Uni-directional cross-domain identity verification based on low correlation of private cipher key and application thereof
An identity verification method and private key technology, applied in the direction of user identity/authority verification, etc., can solve problems such as one-way identity verification function, separate registration, etc., and achieve the effect of good privacy, low correlation, and convenient use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
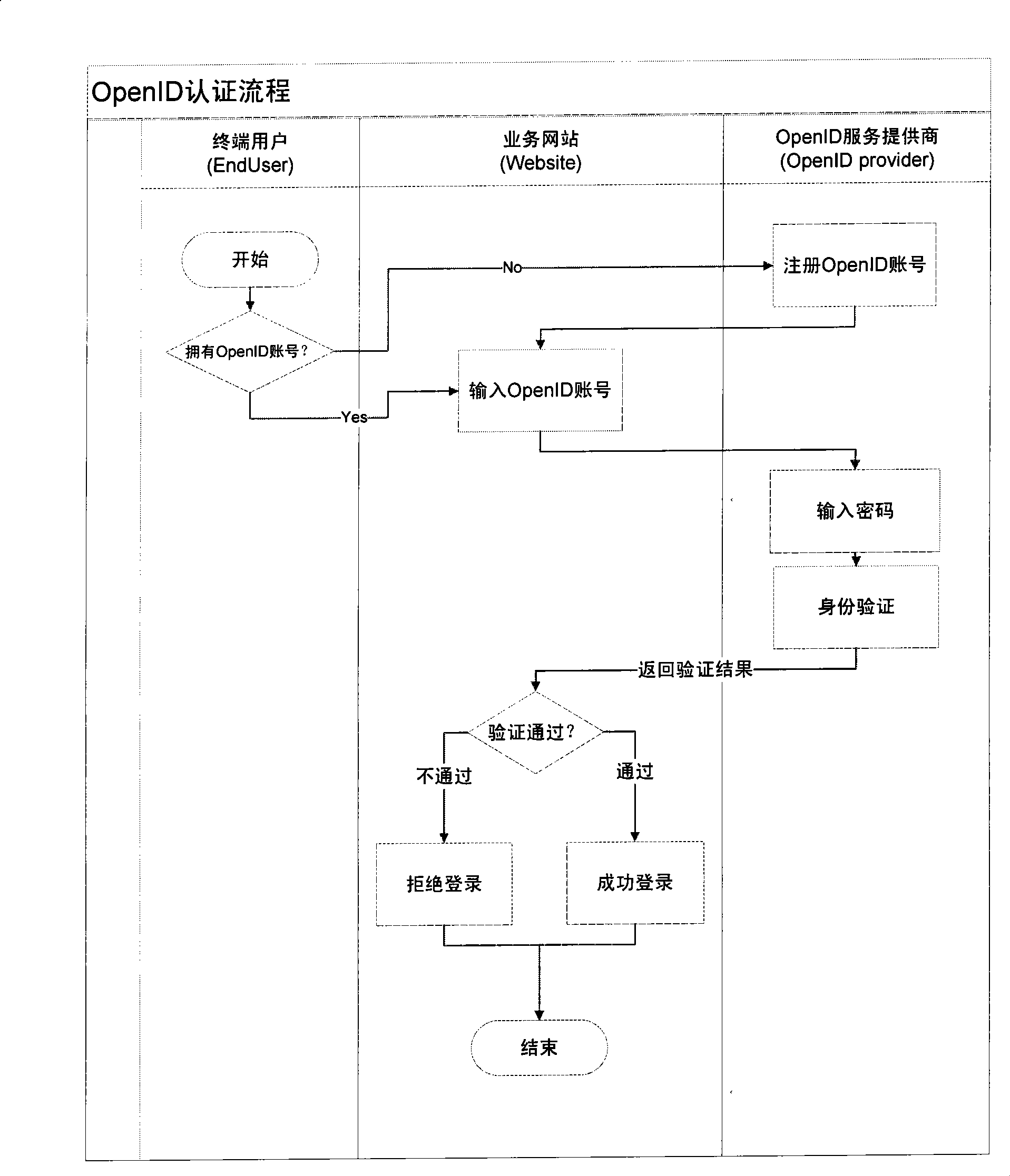
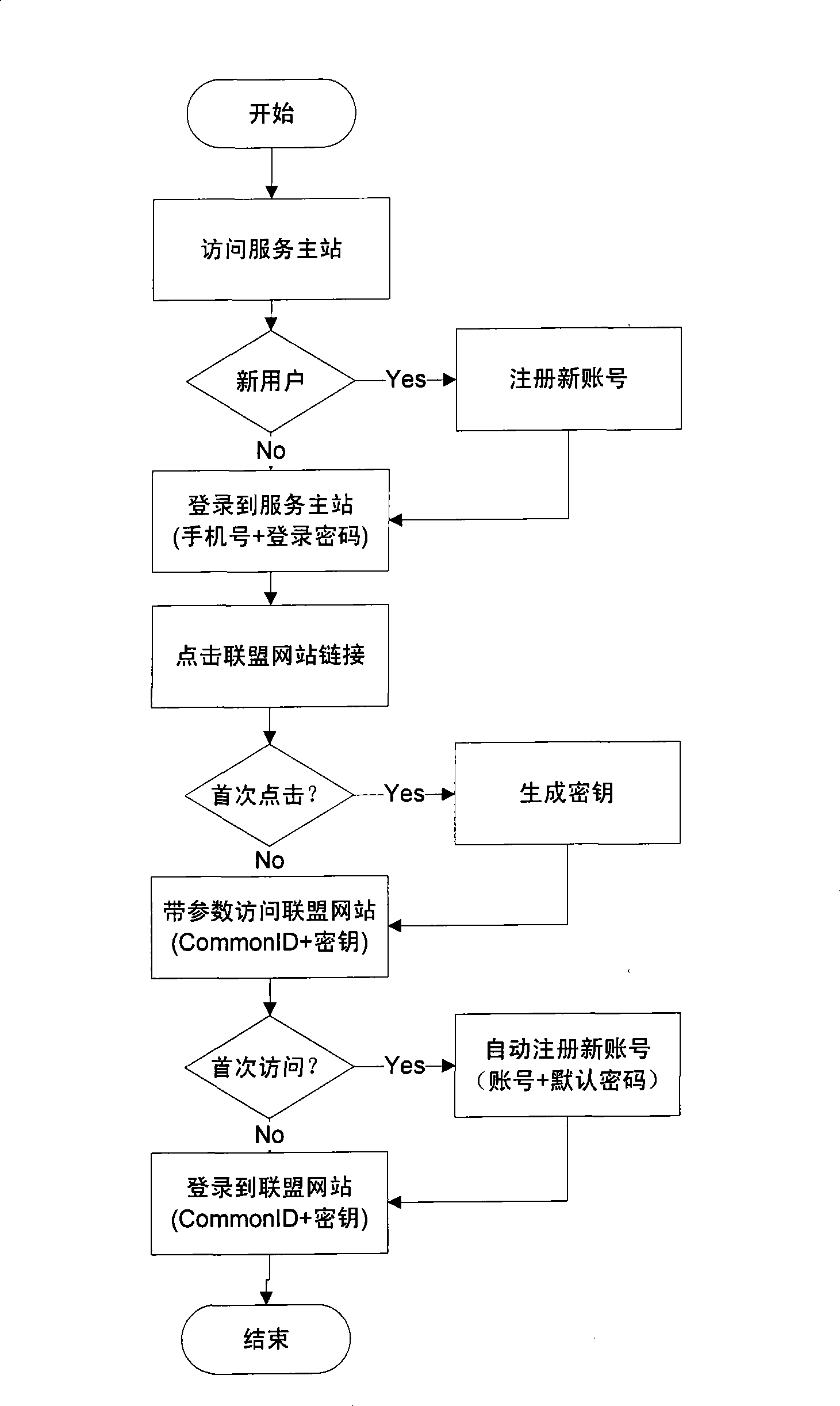
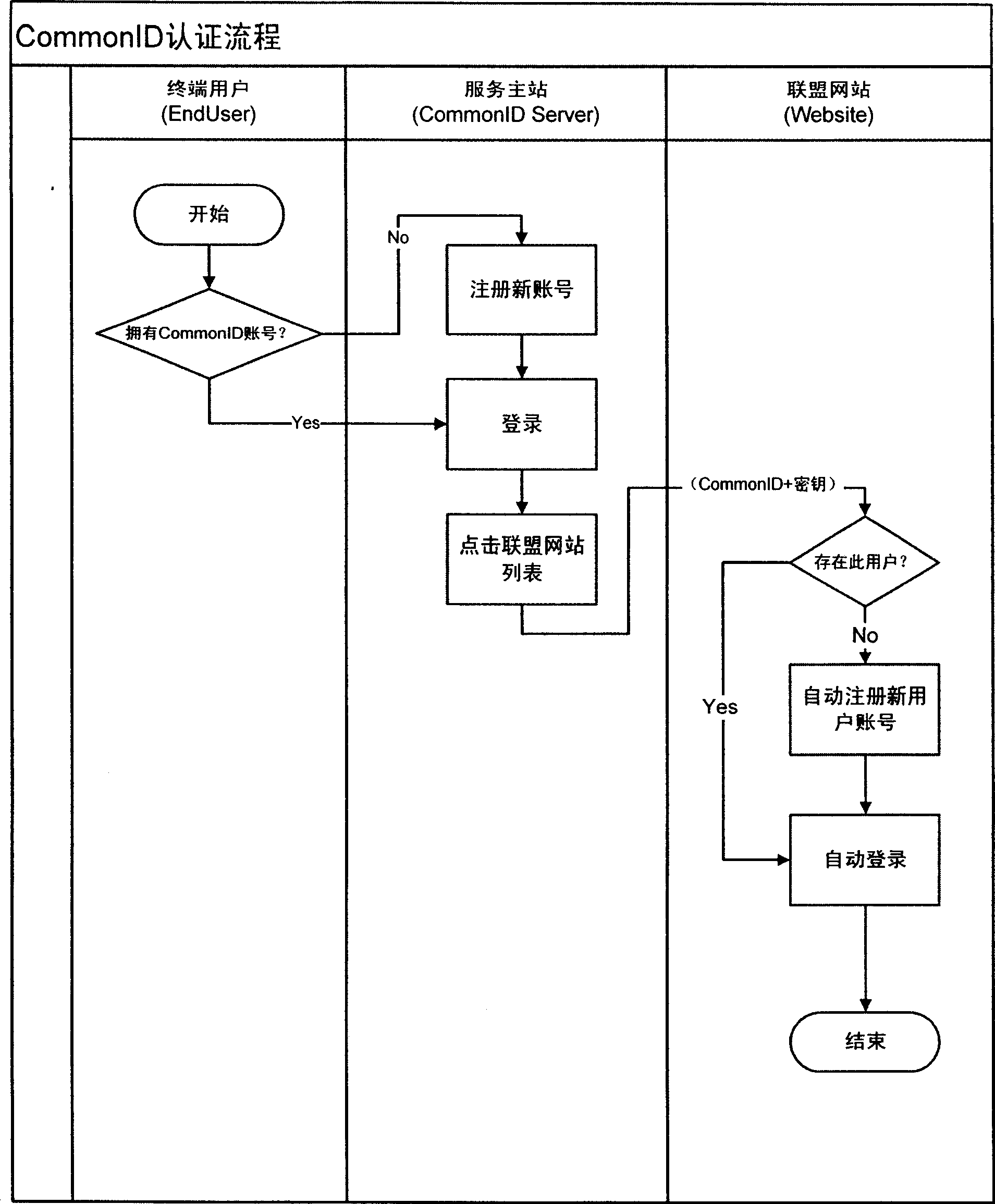
[0035] Figure 2 ~ Figure 4 Show the specific process of the present invention, by figure 2 , image 3 It can be seen that the low-correlation one-way cross-domain authentication method based on the private key includes the following steps:
[0036] (1-1) Before users operate, in order to support the identification number (CommonID) function, the alliance website needs to make the following modifications to the original system (see Figure 4 ): (1) Add "receiving module" and "data access module". The function of "receiving module" is to obtain two parameters from the service master station: identification number and key; (2) Add "CommonID automatic login module" and "CommonID automatic registration module", "CommonID automatic login module" is to realize the common ID + password The "CommonID automatic registration module" is to realize the automatic registration through the identification number CommonID+key method, and the parameters required for the user registr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com