authentication. The invention also provides a corresponding device. According to the method and the device for authenticating the mobile terminal, by acquiring the IMEI, the IMSI and the SMSC number information on the mobile terminal, the mobile terminal is authenticated and the use safety of the mobile terminal on the internet can be improved.
Owner:深圳市爱贝信息技术有限公司
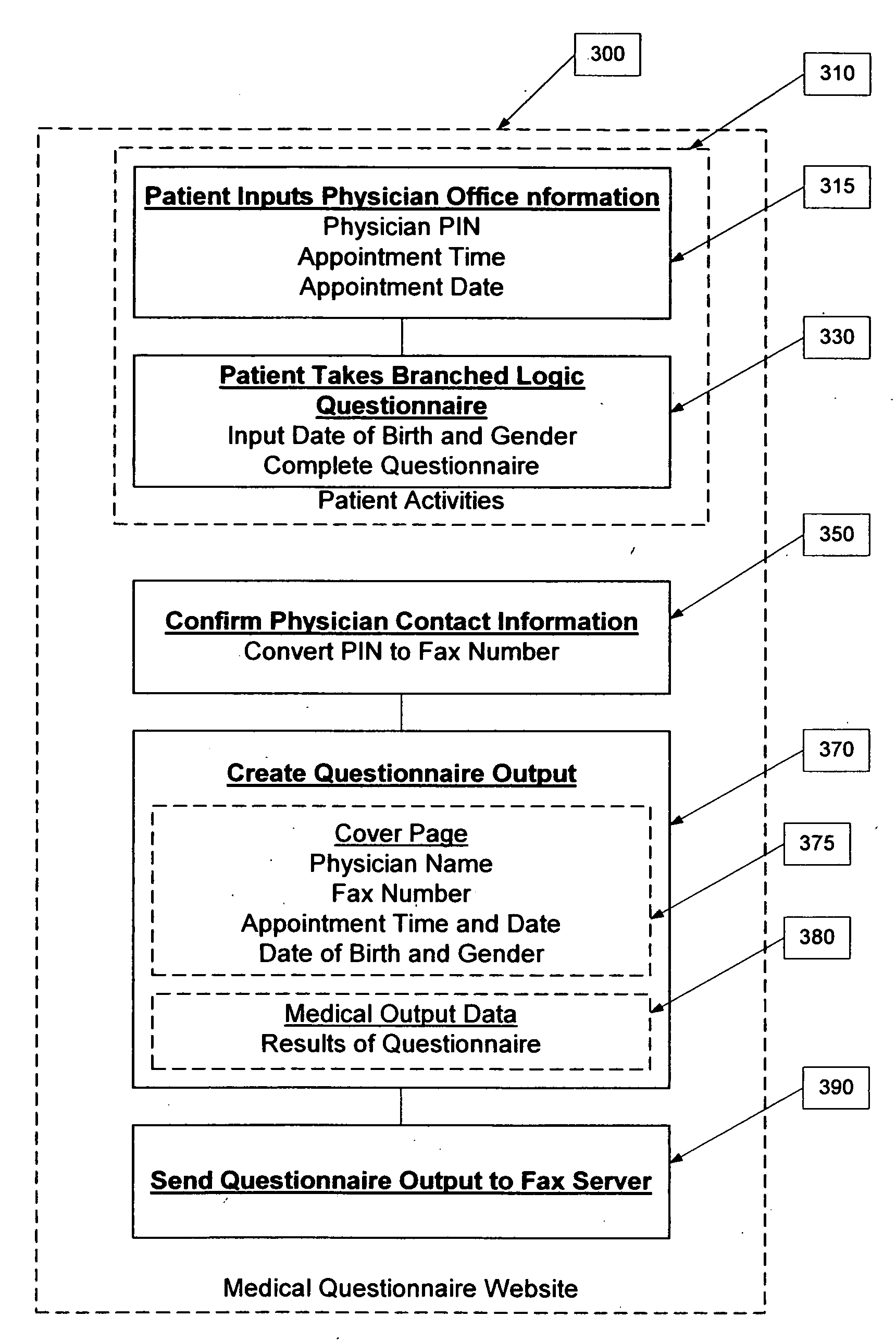
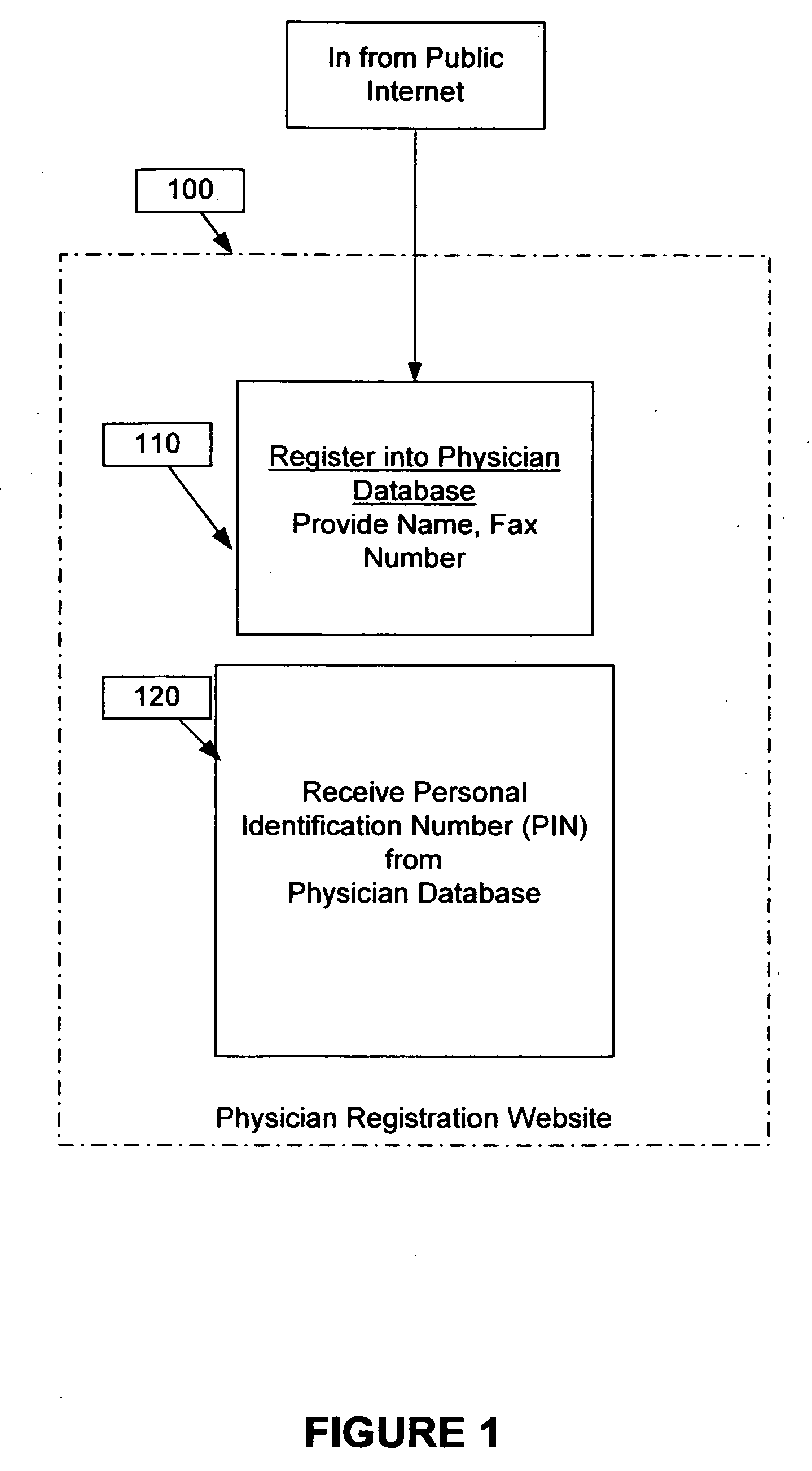
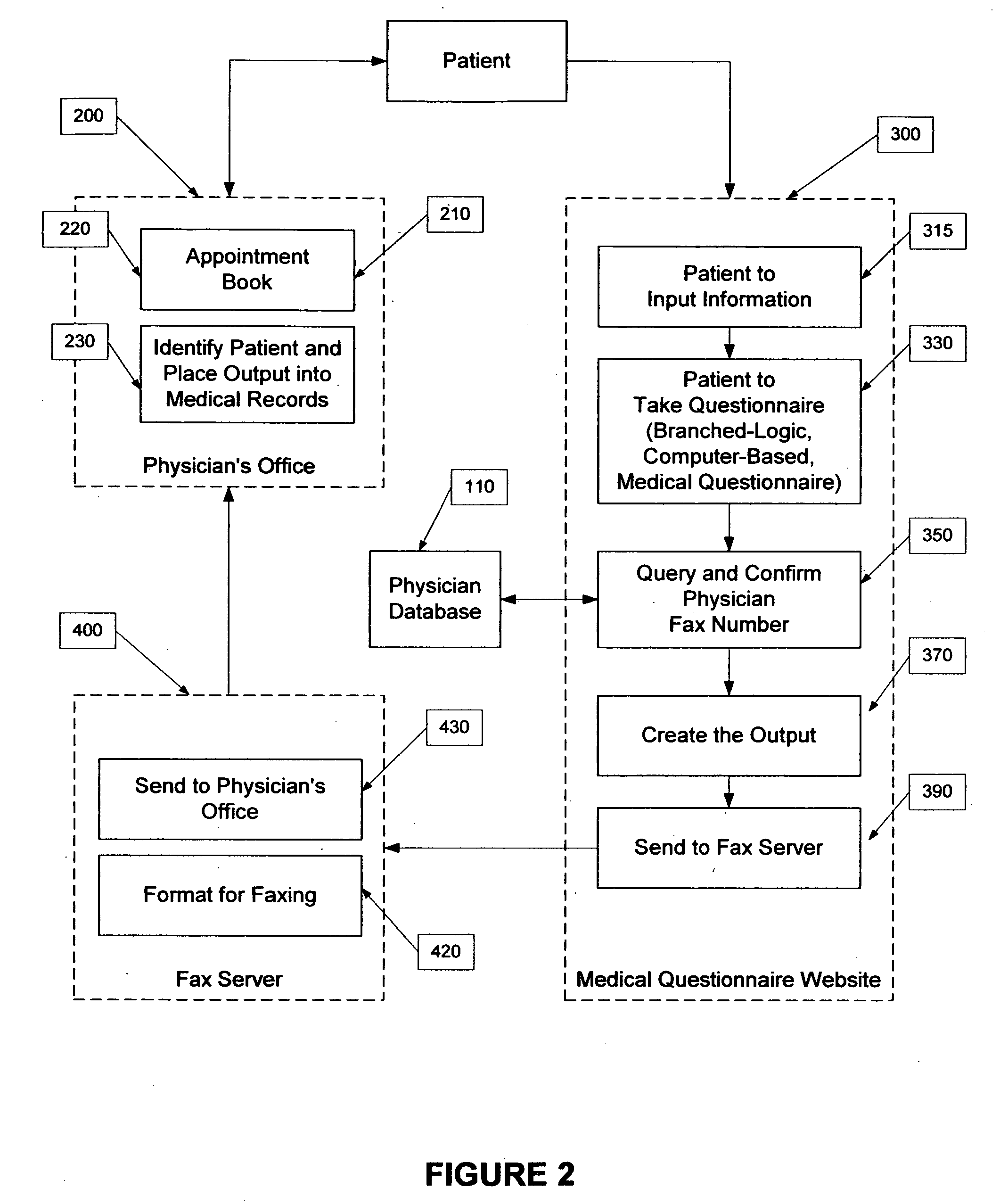
System and method to administer a patient specific anonymous medical questionnaire over the public Internet using manual decryption of user information
InactiveUS20080215356A1Office automationAnalogue processes for specific applicationsPublic interfaceMedical treatment
The invention is a system and method for a physician to administer an interactive, branched logic computerized medical questionnaire over a public internet to patients, such that said patients or said physician does not have to be identified on the questionnaire by name, and, therefore, can remain anonymous. The questionnaire is administered on a public Internet site using a personal identification number for the physician which, when interpreted by a third-party database, routes the output to the physician based on information provided by the physician. The output contains patient-related information which only the physician knows. The physician relates the patient information contained in the output, via manual means, to information already known about the patient based on the physician-patient relationship, the patient is identified and the output can be placed within the patients record.
Owner:VANCHO VINCENT M
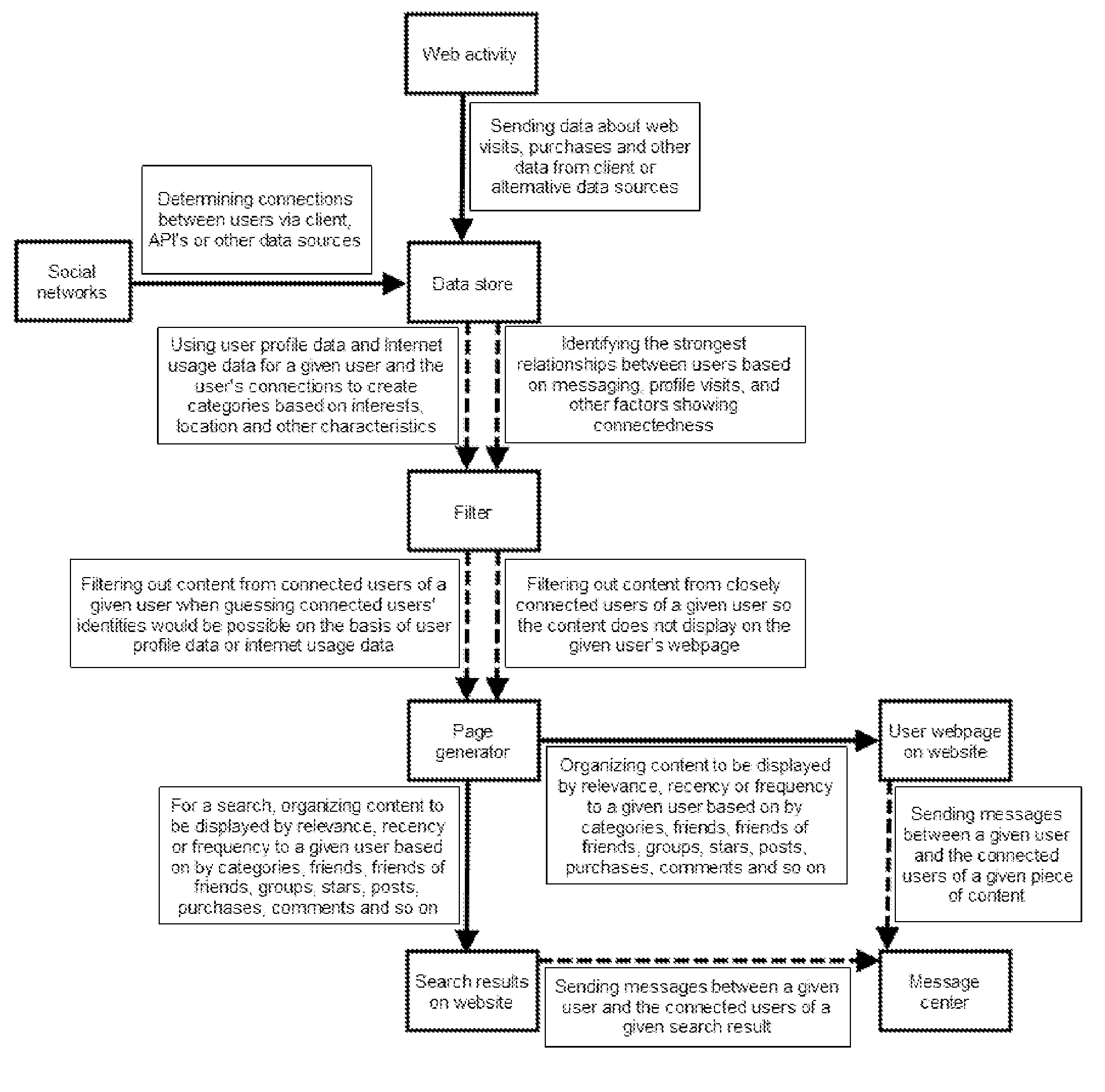
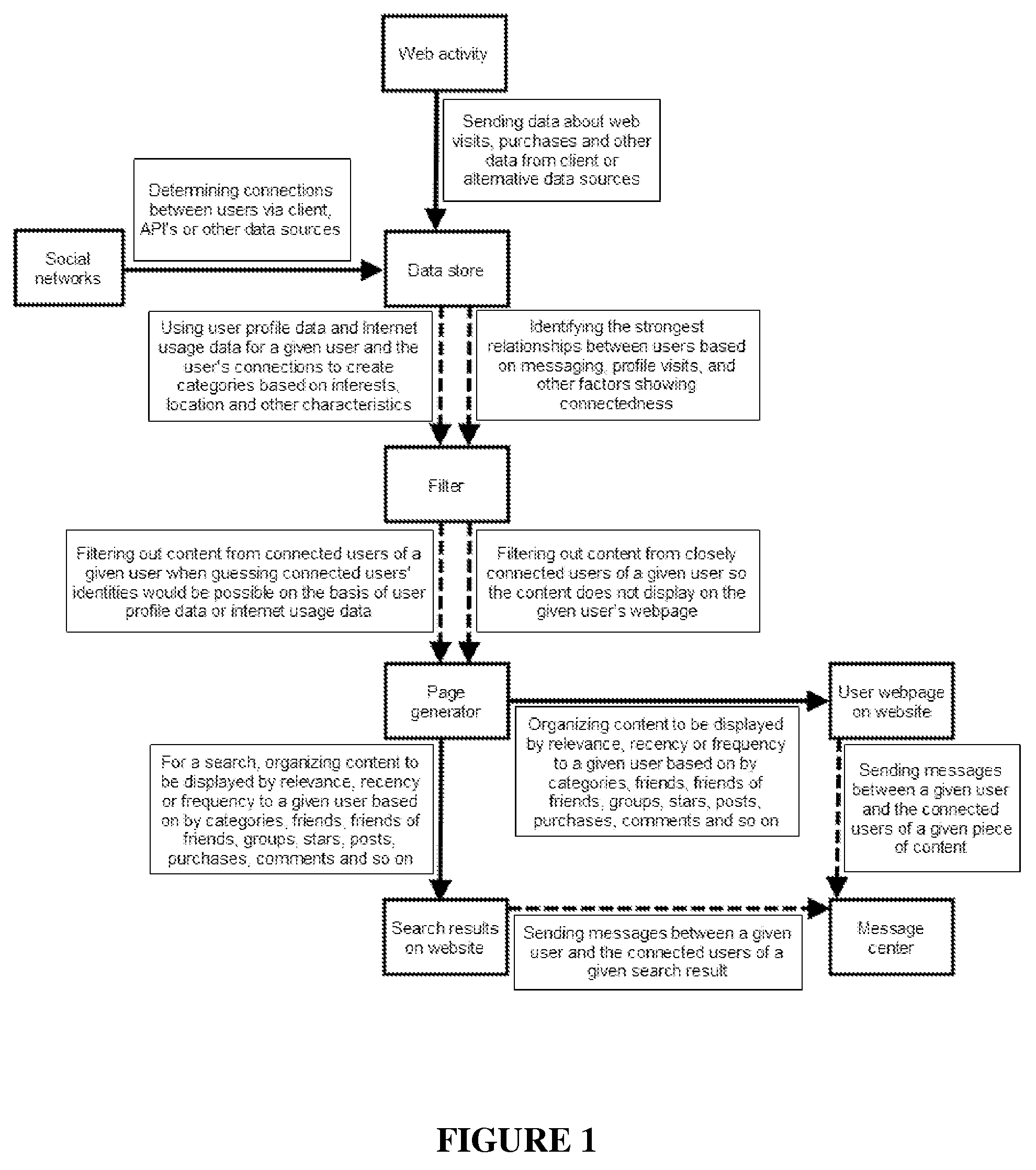
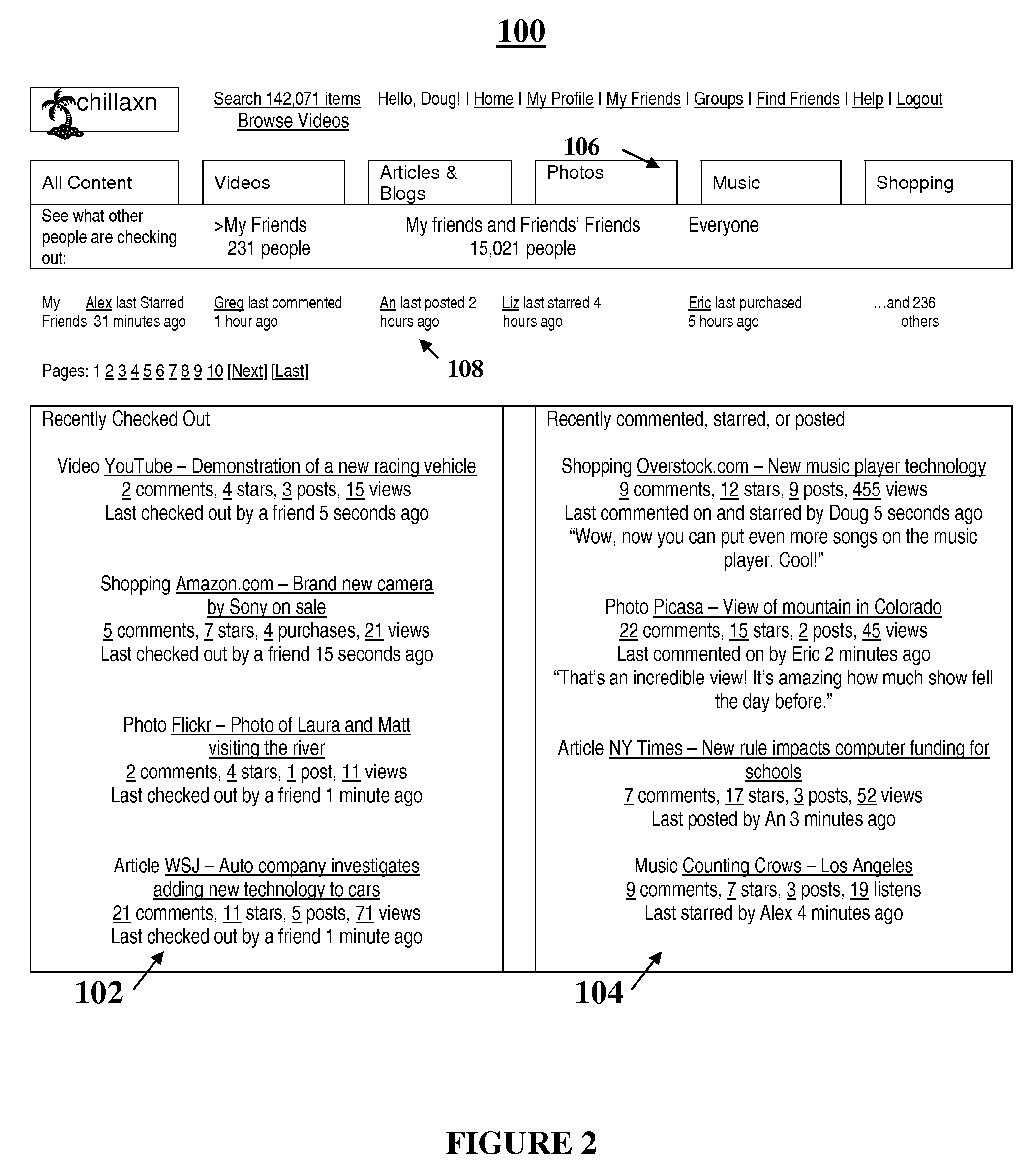
System for targeting third party content to users based on social networks
Owner:SHERRETAB DOUG +1
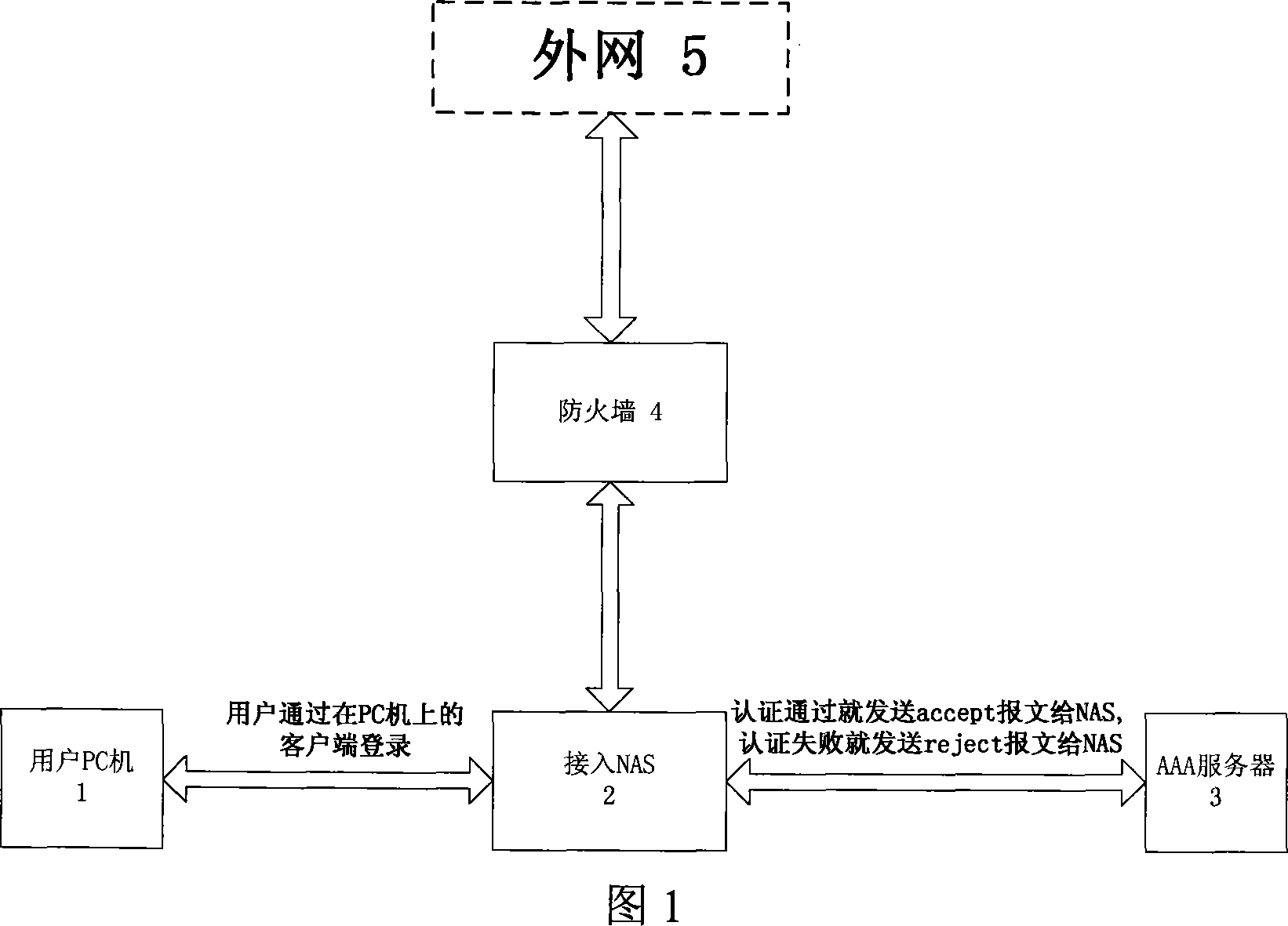
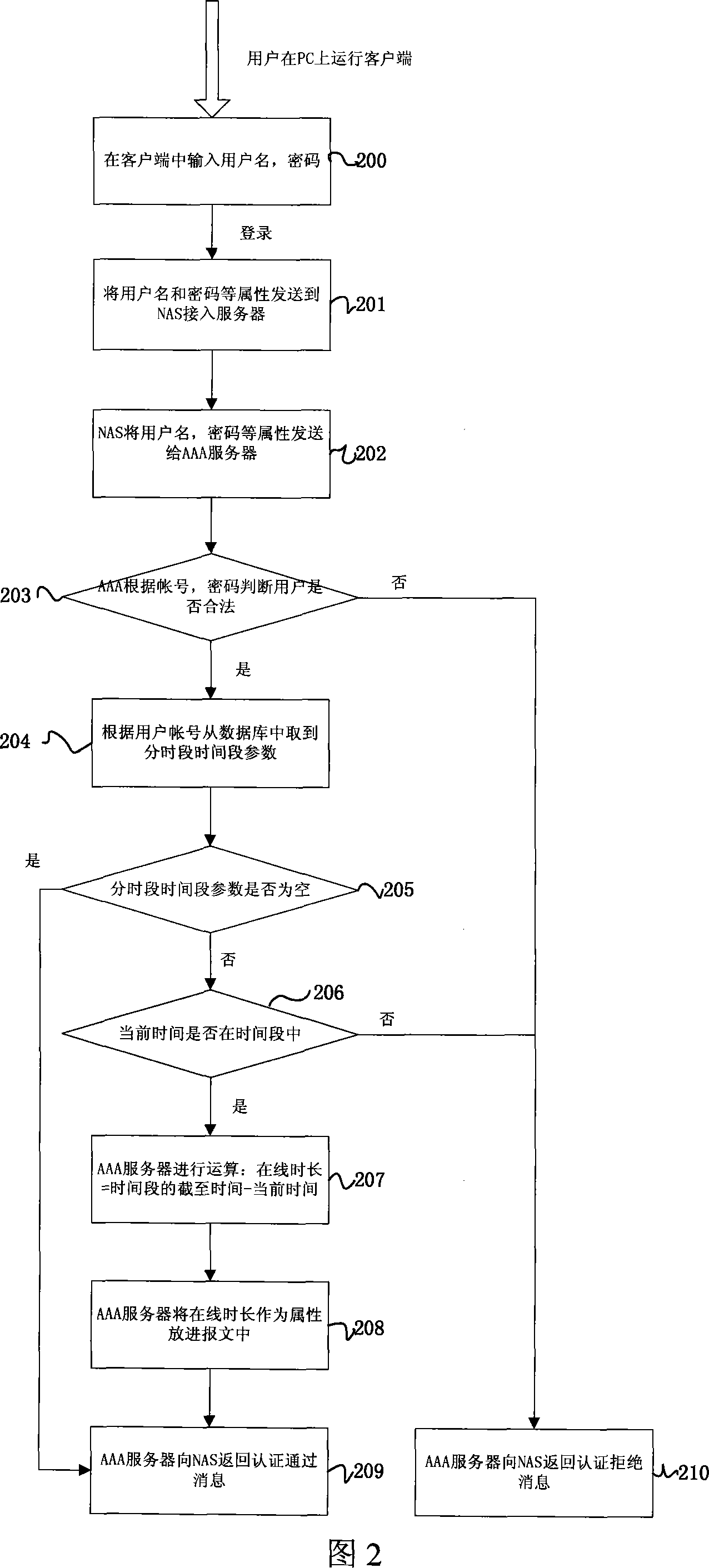
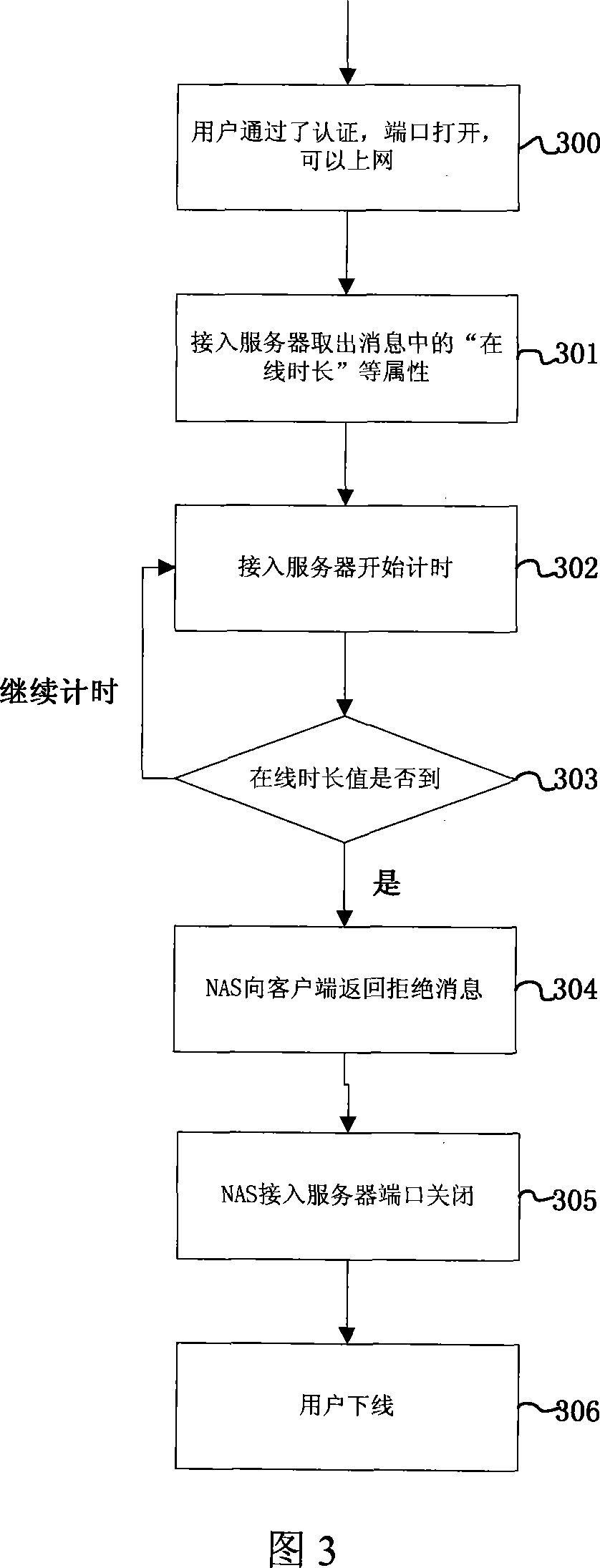
Method for controlling duration of internet use
InactiveCN101174992AGood personalized serviceStandardize Internet managementData switching networksNetwork access serverTime segment
The invention relates to a user net surfing time control method, which includes steps mentioned below in a user login process. Firstly, according to an account used by a login user, an AAA server (3) finds a corresponding allowed net surfing time segment from the corresponding relationship between the user account which is prearranged in the AAA server and one or a plurality of allowed net surfing time segment. The AAA server refuses the login of any user out of the allowed net surfing time segment or allows the login of a privileged user in the allowed net surfing time segment and notifies a network access server (2) to force the user out of the line when the allowed net surfing time segment is over. Compared with the prior art, the control method can specify the net surfing management more effectively and provide various users with better personalized service.
Owner:ZTE CORP
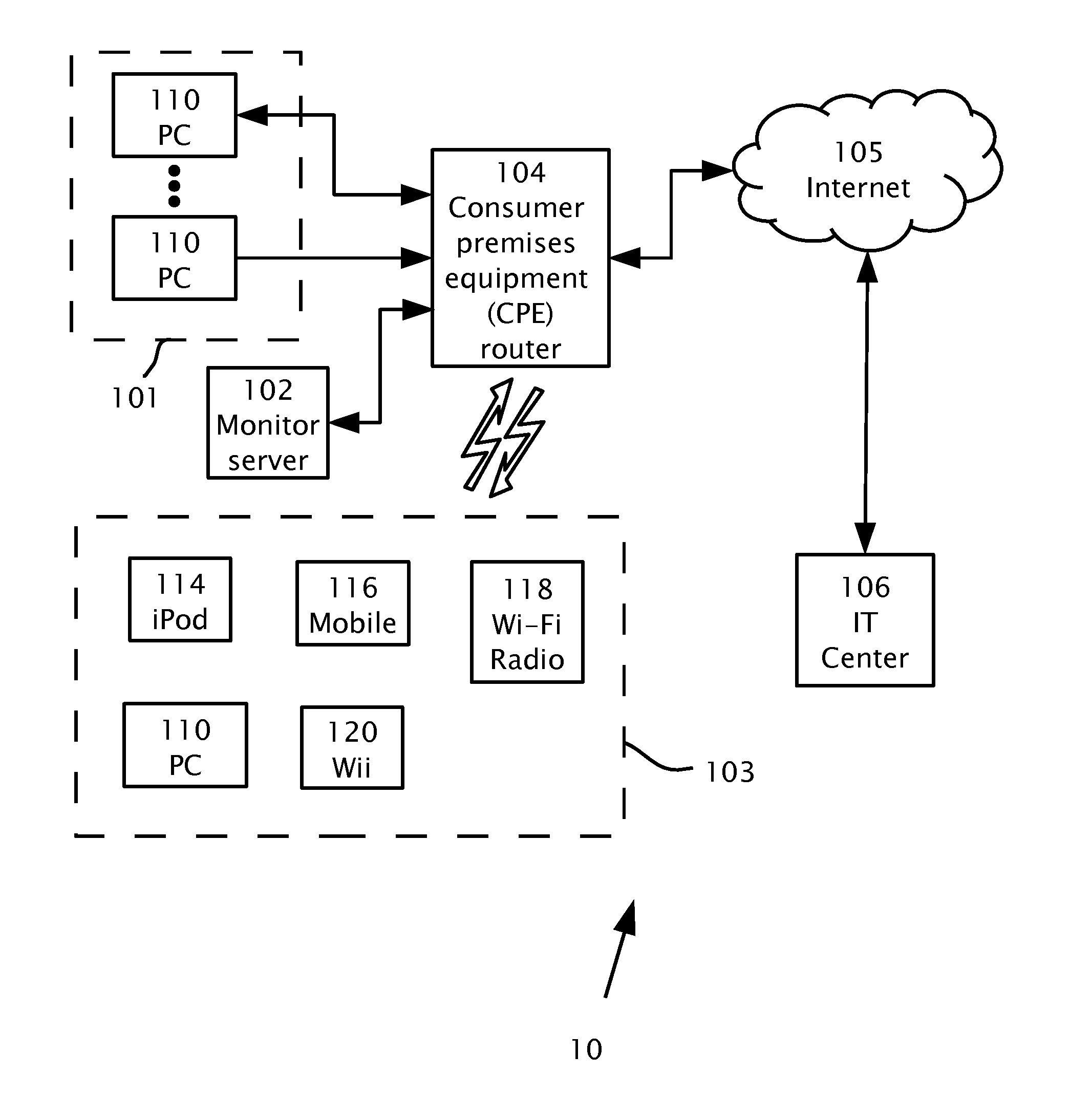
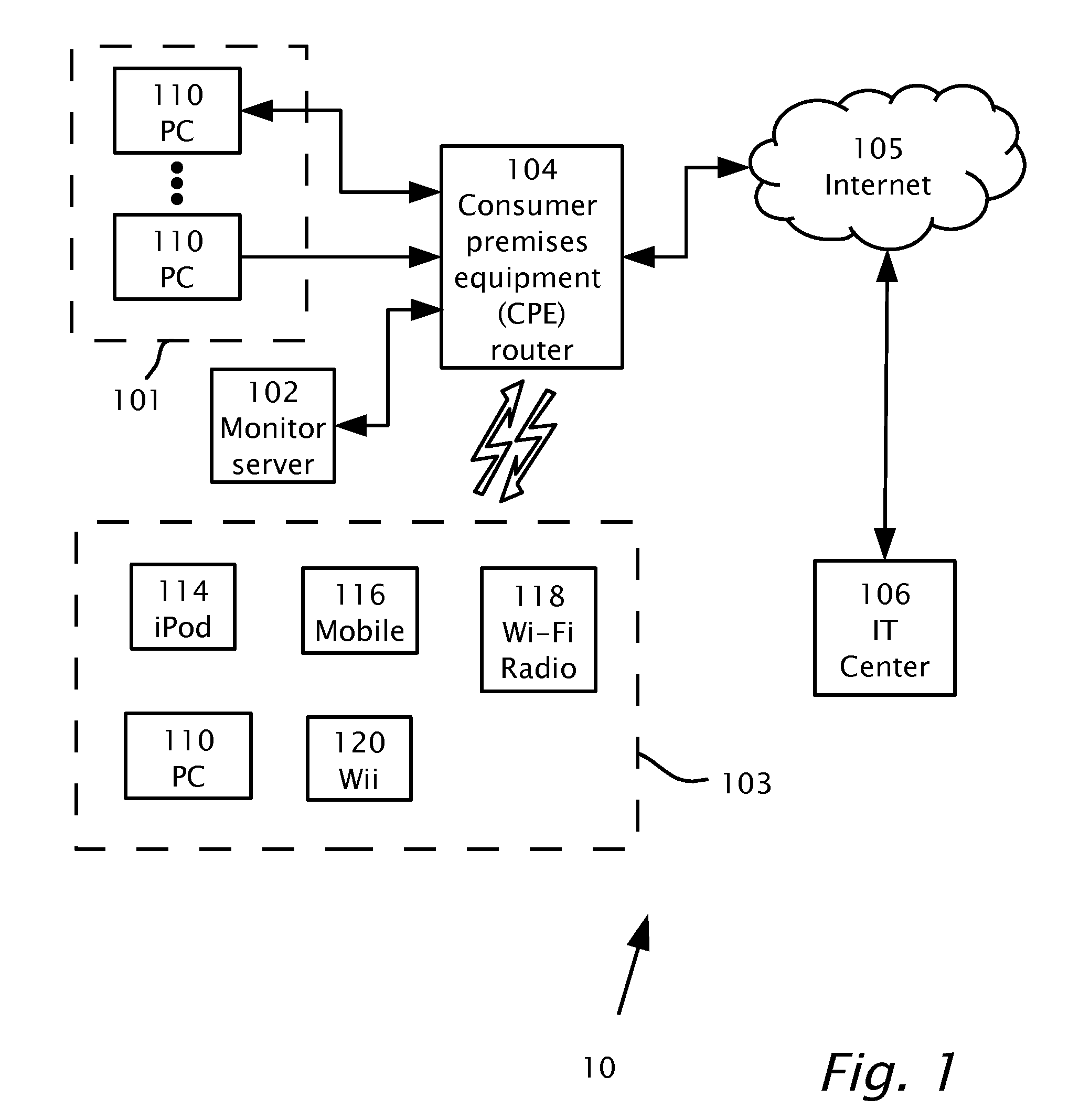
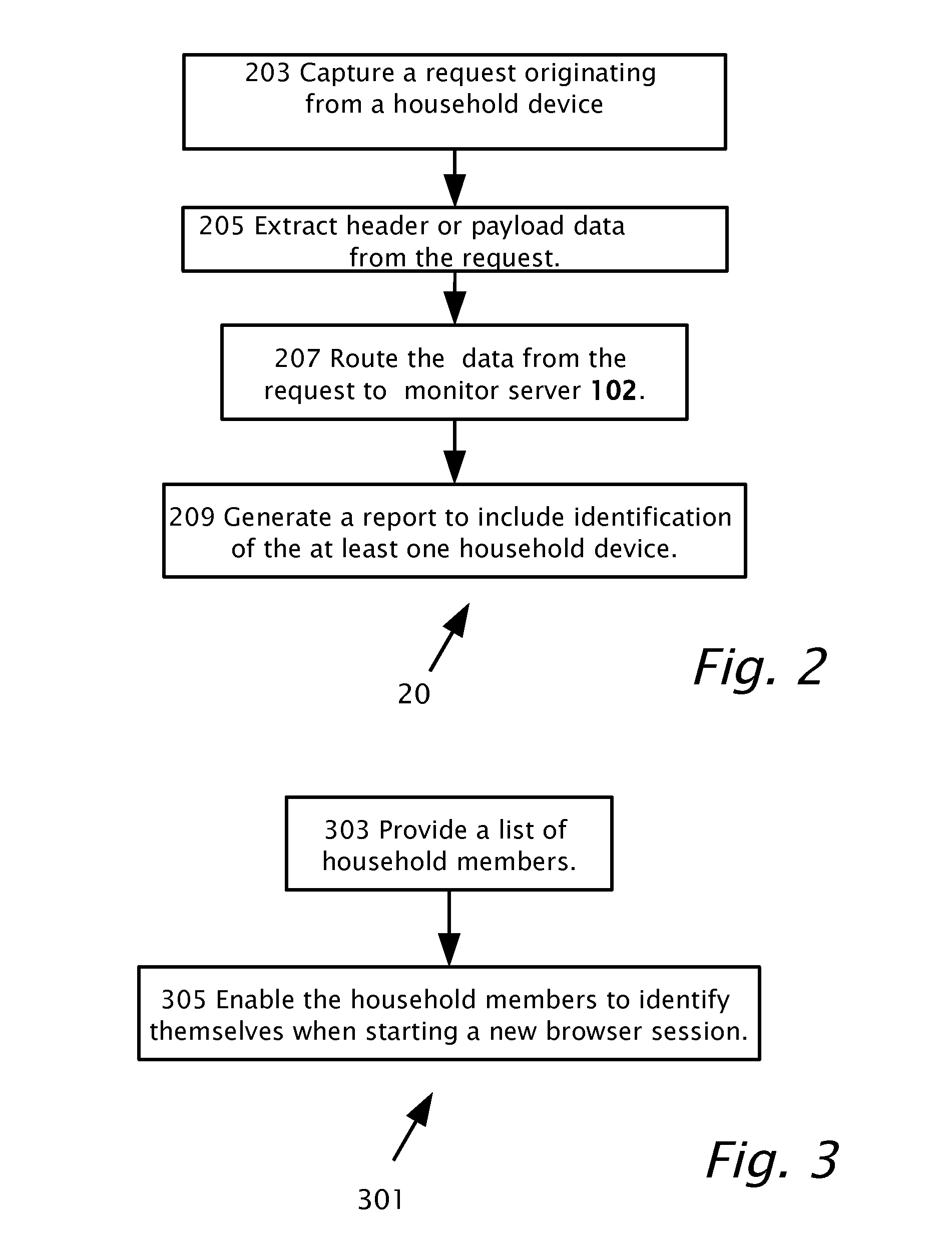
Tracking Internet Usage In A Household
Tracking Internet usage in a home network including multiple household computing devices connectible using a consumer premises router. An agent is installable in the consumer premises router. A monitor server operatively connects to the consumer premises router. The agent is operable to: capture a request originating from at least one of the household devices and to extract data from the request. The data may include an identifier of the household device initiating the request.
Owner:MOBILE RES LABS
A method of surfing the Internet using mobile phones as hotspots
InactiveCN102271187AMeet the needs of instant Internet accessSubstation equipmentTransmissionData synchronizationElectronic mail
The invention relates to a method for surfing the Internet using a mobile phone as a hotspot, and belongs to the field of wireless information communication. It mainly involves mobile phones and wireless devices with Internet access. Its characteristics are: firstly, it is determined that the mobile phone as the wireless signal transmitter has the Internet access function and conditions, and then the relevant system is installed on the mobile phone to make your mobile phone a mobile wireless router. As long as the mobile phone, palmtop or laptop computer with the function of connecting to the wireless local area network is connected to the shared Internet, you can surf the Internet, use e-mail, use Internet calls, etc. In addition to using this method as a hotspot to access the Internet, the system installed on the mobile phone can also support data synchronization, which can easily synchronize contacts and memo pads in the PC terminal or mobile phone wireless signal receiver Outlook with the mobile phone as a hotspot, thereby Bring great convenience to your daily communication. The invention embodies the effectiveness and convenience of scientific and technological progress, and its available space and expansion performance cannot be underestimated.
Owner:SUZHOU BAMMIT INFORMATION TECH
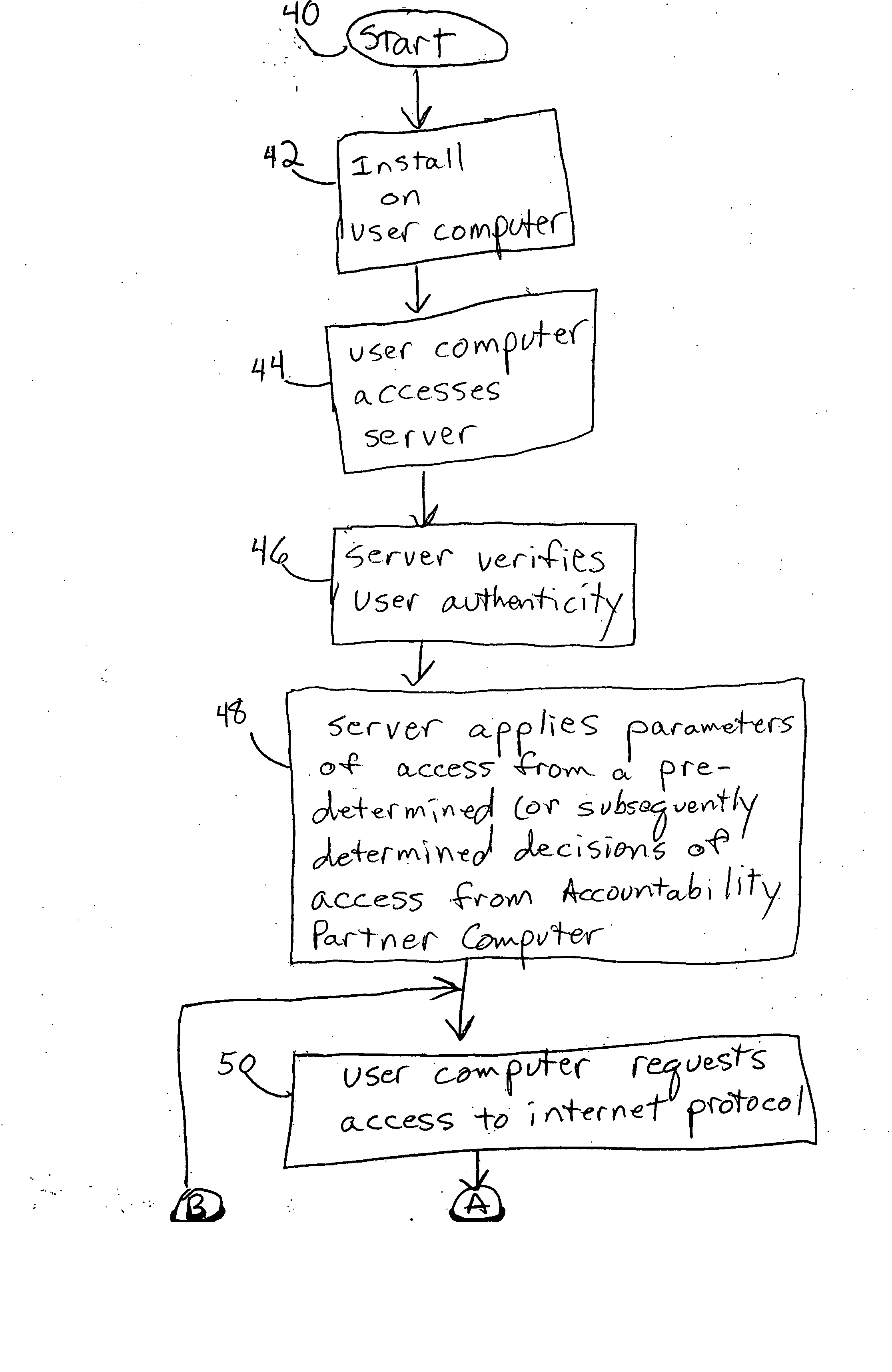
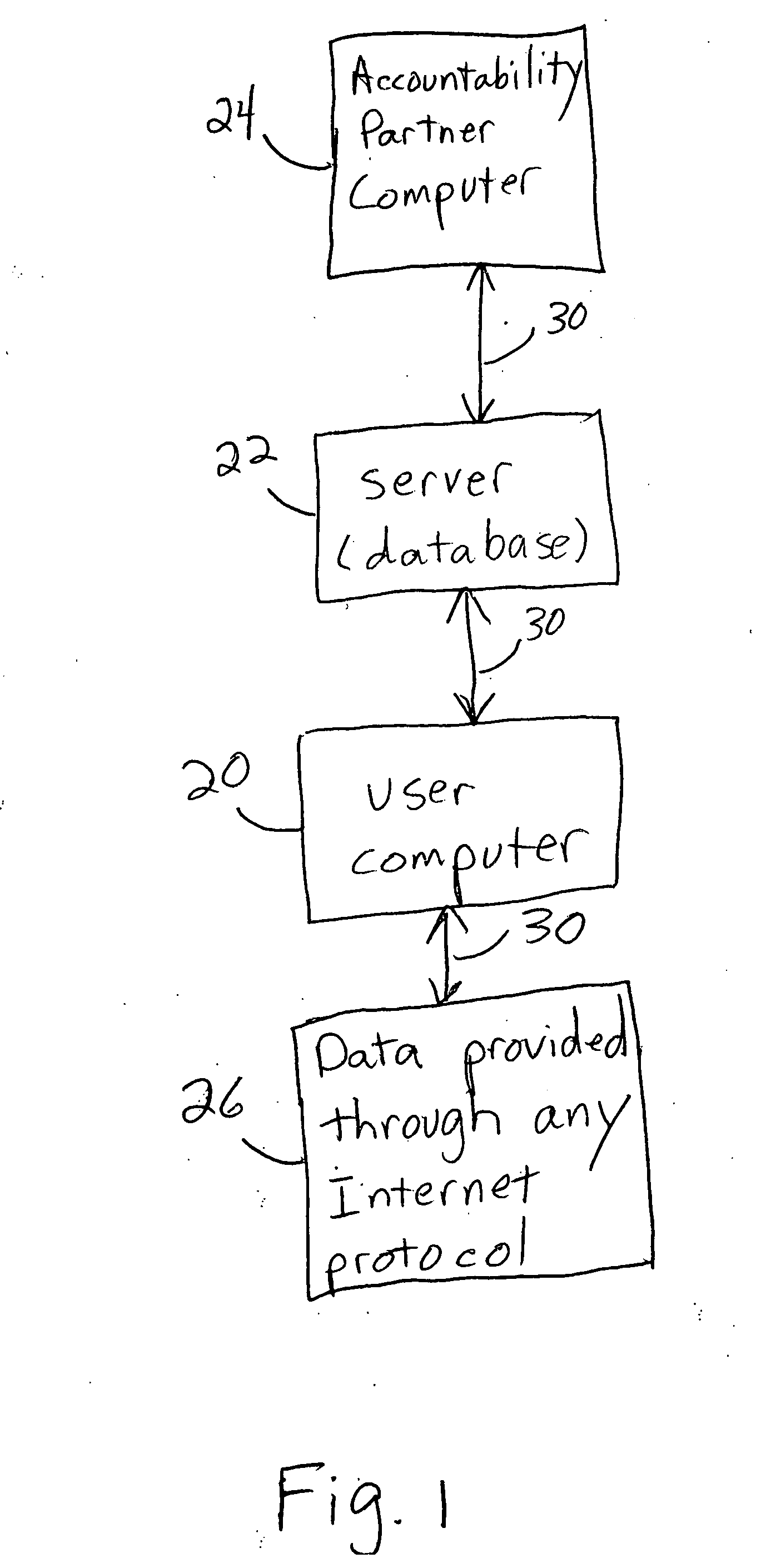
Access of Internet use for a selected user
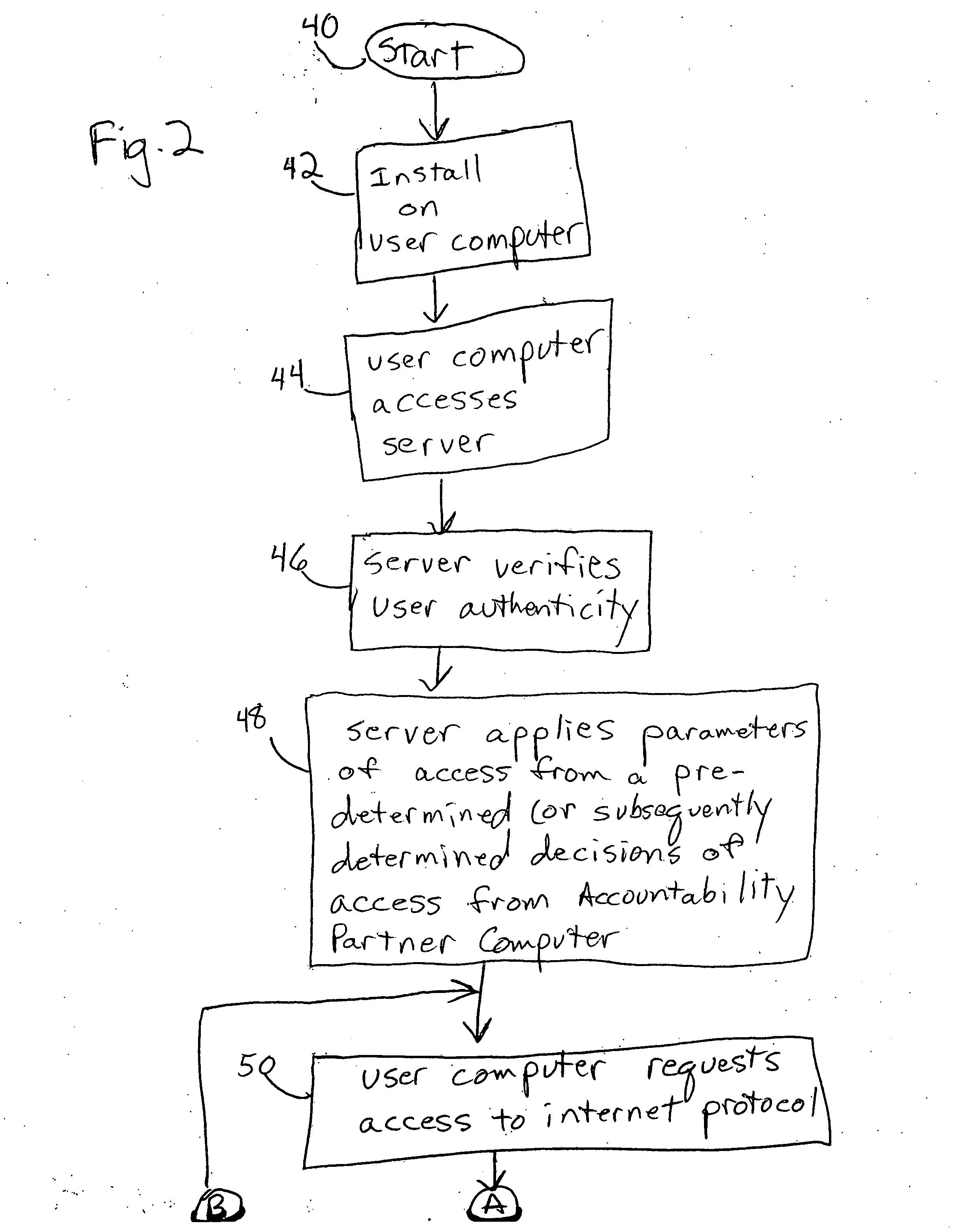
InactiveUS20070061869A1Digital data processing detailsUser identity/authority verificationUsenet newsgroupComputer users
A system for the provision of accountability for and blocking of Internet use of a selected computer user. The system includes a computer which has Internet access blocked, a remote server, and a second computer at which an Accountability Partner communicates to the remote server, such that Internet access is permitted to the person using the first computer. The Internet access activity includes access of at least one Internet protocol from the group consisting of newsgroups, file sharing programs, file transfer programs, chat rooms, peer to peer chats cell phone or PDA transmissions, http, https, and electronic mail activity.
Owner:COVENANT EYES
Multicast-based network data pre-pushing method
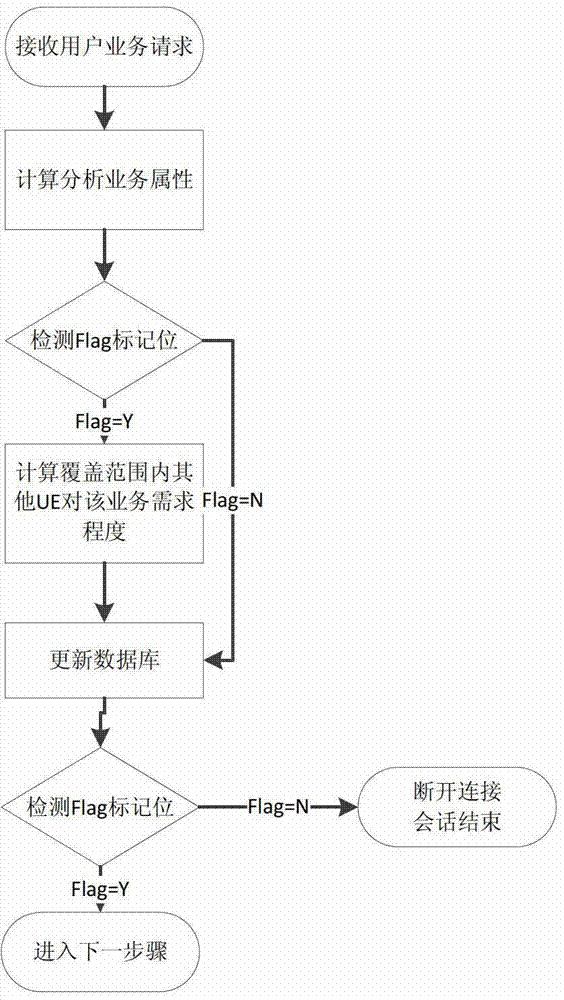
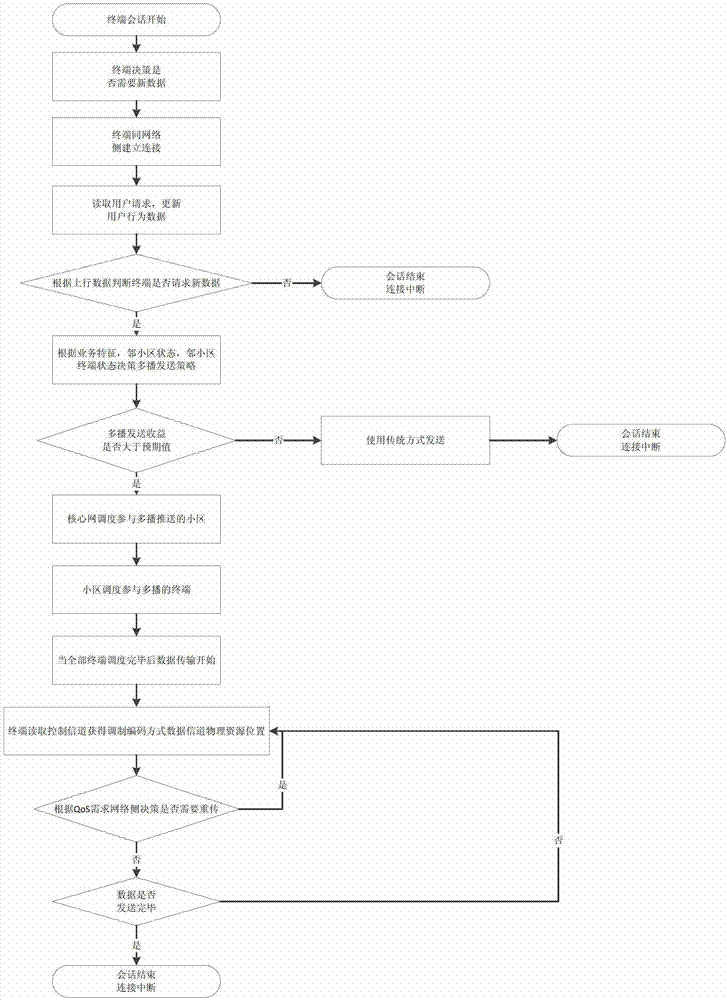
ActiveCN103249006ATo overcome the disadvantage of repeated transmissionImprove resource utilizationEnergy efficient ICTBroadcast service distributionFrequency spectrumHabit
The invention discloses a multicast-based network data pre-pushing method, and belongs to the technical field of wireless network data transmission. In wireless network data transmission, when a user requests network data, according to task request analysis and current network channel states, a base station determines whether the task is pre-pushed in a multicast manner to users with similar internet use habits and within the coverage area of the base station or in neighboring cells; according to a prior probability function of user's internet use habits accumulated previously and channel states of active users, an alternative user scheme, a multi-cell coordinated transmission scheme and a modulation coding scheme that all participate in multicast pre-pushing are calculated; expected revenue which can be obtained by adopting the multicast manner is calculated; and compared with a conventional unicast manner, if the multicast manner obtains the revenue greater than a set threshold value, the multicast-based network data pre-pushing method is adopted for pushing, otherwise, a conventional method is adopted for pushing. The multicast-based network data pre-pushing method can effectively improve the wireless spectrum efficiency and the energy efficiency, and optimizes the transmission performance of the network on the whole.
Owner:北京英特赛科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com