Protective system
A technology for protecting systems, computers, used in the field of Internet user identification and filtering
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
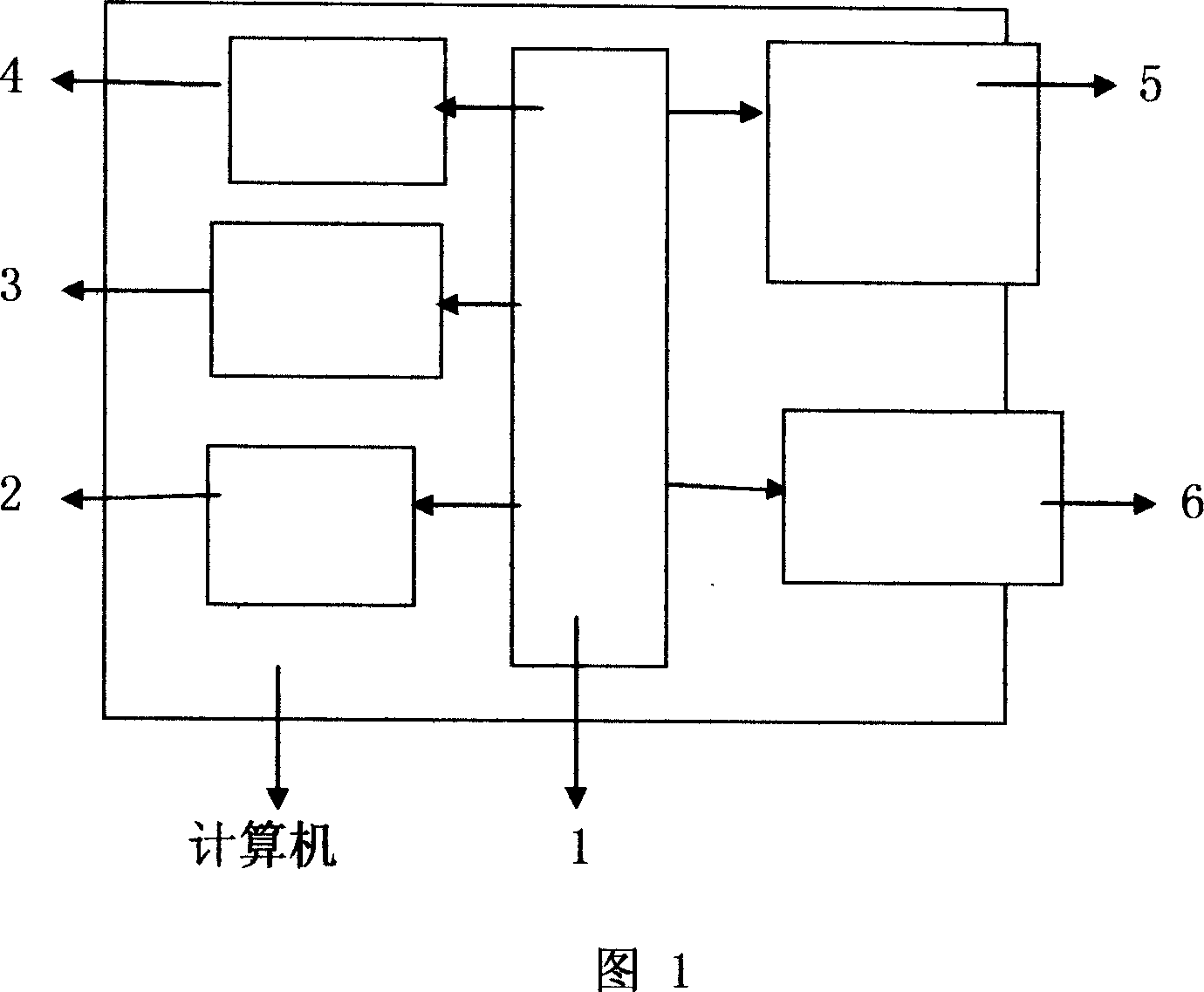
[0010] Embodiment 1: Referring to FIG. 1, the block diagram of the present invention includes: a computer, a control module 1 inside the computer, an input / output module 2, a display module 3, a communication module 4, an age identification device 5, and a storage module 6.
[0011] The control module 1 is connected with the I / O module 2 , the display module 3 , the communication module 4 , the age identification device 5 and the storage module 6 .
[0012] Age recognition device 5 comprises biometrics (hand shape, palm print, face image, handwriting, facial camera, fingerprint, the position of eye corner, pupil center, pupil radius, the position of eye corner, iris, pulse, DNA, specific protein, smell, Sound, ear shape, retina, hand shape, footprint, infrared thermogram, height, weight, lip pattern, brain pattern, blood pattern, key pressure recognition and other biometric devices, ID card, smart card, smart label, certificate) more than one , other age and / or identity identi...
Embodiment 2
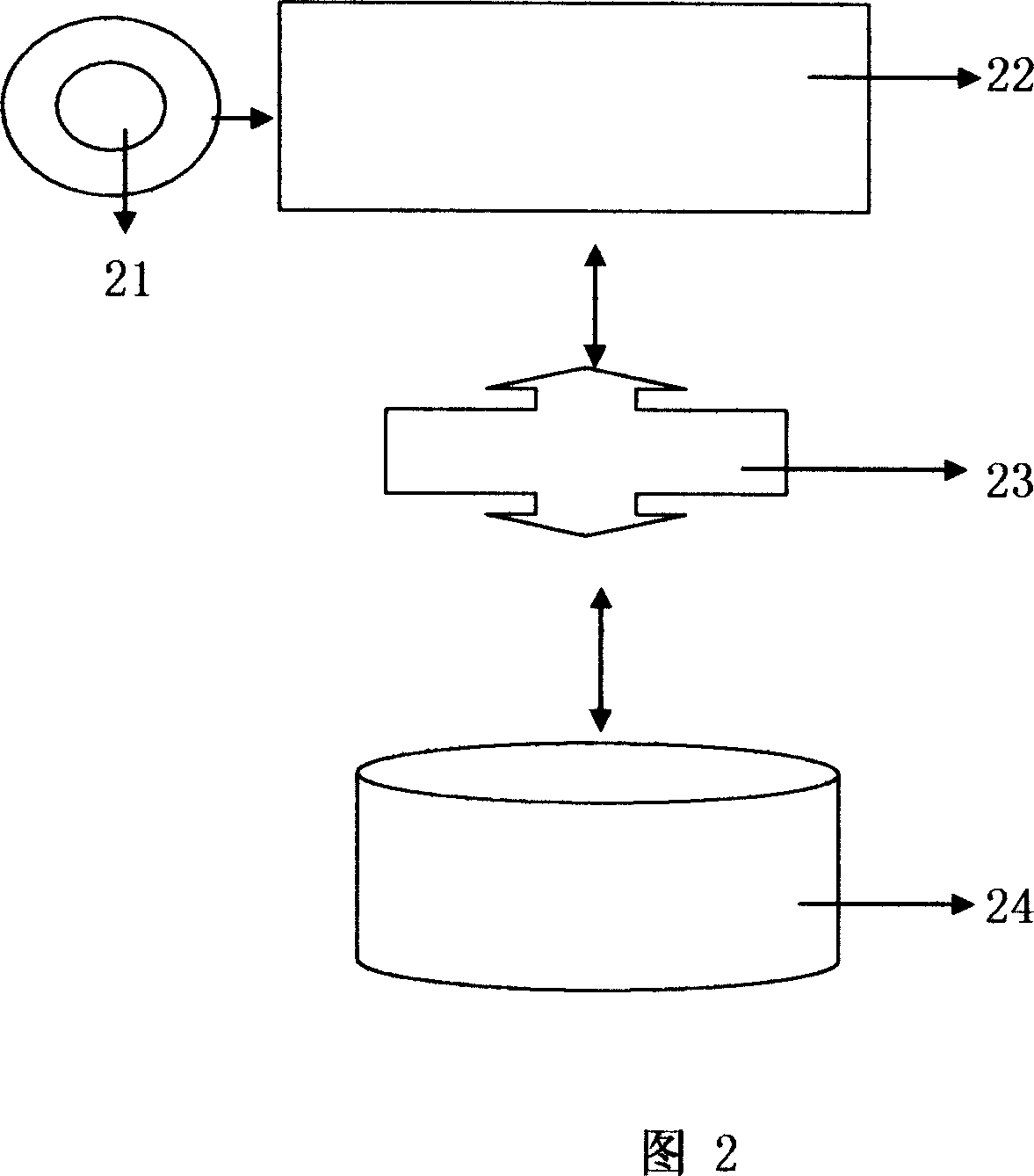
[0022] Embodiment 2: Referring to FIG. 2, the system block diagram of the present invention includes: an age identification device 21, a computer 22, a network 23, and a server 24;
[0023] The age recognition device 21 is connected to a computer 22, and the computer 22 is connected to a server 24 through a network 23;
[0024] Age identification device 21 and / or computer 22 and / or network 23 and / or server 24 install age identification program, data identification program, age code and / or password classification / processing program, comparison database, transmission control program, encryption and decryption program , the remote notifier.
[0025] Age identification device 21 and / or computer 22 and / or network 23 and / or server 24 perform age / gender and / or identity and / or password and / or bad crime and / or credit identification and filter / classify data for users .
[0026] The age identification program identifies and / or compares the data read by the age identification device 21 ...
Embodiment 3
[0033]Embodiment 3: In the computer and / or network and / or server, the age identification program identifies and / or compares the data read by the age identification device 21, and performs age / sex and / or identity and / or password for the user. And / or bad crime and / or credit identification, age code and / or password classification / processing program automatically performs age code and / or password classification / processing on the input data (add age identification code and / or identification code / bad crime / Credit identification code) (such as identification code 10 for ages 3-10, code 20 for ages 11-20, code 30 for ages 20-30, code 40 for ages 30-40; if the identification code for bad crimes is 1-20, it is distinguished according to the crime level; For example, credit identification code grades 1-10 are distinguished according to credit grades), and the content includes URLs, web pages, multimedia (text, sound, music, images) materials and other materials.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com